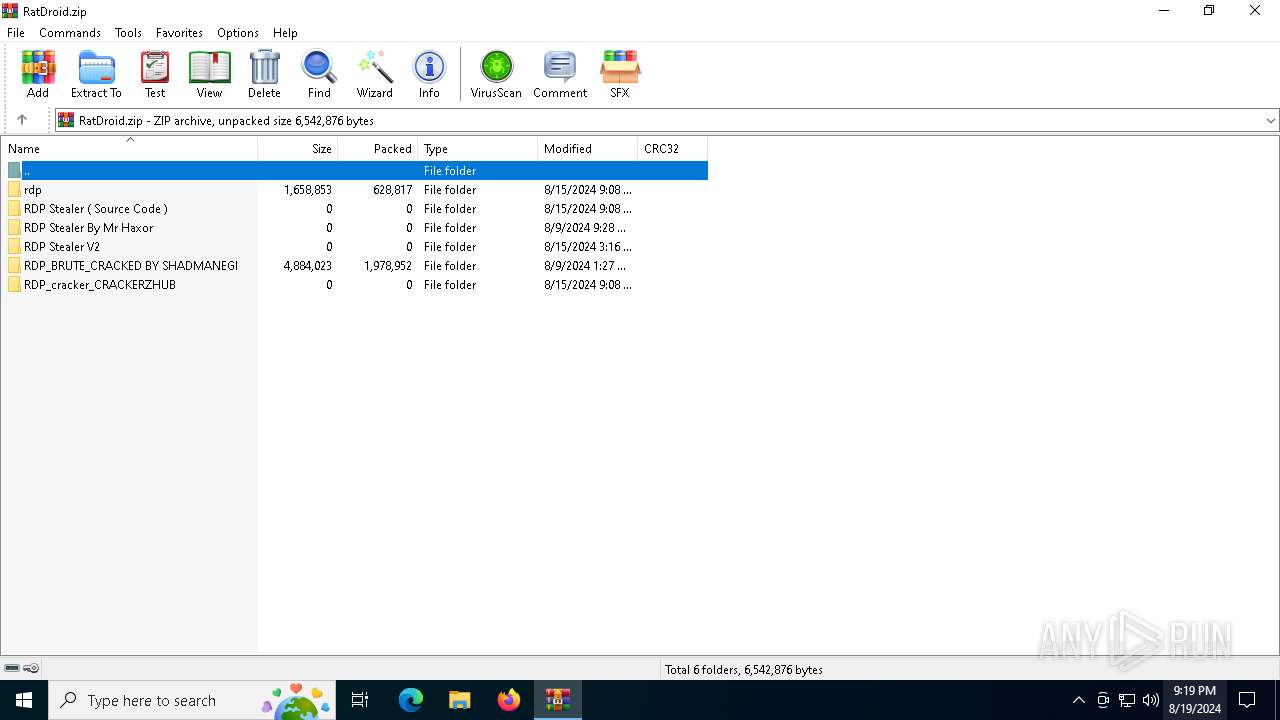
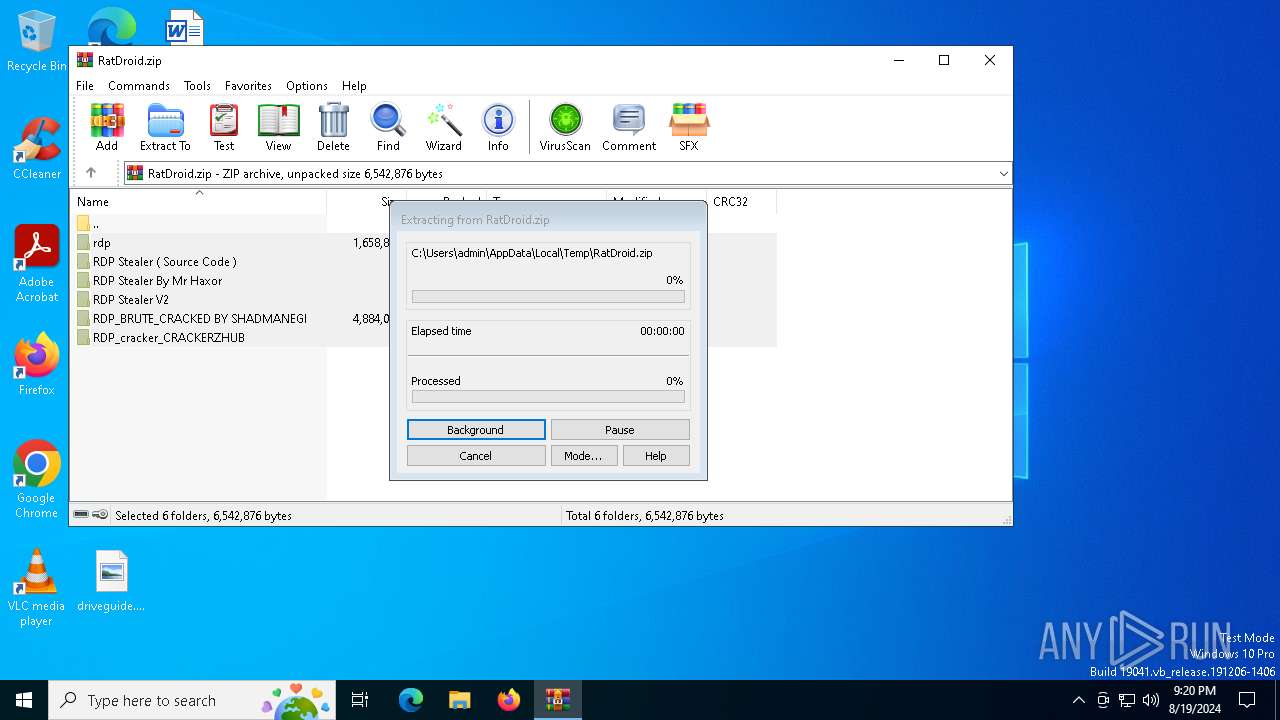
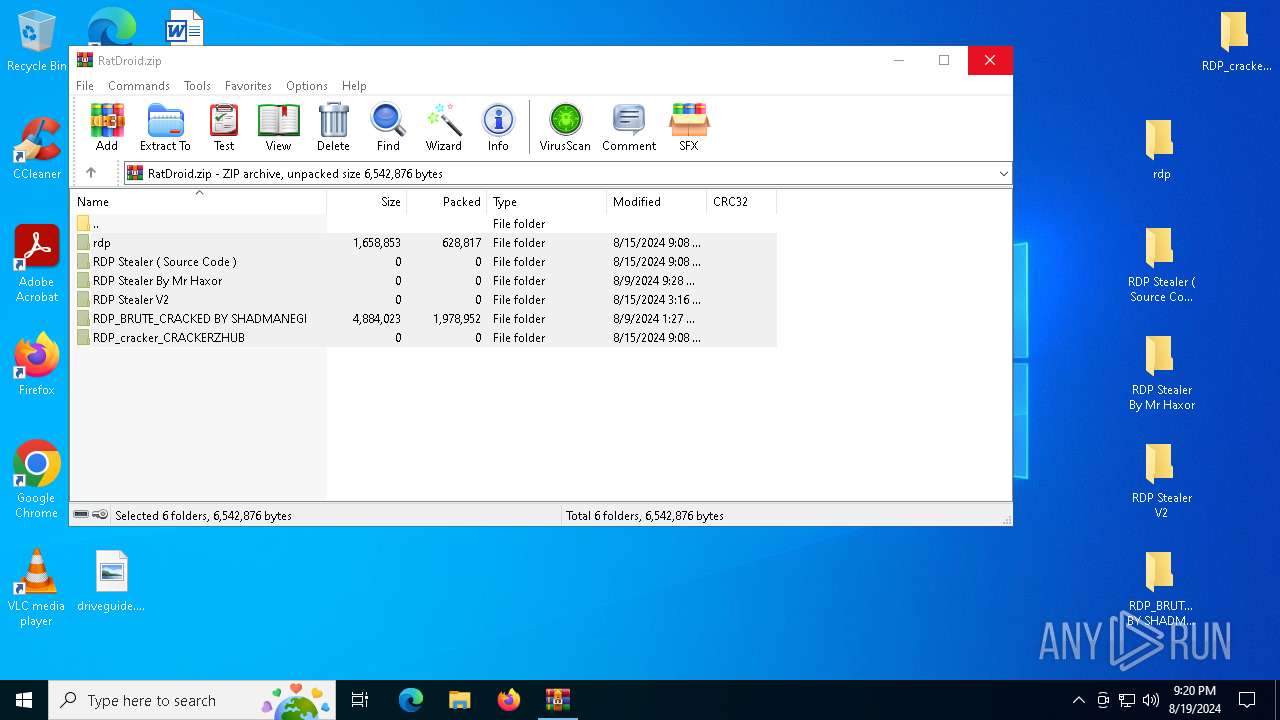
| File name: | RatDroid.zip |
| Full analysis: | https://app.any.run/tasks/2dfa13b7-ed6a-47ba-823c-1a28ccd6c314 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | August 19, 2024, 21:19:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | EF0499EE6EBCA4FA396FDC39F9B4EEC5 |
| SHA1: | 7B8143A3D9F852D3CE992DA9E6A17D3E05618CD8 |
| SHA256: | 1E527E80F8C8AB8B43A757C719F772FAAA96649F777942E499825546CC488876 |
| SSDEEP: | 98304:VWmDc5as7EU1ITgDFSu7hl2ZRo0zy0Aogk1Z8R8xlp4rhRs3zyAgTeWA1Qfc8XmR:+31F8 |
MALICIOUS
Changes the autorun value in the registry
- IPRangy.exe (PID: 6872)
- Windows Defender Security.exe (PID: 4820)
- Windows Update.exe (PID: 6856)
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 2264)
- Windows Security Health Service.exe (PID: 5548)
- Windows Defender Security.exe (PID: 7024)
Connects to the CnC server
- Synaptics.exe (PID: 6784)
QUASAR has been detected (YARA)
- Windows Defender Security.exe (PID: 7024)
- Windows Security Health Service.exe (PID: 5548)
- Windows Update.exe (PID: 1164)
- Windows Defender Security.exe (PID: 1128)
SUSPICIOUS
Drops the executable file immediately after the start
- IPRangy.exe (PID: 6872)
- WinRAR.exe (PID: 6668)
- Synaptics.exe (PID: 6784)
- RDP Brute_Cracked.exe (PID: 4020)
- ._cache_RDP Brute_Cracked.exe (PID: 3812)
- Windows Update.exe (PID: 6856)
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 2264)
Executable content was dropped or overwritten
- IPRangy.exe (PID: 6872)
- RDP Brute_Cracked.exe (PID: 4020)
- Synaptics.exe (PID: 6784)
- Windows Update.exe (PID: 6856)
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 2264)
- ._cache_RDP Brute_Cracked.exe (PID: 3812)
Reads the date of Windows installation
- IPRangy.exe (PID: 6872)
- RDP Brute_Cracked.exe (PID: 4020)
- ._cache_RDP Brute_Cracked.exe (PID: 3812)
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 2264)
Reads security settings of Internet Explorer
- IPRangy.exe (PID: 6872)
- Synaptics.exe (PID: 6784)
- RDP Brute_Cracked.exe (PID: 4020)
- ._cache_RDP Brute_Cracked.exe (PID: 3812)
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 2264)
Contacting a server suspected of hosting an CnC
- Synaptics.exe (PID: 6784)
Reads the Windows owner or organization settings
- ._cache_IPRangy.exe (PID: 6884)
Checks for external IP
- svchost.exe (PID: 2256)
- ._cache_IPRangy.exe (PID: 6884)
- Windows Security Health Service.exe (PID: 5548)
- Windows Defender Security.exe (PID: 7024)
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 2264)
There is functionality for communication dyndns network (YARA)
- Synaptics.exe (PID: 6784)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- ._cache_IPRangy.exe (PID: 6884)
There is functionality for taking screenshot (YARA)
- Synaptics.exe (PID: 6784)
There is functionality for communication over UDP network (YARA)
- Synaptics.exe (PID: 6784)
Probably fake Windows Update
- Windows Update.exe (PID: 6856)
- Windows Update.exe (PID: 2608)
- Windows Update.exe (PID: 1164)
- Windows Update.exe (PID: 7048)
Probably fake Windows Update file has been dropped
- ._cache_RDP Brute_Cracked.exe (PID: 3812)
- Windows Update.exe (PID: 6856)
Process drops legitimate windows executable
- Windows Update.exe (PID: 6856)
- Windows Defender Security.exe (PID: 2264)
- Windows Update.exe (PID: 2608)
- ._cache_RDP Brute_Cracked.exe (PID: 3812)
Executes application which crashes
- RDP Brute_Cracked.exe (PID: 2016)
Application launched itself
- Windows Defender Security.exe (PID: 4820)
- Windows Update.exe (PID: 6856)
- Windows Security Health Service.exe (PID: 7108)
- Windows Defender Security.exe (PID: 7052)
- Windows Update.exe (PID: 7048)
- Windows Defender Security.exe (PID: 3256)
Starts itself from another location
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 2264)
Starts application with an unusual extension
- cmd.exe (PID: 7136)
- cmd.exe (PID: 2876)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7136)
- cmd.exe (PID: 2876)
Executing commands from a ".bat" file
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 2264)
Starts CMD.EXE for commands execution
- Windows Defender Security.exe (PID: 2264)
- Windows Update.exe (PID: 2608)
Connects to unusual port
- Windows Defender Security.exe (PID: 7024)
- Windows Security Health Service.exe (PID: 5548)
Checks Windows Trust Settings
- Synaptics.exe (PID: 6784)
The executable file from the user directory is run by the CMD process
- Windows Update.exe (PID: 7048)
- Windows Defender Security.exe (PID: 3256)
INFO
Manual execution by a user
- IPRangy.exe (PID: 6872)
- RDP Brute_Cracked.exe (PID: 4020)
Reads the computer name
- IPRangy.exe (PID: 6872)
- ._cache_IPRangy.exe (PID: 6884)
- Synaptics.exe (PID: 6784)
- RDP Brute_Cracked.exe (PID: 4020)
- ._cache_RDP Brute_Cracked.exe (PID: 3812)
- Windows Defender Security.exe (PID: 4820)
- RDP Brute_Cracked.exe (PID: 2016)
- Windows Update.exe (PID: 6856)
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 2264)
- Windows Security Health Service.exe (PID: 7108)
- Windows Defender Security.exe (PID: 7052)
- Windows Security Health Service.exe (PID: 5548)
- Windows Defender Security.exe (PID: 7024)
- Windows Update.exe (PID: 7048)
- Windows Update.exe (PID: 1164)
- Windows Defender Security.exe (PID: 3256)
- Windows Defender Security.exe (PID: 1128)
Checks supported languages
- IPRangy.exe (PID: 6872)
- ._cache_IPRangy.exe (PID: 6884)
- Synaptics.exe (PID: 6784)
- RDP Brute_Cracked.exe (PID: 4020)
- ._cache_RDP Brute_Cracked.exe (PID: 3812)
- Windows Update.exe (PID: 6856)
- RDP Brute_Cracked.exe (PID: 2016)
- Windows Defender Security.exe (PID: 4820)
- Windows Defender Security.exe (PID: 2264)
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 7052)
- Windows Security Health Service.exe (PID: 7108)
- Windows Security Health Service.exe (PID: 5548)
- Windows Defender Security.exe (PID: 7024)
- chcp.com (PID: 4708)
- chcp.com (PID: 6940)
- Windows Update.exe (PID: 7048)
- Windows Defender Security.exe (PID: 3256)
- Windows Update.exe (PID: 1164)
- Windows Defender Security.exe (PID: 1128)
Process checks computer location settings
- IPRangy.exe (PID: 6872)
- RDP Brute_Cracked.exe (PID: 4020)
- ._cache_RDP Brute_Cracked.exe (PID: 3812)
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 2264)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6668)
Creates files in the program directory
- IPRangy.exe (PID: 6872)
- Synaptics.exe (PID: 6784)
Reads the machine GUID from the registry
- ._cache_IPRangy.exe (PID: 6884)
- ._cache_RDP Brute_Cracked.exe (PID: 3812)
- Windows Defender Security.exe (PID: 4820)
- Windows Update.exe (PID: 6856)
- Windows Defender Security.exe (PID: 2264)
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 7052)
- Windows Security Health Service.exe (PID: 7108)
- Windows Security Health Service.exe (PID: 5548)
- Windows Defender Security.exe (PID: 7024)
- Synaptics.exe (PID: 6784)
- Windows Update.exe (PID: 7048)
- Windows Update.exe (PID: 1164)
- Windows Defender Security.exe (PID: 3256)
- Windows Defender Security.exe (PID: 1128)
Disables trace logs
- ._cache_IPRangy.exe (PID: 6884)
- Windows Defender Security.exe (PID: 2264)
- Windows Update.exe (PID: 2608)
- Windows Security Health Service.exe (PID: 5548)
- Windows Defender Security.exe (PID: 7024)
Checks proxy server information
- ._cache_IPRangy.exe (PID: 6884)
- Synaptics.exe (PID: 6784)
- WerFault.exe (PID: 2032)
- Windows Defender Security.exe (PID: 2264)
- Windows Update.exe (PID: 2608)
- Windows Security Health Service.exe (PID: 5548)
- Windows Defender Security.exe (PID: 7024)
Reads CPU info
- ._cache_IPRangy.exe (PID: 6884)
Reads the software policy settings
- ._cache_IPRangy.exe (PID: 6884)
- WerFault.exe (PID: 2032)
- Windows Defender Security.exe (PID: 2264)
- Synaptics.exe (PID: 6784)
Reads Environment values
- ._cache_IPRangy.exe (PID: 6884)
- Windows Defender Security.exe (PID: 2264)
- Windows Update.exe (PID: 2608)
- Windows Security Health Service.exe (PID: 5548)
- Windows Defender Security.exe (PID: 7024)
Attempting to use instant messaging service
- svchost.exe (PID: 2256)
- ._cache_IPRangy.exe (PID: 6884)
Creates files or folders in the user directory
- ._cache_RDP Brute_Cracked.exe (PID: 3812)
- Windows Update.exe (PID: 6856)
- Windows Defender Security.exe (PID: 2264)
- Windows Update.exe (PID: 2608)
- WerFault.exe (PID: 2032)
- Synaptics.exe (PID: 6784)
- Windows Security Health Service.exe (PID: 5548)
Create files in a temporary directory
- Synaptics.exe (PID: 6784)
- Windows Update.exe (PID: 2608)
- Windows Defender Security.exe (PID: 2264)
Changes the display of characters in the console
- chcp.com (PID: 4708)
- chcp.com (PID: 6940)
.NET Reactor protector has been detected
- Windows Defender Security.exe (PID: 7024)
- Windows Defender Security.exe (PID: 1128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(5548) Windows Security Health Service.exe
Version2.1.0.0
C2 (2)23.105.131.187:7812
Sub_DirSubDir
Install_NameWindows Security Health Service.exe
MutexVNM_MUTEX_Yv6S9FB2pcVgrrmUN6
StartupWindows Update
Tagkgf6
LogDirLogs
Signature
Certificate
(PID) Process(7024) Windows Defender Security.exe
Version2.1.0.0
C2 (2)23.105.131.187:7812
Sub_DirSubDir
Install_NameWindows Defender Security.exe
MutexVNM_MUTEX_NOLy9wmTFSi1F4L2HO
StartupWindows Security
Tagkgf5
LogDirLogs
Signature
Certificate
(PID) Process(1164) Windows Update.exe
Version2.1.0.0
C2 (2)23.105.131.187:7812
Sub_DirSubDir
Install_NameWindows Security Health Service.exe
MutexVNM_MUTEX_Yv6S9FB2pcVgrrmUN6
StartupWindows Update
Tagkgf6
LogDirLogs
Signature
Certificate
(PID) Process(1128) Windows Defender Security.exe
Version2.1.0.0
C2 (2)23.105.131.187:7812
Sub_DirSubDir
Install_NameWindows Defender Security.exe
MutexVNM_MUTEX_NOLy9wmTFSi1F4L2HO
StartupWindows Security
Tagkgf5
LogDirLogs
Signature
Certificate
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:08:15 08:16:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | RDP Stealer V2/ |
Total processes
171
Monitored processes
33
Malicious processes
16
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1128 | "C:\Users\admin\AppData\Roaming\Windows Defender Security.exe" | C:\Users\admin\AppData\Roaming\Windows Defender Security.exe | Windows Defender Security.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Defender Security Version: 10.0.17763.0 Modules
Quasar(PID) Process(1128) Windows Defender Security.exe Version2.1.0.0 C2 (2)23.105.131.187:7812 Sub_DirSubDir Install_NameWindows Defender Security.exe MutexVNM_MUTEX_NOLy9wmTFSi1F4L2HO StartupWindows Security Tagkgf5 LogDirLogs Signature Certificate | |||||||||||||||
| 1164 | "C:\Users\admin\AppData\Roaming\Windows Update.exe" | C:\Users\admin\AppData\Roaming\Windows Update.exe | Windows Update.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Update Version: 10.0.17763.0 Modules
Quasar(PID) Process(1164) Windows Update.exe Version2.1.0.0 C2 (2)23.105.131.187:7812 Sub_DirSubDir Install_NameWindows Security Health Service.exe MutexVNM_MUTEX_Yv6S9FB2pcVgrrmUN6 StartupWindows Update Tagkgf6 LogDirLogs Signature Certificate | |||||||||||||||
| 2016 | "C:\Users\admin\AppData\Roaming\RDP Brute_Cracked.exe" | C:\Users\admin\AppData\Roaming\RDP Brute_Cracked.exe | ._cache_RDP Brute_Cracked.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2032 | C:\WINDOWS\system32\WerFault.exe -u -p 2016 -s 780 | C:\Windows\System32\WerFault.exe | RDP Brute_Cracked.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2264 | "C:\Users\admin\AppData\Roaming\Windows Defender Security.exe" | C:\Users\admin\AppData\Roaming\Windows Defender Security.exe | Windows Defender Security.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Defender Security Exit code: 0 Version: 10.0.17763.0 Modules
| |||||||||||||||
| 2608 | "C:\Users\admin\AppData\Roaming\Windows Update.exe" | C:\Users\admin\AppData\Roaming\Windows Update.exe | Windows Update.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Update Exit code: 0 Version: 10.0.17763.0 Modules
| |||||||||||||||
| 2728 | ping -n 10 localhost | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2876 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\uBkxA8oMzKmN.bat" " | C:\Windows\SysWOW64\cmd.exe | — | Windows Defender Security.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3256 | "C:\Users\admin\AppData\Roaming\Windows Defender Security.exe" | C:\Users\admin\AppData\Roaming\Windows Defender Security.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Defender Security Exit code: 0 Version: 10.0.17763.0 Modules
| |||||||||||||||
Total events
35 233
Read events
35 092
Write events
141
Delete events
0
Modification events
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RatDroid.zip | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
21
Suspicious files
12
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6668.21631\RDP_BRUTE_CRACKED BY SHADMANEGI\Result\Check\BadRDP (Vista+).txt | text | |
MD5:0CADBCEAACB156D3BDC9B2CFED8F174D | SHA256:29AE36741644510185167000FFCDB0435141B8176CD89665E94DE6DA3F888AED | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6668.21631\RDP_BRUTE_CRACKED BY SHADMANEGI\Result\Check\GoodRDP (XP-2003).txt | text | |
MD5:892B1EF03106ED857B123D78EA2505F0 | SHA256:0046D4F7E49C00A650872DE3A90067998959E8D6B942D5C28F743BC87EBDC42B | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6668.21631\RDP_BRUTE_CRACKED BY SHADMANEGI\Result\ErrorRDP.txt | text | |
MD5:BC219549AE9EDF5DA3F52E88D5E85331 | SHA256:619D5B993C0AC247E7008084220B310FD3264B75E6357A46CB76D818414D7FD3 | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6668.21631\RDP_BRUTE_CRACKED BY SHADMANEGI\Result\Check\BadRDP (XP-2003).txt | text | |
MD5:F602846D915696B3421D2872706E12C2 | SHA256:CB2350787B4C47DD2ECF37BFD25FF6560BF604266E1DE9BEDA69F1DB5964B76C | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6668.21631\RDP_BRUTE_CRACKED BY SHADMANEGI\Result\GoodRDP (Vista+).txt | text | |
MD5:2C8299830679CC80DF7751E6B79ACB77 | SHA256:7D128008709AD5B7D6573C3EEFA8FC30D15B979456F05496A7D0FA7CFD03648A | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6668.21631\RDP_BRUTE_CRACKED BY SHADMANEGI\Result\Check\ErrorRDP.txt | text | |
MD5:ABFBFE836F178E1D24CBD412C7DA20E6 | SHA256:C10AD002F17FD5ABFD69F24D07E23B6D3B238A8484AD38D10EF273EF2AE16376 | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6668.21631\RDP_BRUTE_CRACKED BY SHADMANEGI\Result\Check\GoodRDP (Vista+).txt | text | |
MD5:DEA6AEF31EA9A12C37032941E09E53EB | SHA256:FE28EC26D46CC0F3C6A40DFC474C29FBFC38B0B0A488925AAB4A5F29D96CF3B9 | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6668.21631\rdp\rdp\Best User.txt | text | |
MD5:27074B495E7CCD337F233DA8252E056F | SHA256:40CCB3B9E50C641344D27E8CE398223795D6940383693D74DF1FF893C02363F6 | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6668.21631\rdp\rdp\IPRangy.exe | executable | |
MD5:951480C5C3CB471E687D4D42B9EBBABC | SHA256:BC581A590834EF23238768DCC2146635BCA68B20C36E43FCBDFB8098D6DD725D | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6668.21631\RDP_BRUTE_CRACKED BY SHADMANEGI\Ude.dll | executable | |
MD5:9F96AEE193D53A925D18B2769E7958E0 | SHA256:5A120F43A4B9E7A0D811A680EEAB34948D1A7EDA4DCC988AA203EEFCC33043B6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
56
DNS requests
28
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2264 | Windows Defender Security.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | shared |
7048 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3104 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7024 | Windows Defender Security.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | shared |
5548 | Windows Security Health Service.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | shared |
2608 | Windows Update.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | shared |
6784 | Synaptics.exe | GET | 200 | 69.42.215.252:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | — | — | whitelisted |
6784 | Synaptics.exe | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
6784 | Synaptics.exe | GET | 200 | 142.250.186.35:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCnNXjqMmu3chAgO%2BmpN88J | unknown | — | — | whitelisted |
6784 | Synaptics.exe | GET | 200 | 142.250.186.35:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEHGN%2BKTRSIp4CcztJxB9gYQ%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
608 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3208 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
608 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2324 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2324 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
api.ipify.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6884 | ._cache_IPRangy.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to Abused Domain *.mooo.com |
2256 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
6884 | ._cache_IPRangy.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
2256 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
6884 | ._cache_IPRangy.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2256 | svchost.exe | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |
3 ETPRO signatures available at the full report