| File name: | BANDICUT.msi |
| Full analysis: | https://app.any.run/tasks/77c42a11-0424-4e80-87ea-7bcb7f0dde52 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | October 02, 2024, 13:56:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
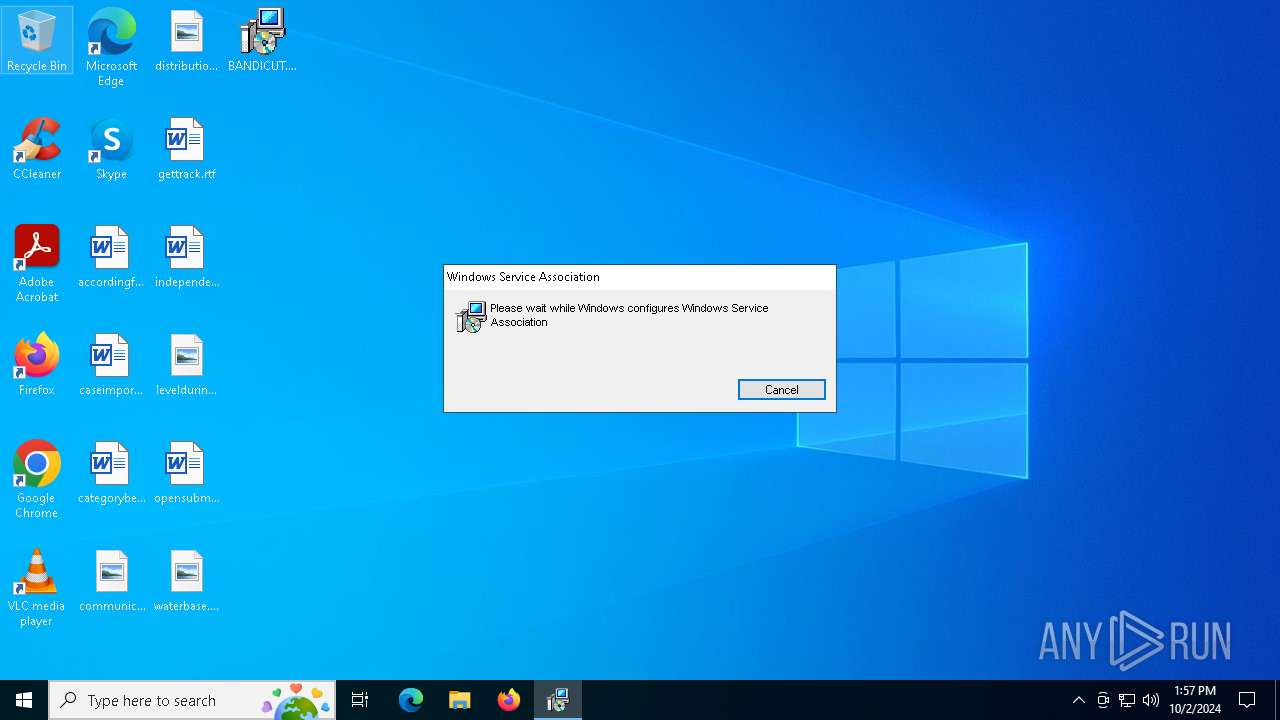
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Sep 18 14:06:51 2020, Security: 0, Code page: 1252, Revision Number: {4203B04D-806D-4EBE-BCFF-E19C0C1E195F}, Number of Words: 2, Subject: Windows Service Association, Author: Microsoft, Name of Creating Application: Windows Service Association, Template: ;1033, Comments: This installer database contains the logic and data required to install Windows Service Association., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | 087D510F4D69F6FAA479E4919F51A175 |
| SHA1: | 084C49D7C83B257AACF8C94B28B992C326A2AD09 |
| SHA256: | 1DD7892458EAB123C341452AFF6F4D817F290EFC7F8C97B76BDB78E1E1FCF8D2 |
| SSDEEP: | 98304:B9IOolfYojhBef1RmHW5LIOmT+1jto4694/QT3IkBvbLn3oYkbCLaCfElqQh4Caz:z+qj9SjM |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 2420)
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 1220)
AMADEY has been detected (SURICATA)
- dropbox.exe (PID: 6664)
Connects to the CnC server
- dropbox.exe (PID: 6664)
AMADEY has been detected (YARA)
- dropbox.exe (PID: 6664)
SUSPICIOUS
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 1220)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2808)
Executable content was dropped or overwritten
- powershell.exe (PID: 2420)
- CapCut_installer.exe (PID: 6460)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 1220)
The process executes Powershell scripts
- msiexec.exe (PID: 1220)
Likely accesses (executes) a file from the Public directory
- CapCut_installer.exe (PID: 6460)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 1220)
- dropbox.exe (PID: 6664)
Malware-specific behavior (creating "System.dll" in Temp)
- CapCut_installer.exe (PID: 6460)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 6216)
Connects to the server without a host name
- dropbox.exe (PID: 6664)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2256)
Contacting a server suspected of hosting an CnC
- dropbox.exe (PID: 6664)
Application launched itself
- dropbox.exe (PID: 6664)
Checks Windows Trust Settings
- msiexec.exe (PID: 2808)
INFO
Reads the software policy settings
- msiexec.exe (PID: 2340)
- msiexec.exe (PID: 2808)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2808)
Checks supported languages
- msiexec.exe (PID: 2808)
- msiexec.exe (PID: 6216)
Reads Environment values
- msiexec.exe (PID: 6216)
Reads the computer name
- msiexec.exe (PID: 2808)
- msiexec.exe (PID: 6216)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2808)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2020:09:18 14:06:51 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {4203B04D-806D-4EBE-BCFF-E19C0C1E195F} |
| Words: | 2 |
| Subject: | Windows Service Association |
| Author: | Microsoft |
| LastModifiedBy: | - |
| Software: | Windows Service Association |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install Windows Service Association. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
130
Monitored processes
14
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1220 | C:\Windows\syswow64\MsiExec.exe -Embedding 961AB263D332E3221313854722761A18 E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1372 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2340 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\Desktop\BANDICUT.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss7D3F.ps1" -propFile "C:\Users\admin\AppData\Local\Temp\msi7D2C.txt" -scriptFile "C:\Users\admin\AppData\Local\Temp\scr7D2D.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\Temp\scr7D2E.txt" -propSep " :<->: " -testPrefix "_testValue." | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2808 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4080 | "C:\Windows\SysWOW64\cmd.exe" /c "C:\Program Files (x86)\Dropbox\Update\dropbox.exe" | C:\Windows\SysWOW64\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6216 | C:\Windows\syswow64\MsiExec.exe -Embedding 0A05D8B44529B9620C72D0BCFDC58651 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6460 | "C:\Users\Public\Documents\capcut_installer.exe" | C:\Users\Public\Documents\CapCut_installer.exe | powershell.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Modules
| |||||||||||||||
Total events
20 077
Read events
20 047
Write events
21
Delete events
9
Modification events
| (PID) Process: | (2808) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: F80A000071E016F7D214DB01 | |||
| (PID) Process: | (2808) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 8235DC7FC94D3263D5CD273E82492F8FF7E17DF03004AED4552E280530EA811C | |||
| (PID) Process: | (2808) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (2808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\3f7510.rbs |
Value: 31134930 | |||
| (PID) Process: | (2808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\3f7510.rbsLow |
Value: | |||
| (PID) Process: | (2808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\2D208A7AC4793F146B25264174A9500B |
| Operation: | write | Name: | A881E280AF7676D429E08C0512D56BCE |
Value: C:\Program Files (x86)\Microsoft\Windows Service Association\ | |||
| (PID) Process: | (2808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\6A803C3591405434F9108DE8AA427B1F |
| Operation: | write | Name: | A881E280AF7676D429E08C0512D56BCE |
Value: 02:\Software\Microsoft\Windows Service Association\Version | |||
| (PID) Process: | (2808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\348656E90AF6BE54485486DEE1BCB3A1 |
| Operation: | write | Name: | A881E280AF7676D429E08C0512D56BCE |
Value: C:\Users\Public\Documents\Dropbox.exe | |||
| (PID) Process: | (2808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\A893E4A58599D724D8D2CB9EA85EF280 |
| Operation: | write | Name: | A881E280AF7676D429E08C0512D56BCE |
Value: C:\Users\Public\Documents\CapCut_installer.exe | |||
Executable files
16
Suspicious files
15
Text files
16
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1220 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\msi7D2C.txt | — | |
MD5:— | SHA256:— | |||
| 1220 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scr7D2D.ps1 | — | |
MD5:— | SHA256:— | |||
| 1220 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scr7D2E.txt | — | |
MD5:— | SHA256:— | |||
| 1220 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pss7D3F.ps1 | — | |
MD5:— | SHA256:— | |||
| 2808 | msiexec.exe | C:\Windows\Installer\MSI77DD.tmp | executable | |
MD5:5788EFA607D26332D6D7F5E6A1F6BD6F | SHA256:9FC2608C9E5EF5A88DD91C82660FA297144BA6BBF4602140D638DE7233A4625D | |||
| 2808 | msiexec.exe | C:\Windows\Installer\MSI7955.tmp | executable | |
MD5:5788EFA607D26332D6D7F5E6A1F6BD6F | SHA256:9FC2608C9E5EF5A88DD91C82660FA297144BA6BBF4602140D638DE7233A4625D | |||
| 2808 | msiexec.exe | C:\Windows\Installer\3f750e.msi | executable | |
MD5:087D510F4D69F6FAA479E4919F51A175 | SHA256:1DD7892458EAB123C341452AFF6F4D817F290EFC7F8C97B76BDB78E1E1FCF8D2 | |||
| 2808 | msiexec.exe | C:\Windows\Installer\MSI7B0D.tmp | binary | |
MD5:BE01224E859CA410C69F244B0BDB1B59 | SHA256:E75E3D0FC1B933D1A25F5816571EE3CDA8D747EA752BA355DA40FFB213C00B81 | |||
| 2808 | msiexec.exe | C:\Windows\Installer\MSI7C85.tmp | executable | |
MD5:637C0F8F44F26EF0C736B8BBD0222334 | SHA256:57DEA716197079FAD873B65AC02A6E002A43FE01202987541AB5295C0F69D28A | |||
| 2808 | msiexec.exe | C:\Users\Public\Documents\goopdate.dll | executable | |
MD5:F10F2B27218C7364F72FA50DA1AF5E2C | SHA256:90D879656C90804E5E9329E8A796E51F1C70C10FFE2A451E261E2E1E592CC1E5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
45
DNS requests
11
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6664 | dropbox.exe | POST | 200 | 45.202.35.101:80 | http://45.202.35.101/pLQvfD4d/index.php | unknown | — | — | malicious |
— | — | GET | — | 2.16.10.175:443 | https://lf16-capcut.faceulv.com/obj/capcutpc-packages-sg/packages/CapCut_4_6_0_1754_capcutpc_0_creatortool.exe | unknown | — | — | unknown |
6664 | dropbox.exe | POST | 200 | 45.202.35.101:80 | http://45.202.35.101/pLQvfD4d/index.php | unknown | — | — | malicious |
— | — | GET | — | 2.16.10.175:443 | https://lf16-capcut.faceulv.com/obj/capcutpc-packages-sg/packages/CapCut_4_6_0_1754_capcutpc_0_creatortool.exe | unknown | — | — | unknown |
— | — | GET | — | 2.16.10.175:443 | https://lf16-capcut.faceulv.com/obj/capcutpc-packages-sg/packages/CapCut_4_6_0_1754_capcutpc_0_creatortool.exe | unknown | — | — | unknown |
— | — | GET | 200 | 2.16.1.187:443 | https://editor-api-sg.capcut.com/service/settings/v3/?app=1&aid=562354&arch_info=x86_64&device_id=2182455761&device_platform=windows&from_aid=562354&from_channel=capcutpc_0&from_version=0.0.0&local_info=en_US&version_code=0.0.0 | unknown | tss | 2.04 Kb | unknown |
— | — | POST | 200 | 2.19.198.216:443 | https://maliva-mcs.byteoversea.com/v1/json | unknown | binary | 14 b | whitelisted |
— | — | GET | 200 | 23.216.77.71:443 | https://sf16-va.tiktokcdn.com/obj/eden-va2/JW-abJwhJ/ljhwZthlaukjlkulzlp/installer/pic/v1/keyframe/keyframe_en.png | unknown | image | 593 Kb | whitelisted |
— | — | GET | 200 | 23.216.77.71:443 | https://sf16-va.tiktokcdn.com/obj/eden-va2/JW-abJwhJ/ljhwZthlaukjlkulzlp/installer/pic/v1/intelligent_subtitles/intelligent_subtitles_en.png | unknown | image | 504 Kb | whitelisted |
— | — | GET | 200 | 23.216.77.71:443 | https://sf16-va.tiktokcdn.com/obj/eden-va2/JW-abJwhJ/ljhwZthlaukjlkulzlp/installer/pic/v1/speech_synthesis/speech_synthesis_en.png | unknown | image | 457 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5000 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5000 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6460 | CapCut_installer.exe | 2.16.1.187:443 | editor-api-sg.capcut.com | Akamai International B.V. | NL | whitelisted |
6460 | CapCut_installer.exe | 23.32.238.82:443 | maliva-mcs.byteoversea.com | Akamai International B.V. | DE | whitelisted |
6460 | CapCut_installer.exe | 23.32.238.58:443 | maliva-mcs.byteoversea.com | Akamai International B.V. | DE | whitelisted |
6460 | CapCut_installer.exe | 23.216.77.71:443 | sf16-va.tiktokcdn.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
editor-api-sg.capcut.com |
| unknown |
maliva-mcs.byteoversea.com |
| whitelisted |
sf16-va.tiktokcdn.com |
| whitelisted |
sgali-mcs.byteoversea.com |
| whitelisted |
lf16-capcut.faceulv.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6664 | dropbox.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 5 |
6664 | dropbox.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
5 ETPRO signatures available at the full report