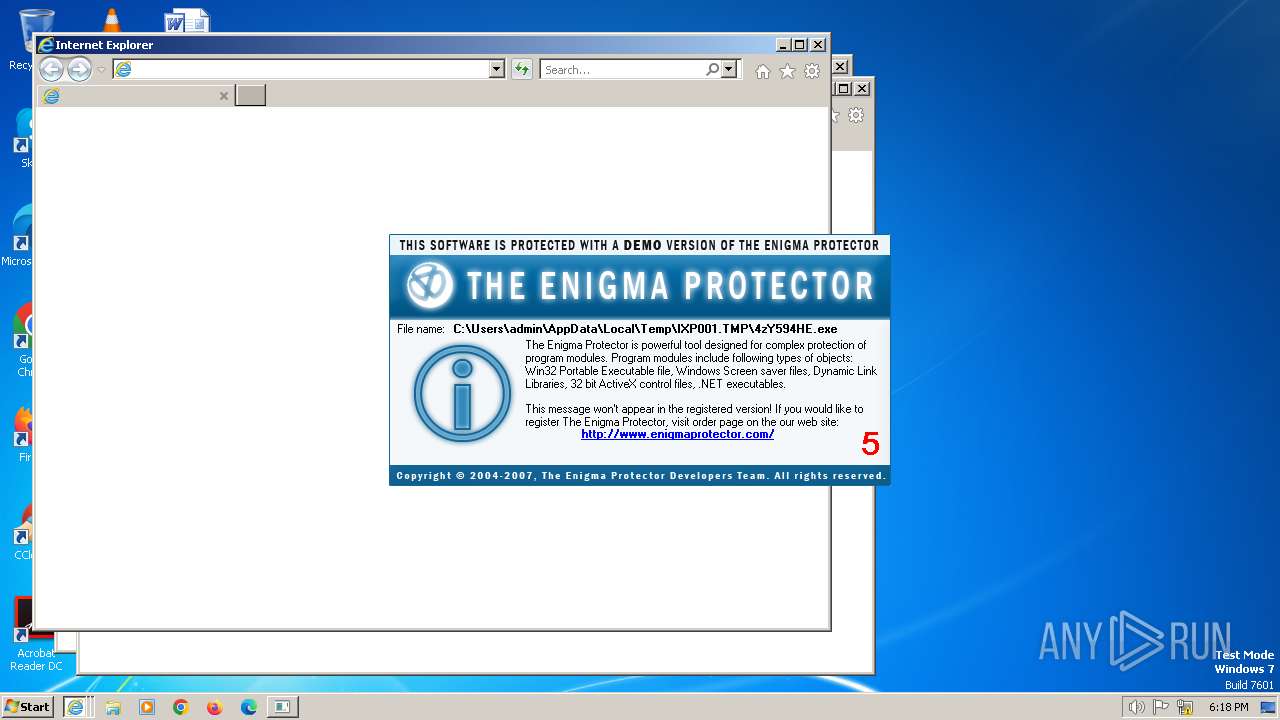
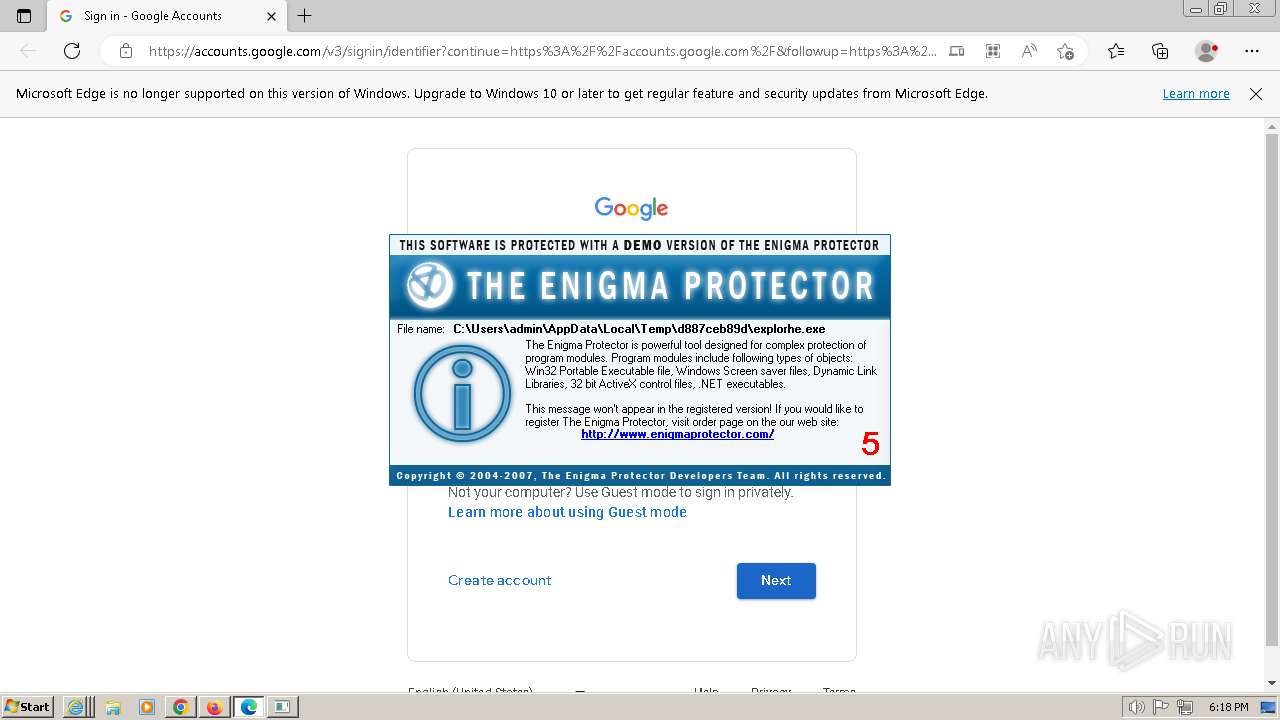
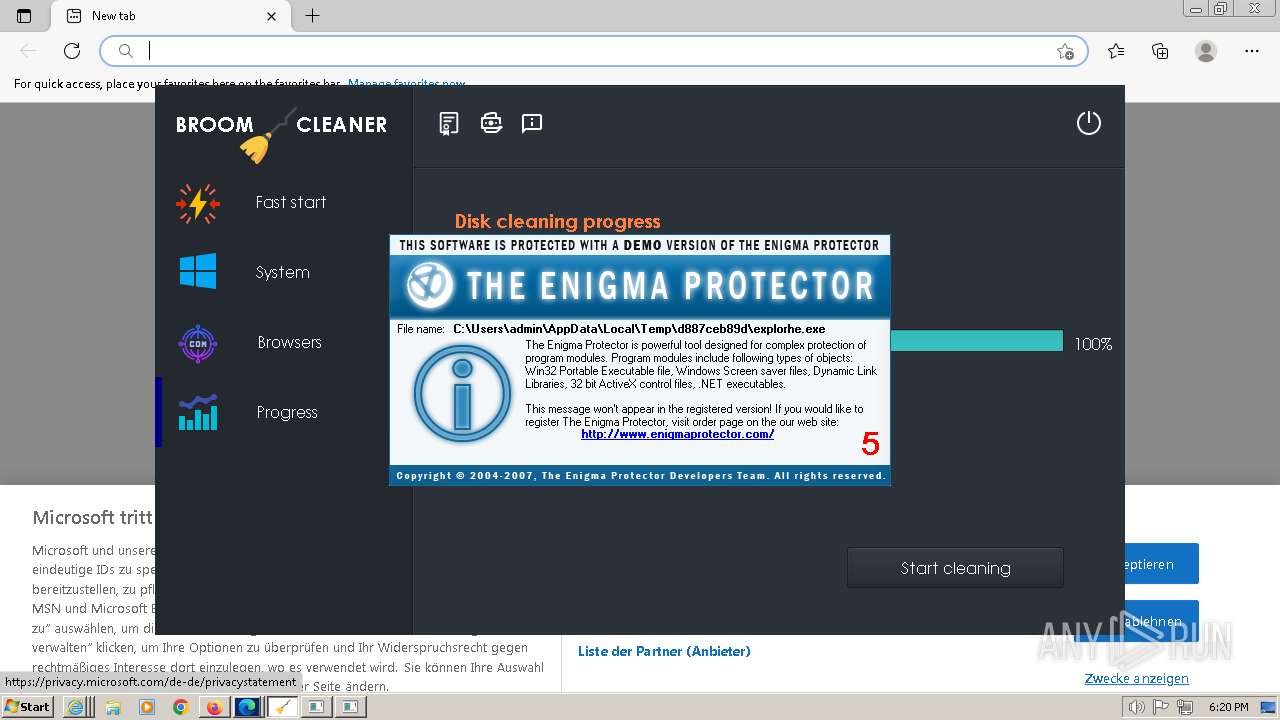
| File name: | 16959ac1a2562a4ca6895bc36a54041caa92013f82a9f2e732c729ffabee27fc.exe |
| Full analysis: | https://app.any.run/tasks/d8e1354b-4cf1-4caf-90ef-20f3120b4493 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | January 15, 2024, 18:18:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | BD05D7DC1A72D37A806C7307D38713F6 |
| SHA1: | 76ADA7A4946FD610FCDBEEEBFBB9359087B82318 |
| SHA256: | 16959AC1A2562A4CA6895BC36A54041CAA92013F82A9F2E732C729FFABEE27FC |
| SSDEEP: | 98304:xn2o4WodJOSVf5QylzU1UcfKq/STHJzlrnc2tbb70MBtQLXZ3wjgR/iOkBJwlAsv:o2M |
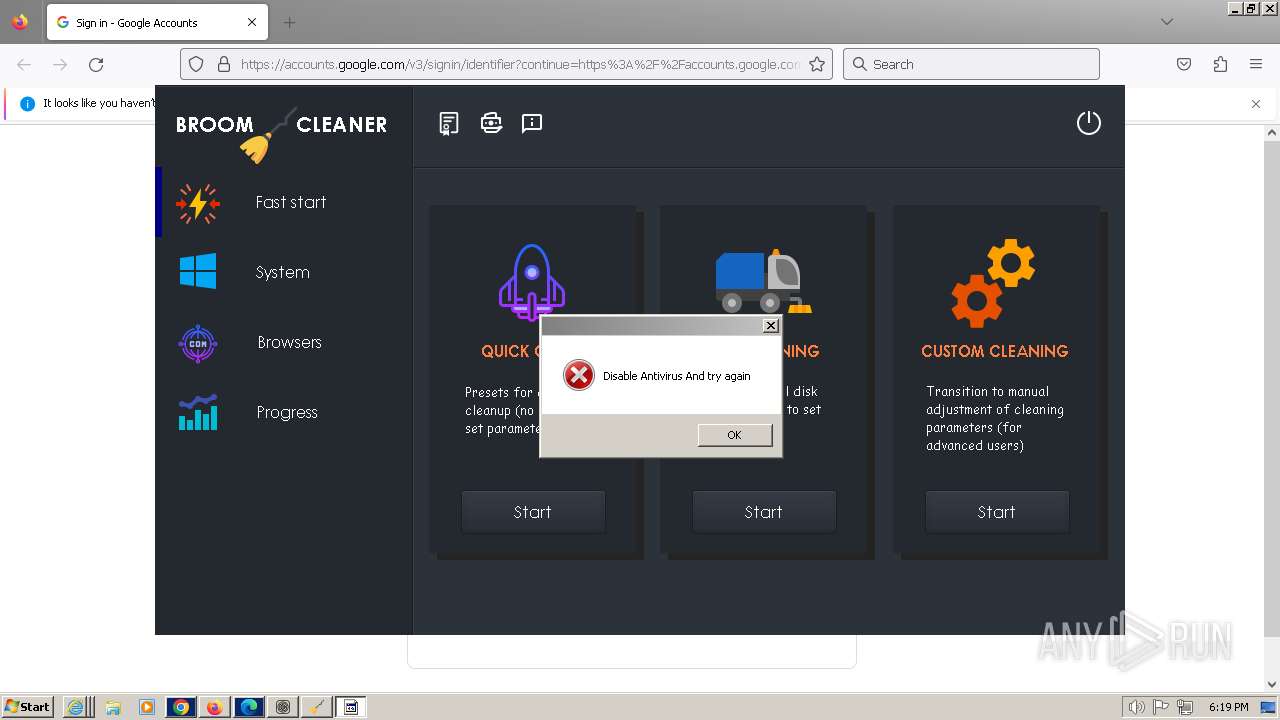
MALICIOUS
Drops the executable file immediately after the start
- Av7wm62.exe (PID: 2740)
- 4zY594HE.exe (PID: 588)
- 6lf1LQ0.exe (PID: 4424)
- explorhe.exe (PID: 4320)
- RegAsm.exe (PID: 4552)
- Miner-XMR1.exe (PID: 2240)
- iojmibhyhiws.exe (PID: 5392)
- latestrocki.exe (PID: 2020)
- InstallSetup7.exe (PID: 5228)
- boxApp.exe (PID: 2656)
- flesh.exe (PID: 4168)
- 322321.exe (PID: 6036)
- support.exe (PID: 4696)
RISEPRO has been detected (SURICATA)
- 6lf1LQ0.exe (PID: 4424)
Uses Task Scheduler to autorun other applications
- 6lf1LQ0.exe (PID: 4424)
RISEPRO has been detected (YARA)
- 6lf1LQ0.exe (PID: 4424)
- liva.exe (PID: 2860)
AMADEY has been detected (SURICATA)
- explorhe.exe (PID: 4320)
Changes the autorun value in the registry
- explorhe.exe (PID: 4320)
- reg.exe (PID: 5652)
Connects to the CnC server
- explorhe.exe (PID: 4320)
- 2024.exe (PID: 3824)
- ms_updater.exe (PID: 4396)
- RRDX.exe (PID: 4840)
- RegAsm.exe (PID: 4440)
- RegAsm.exe (PID: 5304)
- nsl510D.tmp (PID: 3276)
- rty25.exe (PID: 5616)
- jsc.exe (PID: 5540)
REDLINE has been detected (SURICATA)
- 2024.exe (PID: 3824)
- ms_updater.exe (PID: 4396)
- RRDX.exe (PID: 4840)
- RegAsm.exe (PID: 4440)
- flesh.exe (PID: 4168)
- RegAsm.exe (PID: 5304)
- jsc.exe (PID: 5540)
Steals credentials from Web Browsers
- 2024.exe (PID: 3824)
- ms_updater.exe (PID: 4396)
- flesh.exe (PID: 4168)
- RRDX.exe (PID: 4840)
- RegAsm.exe (PID: 5304)
- RegAsm.exe (PID: 4440)
- jsc.exe (PID: 5540)
REDLINE has been detected (YARA)
- 2024.exe (PID: 3824)
- ms_updater.exe (PID: 4396)
- RRDX.exe (PID: 4840)
- RegAsm.exe (PID: 4440)
- 322321.exe (PID: 6036)
- RegAsm.exe (PID: 5304)
Actions looks like stealing of personal data
- 2024.exe (PID: 3824)
- ms_updater.exe (PID: 4396)
- flesh.exe (PID: 4168)
- rty25.exe (PID: 5616)
- RegAsm.exe (PID: 4440)
- RRDX.exe (PID: 4840)
- RegAsm.exe (PID: 5304)
- jsc.exe (PID: 5540)
Unusual connection from system programs
- rundll32.exe (PID: 5452)
KELIHOS has been detected (SURICATA)
- explorhe.exe (PID: 4320)
STEALC has been detected (SURICATA)
- nsl510D.tmp (PID: 3276)
FABOOKIE has been detected (SURICATA)
- rty25.exe (PID: 5616)
SUSPICIOUS
Executable content was dropped or overwritten
- Av7wm62.exe (PID: 2740)
- 16959ac1a2562a4ca6895bc36a54041caa92013f82a9f2e732c729ffabee27fc.exe (PID: 2936)
- 4zY594HE.exe (PID: 588)
- 6lf1LQ0.exe (PID: 4424)
- explorhe.exe (PID: 4320)
- RegAsm.exe (PID: 4552)
- Miner-XMR1.exe (PID: 2240)
- iojmibhyhiws.exe (PID: 5392)
- latestrocki.exe (PID: 2020)
- InstallSetup7.exe (PID: 5228)
- boxApp.exe (PID: 2656)
- flesh.exe (PID: 4168)
- 322321.exe (PID: 6036)
- support.exe (PID: 4696)
Reads the Internet Settings
- 1Xd45Zd4.exe (PID: 3028)
- 4zY594HE.exe (PID: 588)
- explorhe.exe (PID: 4320)
- RegAsm.exe (PID: 4552)
- 2024.exe (PID: 3824)
- rundll32.exe (PID: 5452)
- ms_updater.exe (PID: 4396)
- latestrocki.exe (PID: 2020)
- rty25.exe (PID: 3088)
- InstallSetup7.exe (PID: 5228)
- rty25.exe (PID: 5616)
- nsl510D.tmp (PID: 3276)
- RegAsm.exe (PID: 4440)
- RRDX.exe (PID: 4840)
- RegAsm.exe (PID: 5304)
- jsc.exe (PID: 5540)
Connects to unusual port
- 6lf1LQ0.exe (PID: 4424)
- 2024.exe (PID: 3824)
- ms_updater.exe (PID: 4396)
- RRDX.exe (PID: 4840)
- RegAsm.exe (PID: 4440)
- flesh.exe (PID: 4168)
- RegAsm.exe (PID: 5304)
- jsc.exe (PID: 5540)
Checks for external IP
- 6lf1LQ0.exe (PID: 4424)
Reads settings of System Certificates
- 6lf1LQ0.exe (PID: 4424)
- explorhe.exe (PID: 4320)
- rty25.exe (PID: 3088)
- rty25.exe (PID: 5616)
Connects to the server without a host name
- explorhe.exe (PID: 4320)
- InstallSetup7.exe (PID: 5228)
- nsl510D.tmp (PID: 3276)
Checks Windows Trust Settings
- explorhe.exe (PID: 4320)
- rty25.exe (PID: 3088)
- rty25.exe (PID: 5616)
Reads security settings of Internet Explorer
- explorhe.exe (PID: 4320)
- rty25.exe (PID: 3088)
- rty25.exe (PID: 5616)
Adds/modifies Windows certificates
- explorhe.exe (PID: 4320)
- rty25.exe (PID: 5616)
Process requests binary or script from the Internet
- explorhe.exe (PID: 4320)
- InstallSetup7.exe (PID: 5228)
Searches for installed software
- 2024.exe (PID: 3824)
- ms_updater.exe (PID: 4396)
- flesh.exe (PID: 4168)
- RRDX.exe (PID: 4840)
- RegAsm.exe (PID: 5304)
- RegAsm.exe (PID: 4440)
- jsc.exe (PID: 5540)
Uses REG/REGEDIT.EXE to modify registry
- Miner-XMR1.exe (PID: 2240)
- iojmibhyhiws.exe (PID: 5392)
Reads the BIOS version
- Miner-XMR1.exe (PID: 2240)
- iojmibhyhiws.exe (PID: 5392)
Starts CMD.EXE for commands execution
- Miner-XMR1.exe (PID: 2240)
- BroomSetup.exe (PID: 3244)
Reads browser cookies
- ms_updater.exe (PID: 4396)
- 2024.exe (PID: 3824)
- flesh.exe (PID: 4168)
- RegAsm.exe (PID: 4440)
- RegAsm.exe (PID: 5304)
- RRDX.exe (PID: 4840)
- jsc.exe (PID: 5540)
Drops a system driver (possible attempt to evade defenses)
- iojmibhyhiws.exe (PID: 5392)
Starts application with an unusual extension
- InstallSetup7.exe (PID: 5228)
- cmd.exe (PID: 5872)
Executing commands from a ".bat" file
- BroomSetup.exe (PID: 3244)
Process drops legitimate windows executable
- 322321.exe (PID: 6036)
INFO
Checks supported languages
- 16959ac1a2562a4ca6895bc36a54041caa92013f82a9f2e732c729ffabee27fc.exe (PID: 2936)
- Av7wm62.exe (PID: 2740)
- 1Xd45Zd4.exe (PID: 3028)
- 4zY594HE.exe (PID: 588)
- 6lf1LQ0.exe (PID: 4424)
- explorhe.exe (PID: 4320)
- boxApp.exe (PID: 2656)
- 2024.exe (PID: 3824)
- cryptedpixel.exe (PID: 4288)
- RegAsm.exe (PID: 4552)
- ms_updater.exe (PID: 4396)
- Miner-XMR1.exe (PID: 2240)
- iojmibhyhiws.exe (PID: 5392)
- latestrocki.exe (PID: 2020)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 5476)
- RRDX.exe (PID: 4840)
- BroomSetup.exe (PID: 3244)
- InstallSetup7.exe (PID: 5228)
- rty25.exe (PID: 3088)
- autorun.exe (PID: 5108)
- RegAsm.exe (PID: 4440)
- nsl510D.tmp (PID: 3276)
- support.exe (PID: 4696)
- flesh.exe (PID: 4168)
- MSBuild.exe (PID: 1436)
- RegAsm.exe (PID: 5304)
- rty25.exe (PID: 5616)
- gold.exe (PID: 4764)
- chcp.com (PID: 4000)
- 322321.exe (PID: 6036)
- liva.exe (PID: 2860)
- zona.exe (PID: 712)
- jsc.exe (PID: 5540)
- MSBuild.exe (PID: 3108)
- explorhe.exe (PID: 3260)
Drops the executable file immediately after the start
- 16959ac1a2562a4ca6895bc36a54041caa92013f82a9f2e732c729ffabee27fc.exe (PID: 2936)
- firefox.exe (PID: 3024)
Application launched itself
- chrome.exe (PID: 2524)
- firefox.exe (PID: 3024)
- msedge.exe (PID: 2600)
- chrome.exe (PID: 2900)
- msedge.exe (PID: 3716)
- chrome.exe (PID: 5848)
- rty25.exe (PID: 3088)
- chrome.exe (PID: 1560)
- msedge.exe (PID: 4544)
- chrome.exe (PID: 5088)
- chrome.exe (PID: 2484)
- msedge.exe (PID: 2932)
- msedge.exe (PID: 1096)
- msedge.exe (PID: 5204)
- chrome.exe (PID: 3316)
Reads mouse settings
- 1Xd45Zd4.exe (PID: 3028)
Reads the computer name
- 1Xd45Zd4.exe (PID: 3028)
- 4zY594HE.exe (PID: 588)
- 6lf1LQ0.exe (PID: 4424)
- explorhe.exe (PID: 4320)
- 2024.exe (PID: 3824)
- boxApp.exe (PID: 2656)
- cryptedpixel.exe (PID: 4288)
- RegAsm.exe (PID: 4552)
- ms_updater.exe (PID: 4396)
- latestrocki.exe (PID: 2020)
- InstallSetup7.exe (PID: 5228)
- rty25.exe (PID: 3088)
- BroomSetup.exe (PID: 3244)
- RRDX.exe (PID: 4840)
- support.exe (PID: 4696)
- autorun.exe (PID: 5108)
- RegAsm.exe (PID: 4440)
- flesh.exe (PID: 4168)
- RegAsm.exe (PID: 5304)
- rty25.exe (PID: 5616)
- gold.exe (PID: 4764)
- nsl510D.tmp (PID: 3276)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 5476)
- jsc.exe (PID: 5540)
Create files in a temporary directory
- 4zY594HE.exe (PID: 588)
- 6lf1LQ0.exe (PID: 4424)
- explorhe.exe (PID: 4320)
- iojmibhyhiws.exe (PID: 5392)
- Av7wm62.exe (PID: 2740)
- 16959ac1a2562a4ca6895bc36a54041caa92013f82a9f2e732c729ffabee27fc.exe (PID: 2936)
- latestrocki.exe (PID: 2020)
- InstallSetup7.exe (PID: 5228)
- boxApp.exe (PID: 2656)
- flesh.exe (PID: 4168)
- support.exe (PID: 4696)
Starts itself from another location
- 4zY594HE.exe (PID: 588)
- Miner-XMR1.exe (PID: 2240)
Reads the machine GUID from the registry
- 4zY594HE.exe (PID: 588)
- 6lf1LQ0.exe (PID: 4424)
- explorhe.exe (PID: 4320)
- 2024.exe (PID: 3824)
- ms_updater.exe (PID: 4396)
- latestrocki.exe (PID: 2020)
- rty25.exe (PID: 3088)
- RRDX.exe (PID: 4840)
- InstallSetup7.exe (PID: 5228)
- boxApp.exe (PID: 2656)
- RegAsm.exe (PID: 4440)
- flesh.exe (PID: 4168)
- rty25.exe (PID: 5616)
- RegAsm.exe (PID: 5304)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 5476)
- nsl510D.tmp (PID: 3276)
- jsc.exe (PID: 5540)
- support.exe (PID: 4696)
Creates files or folders in the user directory
- 6lf1LQ0.exe (PID: 4424)
- explorhe.exe (PID: 4320)
- RegAsm.exe (PID: 4552)
- Miner-XMR1.exe (PID: 2240)
- InstallSetup7.exe (PID: 5228)
- rty25.exe (PID: 3088)
- BroomSetup.exe (PID: 3244)
- rty25.exe (PID: 5616)
Creates files in the program directory
- 6lf1LQ0.exe (PID: 4424)
Checks proxy server information
- explorhe.exe (PID: 4320)
- rundll32.exe (PID: 5452)
- rty25.exe (PID: 3088)
- InstallSetup7.exe (PID: 5228)
- rty25.exe (PID: 5616)
- nsl510D.tmp (PID: 3276)
Reads Environment values
- 2024.exe (PID: 3824)
- ms_updater.exe (PID: 4396)
- RRDX.exe (PID: 4840)
- RegAsm.exe (PID: 4440)
- flesh.exe (PID: 4168)
- RegAsm.exe (PID: 5304)
- jsc.exe (PID: 5540)
Executable content was dropped or overwritten
- firefox.exe (PID: 3024)
Process drops legitimate windows executable
- 16959ac1a2562a4ca6895bc36a54041caa92013f82a9f2e732c729ffabee27fc.exe (PID: 2936)
The process executes via Task Scheduler
- explorhe.exe (PID: 3260)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(3824) 2024.exe
C2 (1)195.20.16.103:20440
Botnet2024
Options
ErrorMessage
Keys
XorSitfast
(PID) Process(4396) ms_updater.exe
C2 (1)91.92.240.231:13781
Botnet@Pixelscloud
Options
ErrorMessage
Keys
XorVillan
(PID) Process(4840) RRDX.exe
C2 (1)141.95.211.148:46011
Botnet@RLREBORN Cloud (TG: @FATHEROFCARDERS)
Options
ErrorMessageERROR RDX
Keys
XorSuboxide
(PID) Process(4440) RegAsm.exe
C2 (1)194.33.191.102:21751
BotnetBloomberg
Options
ErrorMessage
Keys
XorVermal
(PID) Process(6036) 322321.exe
C2 (1)185.172.128.33:38294
BotnetLegaa
Options
ErrorMessage
Keys
XorBudge
(PID) Process(5304) RegAsm.exe
C2 (1)20.79.30.95:33223
BotnetLiveTraffic
Version1
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:05:25 00:49:06+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.13 |
| CodeSize: | 25600 |
| InitializedDataSize: | 2554368 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a60 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.17763.1 |
| ProductVersionNumber: | 11.0.17763.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 Cabinet Self-Extractor |
| FileVersion: | 11.00.17763.1 (WinBuild.160101.0800) |
| InternalName: | Wextract |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | WEXTRACT.EXE .MUI |
| ProductName: | Internet Explorer |
| ProductVersion: | 11.00.17763.1 |
Total processes
230
Monitored processes
188
Malicious processes
30
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 244 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=2064 --field-trial-handle=1228,i,7608605005918423292,5233907281314657698,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 272 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0x138,0x13c,0x140,0x10c,0x144,0x7fef2c46b58,0x7fef2c46b68,0x7fef2c46b78 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 552 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2812 --field-trial-handle=1364,i,17525001413387694274,14029964247201294611,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 576 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1588 --field-trial-handle=1216,i,14209033223497061160,17334912501977404252,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 588 | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\4zY594HE.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\4zY594HE.exe | Av7wm62.exe | ||||||||||||
User: admin Company: The Enigma Protector Developers Team Integrity Level: MEDIUM Description: Software Protection Tool Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 624 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0x138,0x13c,0x140,0x10c,0x144,0x7fef23a6b58,0x7fef23a6b68,0x7fef23a6b78 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 684 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2520 --field-trial-handle=1440,i,12987927636963181326,3312507942806198110,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 712 | "C:\Users\admin\AppData\Local\Temp\1000320001\zona.exe" | C:\Users\admin\AppData\Local\Temp\1000320001\zona.exe | — | explorhe.exe | |||||||||||
User: admin Company: The Enigma Protector Developers Team Integrity Level: MEDIUM Description: Software Protection Tool Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 892 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3748 --field-trial-handle=1172,i,11801498847852958215,7801817719413349297,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 980 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1176 --field-trial-handle=1232,i,6490621556834321831,7379139877224367074,131072 /prefetch:2 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
48 199
Read events
47 474
Write events
645
Delete events
80
Modification events
| (PID) Process: | (3028) 1Xd45Zd4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3028) 1Xd45Zd4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3028) 1Xd45Zd4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3028) 1Xd45Zd4.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 5 | |||
| (PID) Process: | (2000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 91676960 | |||
| (PID) Process: | (2000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31049115 | |||
| (PID) Process: | (2000) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31049165 | |||
| (PID) Process: | (2600) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2600) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
Executable files
64
Suspicious files
887
Text files
441
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2524 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF108772.TMP | — | |
MD5:— | SHA256:— | |||
| 2524 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2936 | 16959ac1a2562a4ca6895bc36a54041caa92013f82a9f2e732c729ffabee27fc.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\Av7wm62.exe | executable | |
MD5:CD03DD553D27B55F12EA9D3DBB5B1B79 | SHA256:3DF31BC4B914119D1668BFF79E2CB471C8C0B7FBEB8460E007140AE2F3D6AA07 | |||
| 2524 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 2600 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:B54C9C06FE96D186D5B7093D521FCBB4 | SHA256:0F91AAD9EEC81442CB66E4CE922D296DB730D24F85A140BD612A630F3F7F7D9B | |||
| 2524 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C7925A6B262C5676D1C36638981A6EA | SHA256:07F6FB1E9CBCE4D15C00A9FBF9A95C1F31DE20C4C48B433198862E8759CD128D | |||
| 2600 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF108aec.TMP | — | |
MD5:— | SHA256:— | |||
| 2600 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2740 | Av7wm62.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\4zY594HE.exe | executable | |
MD5:F2D3892701E7FDAA25EA422CEFBEA696 | SHA256:BB3AF81C2A433A521BAC9F26F52E4C45063FB36A45A322C930CB24B027559BE2 | |||
| 2524 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
64
TCP/UDP connections
279
DNS requests
350
Threats
248
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4320 | explorhe.exe | GET | 200 | 184.24.77.207:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?94da68134d876079 | unknown | compressed | 65.2 Kb | unknown |
4320 | explorhe.exe | POST | 200 | 185.215.113.68:80 | http://185.215.113.68/theme/index.php | unknown | text | 2 b | unknown |
4320 | explorhe.exe | POST | 200 | 185.215.113.68:80 | http://185.215.113.68/theme/index.php | unknown | text | 1.26 Kb | unknown |
4320 | explorhe.exe | POST | 200 | 185.215.113.68:80 | http://185.215.113.68/theme/index.php | unknown | text | 4 b | unknown |
4320 | explorhe.exe | POST | 200 | 185.215.113.68:80 | http://185.215.113.68/theme/index.php | unknown | text | 4 b | unknown |
4320 | explorhe.exe | POST | 200 | 185.215.113.68:80 | http://185.215.113.68/theme/index.php | unknown | text | 4 b | unknown |
4320 | explorhe.exe | GET | 404 | 185.215.113.68:80 | http://185.215.113.68/theme/Plugins/cred64.dll | unknown | html | 162 b | unknown |
3024 | firefox.exe | POST | 200 | 2.16.2.73:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3024 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
3024 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
352 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1220 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1112 | iexplore.exe | 142.250.110.84:443 | accounts.google.com | GOOGLE | US | unknown |
2524 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1492 | iexplore.exe | 172.217.18.110:443 | www.youtube.com | GOOGLE | US | whitelisted |
1928 | iexplore.exe | 157.240.0.35:443 | www.facebook.com | FACEBOOK | US | unknown |
2368 | chrome.exe | 142.250.185.132:443 | www.google.com | GOOGLE | US | whitelisted |
2368 | chrome.exe | 142.250.185.131:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2368 | chrome.exe | 142.250.110.84:443 | accounts.google.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
www.youtube.com |
| whitelisted |
www.facebook.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.com |
| whitelisted |
static.xx.fbcdn.net |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
facebook.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4424 | 6lf1LQ0.exe | A Network Trojan was detected | ET MALWARE RisePro TCP Heartbeat Packet |
4424 | 6lf1LQ0.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] RisePro TCP (Token) |
4424 | 6lf1LQ0.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] RisePro TCP (Token) |
4424 | 6lf1LQ0.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
4424 | 6lf1LQ0.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] RisePro TCP (get_settings) |
4320 | explorhe.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 22 |
4320 | explorhe.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey |
4320 | explorhe.exe | A Network Trojan was detected | ET MALWARE Win32/Amadey Host Fingerprint Exfil (POST) M2 |
3824 | 2024.exe | Potentially Bad Traffic | ET INFO Microsoft net.tcp Connection Initialization Activity |
3824 | 2024.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
6lf1LQ0.exe | 4443436 |
6lf1LQ0.exe | gdry4645 |