| File name: | windows.ps1 |
| Full analysis: | https://app.any.run/tasks/6dd4d805-4e96-4797-8b90-e817dda27313 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | July 21, 2024, 12:23:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text |
| MD5: | 63F6C82077C4C39D6D9101409B16A668 |
| SHA1: | 09D1960993C90F39607F437A2106B65DB7AEAE29 |
| SHA256: | 18284686FEAB2A0753BD0059A64004D8B86BB47048065CBA12D323EFBB6CC891 |
| SSDEEP: | 12:6o2W5VrEJ/WoXGIiCXWHlbGRMGPvpXyTkFUJP4Gko:6or1PoWh4cCRMG5yTTPSo |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6348)
Drops the executable file immediately after the start
- powershell.exe (PID: 6348)
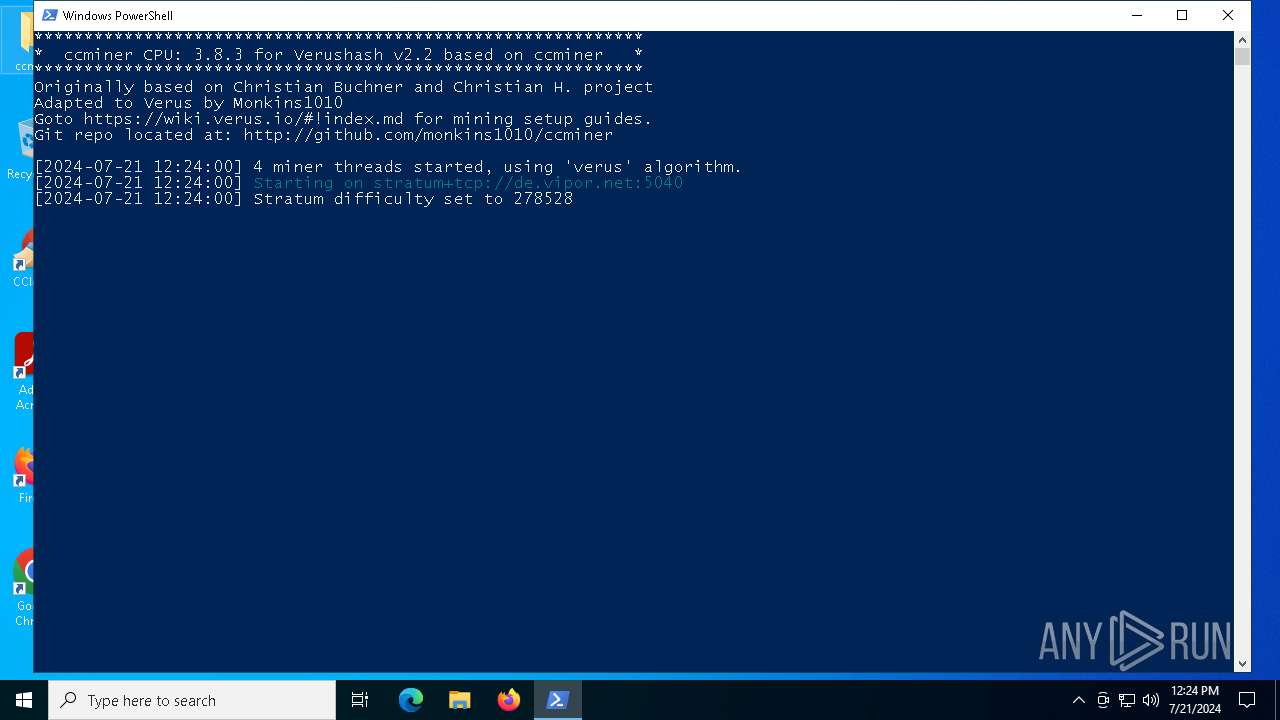
Looks like the application has launched a miner
- powershell.exe (PID: 6348)
SUSPICIOUS
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6348)
Executable content was dropped or overwritten
- powershell.exe (PID: 6348)
Connects to unusual port
- ccminer.exe (PID: 7760)
Crypto Currency Mining Activity Detected
- ccminer.exe (PID: 7760)
Starts CMD.EXE for commands execution
- ccminer.exe (PID: 7760)
Potential Corporate Privacy Violation
- ccminer.exe (PID: 7760)
INFO
Disables trace logs
- powershell.exe (PID: 6348)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6348)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6348)
Checks proxy server information
- powershell.exe (PID: 6348)
- slui.exe (PID: 1884)
Reads the computer name
- ccminer.exe (PID: 7760)
Reads the software policy settings
- slui.exe (PID: 1884)
Checks supported languages
- ccminer.exe (PID: 7760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
140
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1884 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6348 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\windows.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6924 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | ccminer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7760 | "C:\Users\admin\Desktop\ccminer\ccminer\ccminer.exe" -a verus -o stratum+tcp://de.vipor.net:5040 -u RHACKERwSVgjTvV4vNiTjmrkLTD7a92ALD.Windows -p x -t 4 | C:\Users\admin\Desktop\ccminer\ccminer\ccminer.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 2.3 Modules
| |||||||||||||||
| 8088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 217
Read events
13 203
Write events
14
Delete events
0
Modification events
| (PID) Process: | (6348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
2
Suspicious files
6
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6348 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ikcifxkx.srh.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6348 | powershell.exe | C:\Users\admin\Desktop\ccminer\ccminer\run verushhash - cpu.bat | text | |
MD5:B201C7FCD8719663610F3B66746E839F | SHA256:48D35240EA7A349D25E9199CD9EE7B60D955257B8F4E55922F8C641093869DC5 | |||
| 6348 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\QFHJ0U0IWXC52VTBOMWQ.temp | binary | |
MD5:DCC96A1403E274201121DA40EF4A0B7F | SHA256:B1FB6B6717C43A57F96F3609952106EA14FDA0708FEBC043FA34834243F31F90 | |||
| 6348 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF42998f.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6348 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vtx5odzw.mdq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6348 | powershell.exe | C:\Users\admin\Desktop\ccminer\ccminer\ccminer.exe | executable | |
MD5:153E4364A395B282B983DFC2C5884105 | SHA256:6A1077166DE9D1CC6FCEAF6DA6F8C5E1C8D9D5F99F3AB845B9790FC6D395D896 | |||
| 6348 | powershell.exe | C:\Users\admin\Desktop\ccminer.zip | compressed | |
MD5:34EBE82E6C51CCDBB281D2E930CFC0F0 | SHA256:DBA46D49533BD6CD1E69A1F331508B709F51578D45D05F63E5B6878F74061F61 | |||
| 6348 | powershell.exe | C:\Users\admin\Desktop\ccminer\__MACOSX\._ccminer | ad | |
MD5:642211D706B402159A6D87C6CEB9316B | SHA256:A1CEED2D1276A1E9638E9ACADCCB40779A1D6BF8D894ABD60525CA36AA86902E | |||
| 6348 | powershell.exe | C:\Users\admin\Desktop\ccminer\ccminer\libcrypto-1_1-x64.dll | executable | |
MD5:23395359B1CCAD6BC9B0729399E82F59 | SHA256:A2F0F0ACF81849ED881A7EC4A34C235FA7B2FFD97CA949464BD019AA7F746B91 | |||
| 6348 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:C904B83F3EB6B36C24B175843EAE2F18 | SHA256:AE9C3B418FC314078AEA3B8FE77670BDBD72E127D1DAE886D031A73C2074B64F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
43
DNS requests
15
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 40.68.123.157:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 40.68.123.157:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
— | — | GET | 304 | 40.68.123.157:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 20.242.39.171:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
— | — | GET | 200 | 140.82.121.4:443 | https://raw.githubusercontent.com/MomboteQ/mining-scripts/main/verus/ccminer-win.zip | unknown | compressed | 1.35 Mb | unknown |
— | — | POST | 200 | 20.223.35.26:443 | https://arc.msn.com/v4/api/register?asid=A5A6CCA4E57743F6A32905E9D4892058&placement=cdmdevreg&country=US&locale=en-US&poptin=0&fmt=json&arch=AMD64&chassis=1&concp=0&d3dfl=D3D_FEATURE_LEVEL_12_1&devfam=Windows.Desktop&devosver=10.0.19045.4046&dinst=1661339444&dmret=0&flightbranch=&flightring=Retail&icluc=0&localid=w%3AAC7699B0-48EA-FD22-C8DC-06A02098A0F0&oem=DELL&osbranch=vb_release&oslocale=en-US&osret=1&ossku=Professional&osskuid=48&prccn=4&prccs=3094&prcmf=AuthenticAMD&procm=Intel%28R%29%20Core%28TM%29%20i5-6400%20CPU%20%40%202.70GHz&ram=4096&tinst=Client&tl=1&pat=0&smc=0&sac=0&disphorzres=1280&dispsize=15.3&dispvertres=720&ldisphorzres=1280&ldispvertres=720&moncnt=1&cpdsk=260281&frdsk=218542&lo=3613223&tsu=1003753 | unknown | — | — | unknown |
— | — | POST | 401 | 4.209.32.198:443 | https://licensing.mp.microsoft.com/v7.0/licenses/content | unknown | binary | 340 b | unknown |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | unknown |
— | — | GET | 200 | 20.223.35.26:443 | https://fd.api.iris.microsoft.com/v4/api/selection?&asid=0FA5A561830541F6AD7835F471210E4F&nct=1&placement=88000677&bcnt=30&country=US&locale=en-US&poptin=0&fmt=json&arch=AMD64&chassis=1&concp=0&d3dfl=D3D_FEATURE_LEVEL_12_1&devfam=Windows.Desktop&devosver=10.0.19045.4046&dinst=1661339444&dmret=0&flightbranch=&flightring=Retail&icluc=0&localid=w%3AAC7699B0-48EA-FD22-C8DC-06A02098A0F0&oem=DELL&osbranch=vb_release&oslocale=en-US&osret=1&ossku=Professional&osskuid=48&prccn=4&prccs=3094&prcmf=AuthenticAMD&procm=Intel%28R%29%20Core%28TM%29%20i5-6400%20CPU%20%40%202.70GHz&ram=4096&tinst=Client&tl=1&pat=0&smc=0&sac=0&disphorzres=1280&dispsize=15.3&dispvertres=720&ldisphorzres=1280&ldispvertres=720&moncnt=1&cpdsk=260281&frdsk=218542&lo=3613223&tsu=1003753 | unknown | binary | 102 b | unknown |
— | — | GET | 200 | 40.68.123.157:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | compressed | 23.9 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4716 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5620 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7856 | svchost.exe | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4796 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2760 | svchost.exe | 40.113.103.199:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6004 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7876 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
arc.msn.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
de.vipor.net |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
7760 | ccminer.exe | Potential Corporate Privacy Violation | AV POLICY NiceHash Miner Subscribing To Pool |
7760 | ccminer.exe | Crypto Currency Mining Activity Detected | ET COINMINER W32/BitCoinMiner.MultiThreat Subscribe/Authorize Stratum Protocol Message |
7760 | ccminer.exe | Crypto Currency Mining Activity Detected | ET COINMINER W32/BitCoinMiner.MultiThreat Subscribe/Authorize Stratum Protocol Message |
7760 | ccminer.exe | Potential Corporate Privacy Violation | AV POLICY NiceHash Miner Subscribing To Pool |
7760 | ccminer.exe | Crypto Currency Mining Activity Detected | ET COINMINER W32/BitCoinMiner.MultiThreat Subscribe/Authorize Stratum Protocol Message |