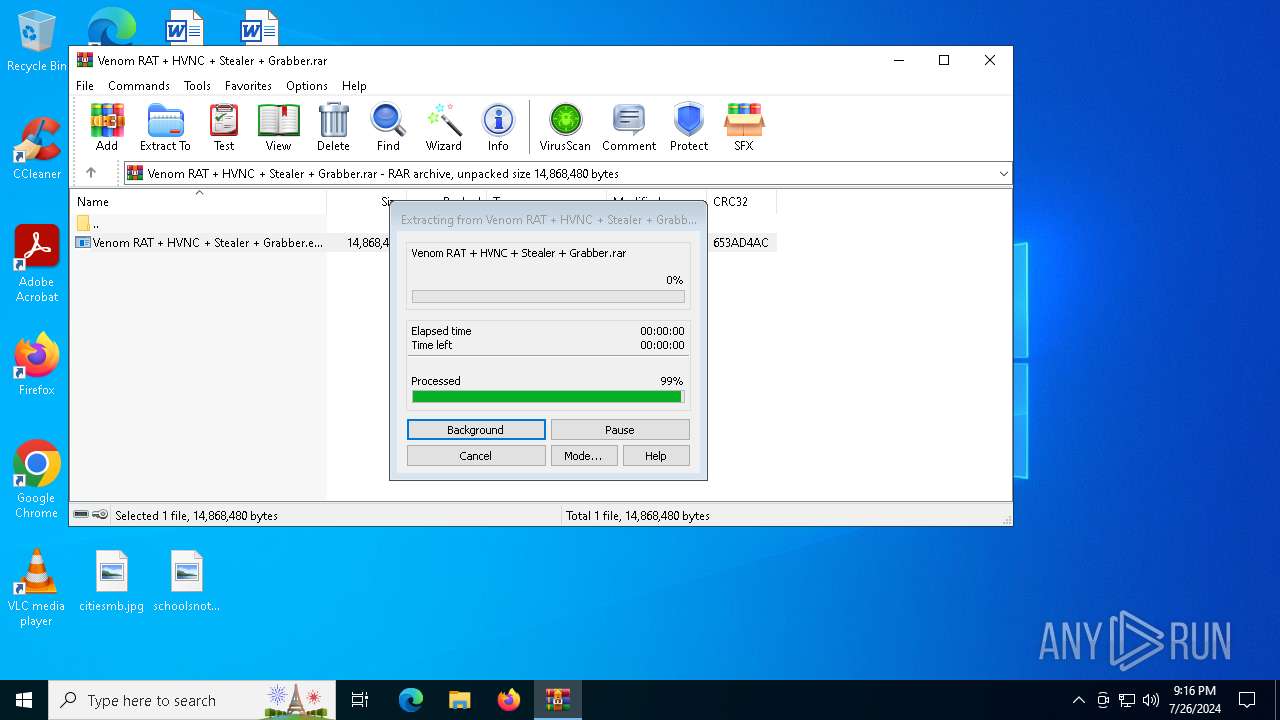
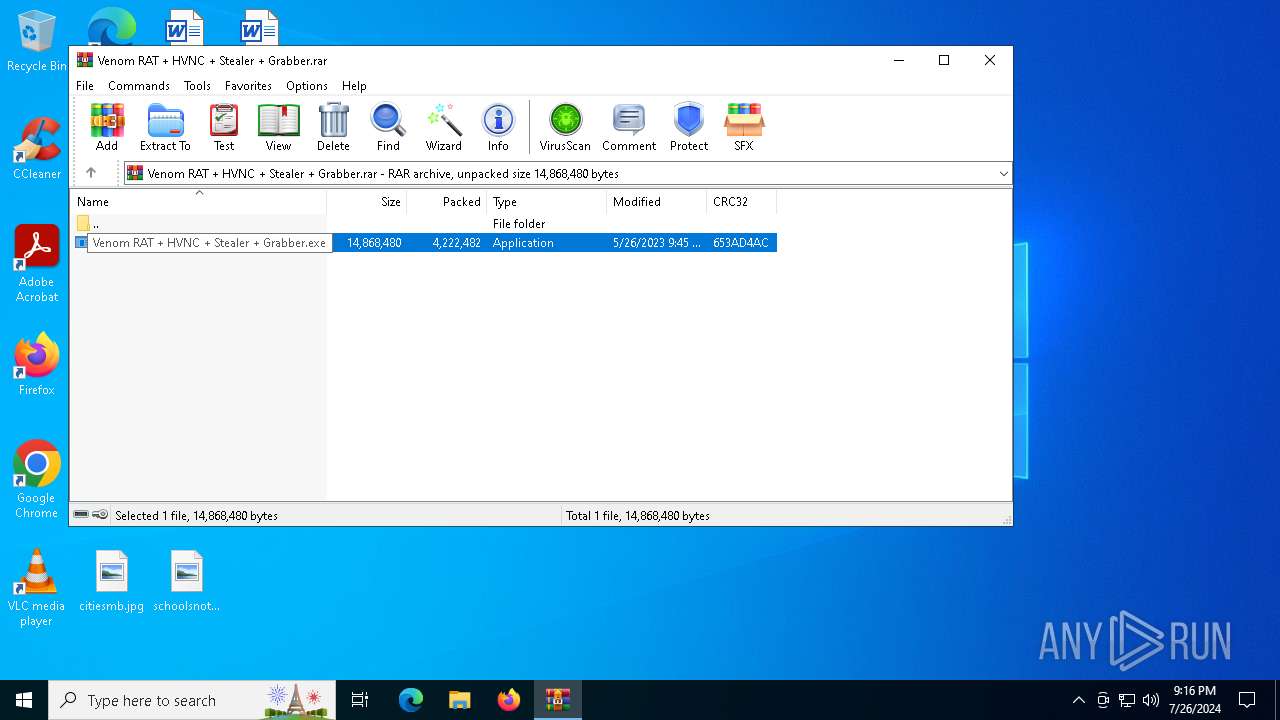
| File name: | Venom RAT + HVNC + Stealer + Grabber.rar |
| Full analysis: | https://app.any.run/tasks/882528bb-7faa-4a52-a25e-2ace93cbf29b |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 26, 2024, 21:16:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 93C3492FD36180F9776E3081437EC07A |
| SHA1: | 508911E0EF544674DE9E6804B19FD2C64F58AABE |
| SHA256: | 17ADB97EF680512C6441EAA68B20C4CC49CA9E9EB8BC0C281CDA0119012EE7E0 |
| SSDEEP: | 98304:L06nHcbfcj6Y4ZDS4oWhzRMMGMlacfiBnge89zZ/gIg4Mfqg4aSwTJgLMkXoo8HI:VjckpzPMP |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2308)
ASYNCRAT has been detected (YARA)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 2332)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2308)
Executes application which crashes
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 2332)
INFO
Creates files or folders in the user directory
- WerFault.exe (PID: 4304)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2308)
Checks proxy server information
- WerFault.exe (PID: 4304)
Checks supported languages
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 2332)
Reads the computer name
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 2332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
148
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2308 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Venom RAT + HVNC + Stealer + Grabber.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2332 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2308.39664\Venom RAT + HVNC + Stealer + Grabber.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2308.39664\Venom RAT + HVNC + Stealer + Grabber.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: VenomRAT Exit code: 3762504530 Version: 6.0.1 Modules
| |||||||||||||||
| 4092 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4304 | C:\WINDOWS\system32\WerFault.exe -u -p 2332 -s 788 | C:\Windows\System32\WerFault.exe | Venom RAT + HVNC + Stealer + Grabber.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6440 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 201
Read events
9 181
Write events
20
Delete events
0
Modification events
| (PID) Process: | (2308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Venom RAT + HVNC + Stealer + Grabber.rar | |||
| (PID) Process: | (2308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
1
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4304 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_Venom RAT + HVNC_ea87d7c01f8e574b49834696c258264836d983e_d3562942_ca63179b-6d23-489f-a8bf-0fc0fdb16938\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4304 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Venom RAT + HVNC + Stealer + Grabber.exe.2332.dmp | — | |
MD5:— | SHA256:— | |||
| 4304 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER2E4B.tmp.dmp | dmp | |
MD5:37859541F203422A2636F1A5B966274B | SHA256:BEAED15991C3644BB9898515425B771DA3C1DBDADD41DD17A55298CA9B794F4E | |||
| 4304 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER2F76.tmp.xml | xml | |
MD5:CF08693D6429E59278A67BFB440F30E9 | SHA256:C7D3412221FC95C2F6F3B0D7A19597BC9581E71C724C94F66BF20AD07CA30218 | |||
| 2308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2308.39664\Venom RAT + HVNC + Stealer + Grabber.exe | executable | |
MD5:3B3A304C6FC7A3A1D9390D7CBFF56634 | SHA256:7331368C01B2A16BDA0F013F376A039E6AEB4CB2DD8B0C2AFC7CA208FB544C58 | |||
| 4304 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER2F56.tmp.WERInternalMetadata.xml | xml | |
MD5:D2927235F92F2D0A36865987AB7C6BC7 | SHA256:EE541D393667424B8EF20CD85E9C5C1798AF6F84D141F933A31485C816657DBE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
50
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1516 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6044 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 131.253.33.254:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 23.207.210.196:443 | — | Akamai International B.V. | DE | unknown |
4548 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1044 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
licensing.mp.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |