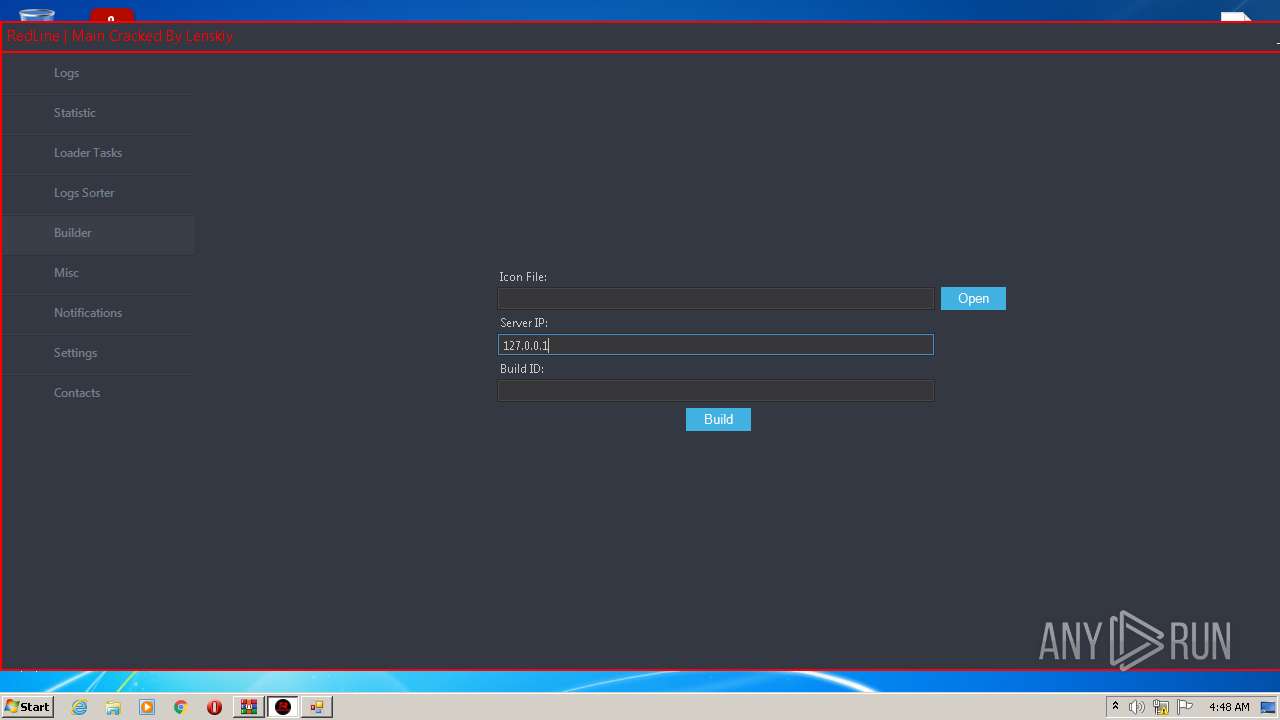
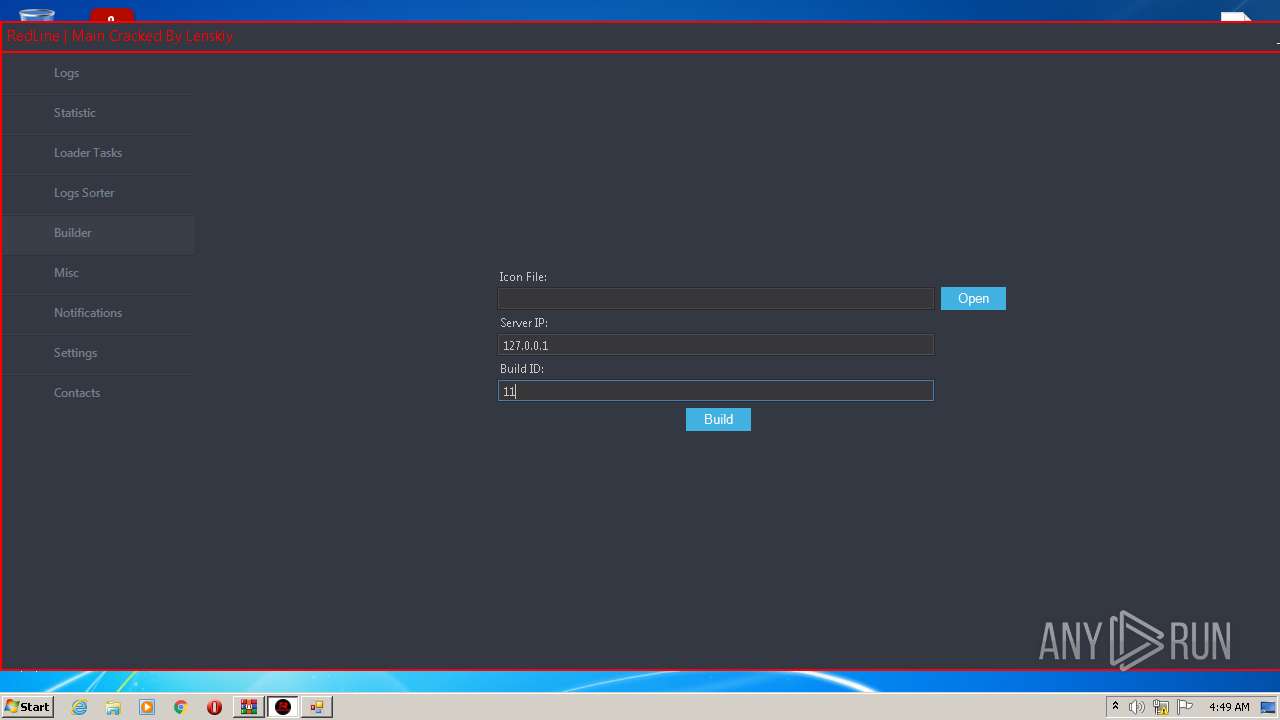
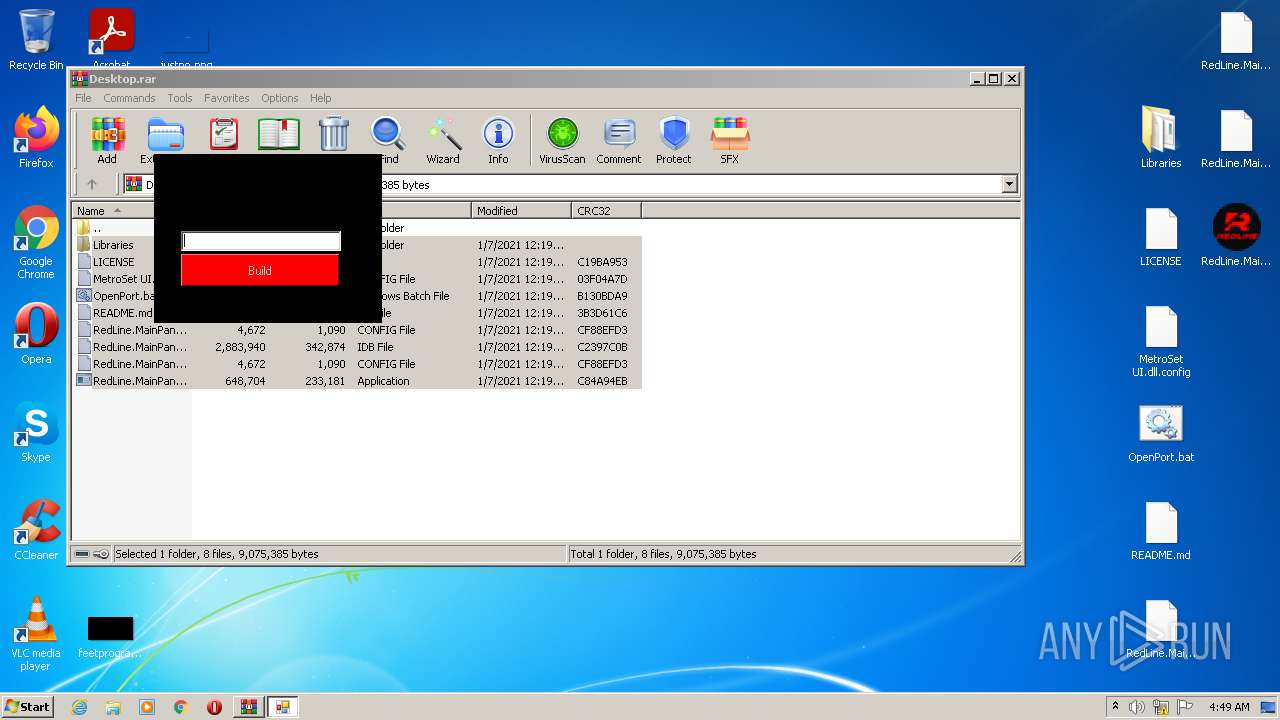
| File name: | Desktop.rar |
| Full analysis: | https://app.any.run/tasks/8d0c7a88-9066-40c1-b751-9e6a3248b327 |
| Verdict: | Malicious activity |
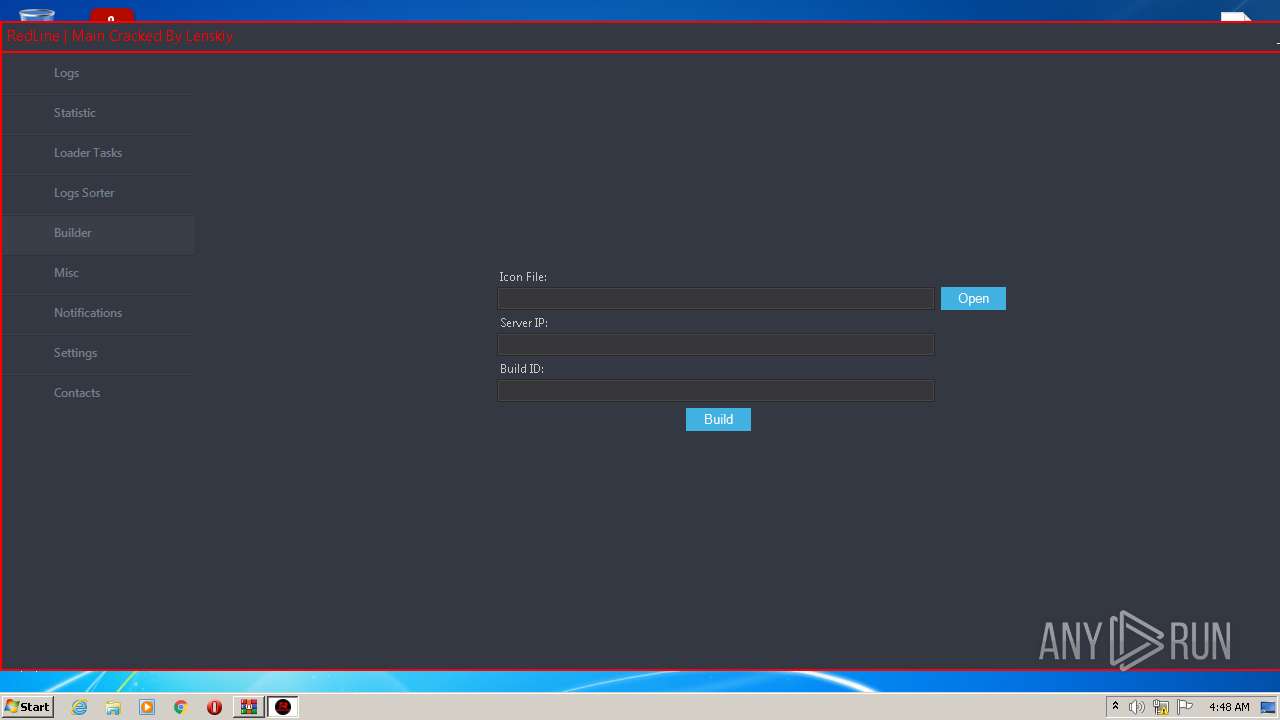
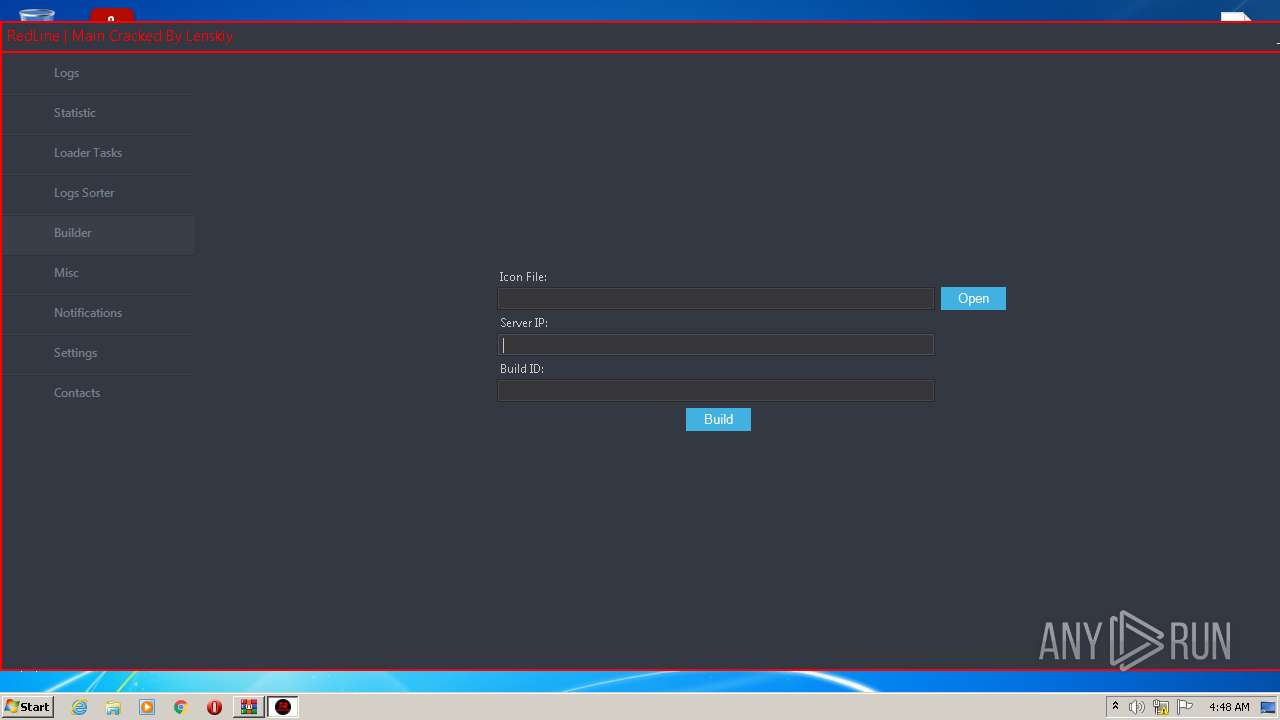
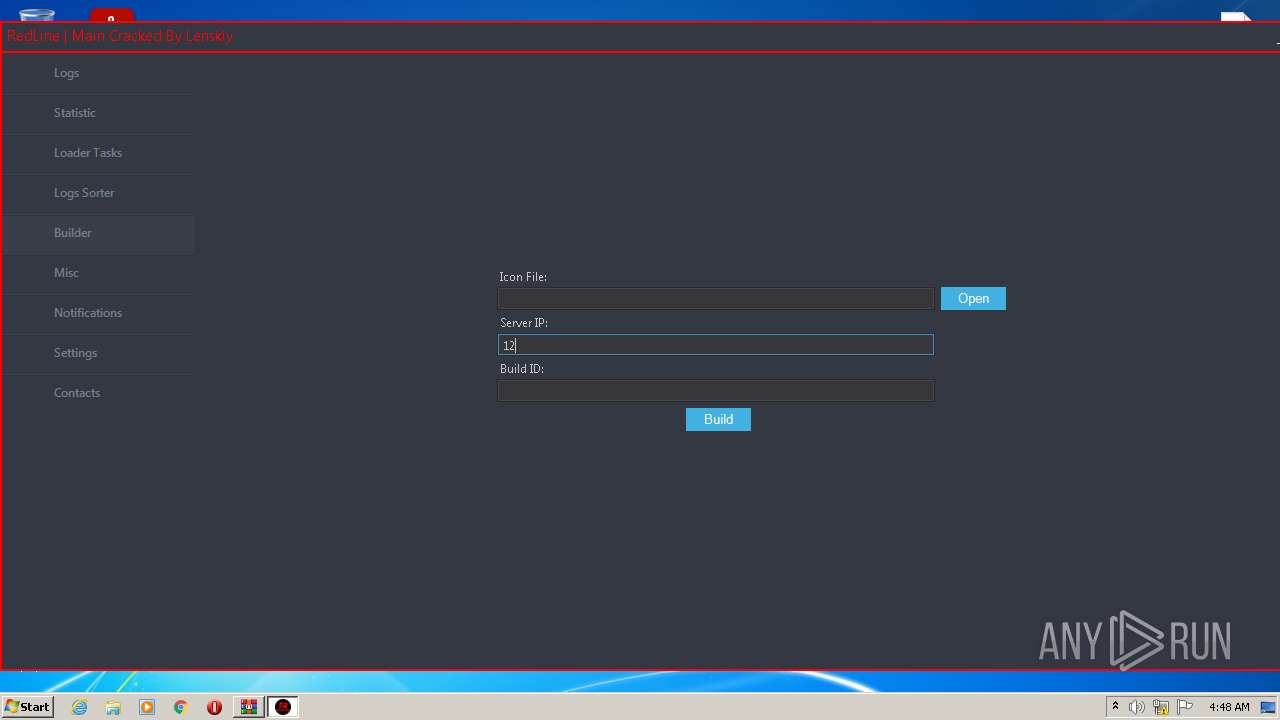
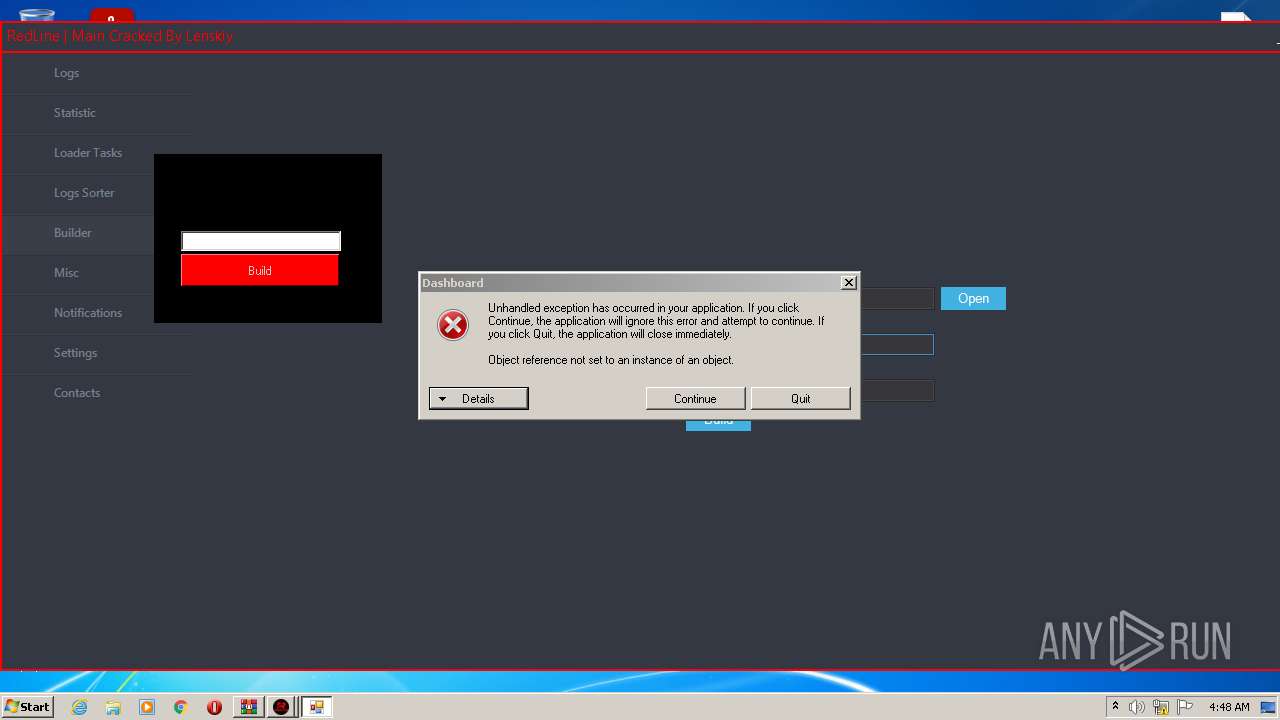
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | October 05, 2022, 03:48:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 6A4BA5C4BB02CE87D05F1C966EE40F10 |
| SHA1: | E21F7F52CC10B6322236C176FDC4F841B3A14CE5 |
| SHA256: | 1BEDD92DAC7E43F220AB2A66AEF17600463E05BE273EE0C600D40DB067C792CE |
| SSDEEP: | 49152:4Rh3un9ehyl3tRuXqrX4v/kQGmEr6Xv/onzU:4LCt3toX4o/ZGTr6//ozU |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3824)
- RedLine.MainPanel-cracked.exe (PID: 3000)
Application was dropped or rewritten from another process
- builder.exe (PID: 904)
- RedLine.MainPanel-cracked.exe (PID: 3000)
REDLINE detected by memory dumps
- RedLine.MainPanel-cracked.exe (PID: 3000)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 1300)
- builder.exe (PID: 904)
- RedLine.MainPanel-cracked.exe (PID: 3000)
Reads the computer name
- WinRAR.exe (PID: 1300)
- builder.exe (PID: 904)
- RedLine.MainPanel-cracked.exe (PID: 3000)
Reads Environment values
- RedLine.MainPanel-cracked.exe (PID: 3000)
INFO
Manual execution by user
- RedLine.MainPanel-cracked.exe (PID: 3000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
37
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 904 | "C:\Users\admin\Desktop\Libraries\builder.exe" | C:\Users\admin\Desktop\Libraries\builder.exe | — | RedLine.MainPanel-cracked.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: builder Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1300 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Desktop.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3000 | "C:\Users\admin\Desktop\RedLine.MainPanel-cracked.exe" | C:\Users\admin\Desktop\RedLine.MainPanel-cracked.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RedLinePanel Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3824 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
Total events
2 322
Read events
2 300
Write events
22
Delete events
0
Modification events
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Desktop.rar | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
14
Suspicious files
5
Text files
7
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1300.35853\Libraries\Mono.Cecil.pdb | binary | |
MD5:C0A69F1B0C50D4F133CD0B278AC2A531 | SHA256:A4F79C99D8923BD6C30EFAFA39363C18BABE95F6609BBAD242BCA44342CCC7BB | |||
| 1300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1300.35853\Libraries\MetroSet UI.dll | odttf | |
MD5:F13DC3CFFEF729D26C4DA102674561CF | SHA256:D490C04E6E89462FD46099D3454985F319F57032176C67403B3B92C86CA58BCB | |||
| 1300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1300.35853\Libraries\builder.pdb | pdb | |
MD5:418DC008EF956465E179EC29D3C3C245 | SHA256:8C7E21B37540211D56C5FDBB7E731655A96945AA83F2988E33D5ADB8AA7C8DF1 | |||
| 1300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1300.35853\Libraries\Bunifu_UI_v1.52.dll | executable | |
MD5:5ECA94D909F1BA4C5F3E35AC65A49076 | SHA256:DE0E530D46C803D85B8AEB6D18816F1B09CB3DAFEFB5E19FDFA15C9F41E0F474 | |||
| 1300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1300.35853\Libraries\Mono.Cecil.dll | executable | |
MD5:7546ACEBC5A5213DEE2A5ED18D7EBC6C | SHA256:7744C9C84C28033BC3606F4DFCE2ADCD6F632E2BE7827893C3E2257100F1CF9E | |||
| 1300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1300.35853\Libraries\Mono.Cecil.Pdb.pdb | binary | |
MD5:8E07476DB3813903E596B669D3744855 | SHA256:AA6469974D04CBA872F86E6598771663BB8721D43A4A0A2A44CF3E2CD2F1E646 | |||
| 1300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1300.35853\Libraries\Mono.Cecil.Mdb.dll | executable | |
MD5:DC80F588F513D998A5DF1CA415EDB700 | SHA256:90CFC73BEFD43FC3FD876E23DCC3F5CE6E9D21D396BBB346513302E2215DB8C9 | |||
| 1300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1300.35853\RedLine.MainPanel1.exe.config | xml | |
MD5:6EBC9B76090C8C4BF6B65C02503C6CD6 | SHA256:EF9352989527D16CF5BE708B0D8E6D384618746A3999230F477CF50F34FF67C9 | |||
| 1300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1300.35853\Libraries\GuiLib.dll | executable | |
MD5:EAF9C55793CD26F133708714ED3A5397 | SHA256:87CFC70BEC2D2A37BCD5D46F9E6F0051F82E015FF96E8F2BC2D81B85F2632F15 | |||
| 1300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1300.35853\RedLine.MainPanel.exe.config | xml | |
MD5:6EBC9B76090C8C4BF6B65C02503C6CD6 | SHA256:EF9352989527D16CF5BE708B0D8E6D384618746A3999230F477CF50F34FF67C9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report