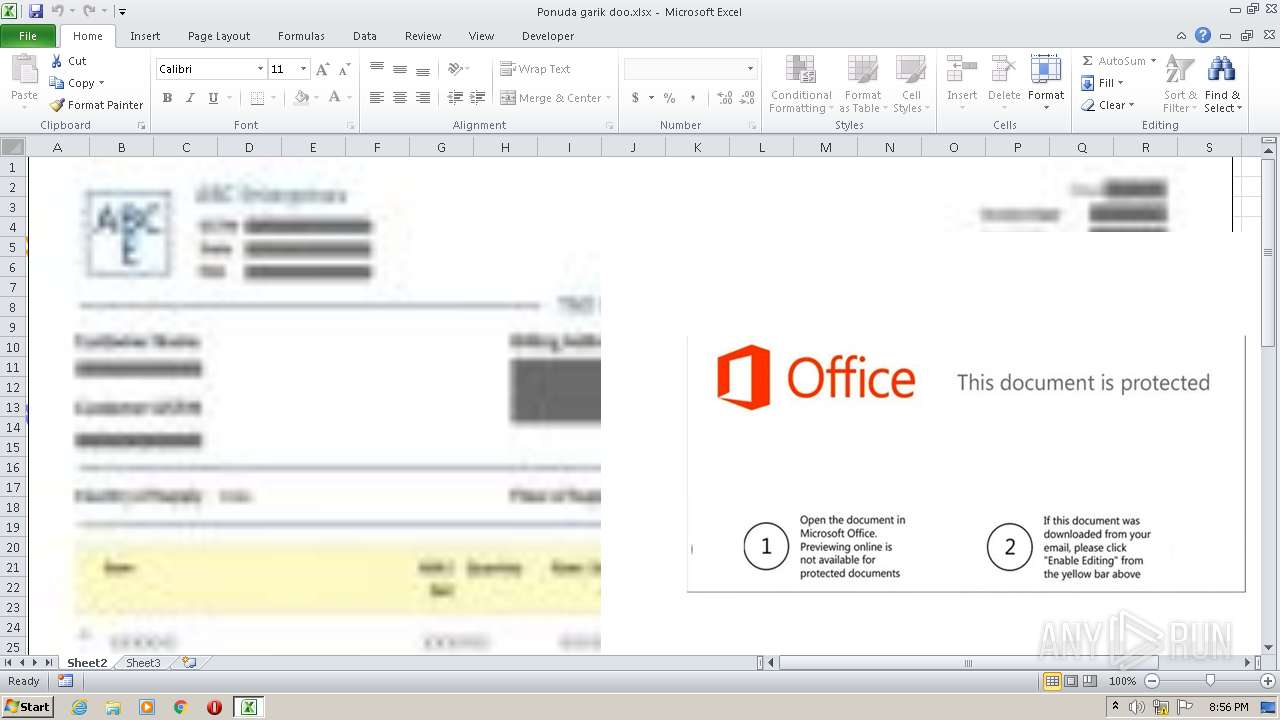
| File name: | Ponuda garik doo.xlsx |
| Full analysis: | https://app.any.run/tasks/6115b2b6-ad63-42da-8d55-ed4f1b7e23f1 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | May 20, 2022, 19:56:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/encrypted |
| File info: | CDFV2 Encrypted |
| MD5: | EB8FFCED9B86B28DE768FBBA330CD68F |
| SHA1: | C73335380259BCBCA94B7F9796810A2F95A479B3 |
| SHA256: | 1B06FCB2F19296DFB7B7410942E38280546AE1D8041CD18C04E0A6939A334EFC |
| SSDEEP: | 6144:Vx3NRgWG92wP7dMB3eU3LWZxGWP1d4iPxicd5T:Vx3NfGcwzdMhx3LWPRP7PPbdZ |
MALICIOUS
Drops executable file immediately after starts
- EQNEDT32.EXE (PID: 3460)
- vbc.exe (PID: 1840)
Application was dropped or rewritten from another process
- rdtykmwm.exe (PID: 2880)
- rdtykmwm.exe (PID: 2372)
- vbc.exe (PID: 1840)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3460)
FORMBOOK detected by memory dumps
- control.exe (PID: 3860)
Connects to CnC server
- Explorer.EXE (PID: 1464)
FORMBOOK was detected
- Explorer.EXE (PID: 1464)
SUSPICIOUS
Checks supported languages
- EQNEDT32.EXE (PID: 3460)
- rdtykmwm.exe (PID: 2372)
- vbc.exe (PID: 1840)
- rdtykmwm.exe (PID: 2880)
Reads the computer name
- EQNEDT32.EXE (PID: 3460)
- vbc.exe (PID: 1840)
- rdtykmwm.exe (PID: 2880)
Executable content was dropped or overwritten
- vbc.exe (PID: 1840)
- EQNEDT32.EXE (PID: 3460)
Executed via COM
- EQNEDT32.EXE (PID: 3460)
Drops a file with a compile date too recent
- EQNEDT32.EXE (PID: 3460)
- vbc.exe (PID: 1840)
Application launched itself
- rdtykmwm.exe (PID: 2372)
Starts CMD.EXE for commands execution
- control.exe (PID: 3860)
Reads Environment values
- control.exe (PID: 3860)
INFO
Reads the computer name
- EXCEL.EXE (PID: 2272)
- control.exe (PID: 3860)
Starts Microsoft Office Application
- Explorer.EXE (PID: 1464)
Checks supported languages
- EXCEL.EXE (PID: 2272)
- control.exe (PID: 3860)
- cmd.exe (PID: 3396)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2272)
Manual execution by user
- control.exe (PID: 3860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
42
Monitored processes
8
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1464 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1840 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | EQNEDT32.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2272 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2372 | C:\Users\admin\AppData\Local\Temp\rdtykmwm.exe C:\Users\admin\AppData\Local\Temp\xsrkd | C:\Users\admin\AppData\Local\Temp\rdtykmwm.exe | — | vbc.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2880 | C:\Users\admin\AppData\Local\Temp\rdtykmwm.exe C:\Users\admin\AppData\Local\Temp\xsrkd | C:\Users\admin\AppData\Local\Temp\rdtykmwm.exe | — | rdtykmwm.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3396 | /c del "C:\Users\admin\AppData\Local\Temp\rdtykmwm.exe" | C:\Windows\System32\cmd.exe | — | control.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3460 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 3860 | "C:\Windows\System32\control.exe" | C:\Windows\System32\control.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 950
Read events
1 865
Write events
74
Delete events
11
Modification events
| (PID) Process: | (1464) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000157665AB480A0F48AFBF088EC0A166E10000000002000000000010660000000100002000000005D407241D18A85CCD4FD1B567787386E23E219B67DBE19C57F578306FEF16EC000000000E8000000002000020000000883D01AFDC229A75D429A7D623DE04AA1908596291702AA69AA3F77A62B56F093000000000AA82B2E89E3500BD26088A47DDA0FC4A3AB0BD4570F3717748C252E39E9A23ECEFC7C543A6311E165B2E5179A70BE740000000C11976B3361451D62C488CE881E0EB90403E71EC965BCA5E5729E10683111647379ED305CDDA76699F1DB7A64DF34CCC2ED79B3B1948628EFEF0ED624A5576C3 | |||
| (PID) Process: | (2272) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | *73 |
Value: 2A373300E0080000010000000000000000000000 | |||
| (PID) Process: | (2272) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2272) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2272) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2272) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2272) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2272) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2272) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2272) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
Executable files
3
Suspicious files
3
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2272 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR932A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3460 | EQNEDT32.EXE | C:\Users\Public\vbc.exe | executable | |
MD5:— | SHA256:— | |||
| 1840 | vbc.exe | C:\Users\admin\AppData\Local\Temp\xsrkd | binary | |
MD5:— | SHA256:— | |||
| 1840 | vbc.exe | C:\Users\admin\AppData\Local\Temp\kseu5ei3unf56bhzq3m | binary | |
MD5:— | SHA256:— | |||
| 1840 | vbc.exe | C:\Users\admin\AppData\Local\Temp\rdtykmwm.exe | executable | |
MD5:— | SHA256:— | |||
| 3460 | EQNEDT32.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\vbc[1].exe | executable | |
MD5:— | SHA256:— | |||
| 1840 | vbc.exe | C:\Users\admin\AppData\Local\Temp\nsqA00B.tmp | binary | |
MD5:— | SHA256:— | |||
| 2272 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\2D4DCE52.emf | emf | |
MD5:— | SHA256:— | |||
| 2272 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\80AB9C55.emf | emf | |
MD5:8E3A74F7AA420B02D34C69E625969C0A | SHA256:0CD83C55739629F98FE6AFD3E25A5BCBB346CBEF58BC592C1260E9F0FA8575A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
15
DNS requests
17
Threats
62
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1464 | Explorer.EXE | GET | — | 198.54.117.211:80 | http://www.hdwallpaperpics.life/arh2/?7nwLw4F=2fLBB+Y67uycfdnUh5p6n4tsYqIPdJn/kRZ7Q2LGn/hgA/5Z2OZAje+lzWkj8hDL84A9SQ==&LXq4A=7nJTvP185r2XJ | US | — | — | malicious |
1464 | Explorer.EXE | GET | — | 76.164.193.184:80 | http://www.bakiin.com/arh2/?7nwLw4F=9rm22c60oDLfNuzsU7swWyedB6tiHSfc/GYF2xufe5ytuqF2WAHKiYnEi757NiiBjscMUA==&LXq4A=7nJTvP185r2XJ | US | — | — | malicious |
1464 | Explorer.EXE | GET | — | 198.54.117.211:80 | http://www.zodiactshirt.com/arh2/?7nwLw4F=XL9UFO+Z0VPglz6nVm+BbYhRy1FYn8mHKO3HG3LZIhf6EoQyksQ900egJ/Avn8SVa71TcQ==&LXq4A=7nJTvP185r2XJ | US | — | — | malicious |
1464 | Explorer.EXE | GET | — | 156.230.243.3:80 | http://www.dezhouofit.com/arh2/?7nwLw4F=Vn6vkdVMNfUxqSk8kRsl2G5lWQzkj21JDX4gy1oiwYjVPqprDL80MQiCsnIekomcm0yCmg==&LXq4A=7nJTvP185r2XJ | ZA | — | — | malicious |
1464 | Explorer.EXE | GET | — | 162.246.16.90:80 | http://www.yashveerresort.com/arh2/?7nwLw4F=NywYy8OCd2OEJNRYf/W+eFkn5E8FqvvT09aZkIzb20Aug0mgUw0C0cXx0Qd8d3QOAISKJw==&LXq4A=7nJTvP185r2XJ | US | — | — | malicious |
3460 | EQNEDT32.EXE | GET | 200 | 103.167.92.57:80 | http://103.167.92.57/__cloud2protect/vbc.exe | unknown | executable | 193 Kb | suspicious |
1464 | Explorer.EXE | GET | 410 | 52.58.78.16:80 | http://www.delfos.online/arh2/?7nwLw4F=XzokvZt68WyNTj+b3gXHID8g+2WyemJ5EnPkSI47bGUAFk3rPLlPxzokF3Av2mKR5xwTEQ==&LXq4A=7nJTvP185r2XJ | DE | html | 111 b | malicious |
1464 | Explorer.EXE | GET | 302 | 188.114.96.10:80 | http://www.abtys6.online/arh2/?7nwLw4F=eqeFoN2RQJQakkqrmJUItG8VywPf2ly9A17XJndZOseLWR3NBbxs40eT9qz0ppvUs4zoig==&LXq4A=7nJTvP185r2XJ | US | — | — | malicious |
1464 | Explorer.EXE | GET | 301 | 198.187.29.194:80 | http://www.misdcf.xyz/arh2/?7nwLw4F=E44jfaUSbdZ2QR9aGRa8Zh7yik7BB41qh6A200ThQrTt36MFpSD1qmDN+q6XqGRe+7omuA==&LXq4A=7nJTvP185r2XJ | US | html | 707 b | malicious |
1464 | Explorer.EXE | GET | 404 | 45.82.73.217:80 | http://www.ginas4t.com/arh2/?7nwLw4F=jAAW+mDX258O1vJOii4r0s40Ppkw5Tk2uG2iUXhCYVbCN45fR//WqyeAxnb1YqxvlwiJzQ==&LXq4A=7nJTvP185r2XJ | unknown | html | 277 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3460 | EQNEDT32.EXE | 103.167.92.57:80 | — | — | — | suspicious |
1464 | Explorer.EXE | 156.230.243.3:80 | www.dezhouofit.com | MacroLAN | ZA | malicious |
1464 | Explorer.EXE | 188.114.96.10:80 | www.abtys6.online | Cloudflare Inc | US | malicious |
1464 | Explorer.EXE | 76.164.193.184:80 | www.bakiin.com | Versaweb, LLC | US | malicious |
1464 | Explorer.EXE | 198.54.117.211:80 | www.hdwallpaperpics.life | Namecheap, Inc. | US | malicious |
1464 | Explorer.EXE | 52.58.78.16:80 | www.delfos.online | Amazon.com, Inc. | DE | whitelisted |
1464 | Explorer.EXE | 34.102.136.180:80 | www.qrcrashview.com | — | US | whitelisted |
1464 | Explorer.EXE | 162.246.16.90:80 | www.yashveerresort.com | NEW JERSEY INTERNATIONAL INTERNET EXCHANGE LLC | US | malicious |
1464 | Explorer.EXE | 45.82.73.217:80 | www.ginas4t.com | — | — | malicious |
1464 | Explorer.EXE | 198.187.29.194:80 | www.misdcf.xyz | Namecheap, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dezhouofit.com |
| malicious |
www.blackountry.com |
| malicious |
www.bakiin.com |
| malicious |
www.abtys6.online |
| malicious |
www.hdwallpaperpics.life |
| malicious |
www.delfos.online |
| malicious |
www.justfinishesofcolorado.com |
| unknown |
www.zodiactshirt.com |
| malicious |
www.qrcrashview.com |
| malicious |
www.iamparrot.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3460 | EQNEDT32.EXE | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
3460 | EQNEDT32.EXE | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
3460 | EQNEDT32.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M1 |
3460 | EQNEDT32.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3460 | EQNEDT32.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M2 |
3460 | EQNEDT32.EXE | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
1464 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1464 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1464 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1464 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |