| File name: | CritScript.exe |
| Full analysis: | https://app.any.run/tasks/1a5bdac2-2bb1-4a83-9508-2b1f914a0f20 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | December 13, 2024, 11:15:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | C28DC010FC5198442496BC07DD50CD5D |
| SHA1: | 0F90A005815C2700A65EA85AE86F13A182CC11E6 |
| SHA256: | 1B701DADED4124260A49040D83DEC15C627B8E4A1A04DC378AAE7FECFCA3ABF3 |
| SSDEEP: | 98304:W02NkKCmRf7uY1+DVlYZ+hHaIDgsTA2K:JXgs1 |
MALICIOUS
Changes the autorun value in the registry
- JUSCHED.EXE (PID: 936)
- jusched.exe (PID: 6300)
QUASAR has been detected (YARA)
- jusched.exe (PID: 6300)
SUSPICIOUS
Executable content was dropped or overwritten
- JUSCHED.EXE (PID: 936)
- CritScript.exe (PID: 4300)
Reads security settings of Internet Explorer
- CritScript.exe (PID: 4300)
Starts itself from another location
- JUSCHED.EXE (PID: 936)
Connects to unusual port
- jusched.exe (PID: 6300)
INFO
Sends debugging messages
- CritScript.exe (PID: 4300)
- Acrobat.exe (PID: 5308)
Checks supported languages
- CritScript.exe (PID: 4300)
- JUSCHED.EXE (PID: 936)
- jusched.exe (PID: 6300)
Reads the computer name
- CritScript.exe (PID: 4300)
- JUSCHED.EXE (PID: 936)
- jusched.exe (PID: 6300)
Process checks computer location settings
- CritScript.exe (PID: 4300)
Create files in a temporary directory
- CritScript.exe (PID: 4300)
Reads the machine GUID from the registry
- JUSCHED.EXE (PID: 936)
- jusched.exe (PID: 6300)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 3544)
Reads Environment values
- JUSCHED.EXE (PID: 936)
- jusched.exe (PID: 6300)
The process uses the downloaded file
- CritScript.exe (PID: 4300)
- jusched.exe (PID: 6300)
- OpenWith.exe (PID: 3544)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 3544)
Application launched itself
- Acrobat.exe (PID: 3988)
- AcroCEF.exe (PID: 3836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(6300) jusched.exe
Version1.4.1
C2 (2)193.161.193.99:32471
Sub_DirJava
Install_Namejusched.exe
Mutex807f3187-d087-4fff-beff-e73293a32af8
StartupJava Update Scheduler
TagDDNS
LogDirCachedLogs
SignaturesBocLBRxMUw3To7ZzewZ3YsrO0Z+fc3KsRzMzv9mfbF5sJ1MJ+tSUeK3n4v0qA9CdzuiNoXDrsMLx0lNGdFJEPGAtWXTb1QPmup0gzzxZYzgUjbW3K6OUlQnrnCRJ5B/gVJhvjpeytHJcJXoVVThOCBhfRHkUdKjWvea5McjXDhUWz1Xu7FF9MqOxPols3wY2Arj/mHwFcuAzhnR5Fg27eVVh2bANkzob/YNZrH+PoUvxMthySf1+JI28o0Nzl9a/PDUUuq4nPq78M0M4glGmHqp4kgCf57NRQhEjF8nTyIm...
CertificateMIIE9DCCAtygAwIBAgIQAKdj9OEEtK/PmVn/2IlEdTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MTExMjA2MTQxN1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAt79yvi82zMkZkRdUuCBbnaQ9a7fqidLALKNd/BEjRKS1OWiYAzTf9ZzAK1K+kOAeePTlezhU...
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:07:03 09:05:04+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 31232 |
| InitializedDataSize: | 3300352 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3248 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
138
Monitored processes
14
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 936 | "C:\Users\admin\AppData\Local\Temp\JUSCHED.EXE" | C:\Users\admin\AppData\Local\Temp\JUSCHED.EXE | CritScript.exe | ||||||||||||
User: admin Company: Oracle Integrity Level: MEDIUM Description: Java Update Scheduler Exit code: 3 Version: 8.0.202.8 Modules
| |||||||||||||||
| 2212 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --first-renderer-process --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2276 --field-trial-handle=1628,i,5717160820309607937,18008752180860803824,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2220 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2708 --field-trial-handle=1628,i,5717160820309607937,18008752180860803824,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 3260 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1652 --field-trial-handle=1628,i,5717160820309607937,18008752180860803824,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 3544 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3836 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
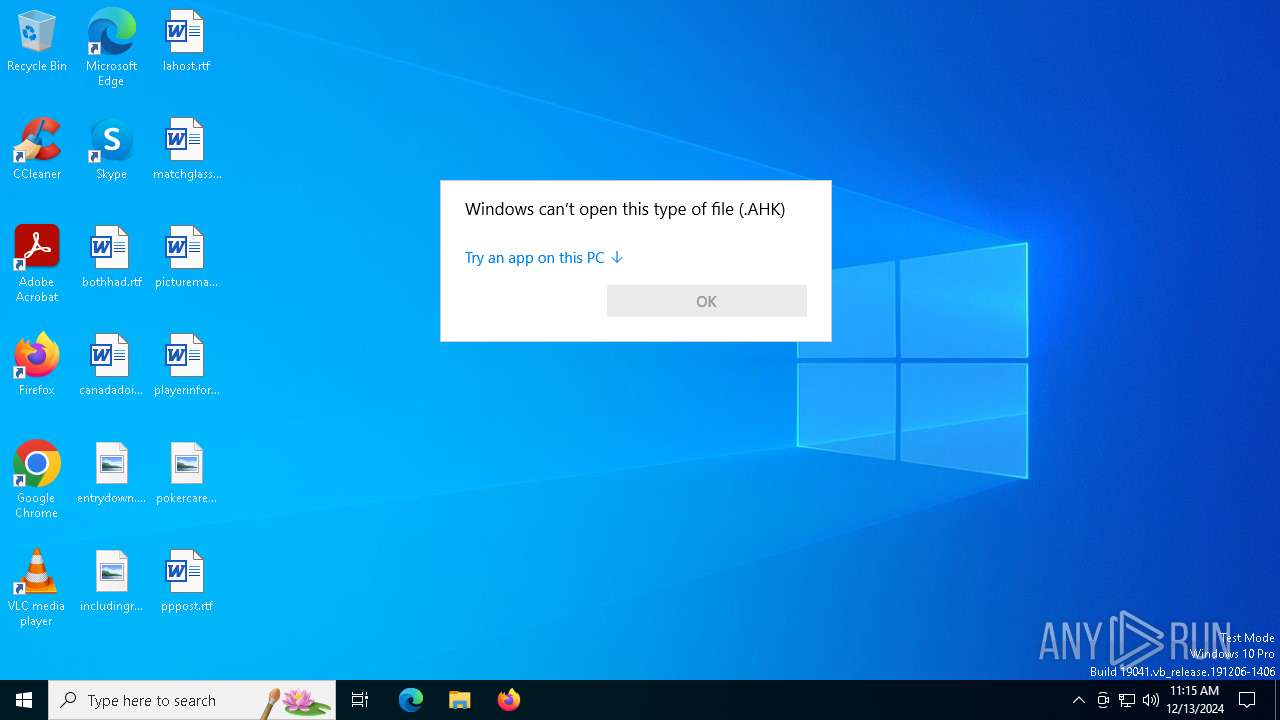
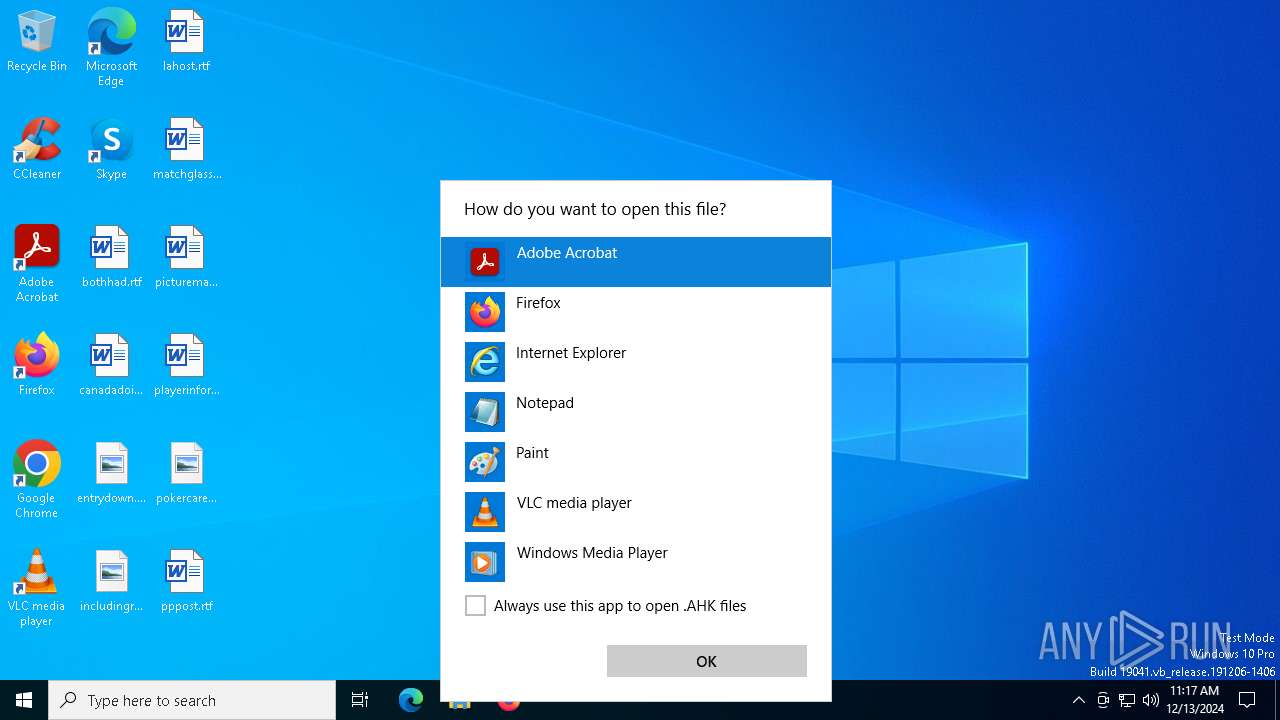
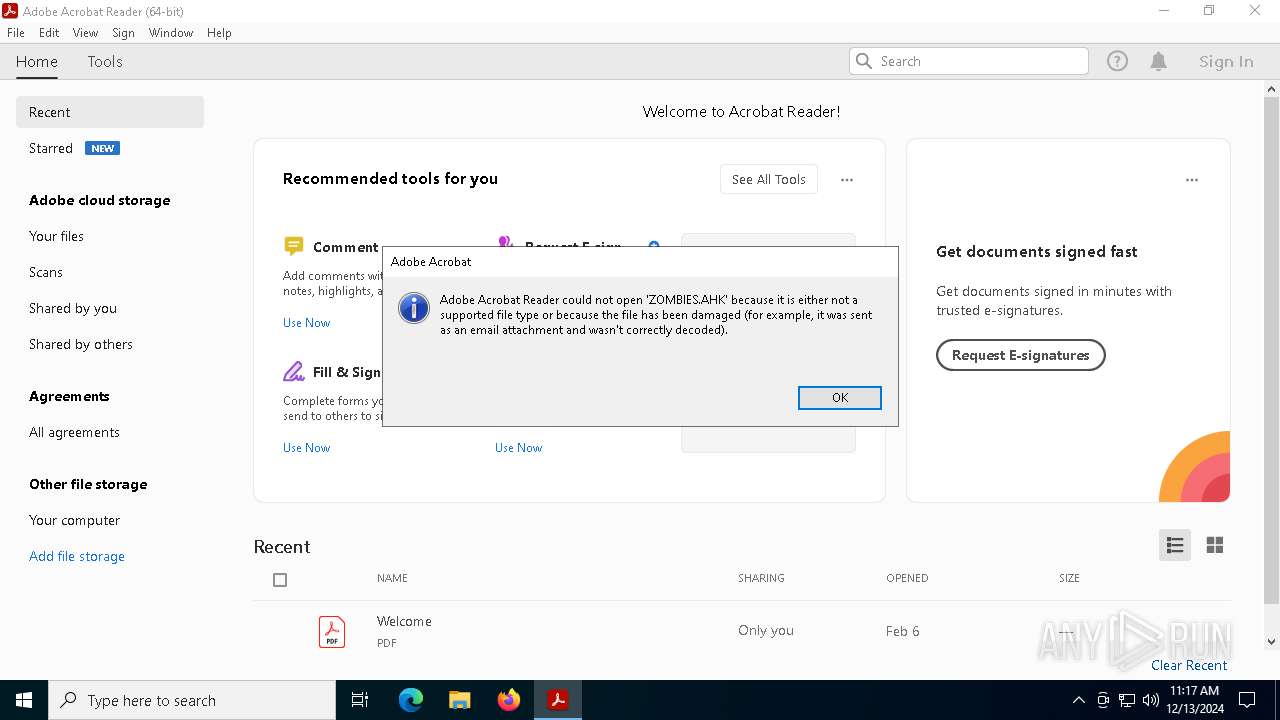
| 3988 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" "C:\Users\admin\AppData\Local\Temp\ZOMBIES.AHK" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 4300 | "C:\Users\admin\AppData\Local\Temp\CritScript.exe" | C:\Users\admin\AppData\Local\Temp\CritScript.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 5308 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\AppData\Local\Temp\ZOMBIES.AHK" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 6300 | "C:\Users\admin\AppData\Roaming\Java\jusched.exe" | C:\Users\admin\AppData\Roaming\Java\jusched.exe | JUSCHED.EXE | ||||||||||||
User: admin Company: Oracle Integrity Level: MEDIUM Description: Java Update Scheduler Version: 8.0.202.8 Modules
Quasar(PID) Process(6300) jusched.exe Version1.4.1 C2 (2)193.161.193.99:32471 Sub_DirJava Install_Namejusched.exe Mutex807f3187-d087-4fff-beff-e73293a32af8 StartupJava Update Scheduler TagDDNS LogDirCachedLogs SignaturesBocLBRxMUw3To7ZzewZ3YsrO0Z+fc3KsRzMzv9mfbF5sJ1MJ+tSUeK3n4v0qA9CdzuiNoXDrsMLx0lNGdFJEPGAtWXTb1QPmup0gzzxZYzgUjbW3K6OUlQnrnCRJ5B/gVJhvjpeytHJcJXoVVThOCBhfRHkUdKjWvea5McjXDhUWz1Xu7FF9MqOxPols3wY2Arj/mHwFcuAzhnR5Fg27eVVh2bANkzob/YNZrH+PoUvxMthySf1+JI28o0Nzl9a/PDUUuq4nPq78M0M4glGmHqp4kgCf57NRQhEjF8nTyIm... CertificateMIIE9DCCAtygAwIBAgIQAKdj9OEEtK/PmVn/2IlEdTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MTExMjA2MTQxN1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAt79yvi82zMkZkRdUuCBbnaQ9a7fqidLALKNd/BEjRKS1OWiYAzTf9ZzAK1K+kOAeePTlezhU... | |||||||||||||||
Total events
10 694
Read events
10 677
Write events
15
Delete events
2
Modification events
| (PID) Process: | (936) JUSCHED.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Java Update Scheduler |
Value: "C:\Users\admin\AppData\Roaming\Java\jusched.exe" | |||
| (PID) Process: | (6300) jusched.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Java Update Scheduler |
Value: "C:\Users\admin\AppData\Roaming\Java\jusched.exe" | |||
| (PID) Process: | (3988) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (5308) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (5308) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | bSynchronizeOPL |
Value: 0 | |||
| (PID) Process: | (5308) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: | |||
| (PID) Process: | (5308) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | iNumAcrobatLaunches |
Value: 7 | |||
| (PID) Process: | (5308) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\HomeWelcomeFirstMile |
| Operation: | write | Name: | iCardCountShown |
Value: 3 | |||
| (PID) Process: | (5308) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\DLLInjection |
| Operation: | write | Name: | bBlockDLLInjection |
Value: 0 | |||
| (PID) Process: | (5308) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | sProductGUID |
Value: 4143524F4241545F475549445F4E474C5F44554D4D5900 | |||
Executable files
2
Suspicious files
96
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4300 | CritScript.exe | C:\Users\admin\AppData\Local\Temp\ZOMBIES.AHK | text | |
MD5:4378EC2852917FED7F557291E72251A6 | SHA256:2BA38AF1FFA558F31AF78AE94C3369D92366838D5CB1E5C01C58369BC92AC914 | |||
| 5308 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt23.lst.5308 | binary | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 4300 | CritScript.exe | C:\Users\admin\AppData\Local\Temp\JUSCHED.EXE | executable | |
MD5:BD4DCBDFDB5FDC1F95BD1168F166153A | SHA256:902BEA9E4AEEED4E0B5D30A9CBCC6F9F1FC687B79C3FDDE8258B94B410D1797A | |||
| 5308 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\acroNGLLog.txt | text | |
MD5:1929F35B21A8DE2A62EEE8B76A60AA06 | SHA256:B4DBDE948F15BD3D9691949DFC385B256278D93CA9AE5C3FA5F9A633A57AEC6C | |||
| 5308 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | mp3 | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 3988 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst | binary | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 936 | JUSCHED.EXE | C:\Users\admin\AppData\Roaming\Java\jusched.exe | executable | |
MD5:BD4DCBDFDB5FDC1F95BD1168F166153A | SHA256:902BEA9E4AEEED4E0B5D30A9CBCC6F9F1FC687B79C3FDDE8258B94B410D1797A | |||
| 5308 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
| 5308 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\NGL\NGLClient_AcrobatReader123.1.20093.6 2024-12-13 11-17-45-329.log | text | |
MD5:460C6041966002D8384A18C895A65EB0 | SHA256:C83EC6E8FB3EC62481289C033238C1D9B08DB8076EAAD304099FD7A7F594F1B9 | |||
| 3836 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:B96B53CEA6476E74340C3A76E7ECA23F | SHA256:858DC58847D22B40476217297FB6BBD1424DC3B43AB9EF03B606029073E2C3EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
135
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1684 | svchost.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1684 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6976 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6488 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6976 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6488 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5064 | SearchApp.exe | 2.23.209.140:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1684 | svchost.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1684 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1684 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6300 | jusched.exe | 193.161.193.99:32471 | — | OOO Bitree Networks | RU | malicious |
5064 | SearchApp.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
CritScript.exe | C:\Users\admin\AppData\Local\Temp\JUSCHED.EXE |
CritScript.exe | C:\Users\admin\AppData\Local\Temp\ZOMBIES.AHK |