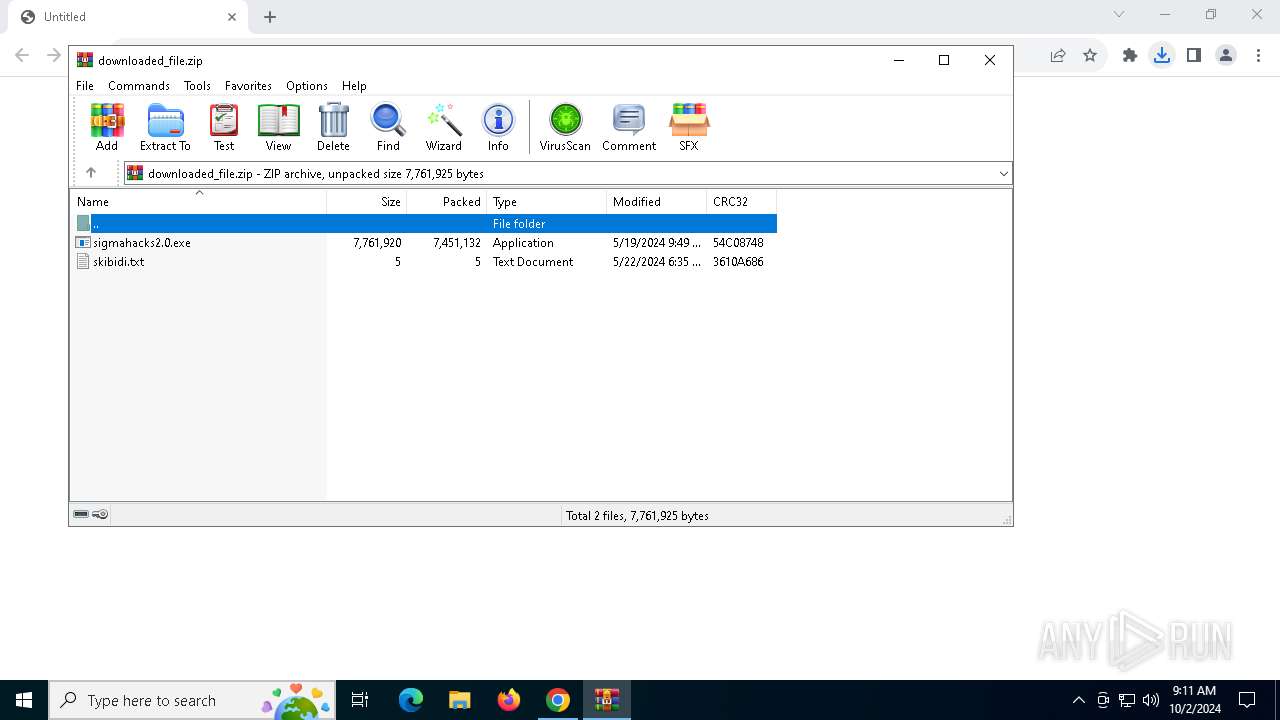
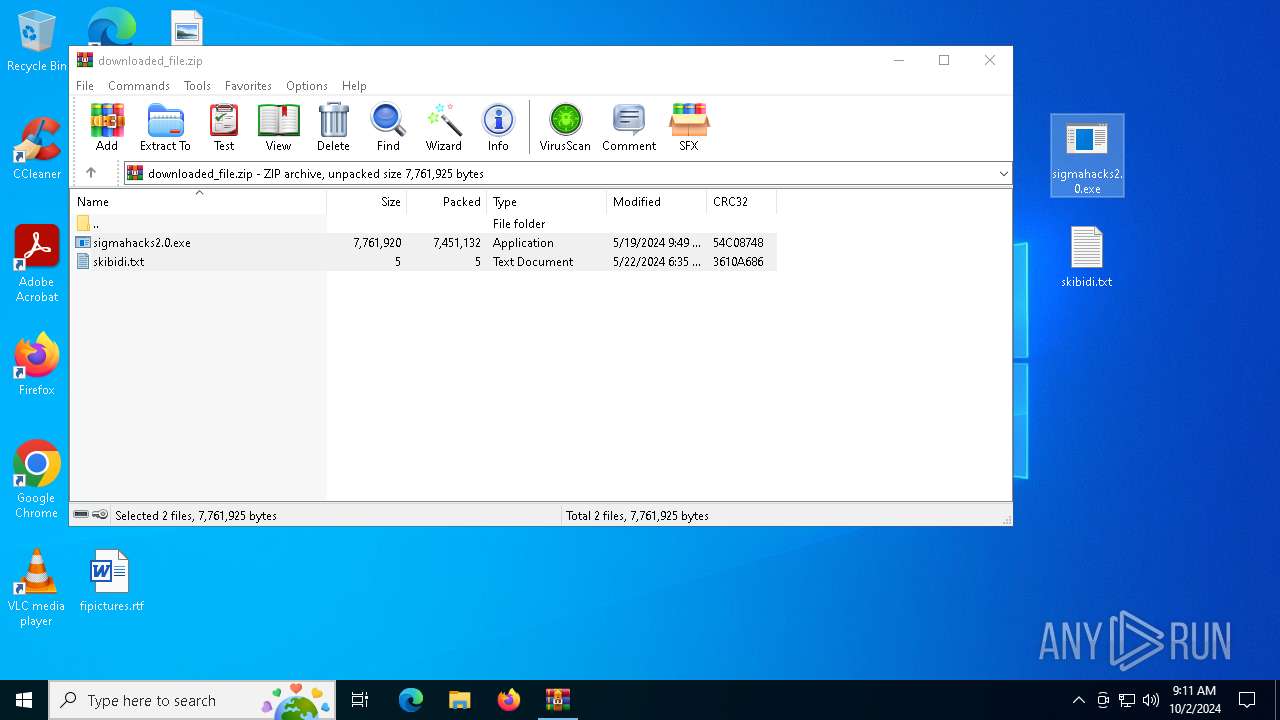
| URL: | https://github.com/nxllone/Auto-MoonSec-v3-Dumper/releases/download/Lua/downloaded_file.zip |
| Full analysis: | https://app.any.run/tasks/6f2df5f0-efef-4df4-8038-8a2471a45a16 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | October 02, 2024, 09:11:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3407C3DE10861E1CCC83F9D672DBC930 |
| SHA1: | 9368280654566252C833A728F201107A00F4E13E |
| SHA256: | 19FF216A508A8D2DADE43DC1B7A2040C716B09EF614B06BA84396A1EAEFF92FF |
| SSDEEP: | 3:N8tEd79K0ScXuJAE2kC+o4sBo9YV:2uv8FJArA9YV |
MALICIOUS
Application was injected by another process
- lsass.exe (PID: 768)
- winlogon.exe (PID: 684)
- dwm.exe (PID: 852)
- svchost.exe (PID: 476)
- svchost.exe (PID: 1200)
- svchost.exe (PID: 1036)
- svchost.exe (PID: 1316)
- svchost.exe (PID: 1472)
- svchost.exe (PID: 1628)
- svchost.exe (PID: 1364)
- svchost.exe (PID: 1620)
- svchost.exe (PID: 1408)
- svchost.exe (PID: 2072)
- svchost.exe (PID: 1508)
- svchost.exe (PID: 1588)
- svchost.exe (PID: 1600)
- svchost.exe (PID: 1816)
- svchost.exe (PID: 1872)
- svchost.exe (PID: 1208)
- svchost.exe (PID: 1272)
- svchost.exe (PID: 1796)
- svchost.exe (PID: 2344)
- svchost.exe (PID: 2000)
- svchost.exe (PID: 2412)
- svchost.exe (PID: 2160)
- svchost.exe (PID: 2496)
- svchost.exe (PID: 2256)
- svchost.exe (PID: 2312)
- svchost.exe (PID: 2184)
- spoolsv.exe (PID: 2592)
- svchost.exe (PID: 2692)
- svchost.exe (PID: 2996)
- svchost.exe (PID: 3020)
- svchost.exe (PID: 2304)
- svchost.exe (PID: 3012)
- svchost.exe (PID: 2788)
- svchost.exe (PID: 3056)
- svchost.exe (PID: 2968)
- svchost.exe (PID: 3200)
- svchost.exe (PID: 3340)
- OfficeClickToRun.exe (PID: 2656)
- dasHost.exe (PID: 3692)
- svchost.exe (PID: 3496)
- svchost.exe (PID: 3548)
- svchost.exe (PID: 3260)
- svchost.exe (PID: 4184)
- svchost.exe (PID: 3220)
- svchost.exe (PID: 4300)
- svchost.exe (PID: 3408)
- svchost.exe (PID: 3304)
- svchost.exe (PID: 4140)
- svchost.exe (PID: 3888)
- MoUsoCoreWorker.exe (PID: 2120)
- explorer.exe (PID: 4552)
- svchost.exe (PID: 4332)
- sihost.exe (PID: 4112)
- svchost.exe (PID: 4808)
- RuntimeBroker.exe (PID: 4244)
- svchost.exe (PID: 4324)
- dllhost.exe (PID: 5568)
- RuntimeBroker.exe (PID: 776)
- dllhost.exe (PID: 3312)
- svchost.exe (PID: 5416)
- ApplicationFrameHost.exe (PID: 4052)
- RuntimeBroker.exe (PID: 5560)
- UserOOBEBroker.exe (PID: 2744)
- svchost.exe (PID: 5236)
- svchost.exe (PID: 5256)
- svchost.exe (PID: 1824)
- svchost.exe (PID: 5036)
- dllhost.exe (PID: 4996)
- svchost.exe (PID: 5996)
- svchost.exe (PID: 6052)
- uhssvc.exe (PID: 536)
- svchost.exe (PID: 4000)
- svchost.exe (PID: 2520)
- svchost.exe (PID: 2956)
- svchost.exe (PID: 6360)
- svchost.exe (PID: 5940)
- svchost.exe (PID: 2208)
- svchost.exe (PID: 2476)
- svchost.exe (PID: 3084)
- WmiPrvSE.exe (PID: 5112)
- svchost.exe (PID: 6284)
- WmiPrvSE.exe (PID: 6336)
- svchost.exe (PID: 6852)
- svchost.exe (PID: 2580)
- RuntimeBroker.exe (PID: 4668)
- svchost.exe (PID: 1864)
- taskhostw.exe (PID: 2088)
- svchost.exe (PID: 5244)
- svchost.exe (PID: 4532)
- ctfmon.exe (PID: 4356)
Adds extension to the Windows Defender exclusion list
- sigmahacks2.0.exe (PID: 4712)
- elzltdtrkrql.exe (PID: 5976)
Runs injected code in another process
- dialer.exe (PID: 5632)
- dialer.exe (PID: 5104)
MINER has been detected (SURICATA)
- dialer.exe (PID: 5164)
- svchost.exe (PID: 2256)
Connects to the CnC server
- dialer.exe (PID: 5164)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- sigmahacks2.0.exe (PID: 5164)
- sigmahacks2.0.exe (PID: 4712)
- elzltdtrkrql.exe (PID: 5976)
Powershell scripting: start process
- sigmahacks2.0.exe (PID: 5164)
Script adds exclusion path to Windows Defender
- sigmahacks2.0.exe (PID: 4712)
- elzltdtrkrql.exe (PID: 5976)
Script adds exclusion extension to Windows Defender
- sigmahacks2.0.exe (PID: 4712)
- elzltdtrkrql.exe (PID: 5976)
Starts CMD.EXE for commands execution
- sigmahacks2.0.exe (PID: 4712)
- elzltdtrkrql.exe (PID: 5976)
Uses powercfg.exe to modify the power settings
- sigmahacks2.0.exe (PID: 4712)
- elzltdtrkrql.exe (PID: 5976)
Process uninstalls Windows update
- wusa.exe (PID: 5476)
- wusa.exe (PID: 5068)
Starts SC.EXE for service management
- sigmahacks2.0.exe (PID: 4712)
Executable content was dropped or overwritten
- sigmahacks2.0.exe (PID: 4712)
- elzltdtrkrql.exe (PID: 5976)
Executes as Windows Service
- elzltdtrkrql.exe (PID: 5976)
Potential Corporate Privacy Violation
- dialer.exe (PID: 5164)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2256)
- dialer.exe (PID: 5164)
Drops a system driver (possible attempt to evade defenses)
- elzltdtrkrql.exe (PID: 5976)
INFO
Creates files in the program directory
- MoUsoCoreWorker.exe (PID: 2120)
Application launched itself
- chrome.exe (PID: 6364)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3276)
Manual execution by a user
- sigmahacks2.0.exe (PID: 5164)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4552)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
192
Monitored processes
148
Malicious processes
99
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 476 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | "C:\Program Files\Microsoft Update Health Tools\uhssvc.exe" | C:\Program Files\Microsoft Update Health Tools\uhssvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Update Health Service Version: 10.0.19041.3626 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 752 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | C:\WINDOWS\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | C:\Windows\System32\RuntimeBroker.exe -Embedding | C:\Windows\System32\RuntimeBroker.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 852 | "dwm.exe" | C:\Windows\System32\dwm.exe | winlogon.exe | ||||||||||||
User: DWM-1 Company: Microsoft Corporation Integrity Level: SYSTEM Description: Desktop Window Manager Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 884 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
48 653
Read events
47 647
Write events
558
Delete events
448
Modification events
| (PID) Process: | (1316) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{C2AF3602-9179-4BAE-85B3-74A4EF5CF51F} |
| Operation: | write | Name: | DynamicInfo |
Value: 03000000BDCB09F80A59DA0160E3C610AB14DB0100000000000000001CB00A14AB14DB01 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000008C00000000000000 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000190068 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456033BCEE44DE41B4E8AEC331E84F566D2 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppBadgeUpdated |
| Operation: | write | Name: | Chrome |
Value: 6 | |||
| (PID) Process: | (6364) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6364) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6364) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6364) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6364) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5236) svchost.exe | Key: | \REGISTRY\A\{86337897-999e-fb05-e6d0-f7eb349132bc}\Root\InventoryDevicePnp |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
Executable files
4
Suspicious files
117
Text files
46
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6364 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF3f5541.TMP | — | |
MD5:— | SHA256:— | |||
| 6364 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6364 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF3f5551.TMP | — | |
MD5:— | SHA256:— | |||
| 6364 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF3f5551.TMP | — | |
MD5:— | SHA256:— | |||
| 6364 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6364 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF3f5561.TMP | — | |
MD5:— | SHA256:— | |||
| 6364 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6364 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6364 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF3f5570.TMP | — | |
MD5:— | SHA256:— | |||
| 6364 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
55
DNS requests
28
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1144 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5996 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3588 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1144 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2620 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3588 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6364 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6524 | chrome.exe | 140.82.121.4:443 | github.com | GITHUB | US | shared |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6524 | chrome.exe | 64.233.167.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6524 | chrome.exe | 185.199.110.133:443 | objects.githubusercontent.com | FASTLY | US | shared |
6524 | chrome.exe | 142.250.184.228:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| shared |
accounts.google.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
www.google.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Crypto Currency Mining Activity Detected | ET COINMINER CoinMiner Domain in DNS Lookup (pool .hashvault .pro) |
5164 | dialer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
5164 | dialer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
1 ETPRO signatures available at the full report