| File name: | 18f456bc4bc4f55266f7456bfabe1f343560b6a59a3f5a68e995a34c0563a760.exe |
| Full analysis: | https://app.any.run/tasks/c5d4c875-d25e-40e5-a051-d41d8688e870 |
| Verdict: | Malicious activity |
| Threats: | MetaStealer is an info-stealing malware primarily targeting sensitive data like login credentials, payment details, and browser history. It typically infects systems via phishing emails or malicious downloads and can exfiltrate data to a command and control (C2) server. MetaStealer is known for its stealthy techniques, including evasion and persistence mechanisms, which make it difficult to detect. This malware has been actively used in various cyberattacks, particularly for financial theft and credential harvesting from individuals and organizations. |
| Analysis date: | July 03, 2024, 18:37:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | EDC8DC2A71AF650C1C6272EFA564ADC3 |
| SHA1: | 697581B70BF91793B76F61A60ACEC8FC764B1679 |
| SHA256: | 18F456BC4BC4F55266F7456BFABE1F343560B6A59A3F5A68E995A34C0563A760 |
| SSDEEP: | 196608:YnnG+D/I5NdBFwXVf/VKALqjIa4ESnfK0p:YnnG+LUdBFwFlKA2saofvp |
MALICIOUS
Drops the executable file immediately after the start
- 18f456bc4bc4f55266f7456bfabe1f343560b6a59a3f5a68e995a34c0563a760.exe (PID: 6824)
- Installer.exe (PID: 8)
- WindowsAutHost (PID: 7640)
Modifies hosts file to block updates
- Installer.exe (PID: 8)
Application was injected by another process
- svchost.exe (PID: 1060)
- dwm.exe (PID: 852)
- winlogon.exe (PID: 684)
- svchost.exe (PID: 320)
- svchost.exe (PID: 1100)
- svchost.exe (PID: 1040)
- svchost.exe (PID: 1180)
- svchost.exe (PID: 1172)
- lsass.exe (PID: 768)
- svchost.exe (PID: 1312)
- svchost.exe (PID: 1252)
- svchost.exe (PID: 1532)
- svchost.exe (PID: 1360)
- svchost.exe (PID: 1400)
- svchost.exe (PID: 1464)
- svchost.exe (PID: 1600)
- svchost.exe (PID: 1608)
- svchost.exe (PID: 1752)
- svchost.exe (PID: 1744)
- svchost.exe (PID: 1620)
- svchost.exe (PID: 1836)
- svchost.exe (PID: 1892)
- svchost.exe (PID: 1900)
- svchost.exe (PID: 2092)
- svchost.exe (PID: 2168)
- svchost.exe (PID: 1984)
- svchost.exe (PID: 2348)
- svchost.exe (PID: 2280)
- svchost.exe (PID: 2384)
- spoolsv.exe (PID: 2544)
- svchost.exe (PID: 2376)
- OfficeClickToRun.exe (PID: 3040)
- svchost.exe (PID: 2592)
- svchost.exe (PID: 2424)
- svchost.exe (PID: 2948)
- svchost.exe (PID: 2696)
- svchost.exe (PID: 2732)
- svchost.exe (PID: 3000)
- svchost.exe (PID: 2956)
- svchost.exe (PID: 3032)
- svchost.exe (PID: 3056)
- svchost.exe (PID: 3608)
- svchost.exe (PID: 2816)
- svchost.exe (PID: 2900)
- svchost.exe (PID: 2760)
- svchost.exe (PID: 3240)
- svchost.exe (PID: 3196)
- svchost.exe (PID: 3368)
- svchost.exe (PID: 3732)
- dasHost.exe (PID: 3948)
- svchost.exe (PID: 3884)
- ctfmon.exe (PID: 4404)
- svchost.exe (PID: 4824)
- svchost.exe (PID: 4384)
- svchost.exe (PID: 4184)
- svchost.exe (PID: 4228)
- svchost.exe (PID: 1488)
- sihost.exe (PID: 4156)
- svchost.exe (PID: 4032)
- svchost.exe (PID: 4344)
- svchost.exe (PID: 4548)
- explorer.exe (PID: 4612)
- dllhost.exe (PID: 5352)
- RuntimeBroker.exe (PID: 5088)
- RuntimeBroker.exe (PID: 5256)
- RuntimeBroker.exe (PID: 5796)
- svchost.exe (PID: 4804)
- svchost.exe (PID: 3644)
- uhssvc.exe (PID: 2656)
- svchost.exe (PID: 3028)
- dllhost.exe (PID: 6096)
- svchost.exe (PID: 3092)
- MoUsoCoreWorker.exe (PID: 2448)
- svchost.exe (PID: 3760)
- audiodg.exe (PID: 1096)
- svchost.exe (PID: 2536)
- dllhost.exe (PID: 6084)
- svchost.exe (PID: 6004)
- UserOOBEBroker.exe (PID: 844)
- ApplicationFrameHost.exe (PID: 1028)
- svchost.exe (PID: 1196)
- svchost.exe (PID: 5588)
- RuntimeBroker.exe (PID: 6708)
- svchost.exe (PID: 6340)
- WmiPrvSE.exe (PID: 3676)
- RuntimeBroker.exe (PID: 6464)
- svchost.exe (PID: 6868)
- svchost.exe (PID: 7068)
- WmiPrvSE.exe (PID: 5464)
- RuntimeBroker.exe (PID: 6332)
- RuntimeBroker.exe (PID: 7968)
Adds extension to the Windows Defender exclusion list
- Installer.exe (PID: 8)
- WindowsAutHost (PID: 7640)
Steals credentials from Web Browsers
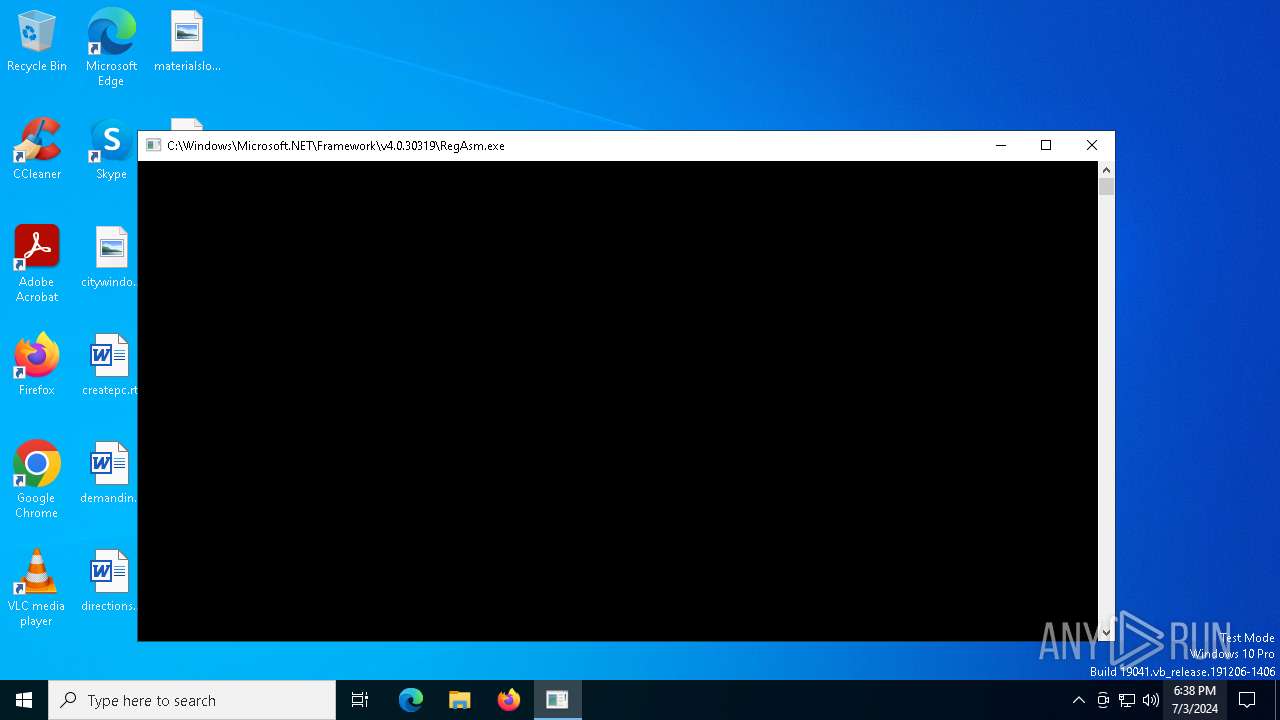
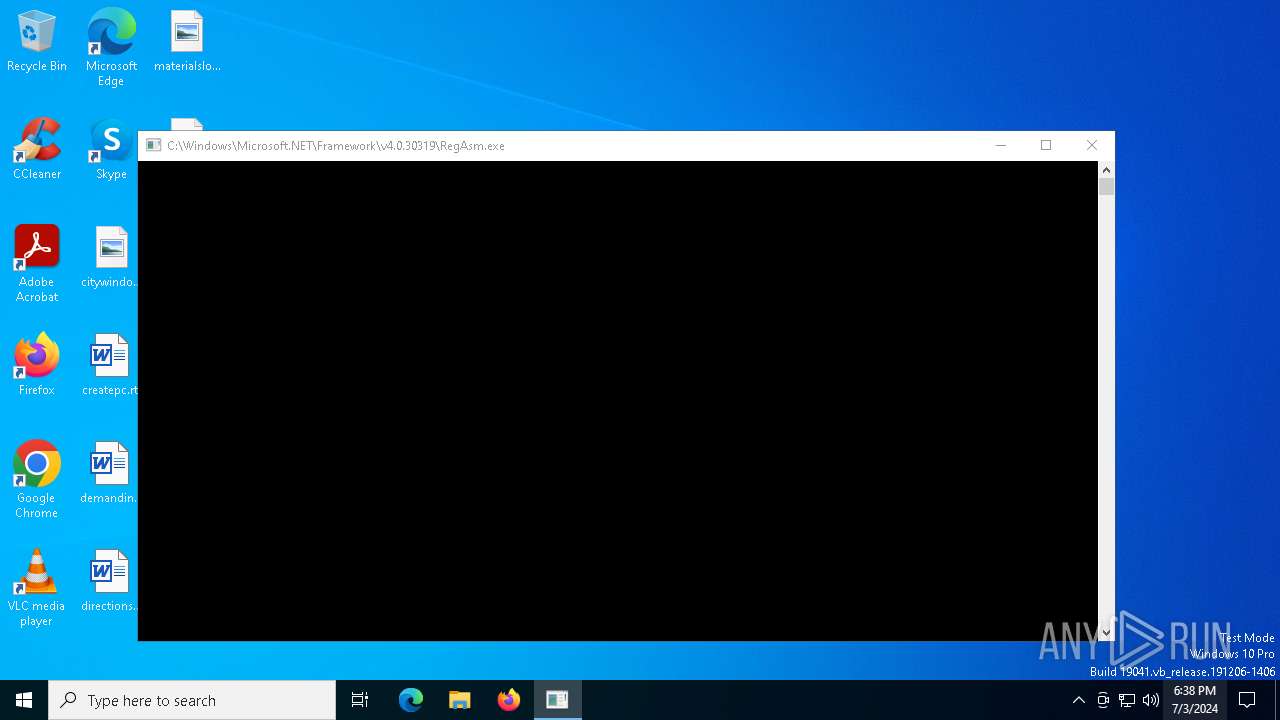
- RegAsm.exe (PID: 7060)
Runs injected code in another process
- dialer.exe (PID: 6304)
- dialer.exe (PID: 4836)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 7060)
METASTEALER has been detected (SURICATA)
- RegAsm.exe (PID: 7060)
Creates a writable file in the system directory
- powershell.exe (PID: 7664)
Connects to the CnC server
- dialer.exe (PID: 5328)
SILENTCRYPTOMINER has been detected (SURICATA)
- dialer.exe (PID: 5328)
XMRIG has been detected (YARA)
- dialer.exe (PID: 5328)
SUSPICIOUS
Reads security settings of Internet Explorer
- 18f456bc4bc4f55266f7456bfabe1f343560b6a59a3f5a68e995a34c0563a760.exe (PID: 6824)
Executable content was dropped or overwritten
- 18f456bc4bc4f55266f7456bfabe1f343560b6a59a3f5a68e995a34c0563a760.exe (PID: 6824)
- Installer.exe (PID: 8)
- WindowsAutHost (PID: 7640)
Reads the date of Windows installation
- 18f456bc4bc4f55266f7456bfabe1f343560b6a59a3f5a68e995a34c0563a760.exe (PID: 6824)
Executes application which crashes
- 4356897439864370634.exe (PID: 7000)
Powershell scripting: start process
- Installer.exe (PID: 7020)
Starts POWERSHELL.EXE for commands execution
- Installer.exe (PID: 7020)
- Installer.exe (PID: 8)
- WindowsAutHost (PID: 7640)
Adds/modifies Windows certificates
- lsass.exe (PID: 768)
Script adds exclusion extension to Windows Defender
- Installer.exe (PID: 8)
- WindowsAutHost (PID: 7640)
Script adds exclusion path to Windows Defender
- Installer.exe (PID: 8)
- WindowsAutHost (PID: 7640)
Searches for installed software
- RegAsm.exe (PID: 7060)
Starts SC.EXE for service management
- Installer.exe (PID: 8)
- WindowsAutHost (PID: 7640)
Starts CMD.EXE for commands execution
- Installer.exe (PID: 8)
- WindowsAutHost (PID: 7640)
Uses powercfg.exe to modify the power settings
- Installer.exe (PID: 8)
- WindowsAutHost (PID: 7640)
Process uninstalls Windows update
- wusa.exe (PID: 5988)
- wusa.exe (PID: 8052)
Executes as Windows Service
- WindowsAutHost (PID: 7640)
Drops a system driver (possible attempt to evade defenses)
- WindowsAutHost (PID: 7640)
Checks for external IP
- RegAsm.exe (PID: 7060)
- svchost.exe (PID: 2168)
Contacting a server suspected of hosting an CnC
- RegAsm.exe (PID: 7060)
Potential Corporate Privacy Violation
- RegAsm.exe (PID: 7060)
- dialer.exe (PID: 5328)
Crypto Currency Mining Activity Detected
- dialer.exe (PID: 5328)
- svchost.exe (PID: 2168)
Checks Windows Trust Settings
- OfficeClickToRun.exe (PID: 3040)
INFO
Creates a writable file in the system directory
- lsass.exe (PID: 768)
- svchost.exe (PID: 1252)
- svchost.exe (PID: 3032)
- OfficeClickToRun.exe (PID: 3040)
Checks supported languages
- 18f456bc4bc4f55266f7456bfabe1f343560b6a59a3f5a68e995a34c0563a760.exe (PID: 6824)
- 4356897439864370634.exe (PID: 7000)
- Installer.exe (PID: 7020)
- RegAsm.exe (PID: 7060)
- Installer.exe (PID: 8)
- WindowsAutHost (PID: 7640)
Reads Microsoft Office registry keys
- OfficeClickToRun.exe (PID: 3040)
Reads the computer name
- 18f456bc4bc4f55266f7456bfabe1f343560b6a59a3f5a68e995a34c0563a760.exe (PID: 6824)
- RegAsm.exe (PID: 7060)
Create files in a temporary directory
- 18f456bc4bc4f55266f7456bfabe1f343560b6a59a3f5a68e995a34c0563a760.exe (PID: 6824)
Process checks computer location settings
- 18f456bc4bc4f55266f7456bfabe1f343560b6a59a3f5a68e995a34c0563a760.exe (PID: 6824)
Creates files in the program directory
- svchost.exe (PID: 7068)
- Installer.exe (PID: 8)
- MoUsoCoreWorker.exe (PID: 2448)
- svchost.exe (PID: 1060)
Reads the software policy settings
- OfficeClickToRun.exe (PID: 3040)
- lsass.exe (PID: 768)
- RegAsm.exe (PID: 7060)
- WerFault.exe (PID: 6384)
- slui.exe (PID: 6588)
Reads the machine GUID from the registry
- RegAsm.exe (PID: 7060)
- OfficeClickToRun.exe (PID: 3040)
Creates files or folders in the user directory
- lsass.exe (PID: 768)
- WerFault.exe (PID: 6384)
The executable file from the user directory is run by the Powershell process
- Installer.exe (PID: 8)
Checks proxy server information
- WerFault.exe (PID: 6384)
- RegAsm.exe (PID: 7060)
Reads Environment values
- RegAsm.exe (PID: 7060)
Reads Windows Product ID
- WmiPrvSE.exe (PID: 5464)
Disables trace logs
- RegAsm.exe (PID: 7060)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1272)
- powershell.exe (PID: 7664)
.NET Reactor protector has been detected
- RegAsm.exe (PID: 7060)
Reads the time zone
- WmiPrvSE.exe (PID: 5464)
UPX packer has been detected
- dialer.exe (PID: 5328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:02:26 09:01:55+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.33 |
| CodeSize: | 236032 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x26670 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
208
Monitored processes
163
Malicious processes
98
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | "C:\Users\admin\AppData\Local\Temp\CHROME_SETUP\Installer.exe" | C:\Users\admin\AppData\Local\Temp\CHROME_SETUP\Installer.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 320 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | C:\WINDOWS\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 844 | C:\Windows\System32\oobe\UserOOBEBroker.exe -Embedding | C:\Windows\System32\oobe\UserOOBEBroker.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: User OOBE Broker Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 852 | "dwm.exe" | C:\Windows\System32\dwm.exe | winlogon.exe | ||||||||||||
User: DWM-1 Company: Microsoft Corporation Integrity Level: SYSTEM Description: Desktop Window Manager Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | C:\WINDOWS\system32\sc.exe stop UsoSvc | C:\Windows\System32\sc.exe | — | Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1004 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1028 | C:\WINDOWS\system32\ApplicationFrameHost.exe -Embedding | C:\Windows\System32\ApplicationFrameHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Application Frame Host Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
108 191
Read events
107 419
Write events
590
Delete events
182
Modification events
| (PID) Process: | (3760) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\S-1-5-18 |
| Operation: | write | Name: | DeviceLicenseUpdateFailureCount |
Value: 0 | |||
| (PID) Process: | (3760) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\IdentityCRL |
| Operation: | write | Name: | GlobalDeviceUpdateTime |
Value: 8A9A856600000000 | |||
| (PID) Process: | (3760) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\S-1-5-18\02lsvnbxpyfjdfiq |
| Operation: | write | Name: | DeviceId |
Value: <Data LastUpdatedTime="1720031882"><User username="02LSVNBXPYFJDFIQ"/></Data>
| |||
| (PID) Process: | (3760) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\S-1-5-18\02lsvnbxpyfjdfiq |
| Operation: | write | Name: | DeviceId |
Value: <Data LastUpdatedTime="1720031882"><User username="02LSVNBXPYFJDFIQ"><HardwareInfo BoundTime="1720031882" TpmKeyStateClient="1" TpmKeyStateServer="3" LicenseKeySequence="1" LicenseInstallError="0" LicenseKeyVersion="2"/></User></Data>
| |||
| (PID) Process: | (3760) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\Logs\02lsvnbxpyfjdfiq |
| Operation: | write | Name: | Provision Wednesday, July 03, 2024 18:38:02 |
Value: AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAQ9hgSoMcwEm5GLlP5E0uDAAAAAACAAAAAAAQZgAAAAEAACAAAAC7RwyTOe8x/VRTc8x4sLvuonDPj2Oo5OTf4n7I6ssDcwAAAAAOgAAAAAIAACAAAADg9v+T3pCE2IBHm14NhEBiVMn1mPKmtAh5xmblJFFpciAAAAAHEfDmDyP/6HxG3Cek9St+jA/M77ScNFVObHw0mJLMyEAAAAD+fyuXVu79SQQaOBF3UNi0R1hsKmLfufBm7Bb4wjVJNys+9sPWiL25Yw230MB+b6fjWKoxM6nvJH3nCAVqLNB8 | |||
| (PID) Process: | (3760) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\S-1-5-18 |
| Operation: | write | Name: | ValidDeviceId |
Value: 02lsvnbxpyfjdfiq | |||
| (PID) Process: | (3760) svchost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\IdentityCRL\DeviceIdentities\production\S-1-5-18\02lsvnbxpyfjdfiq |
| Operation: | write | Name: | AppIdList |
Value: {AFDA72BF-3409-413A-B54E-2AB8D66A7826}; | |||
| (PID) Process: | (5588) svchost.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store |
| Operation: | write | Name: | C:\Users\admin\AppData\Local\Temp\18f456bc4bc4f55266f7456bfabe1f343560b6a59a3f5a68e995a34c0563a760.exe |
Value: 534143500100000000000000070000002800000002F804010000000001000000000000000000000A0021000050BB64EDDDACD5010000000000000000 | |||
| (PID) Process: | (1312) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{C660D735-E9F2-4190-9B4E-97ADF1AFFA16} |
| Operation: | write | Name: | DynamicInfo |
Value: 030000003B22B524AAB7D801EBFFC02278CDDA01000000000000000037456919B92DDA01 | |||
| (PID) Process: | (1312) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{C660D735-E9F2-4190-9B4E-97ADF1AFFA16} |
| Operation: | write | Name: | DynamicInfo |
Value: 030000003B22B524AAB7D801EBFFC02278CDDA01000000000000000025F96E2378CDDA01 | |||
Executable files
4
Suspicious files
82
Text files
16
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 768 | lsass.exe | C:\WINDOWS\system32\Microsoft\Protect\S-1-5-18\User\4a60d843-1c83-49c0-b918-b94fe44d2e0c | binary | |
MD5:49B72031BCE941FA17EFCEC6B534F14C | SHA256:2E4D4D134361252AFAC131CBEDE3CBC4D106732C35974BE7BF7903AA0D1BBF0A | |||
| 3040 | OfficeClickToRun.exe | C:\WINDOWS\system32\config\systemprofile\AppData\Local\Microsoft\Office\16.0\officeclicktorun.exe_Rules.xml | xml | |
MD5:7B8AE1247CA7D14E92668BA5C2D3A0A3 | SHA256:E6CCBC3BBA0CE0A1255545C31F6154274614722402050F58A481EDF485ECAC96 | |||
| 768 | lsass.exe | C:\WINDOWS\system32\Microsoft\Protect\S-1-5-18\User\Preferred | binary | |
MD5:F2F41B65EADFD141E4C4FC550A01BA4F | SHA256:75F693FCC763E26423BCE63BB518190FC53B01380CB24FACF8C4CFB863B0AE3F | |||
| 7068 | svchost.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERA54.tmp.txt | binary | |
MD5:55388E18105FCE6F64D599C872913954 | SHA256:4B7E491A2F7052F293E8BA0ADDBF5875B6696963362E7ED830AFE9279C10C9DE | |||
| 6824 | 18f456bc4bc4f55266f7456bfabe1f343560b6a59a3f5a68e995a34c0563a760.exe | C:\Users\admin\AppData\Local\Temp\CHROME_SETUP\4356897439864370634.exe | executable | |
MD5:5EA30ED7A18CB503C64C9589F415015A | SHA256:1C0C5AABFD797FD5978DF8E5B992946F6F3099B987629C20E77F3EF581579C65 | |||
| 6384 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER801.tmp.dmp | dmp | |
MD5:3016858FC61882B8CF5BABC23A6F4717 | SHA256:0C9D95C11BE53B3B085C0DFB805F4E079CD6EA31EACA0508AC87025952080DD4 | |||
| 6384 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERA07.tmp.xml | xml | |
MD5:A342F166867A26950DD992647C32433D | SHA256:3AF23EE3A89D84BD3A5A9DF45A58A29358E3277A3A363B65BEB29350F4ABB7F8 | |||
| 1608 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-AD0331FB.pf | binary | |
MD5:79121722F4B3EAD46E786DBB576B3EEB | SHA256:DD0942ABD71DF44462FA3D19DF1DA6A66C0947A07D8E6D39AD95E62569B73215 | |||
| 7068 | svchost.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERA24.tmp.csv | binary | |
MD5:36B10DE39F19229FE6A03548D9CE959E | SHA256:647E2286D5B3E88ADCF2362D251714988FC24DCBE202AD520AEAAE6CE538D451 | |||
| 1608 | svchost.exe | C:\Windows\Prefetch\TASKHOSTW.EXE-3E0B74C8.pf | binary | |
MD5:401DA137204E7E00D43537629C7135FF | SHA256:E064812B56EE8EE3A542E9A13E2BC8638F4ACF54A17AF20C520B27DFD111F1F3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
73
DNS requests
25
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
900 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6384 | WerFault.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2416 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6384 | WerFault.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
7804 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
7804 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
5328 | dialer.exe | POST | 200 | 31.31.198.99:80 | http://panelslk.pro/api/endpoint.php | unknown | — | — | unknown |
5328 | dialer.exe | POST | 200 | 31.31.198.99:80 | http://panelslk.pro/api/endpoint.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3040 | OfficeClickToRun.exe | 52.111.227.14:443 | nexusrules.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3760 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
1928 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5328 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6004 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2760 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1928 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nexusrules.officeapps.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
api.ip.sb |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7060 | RegAsm.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 15 |
7060 | RegAsm.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] MetaStealer v.5 TLS Connection |
7060 | RegAsm.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] MetaStealer v.5 TLS Certificate |
5328 | dialer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
2168 | svchost.exe | Crypto Currency Mining Activity Detected | ET COINMINER CoinMiner Domain in DNS Lookup (pool .hashvault .pro) |
5328 | dialer.exe | Crypto Currency Mining Activity Detected | ET MALWARE [ANY.RUN] SilentCryptoMiner Check-in POST Request |
5328 | dialer.exe | Crypto Currency Mining Activity Detected | MINER [ANY.RUN] SilentCryptoMiner HTTP Request to UnamWebPanel |
5328 | dialer.exe | Crypto Currency Mining Activity Detected | ET MALWARE [ANY.RUN] SilentCryptoMiner Check-in POST Request |
5328 | dialer.exe | Crypto Currency Mining Activity Detected | MINER [ANY.RUN] SilentCryptoMiner HTTP Request to UnamWebPanel |
5328 | dialer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
4 ETPRO signatures available at the full report