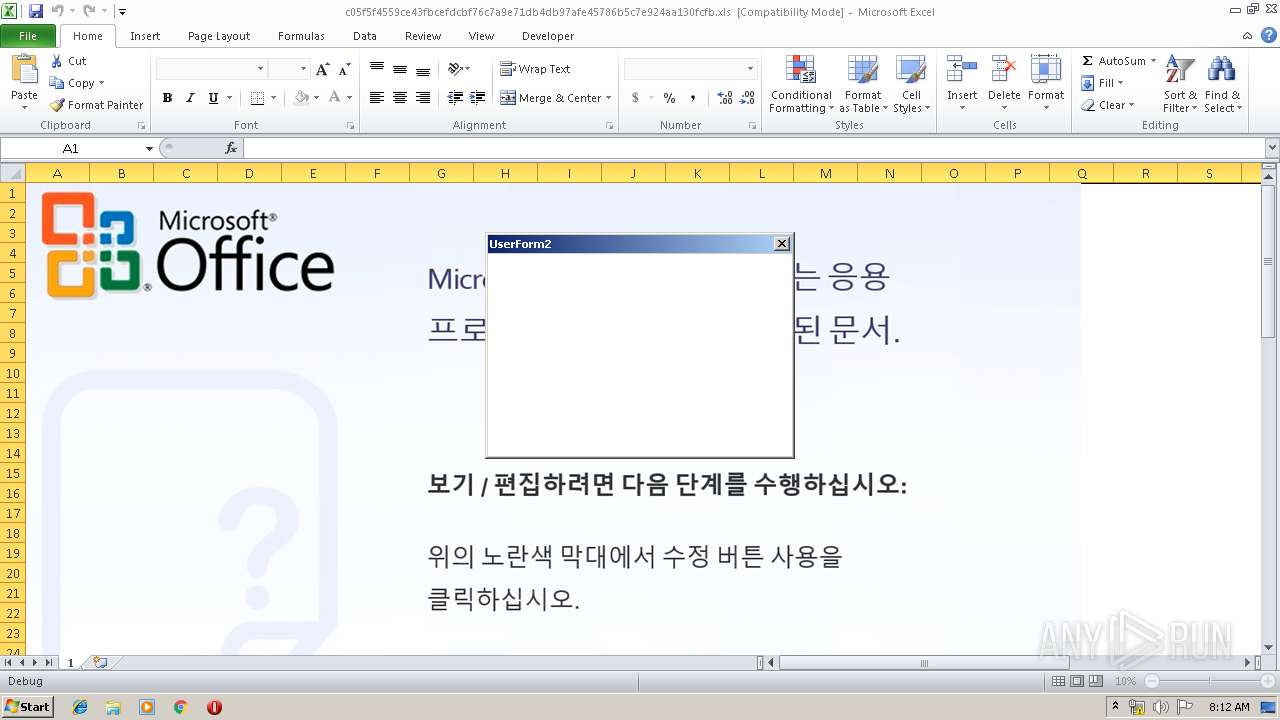
| File name: | c05f5f4559ce43fbcefdcbf76c7a9e71db4db97afe45786b5c7e924aa130fcfb.xls |
| Full analysis: | https://app.any.run/tasks/4c2023b2-694d-446a-b929-33e9c2b619c5 |
| Verdict: | Malicious activity |
| Threats: | FlawedAmmmyy is a RAT type malware that can be used to perform actions remotely on an infected PC. This malware is well known for being featured in especially large campaigns with wide target demographics. |
| Analysis date: | June 20, 2019, 07:12:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1251, Author: kerio, Last Saved By: alex, Name of Creating Application: Microsoft Excel, Create Time/Date: Sat May 18 08:27:21 2019, Last Saved Time/Date: Wed Jun 19 18:42:03 2019, Security: 0 |
| MD5: | 4DEE778771A60586D664D307357763B5 |
| SHA1: | A61FE59A8557B7DF8481D318463290DB0ADFE733 |
| SHA256: | 1838757CE7D5140782DF466C77F0C868A031FC5F773670C84E9ED4ACB4A667A8 |
| SSDEEP: | 6144:6Kpb8rGYrMPelwhKmFV5xtuEsg8/dgpLwQdh4AcC+a1q8/au0MZpq0jO:j0QdhUvAz/aQpq0jO |
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3320)
Application was dropped or rewritten from another process
- stt.exe (PID: 3684)
- wsus.exe (PID: 2128)
- wsus.exe (PID: 772)
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 3320)
Executable content was dropped or overwritten
- EXCEL.EXE (PID: 3320)
AMMYY was detected
- wsus.exe (PID: 2128)
Starts NET.EXE to view/change users group
- stt.exe (PID: 3684)
FLAWEDAMMYY was detected
- wsus.exe (PID: 2128)
Connects to CnC server
- wsus.exe (PID: 2128)
Loads the Task Scheduler COM API
- stt.exe (PID: 3684)
Loads the Task Scheduler DLL interface
- stt.exe (PID: 3684)
Changes the autorun value in the registry
- stt.exe (PID: 3684)
SUSPICIOUS
Creates files in the program directory
- stt.exe (PID: 3684)
Reads Internet Cache Settings
- EXCEL.EXE (PID: 3320)
Executable content was dropped or overwritten
- stt.exe (PID: 3684)
Starts CMD.EXE for commands execution
- stt.exe (PID: 3684)
Executed via Task Scheduler
- wsus.exe (PID: 772)
Creates files in the Windows directory
- stt.exe (PID: 3684)
INFO
Creates files in the user directory
- EXCEL.EXE (PID: 3320)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| CompObjUserTypeLen: | 25 |
|---|---|
| CompObjUserType: | Microsoft Forms 2.0 Form |
| Author: | kerio |
| LastModifiedBy: | alex |
| Software: | Microsoft Excel |
| CreateDate: | 2019:05:18 07:27:21 |
| ModifyDate: | 2019:06:19 17:42:03 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | 1 |
| HeadingPairs: |
|
Total processes
47
Monitored processes
11
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 772 | C:\ProgramData\NuGets\wsus.exe | C:\ProgramData\NuGets\wsus.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1208 | net group /domain | C:\Windows\system32\net.exe | — | stt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1760 | cmd.exe /c start "" stt.exe | C:\Windows\system32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2128 | C:\ProgramData\NuGets\wsus.exe | C:\ProgramData\NuGets\wsus.exe | stt.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2172 | "C:\Windows\system32\cmd.exe" /c del C:\Users\admin\DOCUME~1\stt.exe >> NUL | C:\Windows\system32\cmd.exe | — | stt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2472 | net group /domain | C:\Windows\system32\net.exe | — | stt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2736 | C:\Windows\system32\net1 group /domain | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3200 | C:\Windows\system32\net1 group /domain | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3320 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3656 | "C:\Windows\system32\cmd.exe" /c del C:\Users\admin\DOCUME~1\stt.exe >> NUL | C:\Windows\system32\cmd.exe | — | stt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
760
Read events
643
Write events
110
Delete events
7
Modification events
| (PID) Process: | (3320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | 8i> |
Value: 38693E00F80C0000010000000000000000000000 | |||
| (PID) Process: | (3320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: F80C00000EAD48803727D50100000000 | |||
| (PID) Process: | (3320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | 8i> |
Value: 38693E00F80C0000010000000000000000000000 | |||
| (PID) Process: | (3320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3320) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\11F403 |
| Operation: | write | Name: | 11F403 |
Value: 04000000F80C00006600000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C0063003000350066003500660034003500350039006300650034003300660062006300650066006400630062006600370036006300370061003900650037003100640062003400640062003900370061006600650034003500370038003600620035006300370065003900320034006100610031003300300066006300660062002E0078006C007300000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C000100000000000000C028EC813727D50103F4110003F4110000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
3
Suspicious files
4
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3320 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVREDB8.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3320 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\p2[1] | executable | |
MD5:— | SHA256:— | |||
| 3684 | stt.exe | C:\ProgramData\NuGets\template_41c318.TMPTMPZIP7 | binary | |
MD5:— | SHA256:— | |||
| 3684 | stt.exe | C:\Windows\Tasks\Microsoft System Protect.job | binary | |
MD5:— | SHA256:— | |||
| 3320 | EXCEL.EXE | C:\Users\admin\Documents\stt.exe | executable | |
MD5:— | SHA256:— | |||
| 3684 | stt.exe | C:\ProgramData\NuGets\wsus.exe | executable | |
MD5:— | SHA256:— | |||
| 3320 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3684 | stt.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\02[1].dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
0
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3684 | stt.exe | GET | 200 | 54.38.127.28:80 | http://54.38.127.28/02.dat | FR | binary | 583 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3320 | EXCEL.EXE | 179.43.147.77:80 | — | Private Layer INC | CH | suspicious |
3684 | stt.exe | 54.38.127.28:80 | — | OVH SAS | FR | suspicious |
2128 | wsus.exe | 185.117.89.145:80 | — | Portlane AB | SE | malicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
3320 | EXCEL.EXE | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |
3320 | EXCEL.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M1 |
3320 | EXCEL.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3320 | EXCEL.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M2 |
3320 | EXCEL.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from MSXMLHTTP non-exe extension M2 |
3320 | EXCEL.EXE | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
2128 | wsus.exe | A Network Trojan was detected | MALWARE [PTsecurity] FlawedAmmyy.RAT |
2128 | wsus.exe | A Network Trojan was detected | MALWARE [PTsecurity] AMMYY RAT |
2128 | wsus.exe | A Network Trojan was detected | ET TROJAN Win32/FlawedAmmyy RAT CnC Checkin |
2128 | wsus.exe | A Network Trojan was detected | MALWARE [PTsecurity] FlawedAmmyy.RAT Checkin |
Process | Message |
|---|---|
stt.exe | C:\ProgramData\NuGets\template_41c318.TMPTMPZIP7 |
stt.exe | 1 |