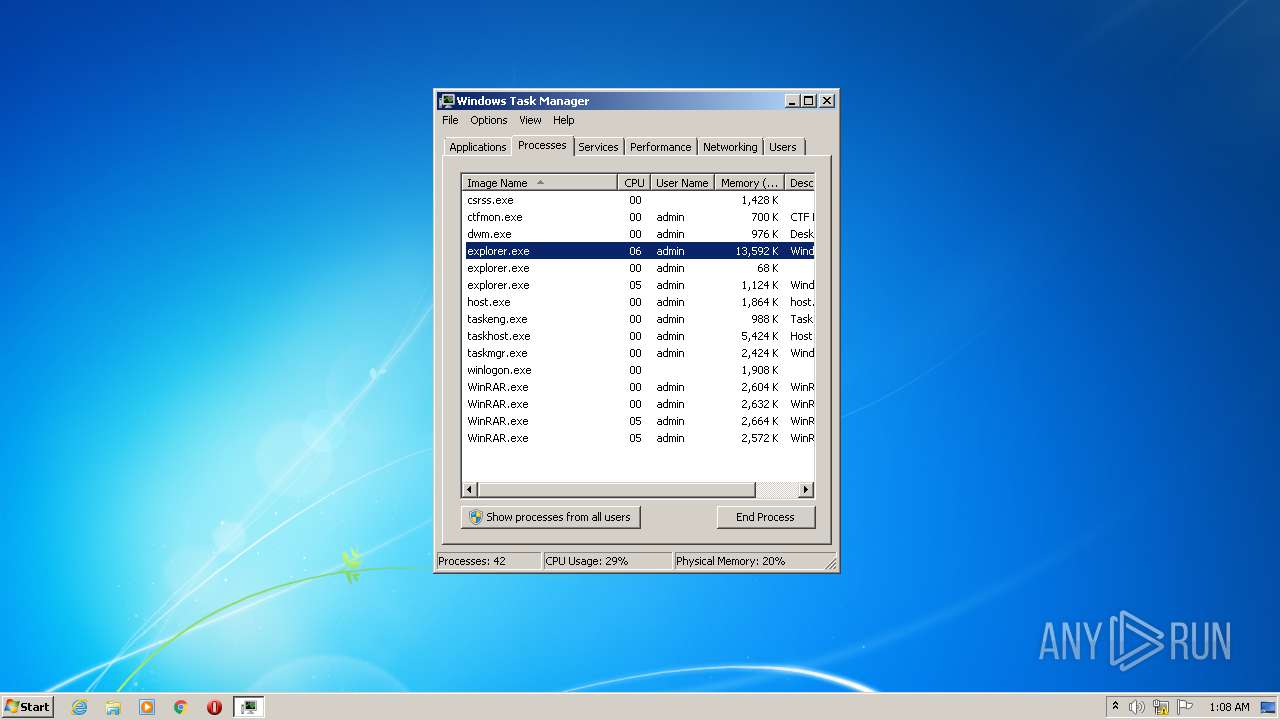
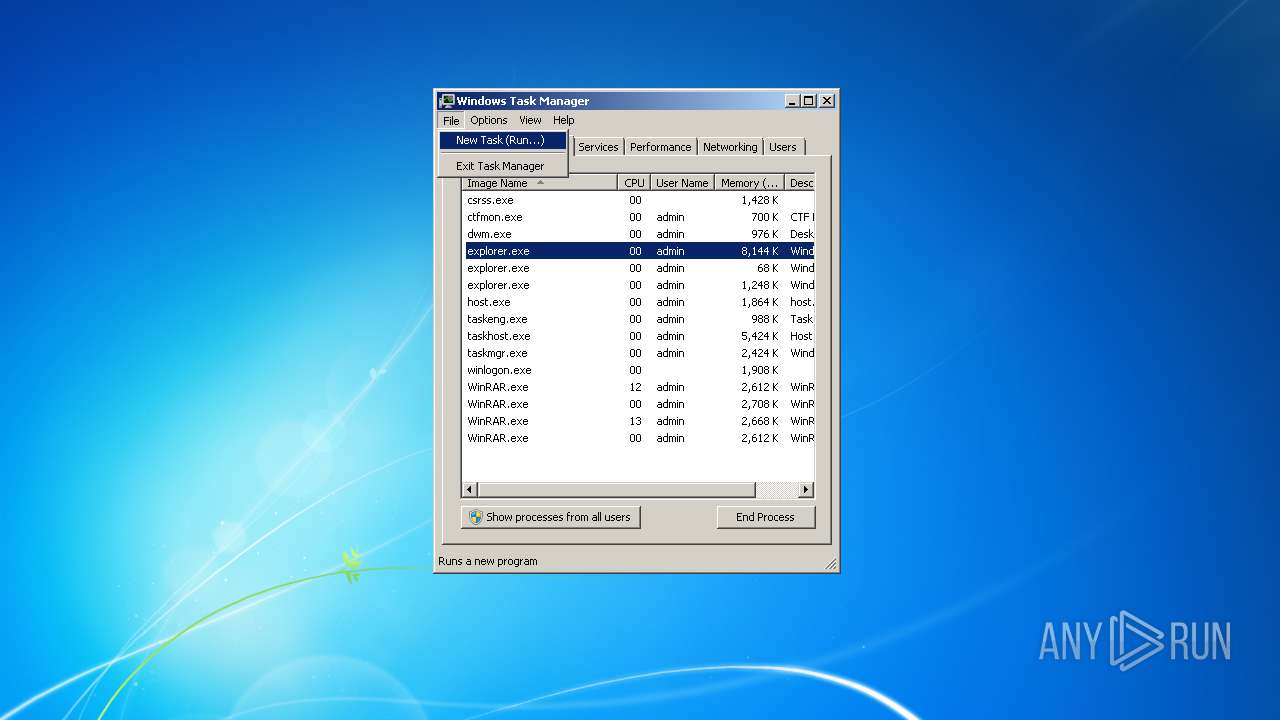
| File name: | TestFile.exe |
| Full analysis: | https://app.any.run/tasks/215fb694-b81c-4693-a9ea-1f9a6d1845a3 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | February 02, 2021, 01:04:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 60FABD1A2509B59831876D5E2AA71A6B |
| SHA1: | 8B91F3C4F721CB04CC4974FC91056F397AE78FAA |
| SHA256: | 1DACDC296FD6EF6BA817B184CCE9901901C47C01D849ADFA4222BFABFED61838 |
| SSDEEP: | 3072:BMhIBKH7j7DzQi7y5bvl4YAbdY9KWvwn7XHMzqEOf64CEEl64HBVdGXPKD:BMh5H7j5g54YZKXoxOuEEl64HZAi |
MALICIOUS
Application was dropped or rewritten from another process
- RakhniDecryptor.exe (PID: 3896)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3960)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3684)
Creates files in the user directory
- WinRAR.exe (PID: 3684)
Executed via COM
- explorer.exe (PID: 3304)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3684)
INFO
Reads the hosts file
- chrome.exe (PID: 3960)
- chrome.exe (PID: 2812)
- chrome.exe (PID: 3180)
Manual execution by user
- taskmgr.exe (PID: 2716)
- explorer.exe (PID: 3944)
- explorer.exe (PID: 3556)
- chrome.exe (PID: 3960)
Reads settings of System Certificates
- chrome.exe (PID: 2812)
Application launched itself
- chrome.exe (PID: 3960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (81) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.2) |
| .exe | | | Win32 Executable (generic) (4.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.2) |
| .exe | | | Generic Win/DOS Executable (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:09:17 10:24:25+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 217088 |
| InitializedDataSize: | 16384 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3644e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 17-Sep-2015 08:24:25 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 17-Sep-2015 08:24:25 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00034454 | 0x00035000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.65243 |
.rsrc | 0x00038000 | 0x00002624 | 0x00003000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.53176 |
.reloc | 0x0003C000 | 0x0000000C | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.0164085 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.25755 | 296 | Latin 1 / Western European | Dutch - Netherlands | RT_ICON |
2 | 3.47151 | 1384 | Latin 1 / Western European | Dutch - Netherlands | RT_ICON |
3 | 3.91708 | 744 | Latin 1 / Western European | Dutch - Netherlands | RT_ICON |
4 | 3.91366 | 2216 | Latin 1 / Western European | Dutch - Netherlands | RT_ICON |
MAINICON | 2.64576 | 62 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
97
Monitored processes
52
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 404 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\RakhniDecryptor.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | chrome.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1396 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1056,4264140124124588296,9404740727793981530,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16228204284001015200 --mojo-platform-channel-handle=4060 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1056,4264140124124588296,9404740727793981530,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11143720652170936006 --mojo-platform-channel-handle=504 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1056,4264140124124588296,9404740727793981530,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=14082213879928067469 --mojo-platform-channel-handle=3904 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1056,4264140124124588296,9404740727793981530,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7546909722744111751 --mojo-platform-channel-handle=2348 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,4264140124124588296,9404740727793981530,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=829971383953025260 --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4204 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2232 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\RakhniDecryptor.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | chrome.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,4264140124124588296,9404740727793981530,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5968072969054529148 --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3772 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 1 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2588 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1056,4264140124124588296,9404740727793981530,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6020278366890559553 --mojo-platform-channel-handle=3736 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2608 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3956 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 1 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
3 151
Read events
2 982
Write events
162
Delete events
7
Modification events
| (PID) Process: | (3960) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3960) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3960) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3960) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3960) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2608) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3960-13256701481781250 |
Value: 259 | |||
| (PID) Process: | (3960) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3960) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3960) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (3960) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3960-13256701481781250 |
Value: 259 | |||
Executable files
1
Suspicious files
82
Text files
350
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-6018A52A-F78.pma | — | |
MD5:— | SHA256:— | |||
| 3960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\c9a0611f-2180-4e29-86d5-ea21a12f554c.tmp | — | |
MD5:— | SHA256:— | |||
| 3960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RFf52d.TMP | text | |
MD5:— | SHA256:— | |||
| 3960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RFf58b.TMP | text | |
MD5:— | SHA256:— | |||
| 3960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3960 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFf81b.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
74
DNS requests
38
Threats
30
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
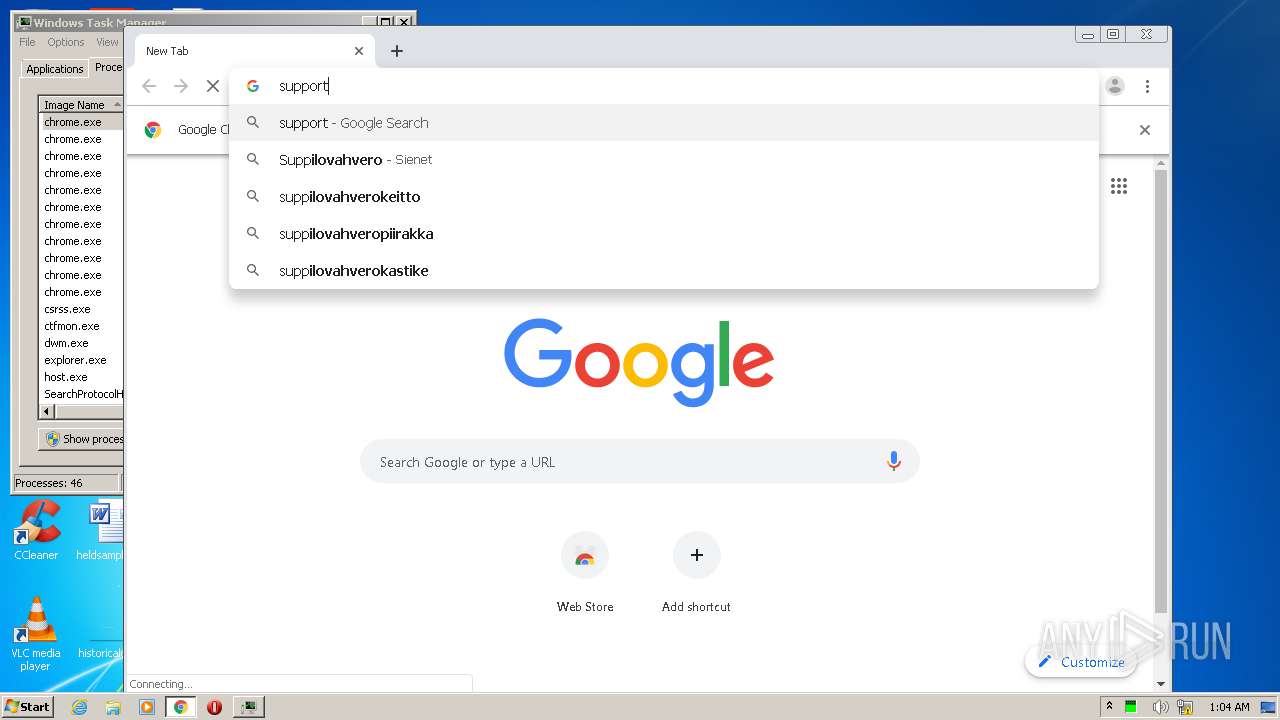
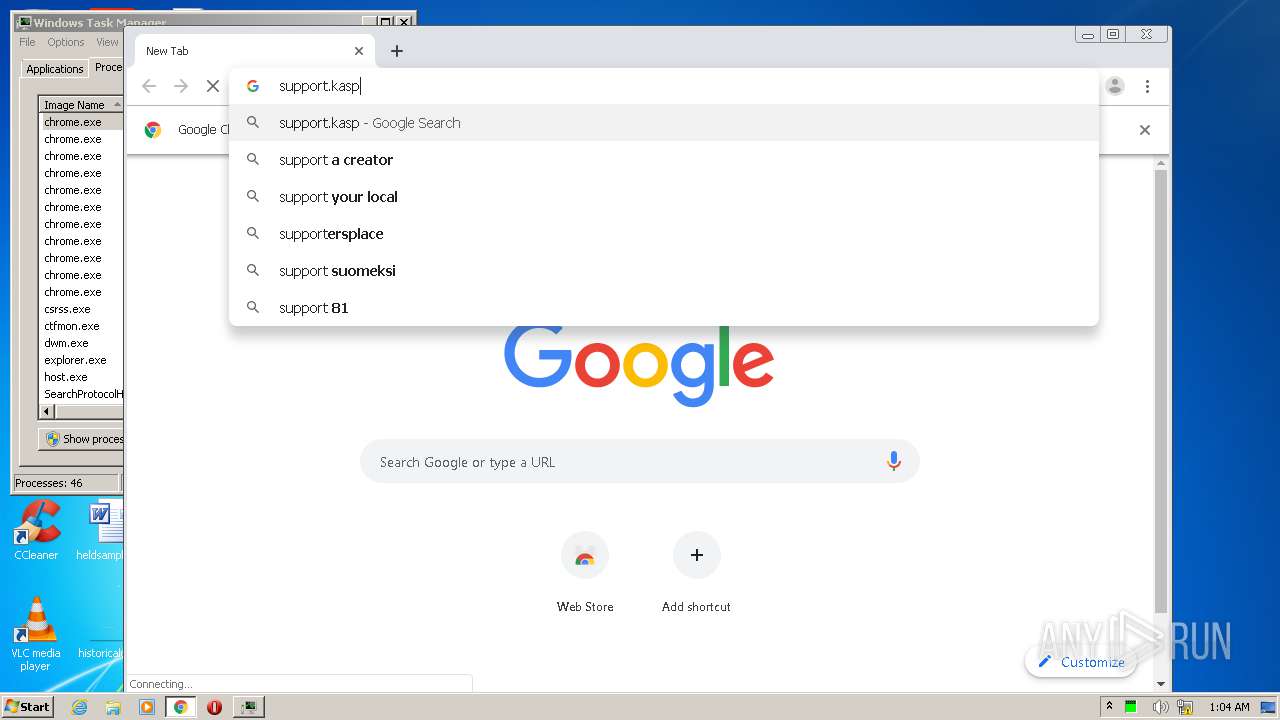
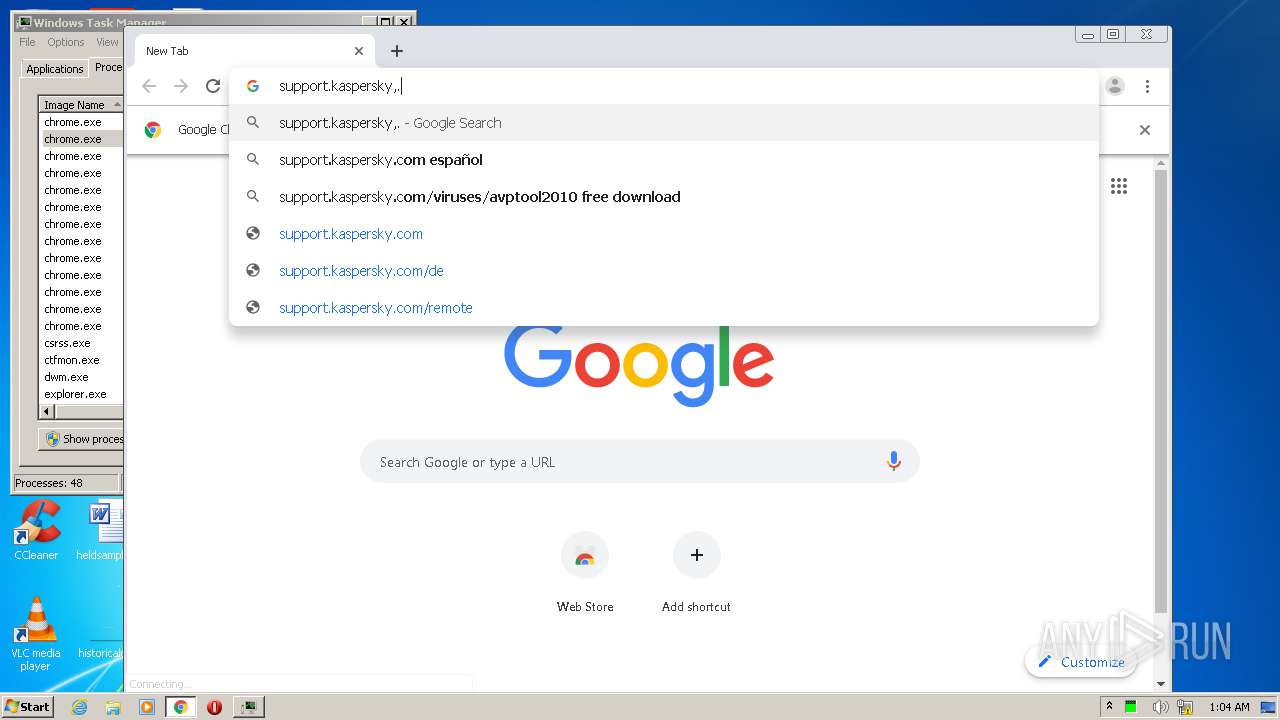
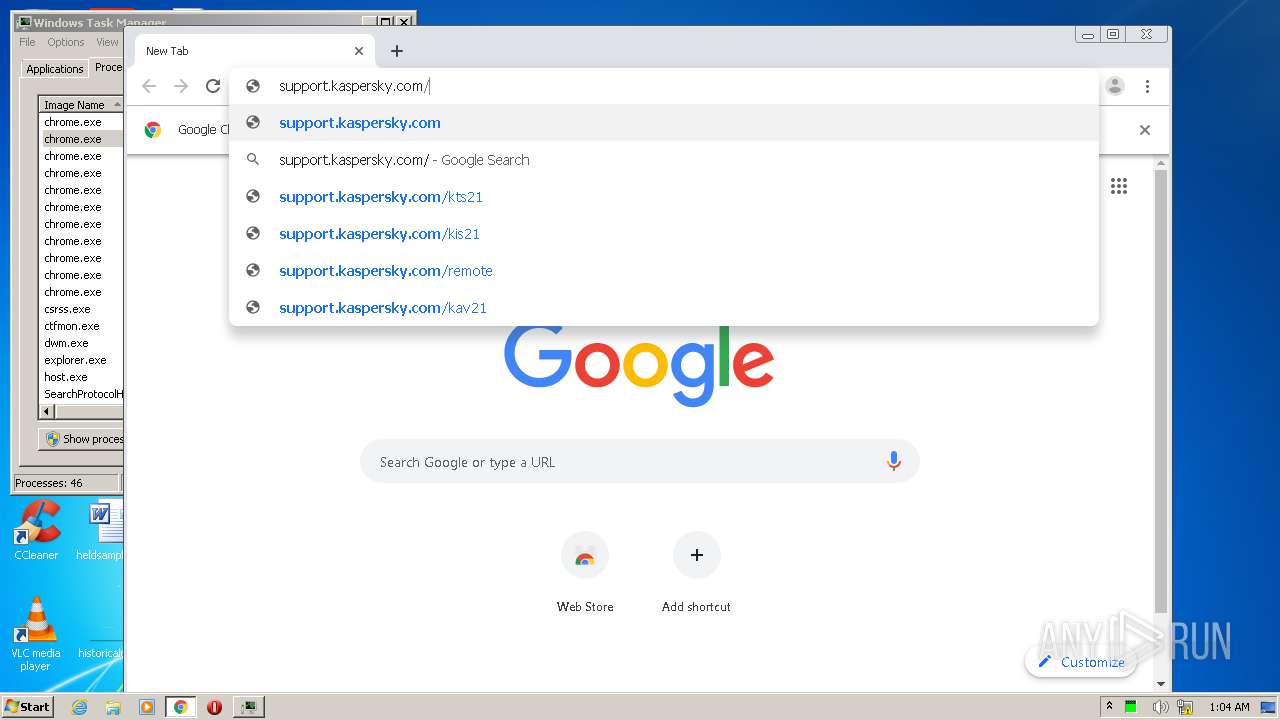
2812 | chrome.exe | GET | 301 | 77.74.178.17:80 | http://support.kaspersky.com/10556 | RU | html | 158 b | whitelisted |
2812 | chrome.exe | GET | 302 | 172.217.18.110:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 520 b | whitelisted |
2812 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAKXB1YM1Knrv%2BJy8eCW2II%3D | US | der | 471 b | whitelisted |
1960 | taskhost.exe | GET | 200 | 66.171.248.178:80 | http://bot.whatismyipaddress.com/ | US | text | 14 b | shared |
2812 | chrome.exe | GET | 200 | 173.194.163.90:80 | http://r4---sn-5go7ynez.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mh=e_&mip=196.244.192.14&mm=28&mn=sn-5go7ynez&ms=nvh&mt=1612227709&mv=u&mvi=4&pl=24&shardbypass=yes | US | crx | 242 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2812 | chrome.exe | 172.217.23.97:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
2812 | chrome.exe | 172.217.18.110:80 | clients2.google.com | Google Inc. | US | whitelisted |
1960 | taskhost.exe | 66.171.248.178:80 | bot.whatismyipaddress.com | Alchemy Communications, Inc. | US | malicious |
2812 | chrome.exe | 216.58.212.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2812 | chrome.exe | 172.217.18.109:443 | accounts.google.com | Google Inc. | US | suspicious |
2812 | chrome.exe | 172.217.23.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2812 | chrome.exe | 142.250.74.195:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2812 | chrome.exe | 142.250.186.174:443 | apis.google.com | Google Inc. | US | whitelisted |
2812 | chrome.exe | 172.217.16.142:443 | ogs.google.com.ua | Google Inc. | US | whitelisted |
2812 | chrome.exe | 142.250.74.206:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bot.whatismyipaddress.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com.ua |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1960 | taskhost.exe | Potential Corporate Privacy Violation | ET TROJAN Possible Chimera Ransomware - Bitmessage Activity |
1960 | taskhost.exe | Misc activity | APP [PTsecurity] CoinWallet |
1960 | taskhost.exe | Potential Corporate Privacy Violation | ET TROJAN Possible Chimera Ransomware - Bitmessage Activity |
1960 | taskhost.exe | Misc activity | APP [PTsecurity] CoinWallet |
1960 | taskhost.exe | Potential Corporate Privacy Violation | ET TROJAN Possible Chimera Ransomware - Bitmessage Activity |
1960 | taskhost.exe | Misc activity | APP [PTsecurity] CoinWallet |
1960 | taskhost.exe | Potential Corporate Privacy Violation | ET TROJAN Possible Chimera Ransomware - Bitmessage Activity |
1960 | taskhost.exe | Misc activity | APP [PTsecurity] CoinWallet |
1960 | taskhost.exe | Potential Corporate Privacy Violation | ET TROJAN Possible Chimera Ransomware - Bitmessage Activity |
1960 | taskhost.exe | Misc activity | APP [PTsecurity] CoinWallet |
2 ETPRO signatures available at the full report