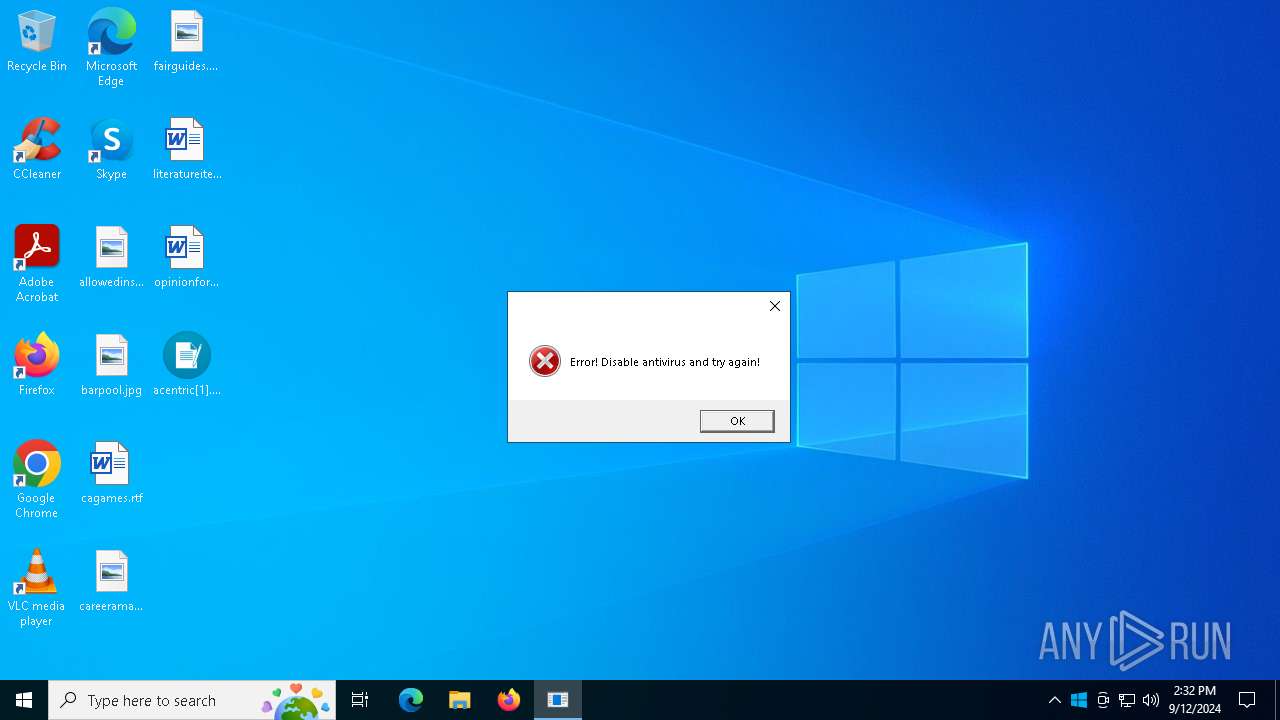
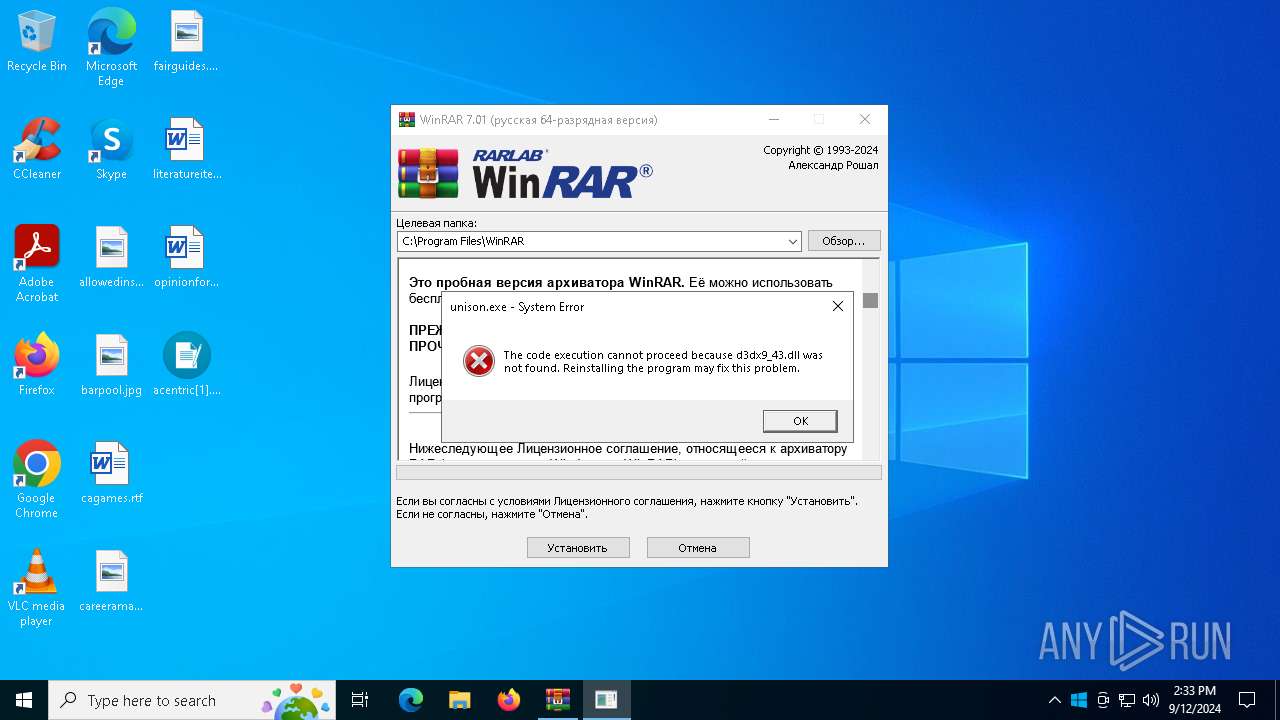
| File name: | acentric[1].exe |
| Full analysis: | https://app.any.run/tasks/066adc63-e6a5-4414-ad38-b1013f1d3eb2 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | September 12, 2024, 14:31:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 37D198AD751D31A71ACC9CB28ED0C64E |
| SHA1: | 8EB519B7A6DF66D84C566605DA9A0946717A921D |
| SHA256: | 1ED4A8B4C74AAB435EA5CD459D5AC961E5A8CA28924801BD84D336135F30EFDE |
| SSDEEP: | 6144:OKF06ln2krIyZLr/tjERcgIgSpL5n9lZKF0Zlk2krI1ZPrZt:OKF06lSyZLr/td9bKF0ZlT1ZPrZt |
MALICIOUS
XORed URL has been found (YARA)
- acentric[1].exe (PID: 2480)
- winmsbt.exe (PID: 3908)
Changes the autorun value in the registry
- winmsbt.exe (PID: 3908)
- acentric[1].exe (PID: 2480)
- kitty.exe (PID: 7436)
- Cerker.exe (PID: 7612)
- acentric.exe (PID: 8000)
- acentric.exe (PID: 7716)
AMADEY has been detected (SURICATA)
- explorer.exe (PID: 3672)
- Hkbsse.exe (PID: 6720)
- axplong.exe (PID: 6708)
Connects to the CnC server
- explorer.exe (PID: 3672)
- mSOoiAKqbK.exe (PID: 6812)
- Hkbsse.exe (PID: 6720)
- axplong.exe (PID: 6708)
- RegAsm.exe (PID: 304)
- BDKwkNtBSP.exe (PID: 2820)
- stealc_default2.exe (PID: 7172)
- bundle.exe (PID: 644)
- svchost015.exe (PID: 6824)
- Sеtup.exe (PID: 7420)
- RegAsm.exe (PID: 5184)
- channel33.exe (PID: 5376)
- icvideoconverter_32.exe (PID: 5760)
Amadey has been detected
- exbuild.exe (PID: 6372)
- Hkbsse.exe (PID: 6720)
- Nework.exe (PID: 4436)
- Hkbsse.exe (PID: 2868)
- Hkbsse.exe (PID: 6276)
- Hkbsse.exe (PID: 2400)
- Hkbsse.exe (PID: 8000)
- Hkbsse.exe (PID: 7296)
Stealers network behavior
- mSOoiAKqbK.exe (PID: 6812)
- Gj7FUXV4FC.exe (PID: 3900)
- RegAsm.exe (PID: 304)
- BDKwkNtBSP.exe (PID: 2820)
- stealc_default2.exe (PID: 7172)
- vlst.exe (PID: 8132)
- bundle.exe (PID: 644)
- svchost015.exe (PID: 6824)
- penis.exe (PID: 7984)
- RegAsm.exe (PID: 6456)
- RegAsm.exe (PID: 3208)
- RegAsm.exe (PID: 6316)
- RegAsm.exe (PID: 5732)
- RegAsm.exe (PID: 788)
REDLINE has been detected (SURICATA)
- mSOoiAKqbK.exe (PID: 6812)
- RegAsm.exe (PID: 304)
- BDKwkNtBSP.exe (PID: 2820)
- bundle.exe (PID: 644)
METASTEALER has been detected (SURICATA)
- mSOoiAKqbK.exe (PID: 6812)
- Gj7FUXV4FC.exe (PID: 3900)
- RegAsm.exe (PID: 304)
- BDKwkNtBSP.exe (PID: 2820)
- vlst.exe (PID: 8132)
- bundle.exe (PID: 644)
- penis.exe (PID: 7984)
- RegAsm.exe (PID: 6456)
- RegAsm.exe (PID: 3208)
- RegAsm.exe (PID: 6316)
- RegAsm.exe (PID: 788)
Steals credentials from Web Browsers
- Gj7FUXV4FC.exe (PID: 3900)
- mSOoiAKqbK.exe (PID: 6812)
- Vhzuag1W7Z.exe (PID: 6456)
- BDKwkNtBSP.exe (PID: 2820)
- RegAsm.exe (PID: 304)
- vlst.exe (PID: 8132)
- stealc_default2.exe (PID: 7172)
- penis.exe (PID: 7984)
- bundle.exe (PID: 644)
- RegAsm.exe (PID: 6456)
- RegAsm.exe (PID: 3208)
- RegAsm.exe (PID: 6316)
- RegAsm.exe (PID: 788)
Actions looks like stealing of personal data
- Gj7FUXV4FC.exe (PID: 3900)
- mSOoiAKqbK.exe (PID: 6812)
- Vhzuag1W7Z.exe (PID: 6456)
- RegAsm.exe (PID: 304)
- BDKwkNtBSP.exe (PID: 2820)
- stealc_default2.exe (PID: 7172)
- vlst.exe (PID: 8132)
- Sеtup.exe (PID: 7420)
- penis.exe (PID: 7984)
- bundle.exe (PID: 644)
- channel33.exe (PID: 5376)
- RegAsm.exe (PID: 6456)
- RegAsm.exe (PID: 5184)
- RegAsm.exe (PID: 3208)
- 3546345.exe (PID: 4344)
- RegAsm.exe (PID: 6316)
- RegAsm.exe (PID: 5732)
- RegAsm.exe (PID: 788)
StealC has been detected
- stealc_default2.exe (PID: 7172)
- svchost015.exe (PID: 6824)
Uses Task Scheduler to run other applications
- Cerker.exe (PID: 7612)
- kitty.exe (PID: 7436)
- cmd.exe (PID: 7860)
- Sеtup.exe (PID: 7420)
STEALC has been detected (SURICATA)
- stealc_default2.exe (PID: 7172)
- svchost015.exe (PID: 6824)
AMADEY has been detected (YARA)
- explorer.exe (PID: 3672)
- Hkbsse.exe (PID: 6720)
- axplong.exe (PID: 6708)
BERBEW mutex has been found
- RegAsm.exe (PID: 5184)
CRYPTBOT has been detected (SURICATA)
- Sеtup.exe (PID: 7420)
- channel33.exe (PID: 5376)
CRYPTBOT has been detected (YARA)
- 3546345.exe (PID: 4344)
PRIVATELOADER has been detected (SURICATA)
- RegAsm.exe (PID: 5184)
DANABOT has been detected (YARA)
- freedom.exe (PID: 7556)
SOCKS5SYSTEMZ has been detected (SURICATA)
- icvideoconverter_32.exe (PID: 5760)
VIDAR has been detected (YARA)
- RegAsm.exe (PID: 5732)
VIDAR has been detected (SURICATA)
- RegAsm.exe (PID: 5732)
SUSPICIOUS
Executable content was dropped or overwritten
- acentric[1].exe (PID: 2480)
- explorer.exe (PID: 3672)
- contorax.exe (PID: 3716)
- exbuild.exe (PID: 6372)
- crypteda.exe (PID: 2724)
- Hkbsse.exe (PID: 6720)
- cd5563c5b7.exe (PID: 5692)
- off.exe (PID: 6612)
- off.tmp (PID: 2024)
- axplong.exe (PID: 6708)
- crypteda.exe (PID: 4436)
- cmd.exe (PID: 4732)
- fikbbm0902845.exe (PID: 1608)
- icvideoconverter_32.exe (PID: 5760)
- kitty.exe (PID: 7436)
- cmd.exe (PID: 7276)
- Intake.pif (PID: 7824)
- stealc_default2.exe (PID: 7172)
- acentric.exe (PID: 8000)
- needmoney.exe (PID: 7908)
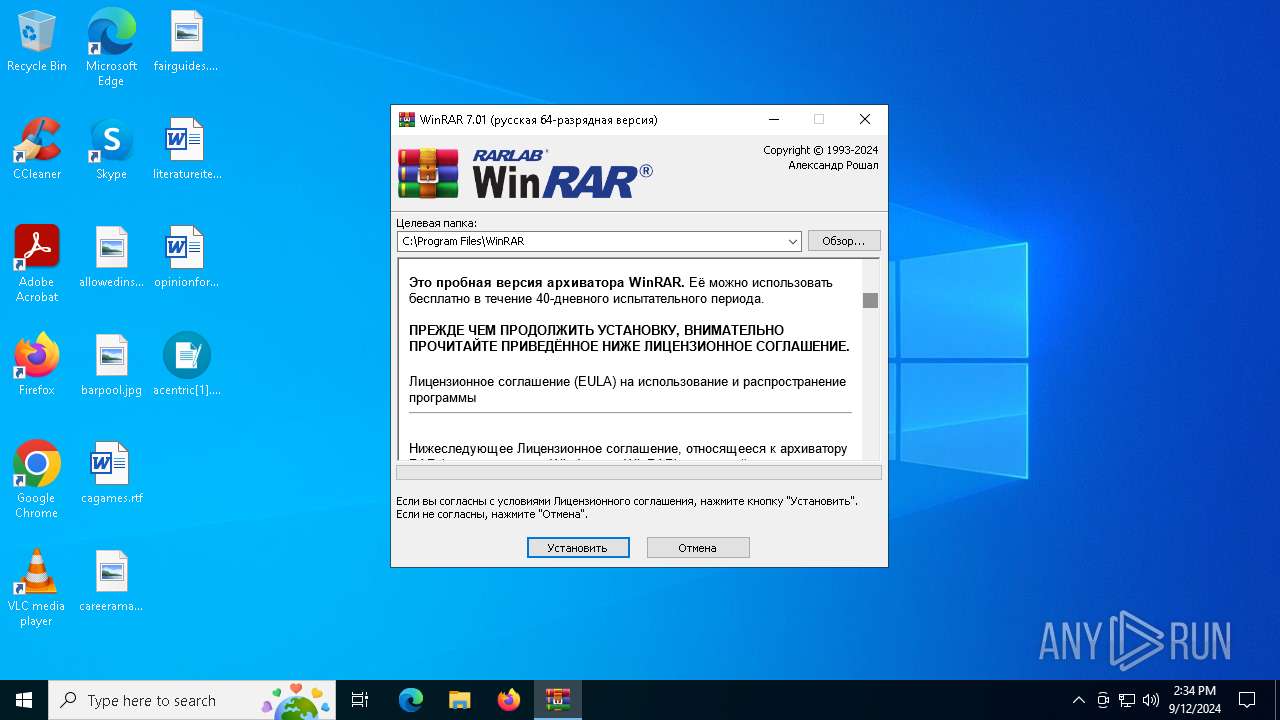
- WinRarInstall.exe (PID: 6428)
- winrar-x64-701ru.exe (PID: 3256)
- RegAsm.exe (PID: 5184)
Reads the date of Windows installation
- contorax.exe (PID: 3716)
- freedom.exe (PID: 7556)
- WinRarInstall.exe (PID: 6428)
- winrar-x64-701ru.exe (PID: 3256)
Reads security settings of Internet Explorer
- contorax.exe (PID: 3716)
- crypteda.exe (PID: 2724)
- exbuild.exe (PID: 6372)
- Hkbsse.exe (PID: 6720)
- cd5563c5b7.exe (PID: 5692)
- axplong.exe (PID: 6708)
- crypteda.exe (PID: 4436)
- stealc_default2.exe (PID: 7172)
- BowExpert.exe (PID: 7196)
- kitty.exe (PID: 7436)
- Cerker.exe (PID: 7612)
- freedom.exe (PID: 7556)
- svchost015.exe (PID: 6824)
- WinRarInstall.exe (PID: 6428)
- winrar-x64-701ru.exe (PID: 3256)
- Sеtup.exe (PID: 7420)
- RegAsm.exe (PID: 5184)
- icvideoconverter_32.exe (PID: 5760)
- RegAsm.exe (PID: 5732)
Starts itself from another location
- contorax.exe (PID: 3716)
- exbuild.exe (PID: 6372)
- cd5563c5b7.exe (PID: 5692)
- kitty.exe (PID: 7436)
Contacting a server suspected of hosting an CnC
- explorer.exe (PID: 3672)
- Hkbsse.exe (PID: 6720)
- Gj7FUXV4FC.exe (PID: 3900)
- axplong.exe (PID: 6708)
- stealc_default2.exe (PID: 7172)
- svchost015.exe (PID: 6824)
- penis.exe (PID: 7984)
- icvideoconverter_32.exe (PID: 5760)
Potential Corporate Privacy Violation
- explorer.exe (PID: 3672)
- Hkbsse.exe (PID: 6720)
- axplong.exe (PID: 6708)
- stealc_default2.exe (PID: 7172)
- RegAsm.exe (PID: 5184)
Process requests binary or script from the Internet
- explorer.exe (PID: 3672)
- Hkbsse.exe (PID: 6720)
- axplong.exe (PID: 6708)
- stealc_default2.exe (PID: 7172)
- RegAsm.exe (PID: 5184)
Connects to the server without a host name
- explorer.exe (PID: 3672)
- Hkbsse.exe (PID: 6720)
- axplong.exe (PID: 6708)
- stealc_default2.exe (PID: 7172)
- RegAsm.exe (PID: 5184)
Connects to unusual port
- mSOoiAKqbK.exe (PID: 6812)
- Gj7FUXV4FC.exe (PID: 3900)
- BDKwkNtBSP.exe (PID: 2820)
- RegAsm.exe (PID: 304)
- Vhzuag1W7Z.exe (PID: 6456)
- bundle.exe (PID: 644)
- penis.exe (PID: 7984)
- RegAsm.exe (PID: 6456)
- RegAsm.exe (PID: 3208)
- icvideoconverter_32.exe (PID: 5760)
- RegAsm.exe (PID: 6316)
- RegAsm.exe (PID: 788)
Reads the BIOS version
- cd5563c5b7.exe (PID: 5692)
- axplong.exe (PID: 6708)
- Cerker.exe (PID: 7612)
- kitty.exe (PID: 7436)
- Cerker.exe (PID: 6376)
- axplong.exe (PID: 7248)
- Cerker.exe (PID: 7352)
- axplong.exe (PID: 6420)
- axplong.exe (PID: 8116)
- Cerker.exe (PID: 7020)
- axplong.exe (PID: 8176)
- Cerker.exe (PID: 5532)
- Cerker.exe (PID: 6616)
- axplong.exe (PID: 2720)
Process drops legitimate windows executable
- off.tmp (PID: 2024)
- explorer.exe (PID: 3672)
- fikbbm0902845.exe (PID: 1608)
- stealc_default2.exe (PID: 7172)
- Intake.pif (PID: 7824)
- RegAsm.exe (PID: 5184)
The process drops C-runtime libraries
- off.tmp (PID: 2024)
- stealc_default2.exe (PID: 7172)
Starts a Microsoft application from unusual location
- fikbbm0902845.exe (PID: 1608)
- RegAsm.exe (PID: 2892)
- RegAsm.exe (PID: 6456)
- RegAsm.exe (PID: 5064)
- RegAsm.exe (PID: 7368)
- RegAsm.exe (PID: 3208)
- RegAsm.exe (PID: 6316)
- RegAsm.exe (PID: 788)
Reads the Windows owner or organization settings
- off.tmp (PID: 2024)
- freedom.exe (PID: 7556)
Executing commands from a ".bat" file
- fikbbm0902845.exe (PID: 1608)
- BowExpert.exe (PID: 7196)
The executable file from the user directory is run by the CMD process
- fkckqoi.exe (PID: 2700)
- Intake.pif (PID: 7824)
Starts CMD.EXE for commands execution
- fikbbm0902845.exe (PID: 1608)
- BowExpert.exe (PID: 7196)
- cmd.exe (PID: 7276)
- winrar-info.exe (PID: 7444)
Windows Defender mutex has been found
- stealc_default2.exe (PID: 7172)
- svchost015.exe (PID: 6824)
Get information on the list of running processes
- cmd.exe (PID: 7276)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7276)
Searches for installed software
- stealc_default2.exe (PID: 7172)
- vlst.exe (PID: 8132)
- Sеtup.exe (PID: 7420)
- channel33.exe (PID: 5376)
- 3546345.exe (PID: 4344)
- Uninstall.exe (PID: 7336)
- RegAsm.exe (PID: 5732)
Application launched itself
- cmd.exe (PID: 7276)
- freedom.exe (PID: 7556)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 7276)
- Intake.pif (PID: 7824)
Starts application with an unusual extension
- cmd.exe (PID: 7276)
- wscript.exe (PID: 1184)
Checks Windows Trust Settings
- Cerker.exe (PID: 7612)
- RegAsm.exe (PID: 5184)
- RegAsm.exe (PID: 5732)
The process drops Mozilla's DLL files
- stealc_default2.exe (PID: 7172)
The process executes via Task Scheduler
- Hkbsse.exe (PID: 2868)
- axplong.exe (PID: 7248)
- Cerker.exe (PID: 6376)
- Cerker.exe (PID: 7352)
- axplong.exe (PID: 6420)
- service123.exe (PID: 5532)
- Hkbsse.exe (PID: 6276)
- Hkbsse.exe (PID: 2400)
- axplong.exe (PID: 8116)
- Cerker.exe (PID: 7020)
- service123.exe (PID: 6328)
- axplong.exe (PID: 8176)
- Hkbsse.exe (PID: 8000)
- service123.exe (PID: 188)
- Cerker.exe (PID: 5532)
- axplong.exe (PID: 2720)
- Cerker.exe (PID: 6616)
- wscript.exe (PID: 1184)
- service123.exe (PID: 6556)
- Hkbsse.exe (PID: 7296)
Payload loading activity detected
- explorer.exe (PID: 3672)
Hides command output
- cmd.exe (PID: 6768)
Reads Microsoft Outlook installation path
- winrar-x64-701ru.exe (PID: 3256)
Reads Internet Explorer settings
- winrar-x64-701ru.exe (PID: 3256)
The process executes VB scripts
- cmd.exe (PID: 6768)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 6748)
Runs shell command (SCRIPT)
- cscript.exe (PID: 6748)
- wscript.exe (PID: 1184)
Checks for external IP
- RegAsm.exe (PID: 5184)
- svchost.exe (PID: 2256)
The process creates files with name similar to system file names
- Intake.pif (PID: 7824)
Drops 7-zip archiver for unpacking
- winrar-x64-701ru.exe (PID: 3256)
There is functionality for communication over UDP network (YARA)
- freedom.exe (PID: 7556)
Found regular expressions for crypto-addresses (YARA)
- service123.exe (PID: 7268)
Creates/Modifies COM task schedule object
- Uninstall.exe (PID: 7336)
Creates a software uninstall entry
- Uninstall.exe (PID: 7336)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- RegAsm.exe (PID: 5732)
INFO
Checks proxy server information
- acentric[1].exe (PID: 2480)
- explorer.exe (PID: 3672)
- winmsbt.exe (PID: 3908)
- Hkbsse.exe (PID: 6720)
- axplong.exe (PID: 6708)
- stealc_default2.exe (PID: 7172)
- Cerker.exe (PID: 7612)
- freedom.exe (PID: 7556)
- acentric.exe (PID: 8000)
- svchost015.exe (PID: 6824)
- winrar-x64-701ru.exe (PID: 3256)
- acentric.exe (PID: 7716)
- RegAsm.exe (PID: 5184)
- slui.exe (PID: 7296)
- icvideoconverter_32.exe (PID: 5760)
- RegAsm.exe (PID: 5732)
Reads the software policy settings
- acentric[1].exe (PID: 2480)
- winmsbt.exe (PID: 3908)
- Gj7FUXV4FC.exe (PID: 3900)
- Vhzuag1W7Z.exe (PID: 6456)
- Cerker.exe (PID: 7612)
- explorer.exe (PID: 3672)
- penis.exe (PID: 7984)
- acentric.exe (PID: 8000)
- winrar-info.exe (PID: 7444)
- RegAsm.exe (PID: 5184)
- acentric.exe (PID: 7716)
- slui.exe (PID: 892)
- slui.exe (PID: 7296)
- RegAsm.exe (PID: 5732)
Disables trace logs
- acentric[1].exe (PID: 2480)
- winmsbt.exe (PID: 3908)
- acentric.exe (PID: 8000)
- acentric.exe (PID: 7716)
Reads the computer name
- acentric[1].exe (PID: 2480)
- contorax.exe (PID: 3716)
- winmsbt.exe (PID: 3908)
- crypteda.exe (PID: 2724)
- mSOoiAKqbK.exe (PID: 6812)
- Gj7FUXV4FC.exe (PID: 3900)
- exbuild.exe (PID: 6372)
- Hkbsse.exe (PID: 6720)
- cd5563c5b7.exe (PID: 5692)
- off.tmp (PID: 2024)
- axplong.exe (PID: 6708)
- 3546345.exe (PID: 4344)
- icvideoconverter_32.exe (PID: 5760)
- RegAsm.exe (PID: 304)
- gold.exe (PID: 6864)
- crypteda.exe (PID: 4436)
- Vhzuag1W7Z.exe (PID: 6456)
- BDKwkNtBSP.exe (PID: 2820)
- fkckqoi.exe (PID: 2700)
- stealc_default2.exe (PID: 7172)
- BowExpert.exe (PID: 7196)
- kitty.exe (PID: 7436)
- Cerker.exe (PID: 7612)
- Intake.pif (PID: 7824)
- acentric.exe (PID: 8000)
- vlst.exe (PID: 8132)
- freedom.exe (PID: 7556)
- bundle.exe (PID: 644)
- penis.exe (PID: 7984)
- Sеtup.exe (PID: 7420)
- acentric.exe (PID: 7716)
- needmoney.exe (PID: 7908)
- svchost015.exe (PID: 6824)
- appgate15.exe (PID: 7196)
- Cerker.exe (PID: 6376)
- RegAsm.exe (PID: 5184)
- WinRarInstall.exe (PID: 6428)
- curl.exe (PID: 4008)
- winrar-info.exe (PID: 7444)
- winrar-x64-701ru.exe (PID: 3256)
- channel33.exe (PID: 5376)
- RegAsm.exe (PID: 6456)
- Cerker.exe (PID: 7352)
- Uninstall.exe (PID: 7336)
- RegAsm.exe (PID: 3208)
- __AhMv4C0ol6xVkMvz5WwCN_.exe (PID: 7508)
- Cerker.exe (PID: 7020)
- RegAsm.exe (PID: 5732)
- RegAsm.exe (PID: 6316)
- Cerker.exe (PID: 5532)
- RegAsm.exe (PID: 788)
- Cerker.exe (PID: 6616)
- freedom.exe (PID: 7956)
Checks supported languages
- acentric[1].exe (PID: 2480)
- contorax.exe (PID: 3716)
- winmsbt.exe (PID: 3908)
- crypteda.exe (PID: 2724)
- mSOoiAKqbK.exe (PID: 6812)
- Gj7FUXV4FC.exe (PID: 3900)
- exbuild.exe (PID: 6372)
- Hkbsse.exe (PID: 6720)
- 3546345.exe (PID: 4344)
- cd5563c5b7.exe (PID: 5692)
- off.exe (PID: 6612)
- axplong.exe (PID: 6708)
- off.tmp (PID: 2024)
- icvideoconverter_32.exe (PID: 5760)
- gold.exe (PID: 6864)
- RegAsm.exe (PID: 304)
- crypteda.exe (PID: 4436)
- Vhzuag1W7Z.exe (PID: 6456)
- BDKwkNtBSP.exe (PID: 2820)
- fikbbm0902845.exe (PID: 1608)
- Nework.exe (PID: 4436)
- fkckqoi.exe (PID: 2700)
- stealc_default2.exe (PID: 7172)
- BowExpert.exe (PID: 7196)
- kitty.exe (PID: 7436)
- Cerker.exe (PID: 7612)
- acentric.exe (PID: 8000)
- vlst.exe (PID: 8132)
- Sеtup.exe (PID: 7420)
- freedom.exe (PID: 7556)
- bundle.exe (PID: 644)
- penis.exe (PID: 7984)
- needmoney.exe (PID: 7908)
- acentric.exe (PID: 7716)
- Hkbsse.exe (PID: 2868)
- axplong.exe (PID: 7248)
- svchost015.exe (PID: 6824)
- appgate15.exe (PID: 7196)
- Cerker.exe (PID: 6376)
- RegAsm.exe (PID: 5184)
- Intake.pif (PID: 7824)
- winrar-info.exe (PID: 7444)
- WinRarInstall.exe (PID: 6428)
- winrar-x64-701ru.exe (PID: 3256)
- curl.exe (PID: 4008)
- channel33.exe (PID: 5376)
- RegAsm.exe (PID: 6456)
- service123.exe (PID: 7268)
- Hkbsse.exe (PID: 6276)
- Cerker.exe (PID: 7352)
- axplong.exe (PID: 6420)
- service123.exe (PID: 5532)
- Uninstall.exe (PID: 7336)
- RegAsm.exe (PID: 3208)
- __AhMv4C0ol6xVkMvz5WwCN_.exe (PID: 7508)
- RegAsm.exe (PID: 5732)
- Hkbsse.exe (PID: 2400)
- axplong.exe (PID: 8116)
- Cerker.exe (PID: 7020)
- service123.exe (PID: 6328)
- RegAsm.exe (PID: 6316)
- axplong.exe (PID: 8176)
- Hkbsse.exe (PID: 8000)
- Cerker.exe (PID: 5532)
- service123.exe (PID: 188)
- RegAsm.exe (PID: 788)
- Hkbsse.exe (PID: 7296)
- Cerker.exe (PID: 6616)
- service123.exe (PID: 6556)
- axplong.exe (PID: 2720)
- TurtleHarbor.pif (PID: 5644)
- freedom.exe (PID: 7956)
Reads security settings of Internet Explorer
- explorer.exe (PID: 3672)
- cscript.exe (PID: 6748)
- Taskmgr.exe (PID: 7772)
The process uses the downloaded file
- contorax.exe (PID: 3716)
- explorer.exe (PID: 3672)
- crypteda.exe (PID: 2724)
- exbuild.exe (PID: 6372)
- Hkbsse.exe (PID: 6720)
- cd5563c5b7.exe (PID: 5692)
- axplong.exe (PID: 6708)
- crypteda.exe (PID: 4436)
- kitty.exe (PID: 7436)
- BowExpert.exe (PID: 7196)
- WinRarInstall.exe (PID: 6428)
- Sеtup.exe (PID: 7420)
- winrar-x64-701ru.exe (PID: 3256)
- freedom.exe (PID: 7556)
Creates files or folders in the user directory
- explorer.exe (PID: 3672)
- mSOoiAKqbK.exe (PID: 6812)
- crypteda.exe (PID: 2724)
- Hkbsse.exe (PID: 6720)
- off.tmp (PID: 2024)
- axplong.exe (PID: 6708)
- RegAsm.exe (PID: 304)
- crypteda.exe (PID: 4436)
- BDKwkNtBSP.exe (PID: 2820)
- stealc_default2.exe (PID: 7172)
- Intake.pif (PID: 7824)
- Cerker.exe (PID: 7612)
- bundle.exe (PID: 644)
- svchost015.exe (PID: 6824)
- RegAsm.exe (PID: 5184)
- Uninstall.exe (PID: 7336)
- RegAsm.exe (PID: 5732)
Reads the machine GUID from the registry
- acentric[1].exe (PID: 2480)
- contorax.exe (PID: 3716)
- winmsbt.exe (PID: 3908)
- mSOoiAKqbK.exe (PID: 6812)
- Gj7FUXV4FC.exe (PID: 3900)
- RegAsm.exe (PID: 304)
- Vhzuag1W7Z.exe (PID: 6456)
- BDKwkNtBSP.exe (PID: 2820)
- fkckqoi.exe (PID: 2700)
- acentric.exe (PID: 8000)
- Cerker.exe (PID: 7612)
- vlst.exe (PID: 8132)
- freedom.exe (PID: 7556)
- penis.exe (PID: 7984)
- bundle.exe (PID: 644)
- acentric.exe (PID: 7716)
- appgate15.exe (PID: 7196)
- RegAsm.exe (PID: 6456)
- service123.exe (PID: 7268)
- service123.exe (PID: 5532)
- RegAsm.exe (PID: 5184)
- RegAsm.exe (PID: 3208)
- service123.exe (PID: 6328)
- RegAsm.exe (PID: 6316)
- RegAsm.exe (PID: 5732)
- service123.exe (PID: 188)
- RegAsm.exe (PID: 788)
- service123.exe (PID: 6556)
- freedom.exe (PID: 7956)
Creates files in the program directory
- contorax.exe (PID: 3716)
- icvideoconverter_32.exe (PID: 5760)
- stealc_default2.exe (PID: 7172)
- winrar-x64-701ru.exe (PID: 3256)
- Uninstall.exe (PID: 7336)
- RegAsm.exe (PID: 5732)
Process checks computer location settings
- contorax.exe (PID: 3716)
- crypteda.exe (PID: 2724)
- exbuild.exe (PID: 6372)
- Hkbsse.exe (PID: 6720)
- cd5563c5b7.exe (PID: 5692)
- axplong.exe (PID: 6708)
- crypteda.exe (PID: 4436)
- BowExpert.exe (PID: 7196)
- kitty.exe (PID: 7436)
- WinRarInstall.exe (PID: 6428)
- Sеtup.exe (PID: 7420)
- winrar-x64-701ru.exe (PID: 3256)
- RegAsm.exe (PID: 5184)
- freedom.exe (PID: 7556)
Reads Environment values
- winmsbt.exe (PID: 3908)
- stealc_default2.exe (PID: 7172)
- freedom.exe (PID: 7556)
- RegAsm.exe (PID: 5732)
Create files in a temporary directory
- explorer.exe (PID: 3672)
- exbuild.exe (PID: 6372)
- cd5563c5b7.exe (PID: 5692)
- off.exe (PID: 6612)
- Hkbsse.exe (PID: 6720)
- off.tmp (PID: 2024)
- axplong.exe (PID: 6708)
- fikbbm0902845.exe (PID: 1608)
- BowExpert.exe (PID: 7196)
- kitty.exe (PID: 7436)
- needmoney.exe (PID: 7908)
- WinRarInstall.exe (PID: 6428)
- Sеtup.exe (PID: 7420)
- curl.exe (PID: 4008)
- Intake.pif (PID: 7824)
- RegAsm.exe (PID: 5732)
Sends debugging messages
- cd5563c5b7.exe (PID: 5692)
- axplong.exe (PID: 6708)
- axplong.exe (PID: 7248)
- axplong.exe (PID: 6420)
- axplong.exe (PID: 8116)
- axplong.exe (PID: 8176)
- axplong.exe (PID: 2720)
Creates a software uninstall entry
- off.tmp (PID: 2024)
Reads CPU info
- fkckqoi.exe (PID: 2700)
- stealc_default2.exe (PID: 7172)
- freedom.exe (PID: 7556)
- Sеtup.exe (PID: 7420)
- channel33.exe (PID: 5376)
- 3546345.exe (PID: 4344)
- RegAsm.exe (PID: 5732)
Reads product name
- stealc_default2.exe (PID: 7172)
- freedom.exe (PID: 7556)
- RegAsm.exe (PID: 5732)
Reads mouse settings
- Intake.pif (PID: 7824)
- TurtleHarbor.pif (PID: 5644)
Manual execution by a user
- cmd.exe (PID: 7860)
- cmd.exe (PID: 7912)
- RegAsm.exe (PID: 2892)
- RegAsm.exe (PID: 6456)
- RegAsm.exe (PID: 7368)
- RegAsm.exe (PID: 3208)
- RegAsm.exe (PID: 5064)
- RegAsm.exe (PID: 6316)
- Taskmgr.exe (PID: 7888)
- Taskmgr.exe (PID: 7772)
- RegAsm.exe (PID: 788)
Reads Windows Product ID
- freedom.exe (PID: 7556)
Themida protector has been detected
- axplong.exe (PID: 6708)
.NET Reactor protector has been detected
- RegAsm.exe (PID: 3208)
- RegAsm.exe (PID: 6316)
- RegAsm.exe (PID: 788)
Attempting to use instant messaging service
- RegAsm.exe (PID: 5732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(2480) acentric[1].exe
Decrypted-URLs (1)https://conditionprovice.pro/tmpdir/9872345234.cab
(PID) Process(3908) winmsbt.exe
Decrypted-URLs (1)https://pastebin.com/raw/fiLr6dSt
Amadey
(PID) Process(3672) explorer.exe
C2185.215.113.19
URLhttp://185.215.113.19/CoreOPT/index.php
Version4.41
Options
Drop directory417fd29867
Drop nameednfoki.exe
Strings (119)ar:
------
4.41
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
exe
Kaspersky Lab
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
random
lv:
id:
&unit=
rundll32
bi:
?scr=1
\
"
=
" && timeout 1 && del
https://
Panda Security
/Plugins/
0123456789
st=s
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
Sophos
cmd /C RMDIR /s/q
WinDefender
clip.dll
Doctor Web
SOFTWARE\Microsoft\Windows NT\CurrentVersion
%USERPROFILE%
ps1
dm:
kernel32.dll
rundll32.exe
SYSTEM\ControlSet001\Services\BasicDisplay\Video
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
shutdown -s -t 0
DefaultSettings.YResolution
sd:
\App
<c>
un:
av:
&& Exit"
:::
&&
2022
ComputerName
e1
cmd
Content-Type: application/x-www-form-urlencoded
Powershell.exe
GET
/CoreOPT/index.php
vs:
Norton
d1
AVG
"taskkill /f /im "
cred.dll
--
2019
%-lu
360TotalSecurity
" && ren
185.215.113.19
Content-Disposition: form-data; name="data"; filename="
ednfoki.exe
ESET
og:
\0000
GetNativeSystemInfo
DefaultSettings.XResolution
VideoID
shell32.dll
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
msi
/k
Startup
e0
/quiet
+++
Comodo
#
rb
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
417fd29867
S-%lu-
-%lu
.jpg
os:
zip
Programs
ProgramData\
Main
dll
<d>
"
Content-Type: application/octet-stream
cred.dll|clip.dll|
POST
-executionpolicy remotesigned -File "
|
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
r=
Bitdefender
wb
CurrentBuild
Content-Type: multipart/form-data; boundary=----
Rem
Avira
ProductName
2016
------
e2
AVAST Software
pc:
http://
(PID) Process(6720) Hkbsse.exe
C2185.215.113.26
URLhttp://185.215.113.26/Dem7kTu/index.php
Version4.41
Options
Drop directory054fdc5f70
Drop nameHkbsse.exe
Strings (119)ar:
------
4.41
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
exe
Kaspersky Lab
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
054fdc5f70
random
lv:
id:
&unit=
rundll32
bi:
?scr=1
\
"
=
" && timeout 1 && del
185.215.113.26
https://
Panda Security
/Plugins/
0123456789
st=s
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
Sophos
cmd /C RMDIR /s/q
WinDefender
clip.dll
Doctor Web
SOFTWARE\Microsoft\Windows NT\CurrentVersion
%USERPROFILE%
ps1
dm:
kernel32.dll
rundll32.exe
SYSTEM\ControlSet001\Services\BasicDisplay\Video
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
shutdown -s -t 0
DefaultSettings.YResolution
sd:
\App
<c>
un:
av:
&& Exit"
:::
&&
2022
ComputerName
e1
cmd
Content-Type: application/x-www-form-urlencoded
Powershell.exe
GET
Hkbsse.exe
vs:
Norton
d1
AVG
"taskkill /f /im "
cred.dll
--
2019
%-lu
360TotalSecurity
" && ren
Content-Disposition: form-data; name="data"; filename="
ESET
og:
\0000
GetNativeSystemInfo
DefaultSettings.XResolution
VideoID
shell32.dll
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
msi
/k
Startup
e0
/quiet
+++
Comodo
#
rb
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
S-%lu-
-%lu
.jpg
os:
zip
Programs
ProgramData\
Main
dll
<d>
"
Content-Type: application/octet-stream
cred.dll|clip.dll|
POST
-executionpolicy remotesigned -File "
|
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
r=
/Dem7kTu/index.php
Bitdefender
wb
CurrentBuild
Content-Type: multipart/form-data; boundary=----
Rem
Avira
ProductName
2016
------
e2
AVAST Software
pc:
http://
(PID) Process(6708) axplong.exe
C2185.215.113.16
URLhttp://185.215.113.16/Jo89Ku7d/index.php
Version4.41
Options
Drop directory44111dbc49
Drop nameaxplong.exe
Strings (119)ar:
------
/Jo89Ku7d/index.php
4.41
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
exe
Kaspersky Lab
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
random
lv:
id:
&unit=
rundll32
bi:
?scr=1
\
"
=
" && timeout 1 && del
https://
Panda Security
/Plugins/
44111dbc49
0123456789
st=s
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
Sophos
cmd /C RMDIR /s/q
WinDefender
clip.dll
Doctor Web
SOFTWARE\Microsoft\Windows NT\CurrentVersion
%USERPROFILE%
ps1
dm:
kernel32.dll
rundll32.exe
SYSTEM\ControlSet001\Services\BasicDisplay\Video
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
shutdown -s -t 0
DefaultSettings.YResolution
sd:
\App
<c>
un:
av:
&& Exit"
:::
&&
2022
ComputerName
e1
cmd
Content-Type: application/x-www-form-urlencoded
Powershell.exe
GET
vs:
Norton
d1
AVG
"taskkill /f /im "
cred.dll
--
2019
%-lu
360TotalSecurity
" && ren
Content-Disposition: form-data; name="data"; filename="
ESET
og:
\0000
GetNativeSystemInfo
DefaultSettings.XResolution
VideoID
shell32.dll
185.215.113.16
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
msi
/k
Startup
e0
/quiet
+++
Comodo
#
rb
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
S-%lu-
-%lu
.jpg
os:
zip
Programs
ProgramData\
Main
dll
<d>
"
Content-Type: application/octet-stream
cred.dll|clip.dll|
POST
-executionpolicy remotesigned -File "
|
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
r=
Bitdefender
wb
CurrentBuild
Content-Type: multipart/form-data; boundary=----
axplong.exe
Rem
Avira
ProductName
2016
------
e2
AVAST Software
pc:
http://
CryptBot
(PID) Process(4344) 3546345.exe
C2 (1)thizx13vt.top
Strings (364)CreateDCA
GetTempPathW
InternetOpenA
GetCurrentProcess
sprintf
IsWow64Process2
InternetOpenUrlW
WinHttpConnect
realloc
MoveFileA
CreateDCW
WinHttpReceiveResponse
WinHttpOpenRequest
/zip.php
GetModuleFileNameExW
GetSystemDirectoryA
GetSystemMetrics
DuplicateHandle
An error occurred while starting the application (0xc000007b). To exit the application, click OK.
ScreenShot.jpeg
VirtualFreeEx
ExpandEnvironmentStringsW
GetDriveTypeW
msvcrt.dll
WideCharToMultiByte
_swprintf
socket
accept
swprintf_s
swprintf
bind
GetCurrentThread
RegQueryValueExW
kernel32.dll
StrStrIA
ExtractFilesW
Process32NextW
MoveFileExW
RegQueryInfoKeyA
_snwprintf
analforeverlovyu.top
shlwapi.dll
\ServiceData\Clip.au3
WinHttpReadData
GetUserNameW
InternetReadFileExW
RmGetList
PathIsDirectoryW
WinHttpReadDataEx
WinHttpAddRequestHeaders
ExitProcess
ShellExecuteA
FCIDestroy
Apps
GetConsoleMode
CreateDirectoryA
wnsprintfA
thizx13vt.top
Sleep
shell32.dll
FindNextFileA
InternetCloseHandle
RegQueryValueExA
RemoveDirectoryW
URLDownloadToFileA
winsqlite3.dll
CreateFileW
GetLastError
BitBlt
ReadConsoleA
InternetOpenUrlA
LocalFree
wininet.dll
VirtualAlloc
HttpQueryInfoA
GetDiskFreeSpaceExW
WinHttpSendRequest
LoadLibraryW
GetFileAttributesA
CloseHandle
GetLogicalDriveStringsW
WaitForSingleObject
POST
\Zxfjskbhxe
LoadLibraryA
SHUnicodeToAnsi
IStream_Read
GetDriveTypeA
CreateFileMappingW
GetCurrentDirectoryA
GetTickCount
GdipGetImageEncoders
crypt32.dll
LoadLibraryExW
GdipSaveImageToFile
GetLocalTime
QueryPerformanceCounter
GetEnvironmentVariableW
CopyFileW
CreateFileMappingA
RegOpenKeyExA
HeapCreate
GetSystemDirectoryW
CopyFileExW
System Error
ole32.dll
CreateMutexA
SetFilePointerEx
ExitThread
GetSystemInfo
GetUserNameA
Temp
"encrypted_key":"
GetModuleHandleExW
InternetConnectW
GdiplusShutdown
GetComputerNameW
UserProfile
DPAPI
FindFirstFileNameA
ReleaseDC
CreateRemoteThread
RegOpenKeyExW
RegEnumKeyExA
vswprintf
CoUninitialize
GetFileInformationByHandle
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
send
SHAnsiToUnicode
GlobalMemoryStatusEx
WinExec
DISPLAY
SleepEx
inet_addr
PathFileExistsA
URLDownloadToFileW
LocalAlloc
Content-Length: %lu
PathFileExistsW
StrStrIW
sprintf_s
EnumDisplaySettingsA
CreateThread
SetFilePointer
FileTimeToSystemTime
GetTempFileNameW
GetSystemWow64DirectoryA
GetKeyboardLayoutList
CreateProcessW
GET
HeapAlloc
ws2_32.dll
GetProcessHeap
UserID.txt
GetDeviceCaps
GetModuleHandleExA
malloc
gdiplus.dll
SHGetFolderPathA
printf
GetLocaleInfoW
listen
AppData
WSACleanup
SelectObject
GdiplusStartup
Others
SetErrorMode
abs
GetProcAddress
NULL
SaveImageToStream
ReadFile
GetFileAttributesW
InternetOpenW
InternetConnectA
WinHttpOpen
gdi32.dll
GetDiskFreeSpaceExA
HttpOpenRequestW
CreateStreamOnHGlobal
RegEnumKeyExW
HttpOpenRequestA
Process32FirstW
CreateCompatibleBitmap
GetModuleHandleA
WriteFile
GetEnvironmentVariableA
InternetReadFile
InternetReadFileExA
FindFirstFileExW
winhttp.dll
GetModuleFileNameW
HeapReAlloc
FCIFlushFolder
RmEndSession
rstrtmgr.dll
$CREEN.JPEG
Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; .NET4.0C; .NET4.0E; rv:11.0) like Gecko
WriteConsoleA
GdipSaveImageToStream
Debug.txt
recvfrom
/c schtasks /create /tn \Service\Data /tr """"%wS""" """%wS"""" /st 00:01 /du 9800:59 /sc once /ri 1 /f
RegQueryInfoKeyW
DeleteObject
Desktop
WinHttpQueryOption
MoveFileW
WinHttpCrackUrl
clock
RmRegisterResources
InternetCrackUrlW
vsnprintf
_wtoi
\ServiceData
GdipGetImageEncodersSize
urlmon.dll
ShellExecuteW
_vscwprintf
IsWow64Process
GdipLoadImageFromFile
ExpandEnvironmentStringsA
CreateDirectoryW
GetModuleFileNameExA
FreeLibrary
OpenThread
MoveFileExA
user32.dll
HeapSize
FCIAddFile
ntdll.dll
log.txt
FindNextFileNameA
Browsers
\ServiceData\Clip.exe
free
IStream_Reset
LocalAppData
GetCurrentDirectoryW
wsprintfW
GetModuleHandleW
curl/8.0.1
closesocket
wsprintfA
SHGetFolderPathW
HttpQueryInfoW
advapi32.dll
WriteConsoleW
GetDIBits
WinHttpQueryHeaders
RtlGetVersion
HTTP
EnumDisplaySettingsW
Extract
WSAGetLastError
GetTickCount64
/gate.php
WSAStartup
FCICreate
ReadConsoleW
_vscprintf
End.txt
HeapFree
RemoveDirectoryA
WinHttpCloseHandle
DeleteDC
Process32NextA
GetExitCodeThread
CreateMutexW
MultiByteToWideChar
VirtualProtectEx
GetVolumeInformationA
GetProcessId
GetTimeZoneInformation
calloc
GetObjectW
VirtualAllocEx
GetFileSize
SystemTimeToFileTime
IsBadReadPtr
FileTimeToDosDateTime
HttpSendRequestW
GetFileSizeEx
URLOpenBlockingStreamA
wprintf
GetFileAttributesExA
CreateCompatibleDC
GetLocaleInfoA
GetTempPathA
GetTempFileNameA
GetUserDefaultLocaleName
IStream_Size
atoi
DeleteFileW
SHCreateMemStream
LoadLibraryExA
GetThreadId
CopyFileA
DeleteFileA
TerminateProcess
CreateRemoteThreadEx
GetObjectA
recv
FCIFlushCabinet
/v1/upload.php
VirtualProtect
CreateProcessA
MessageBoxW
FindFirstFileW
CoInitialize
GetBitmapBits
ReleaseMutex
FindNextFileW
FindFirstFileNameW
_snprintf
GetLogicalDriveStringsA
FindFirstFileExA
CopyFileExA
MessageBoxA
wnsprintfW
cabinet.dll
CreateToolhelp32Snapshot
PathIsDirectoryA
GetCommandLineW
URLOpenBlockingStreamW
Files
WinHttpSetOption
Wallets
advpack.dll
MapViewOfFile
GetNativeSystemInfo
FindFirstFileA
CryptUnprotectData
_snwprintf_s
RmStartSession
LkgwUi
strtod
CreateFileA
RegCloseKey
HTTPS
FindNextFileNameW
GetModuleFileNameA
OpenProcess
User's Computer Information.txt
StretchBlt
GetCommandLineA
HttpSendRequestA
VirtualFree
GetFileAttributesExW
Process32FirstA
UnmapViewOfFile
isspace
GetVolumeInformationW
GdipCreateBitmapFromHBITMAP
/index.php
GetSystemWow64DirectoryW
FindClose
GetComputerNameA
InternetCrackUrlA
ComSpec
htons
ExtractFilesA
DanaBot
(PID) Process(7556) freedom.exe
C2 (2)188.124.59.28:443
45.156.25.118:443
Attributes
(18)187491005CE7E20DA4B7291CE2D30BD7
0123456789ABCDEF0123456789abcdef
77777777777777777777777777777777
424a0d380332858ee55bdebc4af3789f
74e70a2b3ba1cf29d84b9b4bcf3e2e37
00001111222233334444555566667777
20142015201620172018201920202021
20222023202420252026202720282029
20302031203220332034203520362037
20132012201120102009200820072006
20052004200320022001200019991998
19971996199519941993199219911990
19891988198719861985198419831982
19811980197919781977197619751974
19731972197119701969196819671966
19651964196319621961196019591958
19571956195519541953195219511950
51BE137412111014188EEA3770F49F7E
Certificates
(29)-----BEGIN CERTIFICATE-----
MIICvDCCAiUCEEoZ0jiMglkcpV1zXxVd3KMwDQYJKoZIhvcNAQEEBQAwgZ4xHzAd
BgNVBAoTFlZlcmlTaWduIFRydXN0IE5ldHdvcmsxFzAVBgNVBAsTDlZlcmlTaWdu
LCBJbmMuMSwwKgYDVQQLEyNWZXJpU2lnbiBUaW1lIFN0YW1waW5nIFNlcnZpY2Ug
Um9vdDE0MDIGA1UECxMrTk8gTElBQklMSVRZIEFDQ0VQVEVELCAoYyk5NyBWZXJp
U2lnbiw...
-----BEGIN CERTIFICATE-----
MIIEZjCCA06gAwIBAgIQRL4Mi1AAJLQR0zYt4LNfGzANBgkqhkiG9w0BAQUFADCB
lTELMAkGA1UEBhMCVVMxCzAJBgNVBAgTAlVUMRcwFQYDVQQHEw5TYWx0IExha2Ug
Q2l0eTEeMBwGA1UEChMVVGhlIFVTRVJUUlVTVCBOZXR3b3JrMSEwHwYDVQQLExho
dHRwOi8vd3d3LnVzZXJ0cnVzdC5jb20xHTAbBgNVBAMTFFVUTi1VU0VSRmlyc3Qt
T2JqZWN...
-----BEGIN CERTIFICATE-----
MIIDVDCCAjygAwIBAgIDAjRWMA0GCSqGSIb3DQEBBQUAMEIxCzAJBgNVBAYTAlVT
MRYwFAYDVQQKEw1HZW9UcnVzdCBJbmMuMRswGQYDVQQDExJHZW9UcnVzdCBHbG9i
YWwgQ0EwHhcNMDIwNTIxMDQwMDAwWhcNMjIwNTIxMDQwMDAwWjBCMQswCQYDVQQG
EwJVUzEWMBQGA1UEChMNR2VvVHJ1c3QgSW5jLjEbMBkGA1UEAxMSR2VvVHJ1c3Qg
R2xvYmF...
-----BEGIN CERTIFICATE-----
MIIFujCCA6KgAwIBAgIJALtAHEP1Xk+wMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV
BAYTAkNIMRUwEwYDVQQKEwxTd2lzc1NpZ24gQUcxHzAdBgNVBAMTFlN3aXNzU2ln
biBHb2xkIENBIC0gRzIwHhcNMDYxMDI1MDgzMDM1WhcNMzYxMDI1MDgzMDM1WjBF
MQswCQYDVQQGEwJDSDEVMBMGA1UEChMMU3dpc3NTaWduIEFHMR8wHQYDVQQDExZT
d2lzc1N...
-----BEGIN CERTIFICATE-----
MIIDdzCCAl+gAwIBAgIEAgAAuTANBgkqhkiG9w0BAQUFADBaMQswCQYDVQQGEwJJ
RTESMBAGA1UEChMJQmFsdGltb3JlMRMwEQYDVQQLEwpDeWJlclRydXN0MSIwIAYD
VQQDExlCYWx0aW1vcmUgQ3liZXJUcnVzdCBSb290MB4XDTAwMDUxMjE4NDYwMFoX
DTI1MDUxMjIzNTkwMFowWjELMAkGA1UEBhMCSUUxEjAQBgNVBAoTCUJhbHRpbW9y
ZTETMBE...
-----BEGIN CERTIFICATE-----
MIIDIDCCAomgAwIBAgIENd70zzANBgkqhkiG9w0BAQUFADBOMQswCQYDVQQGEwJV
UzEQMA4GA1UEChMHRXF1aWZheDEtMCsGA1UECxMkRXF1aWZheCBTZWN1cmUgQ2Vy
dGlmaWNhdGUgQXV0aG9yaXR5MB4XDTk4MDgyMjE2NDE1MVoXDTE4MDgyMjE2NDE1
MVowTjELMAkGA1UEBhMCVVMxEDAOBgNVBAoTB0VxdWlmYXgxLTArBgNVBAsTJEVx
dWlmYXg...
-----BEGIN CERTIFICATE-----
MIIFtzCCA5+gAwIBAgICBQkwDQYJKoZIhvcNAQEFBQAwRTELMAkGA1UEBhMCQk0x
GTAXBgNVBAoTEFF1b1ZhZGlzIExpbWl0ZWQxGzAZBgNVBAMTElF1b1ZhZGlzIFJv
b3QgQ0EgMjAeFw0wNjExMjQxODI3MDBaFw0zMTExMjQxODIzMzNaMEUxCzAJBgNV
BAYTAkJNMRkwFwYDVQQKExBRdW9WYWRpcyBMaW1pdGVkMRswGQYDVQQDExJRdW9W
YWRpcyB...
-----BEGIN CERTIFICATE-----
MIID3TCCAsWgAwIBAgIBADANBgkqhkiG9w0BAQsFADCBjzELMAkGA1UEBhMCVVMx
EDAOBgNVBAgTB0FyaXpvbmExEzARBgNVBAcTClNjb3R0c2RhbGUxJTAjBgNVBAoT
HFN0YXJmaWVsZCBUZWNobm9sb2dpZXMsIEluYy4xMjAwBgNVBAMTKVN0YXJmaWVs
ZCBSb290IENlcnRpZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTA5MDkwMTAwMDAw
MFoXDTM...
-----BEGIN CERTIFICATE-----
MIIEkTCCA3mgAwIBAgIERWtQVDANBgkqhkiG9w0BAQUFADCBsDELMAkGA1UEBhMC
VVMxFjAUBgNVBAoTDUVudHJ1c3QsIEluYy4xOTA3BgNVBAsTMHd3dy5lbnRydXN0
Lm5ldC9DUFMgaXMgaW5jb3Jwb3JhdGVkIGJ5IHJlZmVyZW5jZTEfMB0GA1UECxMW
KGMpIDIwMDYgRW50cnVzdCwgSW5jLjEtMCsGA1UEAxMkRW50cnVzdCBSb290IENl
cnRpZml...
-----BEGIN CERTIFICATE-----
MIIDdTCCAl2gAwIBAgILBAAAAAABFUtaw5QwDQYJKoZIhvcNAQEFBQAwVzELMAkG
A1UEBhMCQkUxGTAXBgNVBAoTEEdsb2JhbFNpZ24gbnYtc2ExEDAOBgNVBAsTB1Jv
b3QgQ0ExGzAZBgNVBAMTEkdsb2JhbFNpZ24gUm9vdCBDQTAeFw05ODA5MDExMjAw
MDBaFw0yODAxMjgxMjAwMDBaMFcxCzAJBgNVBAYTAkJFMRkwFwYDVQQKExBHbG9i
YWxTaWd...
-----BEGIN CERTIFICATE-----
MIIF2DCCA8CgAwIBAgIQTKr5yttjb+Af907YWwOGnTANBgkqhkiG9w0BAQwFADCB
hTELMAkGA1UEBhMCR0IxGzAZBgNVBAgTEkdyZWF0ZXIgTWFuY2hlc3RlcjEQMA4G
A1UEBxMHU2FsZm9yZDEaMBgGA1UEChMRQ09NT0RPIENBIExpbWl0ZWQxKzApBgNV
BAMTIkNPTU9ETyBSU0EgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkwHhcNMTAwMTE5
MDAwMDA...
-----BEGIN CERTIFICATE-----
MIIEDzCCAvegAwIBAgIBADANBgkqhkiG9w0BAQUFADBoMQswCQYDVQQGEwJVUzEl
MCMGA1UEChMcU3RhcmZpZWxkIFRlY2hub2xvZ2llcywgSW5jLjEyMDAGA1UECxMp
U3RhcmZpZWxkIENsYXNzIDIgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkwHhcNMDQw
NjI5MTczOTE2WhcNMzQwNjI5MTczOTE2WjBoMQswCQYDVQQGEwJVUzElMCMGA1UE
ChMcU3R...
-----BEGIN CERTIFICATE-----
MIIDrzCCApegAwIBAgIQCDvgVpBCRrGhdWrJWZHHSjANBgkqhkiG9w0BAQUFADBh
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBD
QTAeFw0wNjExMTAwMDAwMDBaFw0zMTExMTAwMDAwMDBaMGExCzAJBgNVBAYTAlVT
MRUwEwY...
-----BEGIN CERTIFICATE-----
MIIEIDCCAwigAwIBAgIQNE7VVyDV7exJ9C/ON9srbTANBgkqhkiG9w0BAQUFADCB
qTELMAkGA1UEBhMCVVMxFTATBgNVBAoTDHRoYXd0ZSwgSW5jLjEoMCYGA1UECxMf
Q2VydGlmaWNhdGlvbiBTZXJ2aWNlcyBEaXZpc2lvbjE4MDYGA1UECxMvKGMpIDIw
MDYgdGhhd3RlLCBJbmMuIC0gRm9yIGF1dGhvcml6ZWQgdXNlIG9ubHkxHzAdBgNV
BAMTFnR...
-----BEGIN CERTIFICATE-----
MIIEPjCCAyagAwIBAgIESlOMKDANBgkqhkiG9w0BAQsFADCBvjELMAkGA1UEBhMC
VVMxFjAUBgNVBAoTDUVudHJ1c3QsIEluYy4xKDAmBgNVBAsTH1NlZSB3d3cuZW50
cnVzdC5uZXQvbGVnYWwtdGVybXMxOTA3BgNVBAsTMChjKSAyMDA5IEVudHJ1c3Qs
IEluYy4gLSBmb3IgYXV0aG9yaXplZCB1c2Ugb25seTEyMDAGA1UEAxMpRW50cnVz
dCBSb29...
-----BEGIN CERTIFICATE-----
MIIDuDCCAqCgAwIBAgIQDPCOXAgWpa1Cf/DrJxhZ0DANBgkqhkiG9w0BAQUFADBI
MQswCQYDVQQGEwJVUzEgMB4GA1UEChMXU2VjdXJlVHJ1c3QgQ29ycG9yYXRpb24x
FzAVBgNVBAMTDlNlY3VyZVRydXN0IENBMB4XDTA2MTEwNzE5MzExOFoXDTI5MTIz
MTE5NDA1NVowSDELMAkGA1UEBhMCVVMxIDAeBgNVBAoTF1NlY3VyZVRydXN0IENv
cnBvcmF...
-----BEGIN CERTIFICATE-----
MIIDnzCCAoegAwIBAgIBJjANBgkqhkiG9w0BAQUFADBxMQswCQYDVQQGEwJERTEc
MBoGA1UEChMTRGV1dHNjaGUgVGVsZWtvbSBBRzEfMB0GA1UECxMWVC1UZWxlU2Vj
IFRydXN0IENlbnRlcjEjMCEGA1UEAxMaRGV1dHNjaGUgVGVsZWtvbSBSb290IENB
IDIwHhcNOTkwNzA5MTIxMTAwWhcNMTkwNzA5MjM1OTAwWjBxMQswCQYDVQQGEwJE
RTEcMBo...
-----BEGIN CERTIFICATE-----
MIICPDCCAaUCEHC65B0Q2Sk0tjjKewPMur8wDQYJKoZIhvcNAQECBQAwXzELMAkG
A1UEBhMCVVMxFzAVBgNVBAoTDlZlcmlTaWduLCBJbmMuMTcwNQYDVQQLEy5DbGFz
cyAzIFB1YmxpYyBQcmltYXJ5IENlcnRpZmljYXRpb24gQXV0aG9yaXR5MB4XDTk2
MDEyOTAwMDAwMFoXDTI4MDgwMTIzNTk1OVowXzELMAkGA1UEBhMCVVMxFzAVBgNV
BAoTDlZ...
-----BEGIN CERTIFICATE-----
MIIDkjCCAnqgAwIBAgIRAIW9S/PY2uNp9pTXX8OlRCMwDQYJKoZIhvcNAQEFBQAw
PTELMAkGA1UEBhMCRlIxETAPBgNVBAoTCENlcnRwbHVzMRswGQYDVQQDExJDbGFz
cyAyIFByaW1hcnkgQ0EwHhcNOTkwNzA3MTcwNTAwWhcNMTkwNzA2MjM1OTU5WjA9
MQswCQYDVQQGEwJGUjERMA8GA1UEChMIQ2VydHBsdXMxGzAZBgNVBAMTEkNsYXNz
IDIgUHJ...
-----BEGIN CERTIFICATE-----
MIIDJzCCApCgAwIBAgIBATANBgkqhkiG9w0BAQQFADCBzjELMAkGA1UEBhMCWkEx
FTATBgNVBAgTDFdlc3Rlcm4gQ2FwZTESMBAGA1UEBxMJQ2FwZSBUb3duMR0wGwYD
VQQKExRUaGF3dGUgQ29uc3VsdGluZyBjYzEoMCYGA1UECxMfQ2VydGlmaWNhdGlv
biBTZXJ2aWNlcyBEaXZpc2lvbjEhMB8GA1UEAxMYVGhhd3RlIFByZW1pdW0gU2Vy
dmVyIEN...
-----BEGIN CERTIFICATE-----
MIIDxTCCAq2gAwIBAgIQAqxcJmoLQJuPC3nyrkYldzANBgkqhkiG9w0BAQUFADBs
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSswKQYDVQQDEyJEaWdpQ2VydCBIaWdoIEFzc3VyYW5j
ZSBFViBSb290IENBMB4XDTA2MTExMDAwMDAwMFoXDTMxMTExMDAwMDAwMFowbDEL
MAkGA1U...
-----BEGIN CERTIFICATE-----
MIIEKjCCAxKgAwIBAgIEOGPe+DANBgkqhkiG9w0BAQUFADCBtDEUMBIGA1UEChML
RW50cnVzdC5uZXQxQDA+BgNVBAsUN3d3dy5lbnRydXN0Lm5ldC9DUFNfMjA0OCBp
bmNvcnAuIGJ5IHJlZi4gKGxpbWl0cyBsaWFiLikxJTAjBgNVBAsTHChjKSAxOTk5
IEVudHJ1c3QubmV0IExpbWl0ZWQxMzAxBgNVBAMTKkVudHJ1c3QubmV0IENlcnRp
ZmljYXR...
-----BEGIN CERTIFICATE-----
MIIE0zCCA7ugAwIBAgIQGNrRniZ96LtKIVjNzGs7SjANBgkqhkiG9w0BAQUFADCB
yjELMAkGA1UEBhMCVVMxFzAVBgNVBAoTDlZlcmlTaWduLCBJbmMuMR8wHQYDVQQL
ExZWZXJpU2lnbiBUcnVzdCBOZXR3b3JrMTowOAYDVQQLEzEoYykgMjAwNiBWZXJp
U2lnbiwgSW5jLiAtIEZvciBhdXRob3JpemVkIHVzZSBvbmx5MUUwQwYDVQQDEzxW
ZXJpU2l...
-----BEGIN CERTIFICATE-----
MIIDxTCCAq2gAwIBAgIBADANBgkqhkiG9w0BAQsFADCBgzELMAkGA1UEBhMCVVMx
EDAOBgNVBAgTB0FyaXpvbmExEzARBgNVBAcTClNjb3R0c2RhbGUxGjAYBgNVBAoT
EUdvRGFkZHkuY29tLCBJbmMuMTEwLwYDVQQDEyhHbyBEYWRkeSBSb290IENlcnRp
ZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTA5MDkwMTAwMDAwMFoXDTM3MTIzMTIz
NTk1OVo...
-----BEGIN CERTIFICATE-----
MIIHyTCCBbGgAwIBAgIBATANBgkqhkiG9w0BAQUFADB9MQswCQYDVQQGEwJJTDEW
MBQGA1UEChMNU3RhcnRDb20gTHRkLjErMCkGA1UECxMiU2VjdXJlIERpZ2l0YWwg
Q2VydGlmaWNhdGUgU2lnbmluZzEpMCcGA1UEAxMgU3RhcnRDb20gQ2VydGlmaWNh
dGlvbiBBdXRob3JpdHkwHhcNMDYwOTE3MTk0NjM2WhcNMzYwOTE3MTk0NjM2WjB9
MQswCQY...
-----BEGIN CERTIFICATE-----
MIIEADCCAuigAwIBAgIBADANBgkqhkiG9w0BAQUFADBjMQswCQYDVQQGEwJVUzEh
MB8GA1UEChMYVGhlIEdvIERhZGR5IEdyb3VwLCBJbmMuMTEwLwYDVQQLEyhHbyBE
YWRkeSBDbGFzcyAyIENlcnRpZmljYXRpb24gQXV0aG9yaXR5MB4XDTA0MDYyOTE3
MDYyMFoXDTM0MDYyOTE3MDYyMFowYzELMAkGA1UEBhMCVVMxITAfBgNVBAoTGFRo
ZSBHbyB...
-----BEGIN CERTIFICATE-----
MIIDtzCCAp+gAwIBAgIQDOfg5RfYRv6P5WD8G/AwOTANBgkqhkiG9w0BAQUFADBl
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSQwIgYDVQQDExtEaWdpQ2VydCBBc3N1cmVkIElEIFJv
b3QgQ0EwHhcNMDYxMTEwMDAwMDAwWhcNMzExMTEwMDAwMDAwWjBlMQswCQYDVQQG
EwJVUzE...
-----BEGIN CERTIFICATE-----
MIIEdDCCA1ygAwIBAgIQRL4Mi1AAJLQR0zYq/mUK/TANBgkqhkiG9w0BAQUFADCB
lzELMAkGA1UEBhMCVVMxCzAJBgNVBAgTAlVUMRcwFQYDVQQHEw5TYWx0IExha2Ug
Q2l0eTEeMBwGA1UEChMVVGhlIFVTRVJUUlVTVCBOZXR3b3JrMSEwHwYDVQQLExho
dHRwOi8vd3d3LnVzZXJ0cnVzdC5jb20xHzAdBgNVBAMTFlVUTi1VU0VSRmlyc3Qt
SGFyZHd...
-----BEGIN CERTIFICATE-----
MIIENjCCAx6gAwIBAgIBATANBgkqhkiG9w0BAQUFADBvMQswCQYDVQQGEwJTRTEU
MBIGA1UEChMLQWRkVHJ1c3QgQUIxJjAkBgNVBAsTHUFkZFRydXN0IEV4dGVybmFs
IFRUUCBOZXR3b3JrMSIwIAYDVQQDExlBZGRUcnVzdCBFeHRlcm5hbCBDQSBSb290
MB4XDTAwMDUzMDEwNDgzOFoXDTIwMDUzMDEwNDgzOFowbzELMAkGA1UEBhMCU0Ux
FDASBgN...
Vidar
(PID) Process(5732) RegAsm.exe
C2https://t.me/edm0d
URLhttps://steamcommunity.com/profiles/76561199768374681
RC40123456789ABCDEF
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:09:07 22:51:21+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 281600 |
| InitializedDataSize: | 182784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x46b76 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Notepad |
| FileVersion: | 1.0.0.0 |
| InternalName: | OpticAbyssmal.exe |
| LegalCopyright: | Copyright © 2017 |
| LegalTrademarks: | - |
| OriginalFileName: | OpticAbyssmal.exe |
| ProductName: | Notepad |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
262
Monitored processes
126
Malicious processes
61
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\AppData\Local\Temp\/service123.exe" | C:\Users\admin\AppData\Local\Temp\service123.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 304 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | gold.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 644 | "C:\Users\admin\AppData\Local\Temp\1000259001\bundle.exe" | C:\Users\admin\AppData\Local\Temp\1000259001\bundle.exe | axplong.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: XHP Exit code: 0 Version: 12.9.1.22 Modules
| |||||||||||||||
| 788 | C:\Users\admin\AppData\Local\Temp\684126\RegAsm.exe | C:\Users\admin\AppData\Local\Temp\684126\RegAsm.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 892 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\WINDOWS\system32\wscript.EXE" //B "C:\Users\admin\AppData\Local\SecureData Technologies\TurtleHarbor.js" | C:\Windows\System32\wscript.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1608 | "C:\Users\admin\AppData\Local\Temp\1000226001\fikbbm0902845.exe" | C:\Users\admin\AppData\Local\Temp\1000226001\fikbbm0902845.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Version: 11.00.22621.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RegAsm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2024 | "C:\Users\admin\AppData\Local\Temp\is-GBJI0.tmp\off.tmp" /SL5="$F01F6,2510033,56832,C:\Users\admin\AppData\Local\Temp\1000038001\off.exe" | C:\Users\admin\AppData\Local\Temp\is-GBJI0.tmp\off.tmp | off.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Version: 51.52.0.0 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
73 905
Read events
73 631
Write events
245
Delete events
29
Modification events
| (PID) Process: | (2480) acentric[1].exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\acentric[1]_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2480) acentric[1].exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\acentric[1]_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2480) acentric[1].exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\acentric[1]_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2480) acentric[1].exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\acentric[1]_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2480) acentric[1].exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\acentric[1]_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2480) acentric[1].exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\acentric[1]_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2480) acentric[1].exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\acentric[1]_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2480) acentric[1].exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\acentric[1]_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2480) acentric[1].exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\acentric[1]_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2480) acentric[1].exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\acentric[1]_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
145
Suspicious files
80
Text files
131
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2480 | acentric[1].exe | C:\Users\admin\Pictures\Opportunistic Telegraph\acentric[1].exe | executable | |
MD5:37D198AD751D31A71ACC9CB28ED0C64E | SHA256:1ED4A8B4C74AAB435EA5CD459D5AC961E5A8CA28924801BD84D336135F30EFDE | |||
| 3672 | explorer.exe | C:\Users\admin\AppData\Local\Temp\693682860607 | image | |
MD5:8E03CB3642D25C1B93DAA4364766CF42 | SHA256:DD9CA7B5340303565333613D5046470D4222BC76F0FC96BE6CBE24204E08EEAC | |||
| 3716 | contorax.exe | C:\ProgramData\Microsoft Subsystem Framework\winmsbt.exe | executable | |
MD5:771B8E84BA4F0215298D9DADFE5A10BF | SHA256:3F074FB6A883663F2937FD9435FC90F8D31CEABE496627D40B3813DBCC472ED0 | |||
| 3672 | explorer.exe | C:\Users\admin\AppData\Local\Temp\1000169001\contorax.exe | executable | |
MD5:771B8E84BA4F0215298D9DADFE5A10BF | SHA256:3F074FB6A883663F2937FD9435FC90F8D31CEABE496627D40B3813DBCC472ED0 | |||
| 3672 | explorer.exe | C:\Users\admin\AppData\Local\Temp\1000172001\3546345.exe | executable | |
MD5:FD2DEFC436FC7960D6501A01C91D893E | SHA256:BA13DA01C41FA50EC5E340061973BC912B1F41CD1F96A7CAE5D40AFC00FF7945 | |||
| 6372 | exbuild.exe | C:\Users\admin\AppData\Local\Temp\054fdc5f70\Hkbsse.exe | executable | |
MD5:F5D7B79EE6B6DA6B50E536030BCC3B59 | SHA256:2F1AFF28961BA0CE85EA0E35B8936BC387F84F459A4A1D63D964CE79E34B8459 | |||
| 2724 | crypteda.exe | C:\Users\admin\AppData\Roaming\mSOoiAKqbK.exe | executable | |
MD5:7E39CCB9926A01051635F3C2675FF01D | SHA256:4A5D76A51F341950E5588B373DC03CFC6A107A2799F5E8778D6994F5C15A52FC | |||
| 6372 | exbuild.exe | C:\Windows\Tasks\Hkbsse.job | binary | |
MD5:5AE2B7BCC9F9FBE4483A58B152FCBE04 | SHA256:A9816810E0FA27848611CF4B65DE992A88EE6D86F400A8B15F029B496DC0C6D5 | |||
| 6812 | mSOoiAKqbK.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\76b53b3ec448f7ccdda2063b15d2bfc3_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:BBC8DA7D36DF3F91C460984C2ABE8419 | SHA256:0399CCF5E780949A63400736A46CCE7D1879903D0F45C6B7D194C960BA4DDDC2 | |||
| 3672 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\random[1].exe | executable | |
MD5:527CAFA3AD70BE947F6B6A8354824FAD | SHA256:301071921A24EC63AF25364650115EAB986F45A5E4FE1B045E686AA626788D60 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
137
TCP/UDP connections
138
DNS requests
98
Threats
14 229
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2248 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1448 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3672 | explorer.exe | POST | 200 | 185.215.113.19:80 | http://185.215.113.19/CoreOPT/index.php | unknown | — | — | unknown |
3672 | explorer.exe | POST | 200 | 185.215.113.19:80 | http://185.215.113.19/CoreOPT/index.php | unknown | — | — | unknown |
3672 | explorer.exe | POST | 200 | 185.215.113.19:80 | http://185.215.113.19/CoreOPT/index.php | unknown | — | — | unknown |
3672 | explorer.exe | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/inc/contorax.exe | unknown | — | — | malicious |
3672 | explorer.exe | POST | 200 | 185.215.113.19:80 | http://185.215.113.19/CoreOPT/index.php | unknown | — | — | unknown |
3672 | explorer.exe | POST | 200 | 185.215.113.19:80 | http://185.215.113.19/CoreOPT/index.php?scr=1 | unknown | — | — | unknown |
3672 | explorer.exe | GET | 200 | 185.215.113.26:80 | http://185.215.113.26/exbuild.exe | unknown | — | — | malicious |
6720 | Hkbsse.exe | POST | 200 | 185.215.113.26:80 | http://185.215.113.26/Dem7kTu/index.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2248 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4132 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2248 | svchost.exe | 51.11.168.232:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
2248 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1448 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1448 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
conditionprovice.pro |
| unknown |
pastebin.com |
| shared |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2480 | acentric[1].exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3672 | explorer.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
3672 | explorer.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3672 | explorer.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
3672 | explorer.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
3672 | explorer.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
3672 | explorer.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
3672 | explorer.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
3672 | explorer.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
3672 | explorer.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
8 ETPRO signatures available at the full report
Process | Message |
|---|---|
cd5563c5b7.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|