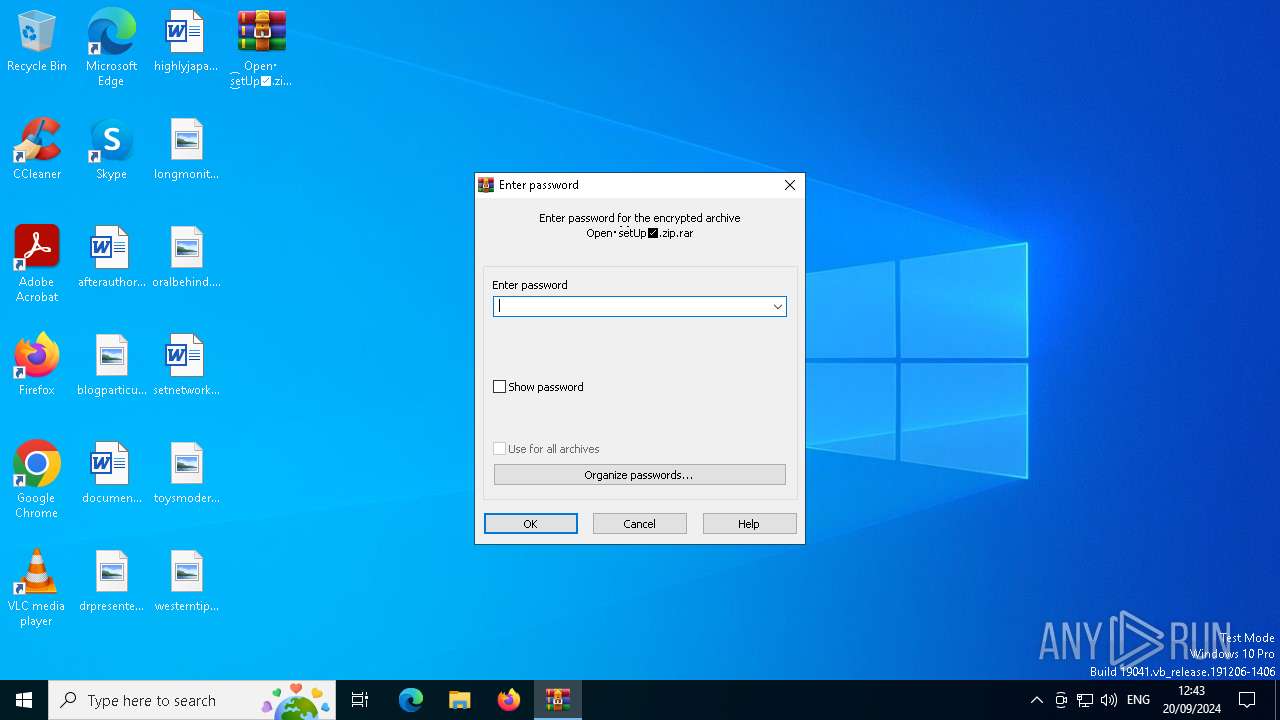
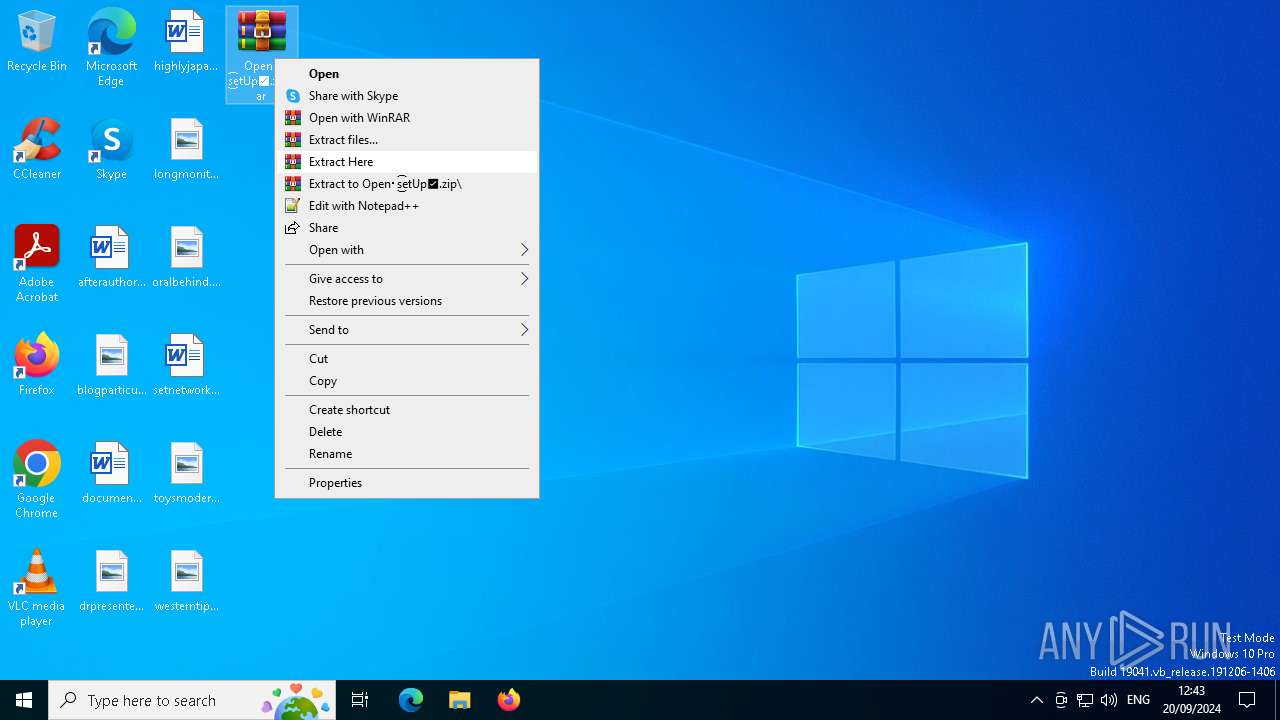
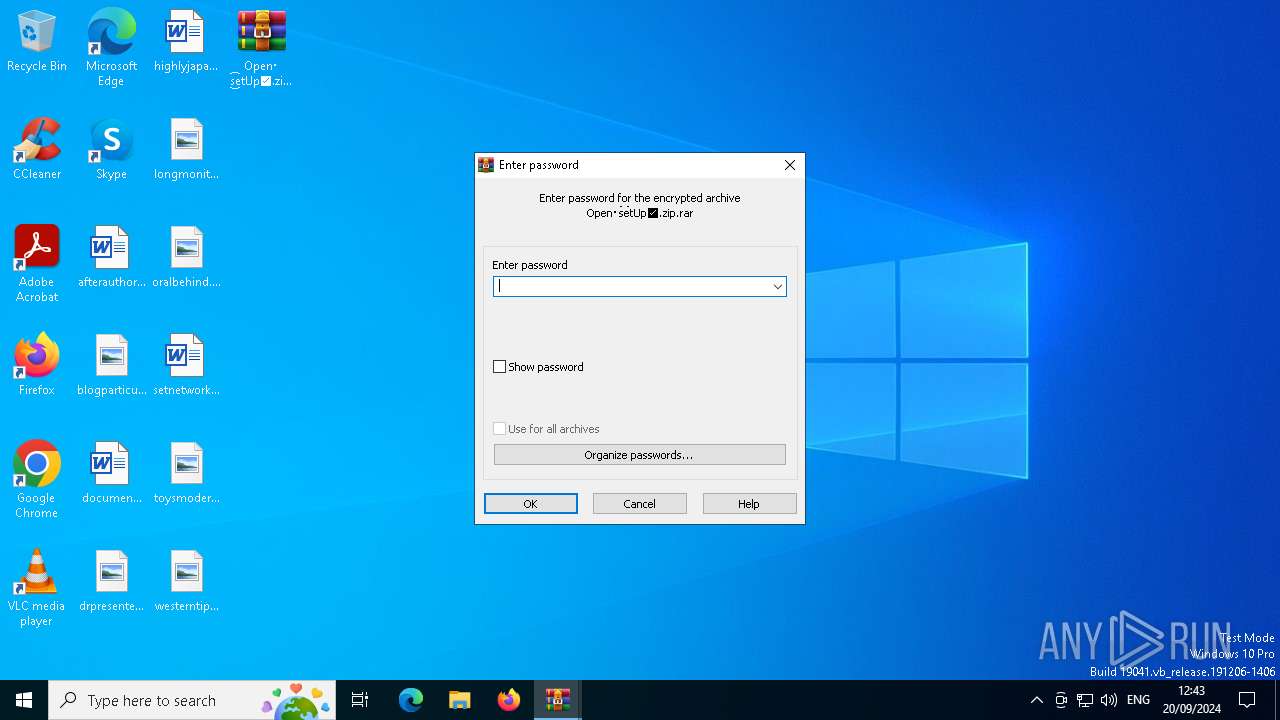
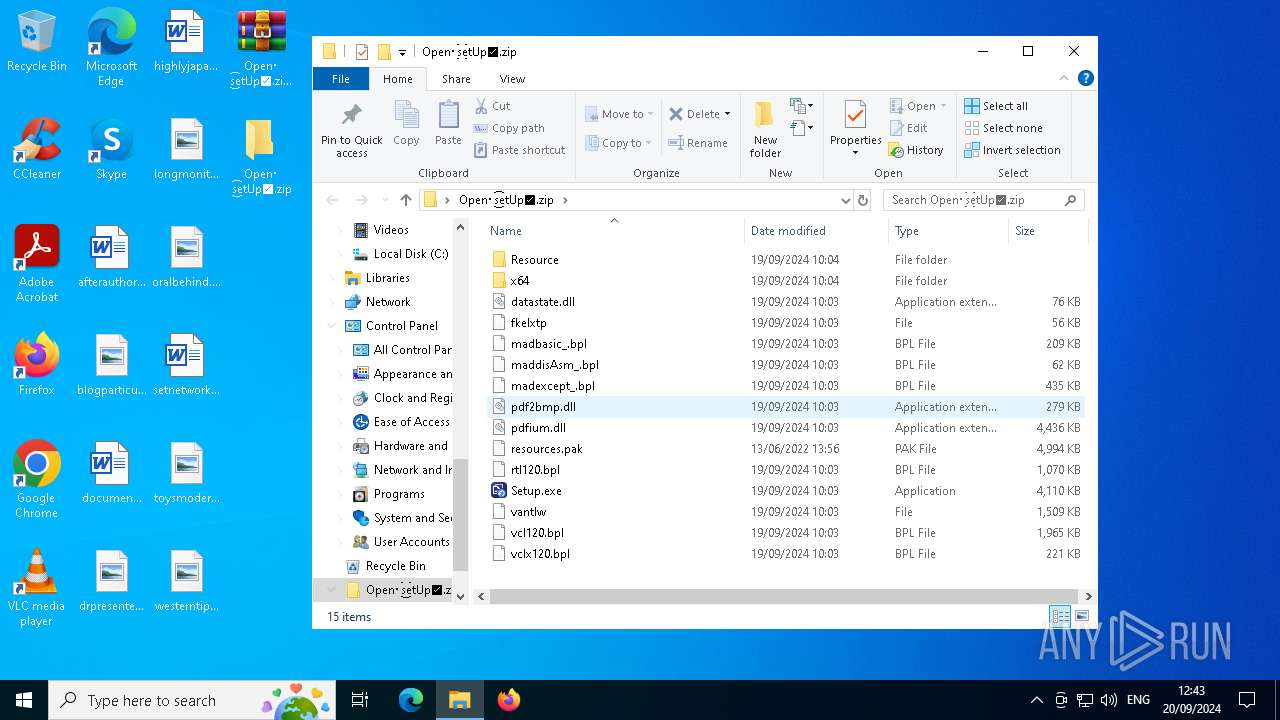
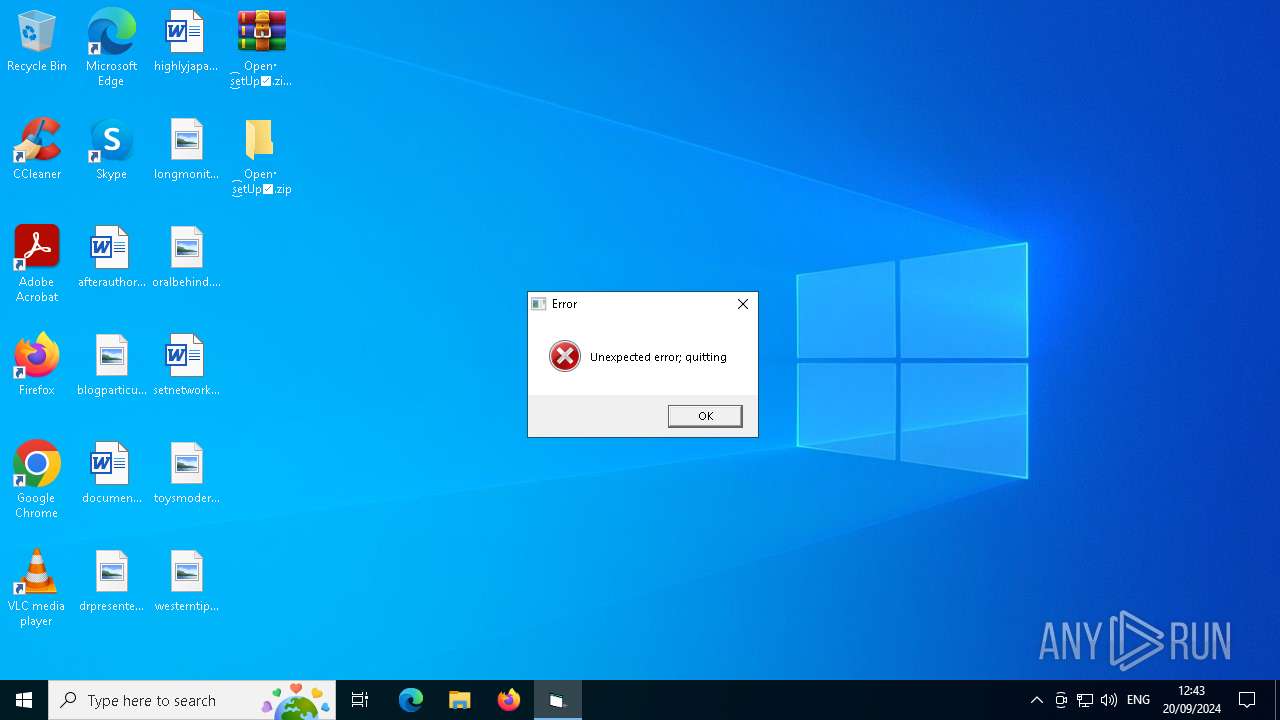
| File name: | Open・s͜͡etUp✅.zip |
| Full analysis: | https://app.any.run/tasks/b4e9f861-af35-44ea-8dd0-1aafafa399b8 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | September 20, 2024, 11:42:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 11AC625B272C2F8FE82BCAC368CB689B |
| SHA1: | 1B75545F66D1E7B27E8BD2D858D3B8BF8ACE991C |
| SHA256: | 1CD8C4AED45E0AE23F474668D07D8BD3017CAA078A6AC4799314FEBB202C2E6B |
| SSDEEP: | 196608:8FkQotG4U2pbojxMnXIDPlPWWoTjfhZmkzkK7HpEYU:8VoM4v1ojO4DPlOWoHfhZmkzkB |
MALICIOUS
Actions looks like stealing of personal data
- GlimmerEmblaze.a3x (PID: 7164)
Bypass execution policy to execute commands
- powershell.exe (PID: 740)
Changes powershell execution policy (Bypass)
- GlimmerEmblaze.a3x (PID: 7164)
LUMMA has been detected (SURICATA)
- GlimmerEmblaze.a3x (PID: 7164)
Stealers network behavior
- GlimmerEmblaze.a3x (PID: 7164)
Probably downloads file via BitsAdmin (POWERSHELL)
- powershell.exe (PID: 740)
SUSPICIOUS
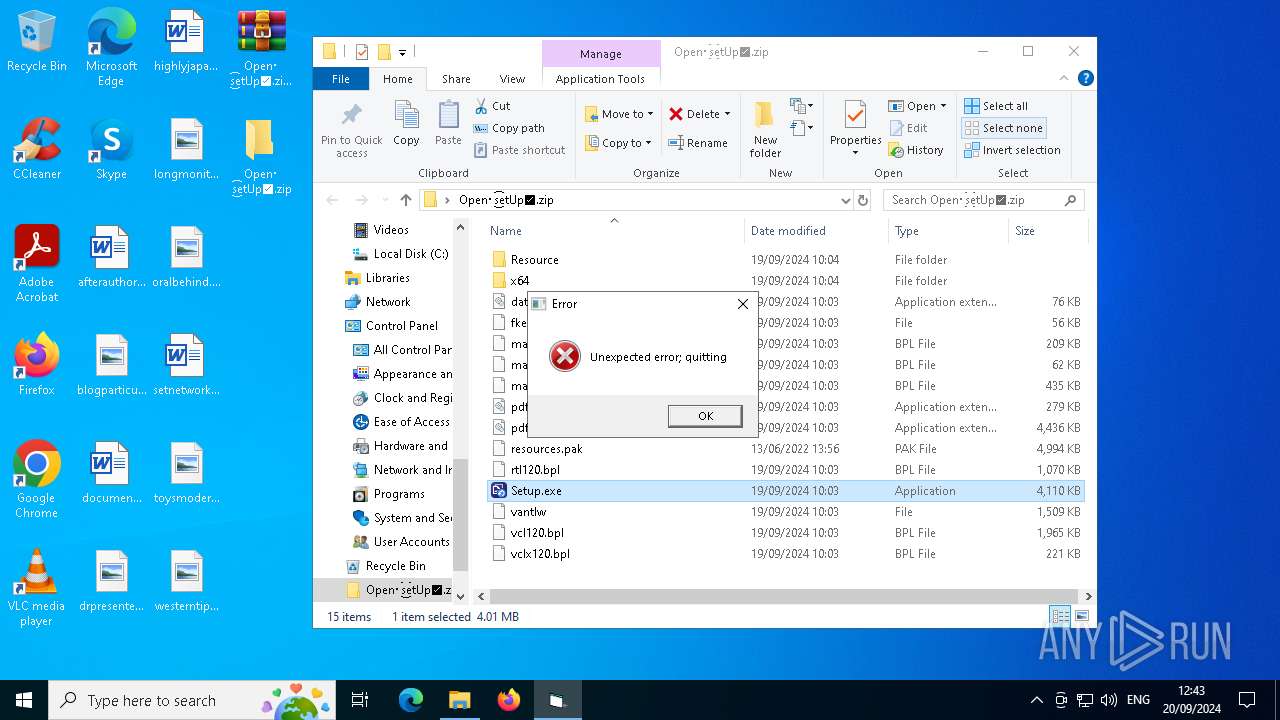
Process drops legitimate windows executable
- WinRAR.exe (PID: 6332)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6332)
Executable content was dropped or overwritten
- Setup.exe (PID: 2636)
- more.com (PID: 6432)
Starts application with an unusual extension
- Setup.exe (PID: 2636)
- more.com (PID: 6432)
Starts POWERSHELL.EXE for commands execution
- GlimmerEmblaze.a3x (PID: 7164)
The process executes Powershell scripts
- GlimmerEmblaze.a3x (PID: 7164)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 740)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 740)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6332)
- powershell.exe (PID: 740)
Manual execution by a user
- WinRAR.exe (PID: 6332)
- Setup.exe (PID: 2636)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6332)
Checks supported languages
- Setup.exe (PID: 2636)
- StrCmp.exe (PID: 3140)
- more.com (PID: 6432)
- GlimmerEmblaze.a3x (PID: 7164)
Reads the computer name
- Setup.exe (PID: 2636)
- StrCmp.exe (PID: 3140)
- GlimmerEmblaze.a3x (PID: 7164)
- more.com (PID: 6432)
Creates files or folders in the user directory
- Setup.exe (PID: 2636)
Create files in a temporary directory
- Setup.exe (PID: 2636)
- GlimmerEmblaze.a3x (PID: 7164)
- more.com (PID: 6432)
Reads the software policy settings
- GlimmerEmblaze.a3x (PID: 7164)
Reads the machine GUID from the registry
- GlimmerEmblaze.a3x (PID: 7164)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 740)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
118
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 740 | powershell -exec bypass -f "C:\Users\admin\AppData\Local\Temp\6WT8ZHNR1IH0Q6TV9OBDPI.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | GlimmerEmblaze.a3x | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2328 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.91.0 Modules
| |||||||||||||||
| 2636 | "C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\Setup.exe" | C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: iTop Inc. Integrity Level: MEDIUM Description: iTop Data Recovery Exit code: 1 Version: 4.4.0.687 Modules
| |||||||||||||||
| 2936 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3140 | C:\Users\admin\AppData\Roaming\rzf\UZASFZBPHGTPQFGGLJMI\StrCmp.exe | C:\Users\admin\AppData\Roaming\rzf\UZASFZBPHGTPQFGGLJMI\StrCmp.exe | — | Setup.exe | |||||||||||
User: admin Company: aaa Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 4980 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6332 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip.rar" C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6432 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6932 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7164 | C:\Users\admin\AppData\Local\Temp\GlimmerEmblaze.a3x | C:\Users\admin\AppData\Local\Temp\GlimmerEmblaze.a3x | more.com | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 1 Modules
| |||||||||||||||
Total events
10 107
Read events
10 095
Write events
12
Delete events
0
Modification events
| (PID) Process: | (2328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_0 |
Value: 4C000000730100000402000000000000F0F0F0000000000000000000000000000000000000000000C403050000000000000000003B000000B402000000000000000000000000000001000000 | |||
| (PID) Process: | (2328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_1 |
Value: 4C000000730100000500000000000000F0F0F0000000000000000000000000000000000000000000C20305000000000000000000180000002A00000000000000000000000000000002000000 | |||
| (PID) Process: | (2328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_2 |
Value: 4C000000730100000400000000000000F0F0F0000000000000000000000000000000000000000000AA020B000000000000000000180000006400000000000000000000000000000003000000 | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
67
Suspicious files
25
Text files
398
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\Resource\TypeSupport\Unicode\Mappings\Mac\CORPCHAR.TXT | text | |
MD5:0FBAD8E1C335AC42617936AA6F89EC89 | SHA256:83246B8C942CBACF1031445A99E62ACBB4733EF4167BEBFBA2BD852869824EAB | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\Resource\TypeSupport\Unicode\Mappings\Mac\CENTEURO.TXT | text | |
MD5:3EA4A9A2765040C721374CCBB8E7BD59 | SHA256:AE8FDF0311FE249EE1A3E08FE36C394CA2DA791C622B665DDEBCB623AC248903 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\Resource\TypeSupport\Unicode\Mappings\win\CP1254.TXT | text | |
MD5:65D7C9205E1A1393B8530670ADD4E596 | SHA256:32FA83C6F8AD346E66E544640942906E0A91CC0D2075324B7F244695DE5740A5 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\Resource\TypeSupport\Unicode\Mappings\Mac\ROMAN.TXT | text | |
MD5:94A43862CB0159469484841D8370E552 | SHA256:A58F56F7CF7767658CFF9FDFD1BA182CC74A513B3A2B6F34E44625FF811F53DD | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\Resource\TypeSupport\Unicode\Mappings\win\CP1257.TXT | text | |
MD5:002134C7EA7F619246BBF445CAAD9F08 | SHA256:7CB16A0B949F8573B06F22F091C44A1EA251CC9904591FCEB2743475302C4640 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\Resource\TypeSupport\Unicode\Mappings\Mac\GREEK.TXT | text | |
MD5:962D73AE58EA74DFA492BDA68064F130 | SHA256:1CE082E86367551B2A21465D1B1C2EDC103242F7D565411DCEA0762E3DD63AA1 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\Resource\TypeSupport\Unicode\Mappings\win\CP1252.TXT | text | |
MD5:93FB108016F8A1E87E4129B21FE9984B | SHA256:FCA3AB5882F0A562794F05D7F15A39157C59D7C07FCBAC79AB7CF3D12C979541 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\Resource\TypeSupport\Unicode\Mappings\win\CP1251.TXT | text | |
MD5:2926366654DBC6711EE71BA2589161C3 | SHA256:F87ED4480CFDDB8F5F6226292338CA407CCC7B1A543F3832F1D20AFF6CB72A58 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\Resource\TypeSupport\Unicode\Mappings\win\CP1253.TXT | text | |
MD5:6B77BAAC03038B028948D2A667EFDAA1 | SHA256:2D36BEC3E1ECBF2B6DE8A37C98717AE21CA8C5BC0B487556996B3FFF2B6F6FD9 | |||
| 6332 | WinRAR.exe | C:\Users\admin\Desktop\Open・s͜͡etUp✅.zip\Resource\TypeSupport\Unicode\Mappings\Mac\SYMBOL.TXT | text | |
MD5:46485E1A024ABC31E8B9D2B4CA9A3B39 | SHA256:C57C451D4A524159BF143573CD0568869C8EED814A999BFF7F3E560DABD39F1D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
27
DNS requests
9
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1288 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | — | 188.114.96.3:443 | https://pang-scrooge-carnage.shop/am.bin | unknown | — | — | unknown |
— | — | GET | 200 | 104.26.2.16:443 | https://rentry.co/mb5grod8/raw | unknown | text | 2.74 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 13.89.179.10:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1288 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7164 | GlimmerEmblaze.a3x | 188.114.97.3:443 | nationattwllwqm.shop | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
nationattwllwqm.shop |
| unknown |
pang-scrooge-carnage.shop |
| unknown |
rentry.co |
| unknown |
fileworld.shop |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7164 | GlimmerEmblaze.a3x | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
2256 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
7164 | GlimmerEmblaze.a3x | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |