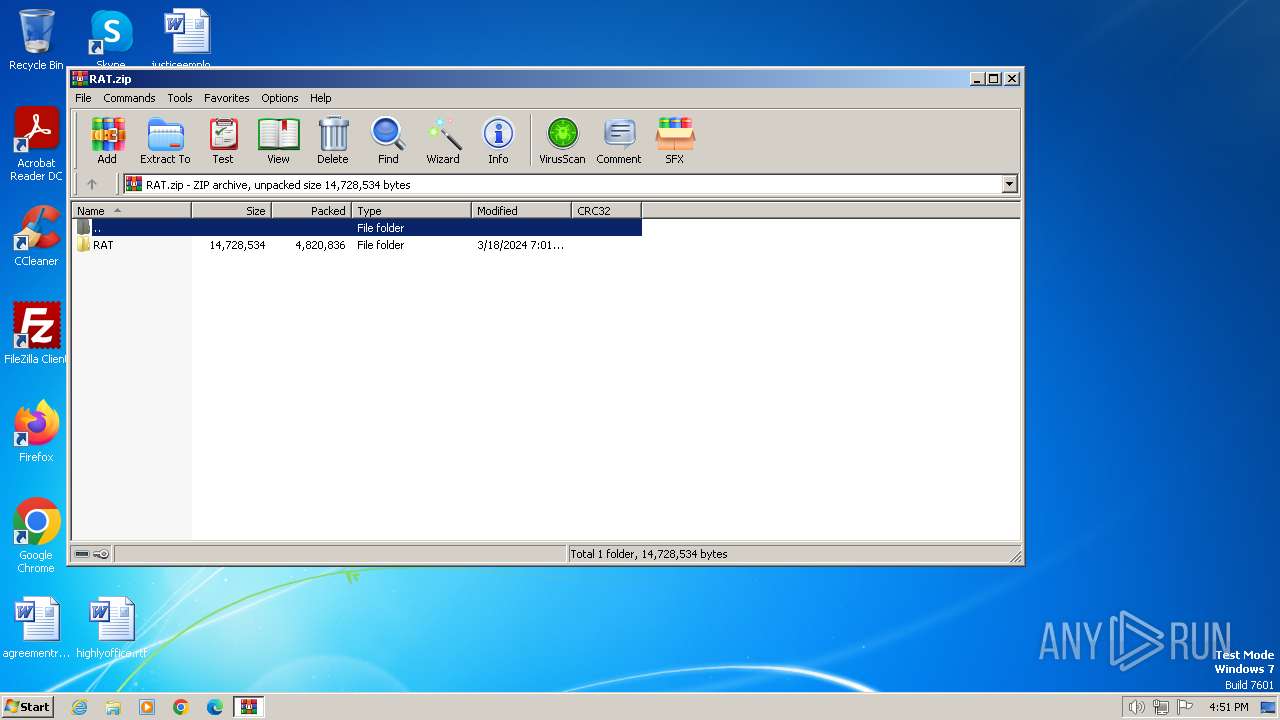
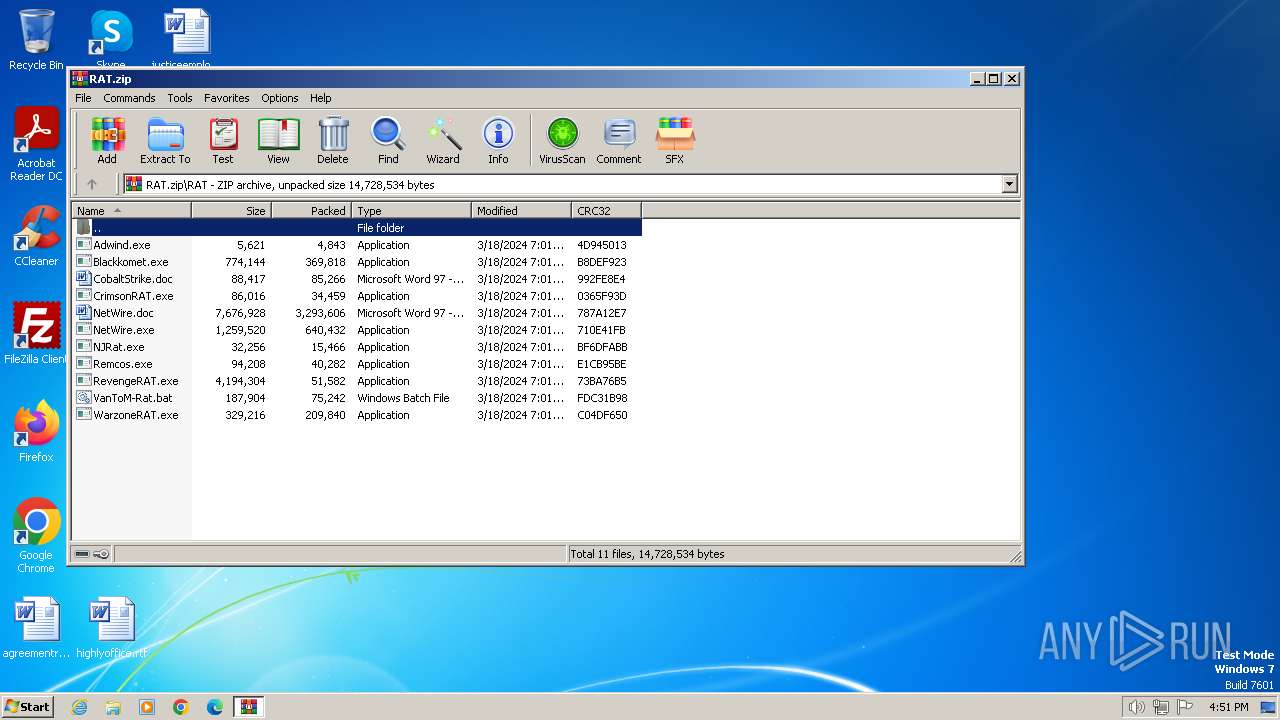
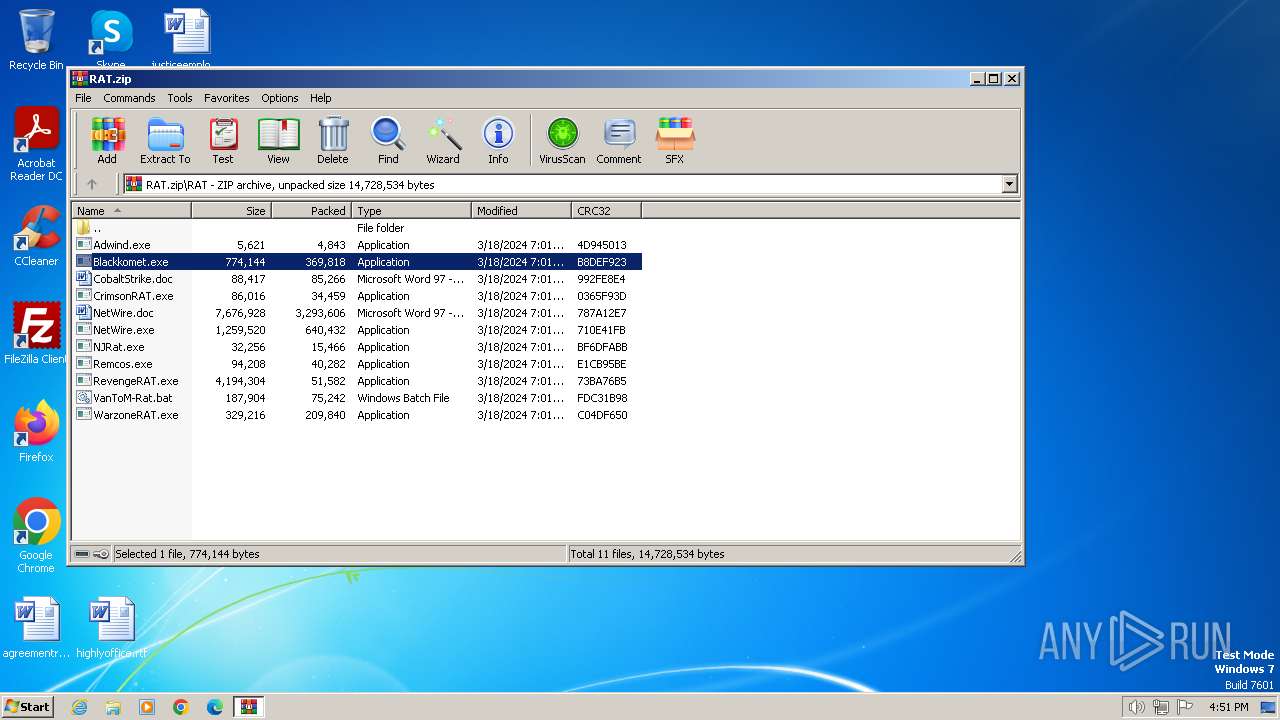
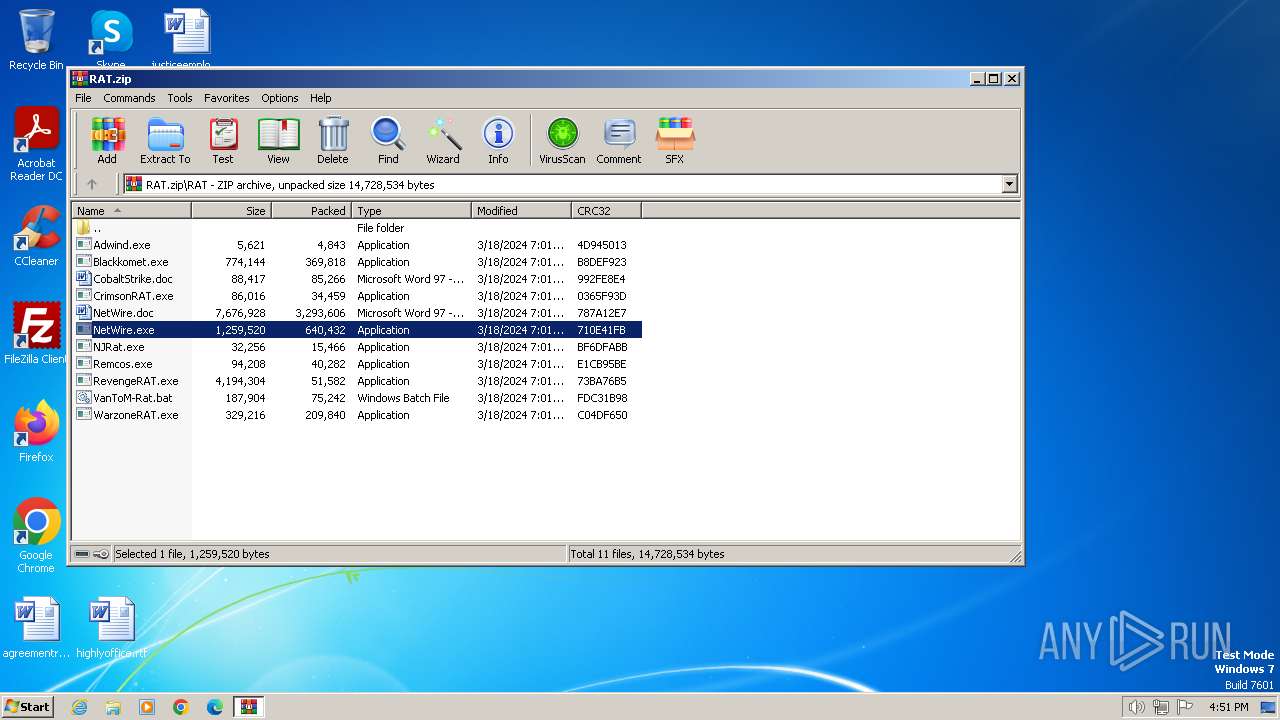
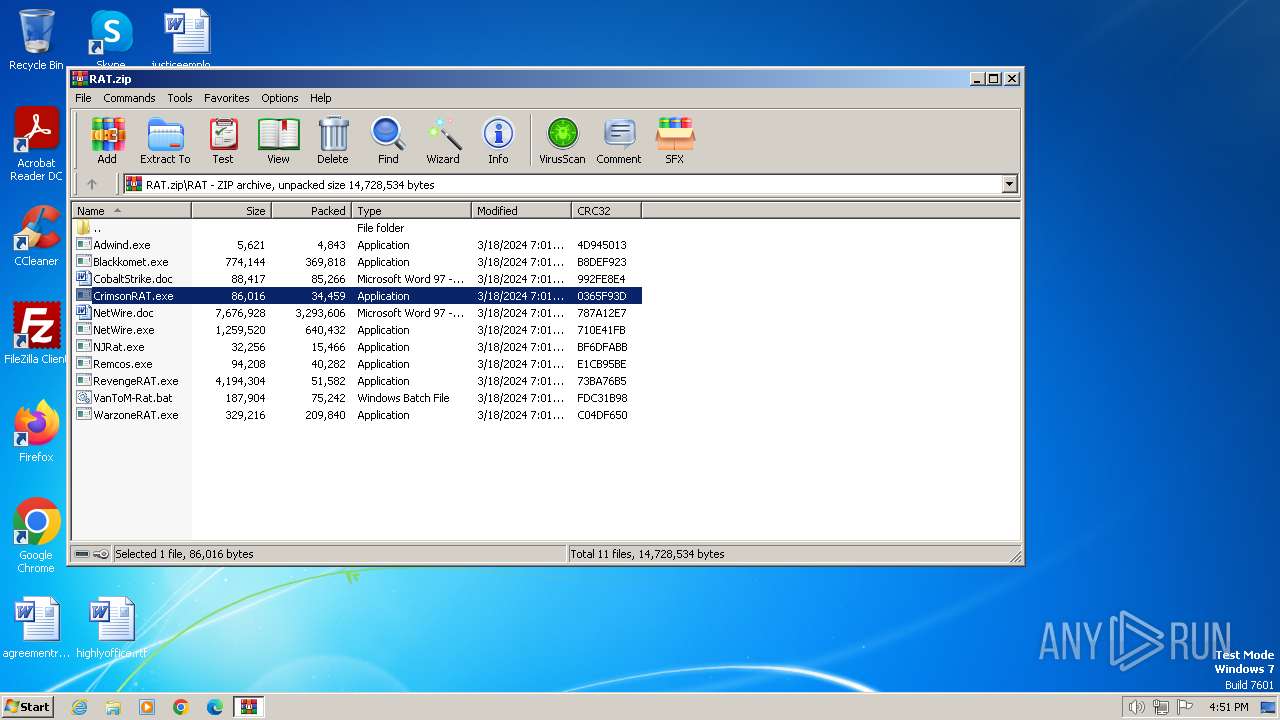
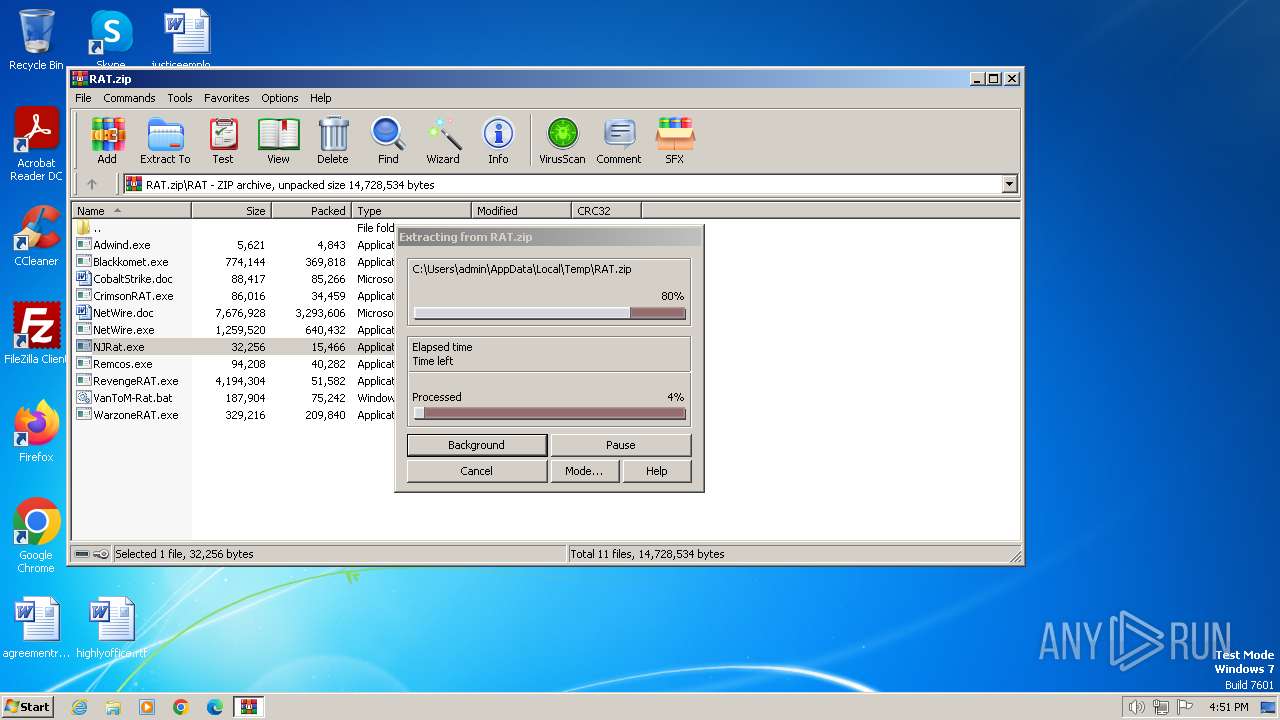
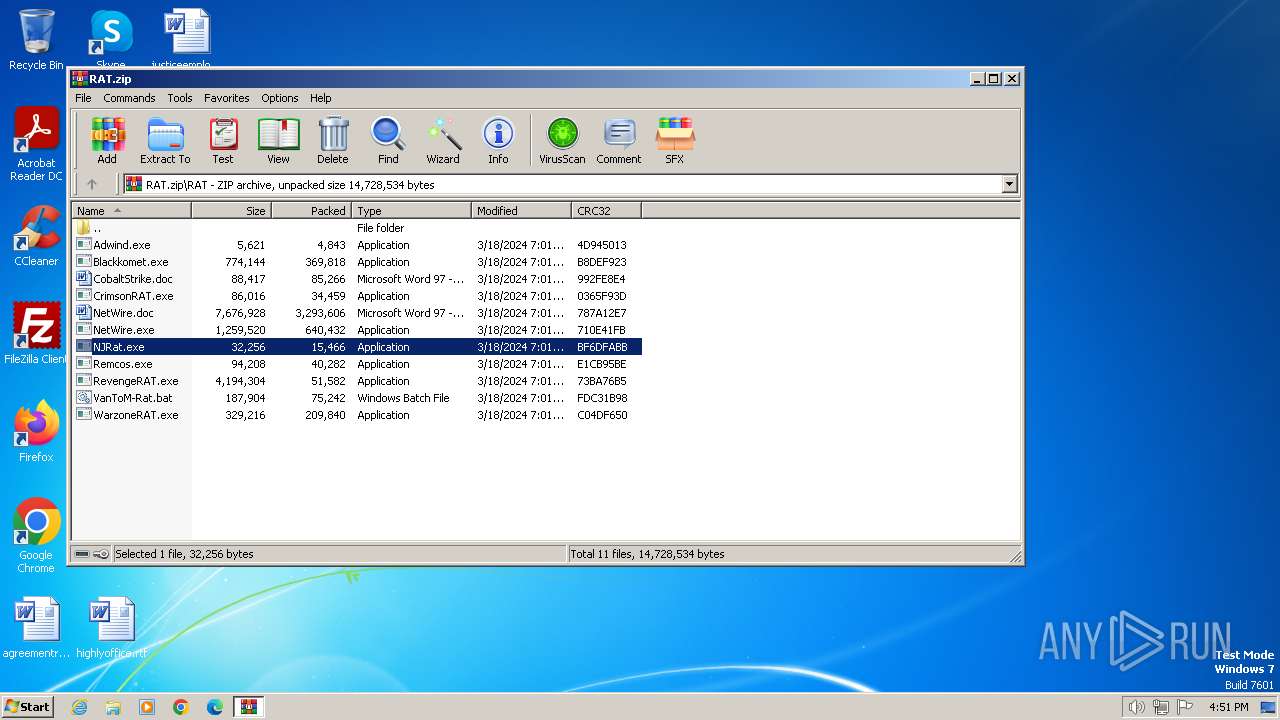
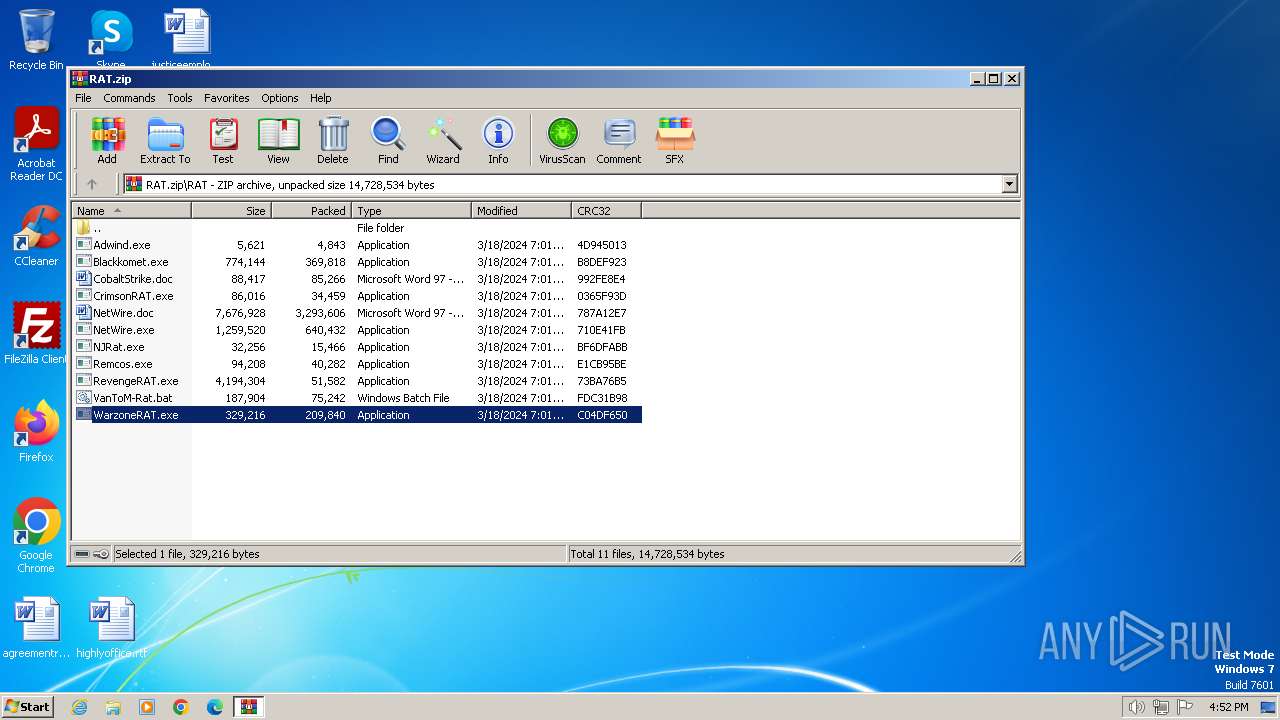
| File name: | RAT.zip |
| Full analysis: | https://app.any.run/tasks/cb51095e-b2d5-411e-9313-d87fa6865c82 |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | March 23, 2024, 16:51:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | F3EECB42442E3DA5480E58B5FBA66EFD |
| SHA1: | 13CE038C499BAD488DD0602BFE6804EF4AB927FF |
| SHA256: | 1B8D5A8D61CA502589461A1D50D925CCBE747425C75E92BCB39E5F3BD8799C5E |
| SSDEEP: | 98304:YL5KE0tQhO9qhD4OI0LK/fe+yhYURtLH2xCc3QVlNnLKomQsjVs3DI8WG3FKrSUc:rJ19vq+rDIuCp/u8 |
MALICIOUS
Changes the login/logoff helper path in the registry
- Blackkomet.exe (PID: 1836)
- Blackkomet.exe (PID: 1604)
- Blackkomet.exe (PID: 1732)
- Blackkomet.exe (PID: 3416)
Changes the autorun value in the registry
- Blackkomet.exe (PID: 1836)
- notepad.exe (PID: 2648)
- Remcos.exe (PID: 1112)
- Server.exe (PID: 3680)
- VanToM-Rat.bat (PID: 2100)
- Userdata.exe (PID: 1624)
- Blackkomet.exe (PID: 1604)
- notepad.exe (PID: 1424)
- Blackkomet.exe (PID: 3416)
- notepad.exe (PID: 1288)
- Blackkomet.exe (PID: 1732)
- notepad.exe (PID: 3040)
- NetWire.exe (PID: 2364)
- NJRat.exe (PID: 2228)
- NetWire.exe (PID: 4544)
- NetWire.exe (PID: 4036)
Remcos is detected
- Remcos.exe (PID: 2208)
- Userdata.exe (PID: 1624)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 120)
- Remcos.exe (PID: 1112)
- VanToM-Rat.bat (PID: 2100)
- WarzoneRAT.exe (PID: 448)
- CrimsonRAT.exe (PID: 3140)
- NetWire.exe (PID: 2364)
- NJRat.exe (PID: 2228)
- cmd.exe (PID: 1932)
UAC/LUA settings modification
- reg.exe (PID: 1308)
- reg.exe (PID: 1792)
- reg.exe (PID: 480)
Actions looks like stealing of personal data
- VanToM-Rat.bat (PID: 2100)
- Server.exe (PID: 3680)
Steals credentials from Web Browsers
- VanToM-Rat.bat (PID: 2100)
- Server.exe (PID: 3680)
Creates a writable file in the system directory
- Remcos.exe (PID: 1112)
- iexplore.exe (PID: 2324)
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 2324)
MEGARAT has been detected (SURICATA)
- Server.exe (PID: 3680)
Connects to the CnC server
- Server.exe (PID: 3680)
NjRAT is detected
- NJRat.exe (PID: 2228)
- NJRat.exe (PID: 2964)
Netwire is detected
- rasphone.exe (PID: 952)
Create files in the Startup directory
- NJRat.exe (PID: 2228)
NJRAT has been detected (YARA)
- NJRat.exe (PID: 2228)
SUSPICIOUS
Start notepad (likely ransomware note)
- Blackkomet.exe (PID: 1836)
- Blackkomet.exe (PID: 1604)
- Blackkomet.exe (PID: 3416)
- Blackkomet.exe (PID: 1732)
- NetWire.exe (PID: 2364)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 120)
- Remcos.exe (PID: 2208)
- Remcos.exe (PID: 1112)
- VanToM-Rat.bat (PID: 2100)
- WarzoneRAT.exe (PID: 2396)
- WarzoneRAT.exe (PID: 448)
- CrimsonRAT.exe (PID: 3140)
- CrimsonRAT.exe (PID: 1956)
- WarzoneRAT.exe (PID: 3100)
Uses ATTRIB.EXE to modify file attributes
- Blackkomet.exe (PID: 1836)
- Blackkomet.exe (PID: 1604)
- Blackkomet.exe (PID: 3416)
- Blackkomet.exe (PID: 1732)
Suspicious files were dropped or overwritten
- WinRAR.exe (PID: 120)
Connects to unusual port
- Blackkomet.exe (PID: 1836)
- Server.exe (PID: 3680)
- MSBuild.exe (PID: 2568)
- dlrarhsiva.exe (PID: 532)
- dlrarhsiva.exe (PID: 1504)
Application launched itself
- NetWire.exe (PID: 1496)
- NetWire.exe (PID: 3816)
- NetWire.exe (PID: 4520)
Reads the Internet Settings
- NetWire.exe (PID: 1496)
- eventvwr.exe (PID: 1572)
- Remcos.exe (PID: 2208)
- Remcos.exe (PID: 1112)
- VanToM-Rat.bat (PID: 2100)
- Server.exe (PID: 3680)
- WarzoneRAT.exe (PID: 448)
- WarzoneRAT.exe (PID: 2396)
- CrimsonRAT.exe (PID: 3140)
- CrimsonRAT.exe (PID: 1956)
- NetWire.exe (PID: 2364)
- NetWire.exe (PID: 4520)
- NetWire.exe (PID: 3816)
- NetWire.exe (PID: 4036)
- NetWire.exe (PID: 4544)
- WarzoneRAT.exe (PID: 3100)
Executable content was dropped or overwritten
- Remcos.exe (PID: 1112)
- VanToM-Rat.bat (PID: 2100)
- WarzoneRAT.exe (PID: 448)
- CrimsonRAT.exe (PID: 3140)
- NJRat.exe (PID: 2228)
- NetWire.exe (PID: 2364)
- notepad.exe (PID: 1432)
- cmd.exe (PID: 1932)
Starts CMD.EXE for commands execution
- Remcos.exe (PID: 1112)
- Userdata.exe (PID: 1624)
- notepad.exe (PID: 1432)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2900)
- cmd.exe (PID: 2632)
- cmd.exe (PID: 1728)
- cmd.exe (PID: 3528)
Executing commands from a ".bat" file
- Remcos.exe (PID: 1112)
- notepad.exe (PID: 1432)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2388)
Starts application with an unusual extension
- WinRAR.exe (PID: 120)
Starts itself from another location
- VanToM-Rat.bat (PID: 2100)
Reads settings of System Certificates
- NetWire.exe (PID: 2364)
- NetWire.exe (PID: 4544)
- NetWire.exe (PID: 4036)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 3528)
- reg.exe (PID: 3504)
- cmd.exe (PID: 1932)
Uses NETSH.EXE to add a firewall rule or allowed programs
- NJRat.exe (PID: 2228)
Process drops legitimate windows executable
- notepad.exe (PID: 1432)
- cmd.exe (PID: 1932)
INFO
Checks supported languages
- Blackkomet.exe (PID: 1836)
- NetWire.exe (PID: 1496)
- NetWire.exe (PID: 2364)
- Remcos.exe (PID: 2208)
- Remcos.exe (PID: 3508)
- Remcos.exe (PID: 1112)
- VanToM-Rat.bat (PID: 2100)
- Server.exe (PID: 3680)
- Userdata.exe (PID: 1624)
- WarzoneRAT.exe (PID: 448)
- MSBuild.exe (PID: 948)
- MSBuild.exe (PID: 2568)
- WarzoneRAT.exe (PID: 2396)
- CrimsonRAT.exe (PID: 3140)
- CrimsonRAT.exe (PID: 1956)
- dlrarhsiva.exe (PID: 1504)
- Blackkomet.exe (PID: 1604)
- Blackkomet.exe (PID: 1732)
- dlrarhsiva.exe (PID: 532)
- Blackkomet.exe (PID: 3416)
- NJRat.exe (PID: 2228)
- NetWire.exe (PID: 3816)
- NetWire.exe (PID: 4036)
- NetWire.exe (PID: 4520)
- NJRat.exe (PID: 2964)
- NetWire.exe (PID: 4544)
- MSBuild.exe (PID: 2268)
- WarzoneRAT.exe (PID: 3100)
Reads the computer name
- Blackkomet.exe (PID: 1836)
- NetWire.exe (PID: 1496)
- NetWire.exe (PID: 2364)
- Remcos.exe (PID: 2208)
- VanToM-Rat.bat (PID: 2100)
- Remcos.exe (PID: 1112)
- Server.exe (PID: 3680)
- WarzoneRAT.exe (PID: 448)
- MSBuild.exe (PID: 2568)
- WarzoneRAT.exe (PID: 2396)
- MSBuild.exe (PID: 948)
- CrimsonRAT.exe (PID: 3140)
- CrimsonRAT.exe (PID: 1956)
- dlrarhsiva.exe (PID: 532)
- Blackkomet.exe (PID: 1604)
- Blackkomet.exe (PID: 1732)
- dlrarhsiva.exe (PID: 1504)
- Blackkomet.exe (PID: 3416)
- NJRat.exe (PID: 2228)
- NetWire.exe (PID: 3816)
- NetWire.exe (PID: 4036)
- NetWire.exe (PID: 4544)
- NetWire.exe (PID: 4520)
- NJRat.exe (PID: 2964)
- MSBuild.exe (PID: 2268)
- WarzoneRAT.exe (PID: 3100)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 120)
Checks proxy server information
- NetWire.exe (PID: 1496)
- NetWire.exe (PID: 2364)
- NetWire.exe (PID: 4520)
- NetWire.exe (PID: 3816)
- NetWire.exe (PID: 4036)
- NetWire.exe (PID: 4544)
Reads product name
- Remcos.exe (PID: 2208)
- Remcos.exe (PID: 1112)
- Userdata.exe (PID: 1624)
Reads security settings of Internet Explorer
- eventvwr.exe (PID: 1572)
Reads the machine GUID from the registry
- VanToM-Rat.bat (PID: 2100)
- Server.exe (PID: 3680)
- WarzoneRAT.exe (PID: 448)
- WarzoneRAT.exe (PID: 2396)
- CrimsonRAT.exe (PID: 3140)
- CrimsonRAT.exe (PID: 1956)
- dlrarhsiva.exe (PID: 532)
- dlrarhsiva.exe (PID: 1504)
- NetWire.exe (PID: 2364)
- NJRat.exe (PID: 2964)
- NJRat.exe (PID: 2228)
- NetWire.exe (PID: 4544)
- NetWire.exe (PID: 4036)
- WarzoneRAT.exe (PID: 3100)
Create files in a temporary directory
- Remcos.exe (PID: 1112)
- VanToM-Rat.bat (PID: 2100)
- Server.exe (PID: 3680)
- WarzoneRAT.exe (PID: 2396)
- WarzoneRAT.exe (PID: 448)
- WarzoneRAT.exe (PID: 3100)
Reads Environment values
- Remcos.exe (PID: 1112)
- Remcos.exe (PID: 2208)
- Server.exe (PID: 3680)
- Userdata.exe (PID: 1624)
- NJRat.exe (PID: 2228)
Creates files or folders in the user directory
- VanToM-Rat.bat (PID: 2100)
- WarzoneRAT.exe (PID: 448)
- NetWire.exe (PID: 2364)
- NJRat.exe (PID: 2228)
Creates files in the program directory
- CrimsonRAT.exe (PID: 3140)
- CrimsonRAT.exe (PID: 1956)
Reads the software policy settings
- NetWire.exe (PID: 2364)
- NetWire.exe (PID: 4036)
- NetWire.exe (PID: 4544)
Drops the executable file immediately after the start
- notepad.exe (PID: 1432)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
NjRat
(PID) Process(2228) NJRat.exe
C2startitit2-23969.portmap.host
Ports1604
BotnetGeforce
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\b9584a316aeb9ca9b31edd4db18381f5
SplitterY262SUCZ4UJJ
Version0.7d
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:03:18 19:01:10 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | RAT/ |
Total processes
123
Monitored processes
67
Malicious processes
27
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\RAT.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 448 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18551\RAT\WarzoneRAT.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18551\RAT\WarzoneRAT.exe | WinRAR.exe | ||||||||||||
User: admin Company: Corporate social responsibility. Integrity Level: MEDIUM Description: Moral responsibility Exit code: 0 Version: 31.0.0.0 Modules
| |||||||||||||||
| 480 | C:\Windows\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 532 | "C:\ProgramData\Hdlharas\dlrarhsiva.exe" | C:\ProgramData\Hdlharas\dlrarhsiva.exe | CrimsonRAT.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: dlrarhsiva Version: 1.0.0.0 Modules
| |||||||||||||||
| 948 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | WarzoneRAT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 952 | "C:\Windows\System32\rasphone.exe" | C:\Windows\System32\rasphone.exe | NetWire.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Access Phonebook Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1112 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18367\RAT\Remcos.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18367\RAT\Remcos.exe | eventvwr.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1288 | notepad | C:\Windows\System32\notepad.exe | Blackkomet.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1308 | C:\Windows\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1424 | notepad | C:\Windows\System32\notepad.exe | Blackkomet.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
31 280
Read events
30 962
Write events
302
Delete events
16
Modification events
| (PID) Process: | (120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (120) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RAT.zip | |||
| (PID) Process: | (120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
155
Suspicious files
19
Text files
11
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18158\RAT\NetWire.doc | — | |
MD5:— | SHA256:— | |||
| 120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18295\RAT\NetWire.doc | — | |
MD5:— | SHA256:— | |||
| 120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18158\RAT\Adwind.exe | java | |
MD5:FE537A3346590C04D81D357E3C4BE6E8 | SHA256:BBC572CCED7C94D63A7208F4ABA4ED20D1350BEF153B099035A86C95C8D96D4A | |||
| 120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18158\RAT\CobaltStrike.doc | document | |
MD5:96FF9D4CAC8D3A8E73C33FC6BF72F198 | SHA256:96DB5D52F4ADDF46B0A41D45351A52041D9E5368AEAD642402DB577BCB33CC3D | |||
| 120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18158\RAT\WarzoneRAT.exe | executable | |
MD5:600E0DBAEFC03F7BF50ABB0DEF3FB465 | SHA256:61E6A93F43049712B5F2D949FD233FA8015FE4BEF01B9E1285D3D87B12F894F2 | |||
| 120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18367\RAT\NetWire.doc | — | |
MD5:— | SHA256:— | |||
| 120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18158\RAT\RevengeRAT.exe | executable | |
MD5:1D9045870DBD31E2E399A4E8ECD9302F | SHA256:9B4826B8876CA2F1378B1DFE47B0C0D6E972BF9F0B3A36E299B26FBC86283885 | |||
| 120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18295\RAT\Adwind.exe | java | |
MD5:FE537A3346590C04D81D357E3C4BE6E8 | SHA256:BBC572CCED7C94D63A7208F4ABA4ED20D1350BEF153B099035A86C95C8D96D4A | |||
| 120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18295\RAT\Remcos.exe | executable | |
MD5:FB598B93C04BAAFE98683DC210E779C9 | SHA256:C851749FD6C9FA19293D8EE2C5B45B3DC8561115DDFE7166FBAEFCB9B353B7C4 | |||
| 120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa120.18158\RAT\Remcos.exe | executable | |
MD5:FB598B93C04BAAFE98683DC210E779C9 | SHA256:C851749FD6C9FA19293D8EE2C5B45B3DC8561115DDFE7166FBAEFCB9B353B7C4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
47
DNS requests
6
Threats
11
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1836 | Blackkomet.exe | 193.242.166.48:1605 | — | Fop Iliushenko Volodymyr Olexandrovuch | UA | unknown |
3680 | Server.exe | 193.161.193.99:22603 | — | OOO Bitree Networks | RU | malicious |
2568 | MSBuild.exe | 168.61.222.215:5400 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | malicious |
2364 | NetWire.exe | 142.250.179.142:443 | drive.google.com | GOOGLE | US | whitelisted |
2364 | NetWire.exe | 142.251.39.97:443 | drive.usercontent.google.com | GOOGLE | US | whitelisted |
4036 | NetWire.exe | 142.250.179.142:443 | drive.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nickman12-46565.portmap.io |
| unknown |
drive.google.com |
| shared |
drive.usercontent.google.com |
| unknown |
tamerimia.ug |
| unknown |
startitit2-23969.portmap.host |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query to a Reverse Proxy Service Observed |
1080 | svchost.exe | Misc activity | ET INFO DNS Query for Port Mapping/Tunneling Service Domain (.portmap .io) |
1080 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query to a Reverse Proxy Service Observed |
1080 | svchost.exe | Misc activity | ET INFO DNS Query for Port Mapping/Tunneling Service Domain (.portmap .io) |
— | — | A Network Trojan was detected | ET MALWARE Backdoor.Win32.DarkComet Keepalive Outbound |
1080 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query to a Reverse Proxy Service Observed |
1080 | svchost.exe | Misc activity | ET INFO DNS Query for Port Mapping/Tunneling Service Domain (.portmap .host) |
— | — | A Network Trojan was detected | ET MALWARE Backdoor.Win32.DarkComet Keepalive Outbound |
— | — | A Network Trojan was detected | ET MALWARE Backdoor.Win32.DarkComet Keepalive Outbound |
2 ETPRO signatures available at the full report