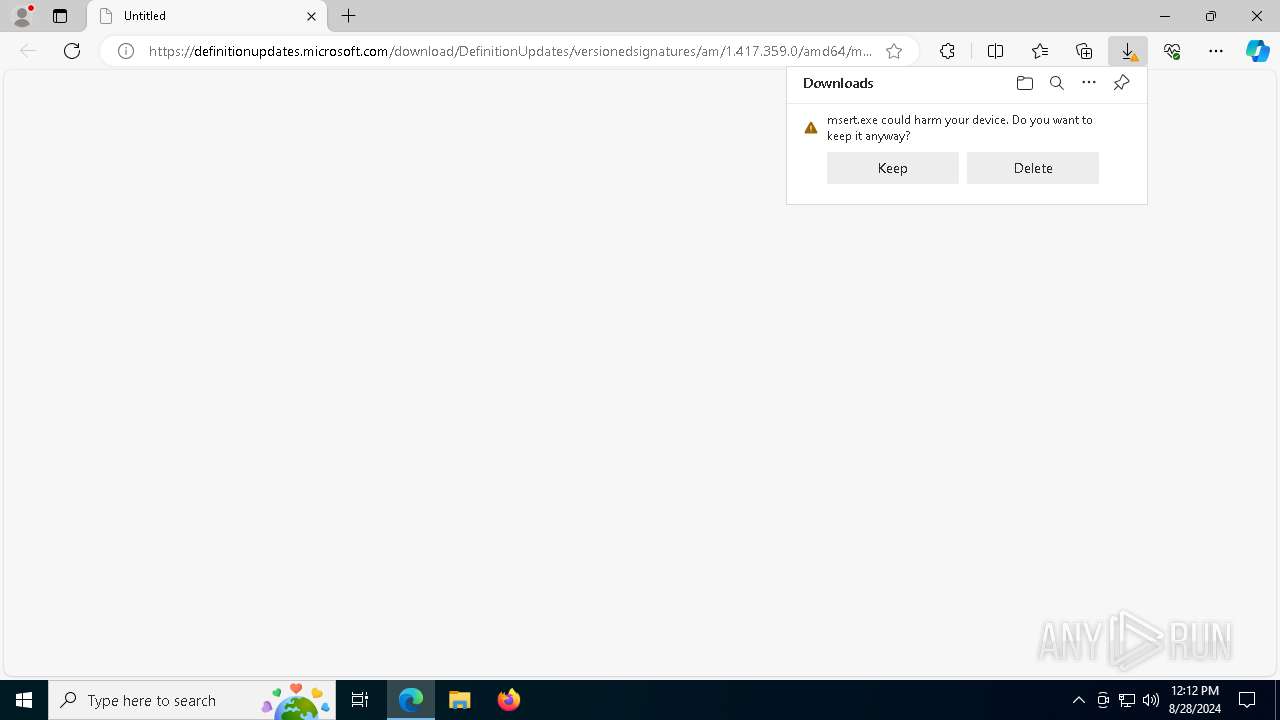
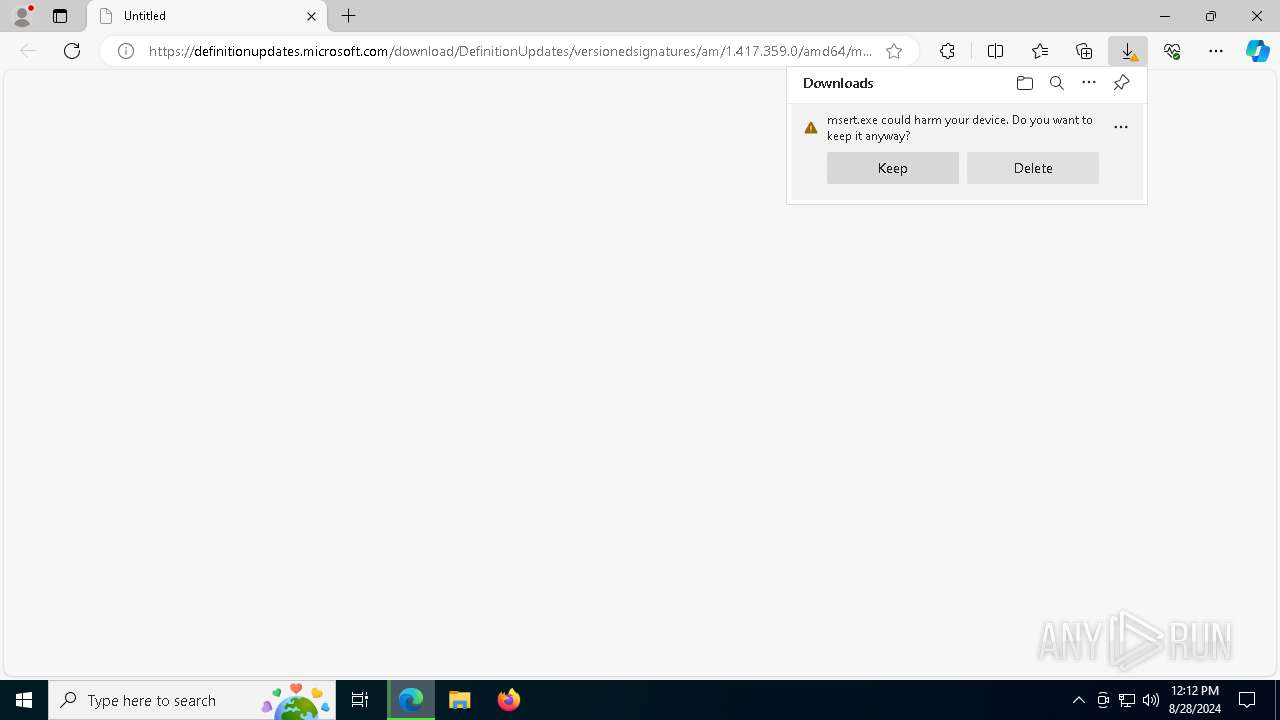
| URL: | https://definitionupdates.microsoft.com/download/DefinitionUpdates/versionedsignatures/am/1.417.359.0/amd64/msert.exe |
| Full analysis: | https://app.any.run/tasks/6ffaae0b-d86a-4622-91cd-b93f8d2fdb66 |
| Verdict: | Malicious activity |
| Threats: | Cobalt Strike is a legitimate penetration software toolkit developed by Forta. But its cracked versions are widely adopted by bad actors, who use it as a C2 system of choice for targeted attacks. |
| Analysis date: | August 28, 2024, 12:12:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | CFFD08AC2BB0614B7D05F6A2725088EE |
| SHA1: | 639F067F0A368C42FDA5920FB9DBEB364E8DD72A |
| SHA256: | 1A40EAFEF66AE545B3A4BE1874B33F7BC26E1E0596FB32EB725C7E47D6D19FA6 |
| SSDEEP: | 3:N8YTNQQdIetR8LWd/wrNNWWM6w2XAWSUS+VKhLTWAXRkA:2YTNQQdIeD8e/wr62AuS+VKh3H/ |
MALICIOUS
Actions looks like stealing of personal data
- msert.exe (PID: 3684)
ATLANTIDA has been detected (YARA)
- msert.exe (PID: 3684)
MASSLOGGER has been detected (YARA)
- msert.exe (PID: 3684)
DCRAT has been detected (YARA)
- msert.exe (PID: 3684)
M0YV has been detected (YARA)
- msert.exe (PID: 3684)
MIMIKATZ has been detected (YARA)
- msert.exe (PID: 3684)
GROWTOPIA has been detected (YARA)
- msert.exe (PID: 3684)
XORed URL has been found (YARA)
- msert.exe (PID: 3684)
DISCORDGRABBER has been detected (YARA)
- msert.exe (PID: 3684)
CRYPTBOT has been detected (YARA)
- msert.exe (PID: 3684)
COBALTSTRIKE has been detected (YARA)
- msert.exe (PID: 3684)
[YARA] DarkVision RAT is detected
- msert.exe (PID: 3684)
LUMMA has been detected (YARA)
- msert.exe (PID: 3684)
SODINOKIBI has been detected (YARA)
- msert.exe (PID: 3684)
CVE-2022-30190 detected
- msert.exe (PID: 3684)
SUSPICIOUS
Reads security settings of Internet Explorer
- msert.exe (PID: 6736)
- msert.exe (PID: 3684)
Reads the date of Windows installation
- msert.exe (PID: 6736)
Drops the executable file immediately after the start
- msert.exe (PID: 3684)
Application launched itself
- msert.exe (PID: 6736)
Checks Windows Trust Settings
- msert.exe (PID: 3684)
The process verifies whether the antivirus software is installed
- msert.exe (PID: 3684)
Found regular expressions for crypto-addresses (YARA)
- msert.exe (PID: 3684)
Detected use of alternative data streams (AltDS)
- msert.exe (PID: 3684)
Process drops legitimate windows executable
- msert.exe (PID: 3684)
Executable content was dropped or overwritten
- msert.exe (PID: 3684)
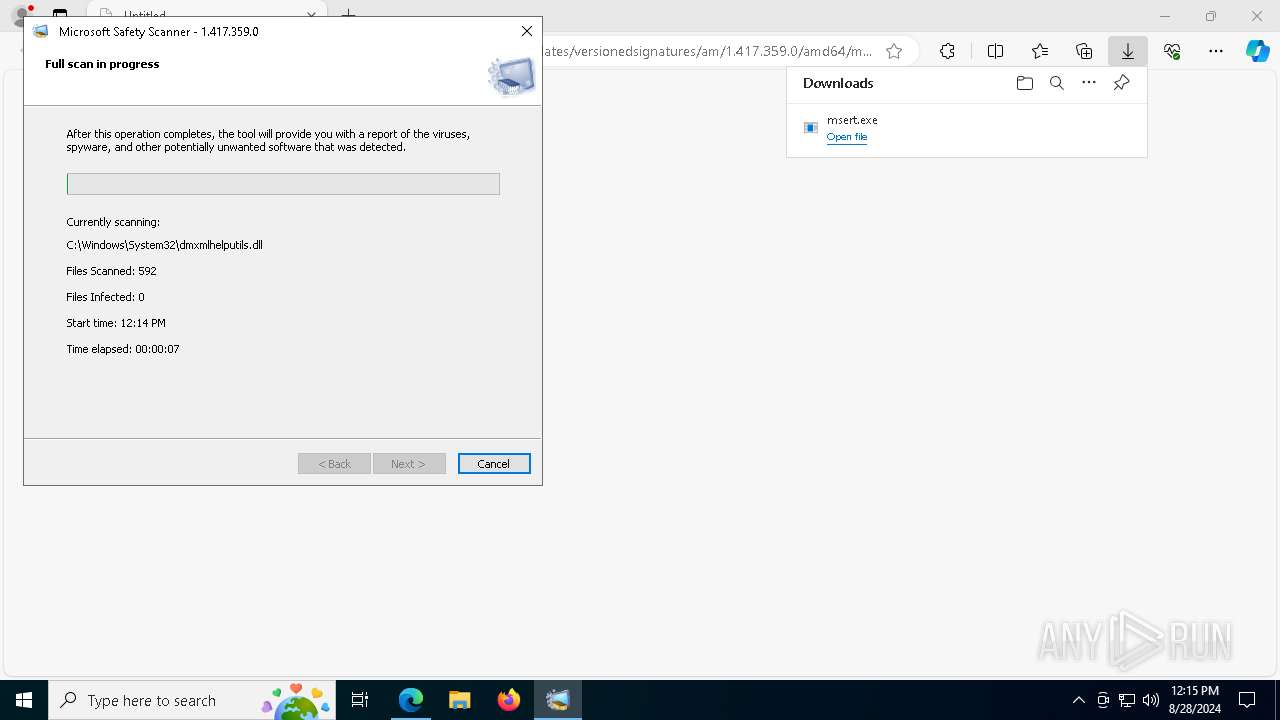
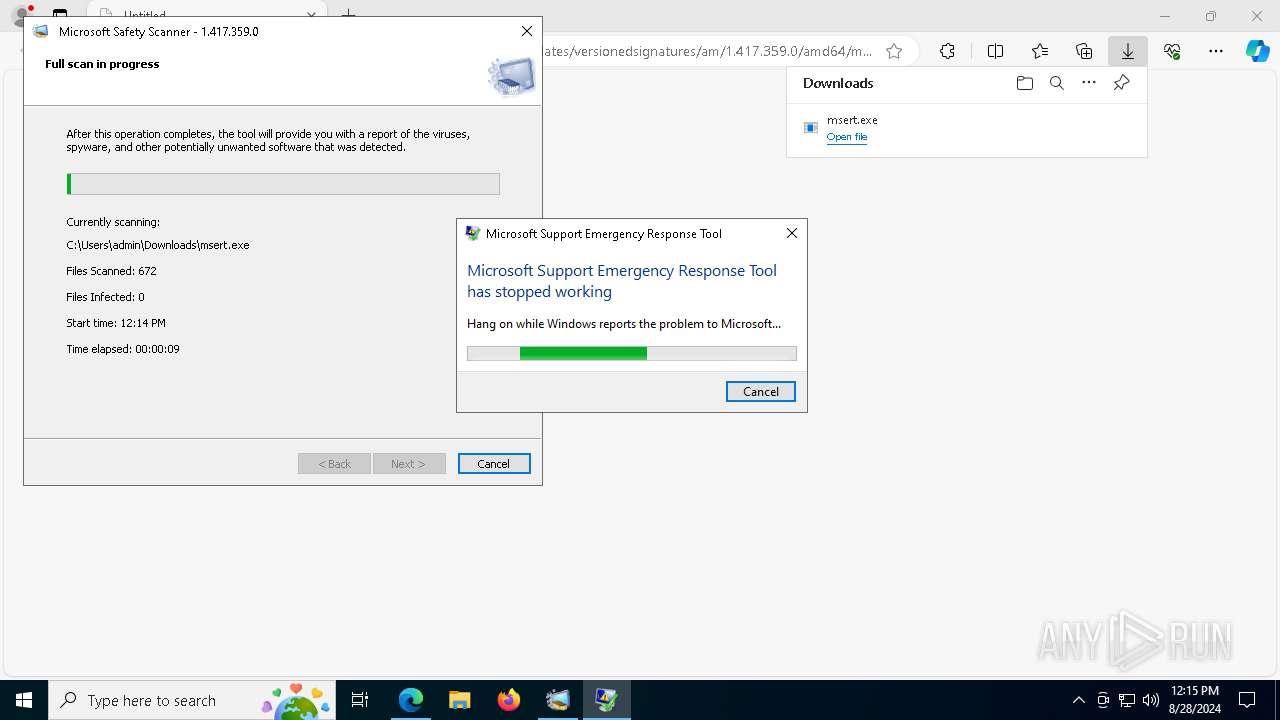
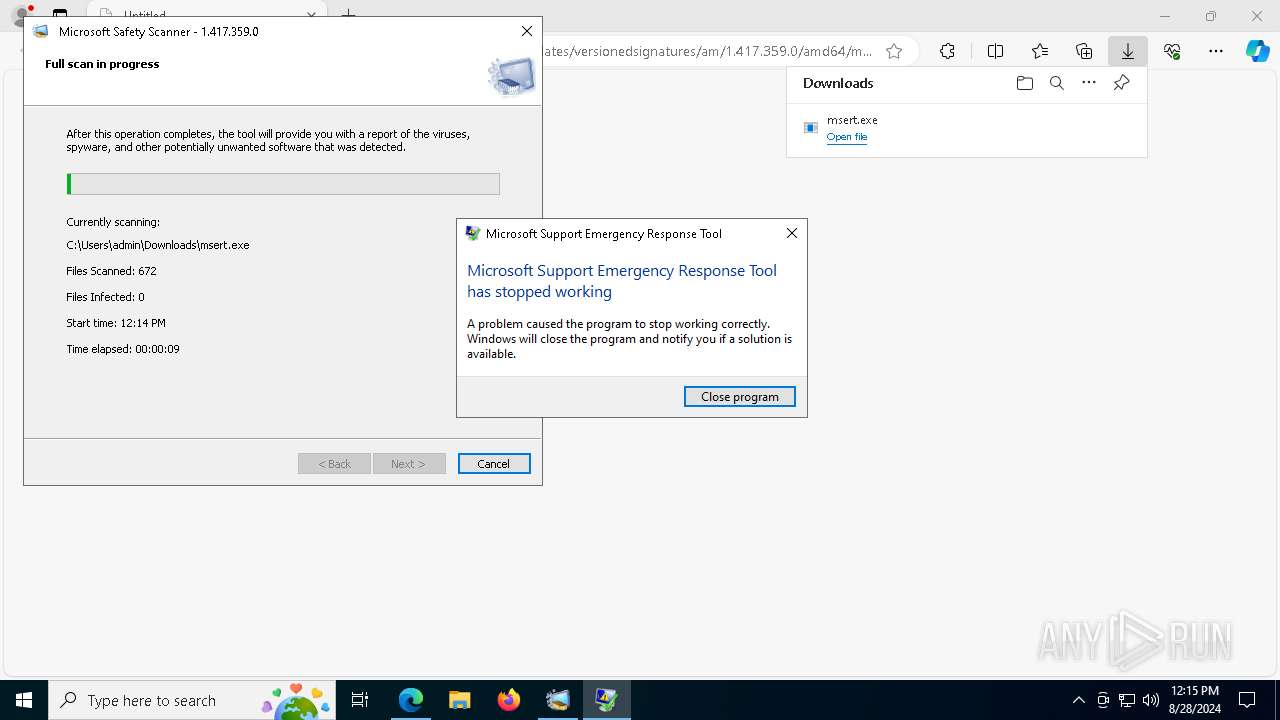
Executes application which crashes
- msert.exe (PID: 3684)
INFO
Application launched itself
- msedge.exe (PID: 6744)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6744)
- msert.exe (PID: 3684)
Executable content was dropped or overwritten
- msedge.exe (PID: 6744)
Checks supported languages
- msert.exe (PID: 6736)
- identity_helper.exe (PID: 4056)
- msert.exe (PID: 3684)
Reads Environment values
- identity_helper.exe (PID: 4056)
- msert.exe (PID: 3684)
Reads the computer name
- identity_helper.exe (PID: 4056)
- msert.exe (PID: 6736)
- msert.exe (PID: 3684)
Process checks computer location settings
- msert.exe (PID: 6736)
Reads the software policy settings
- slui.exe (PID: 6164)
- msert.exe (PID: 3684)
- WerFault.exe (PID: 5984)
- slui.exe (PID: 7128)
Reads the machine GUID from the registry
- msert.exe (PID: 3684)
Found Base64 encoded reference to WMI classes (YARA)
- msert.exe (PID: 3684)
Found Base64 encoded network access via PowerShell (YARA)
- msert.exe (PID: 3684)
Found Base64 encoded reference to AntiVirus WMI classes (YARA)
- msert.exe (PID: 3684)
Potential remote process memory reading (Base64 Encoded 'ReadProcessMemory')
- msert.exe (PID: 3684)
Potential remote process memory writing (Base64 Encoded 'WriteProcessMemory')
- msert.exe (PID: 3684)
Found Base64 encoded access to environment variables via PowerShell (YARA)
- msert.exe (PID: 3684)
Checks proxy server information
- slui.exe (PID: 7128)
- WerFault.exe (PID: 5984)
Potential library load (Base64 Encoded 'LoadLibrary')
- msert.exe (PID: 3684)
Found Base64 encoded reflection usage via PowerShell (YARA)
- msert.exe (PID: 3684)
Reads product name
- msert.exe (PID: 3684)
Potential modification of remote process state (Base64 Encoded 'SetThreadContext')
- msert.exe (PID: 3684)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- msert.exe (PID: 3684)
Found Base64 encoded text manipulation via PowerShell (YARA)
- msert.exe (PID: 3684)
UPX packer has been detected
- msert.exe (PID: 3684)
Manual execution by a user
- WINWORD.EXE (PID: 6032)
- mspaint.exe (PID: 5888)
- mspaint.exe (PID: 4020)
- mspaint.exe (PID: 7156)
Found Base64 encoded file access via PowerShell (YARA)
- msert.exe (PID: 3684)
Potential remote process memory interaction (Base64 Encoded 'VirtualAllocEx')
- msert.exe (PID: 3684)
Creates files or folders in the user directory
- WerFault.exe (PID: 5984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(3684) msert.exe
Decrypted-URLs (1)http://www.pdefender2009.com/buy.php
Decrypted-URLs (2)http://creatonprojects.com/drv32.data
http://powermpeg.com/
Decrypted-URLs (1)http://kurs.ru/index)551
Decrypted-URLs (1)http://khamenei.cogia.net/y.phpD
Decrypted-URLs (1)http://www.jjanfile.co.kr/mqqu?**rrr+oodkcli
Decrypted-URLs (1)http://888.843call.cn/adpack.txtF644F
Decrypted-URLs (2)http://34393.cn/xiao.exe%ALLUSERSPROFILE%
http://clicksmile.org/x92s/uc12vx04/xdtldil.php?id=350'1a
Decrypted-URLs (1)http://www.spamcatchero.biz/dl/bot.dll
Decrypted-URLs (2)http://74.81.81.65/~cledo
http://mymetavids.com/drv32.data
Decrypted-URLs (2)http://humbertocosta.quotaless.com/y.txthttp://silvanasz42.googlepages.com/y.txtw
http://silvanasz42.googlepages.com/y.txtw
Decrypted-URLs (1)http://dawateislami.net/html/fonts/taskkill
Decrypted-URLs (1)http://fund.cmc.orli
Decrypted-URLs (1)http://qd.netkill.com.cn/pw.txtfzfo
Decrypted-URLs (1)http://63.143.48.7/brN04/wap*1Fyxs
Decrypted-URLs (1)http://www.sjservicoAtualiza
Decrypted-URLs (1)http://66.228.132.8/index.htm
Decrypted-URLs (1)http://mm.21380.com/t/sleepdown/updatew
Total processes
201
Monitored processes
55
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5096 --field-trial-handle=2340,i,1836840264951754084,1835485063582856942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1104 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5296 --field-trial-handle=2340,i,1836840264951754084,1835485063582856942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1116 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7544 --field-trial-handle=2340,i,1836840264951754084,1835485063582856942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1172 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1752 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --no-appcompat-clear --mojo-platform-channel-handle=5976 --field-trial-handle=2340,i,1836840264951754084,1835485063582856942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2016 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5312 --field-trial-handle=2340,i,1836840264951754084,1835485063582856942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2056 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7044 --field-trial-handle=2340,i,1836840264951754084,1835485063582856942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2368 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=6056 --field-trial-handle=2340,i,1836840264951754084,1835485063582856942,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2724 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7024 --field-trial-handle=2340,i,1836840264951754084,1835485063582856942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2868 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5568 --field-trial-handle=2340,i,1836840264951754084,1835485063582856942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
42 864
Read events
42 282
Write events
536
Delete events
46
Modification events
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31127875 | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5464) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
9
Suspicious files
279
Text files
124
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF12a168.TMP | — | |
MD5:— | SHA256:— | |||
| 6744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF12a168.TMP | — | |
MD5:— | SHA256:— | |||
| 6744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF12a178.TMP | — | |
MD5:— | SHA256:— | |||
| 6744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF12a188.TMP | — | |
MD5:— | SHA256:— | |||
| 6744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF12a197.TMP | — | |
MD5:— | SHA256:— | |||
| 6744 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
72
DNS requests
72
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2032 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4284 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4ce3ae81-e2a0-4e0e-be1e-729206f9c8c0?P1=1725435785&P2=404&P3=2&P4=AeisVpA%2fePWwZsyvO4FA4hSTEhZ4OmdXgCLM8USyHhRtCWNdzvxK3R5hDTXaQXFB4A9XmAANRMebVKttRfUgQQ%3d%3d | unknown | — | — | whitelisted |
1680 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4284 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4ce3ae81-e2a0-4e0e-be1e-729206f9c8c0?P1=1725435785&P2=404&P3=2&P4=AeisVpA%2fePWwZsyvO4FA4hSTEhZ4OmdXgCLM8USyHhRtCWNdzvxK3R5hDTXaQXFB4A9XmAANRMebVKttRfUgQQ%3d%3d | unknown | — | — | whitelisted |
4284 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4ce3ae81-e2a0-4e0e-be1e-729206f9c8c0?P1=1725435785&P2=404&P3=2&P4=AeisVpA%2fePWwZsyvO4FA4hSTEhZ4OmdXgCLM8USyHhRtCWNdzvxK3R5hDTXaQXFB4A9XmAANRMebVKttRfUgQQ%3d%3d | unknown | — | — | whitelisted |
4284 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4ce3ae81-e2a0-4e0e-be1e-729206f9c8c0?P1=1725435785&P2=404&P3=2&P4=AeisVpA%2fePWwZsyvO4FA4hSTEhZ4OmdXgCLM8USyHhRtCWNdzvxK3R5hDTXaQXFB4A9XmAANRMebVKttRfUgQQ%3d%3d | unknown | — | — | whitelisted |
4284 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4ce3ae81-e2a0-4e0e-be1e-729206f9c8c0?P1=1725435785&P2=404&P3=2&P4=AeisVpA%2fePWwZsyvO4FA4hSTEhZ4OmdXgCLM8USyHhRtCWNdzvxK3R5hDTXaQXFB4A9XmAANRMebVKttRfUgQQ%3d%3d | unknown | — | — | whitelisted |
4284 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4ce3ae81-e2a0-4e0e-be1e-729206f9c8c0?P1=1725435785&P2=404&P3=2&P4=AeisVpA%2fePWwZsyvO4FA4hSTEhZ4OmdXgCLM8USyHhRtCWNdzvxK3R5hDTXaQXFB4A9XmAANRMebVKttRfUgQQ%3d%3d | unknown | — | — | whitelisted |
4284 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4e7e4c6f-7b62-49ca-a1fd-f625399e76b3?P1=1725324795&P2=404&P3=2&P4=JchVbm54G0%2bhLzFp850jwJzJ0Q3qIwAQWJcdwG%2bBZPRnAFTABztK6nCAWrLBslAzw6hlsrtFtJ5smXiolnyRBw%3d%3d | unknown | — | — | whitelisted |
4284 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4ce3ae81-e2a0-4e0e-be1e-729206f9c8c0?P1=1725435785&P2=404&P3=2&P4=AeisVpA%2fePWwZsyvO4FA4hSTEhZ4OmdXgCLM8USyHhRtCWNdzvxK3R5hDTXaQXFB4A9XmAANRMebVKttRfUgQQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6056 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6408 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7096 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6744 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7096 | msedge.exe | 23.212.88.205:443 | definitionupdates.microsoft.com | AKAMAI-AS | MX | whitelisted |
7096 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7096 | msedge.exe | 94.245.104.56:443 | api.edgeoffer.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7096 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
definitionupdates.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
api.edgeoffer.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|