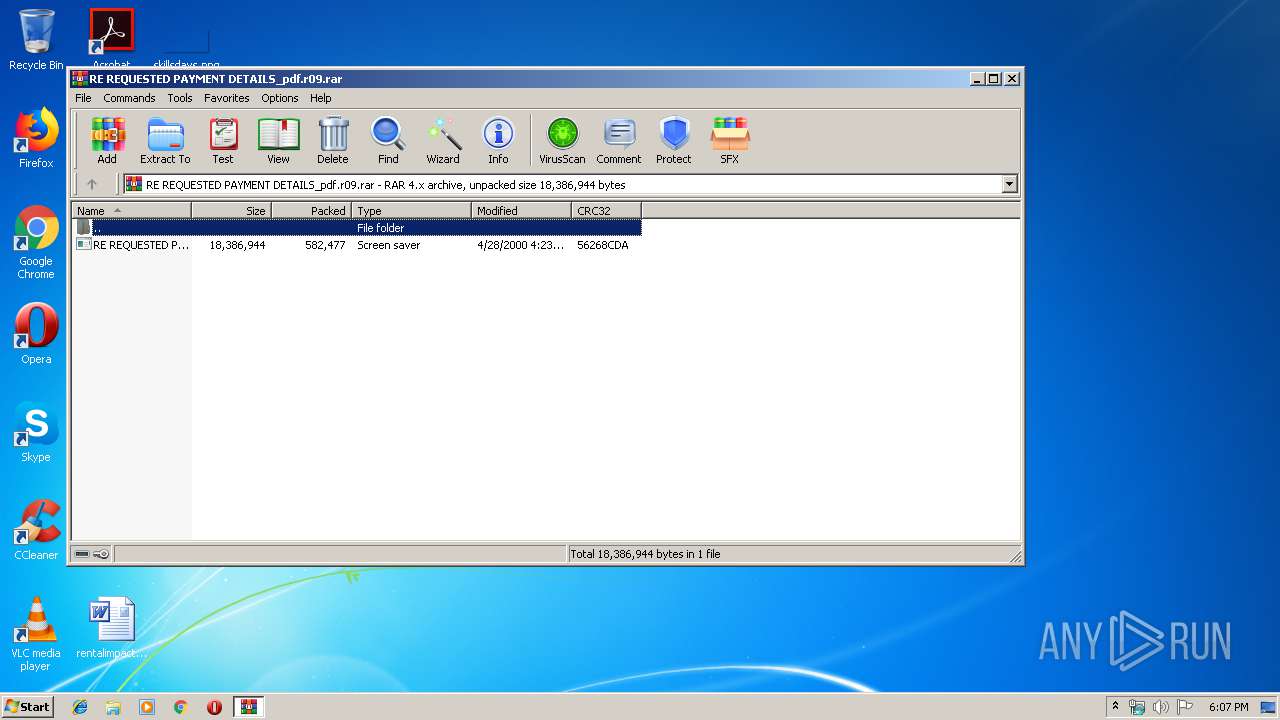
| File name: | RE REQUESTED PAYMENT DETAILS_pdf.r09 |
| Full analysis: | https://app.any.run/tasks/a77491fb-8ea4-41f8-be18-db437a6a5fc0 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | December 02, 2019, 18:06:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 5F611299062543F07CAE41ED48934FA7 |
| SHA1: | E9516430E5177AA2615D3983237FFEAAAA0CD242 |
| SHA256: | 1DEDCE8398CBFE0D6927AD4EC3DDE805F7A34FF2075FD214CE75B0D86F30DFAF |
| SSDEEP: | 12288:wtybIrUM3qIXtIJIGGO78coPW/JxwBUNah1qWxeB1WjsmfZRUs9oKo/NVQRZnRu:icIrl3qIXtrQVo+BxYUNah1qcenQZz94 |
MALICIOUS
Application was dropped or rewritten from another process
- RE REQUESTED PAYMENT DETAILS_pdf.scr (PID: 3148)
- RE REQUESTED PAYMENT DETAILS_pdf.scr (PID: 1036)
- Windows Update.exe (PID: 2148)
- Windows Update.exe (PID: 3980)
- Windows Update.exe (PID: 1944)
Detected Hawkeye Keylogger
- Windows Update.exe (PID: 1944)
Changes the autorun value in the registry
- Windows Update.exe (PID: 1944)
Actions looks like stealing of personal data
- vbc.exe (PID: 3692)
SUSPICIOUS
Executable content was dropped or overwritten
- RE REQUESTED PAYMENT DETAILS_pdf.scr (PID: 1036)
- WinRAR.exe (PID: 2236)
- Windows Update.exe (PID: 1944)
Starts application with an unusual extension
- RE REQUESTED PAYMENT DETAILS_pdf.scr (PID: 3148)
Application launched itself
- RE REQUESTED PAYMENT DETAILS_pdf.scr (PID: 3148)
- Windows Update.exe (PID: 3980)
Creates files in the user directory
- RE REQUESTED PAYMENT DETAILS_pdf.scr (PID: 1036)
- Windows Update.exe (PID: 1944)
Starts itself from another location
- RE REQUESTED PAYMENT DETAILS_pdf.scr (PID: 1036)
Checks for external IP
- Windows Update.exe (PID: 1944)
Executes scripts
- Windows Update.exe (PID: 1944)
Loads DLL from Mozilla Firefox
- vbc.exe (PID: 1928)
INFO
Manual execution by user
- RE REQUESTED PAYMENT DETAILS_pdf.scr (PID: 3148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 582534 |
|---|---|
| UncompressedSize: | 18386944 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2000:04:28 16:23:20 |
| PackingMethod: | Normal |
| ArchivedFileName: | RE REQUESTED PAYMENT DETAILS_pdf.scr |
Total processes
45
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1036 | "C:\Users\admin\Desktop\RE REQUESTED PAYMENT DETAILS_pdf.scr" /S | C:\Users\admin\Desktop\RE REQUESTED PAYMENT DETAILS_pdf.scr | RE REQUESTED PAYMENT DETAILS_pdf.scr | ||||||||||||
User: admin Company: aSUS Integrity Level: MEDIUM Exit code: 0 Version: 5.00 Modules
| |||||||||||||||
| 1928 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holderwb.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | — | Windows Update.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 1944 | "C:\Users\admin\AppData\Roaming\Windows Update.exe" | C:\Users\admin\AppData\Roaming\Windows Update.exe | Windows Update.exe | ||||||||||||
User: admin Company: aSUS Integrity Level: HIGH Exit code: 0 Version: 5.00 Modules
| |||||||||||||||
| 2148 | "C:\Users\admin\AppData\Roaming\Windows Update.exe" | C:\Users\admin\AppData\Roaming\Windows Update.exe | — | RE REQUESTED PAYMENT DETAILS_pdf.scr | |||||||||||
User: admin Company: aSUS Integrity Level: MEDIUM Exit code: 3221226540 Version: 5.00 Modules
| |||||||||||||||
| 2236 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\RE REQUESTED PAYMENT DETAILS_pdf.r09.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3148 | "C:\Users\admin\Desktop\RE REQUESTED PAYMENT DETAILS_pdf.scr" /S | C:\Users\admin\Desktop\RE REQUESTED PAYMENT DETAILS_pdf.scr | — | explorer.exe | |||||||||||
User: admin Company: aSUS Integrity Level: MEDIUM Exit code: 0 Version: 5.00 Modules
| |||||||||||||||
| 3692 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holdermail.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | Windows Update.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\AppData\Roaming\Windows Update.exe" | C:\Users\admin\AppData\Roaming\Windows Update.exe | RE REQUESTED PAYMENT DETAILS_pdf.scr | ||||||||||||
User: admin Company: aSUS Integrity Level: HIGH Exit code: 0 Version: 5.00 Modules
| |||||||||||||||
Total events
927
Read events
886
Write events
41
Delete events
0
Modification events
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RE REQUESTED PAYMENT DETAILS_pdf.r09.rar | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2236) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @shell32,-10162 |
Value: Screen saver | |||
Executable files
3
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3692 | vbc.exe | C:\Users\admin\AppData\Local\Temp\holdermail.txt | — | |
MD5:— | SHA256:— | |||
| 1928 | vbc.exe | C:\Users\admin\AppData\Local\Temp\holderwb.txt | — | |
MD5:— | SHA256:— | |||
| 1036 | RE REQUESTED PAYMENT DETAILS_pdf.scr | C:\Users\admin\AppData\Roaming\Windows Update.exe | executable | |
MD5:— | SHA256:— | |||
| 2236 | WinRAR.exe | C:\Users\admin\Desktop\RE REQUESTED PAYMENT DETAILS_pdf.scr | executable | |
MD5:— | SHA256:— | |||
| 3148 | RE REQUESTED PAYMENT DETAILS_pdf.scr | C:\Users\admin\AppData\Local\Temp\~DF1BD1BD5C369D3816.TMP | binary | |
MD5:— | SHA256:— | |||
| 1036 | RE REQUESTED PAYMENT DETAILS_pdf.scr | C:\Users\admin\AppData\Local\Temp\SysInfo.txt | text | |
MD5:— | SHA256:— | |||
| 1944 | Windows Update.exe | C:\Users\admin\AppData\Roaming\pidloc.txt | text | |
MD5:E9FAEE87A060C806E7234779CFF7B480 | SHA256:CE744D98EF602BA5FE207C4C064DA0075A1BB9BF303E53CA86AF1025AD3AFBF3 | |||
| 1944 | Windows Update.exe | C:\Users\admin\AppData\Roaming\WindowsUpdate.exe | executable | |
MD5:— | SHA256:— | |||
| 3980 | Windows Update.exe | C:\Users\admin\AppData\Local\Temp\~DF356D062CE9906871.TMP | binary | |
MD5:— | SHA256:— | |||
| 1944 | Windows Update.exe | C:\Users\admin\AppData\Roaming\pid.txt | text | |
MD5:6F2688A5FCE7D48C8D19762B88C32C3B | SHA256:F513A0AA4F8F39744C6FDDF2B5EB18CC1EAC55CA866A1B243D835362A023F243 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
4
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1944 | Windows Update.exe | GET | 301 | 104.16.154.36:80 | http://whatismyipaddress.com/ | US | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1944 | Windows Update.exe | 104.16.154.36:80 | whatismyipaddress.com | Cloudflare Inc | US | shared |
1944 | Windows Update.exe | 104.16.154.36:443 | whatismyipaddress.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
whatismyipaddress.com |
| shared |
mail.vensoft.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1944 | Windows Update.exe | Potential Corporate Privacy Violation | ET POLICY Known External IP Lookup Service Domain in SNI |
1944 | Windows Update.exe | A Network Trojan was detected | SPYWARE [PTsecurity] HawkEye / Predator Pain (IP Chck) |
2 ETPRO signatures available at the full report