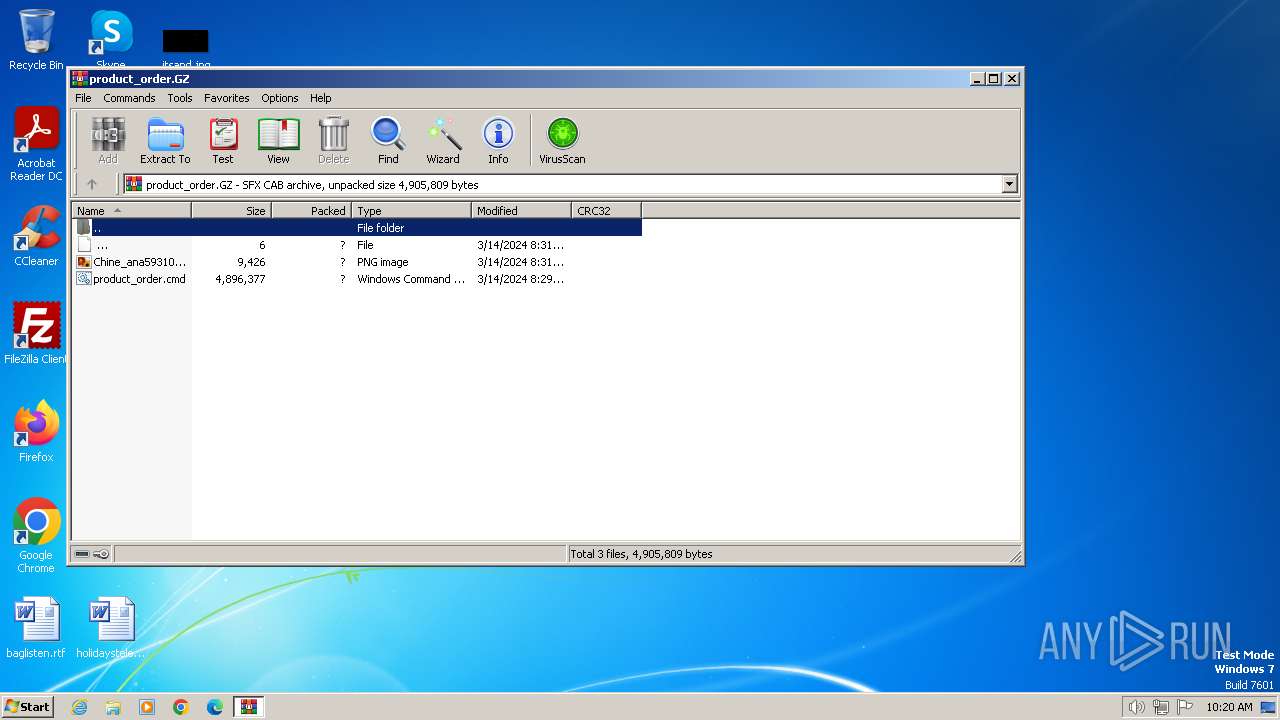
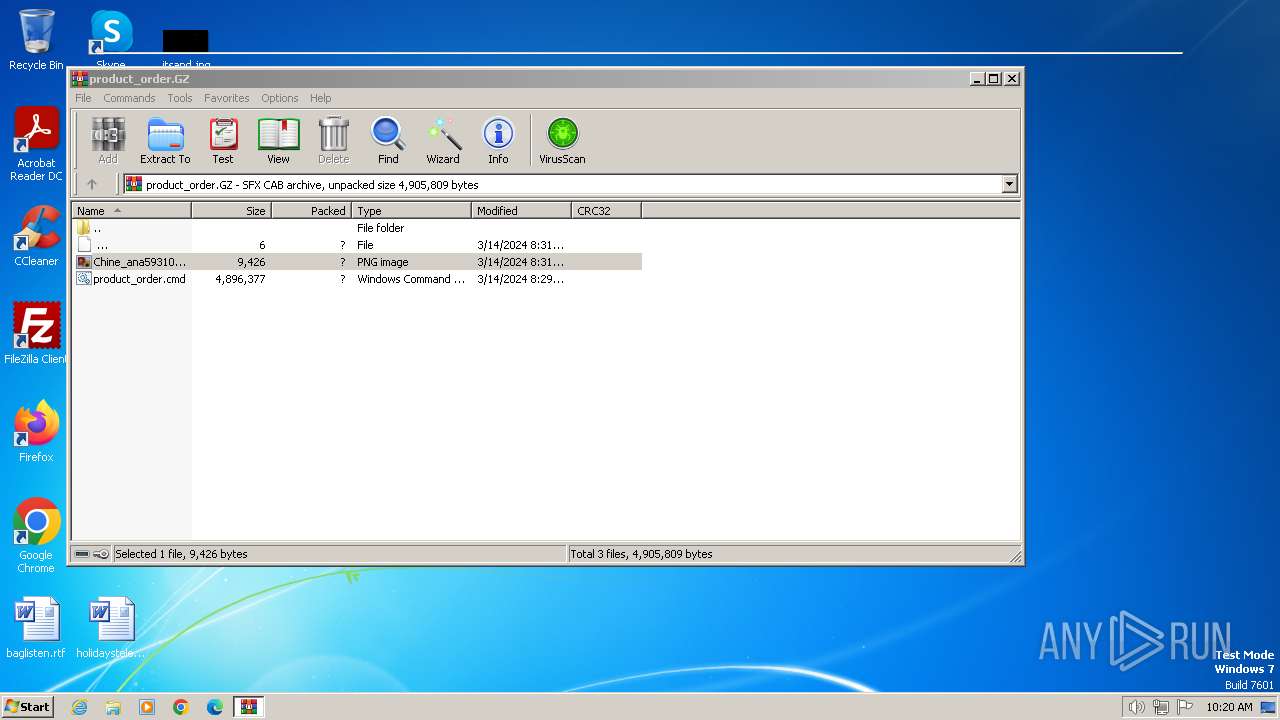
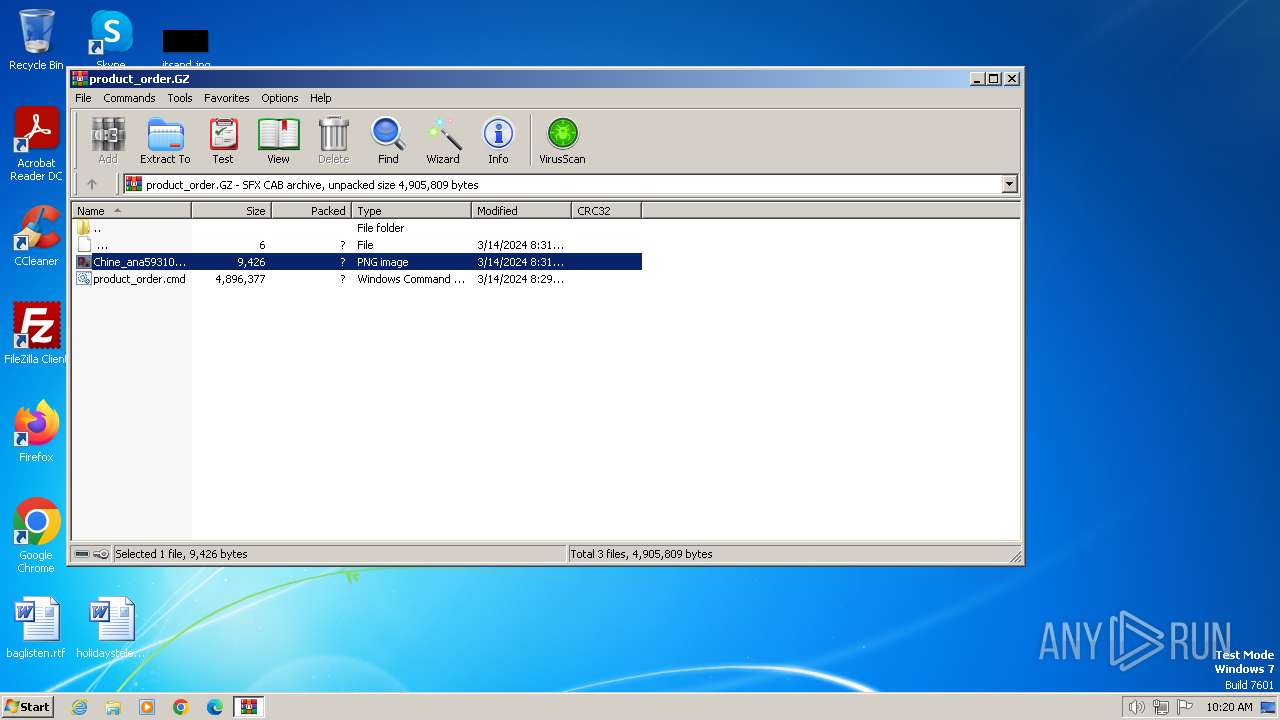
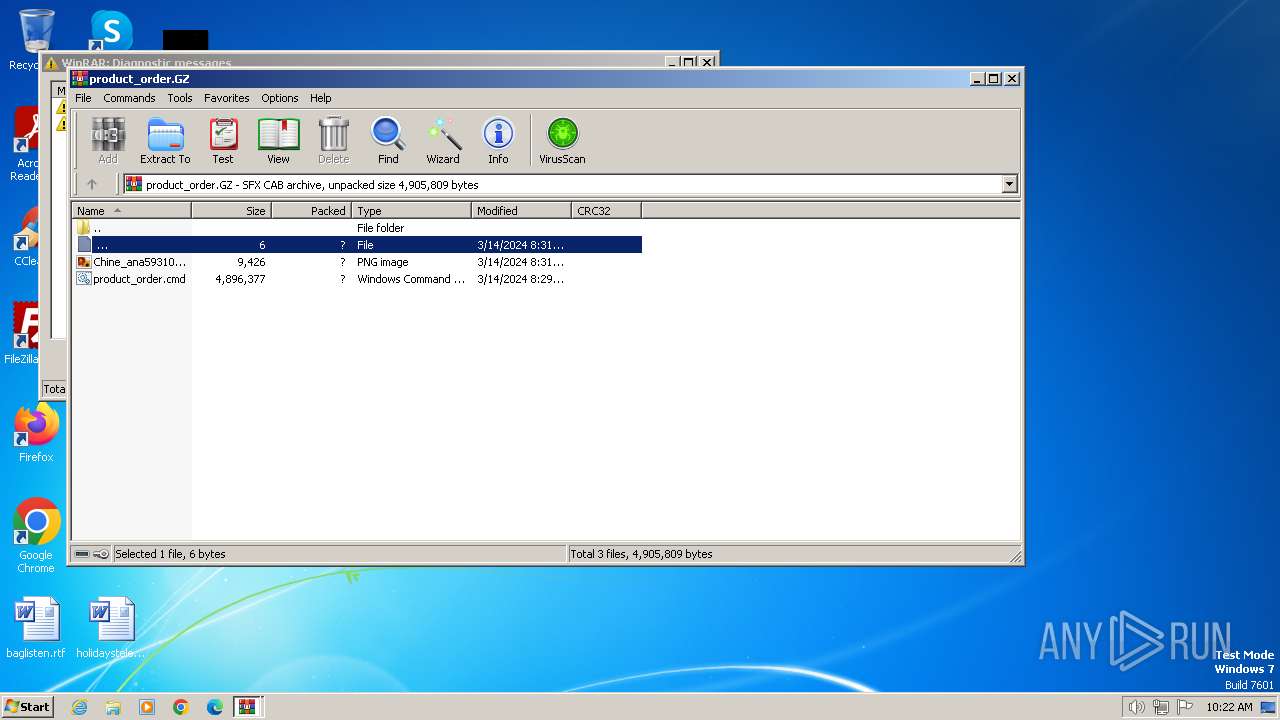
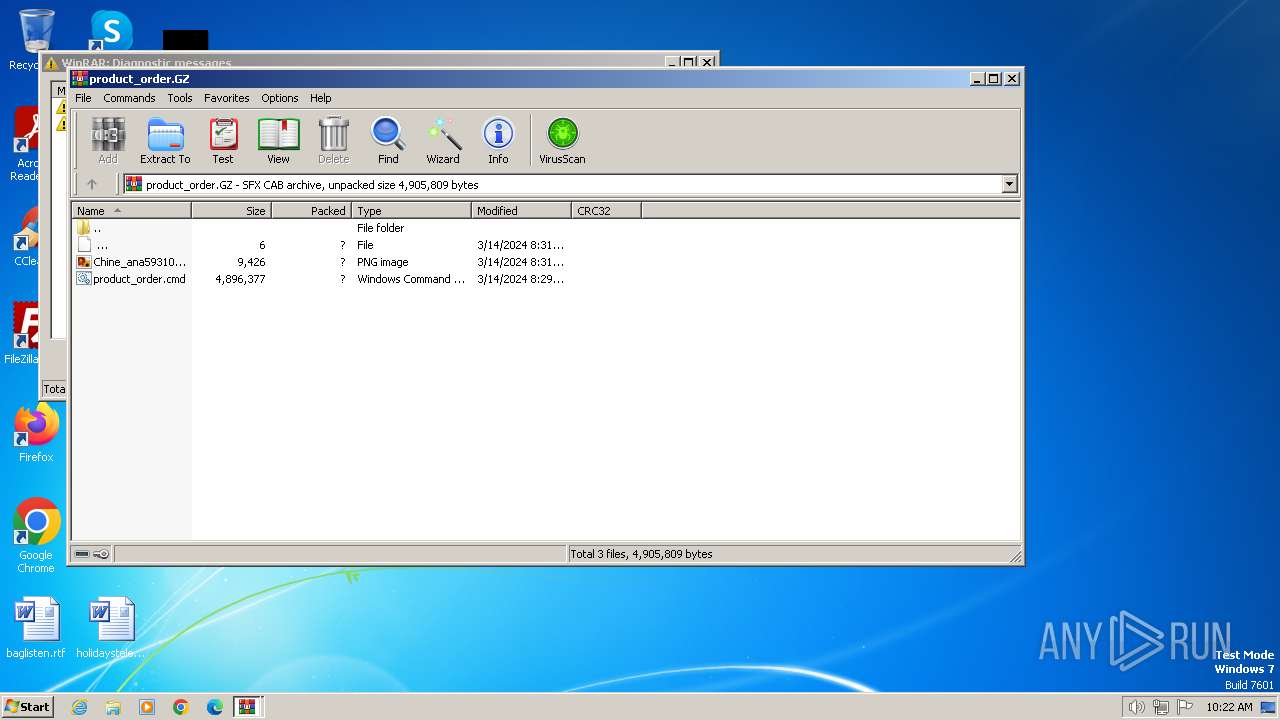
| File name: | product_order.GZ |
| Full analysis: | https://app.any.run/tasks/67935629-a74d-43c9-8fbf-0691bb5ccabc |
| Verdict: | Malicious activity |
| Threats: | DBatLoader is a loader malware used for distributing payloads of different types, including WarzoneRAT and Formbook. It is employed in multi-stage attacks that usually start with a phishing email carrying a malicious attachment. |
| Analysis date: | March 14, 2024, 10:20:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | 6D2CAC997AA18D5A4C8971BFF9FF19DB |
| SHA1: | 1CE6A59A99DD7AC0DFACBF71BA2C186D24A15B1F |
| SHA256: | 19EADE860A8296660BA58596AB821B084E58140FF2CF6A9BD13D534D98B41266 |
| SSDEEP: | 98304:rcjl36W2yd8tjbvgts4G9kQyoR3Jp4GpMFvE8Yj7vAfD8WX0Da+5uD7Bs2JUmyYv:ixt |
MALICIOUS
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 3848)
- xkn.exe (PID: 3936)
- alpha.exe (PID: 2120)
- alpha.exe (PID: 3940)
Starts PowerShell from an unusual location
- alpha.exe (PID: 2120)
Drops the executable file immediately after the start
- kn.exe (PID: 1496)
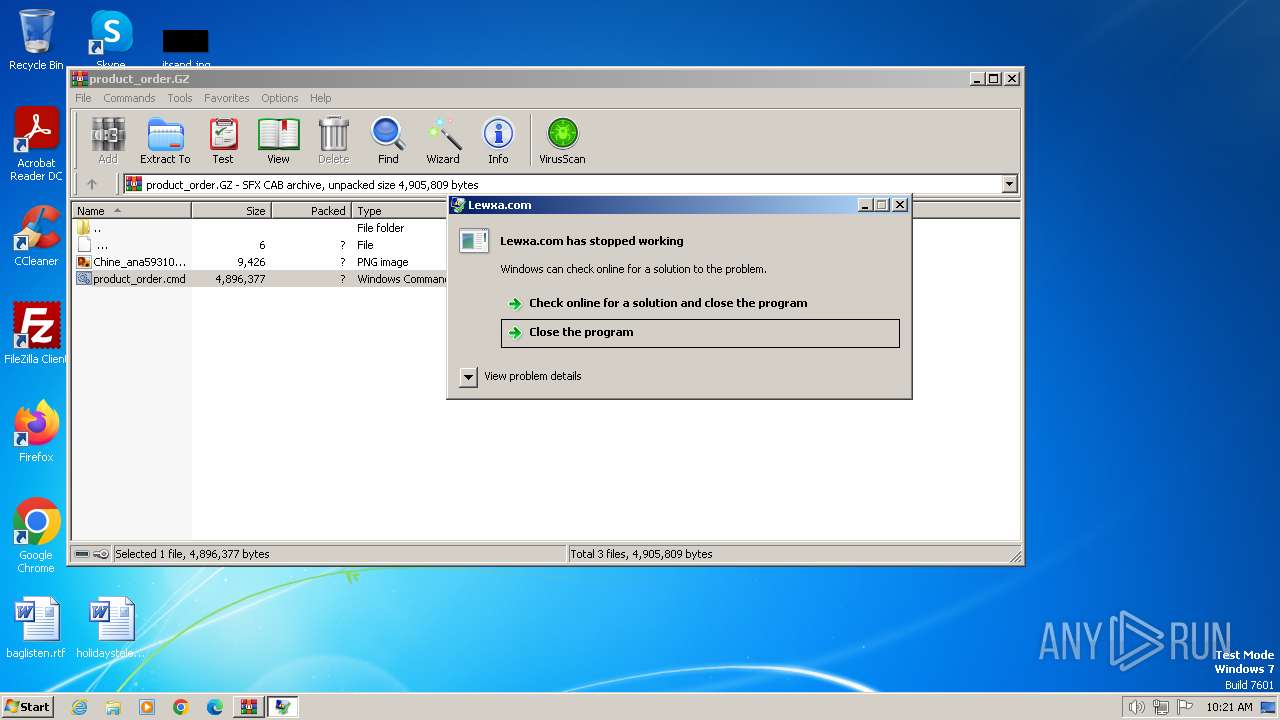
DBATLOADER has been detected (YARA)
- Lewxa.com (PID: 1740)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 3848)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 2160)
- cmd.exe (PID: 3848)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 3460)
- extrac32.exe (PID: 2332)
- alpha.exe (PID: 2444)
- extrac32.exe (PID: 2636)
- extrac32.exe (PID: 120)
- alpha.exe (PID: 2120)
- alpha.exe (PID: 4060)
- alpha.exe (PID: 3940)
- reg.exe (PID: 3392)
- xkn.exe (PID: 3936)
- kn.exe (PID: 1496)
- alpha.exe (PID: 1348)
- alpha.exe (PID: 2208)
- kn.exe (PID: 2672)
- alpha.exe (PID: 2688)
- alpha.exe (PID: 748)
- alpha.exe (PID: 1976)
- Lewxa.com (PID: 1740)
- alpha.exe (PID: 3684)
- alpha.exe (PID: 3068)
- alpha.exe (PID: 1352)
- cmd.exe (PID: 1336)
- alpha.exe (PID: 3508)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2160)
- xkn.exe (PID: 3936)
Executable content was dropped or overwritten
- extrac32.exe (PID: 2332)
- extrac32.exe (PID: 120)
- extrac32.exe (PID: 2636)
- kn.exe (PID: 1496)
Process drops legitimate windows executable
- extrac32.exe (PID: 2332)
- extrac32.exe (PID: 2636)
Executing commands from ".cmd" file
- WinRAR.exe (PID: 2160)
Starts itself from another location
- cmd.exe (PID: 3848)
Starts a Microsoft application from unusual location
- alpha.exe (PID: 2444)
- alpha.exe (PID: 2120)
- alpha.exe (PID: 4060)
- alpha.exe (PID: 3940)
- xkn.exe (PID: 3936)
- kn.exe (PID: 2672)
- alpha.exe (PID: 1348)
- kn.exe (PID: 1496)
- alpha.exe (PID: 2208)
- alpha.exe (PID: 3684)
- alpha.exe (PID: 1976)
- alpha.exe (PID: 748)
- alpha.exe (PID: 2688)
- alpha.exe (PID: 3508)
- alpha.exe (PID: 1352)
- alpha.exe (PID: 3068)
Process drops legitimate windows executable (CertUtil.exe)
- extrac32.exe (PID: 120)
Checks Windows Trust Settings
- xkn.exe (PID: 3936)
Uses REG/REGEDIT.EXE to modify registry
- alpha.exe (PID: 3940)
Reads the Internet Settings
- xkn.exe (PID: 3936)
- Lewxa.com (PID: 1740)
Starts application with an unusual extension
- cmd.exe (PID: 3848)
Runs PING.EXE to delay simulation
- alpha.exe (PID: 2688)
Uses TASKKILL.EXE to kill process
- alpha.exe (PID: 3068)
- alpha.exe (PID: 1352)
INFO
Drops the executable file immediately after the start
- extrac32.exe (PID: 2332)
- extrac32.exe (PID: 120)
- extrac32.exe (PID: 2636)
Checks supported languages
- alpha.exe (PID: 4060)
- alpha.exe (PID: 2120)
- alpha.exe (PID: 2444)
- xkn.exe (PID: 3936)
- alpha.exe (PID: 1348)
- alpha.exe (PID: 3940)
- alpha.exe (PID: 2208)
- kn.exe (PID: 2672)
- alpha.exe (PID: 3684)
- Lewxa.com (PID: 1740)
- alpha.exe (PID: 1976)
- alpha.exe (PID: 748)
- kn.exe (PID: 1496)
- alpha.exe (PID: 2688)
- alpha.exe (PID: 3508)
- alpha.exe (PID: 3068)
- alpha.exe (PID: 1352)
- wmpnscfg.exe (PID: 492)
Process checks Powershell version
- xkn.exe (PID: 3936)
Reads the machine GUID from the registry
- xkn.exe (PID: 3936)
Create files in a temporary directory
- xkn.exe (PID: 3936)
Reads the computer name
- xkn.exe (PID: 3936)
- kn.exe (PID: 1496)
- kn.exe (PID: 2672)
- Lewxa.com (PID: 1740)
- wmpnscfg.exe (PID: 492)
Checks proxy server information
- Lewxa.com (PID: 1740)
Manual execution by a user
- wmpnscfg.exe (PID: 492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DBatLoader
(PID) Process(1740) Lewxa.com
C2 (1)https://onedrive.live.com/download?resid=653A5056738F1A02%21202&authkey=!AEicXFUKIn_6Dzw
Total processes
69
Monitored processes
30
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | extrac32.exe /C /Y C:\\Windows\\System32\\certutil.exe C:\\Users\\Public\\kn.exe | C:\Windows\System32\extrac32.exe | alpha.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® CAB File Extract Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 492 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | C:\\Users\\Public\\alpha /c del "C:\Users\Public\xkn.exe" / A / F / Q / S | C:\Users\Public\alpha.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1336 | cmd /c del "C:\Users\Public\alpha.exe" / A / F / Q / S | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1348 | C:\\Users\\Public\\alpha /c C:\\Users\\Public\\kn -decodehex -F "C:\\Users\\Public\\Lewxa.txt" "C:\\Users\\Public\\Libraries\\Lewxa.com" 12 | C:\Users\Public\alpha.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1352 | C:\\Users\\Public\\alpha /c taskkill /F /IM SystemSettingsAdminFlows.exe | C:\Users\Public\alpha.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1496 | C:\\Users\\Public\\kn -decodehex -F "C:\\Users\\Public\\Lewxa.txt" "C:\\Users\\Public\\Libraries\\Lewxa.com" 12 | C:\Users\Public\kn.exe | alpha.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
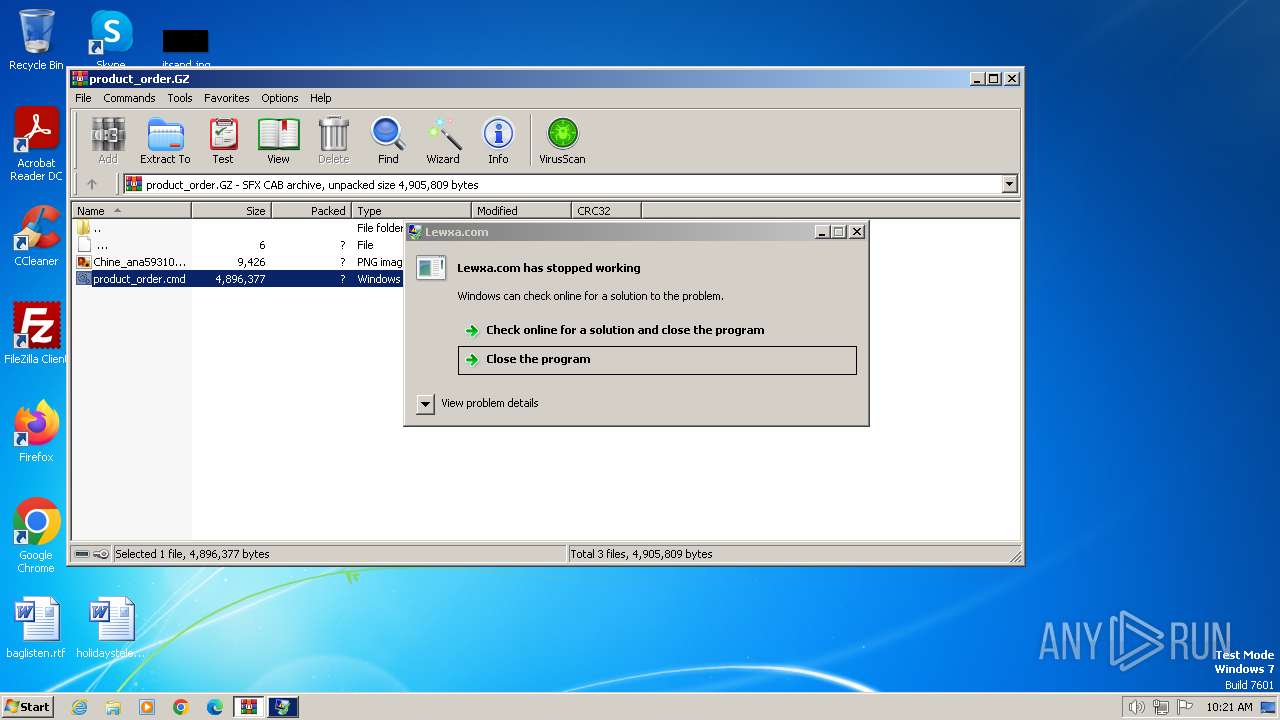
| 1740 | C:\\Users\\Public\\Libraries\\Lewxa.com | C:\Users\Public\Libraries\Lewxa.com | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 250477278 Modules
DBatLoader(PID) Process(1740) Lewxa.com C2 (1)https://onedrive.live.com/download?resid=653A5056738F1A02%21202&authkey=!AEicXFUKIn_6Dzw | |||||||||||||||
| 1976 | C:\\Users\\Public\\alpha /c del "C:\Users\Public\Lewxa.txt" / A / F / Q / S | C:\Users\Public\alpha.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2000 | taskkill /F /IM SystemSettings.exe | C:\Windows\System32\taskkill.exe | — | alpha.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 116
Read events
8 073
Write events
43
Delete events
0
Modification events
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\product_order.GZ | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2160.13423\product_order.cmd | — | |
MD5:— | SHA256:— | |||
| 120 | extrac32.exe | C:\Users\Public\kn.exe | executable | |
MD5:0D52559AEF4AA5EAC82F530617032283 | SHA256:48850FB7229D99E48C3A749556684E962587058D612C659C58F8B8DB2D00ABEE | |||
| 2332 | extrac32.exe | C:\Users\Public\alpha.exe | executable | |
MD5:AD7B9C14083B52BC532FBA5948342B98 | SHA256:17F746D82695FA9B35493B41859D39D786D32B23A9D2E00F4011DEC7A02402AE | |||
| 2672 | kn.exe | C:\Users\Public\Lewxa.txt | text | |
MD5:DEF1BF0C1FDC6A08AE0191027CFA5A45 | SHA256:EF145335FD5948A4C1D2769E6CE2ACBD38F609FB13A8EBFAA0F97A5E8F7CA54B | |||
| 3936 | xkn.exe | C:\Users\admin\AppData\Local\Temp\gzamharn.pmm.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3936 | xkn.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 1496 | kn.exe | C:\Users\Public\Libraries\Lewxa.com | executable | |
MD5:6378E4D04259044C5BC868A3EAEA4622 | SHA256:1926A26327131BA4ABECAD0916699614626FAC7B494AB35B2FC7D562E2B2FE1E | |||
| 2160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2160.12926\Chine_ana593106D403900193D225174FF31157017FF476800loodatke.PNG | image | |
MD5:DC156637AEBF04336700A9BC71C78AAD | SHA256:E739A88AC8FB4FEFA998F8DBF4402A8D7A22EB079EDD05BEE412C4D4C99014EB | |||
| 2636 | extrac32.exe | C:\Users\Public\xkn.exe | executable | |
MD5:EB32C070E658937AA9FA9F3AE629B2B8 | SHA256:70BA57FB0BF2F34B86426D21559F5F6D05C1268193904DE8E959D7B06CE964CE | |||
| 3936 | xkn.exe | C:\Users\admin\AppData\Local\Temp\0phiyuea.lb0.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
5
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1740 | Lewxa.com | 13.107.137.11:443 | onedrive.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1740 | Lewxa.com | 13.107.139.11:443 | onedrive.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
onedrive.live.com |
| shared |
dns.msftncsi.com |
| shared |