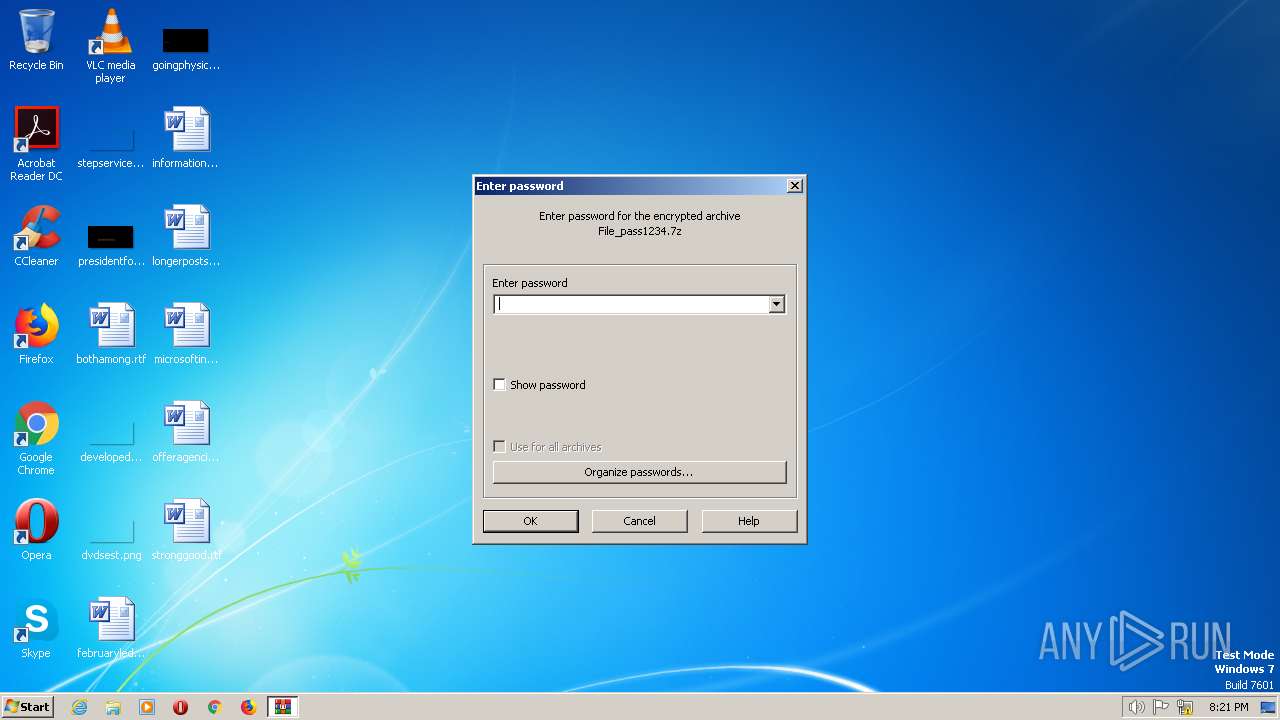
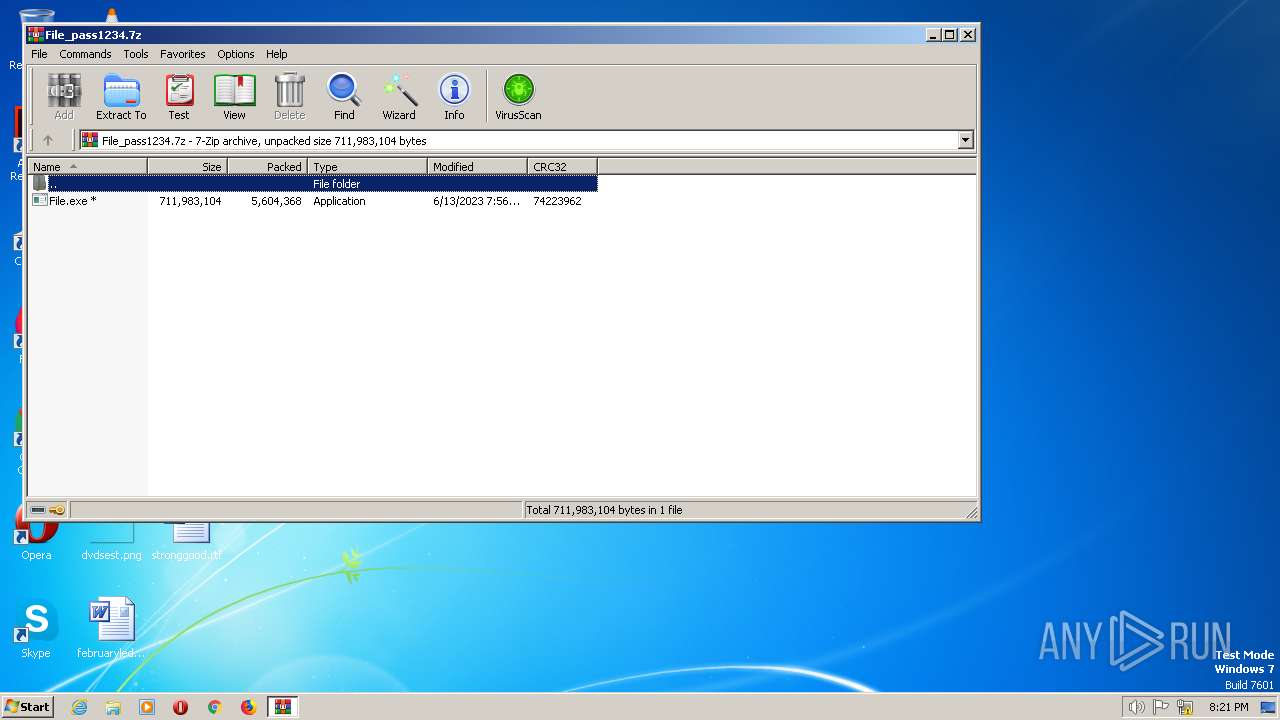
| download: | File_pass1234.7z |
| Full analysis: | https://app.any.run/tasks/142e399e-f83d-4a0f-a853-cf085e6f8c96 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | June 13, 2023, 20:21:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 5D8247884739DBFA2355697F29DFF1E5 |
| SHA1: | 93D5CF504819AD65A4B8BAC59555153F7135BA81 |
| SHA256: | 1AF498CE6C55C10486204397ECCD2F633F9169235269C99467F908B5631733D2 |
| SSDEEP: | 98304:0zwsgldyUmaUISVKKP1VF6L/YQNP+Zku0ALWAiaUqmdhsHCOq24roLvoR6fhAgFb:0zwL/lmNFKKP1vUAEP+iA1l+h0HqrGvl |
MALICIOUS
Creates a writable file the system directory
- File.exe (PID: 2408)
- svchost.exe (PID: 2824)
- powershell.exe (PID: 3064)
Actions looks like stealing of personal data
- File.exe (PID: 2408)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- build2.exe (PID: 2660)
Connects to the CnC server
- File.exe (PID: 2408)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- oneetx.exe (PID: 564)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- Rec613.exe (PID: 2556)
- explorer.exe (PID: 1960)
- build2.exe (PID: 2660)
- build2.exe (PID: 2448)
PRIVATELOADER was detected
- File.exe (PID: 2408)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
Application was dropped or rewritten from another process
- HCgRTQoyreiCQGFkNNSmC0oj.exe (PID: 2484)
- JW4f3rUCy6X9QMYYU8sy5NJI.exe (PID: 2140)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- bhHfPuUtWMmk3BgmQh8i9Q_U.exe (PID: 2772)
- 7xM9NJqIg1Sx3VCbIPBLCvXu.exe (PID: 2924)
- LFOqf5aQugu4X88TvOj_2Mqp.exe (PID: 2984)
- oneetx.exe (PID: 564)
- 2a344302.exe (PID: 464)
- ss41.exe (PID: 2248)
- laszechz.exe (PID: 2832)
- newplayer.exe (PID: 2300)
- VAU2R6lmLeu.exe (PID: 1456)
- EBEF.exe (PID: 568)
- EBEF.exe (PID: 2396)
- F362.exe (PID: 1436)
- EBEF.exe (PID: 1732)
- EBEF.exe (PID: 2072)
- 2B5.exe (PID: 1448)
- 2B5.exe (PID: 2796)
- build2.exe (PID: 2288)
- 2B5.exe (PID: 1624)
- 2B5.exe (PID: 2804)
- build2.exe (PID: 2660)
- build3.exe (PID: 1644)
- build3.exe (PID: 2452)
- mstsca.exe (PID: 1436)
- oneetx.exe (PID: 2676)
- build2.exe (PID: 548)
- build2.exe (PID: 2448)
- aafg31.exe (PID: 2976)
- 430B.exe (PID: 548)
- XandETC.exe (PID: 900)
- XandETC.exe (PID: 3064)
- 4FED.exe (PID: 1264)
- 4FED.exe (PID: 2260)
- 4FED.exe (PID: 1644)
- 4FED.exe (PID: 1168)
- 5ABC.exe (PID: 2316)
- 6A4D.exe (PID: 2676)
- 6A4D.exe (PID: 280)
- build2.exe (PID: 1188)
- build2.exe (PID: 2720)
- 6A4D.exe (PID: 2316)
- build3.exe (PID: 2200)
- 6A4D.exe (PID: 1524)
- build2.exe (PID: 2980)
- build2.exe (PID: 2676)
- 8D18.exe (PID: 2216)
- build3.exe (PID: 2004)
- BA24.exe (PID: 2844)
- updater.exe (PID: 2004)
- oneetx.exe (PID: 2748)
- FA0D.exe (PID: 2120)
Loads dropped or rewritten executable
- is-KHSV8.tmp (PID: 2112)
- build2.exe (PID: 2660)
Changes the autorun value in the registry
- oneetx.exe (PID: 564)
Uses Task Scheduler to run other applications
- oneetx.exe (PID: 564)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- build3.exe (PID: 1644)
- build3.exe (PID: 2452)
- mstsca.exe (PID: 1436)
- powershell.exe (PID: 3012)
Runs injected code in another process
- 7xM9NJqIg1Sx3VCbIPBLCvXu.exe (PID: 2924)
Application was injected by another process
- explorer.exe (PID: 1960)
AMADEY was detected
- oneetx.exe (PID: 564)
GCLEANER was detected
- Rec613.exe (PID: 2556)
Uses Task Scheduler to autorun other applications
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- powershell.exe (PID: 2552)
- powershell.exe (PID: 856)
AMADEY detected by memory dumps
- oneetx.exe (PID: 564)
SMOKE was detected
- explorer.exe (PID: 1960)
TOFSEE detected by memory dumps
- svchost.exe (PID: 2824)
REDLINE detected by memory dumps
- bhHfPuUtWMmk3BgmQh8i9Q_U.exe (PID: 2772)
Stop is detected
- EBEF.exe (PID: 2072)
- 2B5.exe (PID: 2804)
- 4FED.exe (PID: 1644)
- 6A4D.exe (PID: 2316)
Starts CMD.EXE for self-deleting
- Rec613.exe (PID: 2556)
VIDAR was detected
- build2.exe (PID: 2660)
- build2.exe (PID: 2448)
Steals credentials
- build2.exe (PID: 2660)
Steals credentials from Web Browsers
- build2.exe (PID: 2660)
Adds path to the Windows Defender exclusion list
- explorer.exe (PID: 1960)
SUSPICIOUS
Reads settings of System Certificates
- File.exe (PID: 2408)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- EBEF.exe (PID: 2396)
- EBEF.exe (PID: 2072)
- 2B5.exe (PID: 2796)
- build2.exe (PID: 2660)
- 2B5.exe (PID: 2804)
- 4FED.exe (PID: 1168)
- 4FED.exe (PID: 1644)
- 6A4D.exe (PID: 280)
- 6A4D.exe (PID: 2316)
- build2.exe (PID: 2448)
Adds/modifies Windows certificates
- WinRAR.exe (PID: 2436)
- EBEF.exe (PID: 1732)
- build2.exe (PID: 2288)
Connects to the server without a host name
- File.exe (PID: 2408)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- oneetx.exe (PID: 564)
- Rec613.exe (PID: 2556)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- explorer.exe (PID: 1960)
- build2.exe (PID: 2660)
- build2.exe (PID: 2448)
Checks for external IP
- File.exe (PID: 2408)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
Reads the Internet Settings
- File.exe (PID: 2408)
- JW4f3rUCy6X9QMYYU8sy5NJI.exe (PID: 2140)
- LFOqf5aQugu4X88TvOj_2Mqp.exe (PID: 2984)
- newplayer.exe (PID: 2300)
- oneetx.exe (PID: 564)
- Rec613.exe (PID: 2556)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- explorer.exe (PID: 1960)
- EBEF.exe (PID: 2396)
- 2B5.exe (PID: 2796)
- EBEF.exe (PID: 2072)
- build2.exe (PID: 2660)
- 2B5.exe (PID: 2804)
- 430B.exe (PID: 548)
- 4FED.exe (PID: 1168)
- 4FED.exe (PID: 1644)
- 6A4D.exe (PID: 280)
- 6A4D.exe (PID: 2316)
- powershell.exe (PID: 2668)
- build2.exe (PID: 2448)
Process requests binary or script from the Internet
- File.exe (PID: 2408)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- EBEF.exe (PID: 2072)
- 2B5.exe (PID: 2804)
- explorer.exe (PID: 1960)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- 4FED.exe (PID: 1644)
- 6A4D.exe (PID: 2316)
Executable content was dropped or overwritten
- File.exe (PID: 2408)
- HCgRTQoyreiCQGFkNNSmC0oj.exe (PID: 2484)
- is-KHSV8.tmp (PID: 2112)
- JW4f3rUCy6X9QMYYU8sy5NJI.exe (PID: 2140)
- LFOqf5aQugu4X88TvOj_2Mqp.exe (PID: 2984)
- cmd.exe (PID: 2212)
- newplayer.exe (PID: 2300)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- Rec613.exe (PID: 2556)
- explorer.exe (PID: 1960)
- EBEF.exe (PID: 2396)
- EBEF.exe (PID: 2072)
- 2B5.exe (PID: 2804)
- build3.exe (PID: 1644)
- 430B.exe (PID: 548)
- 4FED.exe (PID: 1644)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- 6A4D.exe (PID: 2316)
- build2.exe (PID: 2660)
- XandETC.exe (PID: 3064)
- updater.exe (PID: 2004)
Executes as Windows Service
- raserver.exe (PID: 1984)
- laszechz.exe (PID: 2832)
- raserver.exe (PID: 1356)
Connects to unusual port
- File.exe (PID: 2408)
- bhHfPuUtWMmk3BgmQh8i9Q_U.exe (PID: 2772)
- svchost.exe (PID: 2824)
- build2.exe (PID: 2660)
- build2.exe (PID: 2448)
- conhost.exe (PID: 1440)
Reads the Windows owner or organization settings
- is-KHSV8.tmp (PID: 2112)
Starts CMD.EXE for commands execution
- JW4f3rUCy6X9QMYYU8sy5NJI.exe (PID: 2140)
- oneetx.exe (PID: 564)
- cmd.exe (PID: 124)
- Rec613.exe (PID: 2556)
- explorer.exe (PID: 1960)
- XandETC.exe (PID: 3064)
- updater.exe (PID: 2004)
Starts itself from another location
- newplayer.exe (PID: 2300)
Reads Microsoft Outlook installation path
- Rec613.exe (PID: 2556)
Application launched itself
- cmd.exe (PID: 124)
- EBEF.exe (PID: 568)
- EBEF.exe (PID: 2396)
- EBEF.exe (PID: 1732)
- 2B5.exe (PID: 1448)
- build2.exe (PID: 2288)
- 2B5.exe (PID: 2796)
- 2B5.exe (PID: 1624)
- build2.exe (PID: 548)
- explorer.exe (PID: 1960)
- 4FED.exe (PID: 1168)
- 4FED.exe (PID: 2260)
- 4FED.exe (PID: 1264)
- 6A4D.exe (PID: 2676)
- build2.exe (PID: 1188)
- 6A4D.exe (PID: 1524)
- 6A4D.exe (PID: 280)
- build2.exe (PID: 2980)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 124)
- EBEF.exe (PID: 2396)
Uses NETSH.EXE to add a firewall rule or allowed programs
- JW4f3rUCy6X9QMYYU8sy5NJI.exe (PID: 2140)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- build2.exe (PID: 2660)
- build2.exe (PID: 2448)
Detected use of alternative data streams (AltDS)
- svchost.exe (PID: 2824)
Creates or modifies Windows services
- svchost.exe (PID: 2824)
Reads security settings of Internet Explorer
- EBEF.exe (PID: 2396)
- EBEF.exe (PID: 2072)
- 2B5.exe (PID: 2796)
- 2B5.exe (PID: 2804)
- build2.exe (PID: 2660)
- 4FED.exe (PID: 1168)
- 4FED.exe (PID: 1644)
- 6A4D.exe (PID: 280)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- 6A4D.exe (PID: 2316)
- build2.exe (PID: 2448)
Checks Windows Trust Settings
- EBEF.exe (PID: 2396)
- EBEF.exe (PID: 2072)
- 2B5.exe (PID: 2796)
- build2.exe (PID: 2660)
- 2B5.exe (PID: 2804)
- 4FED.exe (PID: 1644)
- 6A4D.exe (PID: 280)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- 6A4D.exe (PID: 2316)
- 4FED.exe (PID: 1168)
- build2.exe (PID: 2448)
Process communicates with Telegram (possibly using it as an attacker's C2 server)_update
- build2.exe (PID: 2660)
The process executes via Task Scheduler
- mstsca.exe (PID: 1436)
- oneetx.exe (PID: 2676)
- updater.exe (PID: 2004)
- oneetx.exe (PID: 2748)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2716)
Reads browser cookies
- build2.exe (PID: 2660)
Starts POWERSHELL.EXE for commands execution
- XandETC.exe (PID: 3064)
- explorer.exe (PID: 1960)
Searches for installed software
- build2.exe (PID: 2660)
Script adds exclusion path to Windows Defender
- explorer.exe (PID: 1960)
The process checks if current user has admin rights
- explorer.exe (PID: 1960)
- XandETC.exe (PID: 3064)
Starts SC.EXE for service management
- cmd.exe (PID: 2892)
- cmd.exe (PID: 1164)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 2952)
- cmd.exe (PID: 2336)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2892)
- cmd.exe (PID: 1164)
Unusual connection from system programs
- powershell.exe (PID: 3064)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 2004)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 1800)
The Powershell connects to the Internet
- powershell.exe (PID: 3064)
INFO
Checks supported languages
- File.exe (PID: 2408)
- HCgRTQoyreiCQGFkNNSmC0oj.exe (PID: 2484)
- bhHfPuUtWMmk3BgmQh8i9Q_U.exe (PID: 2772)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- is-KHSV8.tmp (PID: 2112)
- JW4f3rUCy6X9QMYYU8sy5NJI.exe (PID: 2140)
- LFOqf5aQugu4X88TvOj_2Mqp.exe (PID: 2984)
- 7xM9NJqIg1Sx3VCbIPBLCvXu.exe (PID: 2924)
- 2a344302.exe (PID: 464)
- Rec613.exe (PID: 2556)
- newplayer.exe (PID: 2300)
- oneetx.exe (PID: 564)
- laszechz.exe (PID: 2832)
- VAU2R6lmLeu.exe (PID: 1456)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- EBEF.exe (PID: 568)
- EBEF.exe (PID: 2396)
- F362.exe (PID: 1436)
- EBEF.exe (PID: 1732)
- EBEF.exe (PID: 2072)
- 2B5.exe (PID: 1448)
- 2B5.exe (PID: 2796)
- build2.exe (PID: 2288)
- build2.exe (PID: 2660)
- 2B5.exe (PID: 1624)
- 2B5.exe (PID: 2804)
- build3.exe (PID: 1644)
- build3.exe (PID: 2452)
- build2.exe (PID: 2448)
- oneetx.exe (PID: 2676)
- mstsca.exe (PID: 1436)
- 430B.exe (PID: 548)
- build2.exe (PID: 548)
- XandETC.exe (PID: 3064)
- oldplayer.exe (PID: 2760)
- 4FED.exe (PID: 1168)
- 4FED.exe (PID: 2260)
- 4FED.exe (PID: 1644)
- 4FED.exe (PID: 1264)
- 5ABC.exe (PID: 2316)
- 6A4D.exe (PID: 2676)
- 6A4D.exe (PID: 280)
- build2.exe (PID: 2720)
- build2.exe (PID: 1188)
- 6A4D.exe (PID: 1524)
- 6A4D.exe (PID: 2316)
- build3.exe (PID: 2200)
- build2.exe (PID: 2980)
- build2.exe (PID: 2676)
- 8D18.exe (PID: 2216)
- build3.exe (PID: 2004)
- updater.exe (PID: 2004)
- oneetx.exe (PID: 2748)
Reads the computer name
- File.exe (PID: 2408)
- is-KHSV8.tmp (PID: 2112)
- bhHfPuUtWMmk3BgmQh8i9Q_U.exe (PID: 2772)
- LFOqf5aQugu4X88TvOj_2Mqp.exe (PID: 2984)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- JW4f3rUCy6X9QMYYU8sy5NJI.exe (PID: 2140)
- newplayer.exe (PID: 2300)
- oneetx.exe (PID: 564)
- laszechz.exe (PID: 2832)
- Rec613.exe (PID: 2556)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- EBEF.exe (PID: 2396)
- EBEF.exe (PID: 2072)
- 2B5.exe (PID: 2796)
- build2.exe (PID: 2660)
- 2B5.exe (PID: 2804)
- build2.exe (PID: 2448)
- 430B.exe (PID: 548)
- 4FED.exe (PID: 1168)
- 4FED.exe (PID: 1644)
- 6A4D.exe (PID: 280)
- build2.exe (PID: 2720)
- 6A4D.exe (PID: 2316)
- build2.exe (PID: 2676)
- 8D18.exe (PID: 2216)
Reads the machine GUID from the registry
- File.exe (PID: 2408)
- bhHfPuUtWMmk3BgmQh8i9Q_U.exe (PID: 2772)
- newplayer.exe (PID: 2300)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- oneetx.exe (PID: 564)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- Rec613.exe (PID: 2556)
- EBEF.exe (PID: 2396)
- EBEF.exe (PID: 2072)
- 2B5.exe (PID: 2796)
- build2.exe (PID: 2660)
- 2B5.exe (PID: 2804)
- build2.exe (PID: 2448)
- 4FED.exe (PID: 1168)
- 4FED.exe (PID: 1644)
- build2.exe (PID: 2720)
- 6A4D.exe (PID: 280)
- 6A4D.exe (PID: 2316)
- build2.exe (PID: 2676)
Process checks computer location settings
- File.exe (PID: 2408)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
Checks proxy server information
- File.exe (PID: 2408)
- oneetx.exe (PID: 564)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- Rec613.exe (PID: 2556)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- EBEF.exe (PID: 2396)
- 2B5.exe (PID: 2796)
- EBEF.exe (PID: 2072)
- build2.exe (PID: 2660)
- 2B5.exe (PID: 2804)
- 4FED.exe (PID: 1168)
- 4FED.exe (PID: 1644)
- 6A4D.exe (PID: 280)
- 6A4D.exe (PID: 2316)
- build2.exe (PID: 2448)
The process checks LSA protection
- File.exe (PID: 2408)
- is-KHSV8.tmp (PID: 2112)
- bhHfPuUtWMmk3BgmQh8i9Q_U.exe (PID: 2772)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- JW4f3rUCy6X9QMYYU8sy5NJI.exe (PID: 2140)
- LFOqf5aQugu4X88TvOj_2Mqp.exe (PID: 2984)
- newplayer.exe (PID: 2300)
- oneetx.exe (PID: 564)
- netsh.exe (PID: 2168)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- Rec613.exe (PID: 2556)
- explorer.exe (PID: 1960)
- EBEF.exe (PID: 2396)
- icacls.exe (PID: 2096)
- EBEF.exe (PID: 2072)
- 2B5.exe (PID: 2796)
- build2.exe (PID: 2660)
- 2B5.exe (PID: 2804)
- 430B.exe (PID: 548)
- taskkill.exe (PID: 276)
- 4FED.exe (PID: 1168)
- 4FED.exe (PID: 1644)
- 6A4D.exe (PID: 280)
- 6A4D.exe (PID: 2316)
- build2.exe (PID: 2448)
- conhost.exe (PID: 1440)
- WMIC.exe (PID: 2812)
Creates files or folders in the user directory
- File.exe (PID: 2408)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- Rec613.exe (PID: 2556)
- explorer.exe (PID: 1960)
- EBEF.exe (PID: 2396)
- EBEF.exe (PID: 2072)
- 2B5.exe (PID: 2796)
- build2.exe (PID: 2660)
- 2B5.exe (PID: 2804)
- build3.exe (PID: 1644)
- 4FED.exe (PID: 1168)
- 4FED.exe (PID: 1644)
- oLdbrFXlr0yNwkHor72Etr4c.exe (PID: 2376)
- 6A4D.exe (PID: 280)
- 6A4D.exe (PID: 2316)
Create files in a temporary directory
- HCgRTQoyreiCQGFkNNSmC0oj.exe (PID: 2484)
- JW4f3rUCy6X9QMYYU8sy5NJI.exe (PID: 2140)
- is-KHSV8.tmp (PID: 2112)
- LFOqf5aQugu4X88TvOj_2Mqp.exe (PID: 2984)
- newplayer.exe (PID: 2300)
- explorer.exe (PID: 1960)
- EBEF.exe (PID: 2396)
- 430B.exe (PID: 548)
Application was dropped or rewritten from another process
- is-KHSV8.tmp (PID: 2112)
Creates files in the program directory
- is-KHSV8.tmp (PID: 2112)
- HMOGkA1cbtJnGbgRByM_Y6fG.exe (PID: 2996)
- build2.exe (PID: 2660)
- XandETC.exe (PID: 3064)
- cmd.exe (PID: 1800)
- updater.exe (PID: 2004)
Reads Environment values
- build2.exe (PID: 2660)
Reads product name
- build2.exe (PID: 2660)
Reads CPU info
- build2.exe (PID: 2660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(564) oneetx.exe
C2 (1)http://45.9.74.80
Version3.83
Options
Drop directory207aa4515d
Drop nameoneetx.exe
Strings (116)SCHTASKS
/Create /SC MINUTE /MO 1 /TN
/TR "
" /F
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Startup
Rem
cmd /C RMDIR /s/q
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
rundll32
/Delete /TN "
Programs
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
%USERPROFILE%
\App
POST
GET
id=
&vs=
&sd=
&os=
&bi=
&ar=
&pc=
&un=
&dm=
&av=
&lv=
&og=
cred.dll|clip.dll|
d1
e1
e0
Main
http://
https://
exe
dll
cmd
ps1
<c>
<d>
Plugins/
+++
#
|
&unit=
=
shell32.dll
kernel32.dll
GetNativeSystemInfo
ProgramData\
AVAST Software
Avira
Kaspersky Lab
ESET
Panda Security
Doctor Web
AVG
360TotalSecurity
Bitdefender
Norton
Sophos
Comodo
WinDefender
0123456789
rb
wb
Content-Type: multipart/form-data; boundary=----
------
Content-Disposition: form-data; name="data"; filename="
"
Content-Type: application/octet-stream
------
--
?scr=1
.jpg
Content-Type: application/x-www-form-urlencoded
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
ComputerName
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
SYSTEM\ControlSet001\Services\BasicDisplay\Video
VideoID
\0000
DefaultSettings.XResolution
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
2019
2022
2016
CurrentBuild
&&
echo Y|CACLS "
" /P "
:N"
CACLS "
" /P "
:R" /E
:F" /E
&&Exit
..\
\
:::
rundll32.exe
/k
"taskkill /f /im "
" && timeout 1 && del
&& Exit"
" && ren
&&
Powershell.exe
-executionpolicy remotesigned -File "
"
Tofsee
(PID) Process(2824) svchost.exe
C2 (2)vanaheim.cn
jotunheim.name
Encrypted Strings (59)c:\Windows
\system32\
ImagePath
.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
MSConfig
/r
.exe
cmd /C move /Y "%s" %s
sc config %s binPath= "%s%s /d\"%s\""
sc start %s
svchost.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
ConsentPromptBehaviorAdmin
PromptOnSecureDesktop
MSConfig
:.repos
USERPROFILE
\Local Settings:.repos
USERPROFILE
\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat.repos
USERPROFILE
\wincookie.repos
TMP
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
SYSTEM\CurrentControlSet\services
ImagePath
SYSTEM\CurrentControlSet\services
SYSTEM\CurrentControlSet\services
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
.exe
qazwsxed
%s%i%i%i%i.bat
@echo off
:next_try
del "%s">nul
if exist "%s" (
ping 127.0.0.1 >nul
goto next_try
)
del %%0
svchost.exe
.exe
/u
USERPROFILE
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/d
/e
/d
/e
.exe
"%s" /u"%s"
USERPROFILE
.exe
USERPROFILE
USERPROFILE
ver=%d lid=%d
win=%X/%d sid=%s
rep=%s
RedLine
(PID) Process(2772) bhHfPuUtWMmk3BgmQh8i9Q_U.exe
C2 (1)185.81.68.115:2920
Botnet@Germany
Err_msg
Auth_value9d15d78194367a949e54a07d6ce02c62
US (139)
This assembly is protected by an unregistered version of Eziriz's ".NET Reactor"! This assembly won't further work.
Search
Reflection
Ammo
Function
Info
Roaming
UNKNOWN
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
ToString
os_crypt
encrypted_key
Network\
Inner
Unknown
:
Read
Kill
Microsoft
GetDirectories
MSObject12
EnumerateDirectories
String.Replace
String.Remove
net.tcp://
/
localhost
9d15d78194367a949e54a07d6ce02c62
Authorization
ns1
CjsVUyADCgELBStWIAMoAQk7HRsjPSQO
FioWDg8EXBElARlf
Gorblimy
MSValue3
EnumerateFiles
ExpandEnvironmentVariables
MSValue2
MSValue1
FullName
Replace
Directory
wa
l
et
d
a
t
.
*wallet*
_
T
e
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
Environment
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
1
String
MyG
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
EngSubs
ElevatedDiagnostics\Reports
-
AddRange
%
(
UNIQUE
"
FileStream.IO
string.Empty
uint
UnmanagedType
hKey
pszProperty
Encoding
bMasterKey
{0}
|
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
Name
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
_[
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
214
Monitored processes
140
Malicious processes
44
Suspicious processes
14
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\Windows\SysWOW64\explorer.exe | C:\Windows\SysWOW64\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 124 | "C:\Windows\System32\cmd.exe" /k echo Y|CACLS "oneetx.exe" /P "admin:N"&&CACLS "oneetx.exe" /P "admin:R" /E&&echo Y|CACLS "..\207aa4515d" /P "admin:N"&&CACLS "..\207aa4515d" /P "admin:R" /E&&Exit | C:\Windows\SysWOW64\cmd.exe | — | oneetx.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 148 | schtasks /create /f /RU "admin" /tr "C:\Program Files (x86)\PowerControl\PowerControl_Svc.exe" /tn "PowerControl LG" /sc ONLOGON /rl HIGHEST | C:\Windows\SysWOW64\schtasks.exe | — | HMOGkA1cbtJnGbgRByM_Y6fG.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 188 | /C /create /F /sc minute /mo 1 /tn "Azure-Update-Task" /tr "C:\Users\admin\AppData\Roaming\Microsoft\Network\mstsca.exe" | C:\Windows\SysWOW64\schtasks.exe | — | build3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | C:\Windows\explorer.exe | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 276 | taskkill /im "Rec613.exe" /f | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 280 | C:\Users\admin\AppData\Local\Temp\6A4D.exe | C:\Users\admin\AppData\Local\Temp\6A4D.exe | 6A4D.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 464 | "C:\Users\admin\AppData\Local\Temp\2a344302.exe" | C:\Users\admin\AppData\Local\Temp\2a344302.exe | LFOqf5aQugu4X88TvOj_2Mqp.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 548 | "C:\Users\admin\AppData\Local\845c4473-54f7-4b1e-b327-80f7d77e6734\build2.exe" | C:\Users\admin\AppData\Local\845c4473-54f7-4b1e-b327-80f7d77e6734\build2.exe | — | 2B5.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 548 | C:\Users\admin\AppData\Local\Temp\430B.exe | C:\Users\admin\AppData\Local\Temp\430B.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
28 990
Read events
28 479
Write events
470
Delete events
41
Modification events
| (PID) Process: | (1960) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB0100000040131FD0E0B45449B5325CF35709B45A0000000002000000000010660000000100002000000097BA847E5D0827CAFBC4D33F7B8AFE8834428DFEF065FA018D8CAB90C5710B0A000000000E8000000002000020000000703BDF28CF4D9DFCAB7DDC229F11B838657F02A563D675B7BA5A582848A73F4F300000008091631BBFD318C1A67DDE62193EF5F65F823DF6F3FB12C344A857963FC714699639A04F9F66927C69CA8E9AC61E02154000000007CED62AF9113E09870DE72EB5744E2CBFDC316C2CF8607885EA5CBB68D61BE0CFB49EE1C4CAF8F2769692B62252F8AB0F88C1F92875F93F72FE70BCC896EFE4 | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\14C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1960) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {6Q809377-6NS0-444O-8957-N3773S02200R}\JvaENE\JvaENE.rkr |
Value: 000000000B000000050000001E9A0000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF30D9B8CEF2F1D80100000000 | |||
| (PID) Process: | (1960) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 0000000091000000940000006A524C00110000000300000071B504007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C0063006D0064002E006500780065000000D3FDFE0700000000000000000000F012D2020000000000000000000000000000000000000000F012D2020000000012C2D2FDFE070000010000000000000000000000000000000000000000000000F012D20200000000000000000000000000000000000000000000000000000000DCD9D3FDFE0700000000000000000000568ED3FDFE07000005000000000000000000000000000000F012D20200000000C9AAD2FDFE07000000000000000000000500000000000000000000000000000000000000000000000100000000000000C3AAD3FDFE070000F012D202000000000500000000000000010000000000000001000000FFFFFFFF00000000000000000000000000000000000000001C000000010000000000000001000000FFFFFFFF0C18D202000000002C18D202000000000000000000000000010000000600000071D8D3FDFE070000F0E676030000000000000000000000000500000000000000F012D20200000000F012D2020000000063B3D2FDFE07000001000000000000000000000000000000000000000000000005000000FE0700004413D20200000000D017D202000000008014D202100000001B000000C95F05007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E00650078006500000000000000FE221EFEFE07000060000100000000008202000000000000820200000000000001FFFFFF000000006A00A603000000008C00A60300000000B8ACA6030000000050DFE3020000000000010001010000000001E302000000004CE2E3020000000094DFE302000000000000000009090900090909090009111100000000000000008202000000000000820200000000000001000000000000008202000000000000DB9B5A77000000006000010000000000000000000000000000000000000000000000000000000000110000000300000071B504007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C0063006D0064002E006500780065000000D3FDFE0700000000000000000000F012D2020000000000000000000000000000000000000000F012D2020000000012C2D2FDFE070000010000000000000000000000000000000000000000000000F012D2020000000000000000000000000000000000000000000000000000000013000000A80916007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C007400610073006B006D00670072002E006500780065000000008000000000542D3EFFFE07000000000000000000006800690200000000580001000000000000000000000000000000290000000000EB1ABB7700000000680069020000000000000000FE070000282547FFFE070000B0EA330000000000180069020000000000000000000000000100000000000000BF1D3EFFFE07000090DEF3020000000070C936000000000000000000000000003B94B5FDFE070000E00736000000000008006902000000005800010000000000869AA977000000000814FEDA97F1000082020000000000000000000000000000580001000000000000000000000000008202000000000000020000000000000058000100000000000000000000000000820200000000000080A671FF00000000C81263FF00000000E00736000000000001000000000000000F0000C000000000941AC90200000000820200000000000001000000000000008202000000000000DB9BA977000000005800010000000000000000000000000000000000000000000100000000000000000000000000000081020000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7AndW2K8R2-KB3191566-x64.zip | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
84
Suspicious files
49
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2436.17935\File.exe | — | |
MD5:— | SHA256:— | |||
| 2408 | File.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:CDFD60E717A44C2349B553E011958B85 | SHA256:0EE08DA4DA3E4133E1809099FC646468E7156644C9A772F704B80E338015211F | |||
| 2408 | File.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2U1WPAC\2[1].exe | executable | |
MD5:918731493DC265322EB7B5563061A665 | SHA256:6887704723D5A6150375AAC34FD0F2728FDF221FC064AEAC93D9A7BF5A6C0FF6 | |||
| 2408 | File.exe | C:\Windows\System32\GroupPolicy\gpt.ini | text | |
MD5:39DFFC602ED934569F26BE44EC645814 | SHA256:B57A88E5B1ACF3A784BE88B87FA3EE1F0991CB7C1C66DA423F3595FFC6E0C5C2 | |||
| 2408 | File.exe | C:\Users\admin\Pictures\Minor Policy\ibtFpfoCTsrOvzoMhlu8ufls.exe | html | |
MD5:81F7A08F650AA005B8EC636C9E385065 | SHA256:04CBBABD3A2B199EBFE272F04EEF2EEF33B033B987E1E3B13096D7DE7988BA90 | |||
| 2408 | File.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\D2U1WPAC\obins[1].exe | executable | |
MD5:8A06751312436A705C6404180C8B1519 | SHA256:0875F2085B2F40B96DB96D317CFDD1D870541182D4200DE33FAE9CBEFAF07797 | |||
| 2408 | File.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\BDW1XBVN\qdk2rlsncuqts[1].exe | executable | |
MD5:2A9C91D22B235EF9675F44B871A03A83 | SHA256:1FAF53A182B0295309F4E97E21469BE2867A9B0669D1E9FECA5EF45A64B82089 | |||
| 2408 | File.exe | C:\Users\admin\Pictures\Minor Policy\7xM9NJqIg1Sx3VCbIPBLCvXu.exe | executable | |
MD5:3C465371B9755C67FECA54FEE5FA174B | SHA256:61BD39FF52FF66E58A3F46C49EE5F2453C1DF77E911782D163DDF06CC36E4EC8 | |||
| 2112 | is-KHSV8.tmp | C:\Users\admin\AppData\Local\Temp\is-VQVLK.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 2408 | File.exe | C:\Users\admin\Pictures\Minor Policy\bhHfPuUtWMmk3BgmQh8i9Q_U.exe | executable | |
MD5:918731493DC265322EB7B5563061A665 | SHA256:6887704723D5A6150375AAC34FD0F2728FDF221FC064AEAC93D9A7BF5A6C0FF6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
113
TCP/UDP connections
144
DNS requests
43
Threats
832
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2408 | File.exe | HEAD | — | 194.169.175.124:80 | http://194.169.175.124:3002/ | US | — | — | malicious |
2408 | File.exe | HEAD | 200 | 45.9.74.6:80 | http://45.9.74.6/2.exe | SC | — | — | malicious |
2408 | File.exe | HEAD | — | 176.113.115.239:80 | http://176.113.115.239:8080/4.php | RU | — | — | suspicious |
2408 | File.exe | HEAD | 200 | 45.9.74.80:80 | http://45.9.74.80/obins.exe | SC | — | — | malicious |
2408 | File.exe | HEAD | 200 | 163.123.143.4:80 | http://163.123.143.4/download/Service32.exe | unknown | — | — | malicious |
2408 | File.exe | HEAD | — | 83.97.73.131:80 | http://83.97.73.131/gallery/photo221.exe | unknown | — | — | malicious |
2408 | File.exe | HEAD | 403 | 188.114.96.0:80 | http://ji.jahhaega2qq.com/m/p0aw25.exe | US | — | — | malicious |
2408 | File.exe | HEAD | 200 | 45.12.253.74:80 | http://45.12.253.74/pineapple.php?pub=mixinte | BG | — | — | malicious |
2408 | File.exe | HEAD | — | 91.215.85.147:80 | http://hugersi.com/dl/6523.exe | RU | — | — | suspicious |
2408 | File.exe | GET | — | 194.169.175.124:3002 | http://194.169.175.124:3002/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2408 | File.exe | 91.215.85.147:80 | hugersi.com | — | RU | suspicious |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
328 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2408 | File.exe | 208.67.104.60:80 | — | Delis LLC | US | malicious |
2408 | File.exe | 104.26.8.59:443 | api.myip.com | CLOUDFLARENET | US | suspicious |
2408 | File.exe | 87.240.132.72:80 | vk.com | VKontakte Ltd | RU | suspicious |
2408 | File.exe | 34.117.59.81:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
2408 | File.exe | 87.240.132.72:443 | vk.com | VKontakte Ltd | RU | suspicious |
2408 | File.exe | 83.97.73.131:80 | — | — | — | malicious |
2408 | File.exe | 194.169.175.124:80 | — | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.myip.com |
| suspicious |
ipinfo.io |
| shared |
vk.com |
| whitelisted |
teredo.ipv6.microsoft.com |
| whitelisted |
ji.jahhaega2qq.com |
| malicious |
hugersi.com |
| suspicious |
dns.msftncsi.com |
| shared |
telegram.org |
| whitelisted |
twitter.com |
| whitelisted |
yandex.ru |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2408 | File.exe | Device Retrieving External IP Address Detected | ET INFO Observed External IP Lookup Domain in TLS SNI (api .myip .com) |
2408 | File.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/BeamWinHTTP CnC Activity M2 (GET) |
2408 | File.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
2408 | File.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 20 |
2408 | File.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2408 | File.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2408 | File.exe | A Network Trojan was detected | ET MALWARE Single char EXE direct download likely trojan (multiple families) |
2408 | File.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2408 | File.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2408 | File.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
39 ETPRO signatures available at the full report