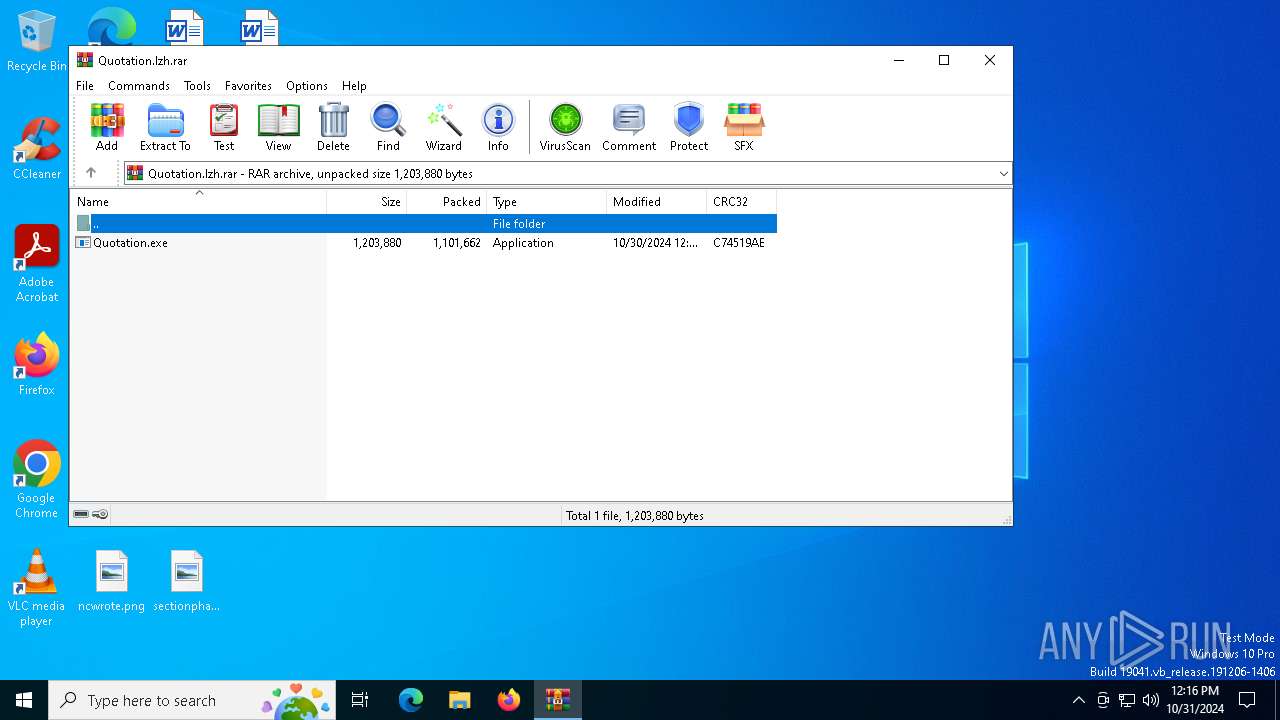
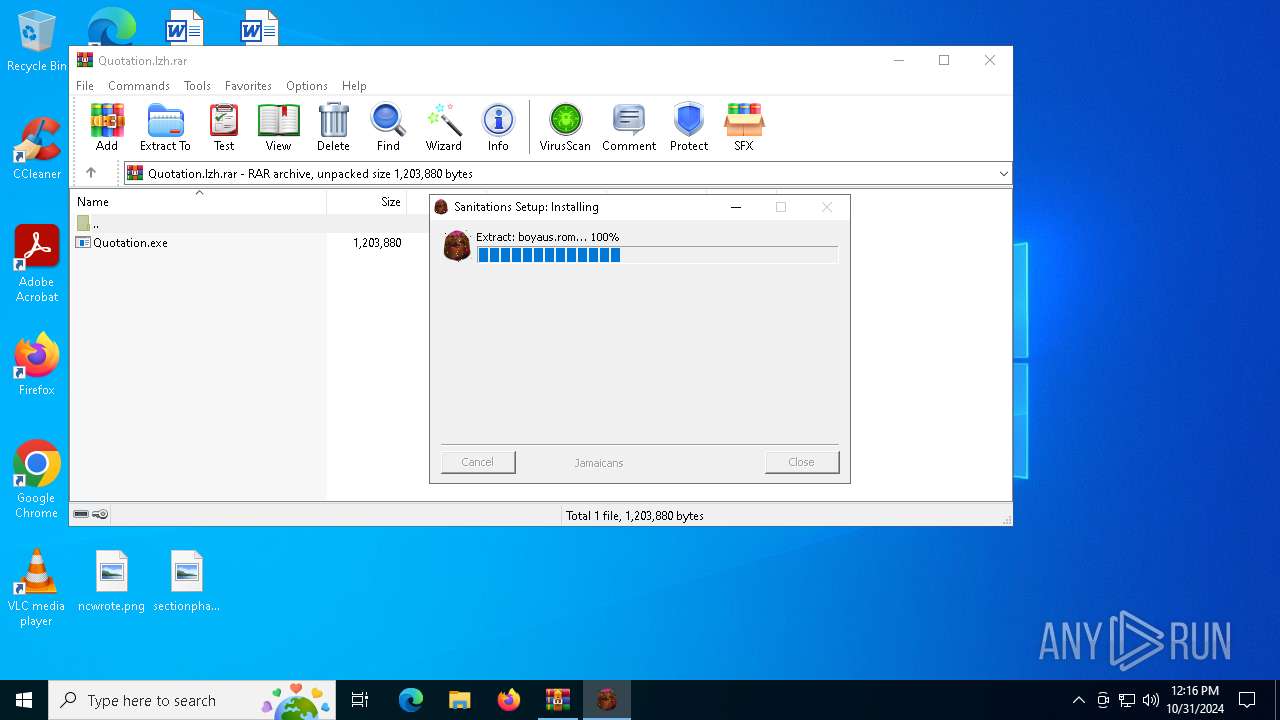
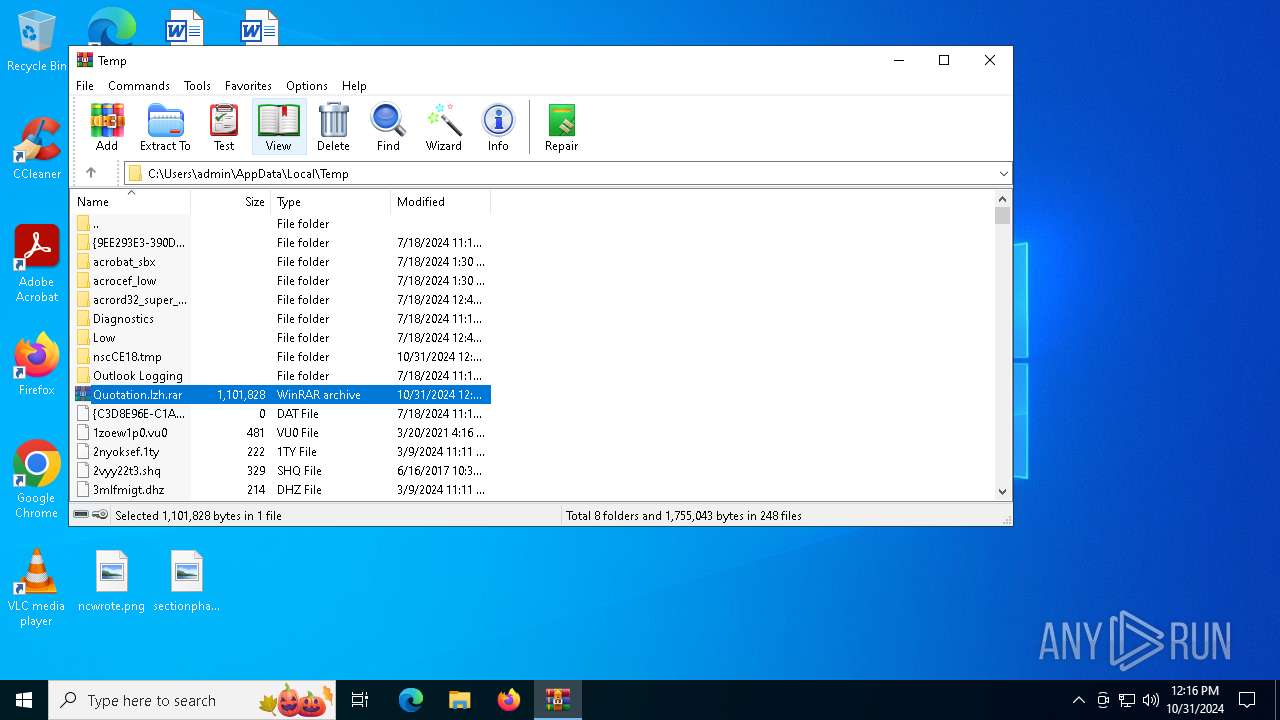
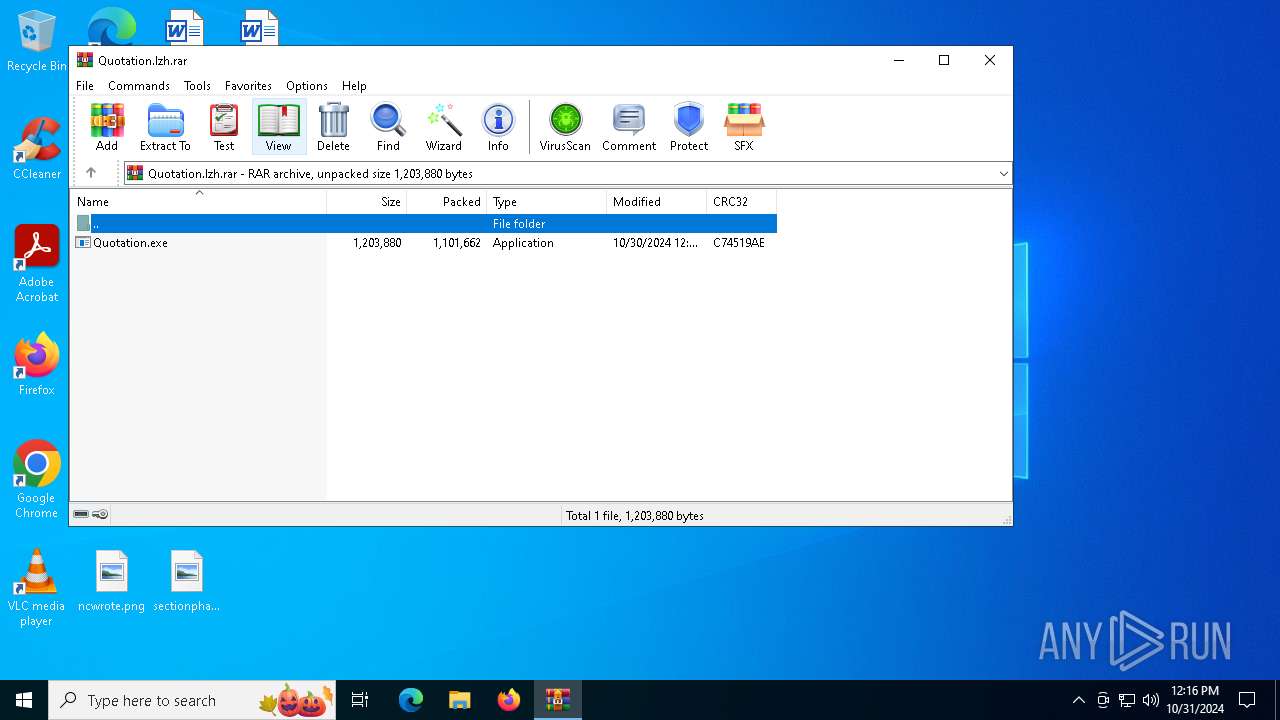
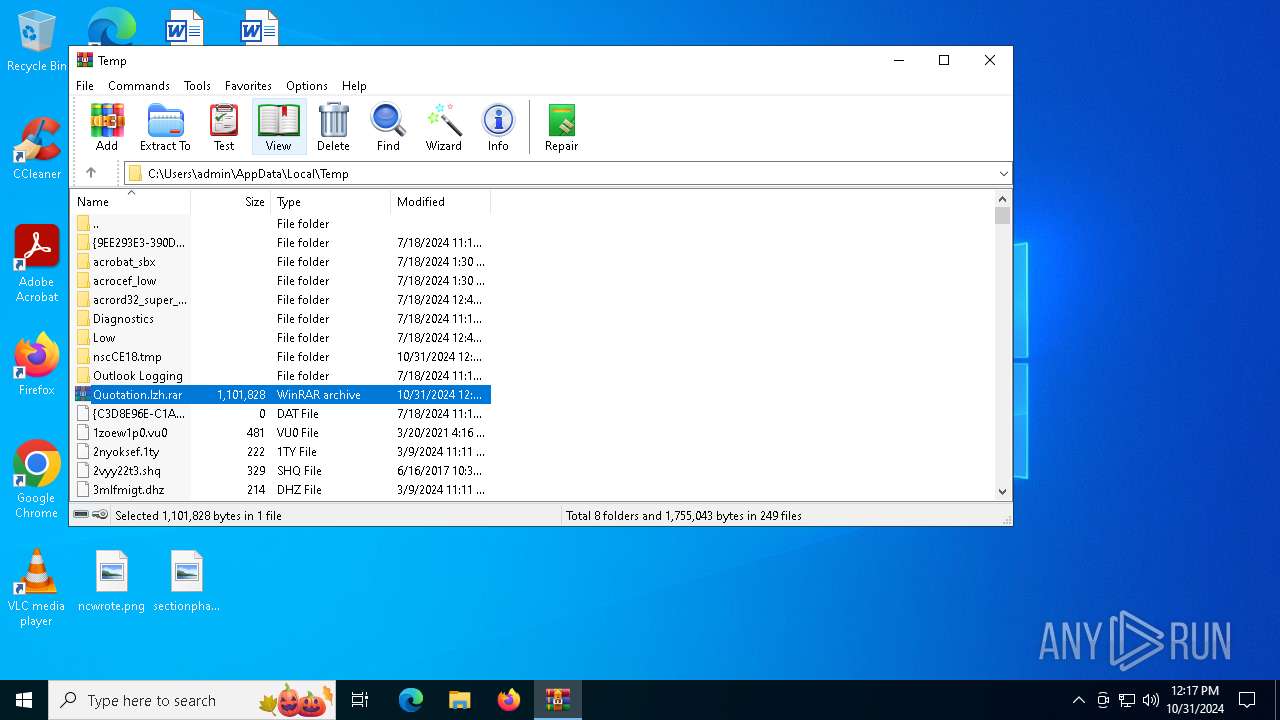
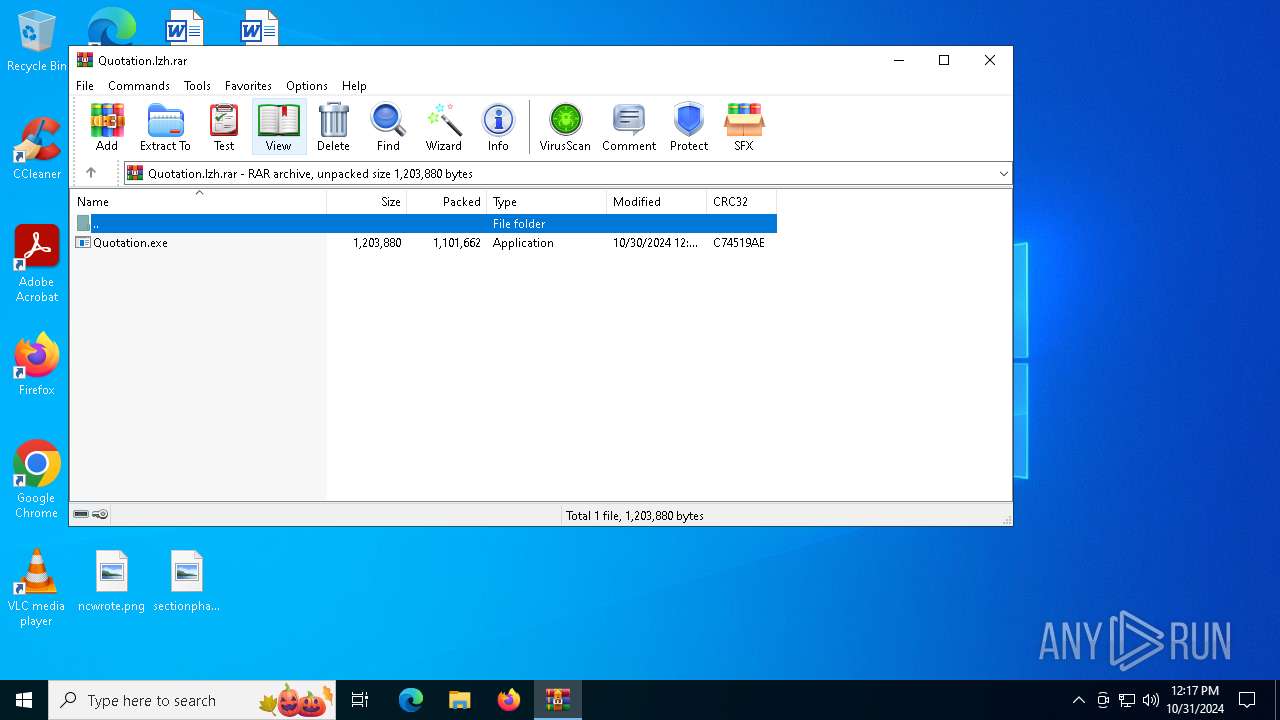
| File name: | Quotation.lzh |
| Full analysis: | https://app.any.run/tasks/da72a43a-3920-48b1-bb78-48d9e29c4471 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | October 31, 2024, 12:16:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 0738B8E8CC05B821858062D0349D3644 |
| SHA1: | EB94F9849783C05DF3C515917056A23FCCA9F5FA |
| SHA256: | 19B8F3E726976E0285670A8CB0A227D173A41DAD108DF4BB171D8A8D9A0F63B8 |
| SSDEEP: | 49152:rBRXqiOEbEzJhvKo1MtPu6JBqozoxuQWhXPNkvmg/g/xhUY5H8FeeihrV:fqiOEkFytPu6JBhoxz40EjPV |
MALICIOUS
FORMBOOK has been detected (SURICATA)
- WinRAR.exe (PID: 5220)
Connects to the CnC server
- WinRAR.exe (PID: 5220)
Generic archive extractor
- WinRAR.exe (PID: 5220)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- WinRAR.exe (PID: 5220)
Application launched itself
- Quotation.exe (PID: 6680)
Executable content was dropped or overwritten
- Quotation.exe (PID: 6680)
Malware-specific behavior (creating "System.dll" in Temp)
- Quotation.exe (PID: 6680)
Suspicious use of NETSH.EXE
- WinRAR.exe (PID: 5220)
INFO
Manual execution by a user
- Quotation.exe (PID: 6680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1101662 |
| UncompressedSize: | 1203880 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Quotation.exe |
Total processes
134
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 824 | "C:\Users\admin\Desktop\Quotation.exe" | C:\Users\admin\Desktop\Quotation.exe | Quotation.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: screamer slounge Exit code: 0 Modules
| |||||||||||||||
| 5220 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Quotation.lzh.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6332 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | netsh.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 6396 | "C:\Windows\SysWOW64\netsh.exe" | C:\Windows\SysWOW64\netsh.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6680 | "C:\Users\admin\Desktop\Quotation.exe" | C:\Users\admin\Desktop\Quotation.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: screamer slounge Exit code: 0 Modules
| |||||||||||||||
Total events
15 238
Read events
14 903
Write events
335
Delete events
0
Modification events
| (PID) Process: | (5220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Quotation.lzh.rar | |||
| (PID) Process: | (5220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6680) Quotation.exe | Key: | HKEY_CURRENT_USER\Zoofulvin68\Uninstall\brevbrere |
| Operation: | write | Name: | aircondition |
Value: 1 | |||
| (PID) Process: | (5220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (5220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
1
Suspicious files
18
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6680 | Quotation.exe | C:\Users\admin\overlays\besvangredes\Proprietrer.bet | binary | |
MD5:0B62328C4966F6B879B3C13B7FBD9C0D | SHA256:645C325F62AF720972466322B09A7E396E46D8E640B138D582374B68D763A3A7 | |||
| 6680 | Quotation.exe | C:\Users\admin\Music\antithetic.ini | text | |
MD5:58AC0B5E1D49D0EE1AED2FE13FAE6C7A | SHA256:624F49944CB84ED51FECABCD549AE3B47152F9A20C4A95E93C8B007AEFE9FEAB | |||
| 824 | Quotation.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:AB8FD3A63D3CB531D4D7575CE12F196E | SHA256:5FEEE7CF94F535FCD8E25C4832148674434A1EE2B0F73A2D227452A52C4C2762 | |||
| 6680 | Quotation.exe | C:\Users\admin\overlays\besvangredes\Billigudgavens.Cus | binary | |
MD5:C8294E0EC7F0506E2CEF87F454073DC2 | SHA256:AC38CD1CF8C08207F418E1CD4CD36B3F7CEEAFFF307B1BC78DA87616E37DF5A0 | |||
| 6680 | Quotation.exe | C:\Users\admin\overlays\besvangredes\Trikstanks.pra | binary | |
MD5:49BE0E06F2E4F0CCFFB46426EE262642 | SHA256:A55DAC07FB586D4B64F0DDF812087A2EEEC6F5286D9BC73AD648ED3220ABDD3A | |||
| 824 | Quotation.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:E935BC5762068CAF3E24A2683B1B8A88 | SHA256:A8ACCFCFEB51BD73DF23B91F4D89FF1A9EB7438EF5B12E8AFDA1A6FF1769E89D | |||
| 824 | Quotation.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:A932F636E9413F20CBF2D459B95B6FE7 | SHA256:E90747952CCE860B18015C40005FECD320A7871A93E4B70F3B2F61E93C7F589E | |||
| 824 | Quotation.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B3513D73A177A2707D910183759B389B_CD08734C3F770C014F2620E6CA4CE9C7 | binary | |
MD5:FF53DF46CA9A9A54467BE94BF541FCF0 | SHA256:0233D19BCB2CE770BFCFEB2E26DDFA67375E78A65E810172B048B0E5B2391826 | |||
| 824 | Quotation.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4FA45AE1010E09657982D8D28B3BD38E_CC847C1C687BCB4C6B5074DF051D733B | binary | |
MD5:A2CDAF05BECCFA59180EB4D567DEDBAD | SHA256:9B0D7182B9CB5620478A47C3C6BC7FD88504F11A76E55D3C6E70421E4A4E2E0D | |||
| 824 | Quotation.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:53373FC482DBE858CE47866583CB9D74 | SHA256:A76DBB249261213C36503EDED4F90A9CC64EA617584A8611FFD697BC52DF0027 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
57
DNS requests
30
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6936 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1552 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3676 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
824 | Quotation.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
824 | Quotation.exe | GET | 200 | 142.250.184.195:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
824 | Quotation.exe | GET | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACECt1gF5RMj4mChEciVJIkog%3D | unknown | — | — | whitelisted |
824 | Quotation.exe | GET | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQDzySkSNBgXtBKLijHUmMxR | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 104.126.37.171:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1752 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.32.238.107:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
816 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5220 | WinRAR.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) M5 |
5220 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
5220 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
5220 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
5220 | WinRAR.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) M5 |
2 ETPRO signatures available at the full report