| File name: | rizzler.exe |
| Full analysis: | https://app.any.run/tasks/8cf407af-a698-447a-b4fe-cd209664cd1a |
| Verdict: | Malicious activity |
| Threats: | Chaos ransomware is a malware family known for its destructive capabilities and diverse variants. It first appeared in 2021 as a ransomware builder and later acted as a wiper. Unlike most ransomware strains that encrypt data to extort payment, early Chaos variants permanently corrupted files, while later versions adopted more conventional encryption techniques. |
| Analysis date: | July 30, 2024, 19:02:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | FC031CDD7FE84E5221305C87E6375E13 |
| SHA1: | 57F0E3CD6BF5DC09FBAACD0D9FCB7BF35AF8EED7 |
| SHA256: | 1E93D49CB048B0BF26DDD4CF728FC9E7900B33222DE596140CAC44DC41BC14F4 |
| SSDEEP: | 6144:IkGc9jqFqg0UtSIIIIIIIZIIIIIIIIIIIIIIIlnFf:Ik5qkg0Uc |
MALICIOUS
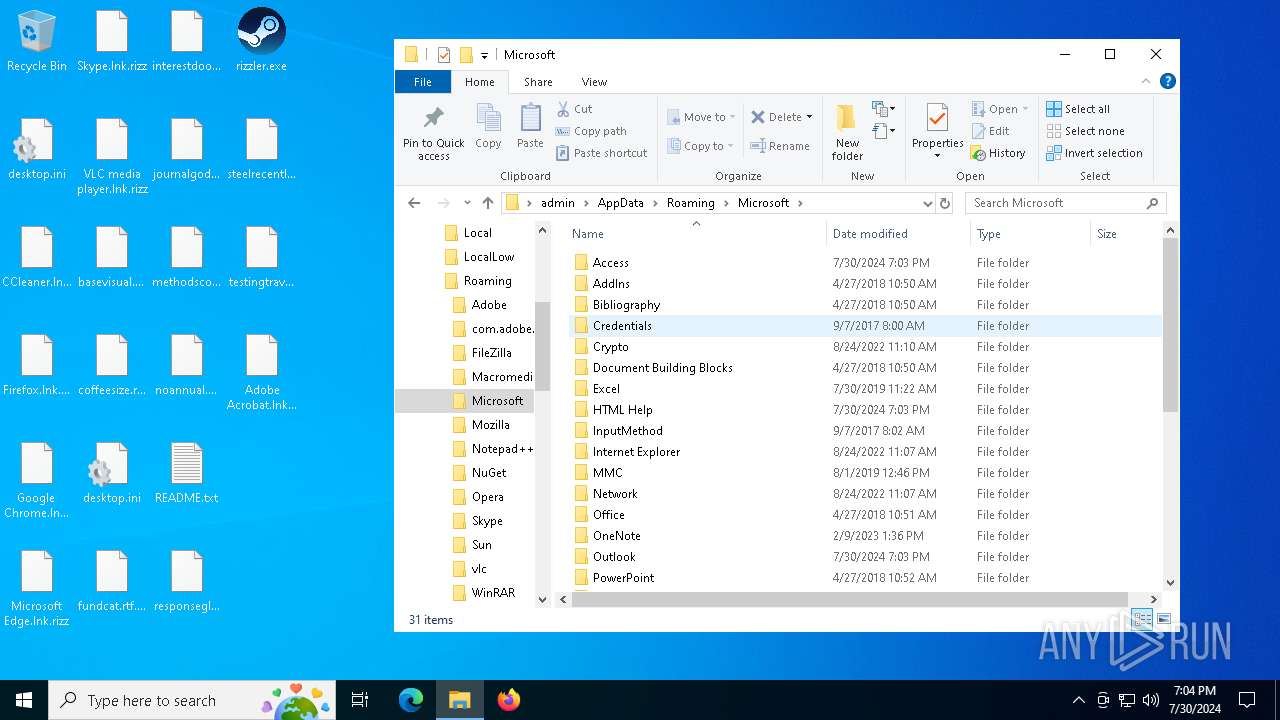
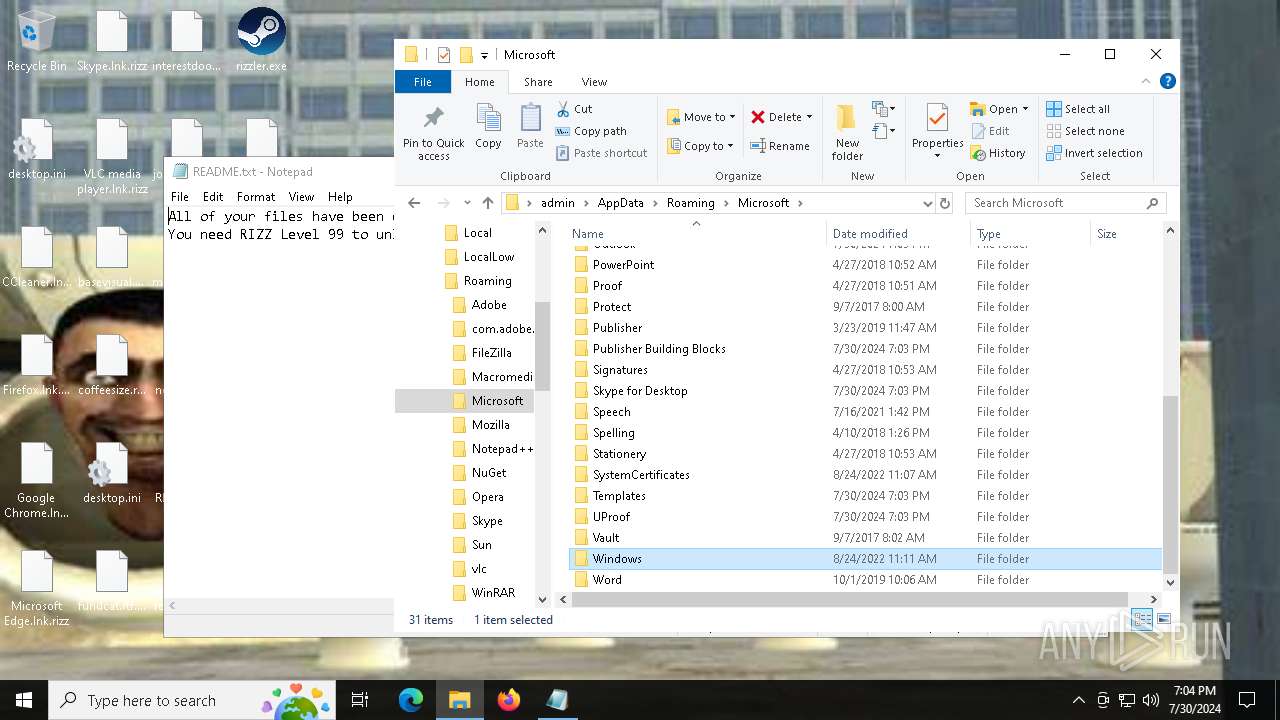
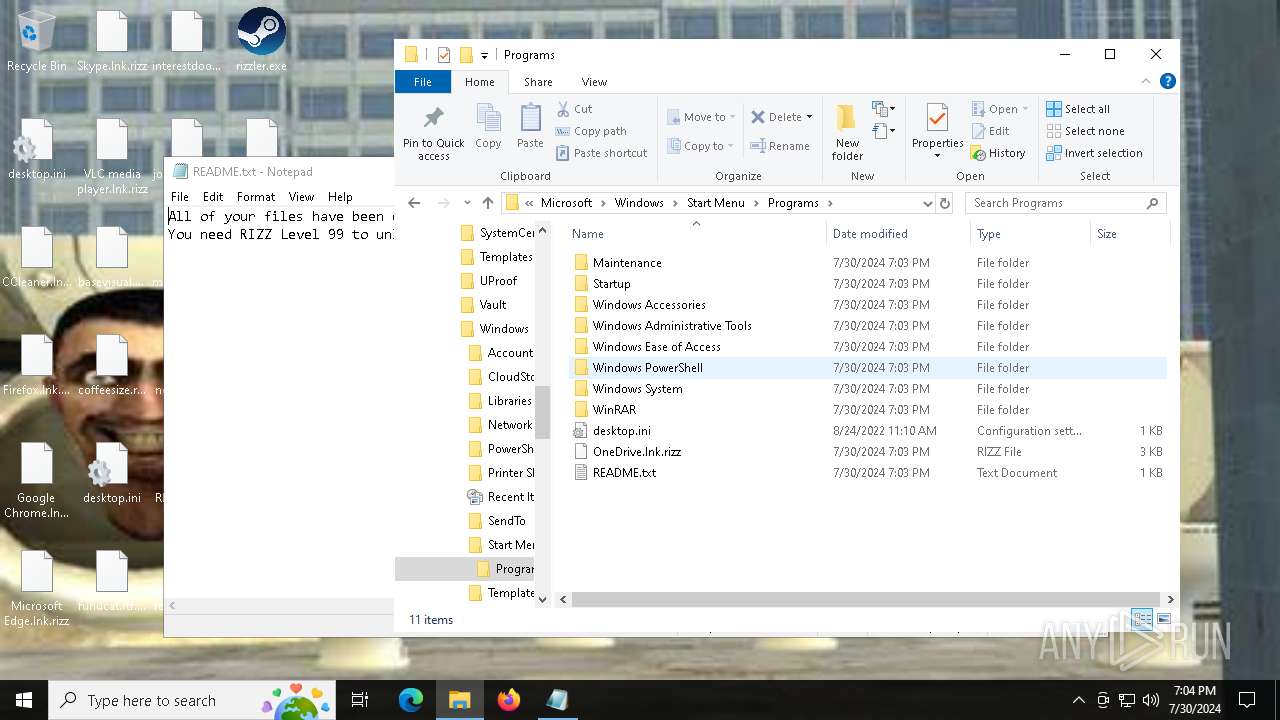
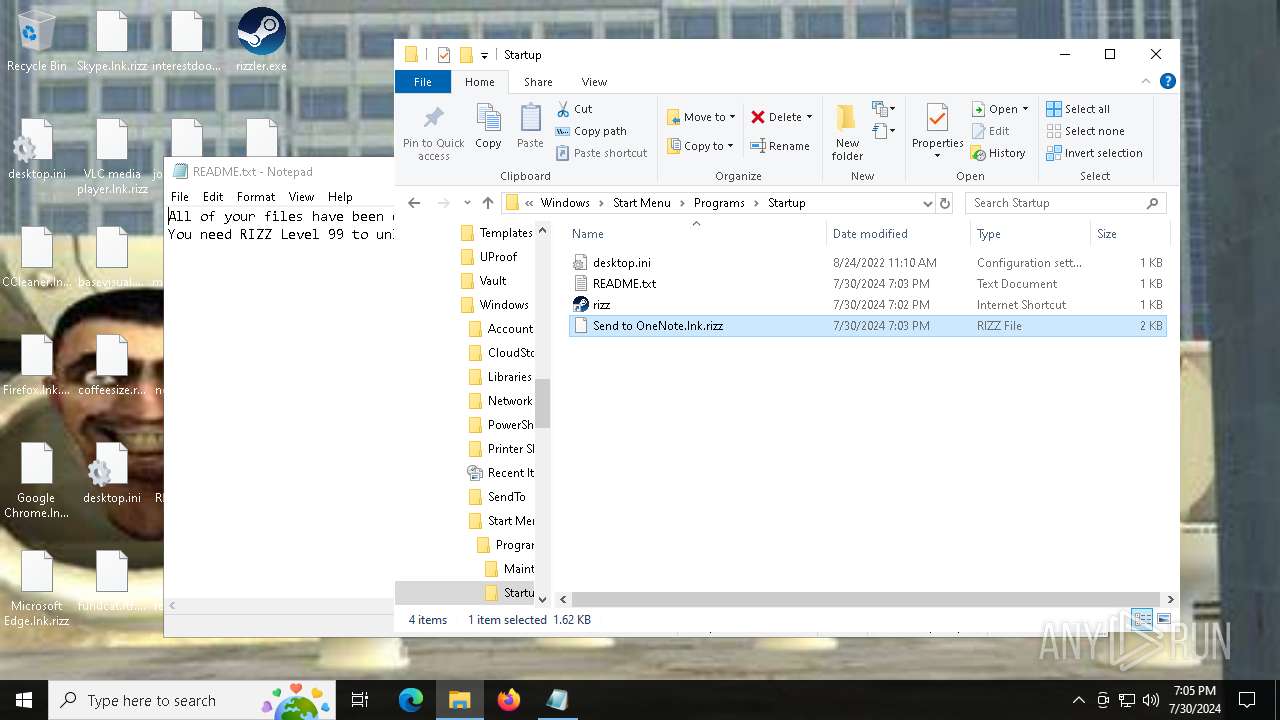
Drops the executable file immediately after the start
- rizzler.exe (PID: 7220)
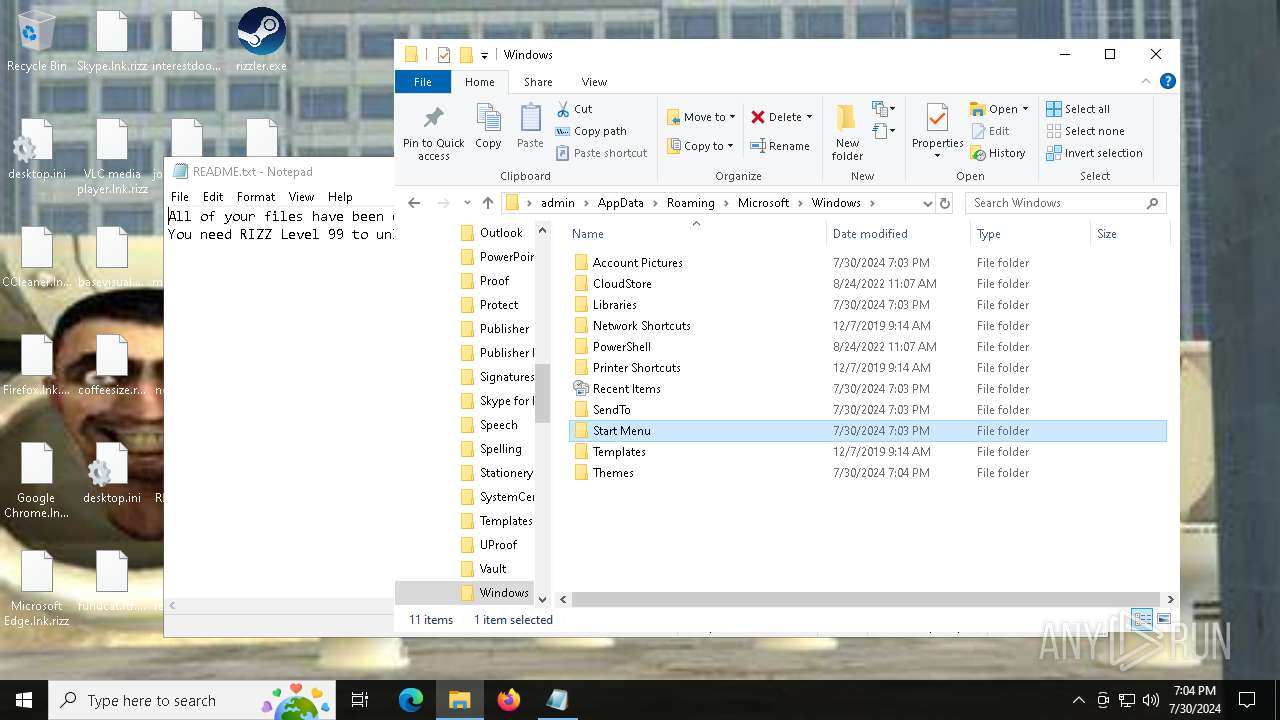
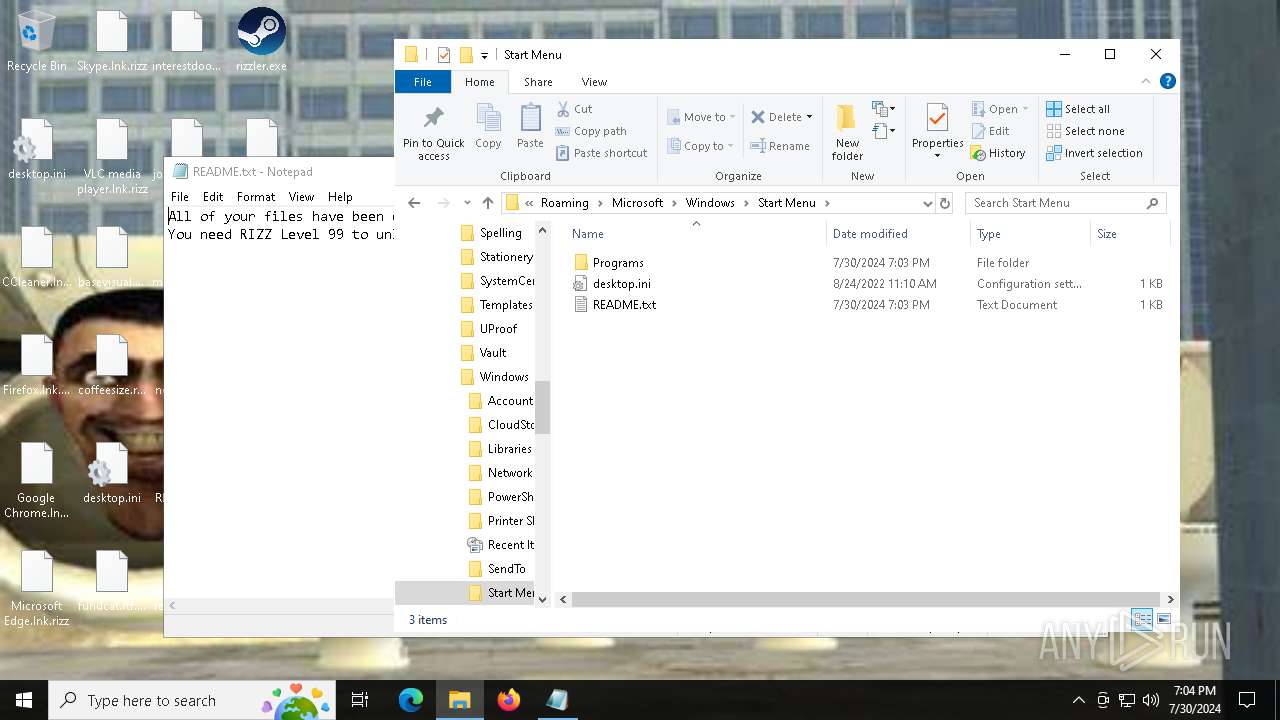
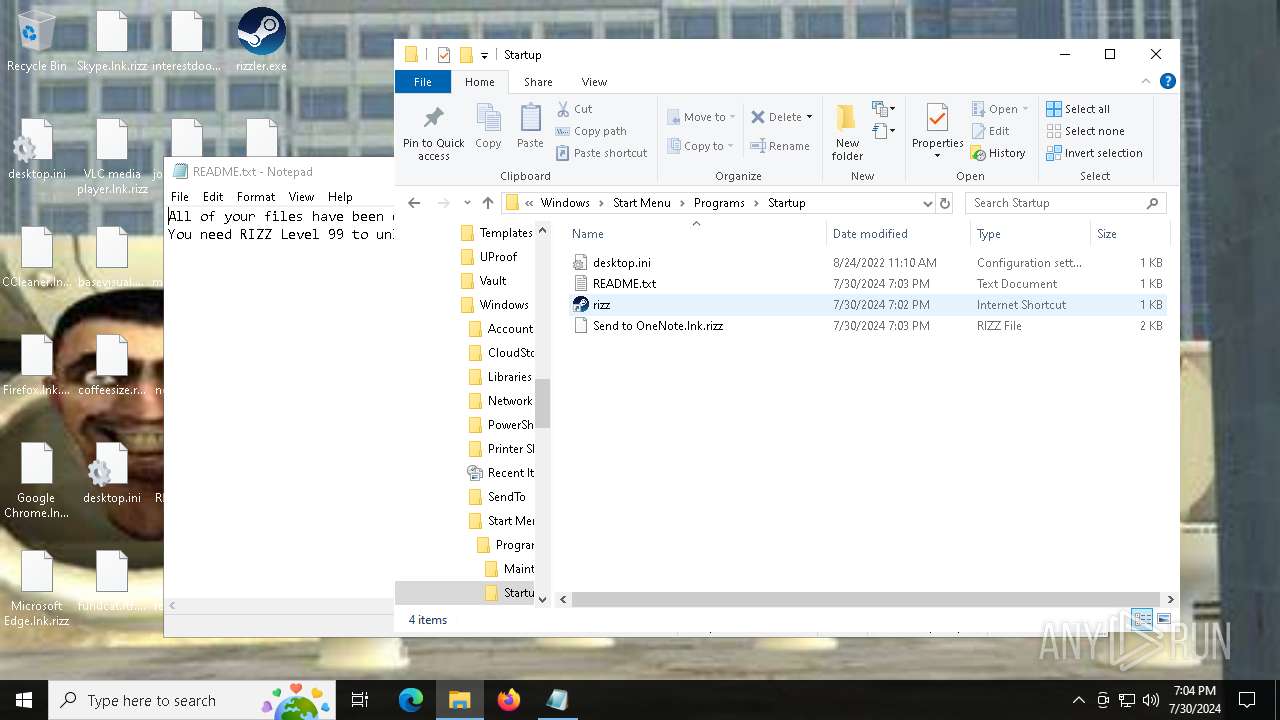
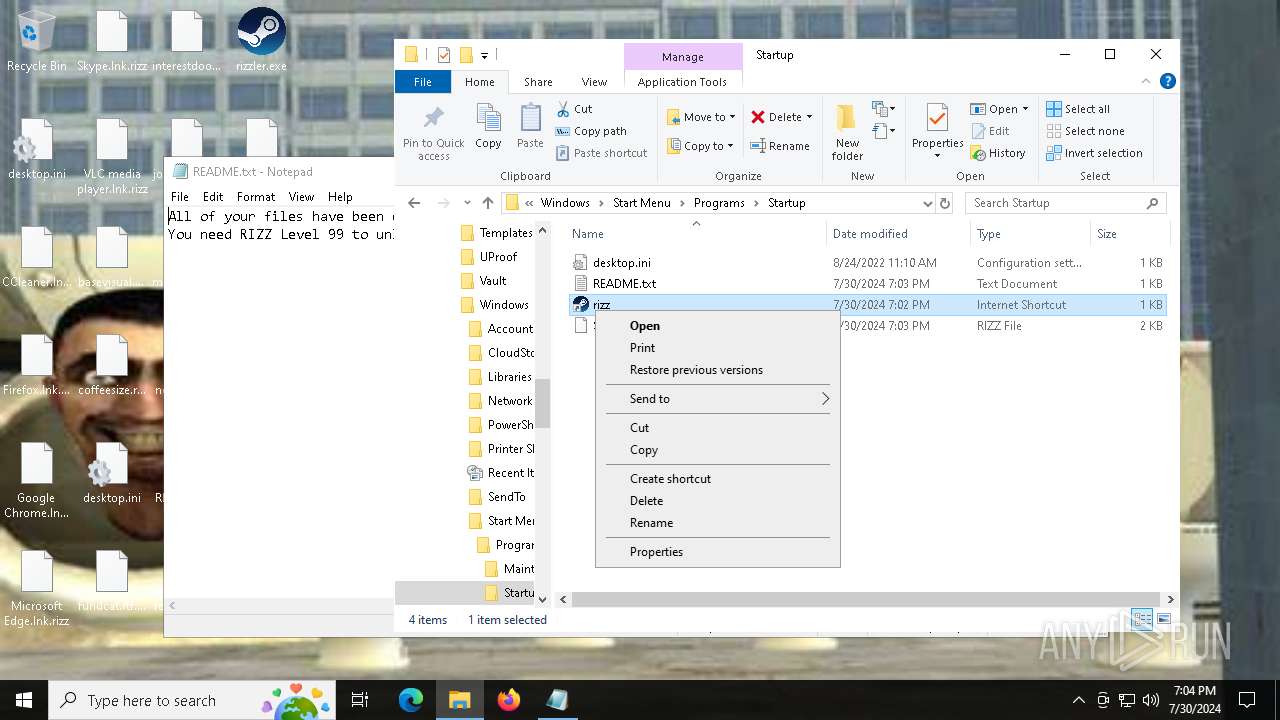
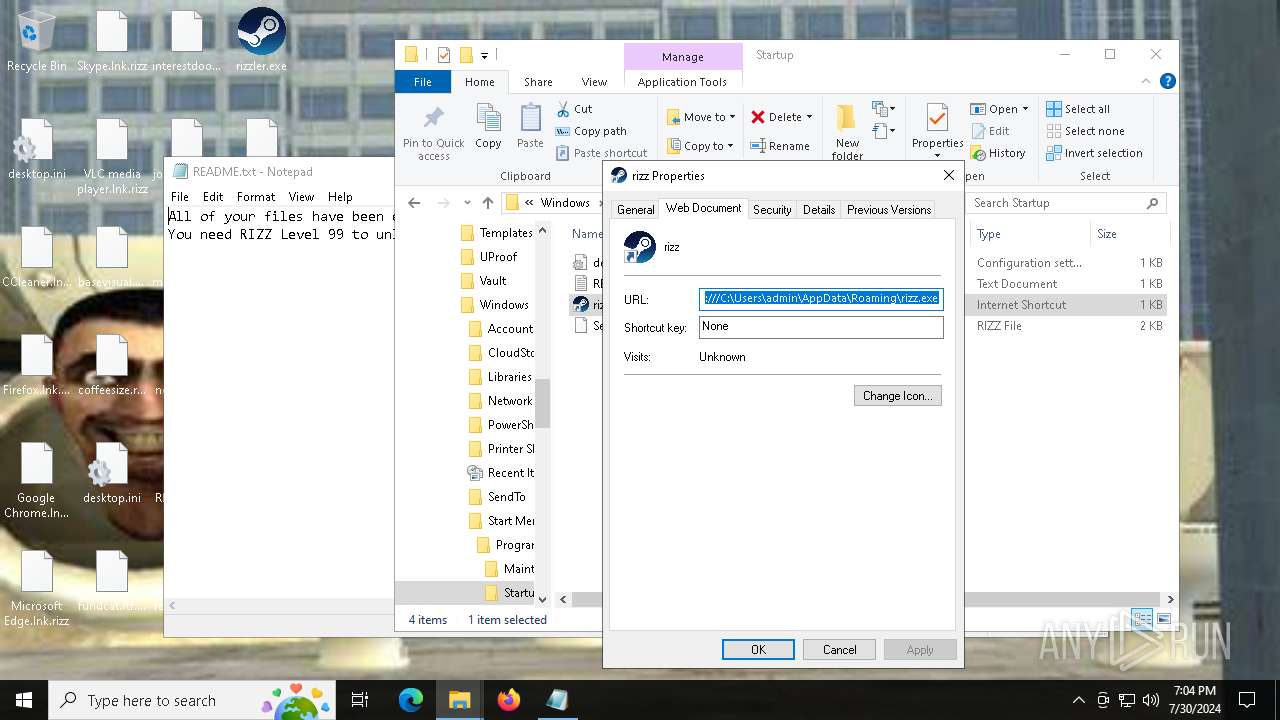
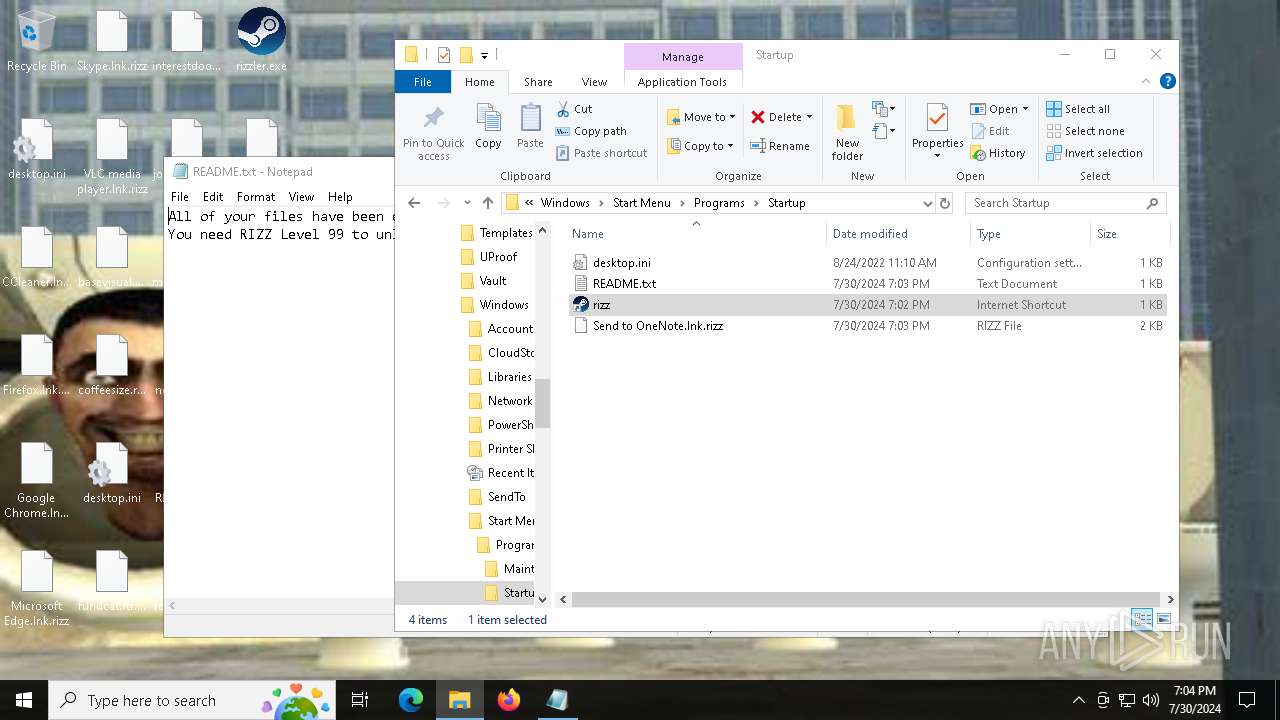
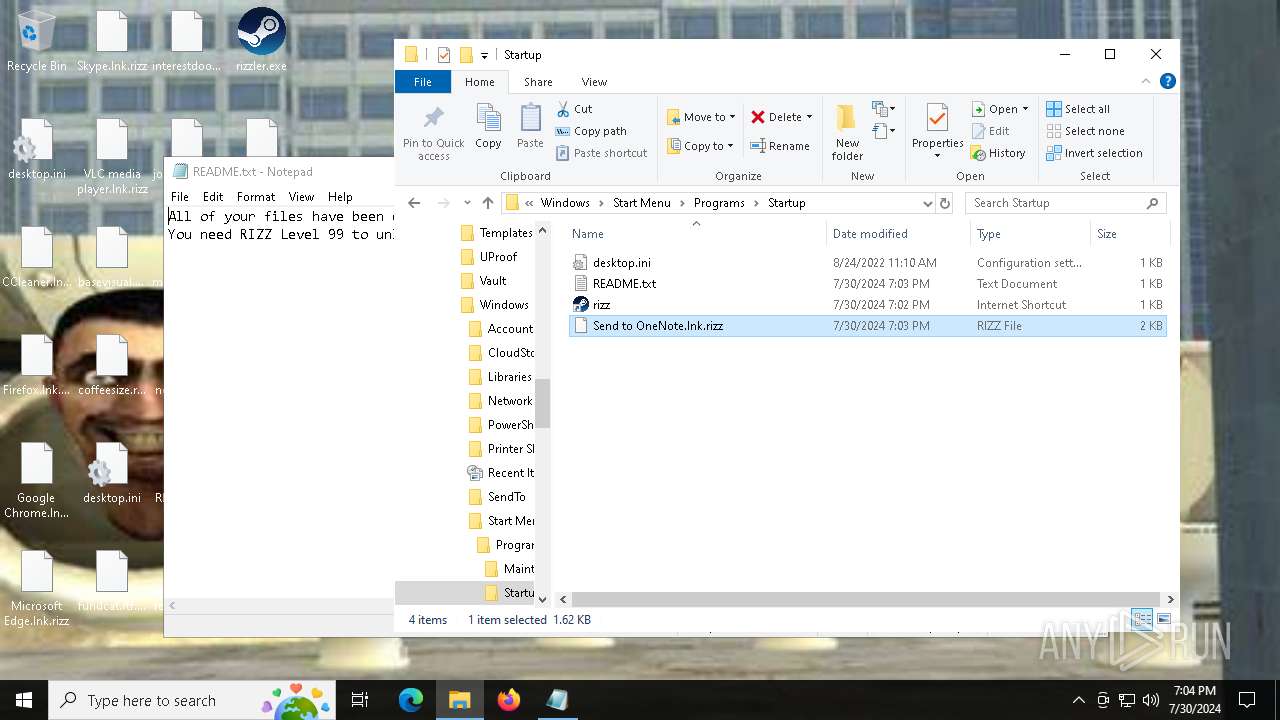
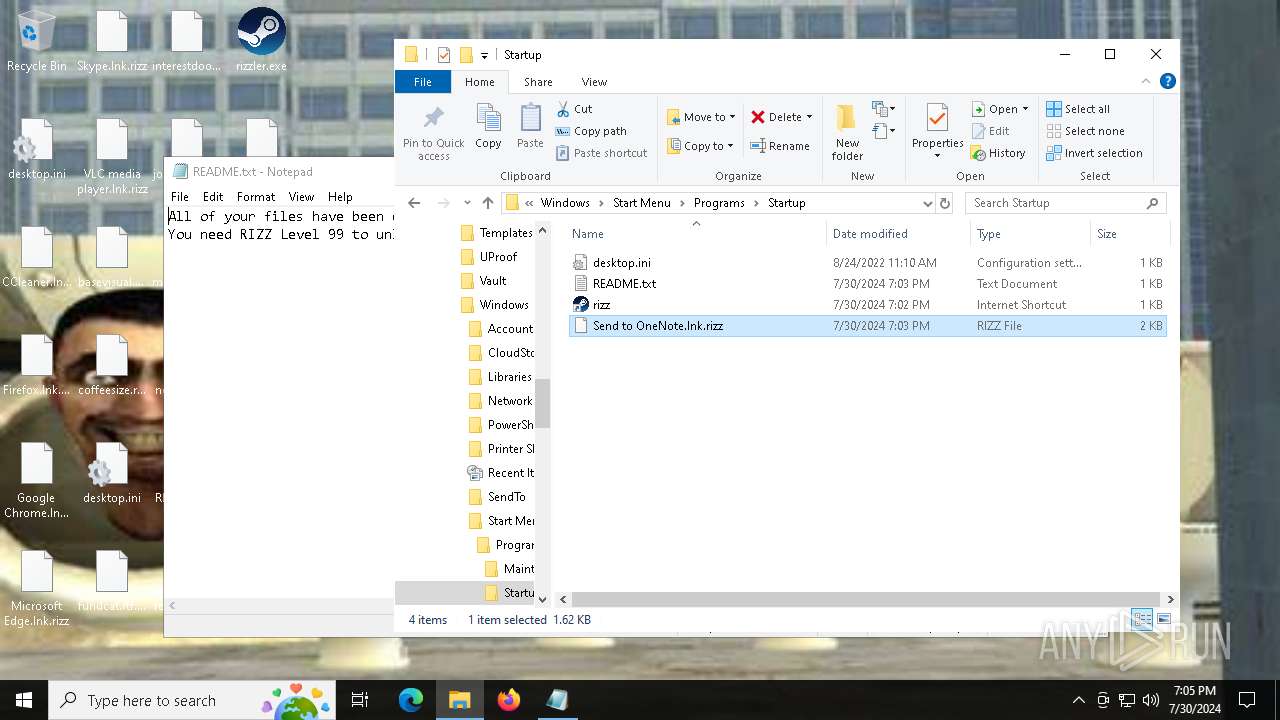
Create files in the Startup directory
- rizz.exe (PID: 7680)
Deletes shadow copies
- cmd.exe (PID: 7844)
- cmd.exe (PID: 6504)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 3196)
Steals credentials from Web Browsers
- rizz.exe (PID: 7680)
CHAOS has been detected (YARA)
- rizz.exe (PID: 7680)
- rizz.exe (PID: 7568)
- rizz.exe (PID: 7848)
Modifies files in the Chrome extension folder
- rizz.exe (PID: 7680)
Actions looks like stealing of personal data
- rizz.exe (PID: 7680)
SUSPICIOUS
Executable content was dropped or overwritten
- rizzler.exe (PID: 7220)
Reads security settings of Internet Explorer
- rizzler.exe (PID: 7220)
- rizz.exe (PID: 7680)
Starts CMD.EXE for commands execution
- rizz.exe (PID: 7680)
Starts itself from another location
- rizzler.exe (PID: 7220)
Executes as Windows Service
- VSSVC.exe (PID: 7932)
- wbengine.exe (PID: 3720)
- vds.exe (PID: 4356)
Reads the date of Windows installation
- rizzler.exe (PID: 7220)
- rizz.exe (PID: 7680)
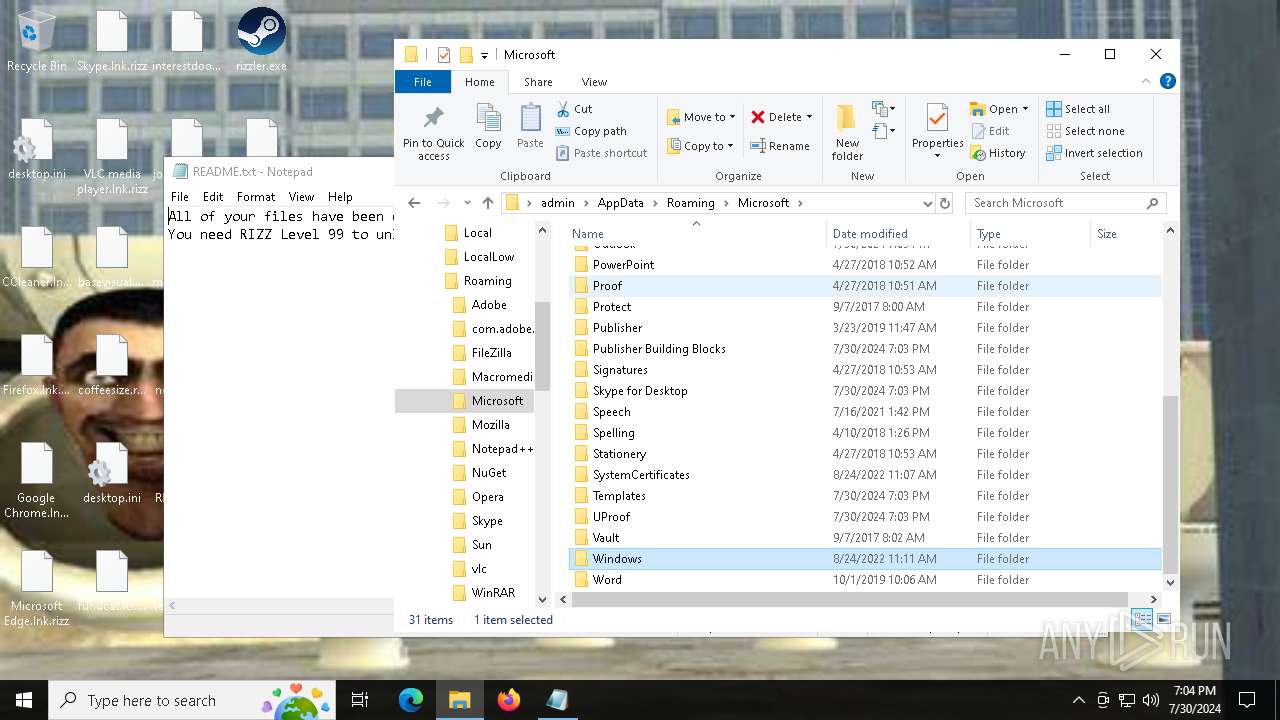
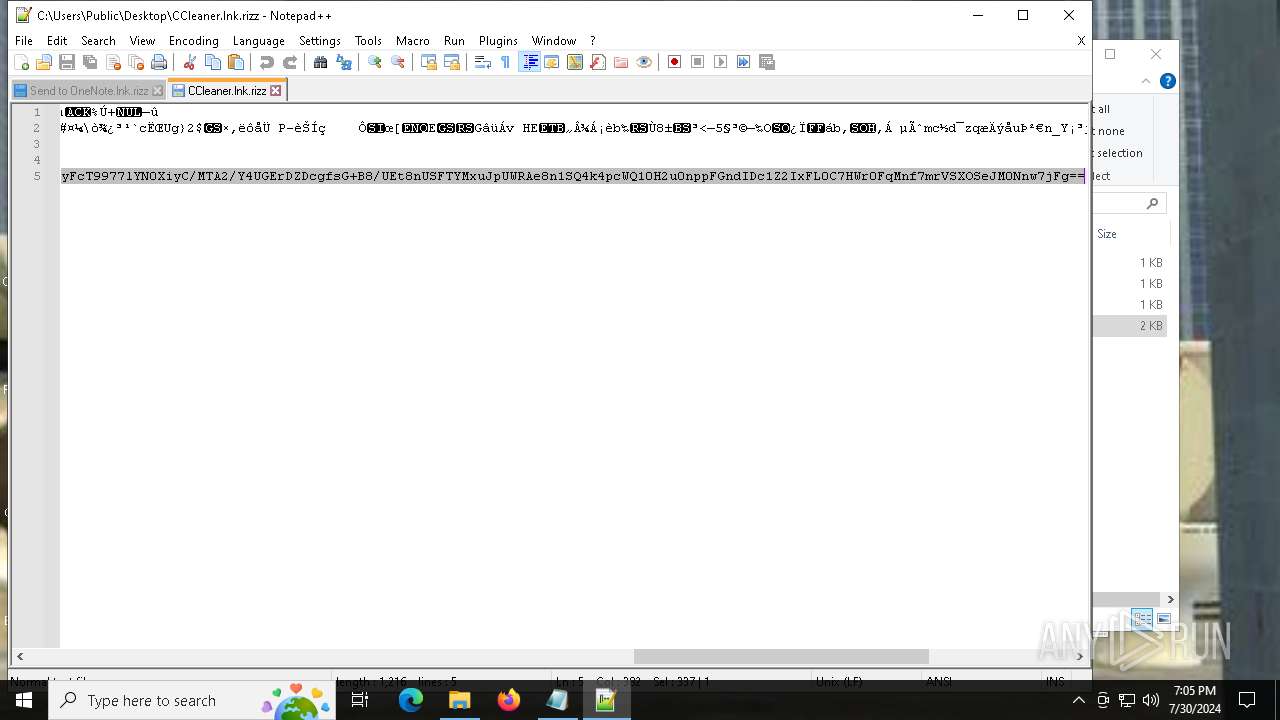
Creates files like ransomware instruction
- rizz.exe (PID: 7680)
Found regular expressions for crypto-addresses (YARA)
- rizz.exe (PID: 7680)
- rizz.exe (PID: 7848)
- rizz.exe (PID: 7568)
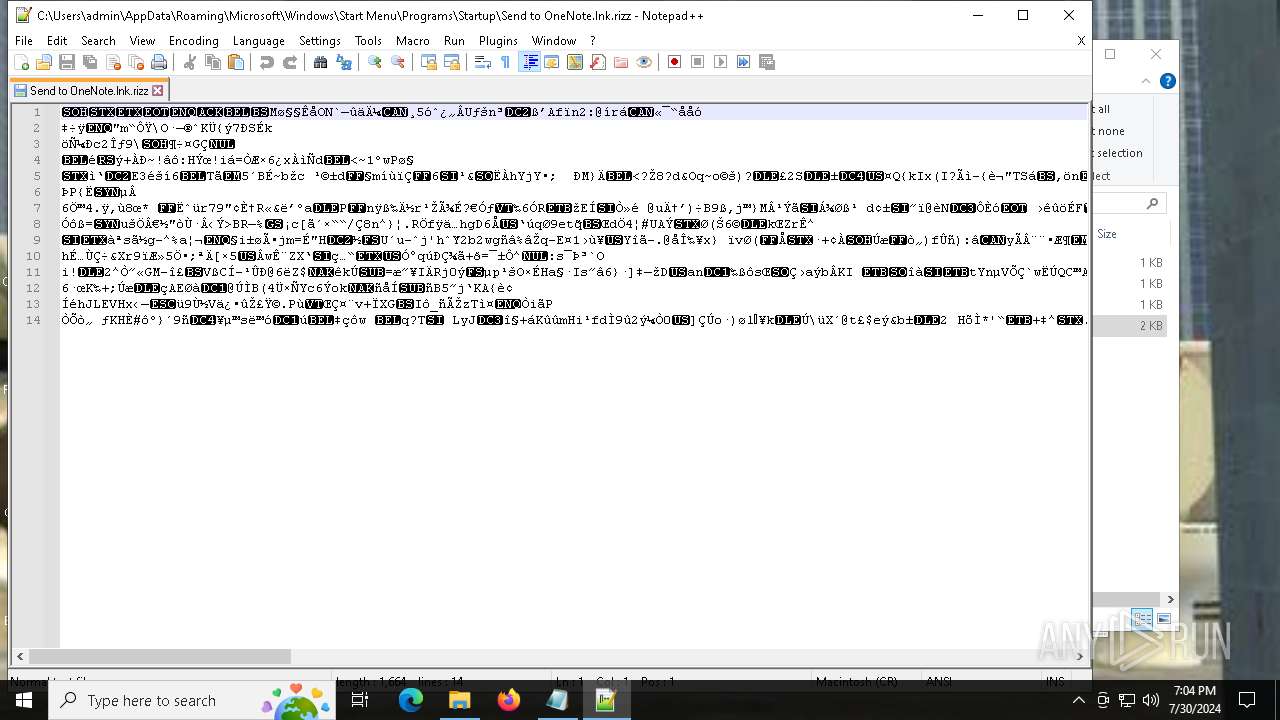
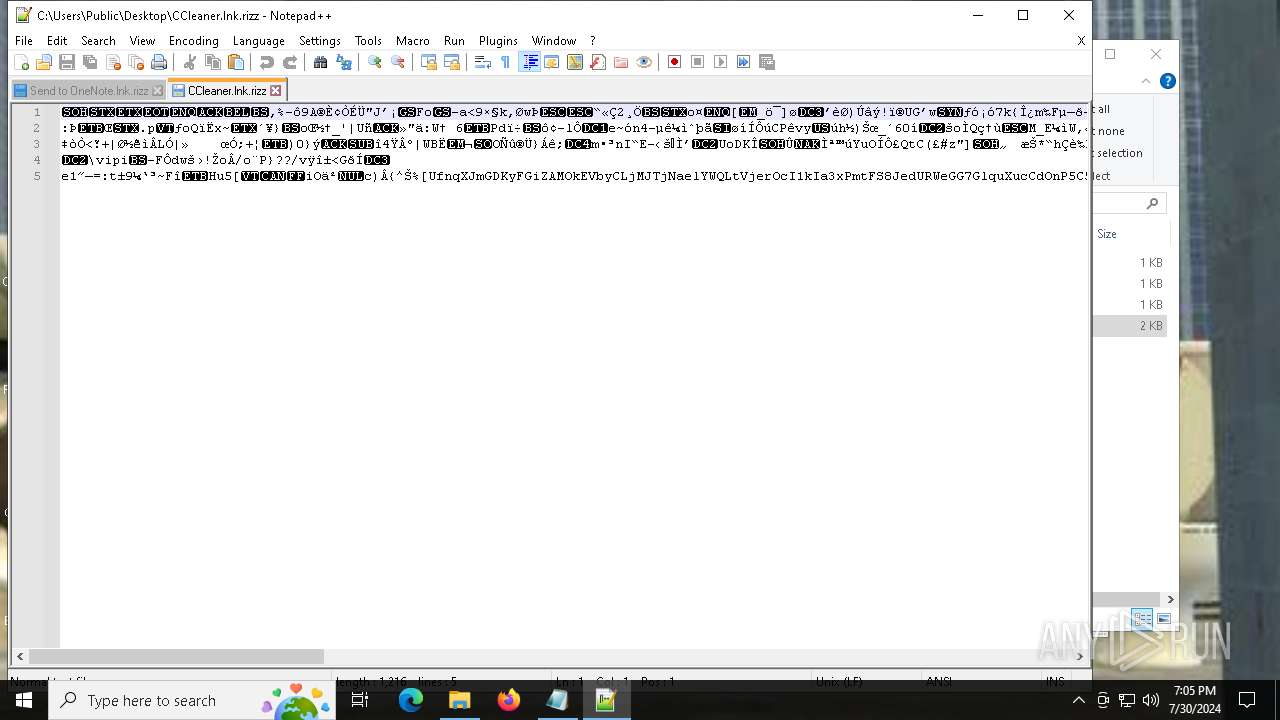
Start notepad (likely ransomware note)
- rizz.exe (PID: 7680)
Likely accesses (executes) a file from the Public directory
- notepad++.exe (PID: 6372)
INFO
Reads the computer name
- rizzler.exe (PID: 7220)
- rizz.exe (PID: 7680)
- rizz.exe (PID: 7568)
- rizz.exe (PID: 7848)
Checks supported languages
- rizz.exe (PID: 7680)
- rizzler.exe (PID: 7220)
- rizz.exe (PID: 7568)
- rizz.exe (PID: 7848)
Process checks computer location settings
- rizz.exe (PID: 7680)
- rizzler.exe (PID: 7220)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 2120)
- notepad.exe (PID: 7912)
Creates files or folders in the user directory
- rizzler.exe (PID: 7220)
- rizz.exe (PID: 7680)
Reads the software policy settings
- slui.exe (PID: 5608)
Reads Microsoft Office registry keys
- rizz.exe (PID: 7680)
Checks proxy server information
- slui.exe (PID: 5608)
Manual execution by a user
- rizz.exe (PID: 7568)
- rizz.exe (PID: 7848)
- notepad++.exe (PID: 1468)
- notepad++.exe (PID: 6372)
Reads the machine GUID from the registry
- rizz.exe (PID: 7568)
- rizz.exe (PID: 7680)
- rizz.exe (PID: 7848)
Create files in a temporary directory
- rizz.exe (PID: 7680)
Creates files in the program directory
- rizz.exe (PID: 7680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:30 18:49:24+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 83456 |
| InitializedDataSize: | 272384 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x165ce |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | rizzler.exe |
| LegalCopyright: | |
| OriginalFileName: | rizzler.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
162
Monitored processes
23
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1468 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Send to OneNote.lnk.rizz" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 1476 | wbadmin delete catalog -quiet | C:\Windows\System32\wbadmin.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® BLB Backup Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2120 | wmic shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | C:\WINDOWS\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Loader Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2492 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2952 | bcdedit /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3196 | "C:\Windows\System32\cmd.exe" /C bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no | C:\Windows\System32\cmd.exe | — | rizz.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3720 | "C:\WINDOWS\system32\wbengine.exe" | C:\Windows\System32\wbengine.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Block Level Backup Engine Service EXE Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4356 | C:\WINDOWS\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 683
Read events
13 605
Write events
58
Delete events
20
Modification events
| (PID) Process: | (7220) rizzler.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7220) rizzler.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7220) rizzler.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7220) rizzler.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7680) rizz.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7680) rizz.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7680) rizz.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7680) rizz.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2952) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2952) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Description |
| Operation: | write | Name: | FirmwareModified |
Value: 1 | |||
Executable files
1
Suspicious files
577
Text files
882
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7680 | rizz.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\rizz.url | text | |
MD5:CCD9ADB41C9D7852BD84576FD8628459 | SHA256:4B7387EE4480578B9E1E56D9558D96349969B3476D3D4AB276213810B34189E3 | |||
| 7680 | rizz.exe | C:\$WinREAgent\Backup\ReAgent.xml.rizz | dcf | |
MD5:5319DA9E629C0E549110135FE66660D2 | SHA256:4F6488BDED90D99FDABED7B0BB2DB9CED04A334DA2DA7D205449CCC14D85A16C | |||
| 7680 | rizz.exe | C:\$WinREAgent\Backup\README.txt | text | |
MD5:112B5F9570B63D4B6DD4FD5E592F20AF | SHA256:37DEE262DA5BB8982909A2D9A13804D14E0477EDC90363221603D4CA152218C9 | |||
| 7680 | rizz.exe | C:\found.000\dir0001.chk\WmiApRpl.ini.rizz | binary | |
MD5:542AAC32A295A4600033CE4AD6CFD7D4 | SHA256:F28024BCAE33405AA2AEDA1EDDD00FF57B65F151A5CB72748615B4D3C0B8844F | |||
| 7680 | rizz.exe | C:\Recovery\README.txt | text | |
MD5:112B5F9570B63D4B6DD4FD5E592F20AF | SHA256:37DEE262DA5BB8982909A2D9A13804D14E0477EDC90363221603D4CA152218C9 | |||
| 7680 | rizz.exe | C:\Recovery\OEM\ResetConfig.xml.rizz | binary | |
MD5:61724EDBBF042416678FE2BD33B543B1 | SHA256:1F7ADF722F2F0AD3D7B3428D3699F6C522C6ADC2DC1DD46B53718DCDA7814E59 | |||
| 7680 | rizz.exe | C:\$WinREAgent\Rollback.xml.rizz | binary | |
MD5:46CAB17623A3AB44B7FCD9B29E6BC86F | SHA256:16926106D95436F7980234A97580F327186B71B6AB1001D1C986D93F7A71096C | |||
| 7680 | rizz.exe | C:\found.000\dir0001.chk\README.txt | text | |
MD5:112B5F9570B63D4B6DD4FD5E592F20AF | SHA256:37DEE262DA5BB8982909A2D9A13804D14E0477EDC90363221603D4CA152218C9 | |||
| 7680 | rizz.exe | C:\$WinREAgent\RollbackInfo.ini | binary | |
MD5:D1457B72C3FB323A2671125AEF3EAB5D | SHA256:8A8DE823D5ED3E12746A62EF169BCF372BE0CA44F0A1236ABC35DF05D96928E1 | |||
| 7680 | rizz.exe | C:\$WinREAgent\RollbackInfo.ini.rizz | binary | |
MD5:90DE56777EF8AF431C132D01CEBDD72F | SHA256:BED79F6C91077A0131BA710F23D4CE2A898ACD832B41EB0B71955941A60B43D6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
41
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7500 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6412 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2668 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5368 | SearchApp.exe | 104.126.37.42:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5368 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4424 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
t-ring-fdv2.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
a-ring-fallback.msedge.net |
| unknown |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
wbadmin.exe | Invalid parameter passed to C runtime function.
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|