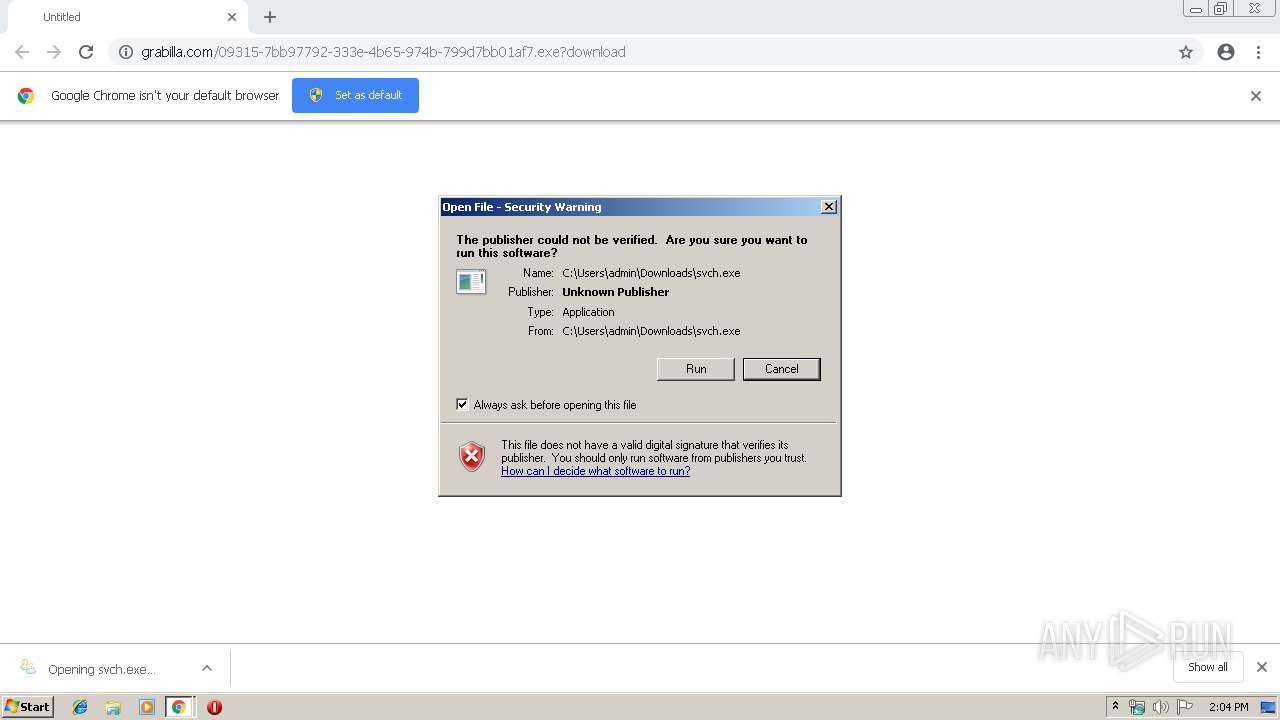
| URL: | http://grabilla.com/09315-7bb97792-333e-4b65-974b-799d7bb01af7.exe?download |
| Full analysis: | https://app.any.run/tasks/a09d4e03-0d28-4a53-b119-282e94fde1a1 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | March 21, 2019, 14:03:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0A55C4F45EA695B21D9DB83A3B1E2417 |
| SHA1: | AB6BF22CB218A18750A148B384F16ACBE1EA55DA |
| SHA256: | 1C76E69D2391B74541D9F1CA43FED07F7DB46DCCB13F8B24BE2A7DAE39E66671 |
| SSDEEP: | 3:N1KZXVGIOFnjvXV75UVUEOL8zKo:CLG/vnU+Elt |
MALICIOUS
Application was dropped or rewritten from another process
- svch.exe (PID: 2840)
- svch.exe (PID: 2524)
- d8i8mzfxv.exe (PID: 3584)
- d8i8mzfxv.exe (PID: 580)
Downloads executable files from the Internet
- chrome.exe (PID: 3248)
FORMBOOK was detected
- explorer.exe (PID: 1696)
Formbook was detected
- msdt.exe (PID: 3556)
- Firefox.exe (PID: 3048)
Connects to CnC server
- explorer.exe (PID: 1696)
Changes the autorun value in the registry
- msdt.exe (PID: 3556)
Actions looks like stealing of personal data
- msdt.exe (PID: 3556)
Stealing of credential data
- msdt.exe (PID: 3556)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 1708)
- explorer.exe (PID: 1696)
- DllHost.exe (PID: 4032)
Starts CMD.EXE for commands execution
- msdt.exe (PID: 3556)
Application launched itself
- svch.exe (PID: 2840)
- d8i8mzfxv.exe (PID: 3584)
Modifies files in Chrome extension folder
- chrome.exe (PID: 1708)
Loads DLL from Mozilla Firefox
- msdt.exe (PID: 3556)
Creates files in the user directory
- msdt.exe (PID: 3556)
Creates files in the program directory
- DllHost.exe (PID: 4032)
Uses NETSTAT.EXE to discover network connections
- explorer.exe (PID: 1696)
INFO
Application launched itself
- chrome.exe (PID: 1708)
Creates files in the user directory
- Firefox.exe (PID: 3048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
66
Monitored processes
30
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=896,8012304632688171530,16865855876165808760,131072 --enable-features=PasswordImport --service-pipe-token=14437837589089298652 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14437837589089298652 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2316 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 580 | "C:\Program Files\Zcrchzlj\d8i8mzfxv.exe" | C:\Program Files\Zcrchzlj\d8i8mzfxv.exe | — | d8i8mzfxv.exe | |||||||||||
User: admin Company: caMSTUDiO GrOUP Integrity Level: MEDIUM Description: the pIDGiN deVElOpEr cOmmunity Exit code: 0 Version: 4.09.0005 Modules
| |||||||||||||||
| 612 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1104 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=896,8012304632688171530,16865855876165808760,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=9679246118786840545 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9679246118786840545 --renderer-client-id=17 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3868 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1220 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=896,8012304632688171530,16865855876165808760,131072 --enable-features=PasswordImport --service-pipe-token=16215872599103831013 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16215872599103831013 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2100 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1464 | /c del "C:\Users\admin\Downloads\svch.exe" | C:\Windows\System32\cmd.exe | — | msdt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1696 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" http://grabilla.com/09315-7bb97792-333e-4b65-974b-799d7bb01af7.exe?download | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=896,8012304632688171530,16865855876165808760,131072 --enable-features=PasswordImport --service-pipe-token=1319514406212120930 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1319514406212120930 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2112 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1932 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=896,8012304632688171530,16865855876165808760,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11186284436143451236 --mojo-platform-channel-handle=3760 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
3 582
Read events
3 428
Write events
150
Delete events
4
Modification events
| (PID) Process: | (1696) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000418795FC2F2C5A46852A5EA30B2A11D1000000000200000000001066000000010000200000002B3277F282C330D3DA2961B1DAF460E4E4CD23AC140A40A8CAEA6A4FDF018D76000000000E8000000002000020000000B313C688516ADA594E6CF494214905A2C4C2B5FE4C2DFAF62BD8ABE2DF50D8E230000000928713A04160068ACC0BEB071F6F0AE2291F7942A556BD2A98C3DE5959CA1A408C9B32D3F1DF3C071B2ACE7C8933DCE040000000785EADB5D0C00CEFF716D597C2524F958473C7583338160899E5D41FB1FDAB7D1C23AC44160D994B1594F9304F6DB1FA1D2B89B012BB10A43F37992FA2AEDAA9 | |||
| (PID) Process: | (1708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (612) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 1708-13197650626342500 |
Value: 259 | |||
| (PID) Process: | (1708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1708) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
Executable files
5
Suspicious files
143
Text files
220
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 1708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 1708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 1708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 1708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 1708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\2e7103a3-0c68-4239-9f03-b178303f9dae.tmp | — | |
MD5:— | SHA256:— | |||
| 1708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | — | |
MD5:— | SHA256:— | |||
| 1708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 1708 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
27
DNS requests
22
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1696 | explorer.exe | GET | — | 183.181.79.87:80 | http://www.kataduke-teineinakurashi.com/sh/?iBkH1n=3x2YoFU14KtbbyEV6cJj8XbbY/LTlWuYYJJ+QYxkN8tWUAsqQ3/dN0lOrRTvaFQUjI+J+Q==&-ZUDU=Mj9L_rMX | JP | — | — | malicious |
1696 | explorer.exe | GET | — | 66.254.168.213:80 | http://www.world-fireworks.com/sh/?iBkH1n=PXOqnmaJ5S1diRXMm/dd2vk5YC7cxY+rajcA0korVaduwWu/bsYWmFj3cUI7eSJznYh9xA==&-ZUDU=Mj9L_rMX&sql=1 | US | — | — | malicious |
3248 | chrome.exe | GET | 302 | 216.58.207.78:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 504 b | whitelisted |
3248 | chrome.exe | GET | 200 | 173.194.19.183:80 | http://r1---sn-5go7yn7z.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=82.102.22.104&mm=28&mn=sn-5go7yn7z&ms=nvh&mt=1553177125&mv=m&pl=24&shardbypass=yes | US | crx | 842 Kb | whitelisted |
— | — | POST | — | 66.254.168.213:80 | http://www.world-fireworks.com/sh/ | US | — | — | malicious |
3248 | chrome.exe | GET | 200 | 192.81.132.172:80 | http://grabilla.com/09315-7bb97792-333e-4b65-974b-799d7bb01af7.exe?download | US | executable | 235 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3248 | chrome.exe | 172.217.22.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3248 | chrome.exe | 192.81.132.172:80 | grabilla.com | Linode, LLC | US | suspicious |
3248 | chrome.exe | 172.217.22.109:443 | accounts.google.com | Google Inc. | US | whitelisted |
3248 | chrome.exe | 172.217.22.4:443 | www.google.com | Google Inc. | US | whitelisted |
3248 | chrome.exe | 172.217.16.142:443 | clients1.google.com | Google Inc. | US | whitelisted |
3248 | chrome.exe | 172.217.22.14:443 | apis.google.com | Google Inc. | US | whitelisted |
3248 | chrome.exe | 216.58.207.78:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
1696 | explorer.exe | 157.7.144.96:80 | www.hatsuratsu-houmon.com | GMO Internet,Inc | JP | malicious |
3248 | chrome.exe | 173.194.19.183:80 | r1---sn-5go7yn7z.gvt1.com | Google Inc. | US | whitelisted |
1696 | explorer.exe | 66.254.168.213:80 | www.world-fireworks.com | eSited Solutions | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
grabilla.com |
| suspicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
clients1.google.com |
| whitelisted |
www.google.com |
| malicious |
apis.google.com |
| whitelisted |
play.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3248 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3248 | chrome.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
1696 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
— | — | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
— | — | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
— | — | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
— | — | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
3 ETPRO signatures available at the full report