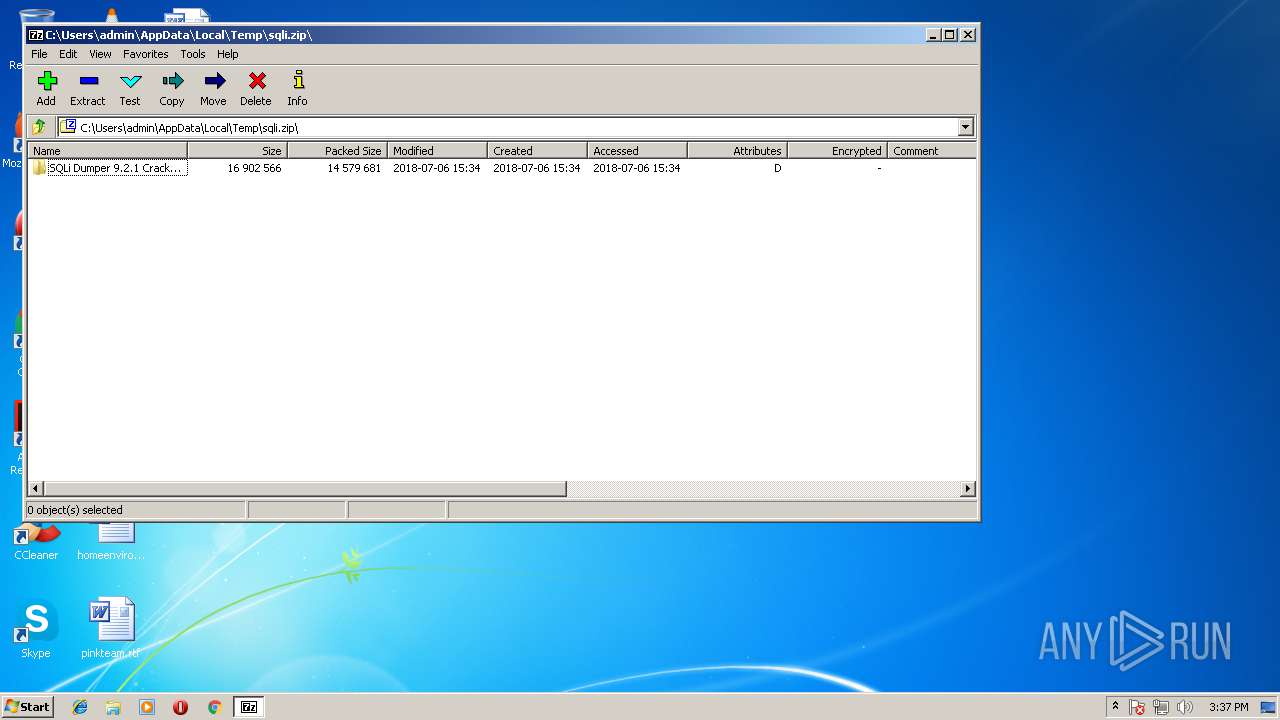
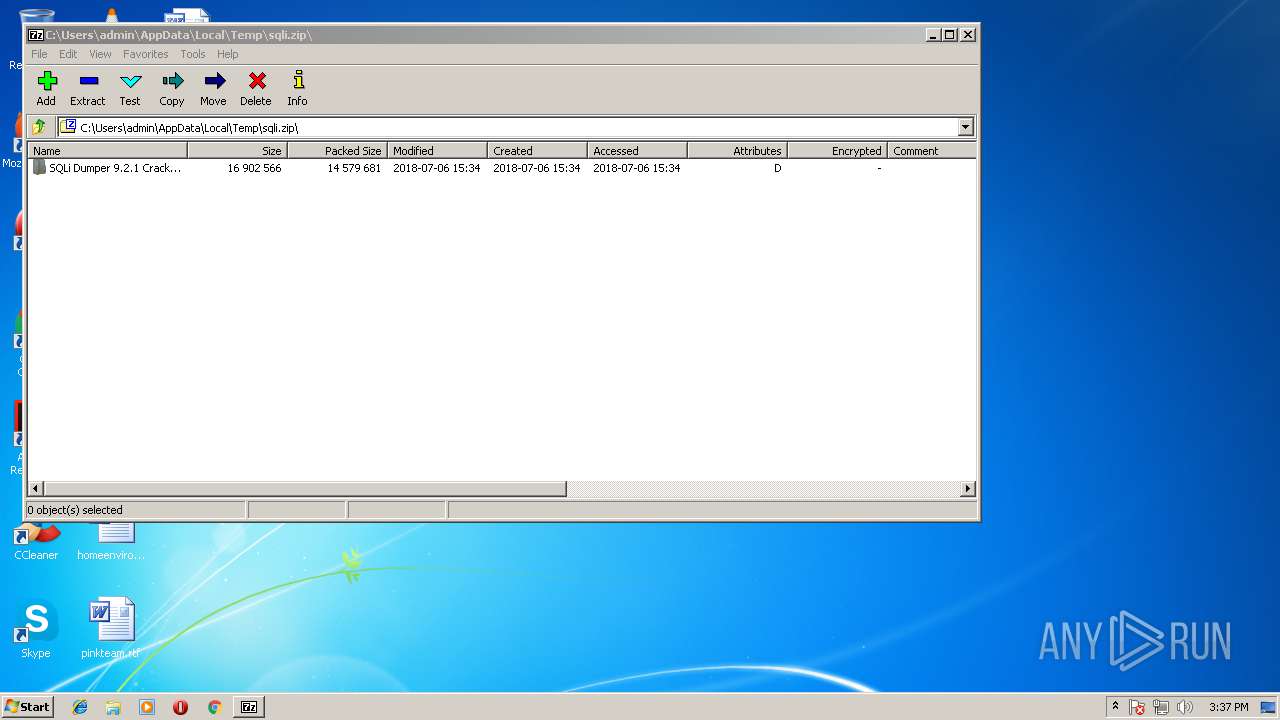
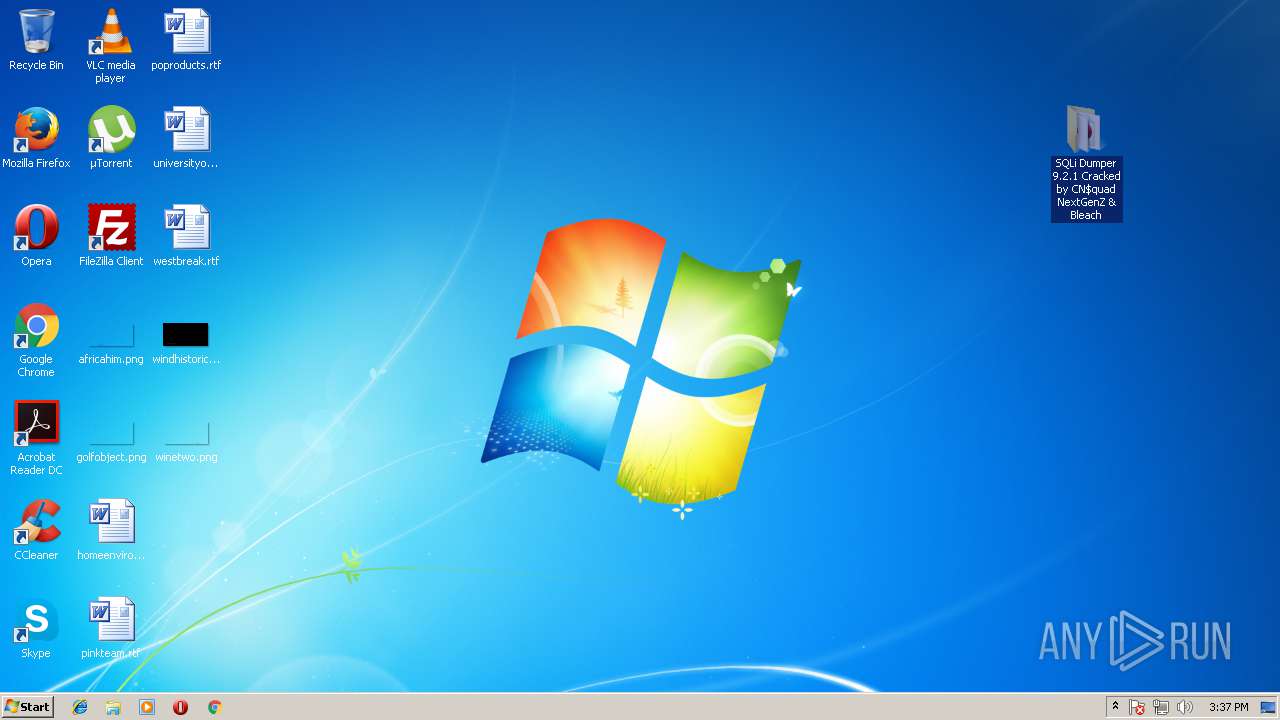
| File name: | sqli.zip |
| Full analysis: | https://app.any.run/tasks/bac5cc50-39da-4f50-94ba-9f1a91e1ba3a |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | July 06, 2018, 14:36:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | F91C3074373F08DBBB99650311E93D97 |
| SHA1: | FF68B7826256627FD09B50E72D4B03BFC0C0B792 |
| SHA256: | 19B8500EFD85684B03CCCEC9F55A80EA9D42D33918A119860488181FF59831C4 |
| SSDEEP: | 393216:JBt1YzYHC8WhMMhenR2obMIjJ+Fh1DuRu7z8oDC:/t1GYi8CMMheuMJ+FhQRu7z8oO |
MALICIOUS
Application was dropped or rewritten from another process
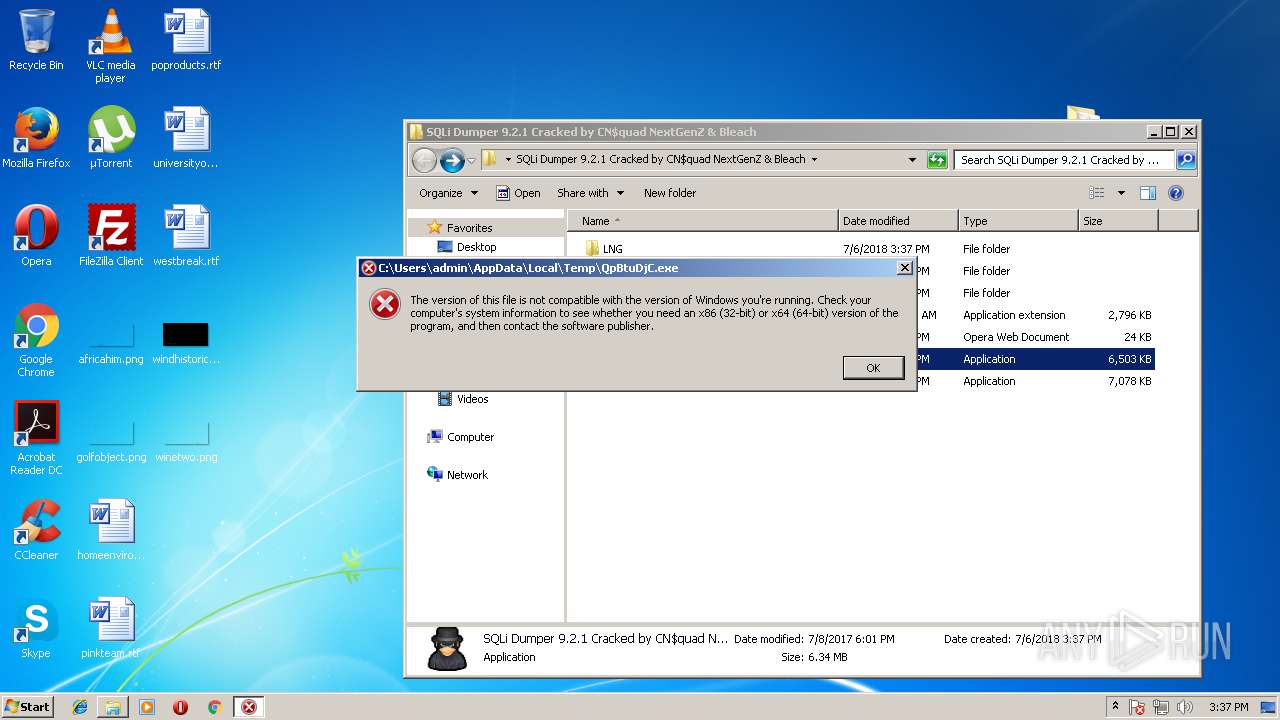
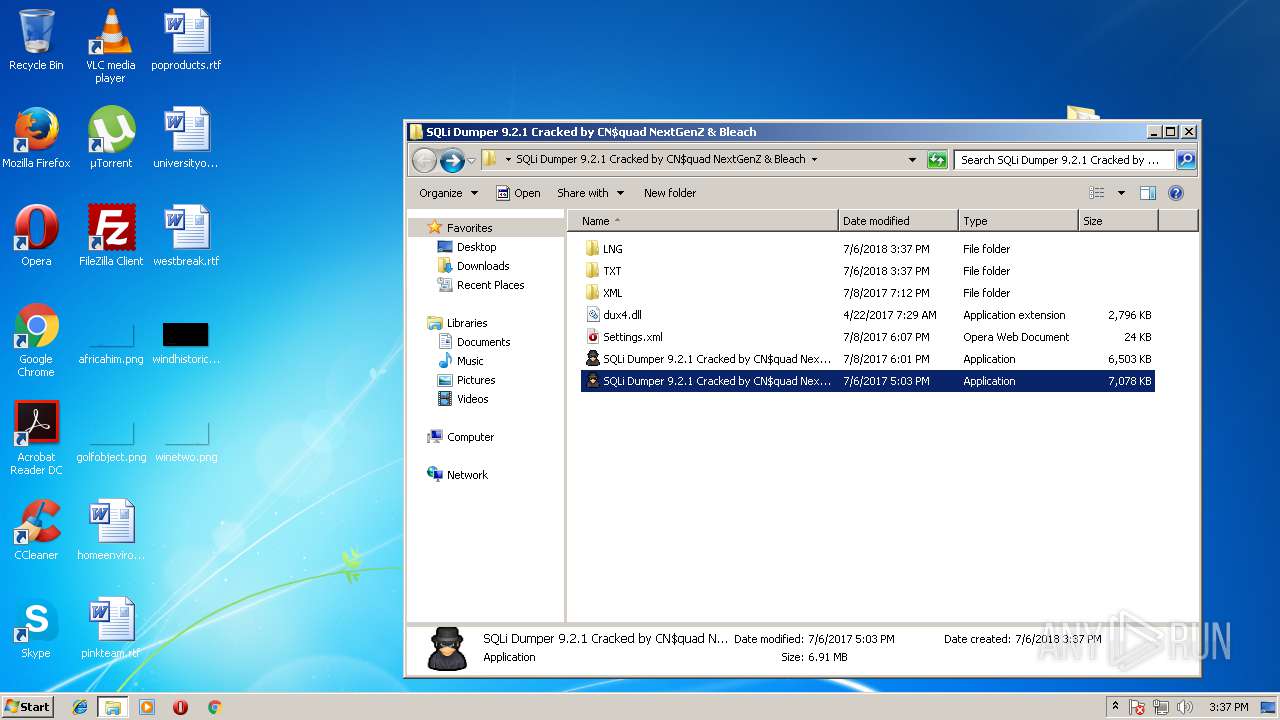
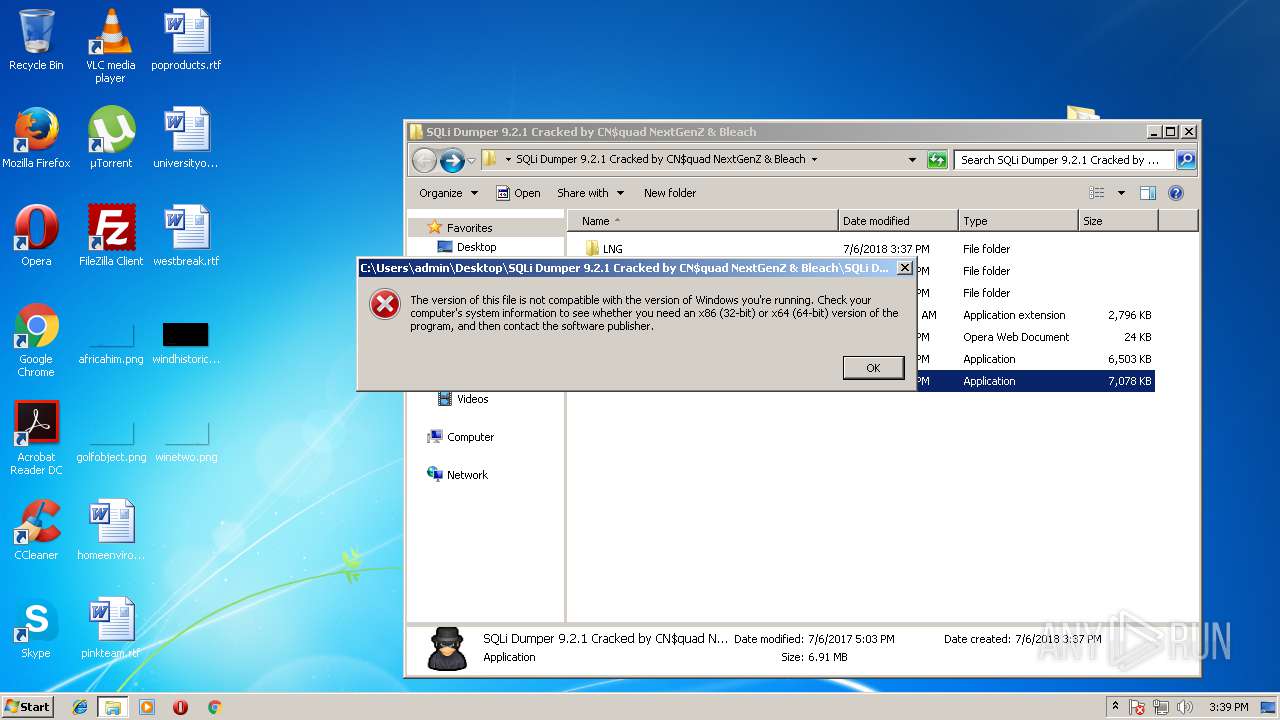
- SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach.exe (PID: 2836)
- VradmnZO.exe (PID: 3700)
Looks like application has launched a miner
- installutil.exe (PID: 352)
SUSPICIOUS
Executable content was dropped or overwritten
- SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach.exe (PID: 2836)
Executes scripts
- installutil.exe (PID: 352)
Connects to unusual port
- vbc.exe (PID: 976)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:07:06 16:34:21 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach/ |
Total processes
40
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 352 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\installutil.exe" /logtoconsole=false /logfile= /u "C:\Users\admin\AppData\Local\Temp\VradmnZO.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\installutil.exe | — | VradmnZO.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 976 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" --max-cpu-usage=25 -o xmr.pool.minergate.com:45560 -u ownyaga@gmail.com -p x | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | installutil.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
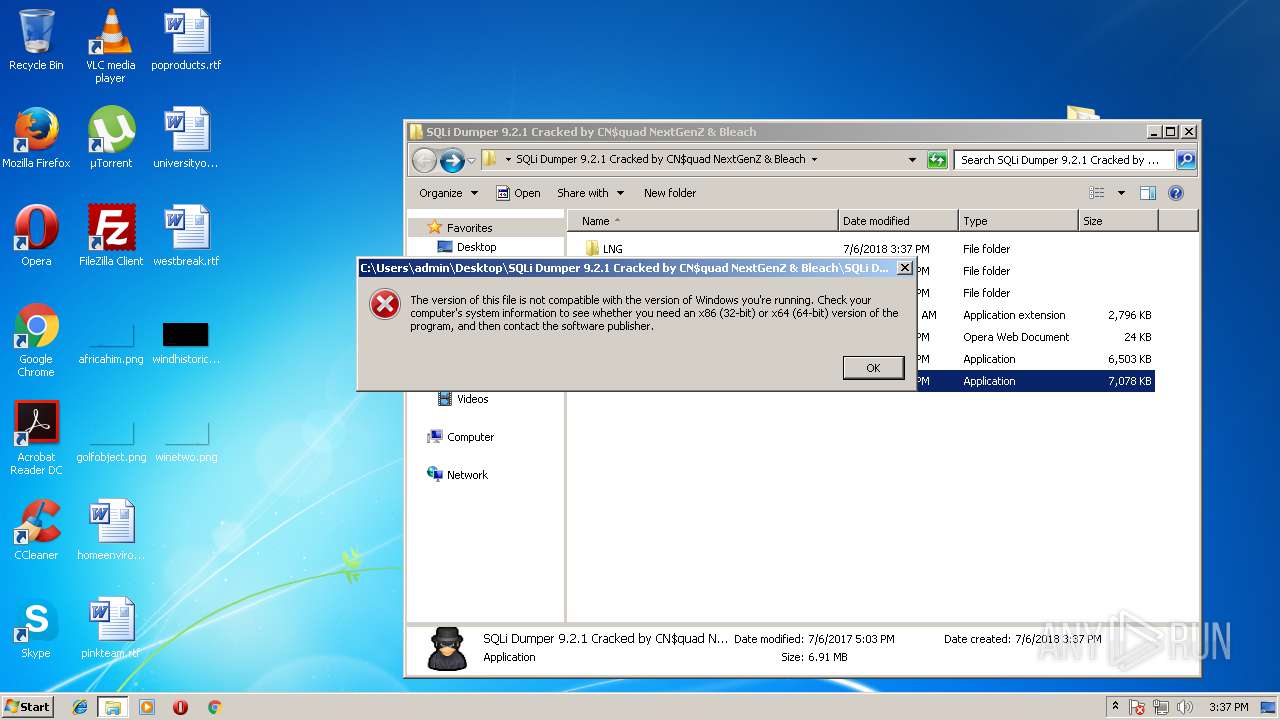
| 2836 | "C:\Users\admin\Desktop\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach.exe" | C:\Users\admin\Desktop\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2856 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\sqli.zip" | C:\Program Files\7-Zip\7zFM.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 3700 | "C:\Users\admin\AppData\Local\Temp\VradmnZO.exe" | C:\Users\admin\AppData\Local\Temp\VradmnZO.exe | — | SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
446
Read events
429
Write events
17
Delete events
0
Modification events
| (PID) Process: | (2856) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderShortcuts |
Value: | |||
| (PID) Process: | (2856) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00730071006C0069002E007A00690070005C000000 | |||
| (PID) Process: | (2856) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath0 |
Value: C:\Users\admin\AppData\Local\Temp\ | |||
| (PID) Process: | (2856) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc0 |
Value: 0 | |||
| (PID) Process: | (2856) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath1 |
Value: | |||
| (PID) Process: | (2856) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc1 |
Value: 0 | |||
| (PID) Process: | (2856) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | ListMode |
Value: 771 | |||
| (PID) Process: | (2856) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Position |
Value: 1600000016000000D60300000B02000000000000 | |||
| (PID) Process: | (2856) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Panels |
Value: 0100000000000000DA010000 | |||
| (PID) Process: | (2836) SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
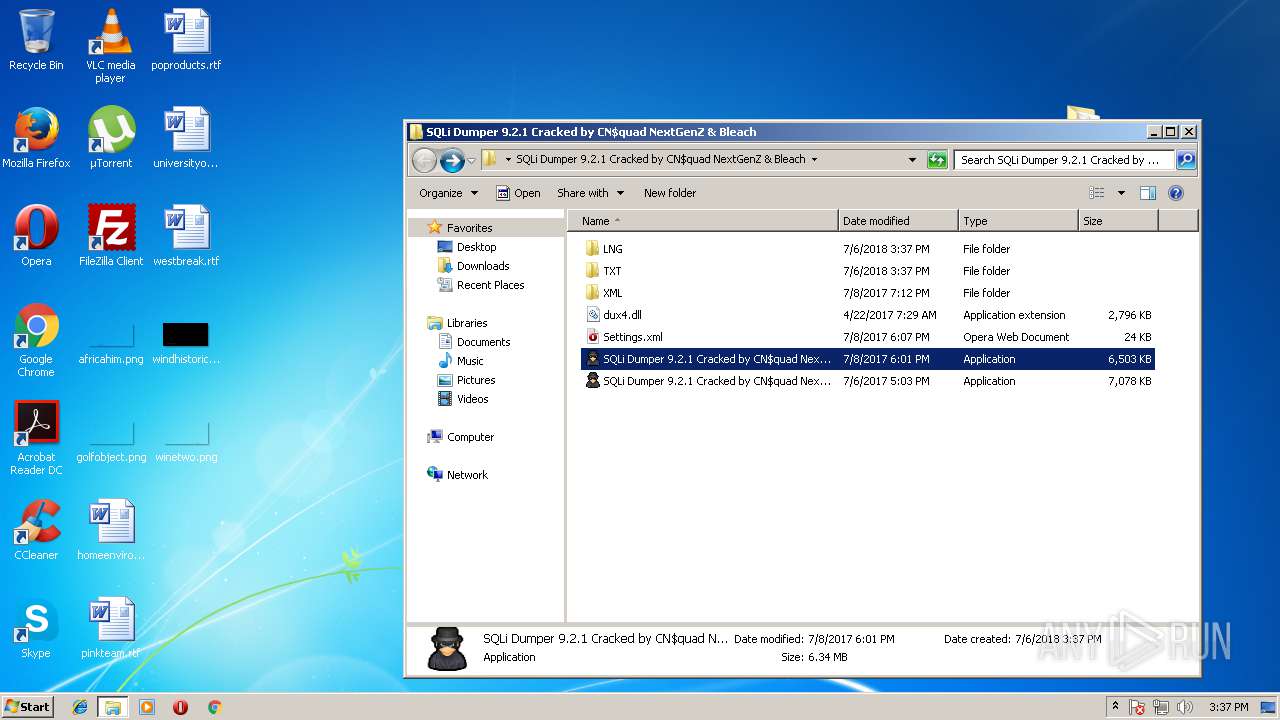
| 2856 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE82BC37EA\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach\dux4.dll | — | |
MD5:— | SHA256:— | |||
| 2856 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE82BC37EA\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach\LNG\English.xml | — | |
MD5:— | SHA256:— | |||
| 2856 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE82BC37EA\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach\LNG\Russian.xml | — | |
MD5:— | SHA256:— | |||
| 2856 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE82BC37EA\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach\Settings.xml | — | |
MD5:— | SHA256:— | |||
| 2856 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE82BC37EA\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach.exe | — | |
MD5:— | SHA256:— | |||
| 2856 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE82BC37EA\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach_afterregistration.exe | — | |
MD5:— | SHA256:— | |||
| 2856 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE82BC37EA\SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach\TXT\Queue.txt | — | |
MD5:— | SHA256:— | |||
| 2836 | SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach.exe | C:\Users\admin\AppData\Local\Temp\VradmnZO.exe | executable | |
MD5:— | SHA256:— | |||
| 2836 | SQLi Dumper 9.2.1 Cracked by CN$quad NextGenZ & Bleach.exe | C:\Users\admin\AppData\Local\Temp\QpBtuDjC.exe | executable | |
MD5:EFB5FF8E854308C461A8F91F3ED7F68C | SHA256:93FE36AA75B798D3AB09884EB998F474550D86B6A810FD3FFD75382A344638D5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
8
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
976 | vbc.exe | 136.243.88.145:45560 | xmr.pool.minergate.com | Hetzner Online GmbH | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
xmr.pool.minergate.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | A Network Trojan was detected | ET POLICY Monero Mining Pool DNS Lookup |
976 | vbc.exe | A Network Trojan was detected | ET POLICY Crypto Coin Miner Login |
976 | vbc.exe | A Network Trojan was detected | ET TROJAN CoinMiner Known Malicious Stratum Authline (2017-07-17 7) |
976 | vbc.exe | Misc activity | [PT SUSPICIOUS] Riskware/CoinMiner JSON_RPC Response |
976 | vbc.exe | Misc activity | [PT SUSPICIOUS] Risktool.W32.coinminer!c |
976 | vbc.exe | Misc activity | [PT SUSPICIOUS] Risktool.W32.coinminer!c |
976 | vbc.exe | Misc activity | [PT SUSPICIOUS] Riskware/CoinMiner JSON_RPC Response |
976 | vbc.exe | Misc activity | [PT SUSPICIOUS] Risktool.W32.coinminer!c |