| File name: | 1c168219f487ed2749eac61d8564ba214670a535fc4277b10773f4d4d8299e8a |
| Full analysis: | https://app.any.run/tasks/5734b400-ce46-40e6-950d-7d8ce03001e9 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 17, 2025, 01:57:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 8 sections |
| MD5: | 7A88F024575EFDB8A034FEDEA19C9C11 |
| SHA1: | 7BDC95B0A4016DDF5EA19E557429CB0DB16514D7 |
| SHA256: | 1C168219F487ED2749EAC61D8564BA214670A535FC4277B10773F4D4D8299E8A |
| SSDEEP: | 98304:BkVH6KaNz9hl4T9TB6XzDL7ChuABolDPGTy9T1cMRo+o8D7VFtrQ/3L//OLBUOJS:Z/yBrSq90jSi6r986CFtpnx56f |
MALICIOUS
Changes the autorun value in the registry
- efgk.exe (PID: 7992)
ASYNCRAT has been detected (YARA)
- Antimalware Core Servicex.exe (PID: 8188)
SUSPICIOUS
Reads security settings of Internet Explorer
- 1c168219f487ed2749eac61d8564ba214670a535fc4277b10773f4d4d8299e8a.exe (PID: 7876)
Reads the date of Windows installation
- 1c168219f487ed2749eac61d8564ba214670a535fc4277b10773f4d4d8299e8a.exe (PID: 7876)
Starts CMD.EXE for commands execution
- efgk.exe (PID: 7992)
Executable content was dropped or overwritten
- 1c168219f487ed2749eac61d8564ba214670a535fc4277b10773f4d4d8299e8a.exe (PID: 7876)
- efgk.exe (PID: 7992)
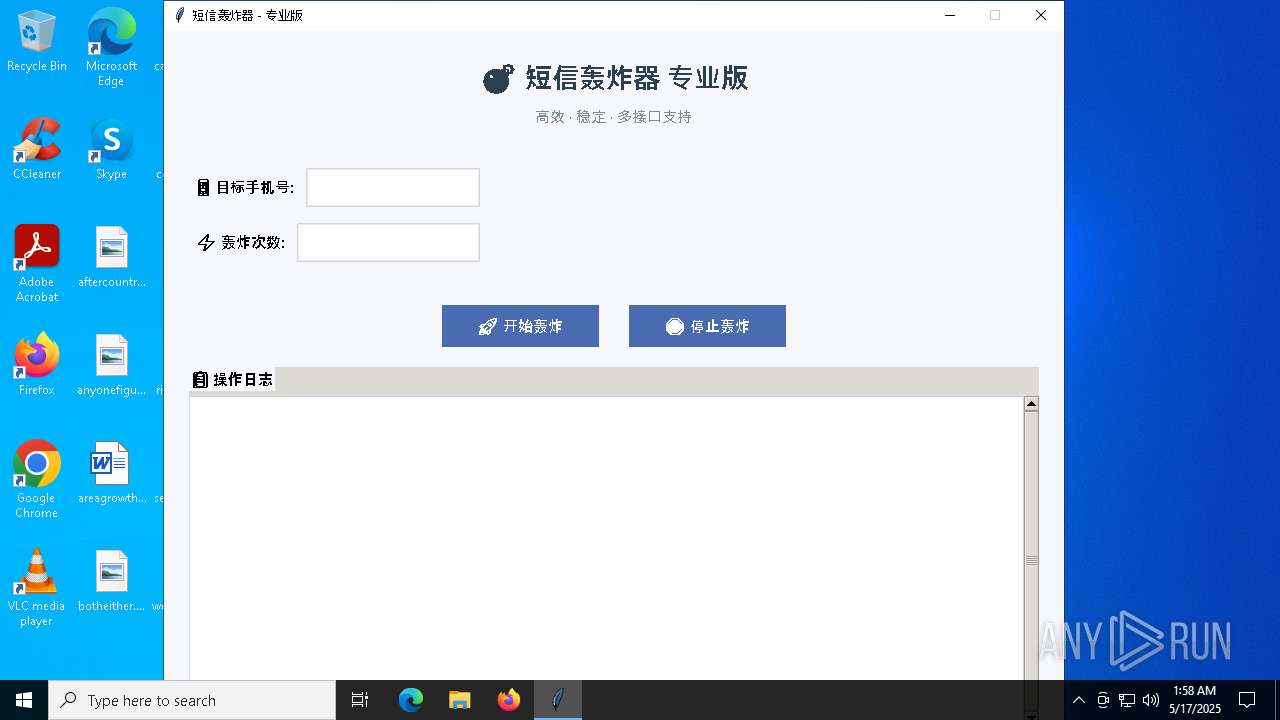
- 短信轰炸器.exe (PID: 7972)
The executable file from the user directory is run by the CMD process
- Antimalware Core Servicex.exe (PID: 8188)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 8084)
Connects to unusual port
- Antimalware Core Servicex.exe (PID: 8188)
Process drops legitimate windows executable
- 短信轰炸器.exe (PID: 7972)
The process drops C-runtime libraries
- 短信轰炸器.exe (PID: 7972)
Executing commands from a ".bat" file
- efgk.exe (PID: 7992)
Process drops python dynamic module
- 短信轰炸器.exe (PID: 7972)
Application launched itself
- 短信轰炸器.exe (PID: 7972)
There is functionality for taking screenshot (YARA)
- 短信轰炸器.exe (PID: 7972)
- 短信轰炸器.exe (PID: 516)
Loads Python modules
- 短信轰炸器.exe (PID: 516)
Executes application which crashes
- Antimalware Core Servicex.exe (PID: 7504)
INFO
Reads the computer name
- 1c168219f487ed2749eac61d8564ba214670a535fc4277b10773f4d4d8299e8a.exe (PID: 7876)
- 短信轰炸器.exe (PID: 7972)
- efgk.exe (PID: 7992)
- Antimalware Core Servicex.exe (PID: 8188)
- 短信轰炸器.exe (PID: 516)
Process checks computer location settings
- 1c168219f487ed2749eac61d8564ba214670a535fc4277b10773f4d4d8299e8a.exe (PID: 7876)
The sample compiled with english language support
- 短信轰炸器.exe (PID: 7972)
Checks supported languages
- 1c168219f487ed2749eac61d8564ba214670a535fc4277b10773f4d4d8299e8a.exe (PID: 7876)
- efgk.exe (PID: 7992)
- 短信轰炸器.exe (PID: 7972)
- Antimalware Core Servicex.exe (PID: 8188)
- Antimalware Core Servicex.exe (PID: 7504)
- 短信轰炸器.exe (PID: 516)
Create files in a temporary directory
- 短信轰炸器.exe (PID: 7972)
- efgk.exe (PID: 7992)
Auto-launch of the file from Registry key
- efgk.exe (PID: 7992)
Creates files or folders in the user directory
- efgk.exe (PID: 7992)
- WerFault.exe (PID: 7400)
Reads the machine GUID from the registry
- efgk.exe (PID: 7992)
- Antimalware Core Servicex.exe (PID: 8188)
Manual execution by a user
- Antimalware Core Servicex.exe (PID: 7504)
PyInstaller has been detected (YARA)
- 短信轰炸器.exe (PID: 7972)
- 短信轰炸器.exe (PID: 516)
Reads the software policy settings
- slui.exe (PID: 6004)
Checks proxy server information
- slui.exe (PID: 6004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(8188) Antimalware Core Servicex.exe
C2 (1)110.42.61.91
Ports (1)8995
VersionPortHack 1.0.0
Options
AutoRuntrue
MutexDcRatMutex
InstallFolder%AppData%
Certificates
Cert1MIICMDCCAZmgAwIBAgIVAKTEcVbts/PEwS7j1NQs9gm8MTvZMA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDERjUmF0IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTI0MDcyOTExNDMwOFoXDTM1MDUwODExNDMwOFowEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A...
Server_SignatureT4oul2WeKlORf3LiX9BKRbUDrG/U4WIJAh0HEArcfBHmTBB9qWL0JogPvxZdQp62EzwKKtboKNnwUbBCdcl0wuUlWwRvIUomcerpYvPgUox4LHgFCnT8mlOb/je+VZzWjvPbgwgprdHO5hW0nuMawXVKkCuhdxMRc+thYJuc3YE=
Keys
AESc2b1bd9ba2d16de08a82eb6f34936f4de4e3c1b3c47d093691afda994ac5f597
SaltDcRatByqwqdanchun
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:02:26 09:01:47+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.33 |
| CodeSize: | 288768 |
| InitializedDataSize: | 171520 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x32e60 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
138
Monitored processes
14
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Windows\Temp\短信轰炸器.exe" | C:\Windows\Temp\短信轰炸器.exe | — | 短信轰炸器.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5588 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Antimalware Core Servicex.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6004 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7348 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Antimalware Core Servicex.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7400 | C:\WINDOWS\system32\WerFault.exe -u -p 7504 -s 216 | C:\Windows\System32\WerFault.exe | — | Antimalware Core Servicex.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7504 | "C:\Users\admin\AppData\Roaming\Antimalware Core Servicex.exe" | C:\Users\admin\AppData\Roaming\Antimalware Core Servicex.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 7876 | "C:\Users\admin\Desktop\1c168219f487ed2749eac61d8564ba214670a535fc4277b10773f4d4d8299e8a.exe" | C:\Users\admin\Desktop\1c168219f487ed2749eac61d8564ba214670a535fc4277b10773f4d4d8299e8a.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7972 | "C:\Windows\Temp\短信轰炸器.exe" | C:\Windows\Temp\短信轰炸器.exe | 1c168219f487ed2749eac61d8564ba214670a535fc4277b10773f4d4d8299e8a.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7992 | "C:\Windows\Temp\efgk.exe" | C:\Windows\Temp\efgk.exe | 1c168219f487ed2749eac61d8564ba214670a535fc4277b10773f4d4d8299e8a.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 8000 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | efgk.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 343
Read events
6 342
Write events
1
Delete events
0
Modification events
| (PID) Process: | (7992) efgk.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Antimalware Core Servicex |
Value: "C:\Users\admin\AppData\Roaming\Antimalware Core Servicex.exe" | |||
Executable files
30
Suspicious files
7
Text files
941
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7972 | 短信轰炸器.exe | C:\Users\admin\AppData\Local\Temp\_MEI79722\VCRUNTIME140_1.dll | executable | |
MD5:C0C0B4C611561F94798B62EB43097722 | SHA256:497A280550443E3E9F89E428E51CB795139CA8944D5DEDD54A7083C00E7164E5 | |||
| 7876 | 1c168219f487ed2749eac61d8564ba214670a535fc4277b10773f4d4d8299e8a.exe | C:\Windows\Temp\短信轰炸器.exe | executable | |
MD5:F68AA26FF1817FD095429E380A8D755C | SHA256:BDED591497224DDF09D9137D5AC41521654ADA8426D75BF0E7C71165C20D4DF1 | |||
| 7972 | 短信轰炸器.exe | C:\Users\admin\AppData\Local\Temp\_MEI79722\_ssl.pyd | executable | |
MD5:689F1ABAC772C9E4C2D3BAD3758CB398 | SHA256:D3A89AA7E4A1DF1151632A8A5CAF338C4DDDB674EC093BFDBC122ADC9DB28A97 | |||
| 7972 | 短信轰炸器.exe | C:\Users\admin\AppData\Local\Temp\_MEI79722\_ctypes.pyd | executable | |
MD5:29873384E13B0A78EE9857604161514B | SHA256:3CC8500A958CC125809B0467930EBCCE88A09DCC0CEDD7A45FACF3E332F7DB33 | |||
| 7972 | 短信轰炸器.exe | C:\Users\admin\AppData\Local\Temp\_MEI79722\_tcl_data\auto.tcl | text | |
MD5:97EFA9EBE840EA051F9706504C8BD783 | SHA256:08113823951619D659EB03A1F6ACD2F9500E1264795219125A5DF7B83CABCB99 | |||
| 7972 | 短信轰炸器.exe | C:\Users\admin\AppData\Local\Temp\_MEI79722\_bz2.pyd | executable | |
MD5:684D656AADA9F7D74F5A5BDCF16D0EDB | SHA256:A5DFB4A663DEF3D2276B88866F6D220F6D30CC777B5D841CF6DBB15C6858017C | |||
| 7972 | 短信轰炸器.exe | C:\Users\admin\AppData\Local\Temp\_MEI79722\_hashlib.pyd | executable | |
MD5:3E540EF568215561590DF215801B0F59 | SHA256:0ED7A6ED080499BC6C29D7113485A8A61BDBA93087B010FCA67D9B8289CBE6FA | |||
| 7972 | 短信轰炸器.exe | C:\Users\admin\AppData\Local\Temp\_MEI79722\_lzma.pyd | executable | |
MD5:D63E2E743EA103626D33B3C1D882F419 | SHA256:7C2D2030D5D246739C5D85F087FCF404BC36E1815E69A8AC7C9541267734FC28 | |||
| 7972 | 短信轰炸器.exe | C:\Users\admin\AppData\Local\Temp\_MEI79722\_queue.pyd | executable | |
MD5:CC0F4A77CCFE39EFC8019FA8B74C06D0 | SHA256:DEE7D19A9FCAB0DF043DC56F2CDC32F1A2A968AB229679B38B378C61CA0CBA53 | |||
| 7972 | 短信轰炸器.exe | C:\Users\admin\AppData\Local\Temp\_MEI79722\_overlapped.pyd | executable | |
MD5:363409FBACB1867F2CE45E3C6922DDB4 | SHA256:F154AC9D5CA0646D18F6197C0406F7541B6E0752B2D82A330036C1E39D3A49E7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
39
DNS requests
21
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
8188 | Antimalware Core Servicex.exe | 110.42.61.91:8995 | — | NINGBO, ZHEJIANG Province, P.R.China. | CN | malicious |
7244 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7244 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7760 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6004 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
dns.msftncsi.com |
| whitelisted |