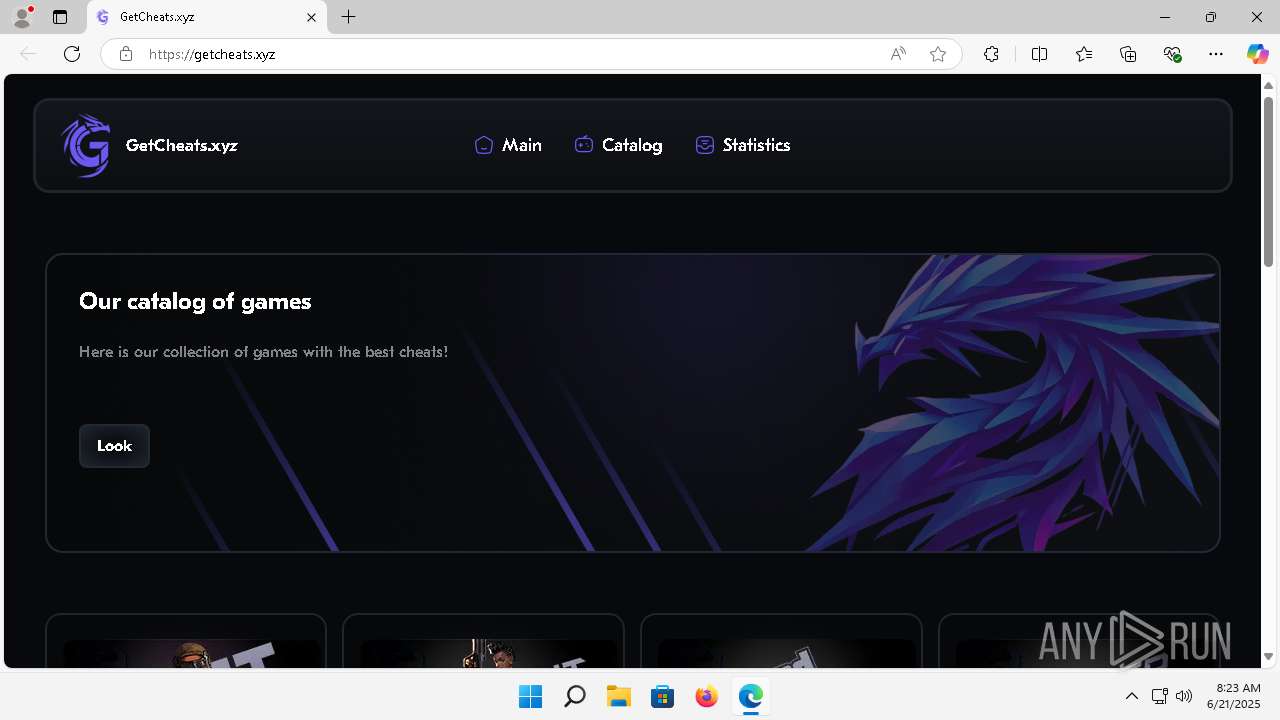
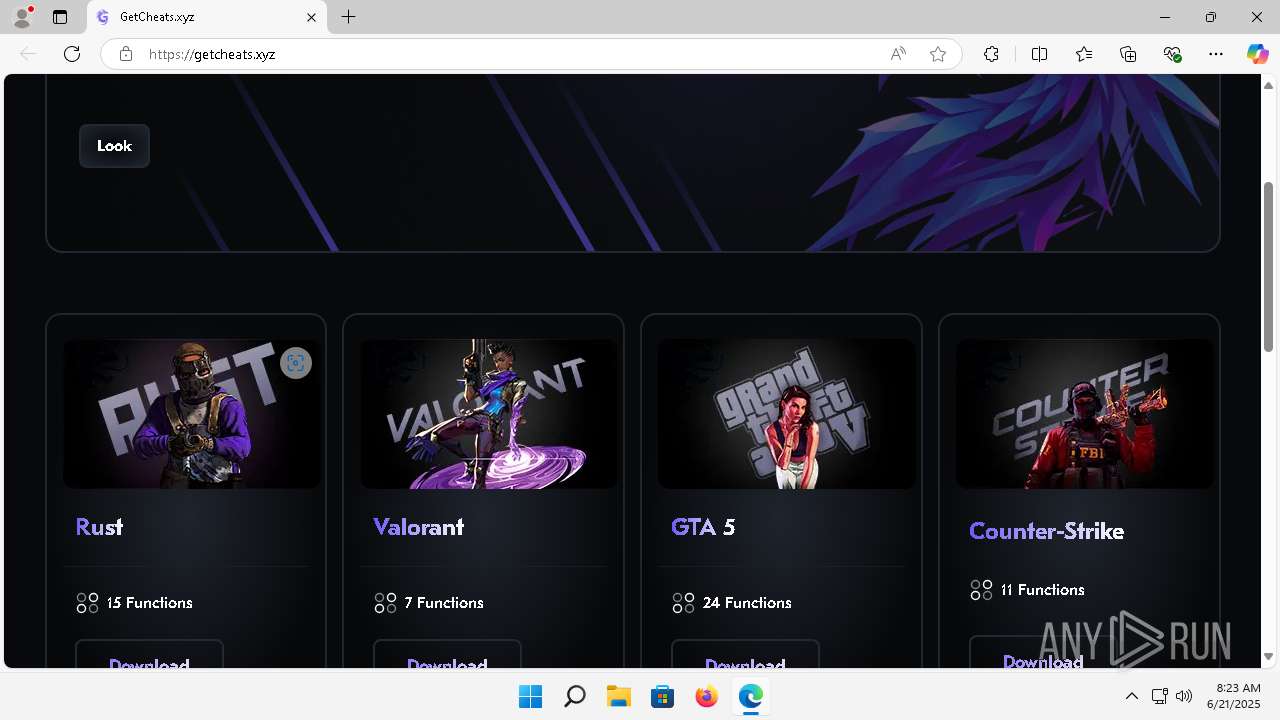
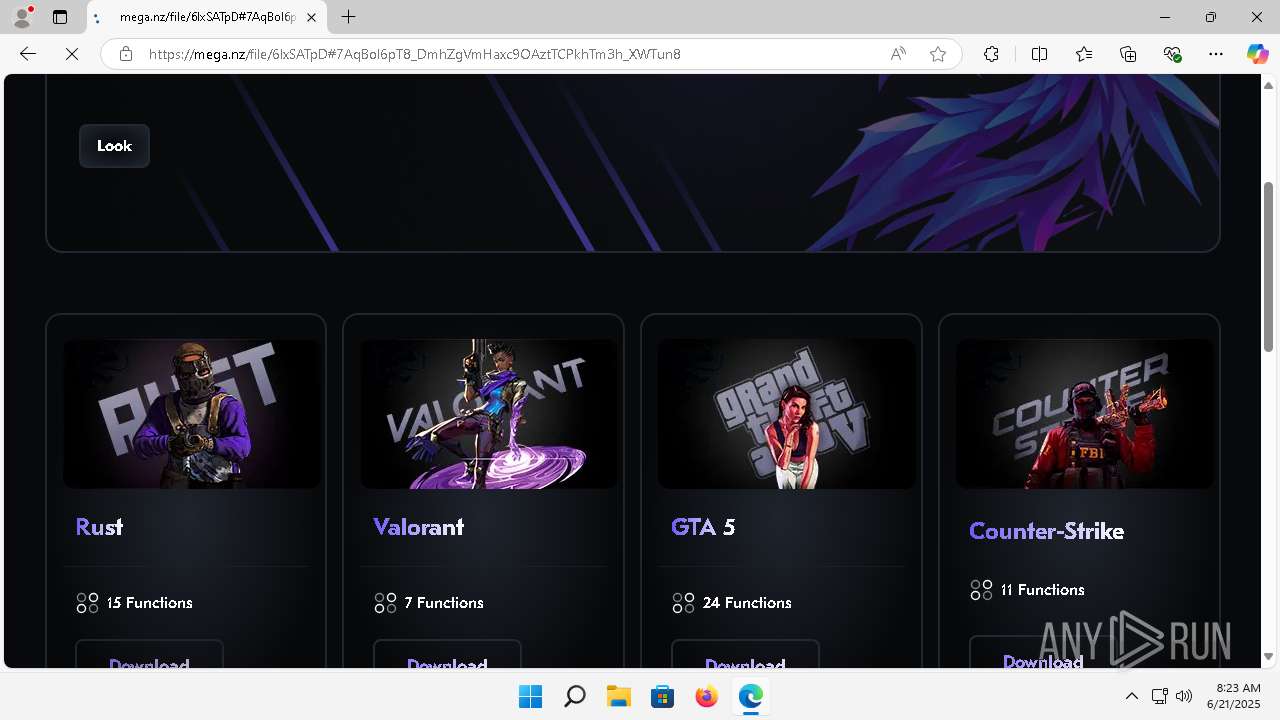
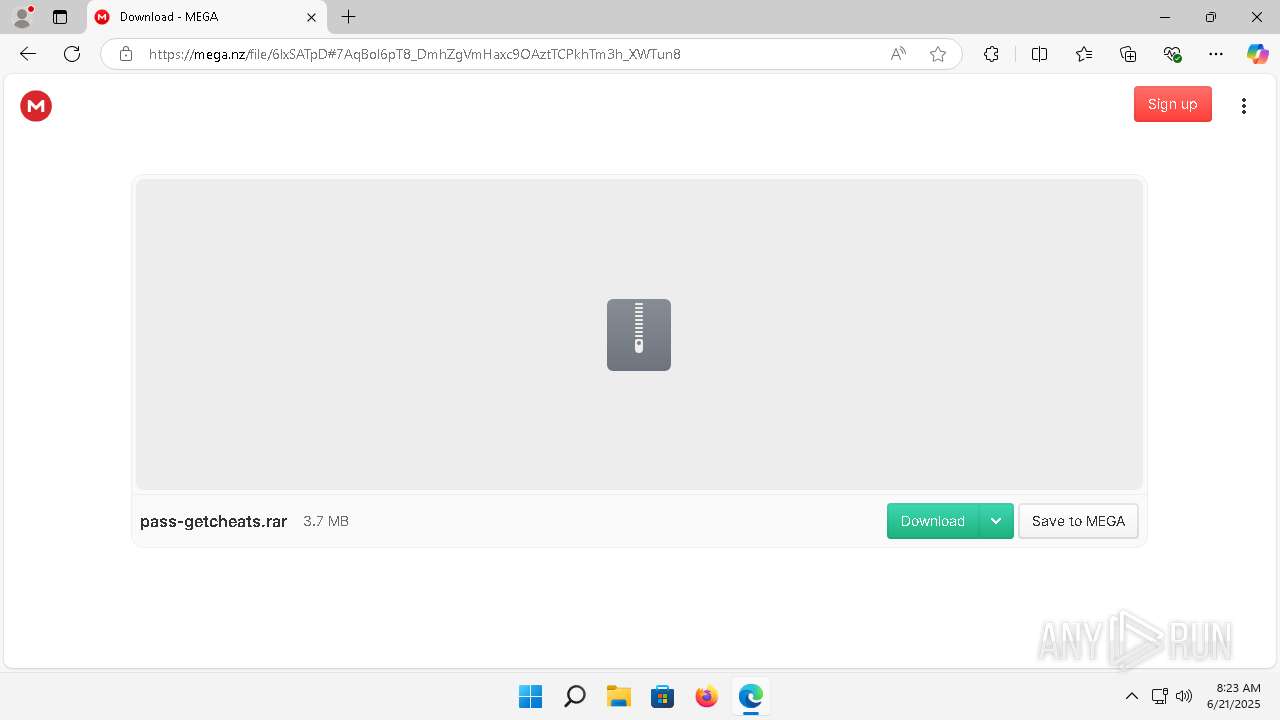
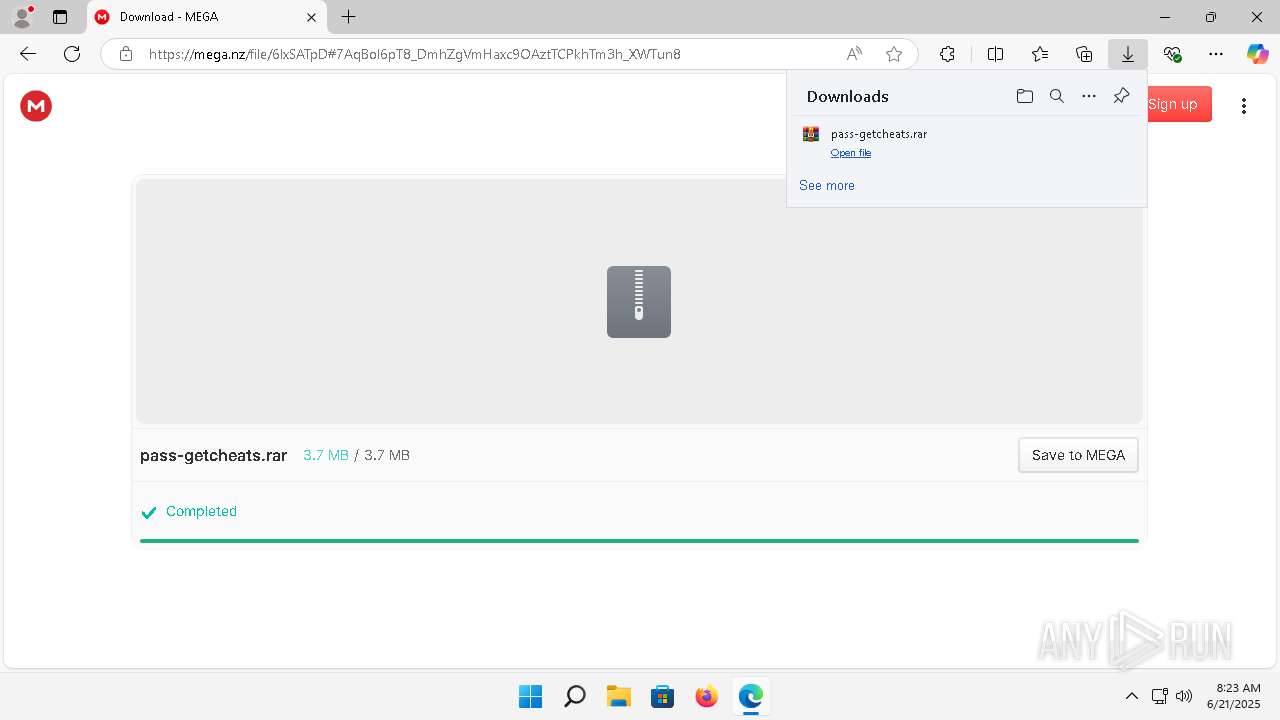
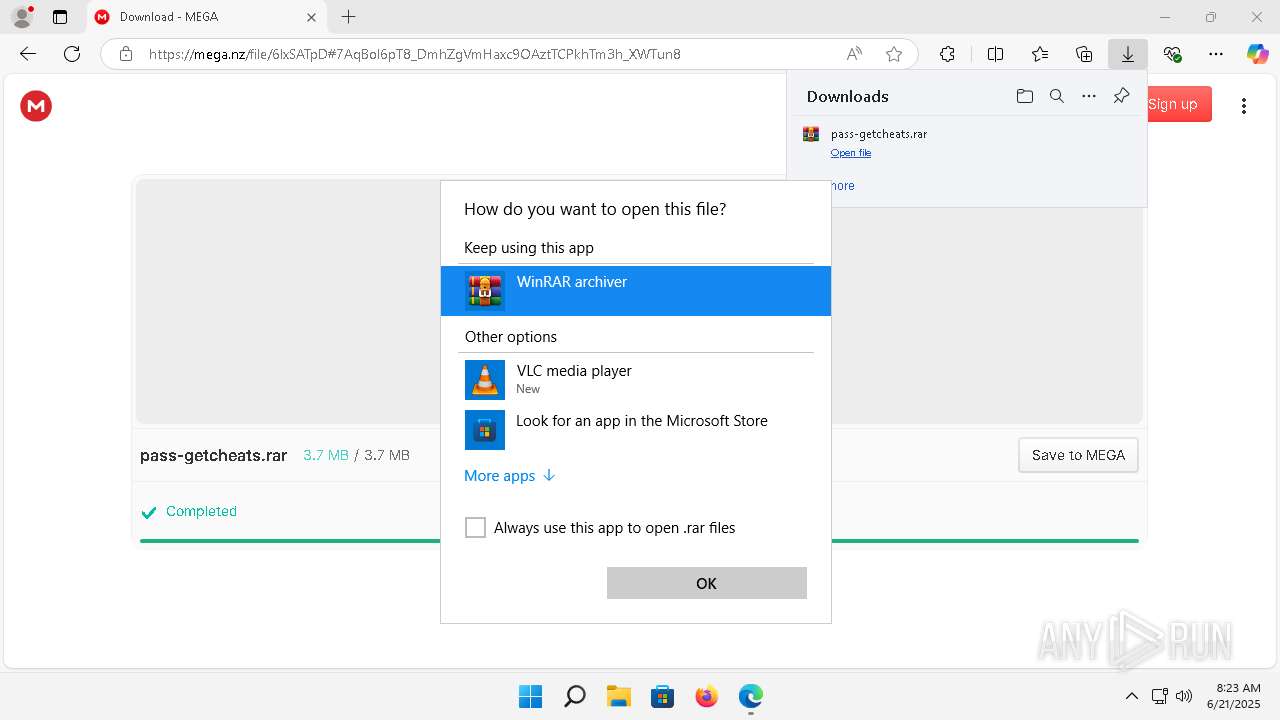
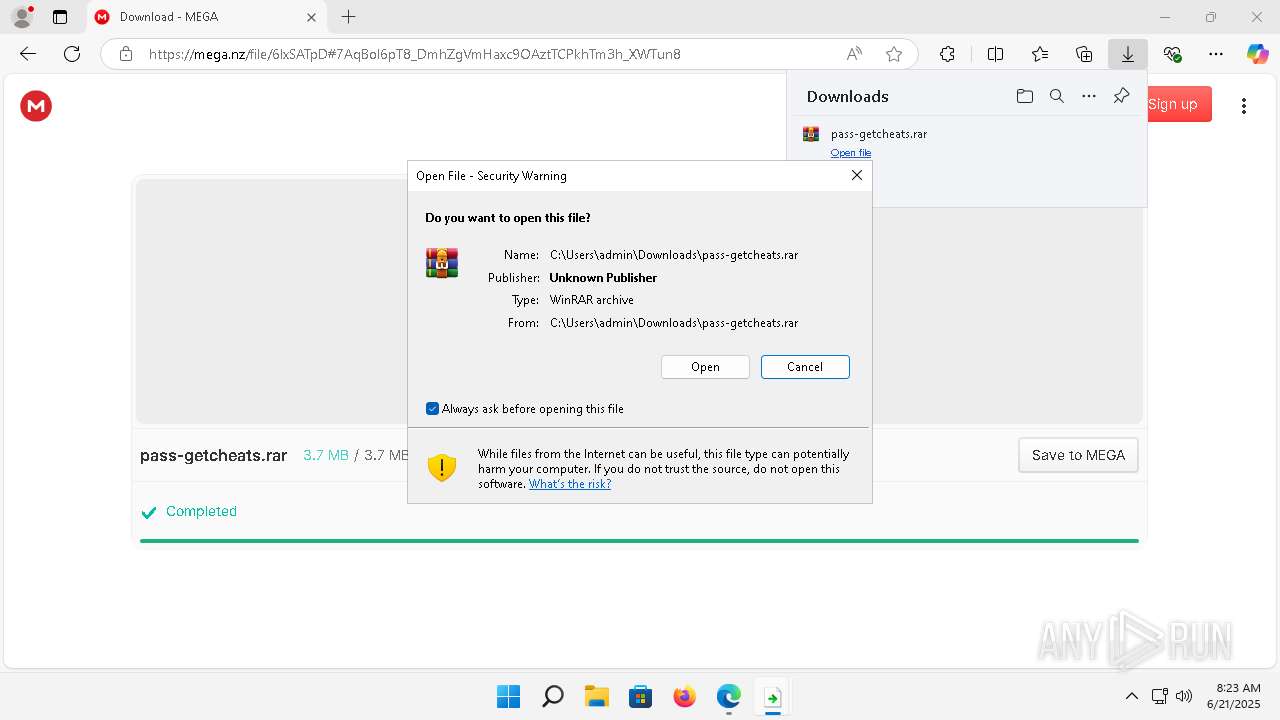
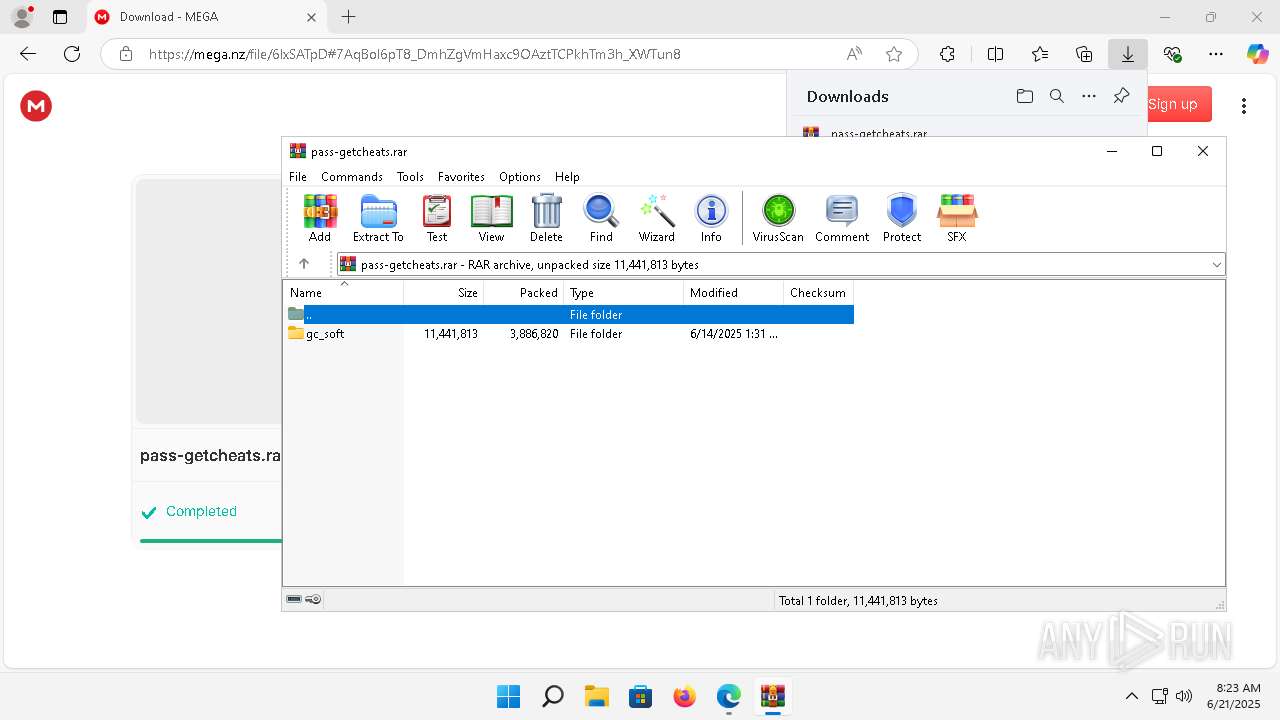
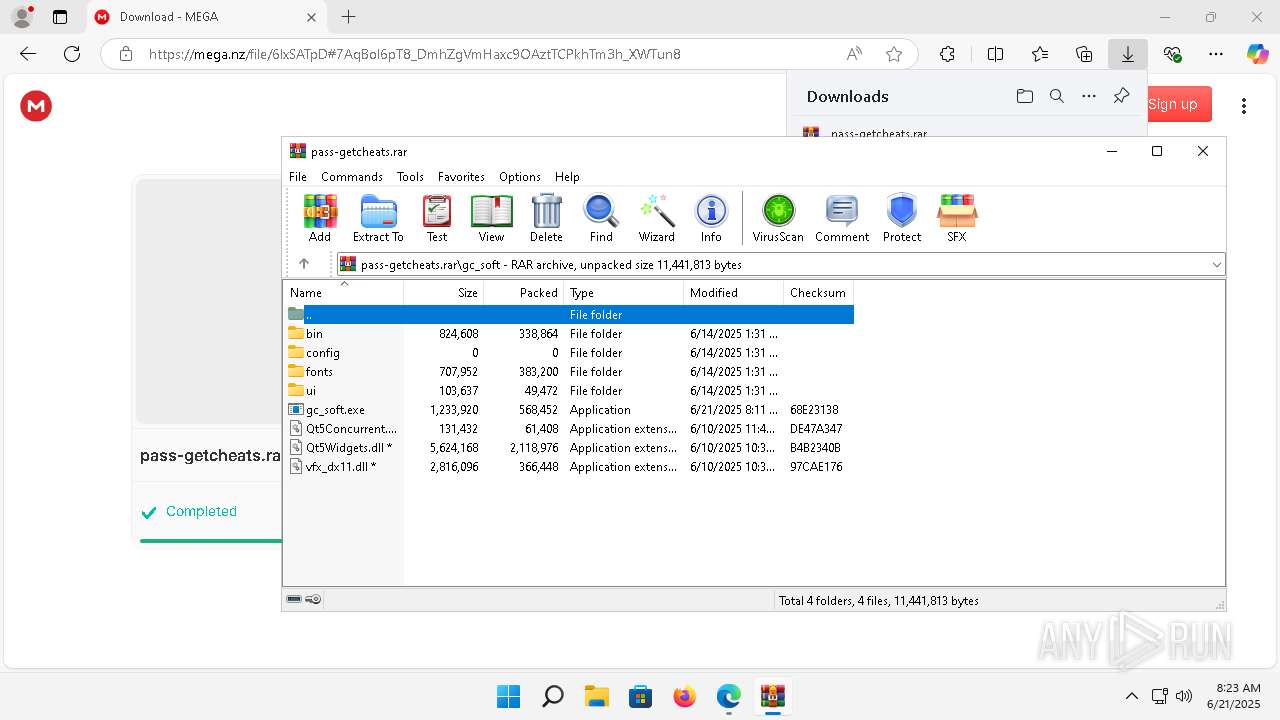
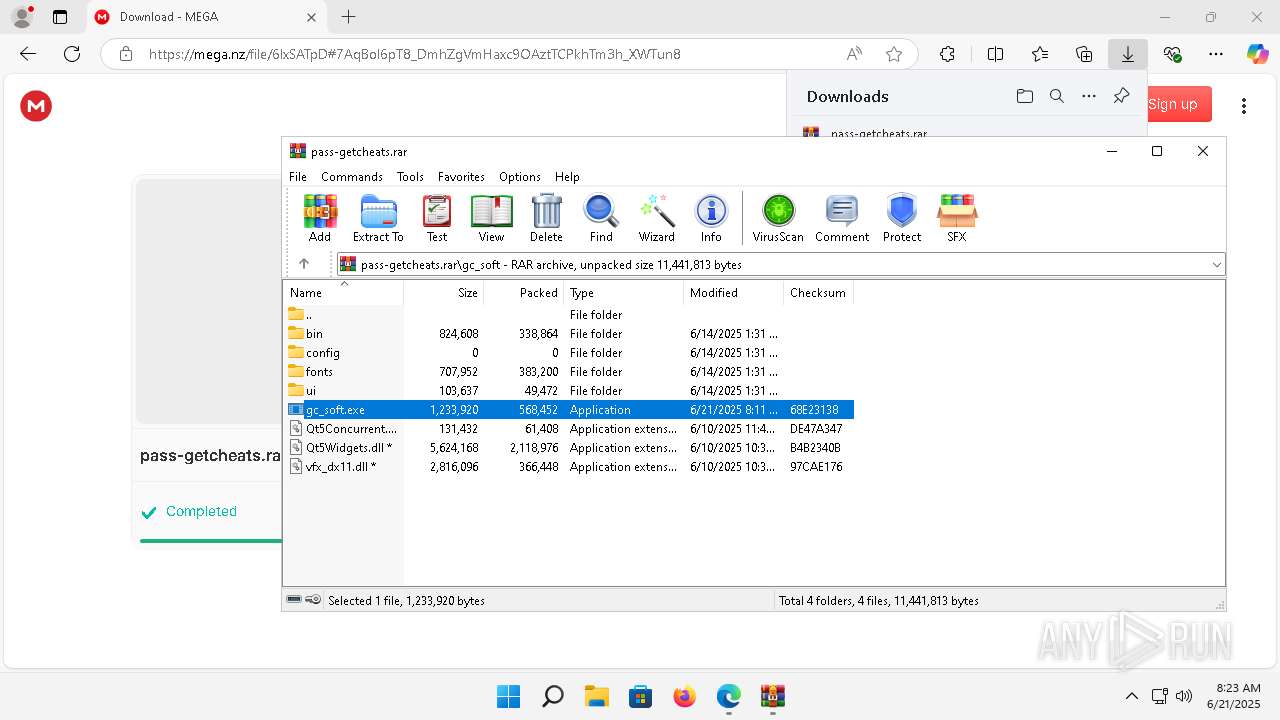
| URL: | https://getcheats.xyz |
| Full analysis: | https://app.any.run/tasks/128ce01a-fe06-41e2-bf51-30c959386c5a |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | June 21, 2025, 08:23:04 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 79CE6A51F640E44233540D80489C0A76 |
| SHA1: | 99D174ECBD80168449C65396220C00F99CBF847F |
| SHA256: | 16B438C6F37063BB583E994EF21C918815ED7B9C6D2C8CE175AFA75C16E859C4 |
| SSDEEP: | 3:N8hIHWyf:26HWyf |
MALICIOUS
LUMMA has been detected (YARA)
- MSBuild.exe (PID: 1892)
LUMMA mutex has been found
- MSBuild.exe (PID: 1892)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- MSBuild.exe (PID: 1892)
Process drops legitimate windows executable
- msedge.exe (PID: 3360)
- WinRAR.exe (PID: 2540)
Reads the Internet Settings
- OpenWith.exe (PID: 6224)
- OpenWith.exe (PID: 5072)
- MSBuild.exe (PID: 1892)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2540)
Starts a Microsoft application from unusual location
- gc_soft.exe (PID: 496)
Reads settings of System Certificates
- MSBuild.exe (PID: 1892)
INFO
Application launched itself
- msedge.exe (PID: 7972)
- msedge.exe (PID: 3360)
- chrome.exe (PID: 7612)
- chrome.exe (PID: 7196)
- chrome.exe (PID: 7628)
- msedge.exe (PID: 6452)
- chrome.exe (PID: 5932)
The sample compiled with english language support
- msedge.exe (PID: 3360)
- WinRAR.exe (PID: 2540)
Reads Microsoft Office registry keys
- msedge.exe (PID: 3360)
- OpenWith.exe (PID: 6224)
- OpenWith.exe (PID: 5072)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 6224)
- OpenWith.exe (PID: 5072)
Launching a file from the Downloads directory
- msedge.exe (PID: 3360)
Checks supported languages
- identity_helper.exe (PID: 5244)
- MSBuild.exe (PID: 1892)
- gc_soft.exe (PID: 496)
Reads Environment values
- identity_helper.exe (PID: 5244)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2540)
Reads the computer name
- MSBuild.exe (PID: 1892)
- identity_helper.exe (PID: 5244)
Reads the machine GUID from the registry
- MSBuild.exe (PID: 1892)
Reads the software policy settings
- MSBuild.exe (PID: 1892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(1892) MSBuild.exe
C2 (9)ropyi.xyz/zadf
skjgx.xyz/riuw
gewgb.xyz/axgh
baviip.xyz/twiw
equidn.xyz/xapq
spjeo.xyz/axka
firddy.xyz/yhbc
shaeb.xyz/ikxz
trqqe.xyz/xudu
Total processes
209
Monitored processes
92
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
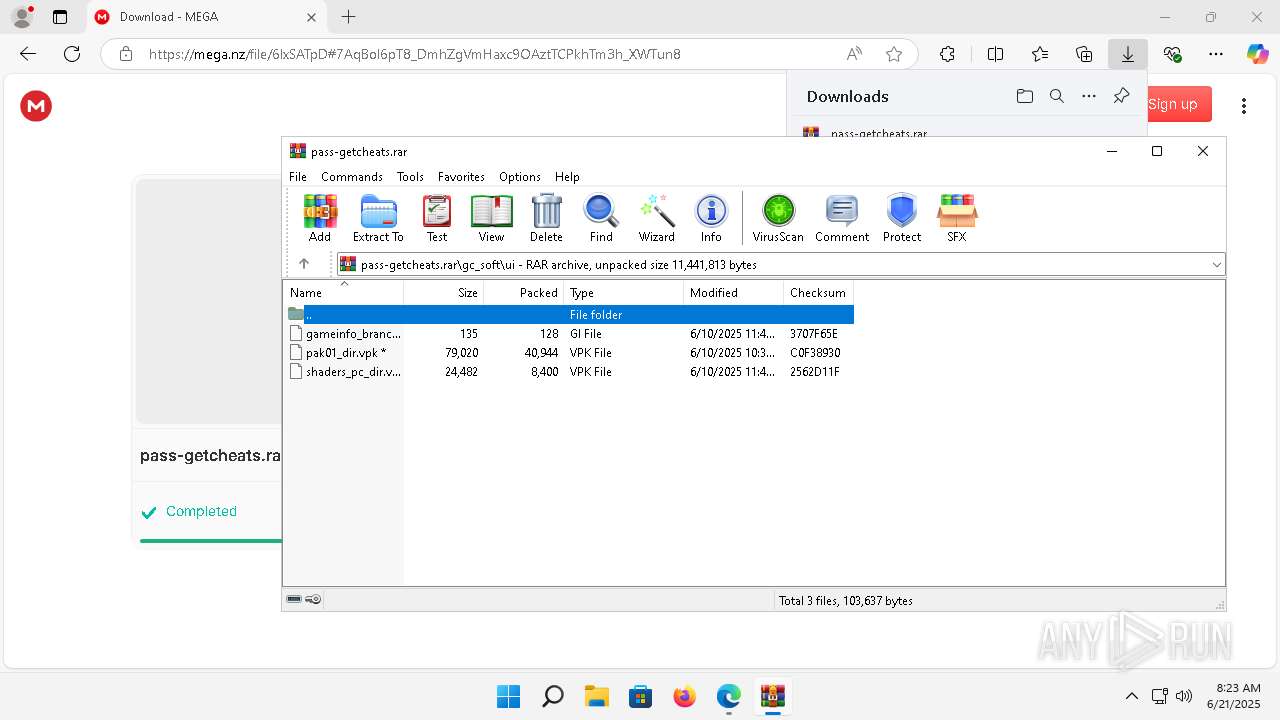
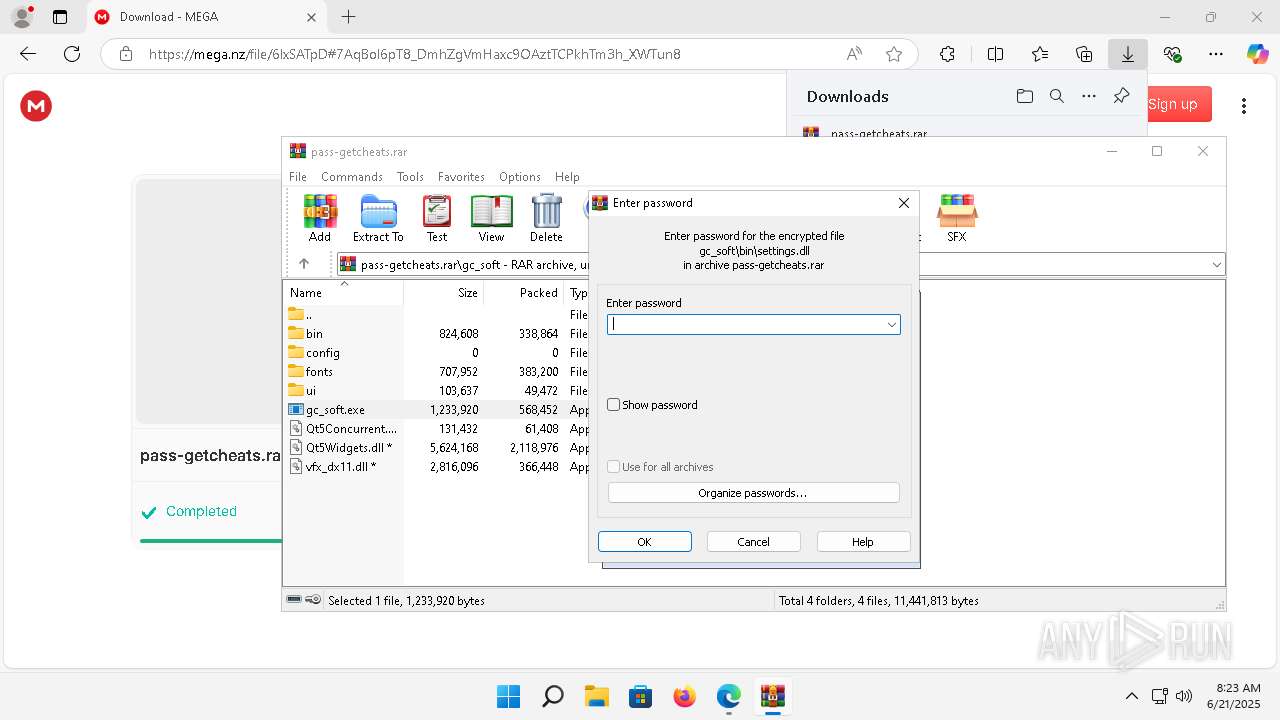
| 496 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2540.3426\gc_soft\gc_soft.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2540.3426\gc_soft\gc_soft.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Sxs Tracing Tool Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 496 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=1888,i,6211446374549328820,3744183857002937746,262144 --variations-seed-version=20250305-180124.387000 --mojo-platform-channel-handle=3316 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 134.0.6998.36 Modules
| |||||||||||||||
| 1040 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6680,i,11566028425644775127,3227100515277577570,262144 --variations-seed-version --mojo-platform-channel-handle=6728 /prefetch:12 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1140 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=1492,i,11566028425644775127,3227100515277577570,262144 --variations-seed-version --mojo-platform-channel-handle=6052 /prefetch:14 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1140 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3464,i,7198630791765825802,15104833063263963791,262144 --variations-seed-version --mojo-platform-channel-handle=3456 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1284 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=1984,i,9109911120029493129,8006765729145254785,262144 --variations-seed-version --mojo-platform-channel-handle=1980 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1436 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5776,i,11566028425644775127,3227100515277577570,262144 --variations-seed-version --mojo-platform-channel-handle=6032 /prefetch:14 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2504,i,11566028425644775127,3227100515277577570,262144 --variations-seed-version --mojo-platform-channel-handle=2564 /prefetch:13 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1548 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5996,i,11566028425644775127,3227100515277577570,262144 --variations-seed-version --mojo-platform-channel-handle=6072 /prefetch:14 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1588 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-pre-read-main-dll --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=1888,i,6211446374549328820,3744183857002937746,262144 --variations-seed-version=20250305-180124.387000 --mojo-platform-channel-handle=1980 /prefetch:2 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 134.0.6998.36 Modules
| |||||||||||||||
Total events
18 638
Read events
18 486
Write events
149
Delete events
3
Modification events
| (PID) Process: | (3728) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3728) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3728) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3728) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3728) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3728) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3728) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3728) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3728) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3728) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
Executable files
48
Suspicious files
672
Text files
303
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5932 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF13e87f.TMP | — | |
MD5:— | SHA256:— | |||
| 5932 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5932 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF13e87f.TMP | — | |
MD5:— | SHA256:— | |||
| 5932 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5932 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF13e88e.TMP | — | |
MD5:— | SHA256:— | |||
| 5932 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5932 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RF13e88e.TMP | — | |
MD5:— | SHA256:— | |||
| 5932 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF13e88e.TMP | — | |
MD5:— | SHA256:— | |||
| 5932 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5932 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF13e88e.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
219
DNS requests
203
Threats
25
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3444 | firefox.exe | POST | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
2840 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6e89692cca504d0f | unknown | — | — | whitelisted |
2840 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1726d6d8b0d81d39 | unknown | — | — | whitelisted |
4132 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1524 | svchost.exe | GET | 200 | 23.55.104.146:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
2060 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:D5ZvNx_Yi7w6wdH73HTDqrA9YSDIqPBGCi7IMJo5LSI&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2744 | chrome.exe | GET | 200 | 142.250.186.110:80 | http://clients2.google.com/time/1/current?cup2key=8:o8kAJOQwgBeNiRhZL1F4pQ_1k-hvAFuF1YRyYiMHxKY&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
7800 | chrome.exe | GET | 200 | 142.250.186.110:80 | http://clients2.google.com/time/1/current?cup2key=8:HlQI_4ylJGc-WhVSjT6nD4MakGvQDHjksmSQSMYCwRI&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
7156 | chrome.exe | GET | 200 | 142.250.186.110:80 | http://clients2.google.com/time/1/current?cup2key=8:JTqDCs0dj1aH0i90EJD8LGLZfF_zN_ypiAUJF9Lu-MU&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
5268 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751015323&P2=404&P3=2&P4=LhvwhQsjYNbPtY5oZew7%2fddCfoRXPSP7PqXjCBo9fD1yuOu7F85W9LoqcaLR%2f33iLqhtt65KkOoP4qnpmY2L%2bQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
3696 | OfficeC2RClient.exe | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
1524 | svchost.exe | 23.55.104.138:80 | — | Akamai International B.V. | US | unknown |
— | — | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
1556 | pingsender.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
3444 | firefox.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
3444 | firefox.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | unknown |
6224 | rundll32.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2860 | svchost.exe | 20.189.173.26:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
incoming.telemetry.mozilla.org |
| whitelisted |
telemetry-incoming.r53-2.services.mozilla.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
e3913.cd.akamaiedge.net |
| unknown |
google.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
getcheats.xyz |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2060 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2060 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2060 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2060 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2060 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2060 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2060 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2060 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2060 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
2060 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |