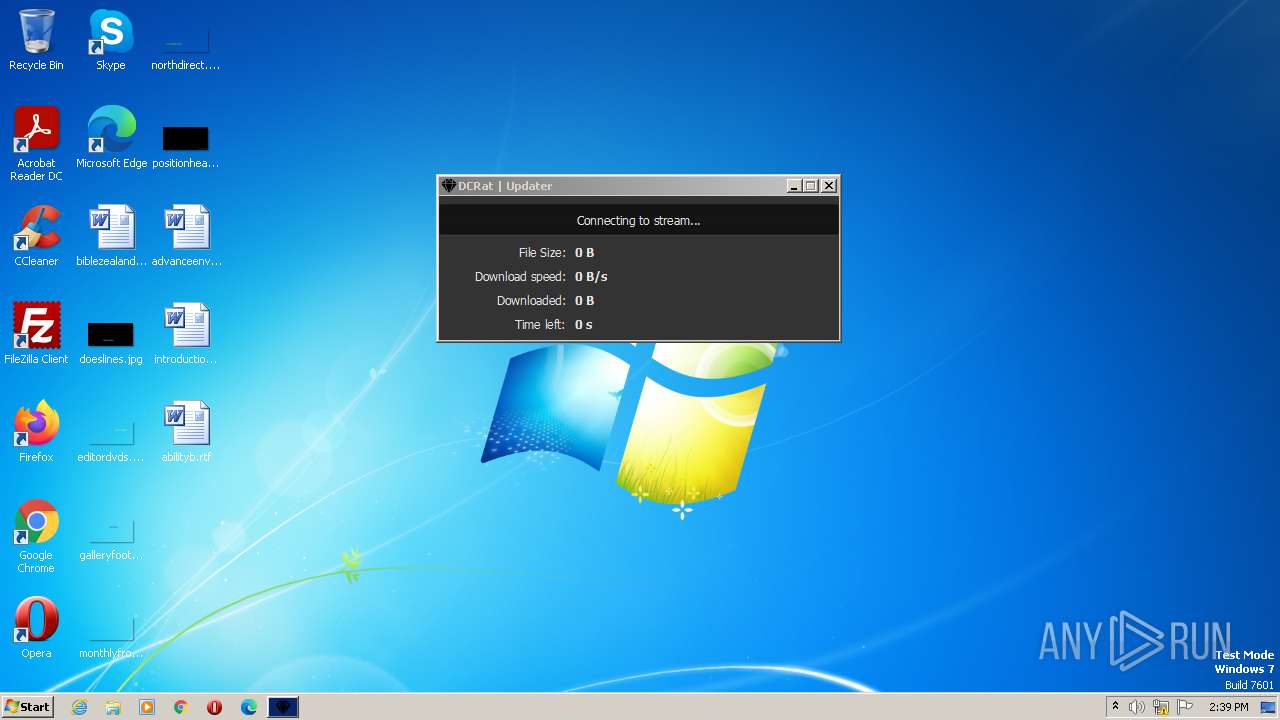
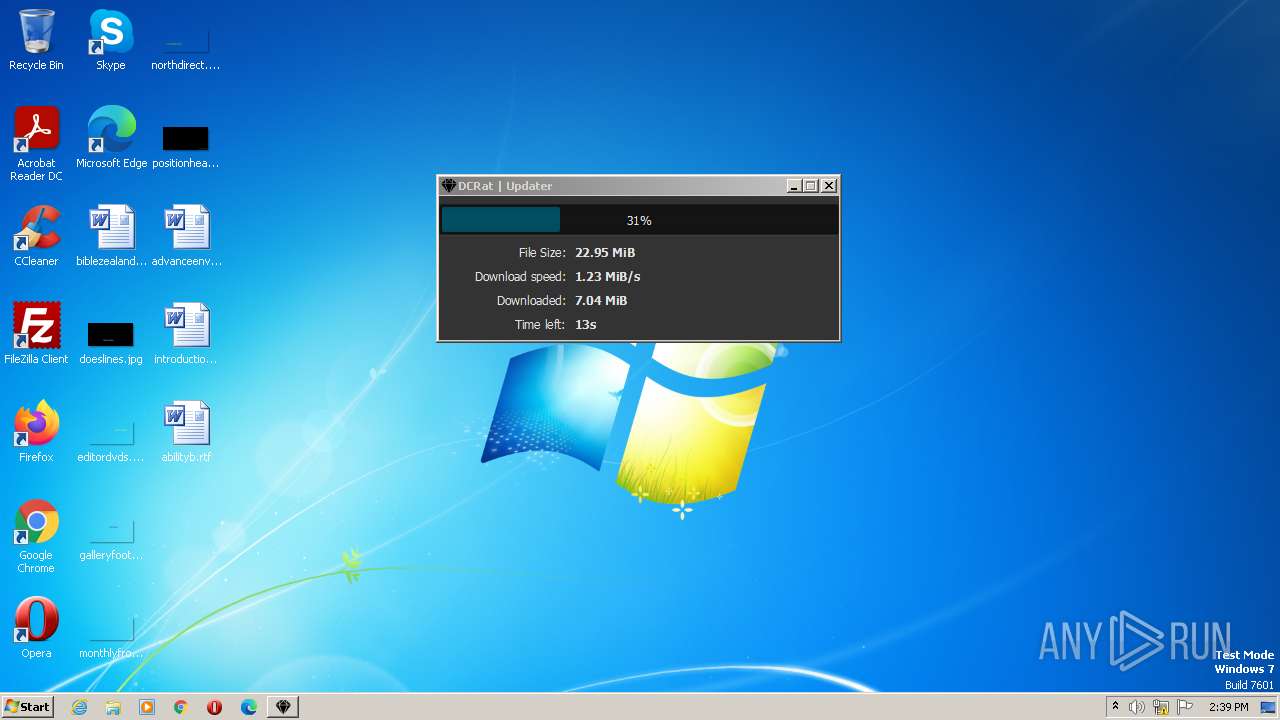
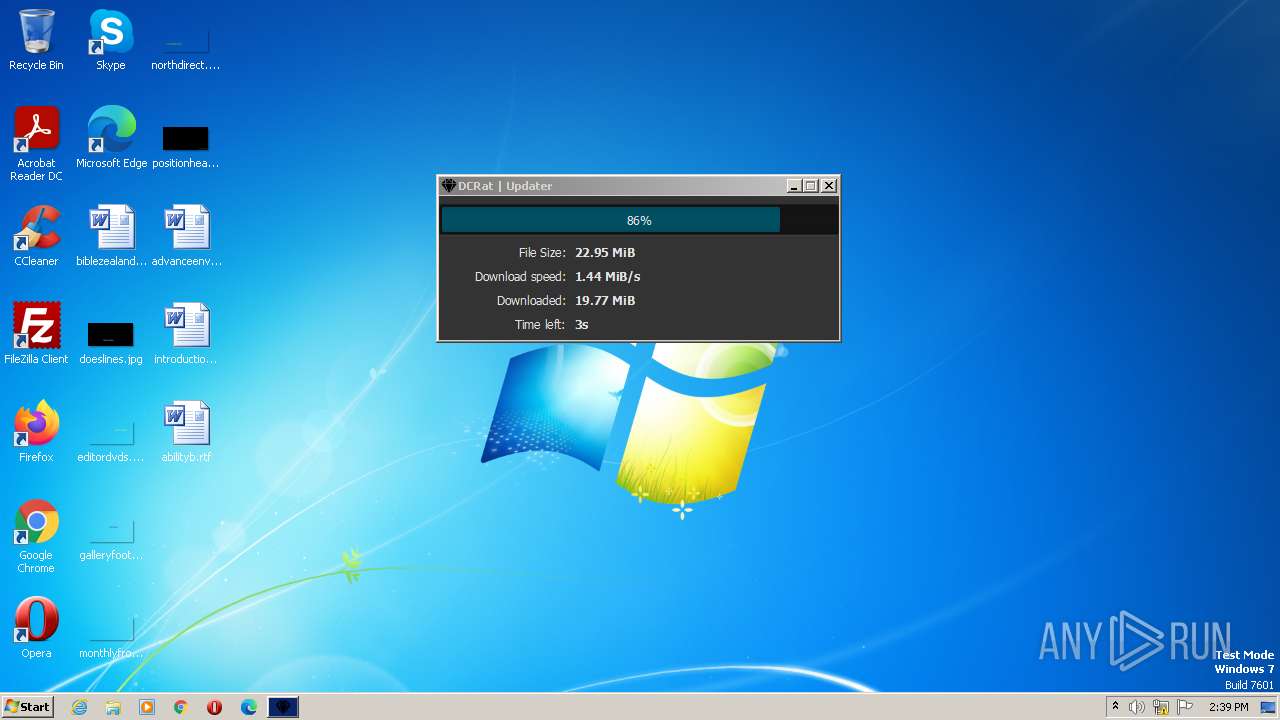
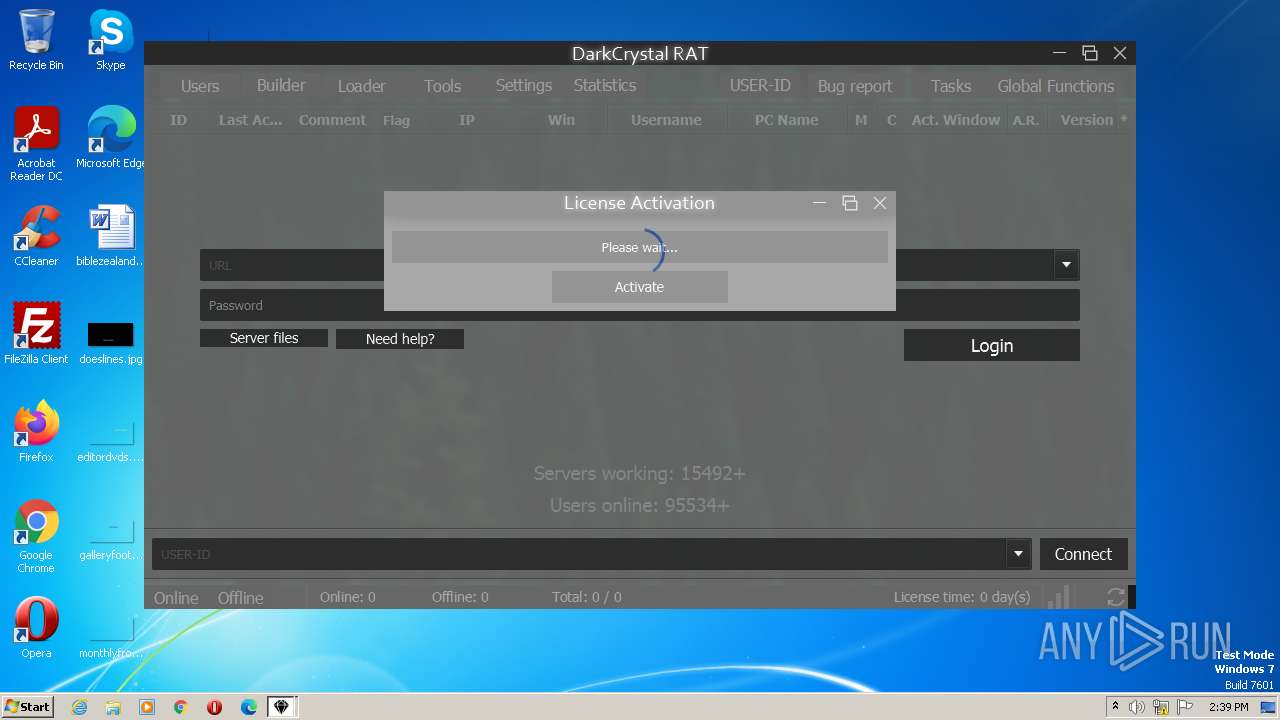
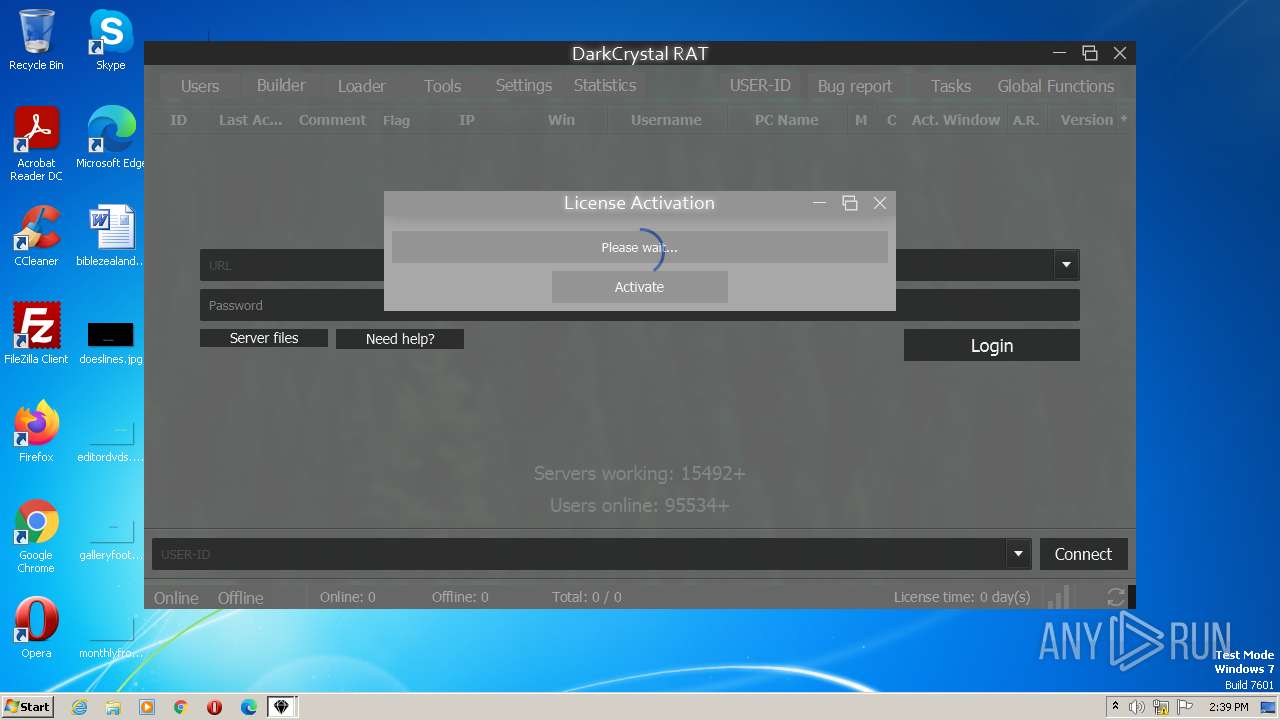
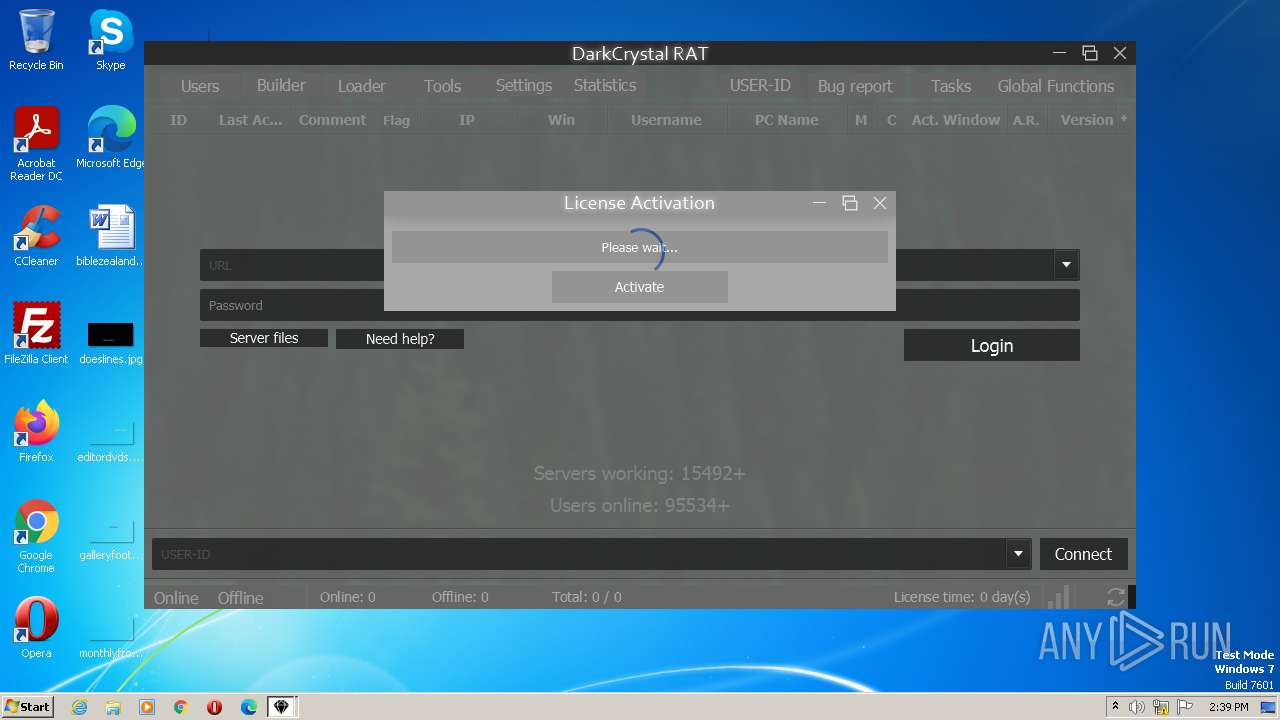
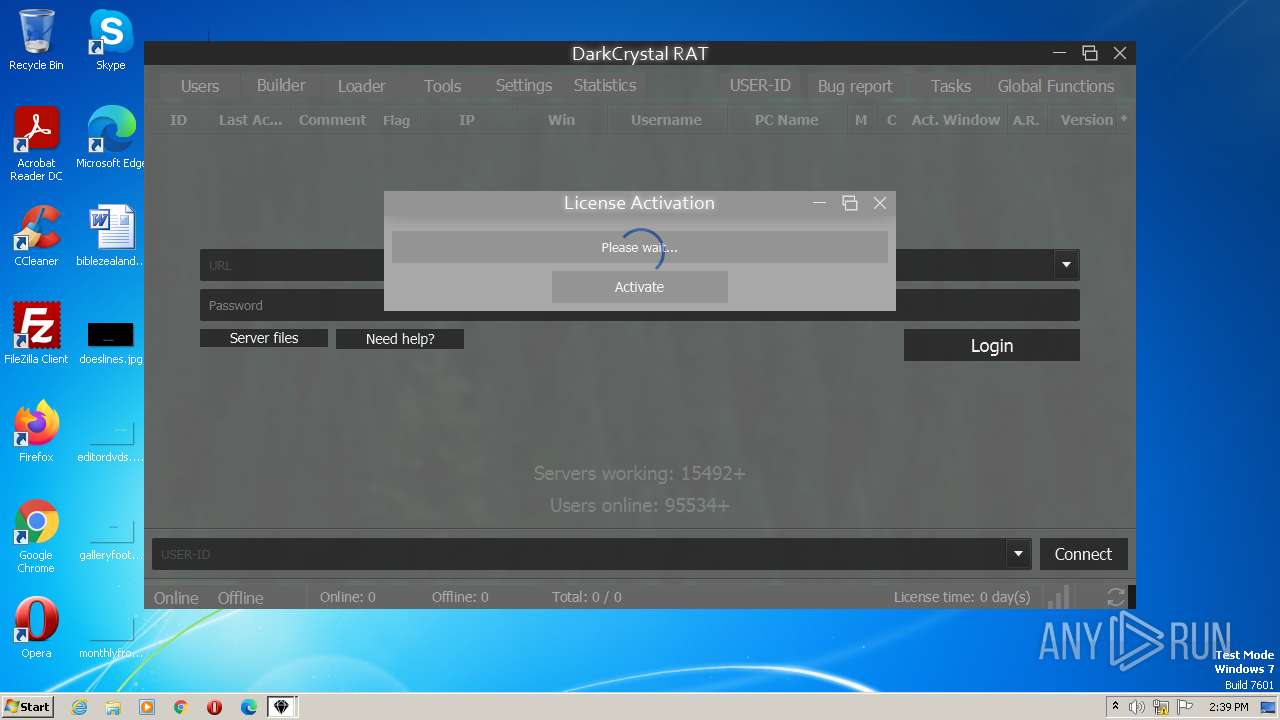
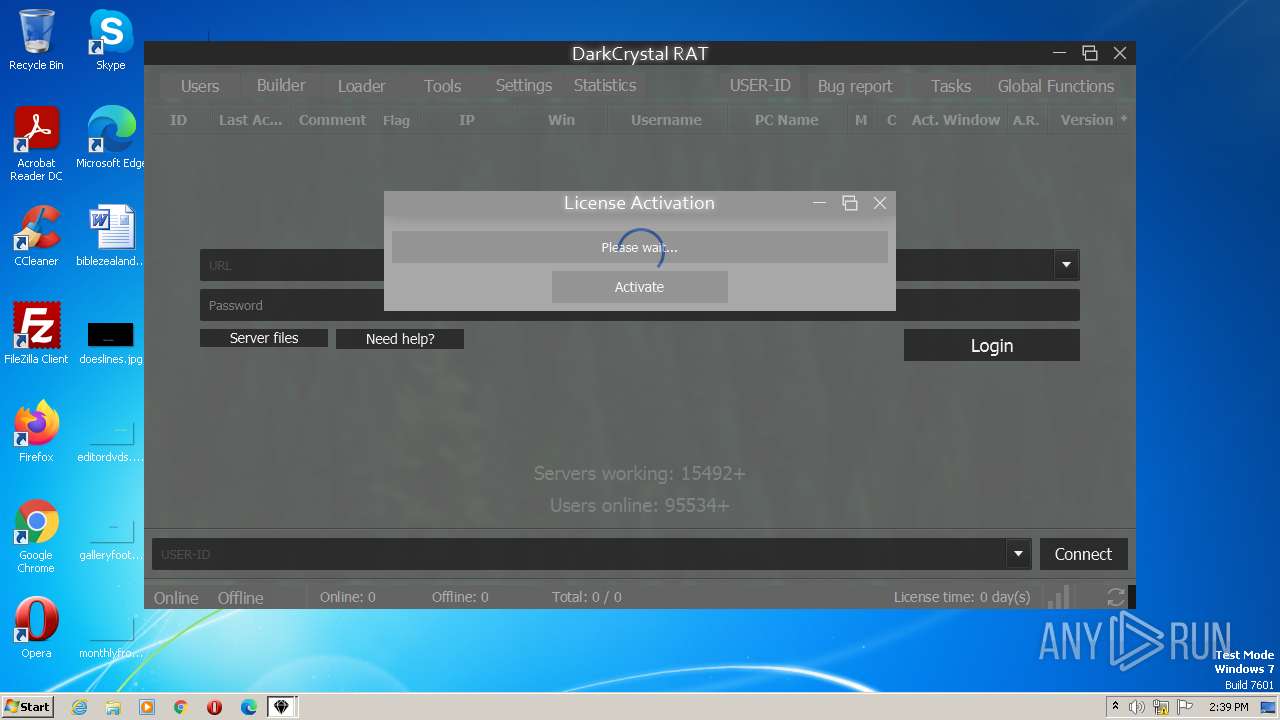
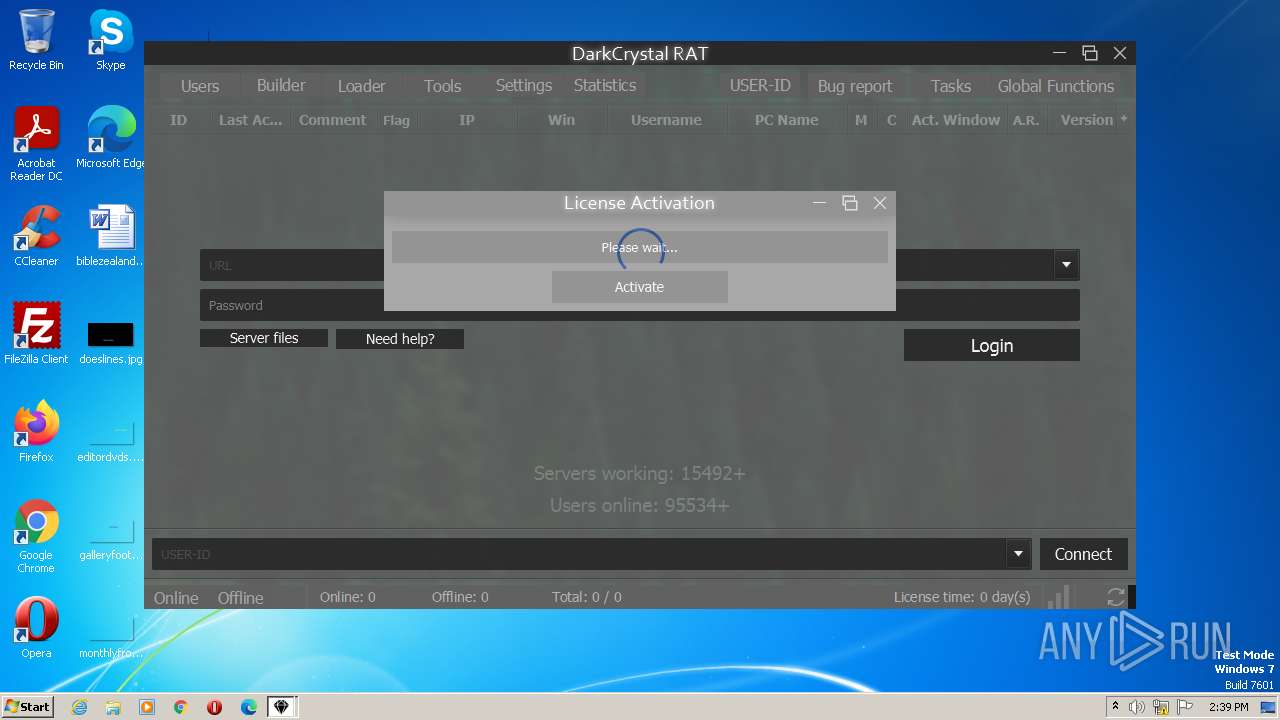
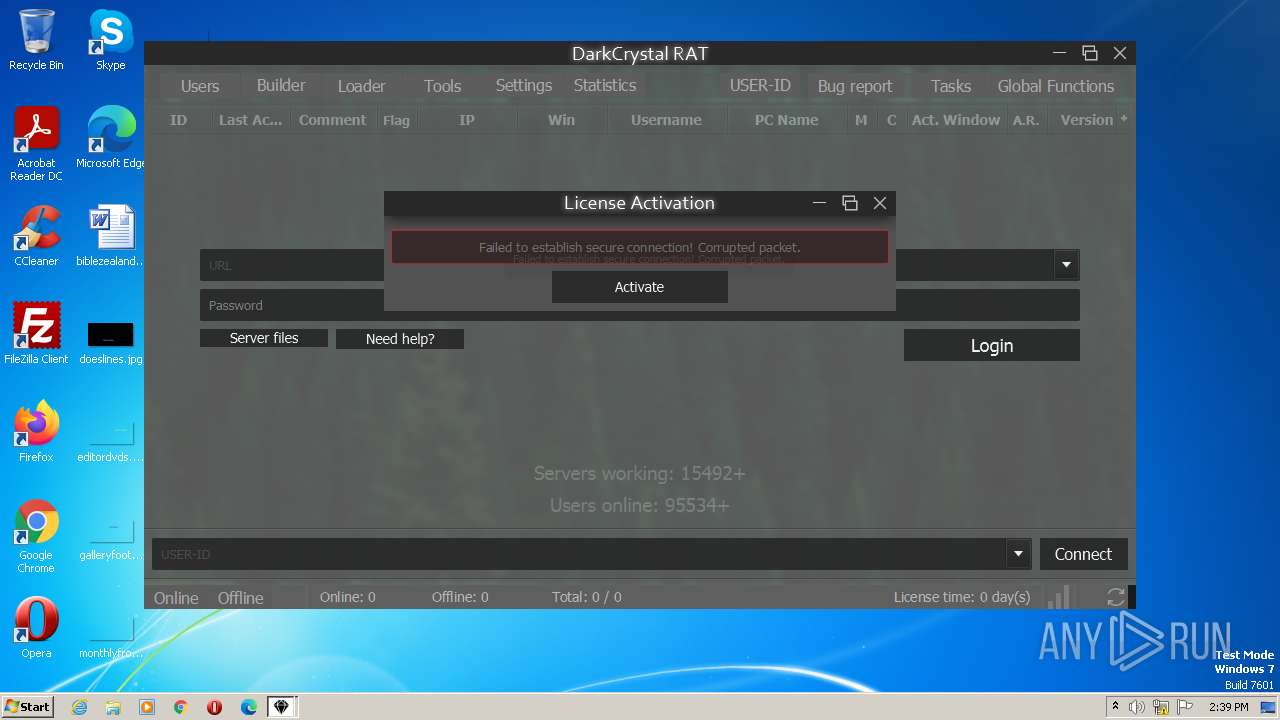
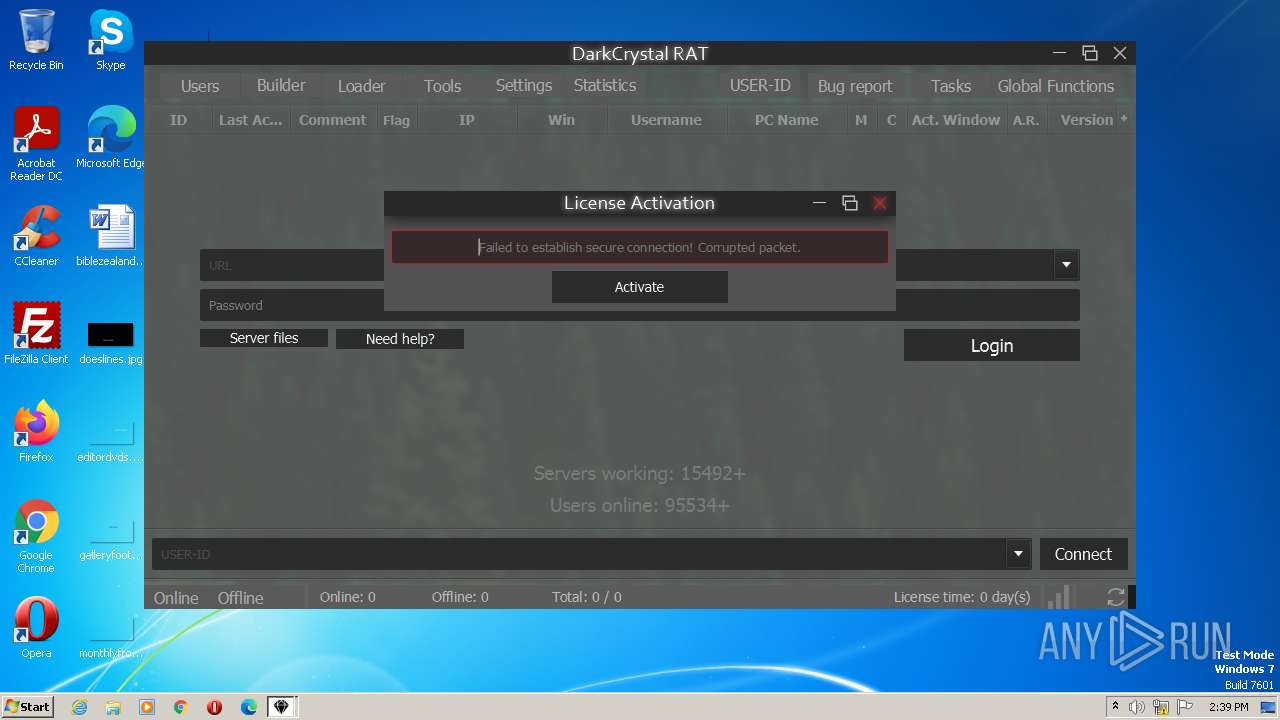
| File name: | dcrat_updservice.exe |
| Full analysis: | https://app.any.run/tasks/7e692ece-f314-42ea-9b27-a6a5bc778c7c |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | July 17, 2023, 13:38:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | 2EBBA84C4BBE13FDC53C9082918D5969 |
| SHA1: | FC95A94F45468593D1D85544E1928401484256CF |
| SHA256: | 1A232ABB03338036811688110B5A6D85B4A7C3FBF83A059DB8AA8ED7D6D57E70 |
| SSDEEP: | 98304:YRk4EIkn6pNrHJWGs2NyqeoNE/7SRYYJcl:YSd6pJHJack+Yl |
MALICIOUS
Application was dropped or rewritten from another process
- DCRat.exe (PID: 2988)
SUSPICIOUS
Checks for Java to be installed
- dcrat_updservice.exe (PID: 3272)
- DCRat.exe (PID: 2988)
Reads the Internet Settings
- explorer.exe (PID: 1232)
- WMIC.exe (PID: 3032)
- WMIC.exe (PID: 964)
- WMIC.exe (PID: 3984)
- WMIC.exe (PID: 3504)
- WMIC.exe (PID: 1840)
- WMIC.exe (PID: 856)
Executable content was dropped or overwritten
- javaw.exe (PID: 3620)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 3320)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 2600)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- cmd.exe (PID: 3580)
- cmd.exe (PID: 2976)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 3416)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 3656)
- cmd.exe (PID: 2448)
INFO
Checks supported languages
- dcrat_updservice.exe (PID: 3272)
- javaw.exe (PID: 3620)
- DCRat.exe (PID: 2988)
- javaw.exe (PID: 3320)
The process checks LSA protection
- javaw.exe (PID: 3620)
- icacls.exe (PID: 3392)
- explorer.exe (PID: 1348)
- explorer.exe (PID: 1232)
- javaw.exe (PID: 3320)
- WMIC.exe (PID: 3032)
- WMIC.exe (PID: 964)
- WMIC.exe (PID: 3504)
- WMIC.exe (PID: 1840)
- WMIC.exe (PID: 856)
- WMIC.exe (PID: 3984)
Reads the computer name
- javaw.exe (PID: 3620)
- javaw.exe (PID: 3320)
Reads the machine GUID from the registry
- javaw.exe (PID: 3620)
- javaw.exe (PID: 3320)
Creates files in the program directory
- javaw.exe (PID: 3620)
Create files in a temporary directory
- javaw.exe (PID: 3320)
- javaw.exe (PID: 3620)
Creates files or folders in the user directory
- javaw.exe (PID: 3320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 4 |
| ImageVersion: | 1 |
| OSVersion: | 4 |
| EntryPoint: | 0x1290 |
| UninitializedDataSize: | 36864 |
| InitializedDataSize: | 65024 |
| CodeSize: | 25088 |
| LinkerVersion: | 2.22 |
| PEType: | PE32 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| TimeStamp: | 2021:09:19 11:00:06+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Sep-2021 11:00:06 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 19-Sep-2021 11:00:06 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00006080 | 0x00006200 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.98243 |
.data | 0x00008000 | 0x00000040 | 0x00000200 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.163808 |
.rdata | 0x00009000 | 0x00000510 | 0x00000600 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.01355 |
.bss | 0x0000A000 | 0x00008E30 | 0x00000000 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00013000 | 0x00000AA8 | 0x00000C00 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.65264 |
.rsrc | 0x00014000 | 0x0000E952 | 0x0000EA00 | IMAGE_SCN_ALIGN_1024BYTES, IMAGE_SCN_ALIGN_16BYTES, IMAGE_SCN_ALIGN_1BYTES, IMAGE_SCN_ALIGN_256BYTES, IMAGE_SCN_ALIGN_2BYTES, IMAGE_SCN_ALIGN_32BYTES, IMAGE_SCN_ALIGN_4096BYTES, IMAGE_SCN_ALIGN_4BYTES, IMAGE_SCN_ALIGN_512BYTES, IMAGE_SCN_ALIGN_64BYTES, IMAGE_SCN_ALIGN_8192BYTES, IMAGE_SCN_ALIGN_MASK, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.52557 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 2.93465 | 118 | UNKNOWN | Process Default Language | RT_GROUP_ICON |
2 | 2.25163 | 6 | UNKNOWN | Process Default Language | RT_RCDATA |
3 | 4.08494 | 9640 | UNKNOWN | Process Default Language | RT_ICON |
4 | 4.14548 | 6760 | UNKNOWN | Process Default Language | RT_ICON |
5 | 4.14132 | 4264 | UNKNOWN | Process Default Language | RT_ICON |
6 | 4.33102 | 2440 | UNKNOWN | Process Default Language | RT_ICON |
7 | 4.43035 | 1720 | UNKNOWN | Process Default Language | RT_ICON |
8 | 1 | 2 | UNKNOWN | Process Default Language | RT_RCDATA |
12 | 4.0958 | 22 | UNKNOWN | Process Default Language | RT_RCDATA |
15 | 4.21782 | 41 | UNKNOWN | Process Default Language | RT_RCDATA |
Imports
ADVAPI32.DLL |
KERNEL32.dll |
SHELL32.DLL |
USER32.dll |
msvcrt.dll |
Total processes
64
Monitored processes
20
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | C:\Windows\System32\wbem\wmic.exe diskdrive where 'Index=0' get 'size' | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 964 | C:\Windows\System32\wbem\wmic.exe baseboard get Product | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1348 | explorer C:\Users\admin\AppData\Local\Temp\DCRat.exe | C:\Windows\explorer.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1840 | C:\Windows\System32\wbem\wmic.exe Path Win32_VideoController Get VideoProcessor | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2296 | C:\Windows\System32\cmd.exe /c USERPROFILE | C:\Windows\System32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2448 | C:\Windows\System32\cmd.exe /c C:\Windows\System32\wbem\wmic.exe diskdrive where 'Index=0' get 'size' | C:\Windows\System32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2600 | C:\Windows\System32\cmd.exe /c C:\Windows\System32\wbem\wmic.exe Path Win32_VideoController Get VideoProcessor | C:\Windows\System32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2976 | C:\Windows\System32\cmd.exe /c C:\Windows\System32\wbem\wmic.exe baseboard get Product | C:\Windows\System32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2988 | "C:\Users\admin\AppData\Local\Temp\DCRat.exe" | C:\Users\admin\AppData\Local\Temp\DCRat.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 939
Read events
1 925
Write events
14
Delete events
0
Modification events
| (PID) Process: | (3620) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (1232) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1232) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1232) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1232) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3320) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
Executable files
21
Suspicious files
33
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3620 | javaw.exe | C:\Users\admin\AppData\Local\Temp\design\DeleteAll_legacy.json | text | |
MD5:9F362DF9EAE724C6FA1206150FA64A08 | SHA256:4BA6475A0A4C6C5066EDF7E6804B3AEA7F068158A5D4F6338CD588AABFB5761B | |||
| 3620 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:9C71098EBCE178C6B5EB877B2359C1BE | SHA256:681AFF035D198376C1B1C07AA234AC26EE2CAEDB73AC1CF13EBD0D61FB6ED77D | |||
| 3620 | javaw.exe | C:\Users\admin\AppData\Local\Temp\temp.zip | compressed | |
MD5:61404CC344C15B006188966F1DB9300E | SHA256:C0FE61672CE0F0BB6A2B6F64ED722786E7D4A9EE90DA18F9F6DF391AEABB976E | |||
| 3620 | javaw.exe | C:\Users\admin\AppData\Local\Temp\data\Rar.exe | executable | |
MD5:EB24024A8A46C71303E0B18D0E1859F6 | SHA256:770D7B5E40ED9B0AFF5D0E3FC2CCF9BA10D4925D3441F38B71A35BD26E6E8D98 | |||
| 3620 | javaw.exe | C:\Users\admin\AppData\Local\Temp\data\enc.vbe | binary | |
MD5:F88125F6EAFC7F4805913CF4077B2525 | SHA256:5981E508E89C65C445FCA892E91B8EC39B1D8563804D0999D963D640AA592444 | |||
| 3620 | javaw.exe | C:\Users\admin\AppData\Local\Temp\data\NCC2.dll | executable | |
MD5:12E7983A050A5F7F7B501D3CDA914248 | SHA256:A0B6BB521E52A99ABF5AC1017302DA014D37296619078D42D9EDF5D86D137F63 | |||
| 3620 | javaw.exe | C:\Users\admin\AppData\Local\Temp\data\dnlib.dll | executable | |
MD5:DE0069C4097C987BD30EBE8155A8AF35 | SHA256:83445595D38A8E33513B33DFC201983AF4746E5327C9BED470A6282D91D539B6 | |||
| 3620 | javaw.exe | C:\Users\admin\AppData\Local\Temp\data\dotNET_Reactor.exe | executable | |
MD5:BBC5441ECD131F5A98DFF8BE2EBC5294 | SHA256:78684AEA83B1A5C402A87BA0CE2E7AD5B0338462CC804E97369203CE53D29834 | |||
| 3620 | javaw.exe | C:\Users\admin\AppData\Local\Temp\data\dotNET_Reactor.Console.exe | executable | |
MD5:0B4DBF61A98F3E34CDD3A1B08A6A4609 | SHA256:E817802F166662A7DF0B144571354D74B10E34D120F91AE9D84CA3BA925241C6 | |||
| 3620 | javaw.exe | C:\Users\admin\AppData\Local\Temp\data\DCRCC.exe | executable | |
MD5:7369469D49C34493F1B8A06FC89D9C7F | SHA256:8F5B38FDDE20187E5AB965E60C024B98DEF9D565EA23F596DA4FE13D12E5F5B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
7
DNS requests
3
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1068 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3620 | javaw.exe | 172.67.199.24:443 | cdn.dcrat.ru | CLOUDFLARENET | US | malicious |
3320 | javaw.exe | 104.21.21.138:443 | cdn.dcrat.ru | CLOUDFLARENET | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.dcrat.ru |
| malicious |
dcrat.ru |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1068 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE DCRat Related CnC Domain in DNS Lookup |