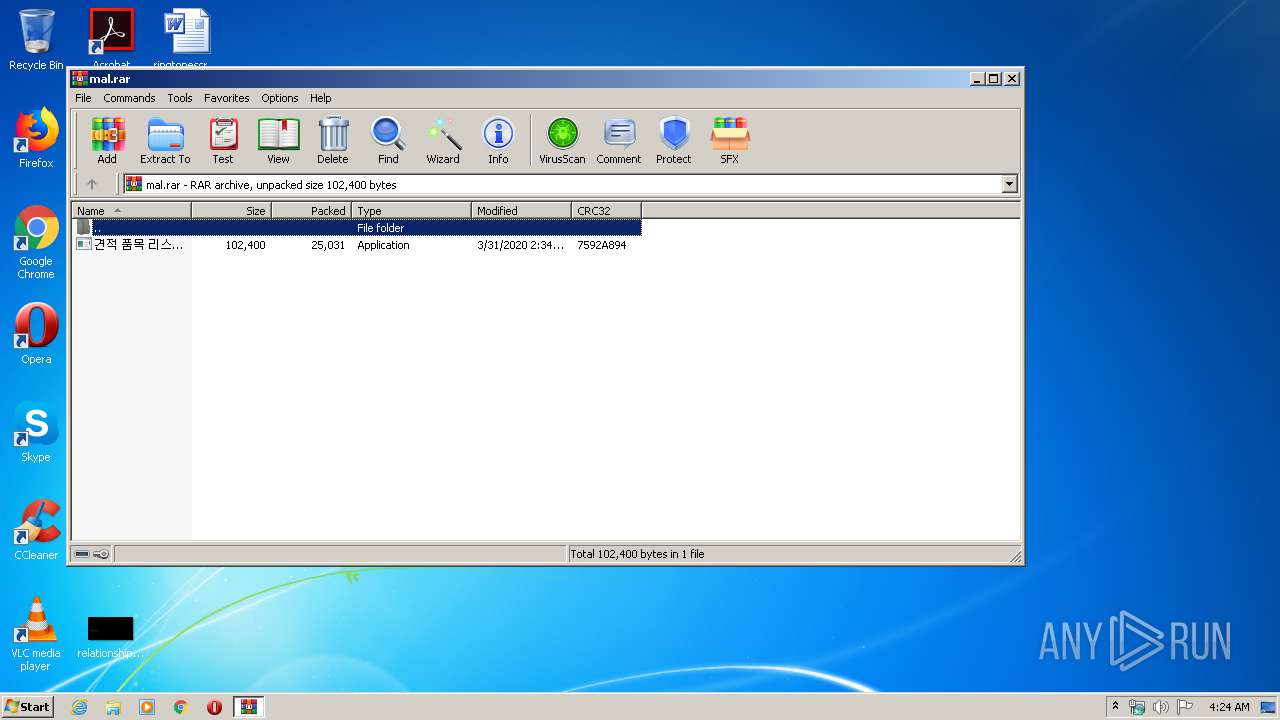
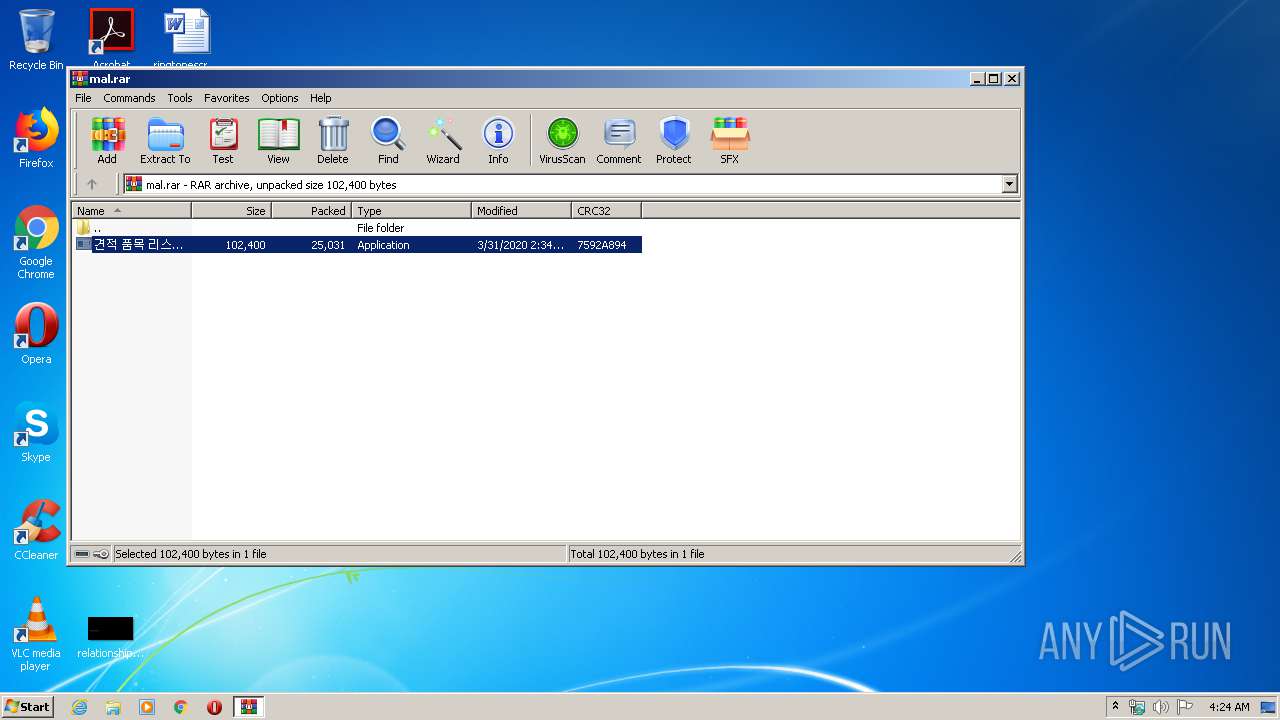
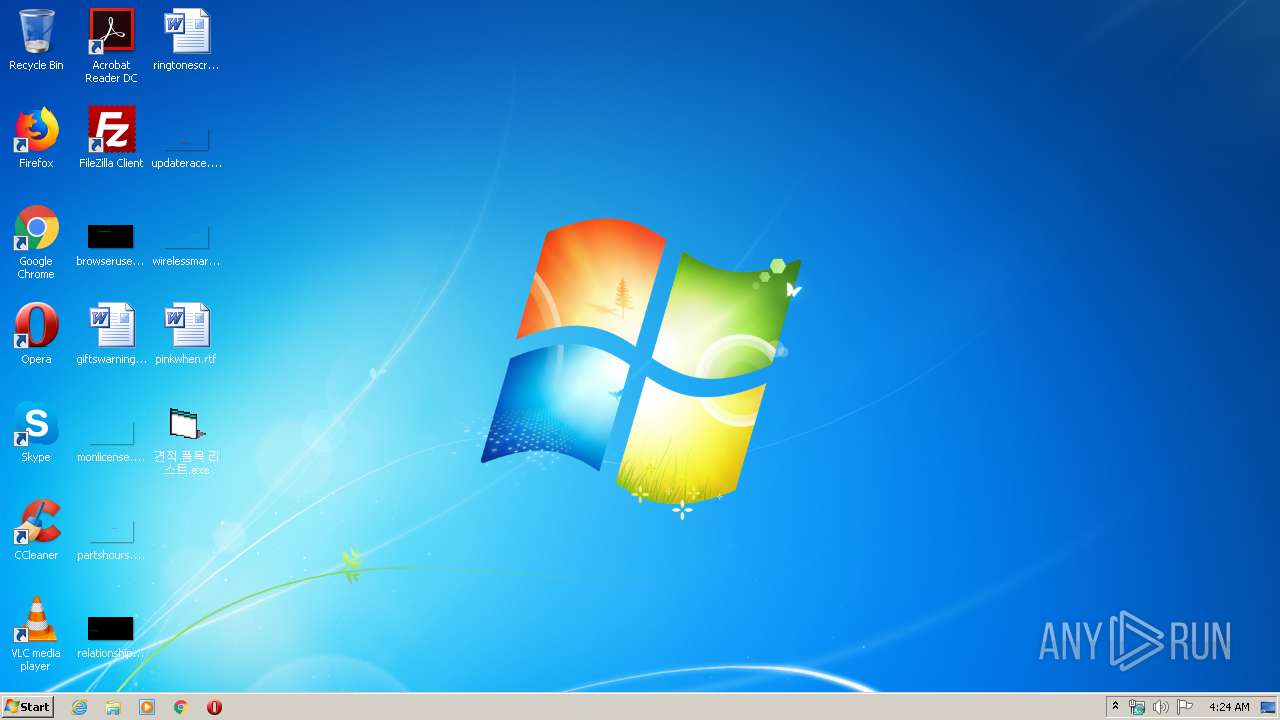
| File name: | mal |
| Full analysis: | https://app.any.run/tasks/aeb7d338-7c8b-458d-a5ba-d93830178094 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | March 31, 2020, 03:23:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | B78C45D89A5512E57CFCEE073F746BDC |
| SHA1: | 01246D4459FBEB136052F26DD04E25B7688BC277 |
| SHA256: | 1ADD04C4F6F527059AF44EB3905994A269931EE0BEB10779BEBE764641FB7282 |
| SSDEEP: | 768:Wa3F/hkj2X1R3rB4tJReuZCnTe0gCJh8+lxJeDQ:Wa3F/h6o1JrB4vUuEnTeNCtlxiQ |
MALICIOUS
Application was dropped or rewritten from another process
- filename1.exe (PID: 3376)
- 견적 품목 리스트.exe (PID: 2836)
- 견적 품목 리스트.exe (PID: 1916)
- filename1.exe (PID: 2128)
- _jd4stohlpwt.exe (PID: 3864)
- _jd4stohlpwt.exe (PID: 1712)
- filename1.exe (PID: 1840)
- filename1.exe (PID: 2856)
Changes the autorun value in the registry
- 견적 품목 리스트.exe (PID: 1916)
- filename1.exe (PID: 3376)
- NETSTAT.EXE (PID: 3764)
- _jd4stohlpwt.exe (PID: 3864)
- filename1.exe (PID: 2856)
Connects to CnC server
- explorer.exe (PID: 372)
FORMBOOK was detected
- NETSTAT.EXE (PID: 3764)
- explorer.exe (PID: 372)
- Firefox.exe (PID: 3664)
Actions looks like stealing of personal data
- NETSTAT.EXE (PID: 3764)
Stealing of credential data
- NETSTAT.EXE (PID: 3764)
Changes settings of System certificates
- filename1.exe (PID: 1840)
- filename1.exe (PID: 2128)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4092)
- 견적 품목 리스트.exe (PID: 2836)
- explorer.exe (PID: 372)
- DllHost.exe (PID: 2744)
- _jd4stohlpwt.exe (PID: 1712)
Application launched itself
- 견적 품목 리스트.exe (PID: 1916)
- filename1.exe (PID: 3376)
- _jd4stohlpwt.exe (PID: 3864)
- filename1.exe (PID: 2856)
Reads Internet Cache Settings
- filename1.exe (PID: 2128)
- filename1.exe (PID: 1840)
Starts itself from another location
- 견적 품목 리스트.exe (PID: 2836)
Creates files in the user directory
- filename1.exe (PID: 2128)
- NETSTAT.EXE (PID: 3764)
- filename1.exe (PID: 1840)
Starts CMD.EXE for commands execution
- NETSTAT.EXE (PID: 3764)
Uses NETSTAT.EXE to discover network connections
- explorer.exe (PID: 372)
Loads DLL from Mozilla Firefox
- NETSTAT.EXE (PID: 3764)
Creates files in the program directory
- DllHost.exe (PID: 2744)
Executed via COM
- DllHost.exe (PID: 2744)
Adds / modifies Windows certificates
- filename1.exe (PID: 2128)
- filename1.exe (PID: 1840)
INFO
Manual execution by user
- 견적 품목 리스트.exe (PID: 1916)
- NETSTAT.EXE (PID: 3764)
Reads settings of System Certificates
- filename1.exe (PID: 2128)
- filename1.exe (PID: 1840)
Reads the hosts file
- NETSTAT.EXE (PID: 3764)
Creates files in the user directory
- Firefox.exe (PID: 3664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
MPEG
| MPEGAudioVersion: | 1 |
|---|---|
| AudioLayer: | 3 |
| AudioBitrate: | 96 kbps |
| SampleRate: | 32000 |
| ChannelMode: | Single Channel |
| MSStereo: | On |
| IntensityStereo: | On |
| CopyrightFlag: | |
| OriginalMedia: | |
| Emphasis: | None |
Composite
| Duration: | 2.10 s (approx) |
|---|
Total processes
51
Monitored processes
15
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1712 | "C:\Program Files\Qar2\_jd4stohlpwt.exe" | C:\Program Files\Qar2\_jd4stohlpwt.exe | _jd4stohlpwt.exe | ||||||||||||
User: admin Company: WONDerware Integrity Level: MEDIUM Description: tint Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1840 | "C:\Users\admin\subfolder1\filename1.exe" | C:\Users\admin\subfolder1\filename1.exe | filename1.exe | ||||||||||||
User: admin Company: WONDerware Integrity Level: MEDIUM Description: tint Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1916 | "C:\Users\admin\Desktop\견적 품목 리스트.exe" | C:\Users\admin\Desktop\견적 품목 리스트.exe | explorer.exe | ||||||||||||
User: admin Company: WONDerware Integrity Level: MEDIUM Description: tint Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2128 | "C:\Users\admin\subfolder1\filename1.exe" | C:\Users\admin\subfolder1\filename1.exe | filename1.exe | ||||||||||||
User: admin Company: WONDerware Integrity Level: MEDIUM Description: tint Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2740 | /c del "C:\Users\admin\subfolder1\filename1.exe" | C:\Windows\System32\cmd.exe | — | NETSTAT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2744 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2836 | "C:\Users\admin\Desktop\견적 품목 리스트.exe" | C:\Users\admin\Desktop\견적 품목 리스트.exe | 견적 품목 리스트.exe | ||||||||||||
User: admin Company: WONDerware Integrity Level: MEDIUM Description: tint Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2856 | "C:\Users\admin\subfolder1\filename1.exe" | C:\Users\admin\subfolder1\filename1.exe | _jd4stohlpwt.exe | ||||||||||||
User: admin Company: WONDerware Integrity Level: MEDIUM Description: tint Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3180 | "C:\Windows\System32\spoolsv.exe" | C:\Windows\System32\spoolsv.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Spooler SubSystem App Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 249
Read events
2 084
Write events
4 791
Delete events
2 374
Modification events
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\mal.rar | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4092) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
Executable files
5
Suspicious files
77
Text files
5
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2128 | filename1.exe | C:\Users\admin\AppData\Local\Temp\Cab2231.tmp | — | |
MD5:— | SHA256:— | |||
| 2128 | filename1.exe | C:\Users\admin\AppData\Local\Temp\Tar2232.tmp | — | |
MD5:— | SHA256:— | |||
| 1840 | filename1.exe | C:\Users\admin\AppData\Local\Temp\Cab8338.tmp | — | |
MD5:— | SHA256:— | |||
| 1840 | filename1.exe | C:\Users\admin\AppData\Local\Temp\Tar8339.tmp | — | |
MD5:— | SHA256:— | |||
| 2836 | 견적 품목 리스트.exe | C:\Users\admin\subfolder1\filename1.exe | executable | |
MD5:— | SHA256:— | |||
| 2836 | 견적 품목 리스트.exe | C:\Users\admin\subfolder1\filename1.vbs | text | |
MD5:— | SHA256:— | |||
| 2128 | filename1.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_C9FB72B5AE80778A08024D8B0FDECC6F | der | |
MD5:— | SHA256:— | |||
| 4092 | WinRAR.exe | C:\Users\admin\Desktop\견적 품목 리스트.exe | executable | |
MD5:— | SHA256:— | |||
| 2128 | filename1.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_D9817BD5013875AD517DA73475345203 | der | |
MD5:— | SHA256:— | |||
| 2128 | filename1.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_D9817BD5013875AD517DA73475345203 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
31
DNS requests
16
Threats
46
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
372 | explorer.exe | GET | 301 | 35.242.251.130:80 | http://www.baribh.com/sa22/?9rfx9hDX=IDe74EdX1tMu3Io0WHkb2YSV0r0oUakV0rZ2YSNHGafdYlxyPzlEEy0P+41r6Agx+Gdyrg==&rZE=X4_4ANE82 | US | — | — | malicious |
372 | explorer.exe | GET | — | 184.168.221.91:80 | http://www.goforfootball.com/sa22/?9rfx9hDX=kzPpBLvn8rMiCf0lAslMPtRg/j5Py6K0V3qNlkw/YpyzLfzAYva/70so1x8LHgmZ9cru9w==&rZE=X4_4ANE82 | US | — | — | malicious |
372 | explorer.exe | POST | — | 184.168.221.91:80 | http://www.goforfootball.com/sa22/ | US | — | — | malicious |
372 | explorer.exe | GET | 200 | 156.226.241.57:80 | http://www.xingli60.com/sa22/?9rfx9hDX=3sOu6G2VjR7V7eD+TKDj4IVnPF2Pia1O8vnLEq2QdRhzG2b1hDGqq2BgvzopuAotEL9Y/w==&rZE=X4_4ANE82 | ZA | text | 53 b | malicious |
1052 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.0 Kb | whitelisted |
372 | explorer.exe | POST | — | 156.226.241.57:80 | http://www.xingli60.com/sa22/ | ZA | — | — | malicious |
372 | explorer.exe | POST | — | 156.226.241.57:80 | http://www.xingli60.com/sa22/ | ZA | — | — | malicious |
372 | explorer.exe | GET | 404 | 162.213.250.169:80 | http://www.allixanes.com/sa22/?9rfx9hDX=JMM0tJzek7OfGpItd7GZSDXDp6JdgYgBE5yHy+eQKsts3D1xYsicJlQH435XxcrMhotTVA==&rZE=X4_4ANE82 | US | html | 328 b | malicious |
2128 | filename1.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAtqs7A%2Bsan2xGCSaqjN%2FrM%3D | US | der | 1.47 Kb | whitelisted |
372 | explorer.exe | POST | — | 162.213.250.169:80 | http://www.allixanes.com/sa22/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2128 | filename1.exe | 13.107.42.13:443 | onedrive.live.com | Microsoft Corporation | US | malicious |
2128 | filename1.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2128 | filename1.exe | 13.107.42.12:443 | hmhxvw.dm.files.1drv.com | Microsoft Corporation | US | suspicious |
372 | explorer.exe | 185.47.245.223:80 | www.xn--diseowebbadajoz-1qb.com | Grupo Loading Systems, S.L. | ES | malicious |
372 | explorer.exe | 162.213.250.169:80 | www.allixanes.com | Namecheap, Inc. | US | malicious |
1840 | filename1.exe | 13.107.42.13:443 | onedrive.live.com | Microsoft Corporation | US | malicious |
1840 | filename1.exe | 13.107.42.12:443 | hmhxvw.dm.files.1drv.com | Microsoft Corporation | US | suspicious |
372 | explorer.exe | 184.168.221.91:80 | www.goforfootball.com | GoDaddy.com, LLC | US | malicious |
1052 | svchost.exe | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
372 | explorer.exe | 157.7.107.191:80 | www.breeze-iwaki.com | GMO Internet,Inc | JP | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
onedrive.live.com |
| shared |
ocsp.digicert.com |
| whitelisted |
hmhxvw.dm.files.1drv.com |
| whitelisted |
www.xn--diseowebbadajoz-1qb.com |
| malicious |
www.allixanes.com |
| malicious |
www.readytraffic4upgrade.download |
| unknown |
www.goforfootball.com |
| malicious |
www.download.windowsupdate.com |
| whitelisted |
www.xingli60.com |
| malicious |
www.baribh.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
372 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
19 ETPRO signatures available at the full report