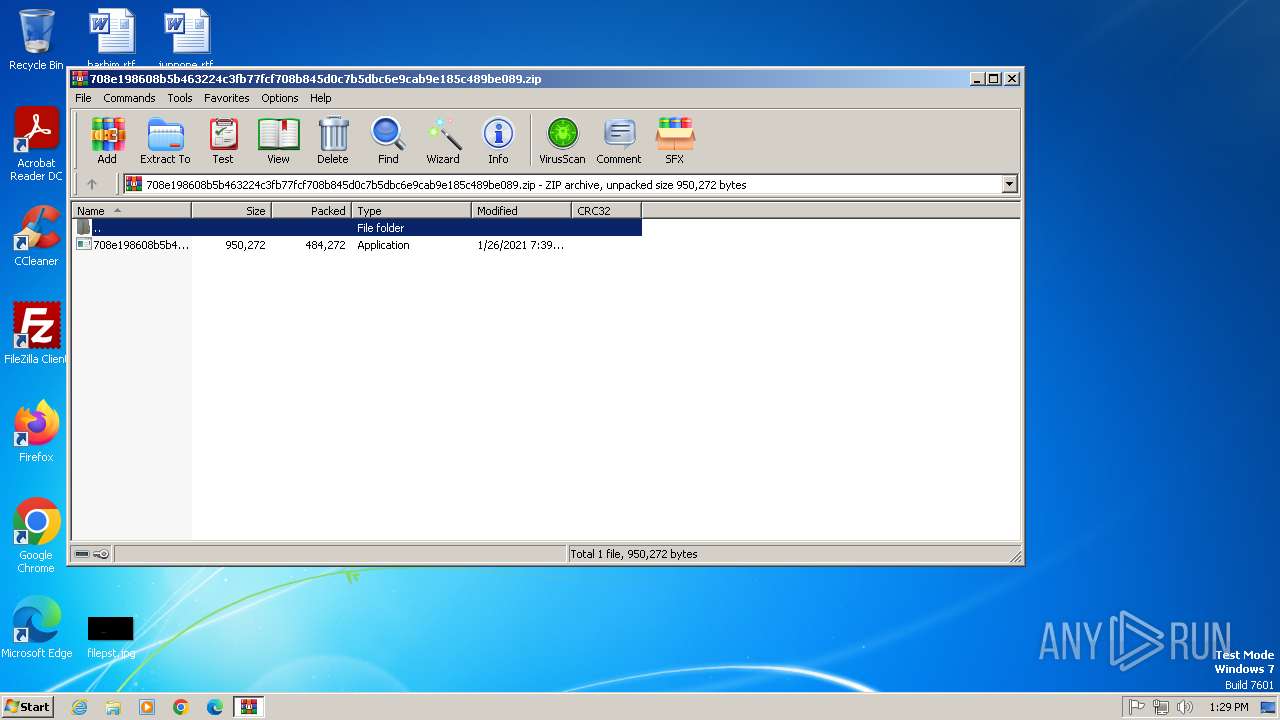
| File name: | 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.zip |
| Full analysis: | https://app.any.run/tasks/4a3877e5-1aca-4b75-b92b-eb715de42957 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 21, 2025, 12:29:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
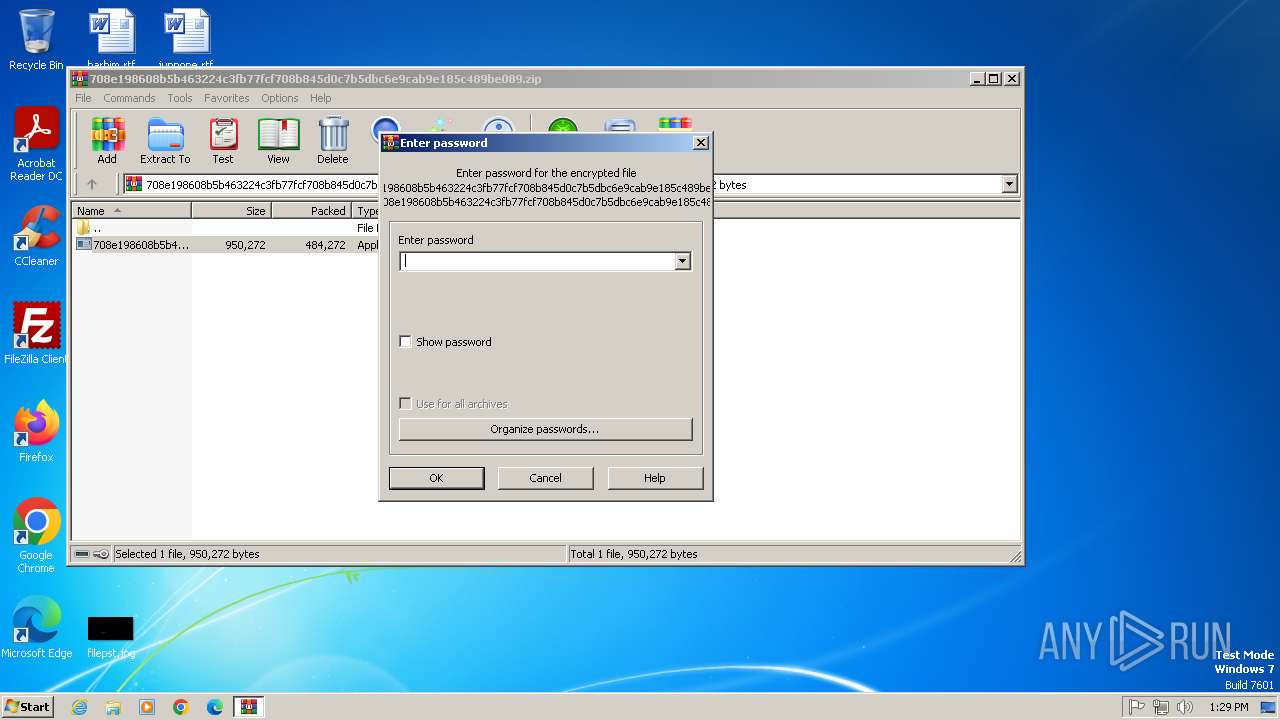
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | E0C049B213F76DC3A9133B78EBEB18B8 |
| SHA1: | F33E372DE178076C3476322E97C0E80F9E36BFE2 |
| SHA256: | 1D4C38DAEAA29E6AF28D94B4C50711DB0FCD74ED356E191B231F3CA871362FFC |
| SSDEEP: | 12288:cAHNvuO1yx3JiNsKpTR9kRPwqK94zij+L2:cMNvuOKZ+xTR9mPjlij9 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2564)
AGENTTESLA mutex has been found
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3184)
Steals credentials from Web Browsers
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 1548)
Actions looks like stealing of personal data
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 1548)
Uses Task Scheduler to run other applications
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3184)
AGENTTESLA has been detected (YARA)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 1548)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2564)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3184)
Executable content was dropped or overwritten
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3184)
Reads the Internet Settings
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3184)
Application launched itself
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3184)
Accesses Microsoft Outlook profiles
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 1548)
Reads browser cookies
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 1548)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2564)
Reads the computer name
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3184)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 1548)
Reads the machine GUID from the registry
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3184)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 1548)
Checks supported languages
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3184)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 1548)
Creates files or folders in the user directory
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3184)
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 1548)
ULTRAVNC has been detected
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 1548)
Create files in a temporary directory
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 3184)
Reads Environment values
- 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe (PID: 1548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(1548) 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe
Protocolsmtp
Hostsmtp.godforeu.com
Port587
Usernamelogs@godforeu.com
PasswordO8k#Pz4sk:w_
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2021:01:26 19:39:10 |
| ZipCRC: | 0xbba1382e |
| ZipCompressedSize: | 484272 |
| ZipUncompressedSize: | 950272 |
| ZipFileName: | 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe |
Total processes
39
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1080 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1548 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2564.30068\708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2564.30068\708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe | 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: App Version: 1.0.0.0 Modules
AgentTesla(PID) Process(1548) 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe Protocolsmtp Hostsmtp.godforeu.com Port587 Usernamelogs@godforeu.com PasswordO8k#Pz4sk:w_ | |||||||||||||||
| 2564 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2604 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\neHneiobyhcrJJ" /XML "C:\Users\admin\AppData\Local\Temp\tmp4368.tmp" | C:\Windows\System32\schtasks.exe | — | 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3184 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2564.30068\708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2564.30068\708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: App Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
5 570
Read events
5 536
Write events
34
Delete events
0
Modification events
| (PID) Process: | (1080) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {4040CF00-1B3E-486A-B407-FA14C56B6FC0} |
Value: D4DA6D2861EC | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.zip | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
2
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2564.30068\708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe | executable | |
MD5:80B51E872031A2BEFEB9A0A13E6FC480 | SHA256:708E198608B5B463224C3FB77FCF708B845D0C7B5DBC6E9CAB9E185C489BE089 | |||
| 3184 | 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe | C:\Users\admin\AppData\Local\Temp\tmp4368.tmp | xml | |
MD5:984EC3A9799C9300727FC04436E9F3A4 | SHA256:16D44F358DBF6AAD7FCACC3B68A0506FFD7395B7887D7847A77D55170BCF02B7 | |||
| 3184 | 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe | C:\Users\admin\AppData\Roaming\neHneiobyhcrJJ.exe | executable | |
MD5:80B51E872031A2BEFEB9A0A13E6FC480 | SHA256:708E198608B5B463224C3FB77FCF708B845D0C7B5DBC6E9CAB9E185C489BE089 | |||
| 1548 | 708e198608b5b463224c3fb77fcf708b845d0c7b5dbc6e9cab9e185c489be089.exe | C:\Users\admin\AppData\Roaming\xzsyeltq.05z\Firefox\Profiles\qldyz51w.default\cookies.sqlite | binary | |
MD5:23D08A78BC908C0B29E9800D3D5614E7 | SHA256:F6BD7DF5DFAE9FD88811A807DBA14085E00C1B5A6D7CC3D06CC68F6015363D59 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
smtp.godforeu.com |
| malicious |