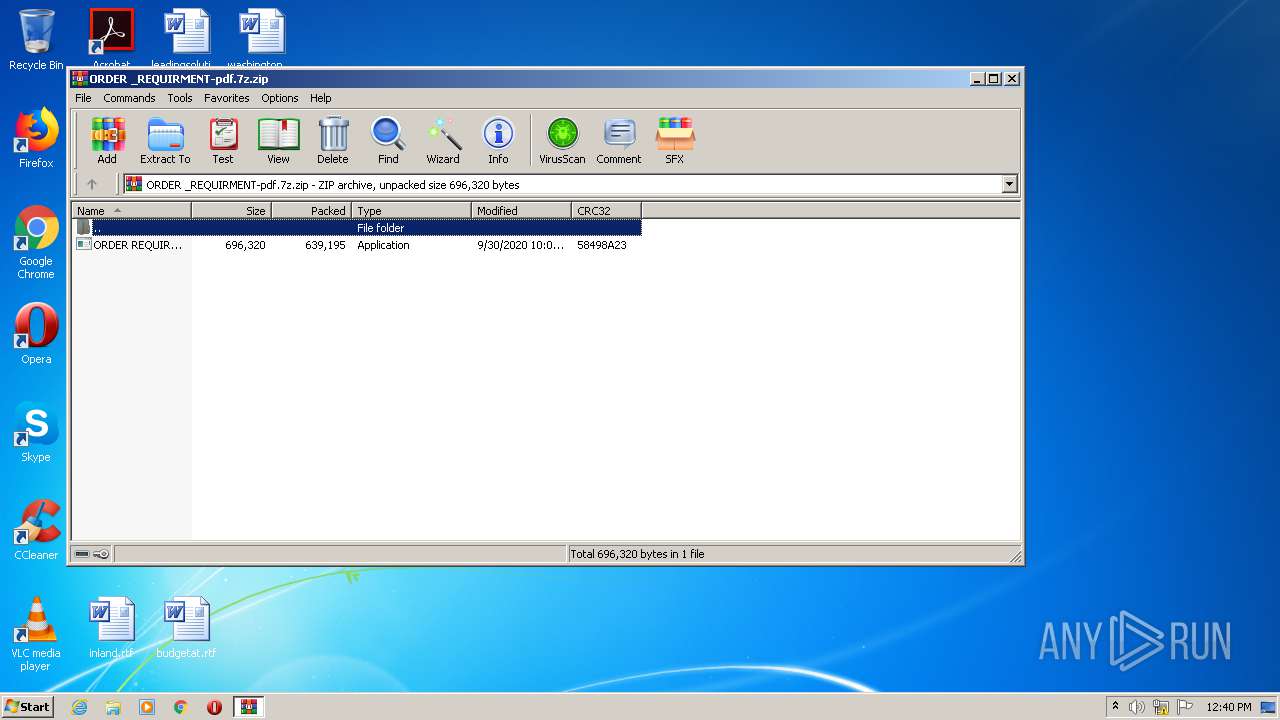
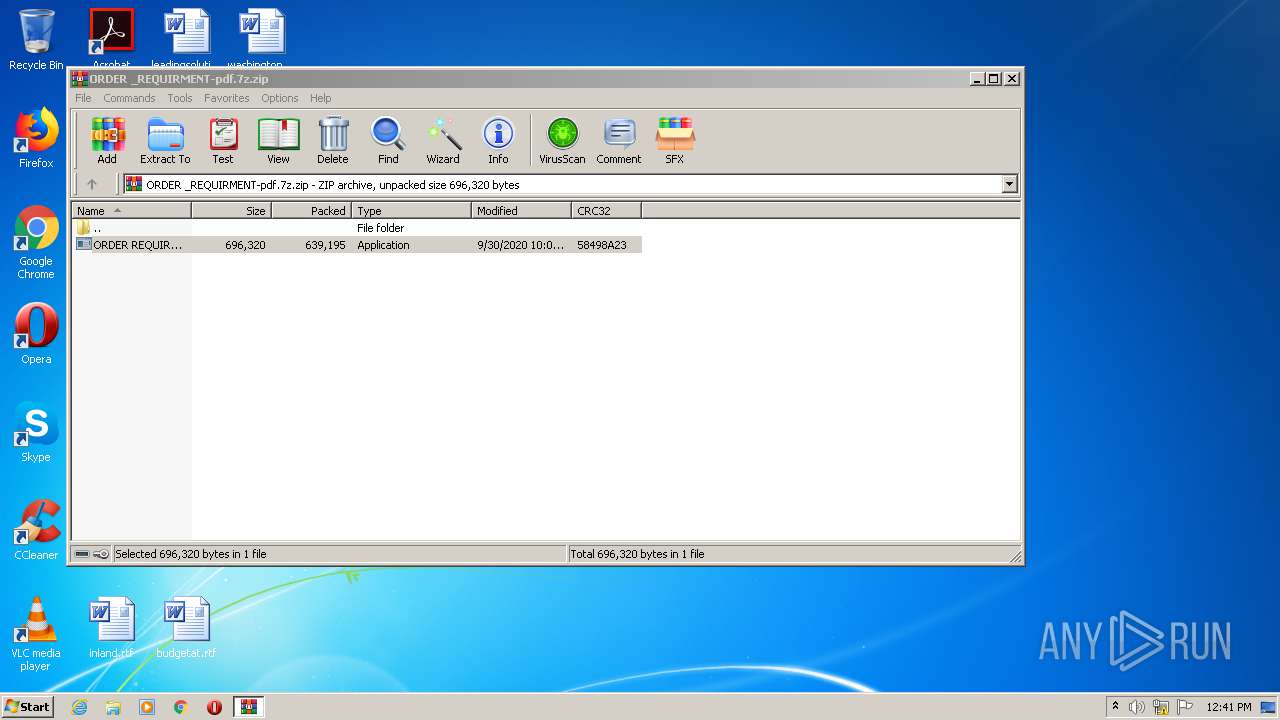
| File name: | ORDER _REQUIRMENT-pdf.7z |
| Full analysis: | https://app.any.run/tasks/d5799419-7ce1-4690-aed3-5513721cc3f2 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | September 30, 2020, 11:40:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | FAC0600E68996B83B16BA807982C794D |
| SHA1: | 4A36A56B212064C3F3C0F6735BADB3D63C735D44 |
| SHA256: | 1F1BBE061B7A239D1FCA44939347A10122C3A6EE2B350FC5D50F8D200AF6281D |
| SSDEEP: | 12288:PcY4s5FjJUrq7MSrwb+Kb3mFH1VB4sTRWm4xUfkfKRY62yVdzr/N00mZ:PcY4sb9FHwb+I3mV1VB4sTRixUfkjyVA |
MALICIOUS
Application was dropped or rewritten from another process
- ORDER REQUIRMENT-pdf.exe (PID: 2316)
- ORDER REQUIRMENT-pdf.exe (PID: 2176)
AGENTTESLA was detected
- ORDER REQUIRMENT-pdf.exe (PID: 2176)
Actions looks like stealing of personal data
- ORDER REQUIRMENT-pdf.exe (PID: 2176)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1920)
Application launched itself
- ORDER REQUIRMENT-pdf.exe (PID: 2316)
INFO
Manual execution by user
- ORDER REQUIRMENT-pdf.exe (PID: 2316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:09:30 10:09:01 |
| ZipCRC: | 0x58498a23 |
| ZipCompressedSize: | 639195 |
| ZipUncompressedSize: | 696320 |
| ZipFileName: | ORDER REQUIRMENT-pdf.exe |
Total processes
38
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1920 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ORDER _REQUIRMENT-pdf.7z.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2176 | "{path}" | C:\Users\admin\Desktop\ORDER REQUIRMENT-pdf.exe | ORDER REQUIRMENT-pdf.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: drawableObjects Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2316 | "C:\Users\admin\Desktop\ORDER REQUIRMENT-pdf.exe" | C:\Users\admin\Desktop\ORDER REQUIRMENT-pdf.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: drawableObjects Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
503
Read events
483
Write events
20
Delete events
0
Modification events
| (PID) Process: | (1920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1920) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ORDER _REQUIRMENT-pdf.7z.zip | |||
| (PID) Process: | (1920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2176) ORDER REQUIRMENT-pdf.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ORDER REQUIRMENT-pdf_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2176) ORDER REQUIRMENT-pdf.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ORDER REQUIRMENT-pdf_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1920 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1920.40034\ORDER REQUIRMENT-pdf.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
8
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2176 | ORDER REQUIRMENT-pdf.exe | 98.142.108.42:21 | ftp.ayudasaudiovisuales.com | HostDime.com, Inc. | FR | malicious |
2176 | ORDER REQUIRMENT-pdf.exe | 98.142.108.42:31792 | ftp.ayudasaudiovisuales.com | HostDime.com, Inc. | FR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ftp.ayudasaudiovisuales.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2176 | ORDER REQUIRMENT-pdf.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2176 | ORDER REQUIRMENT-pdf.exe | A Network Trojan was detected | ET TROJAN AgentTesla Exfil via FTP |
2176 | ORDER REQUIRMENT-pdf.exe | A Network Trojan was detected | ET TROJAN AgentTesla HTML System Info Report Exfil via FTP |
2176 | ORDER REQUIRMENT-pdf.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
2176 | ORDER REQUIRMENT-pdf.exe | A Network Trojan was detected | ET TROJAN AgentTesla HTML System Info Report Exfil via FTP |
2176 | ORDER REQUIRMENT-pdf.exe | A Network Trojan was detected | SPYWARE [PTsecurity] AgentTesla Exfiltration |
2 ETPRO signatures available at the full report