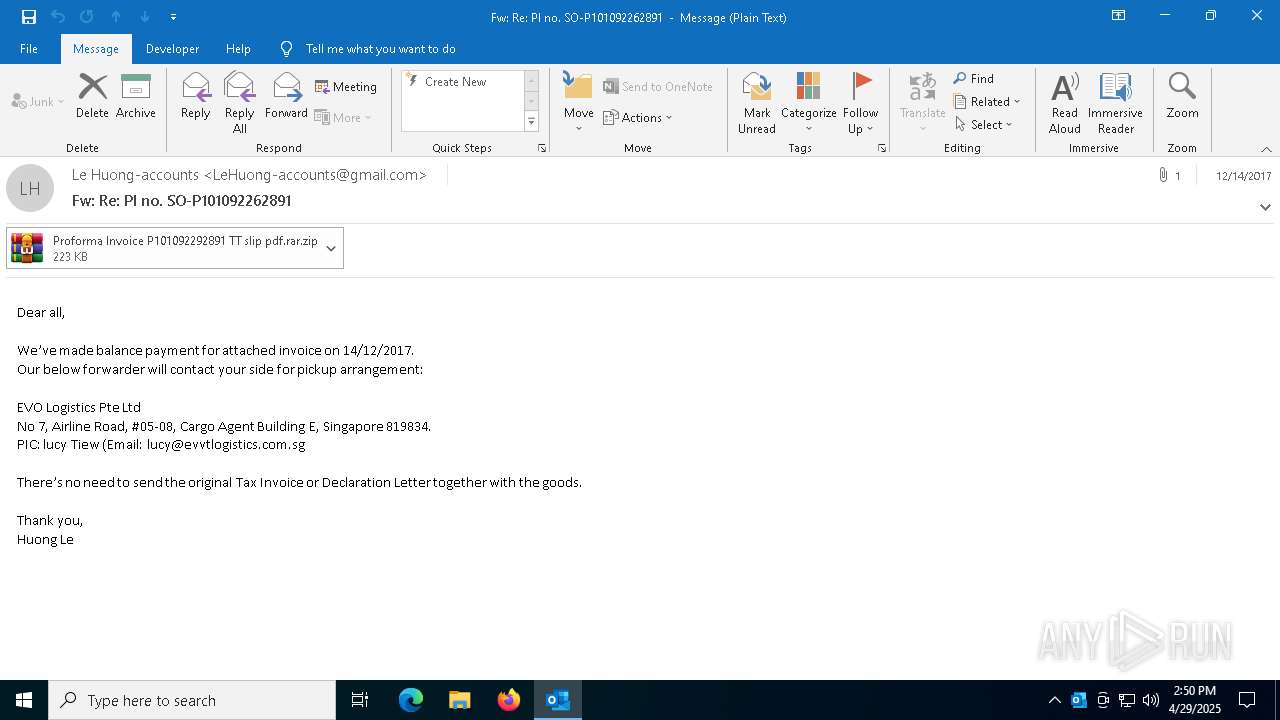
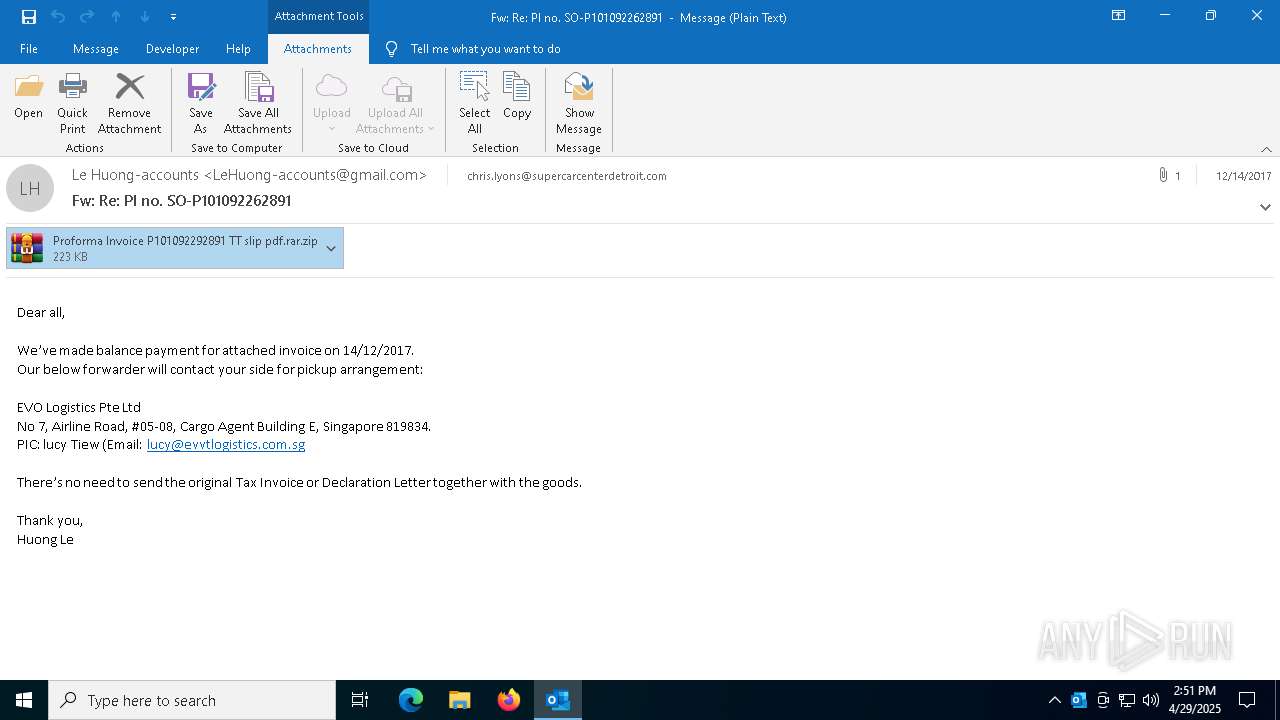
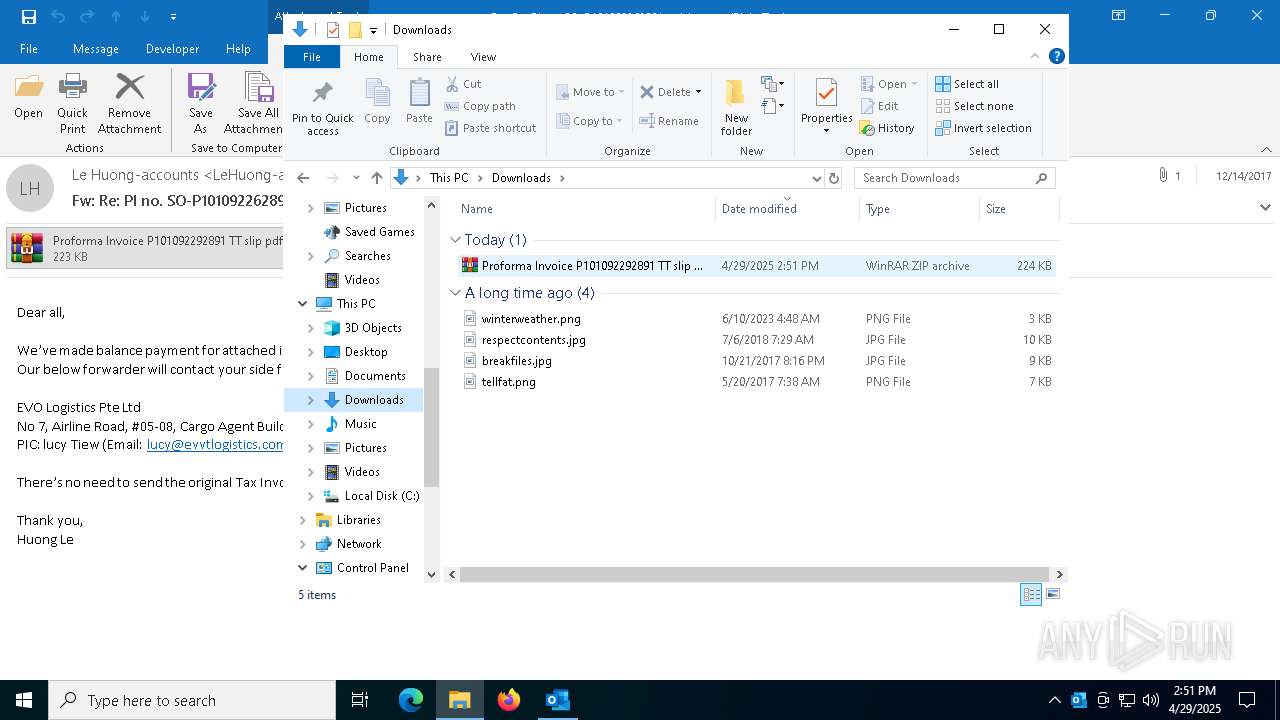
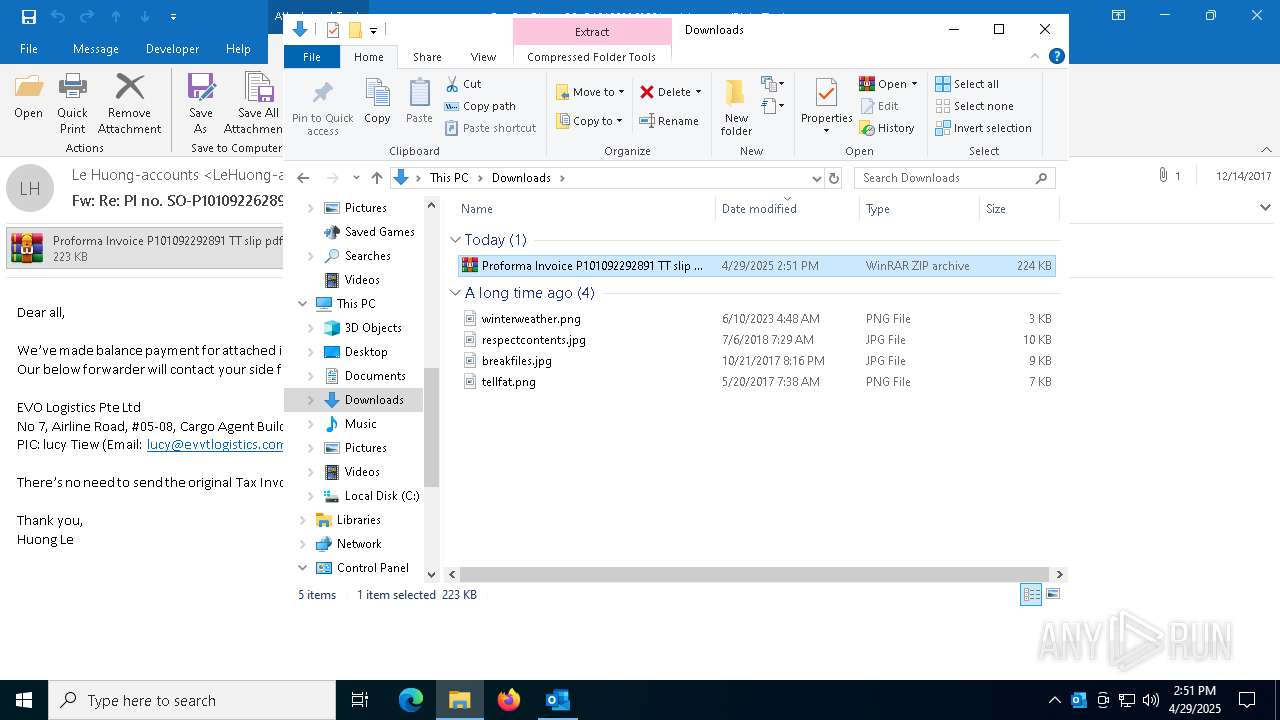
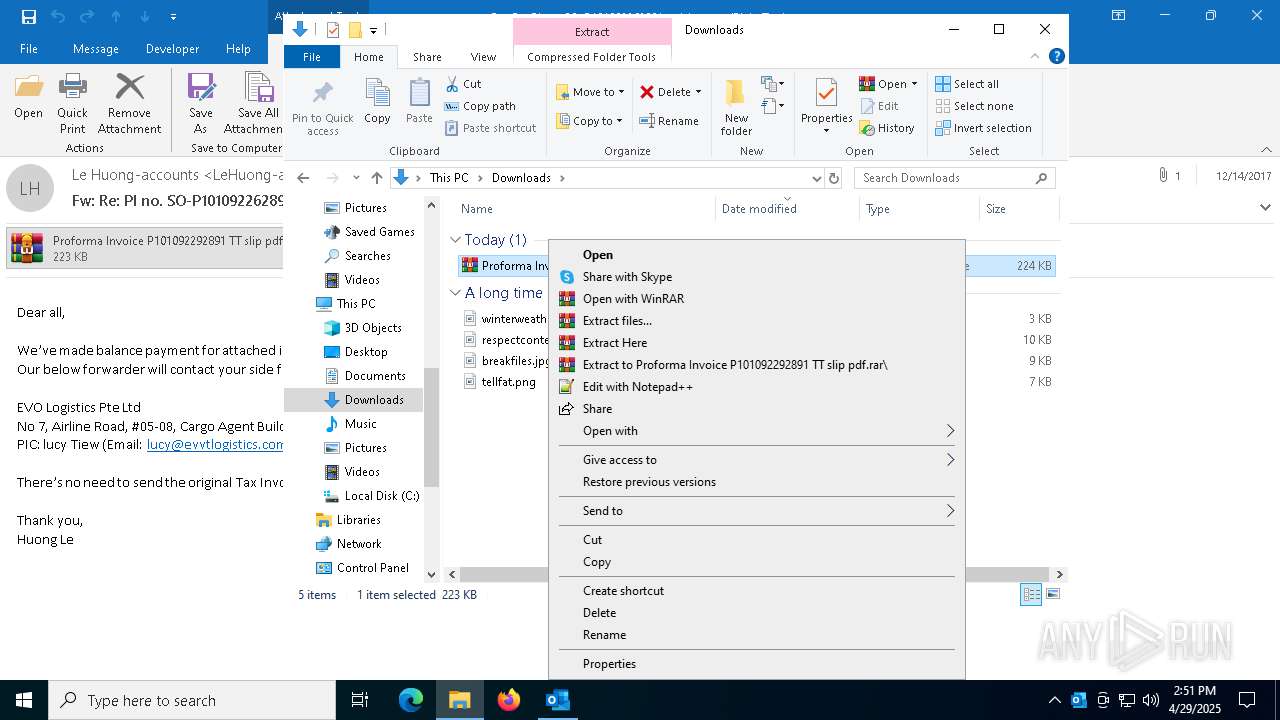
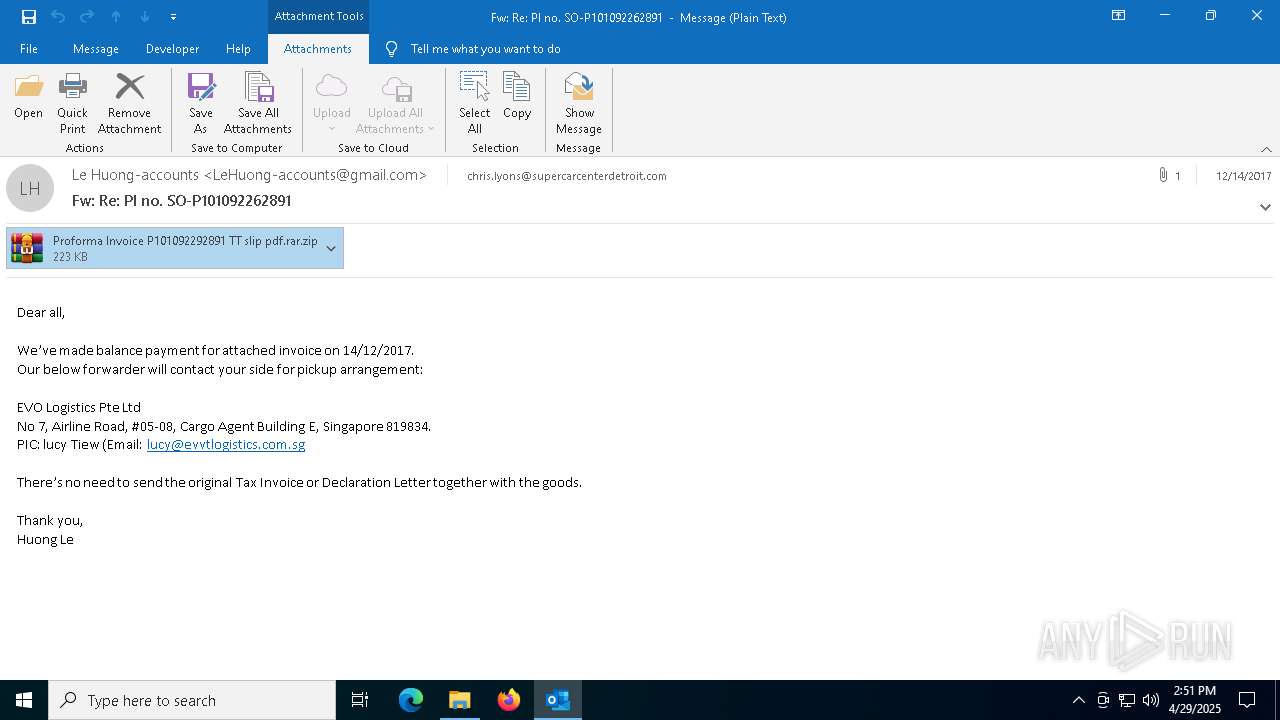
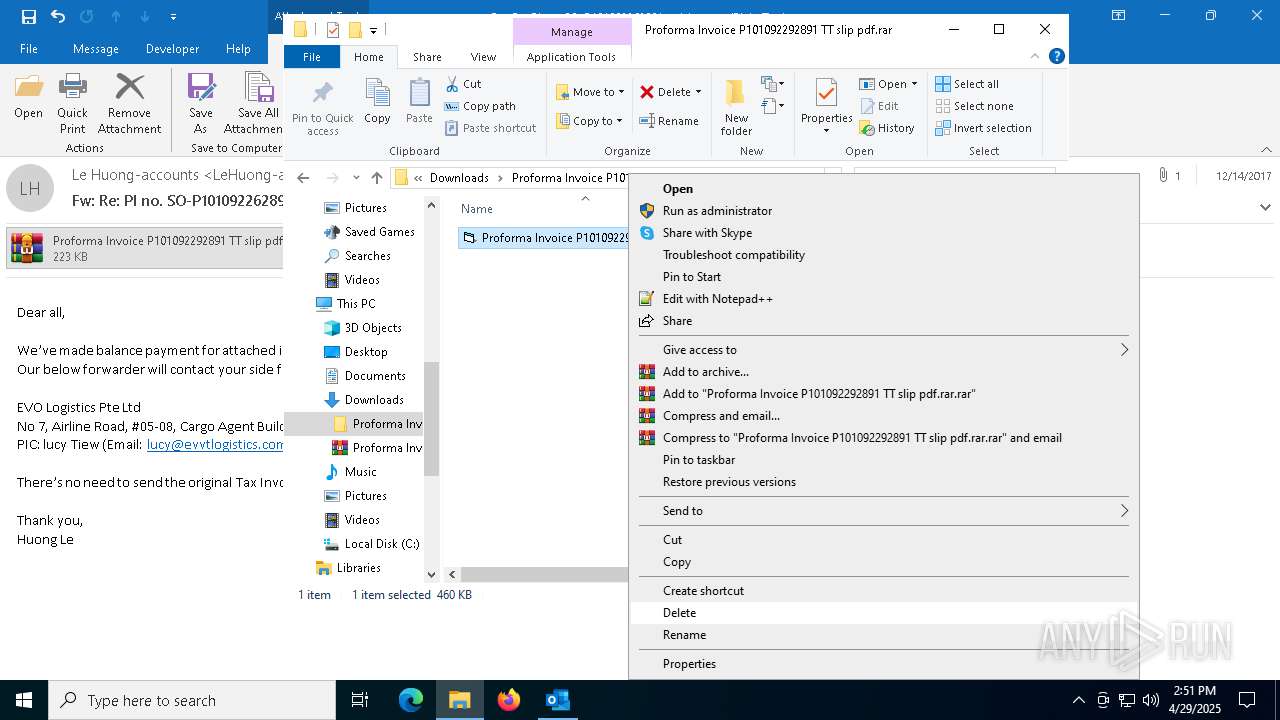
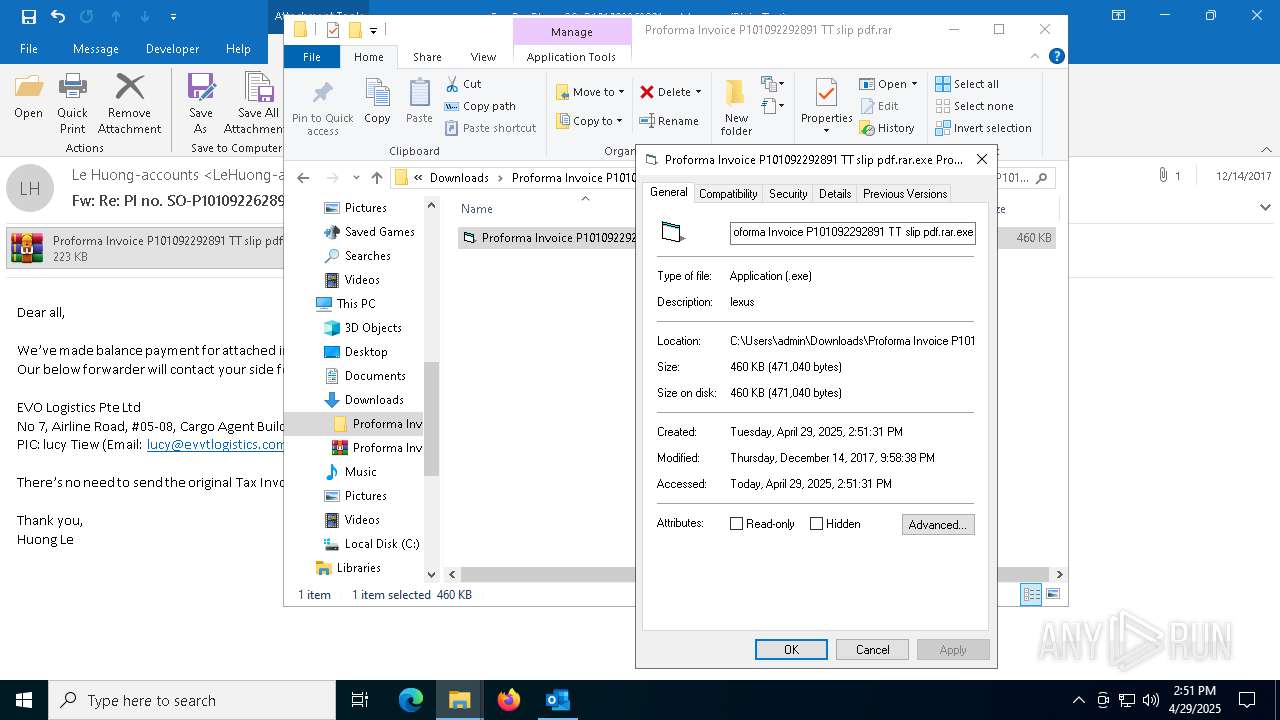
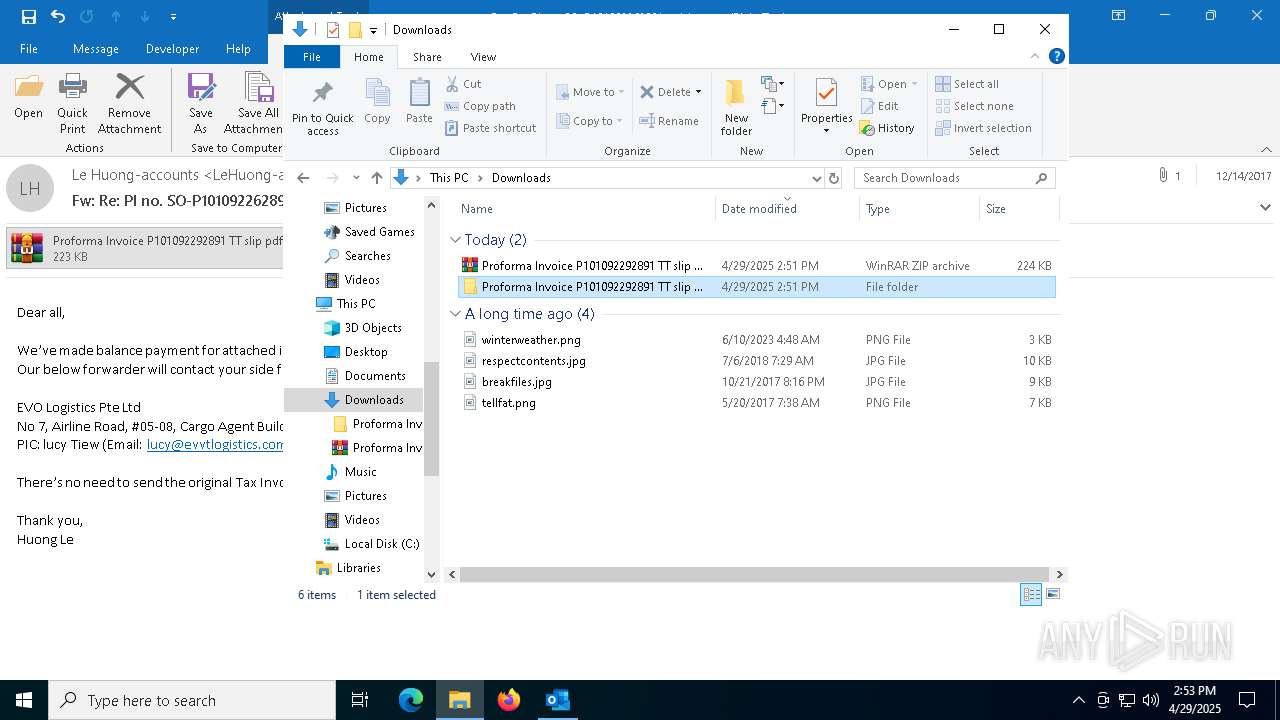
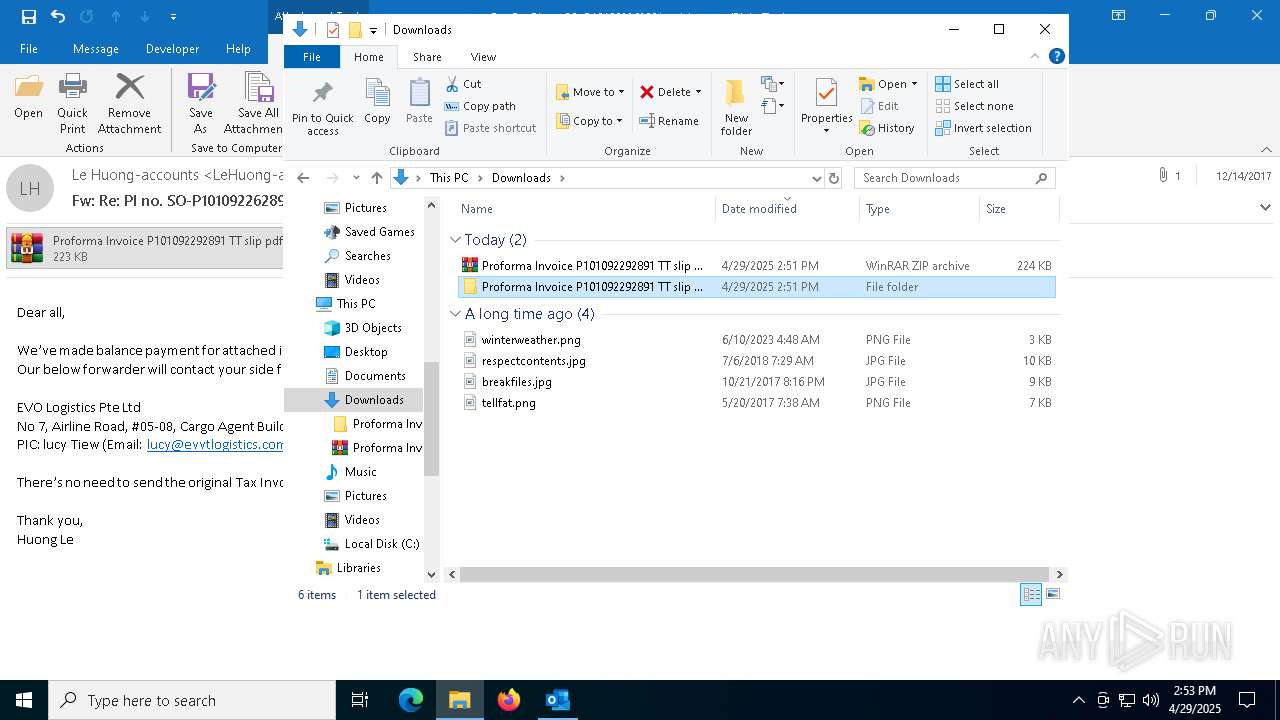
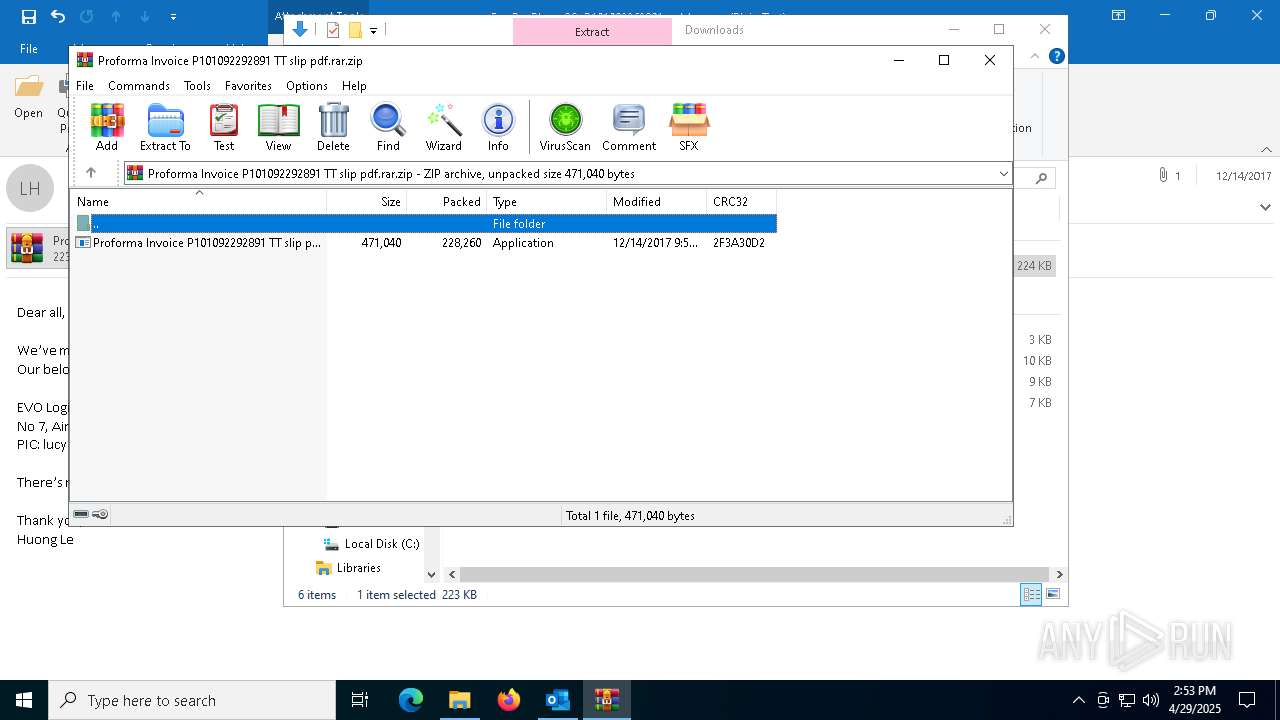
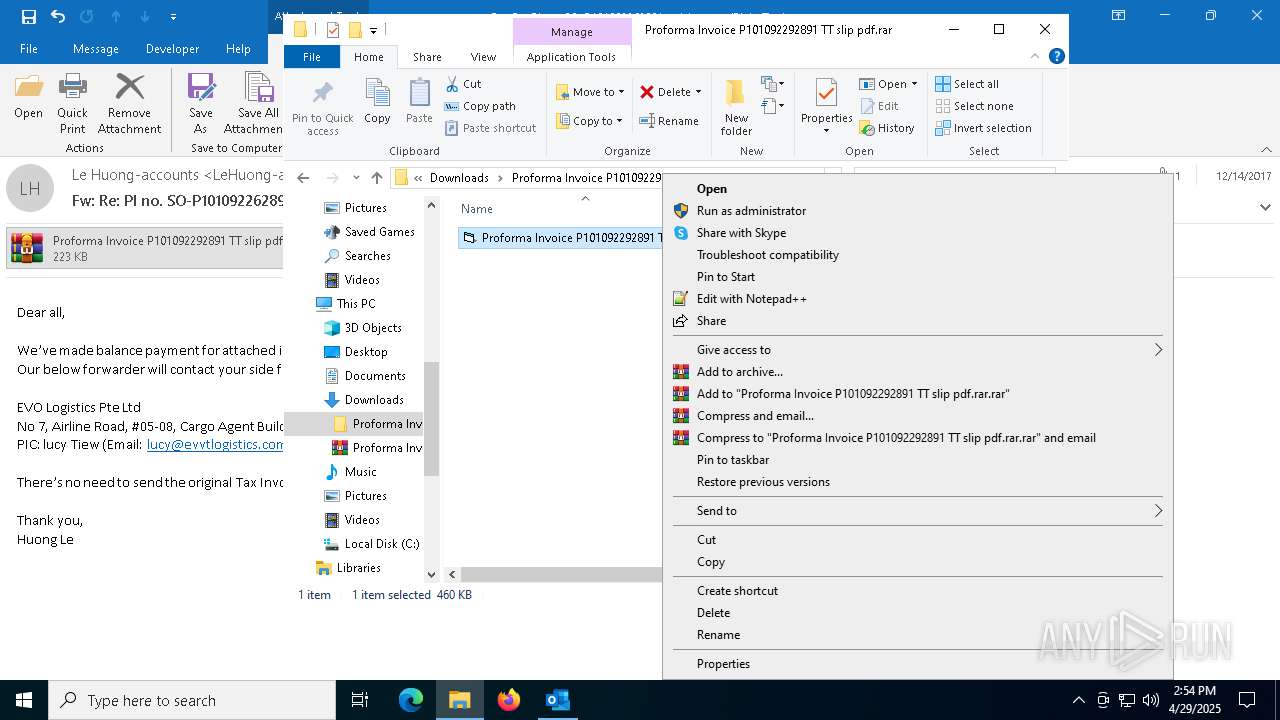
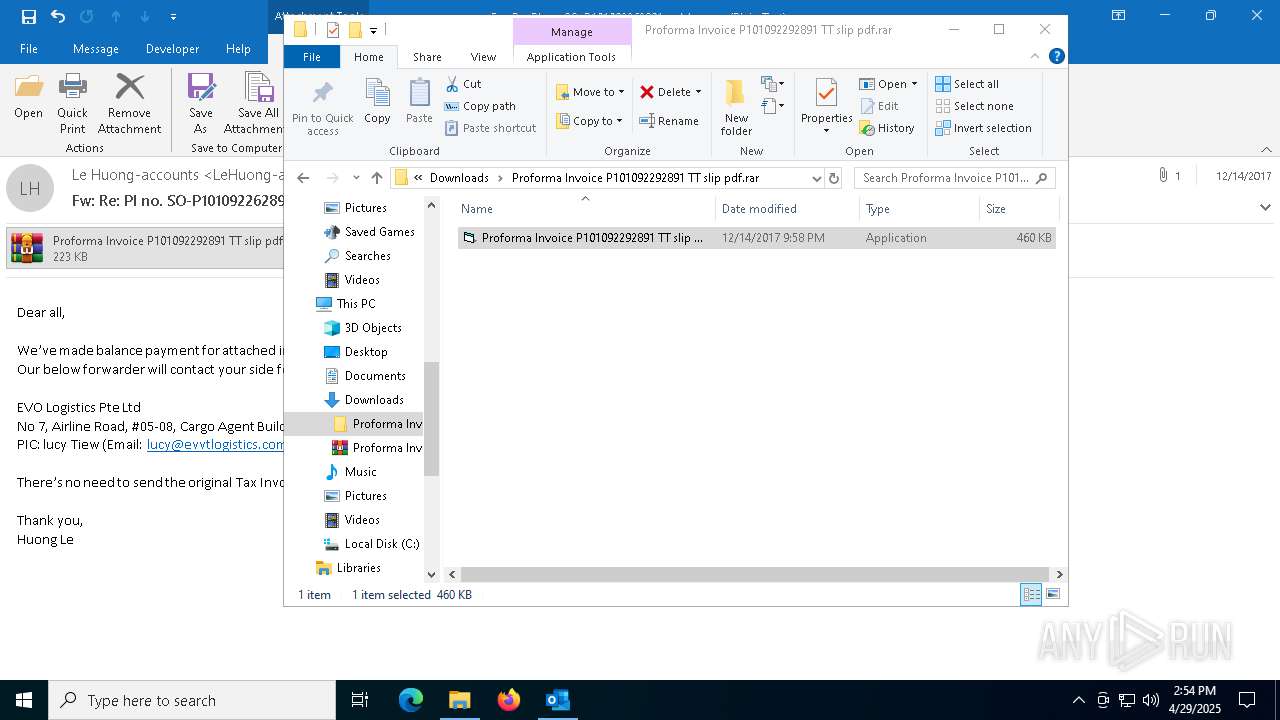
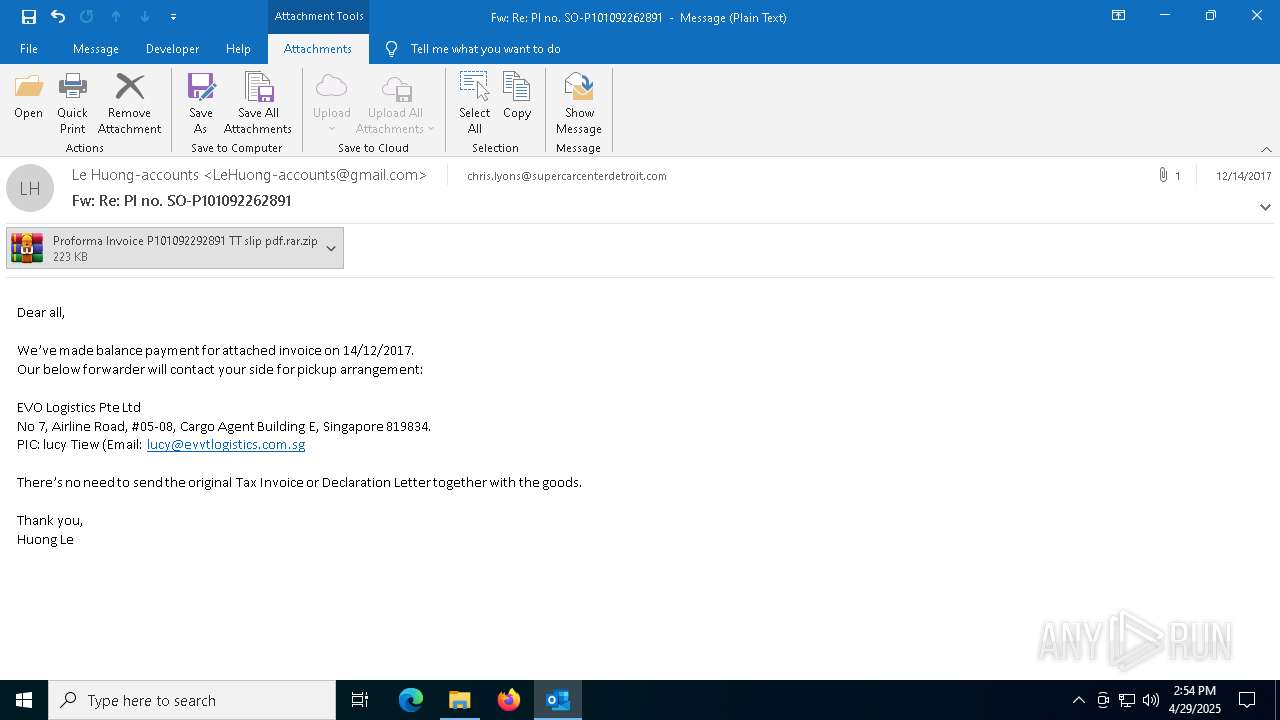
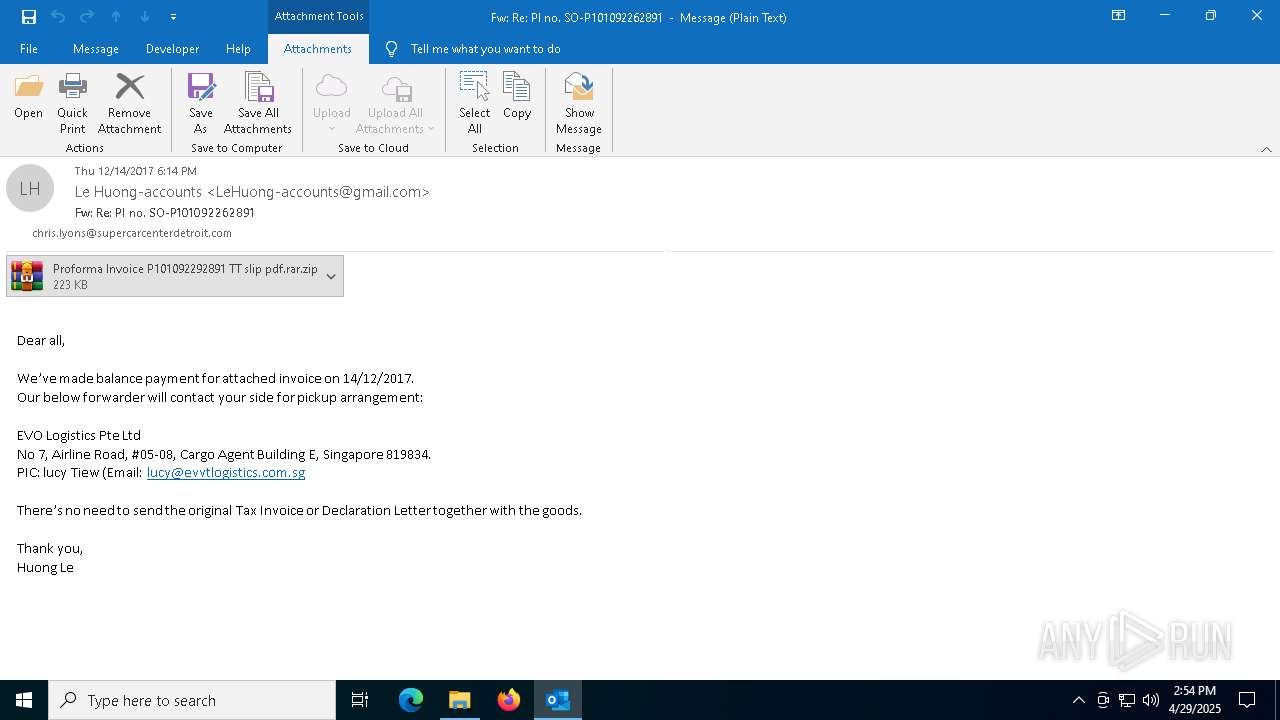
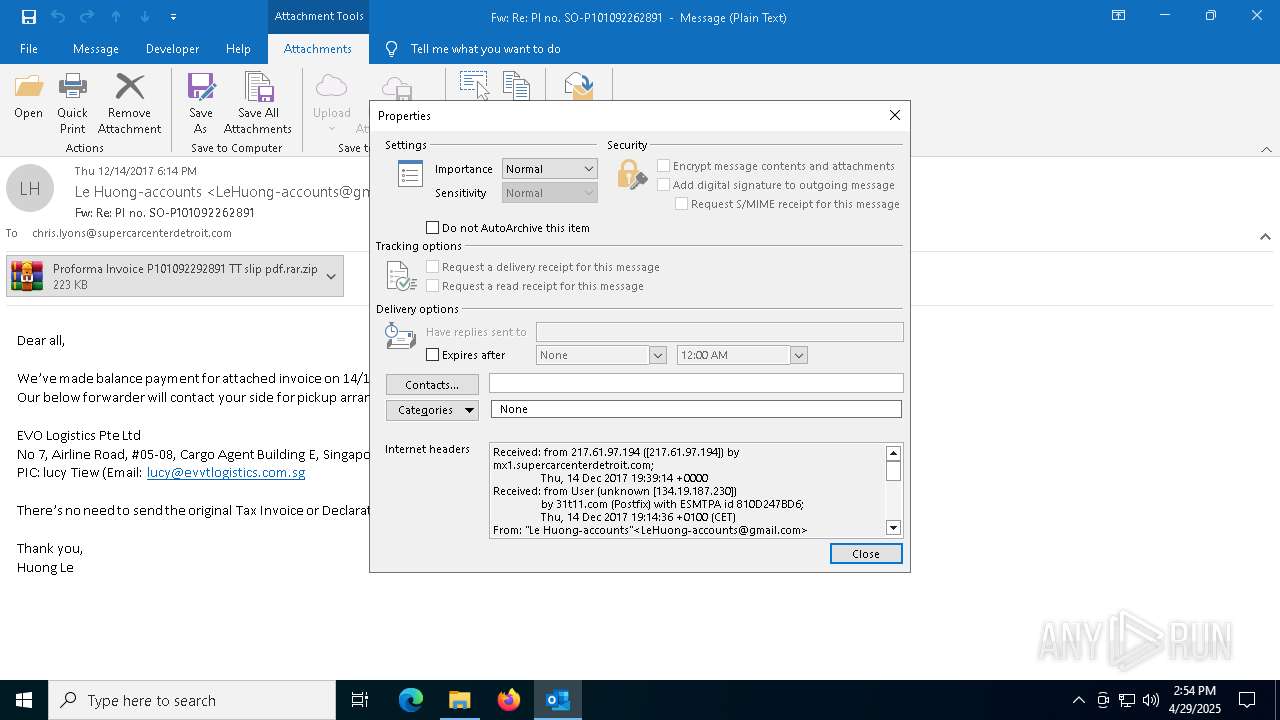
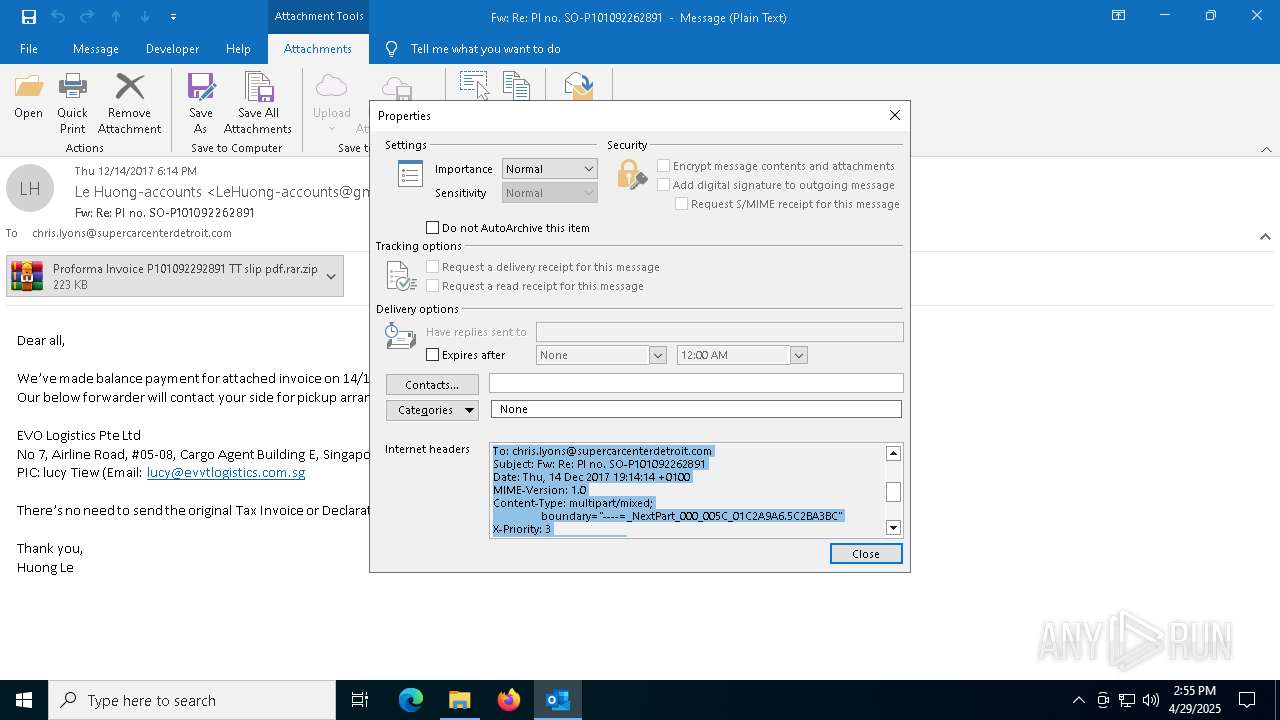
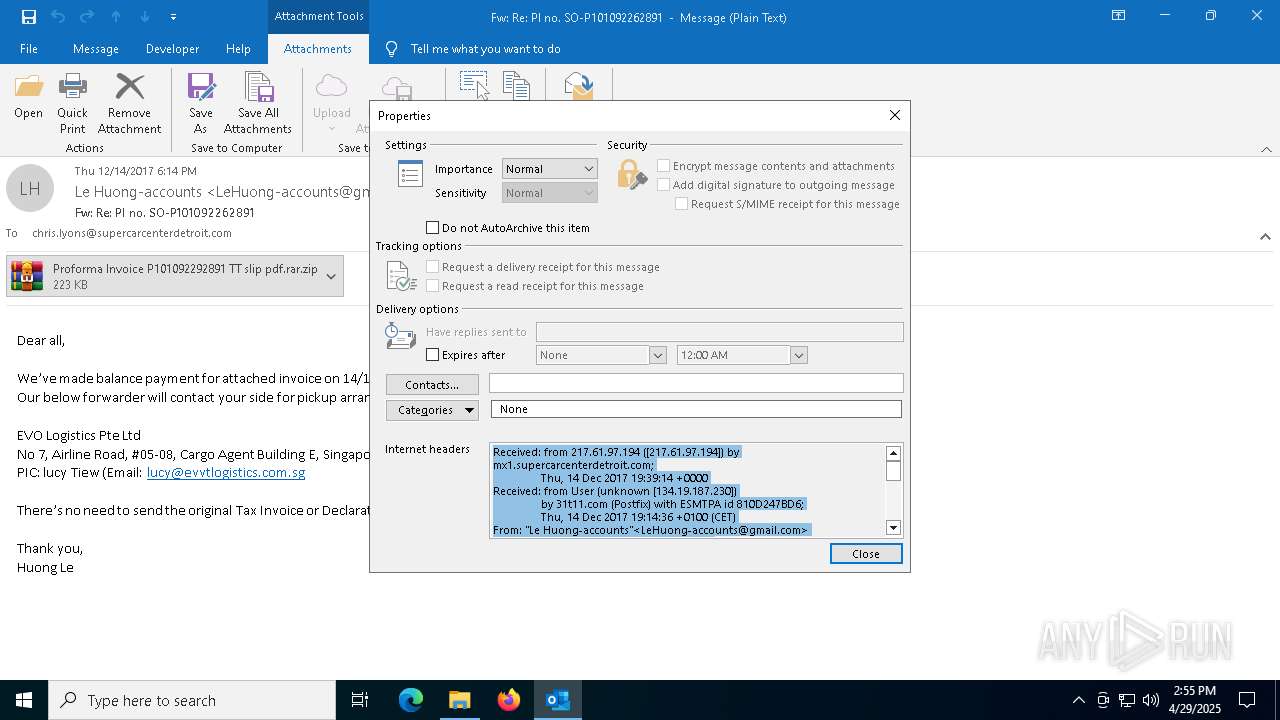
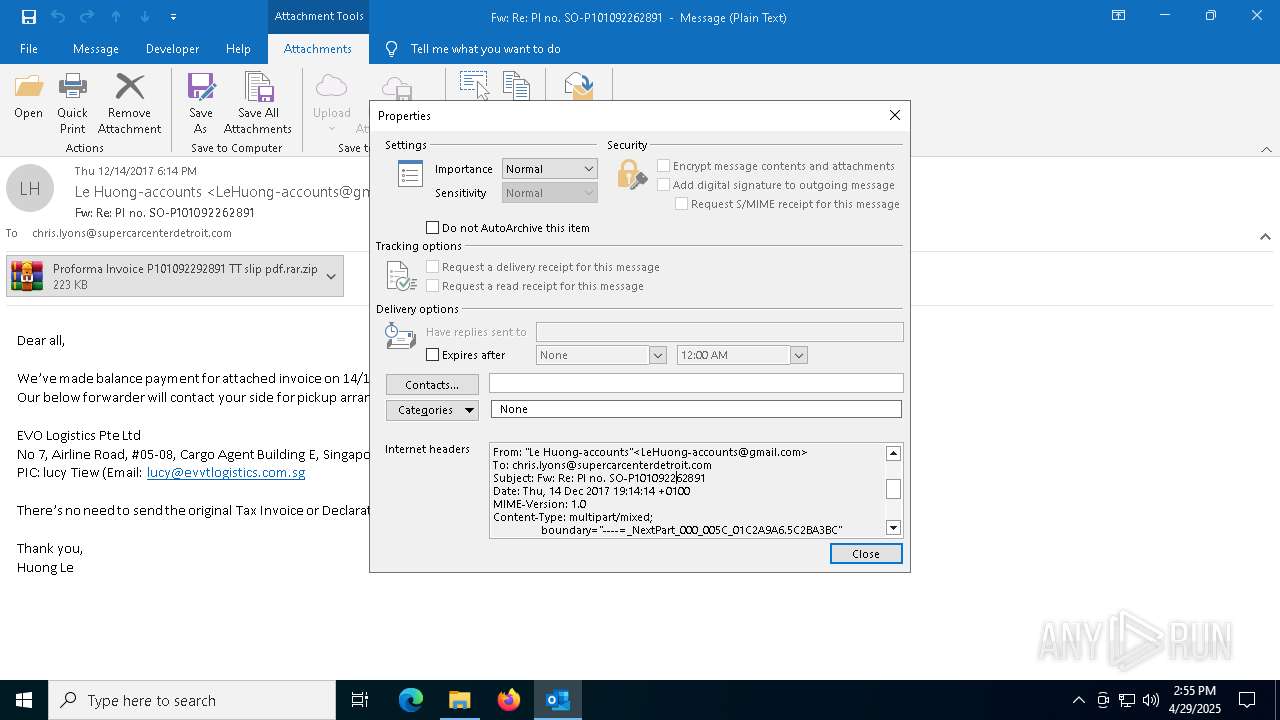
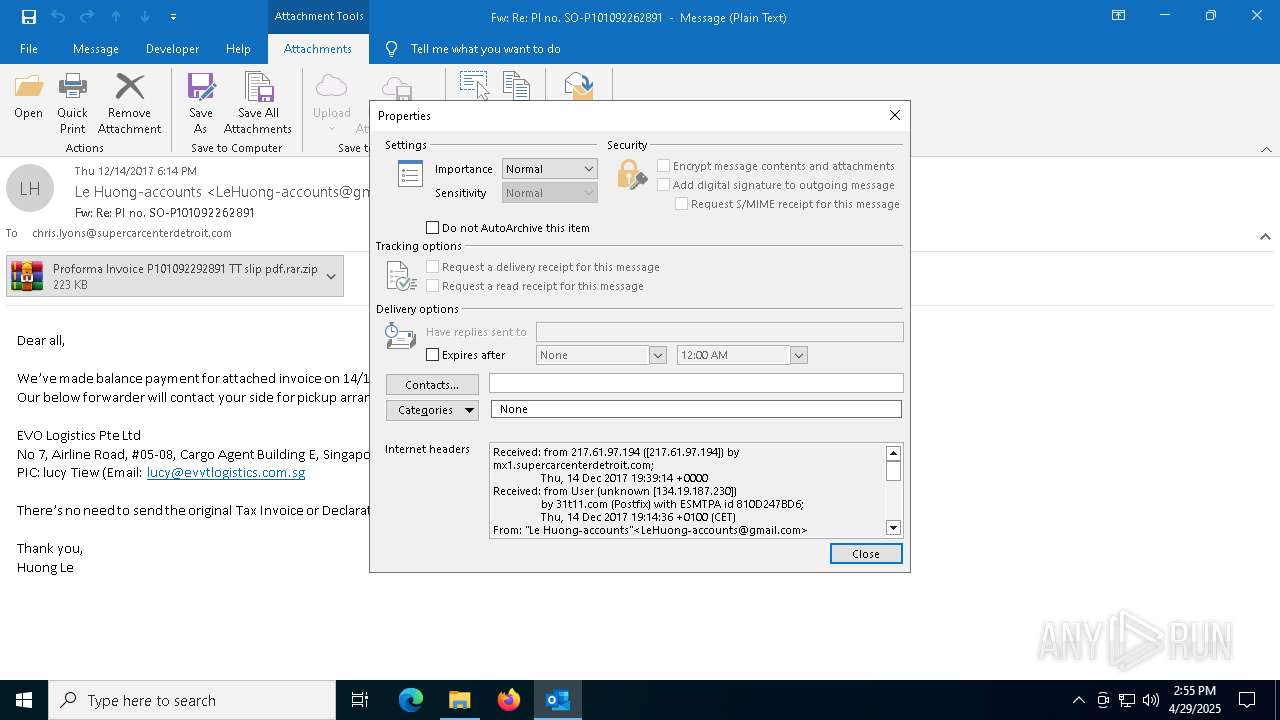
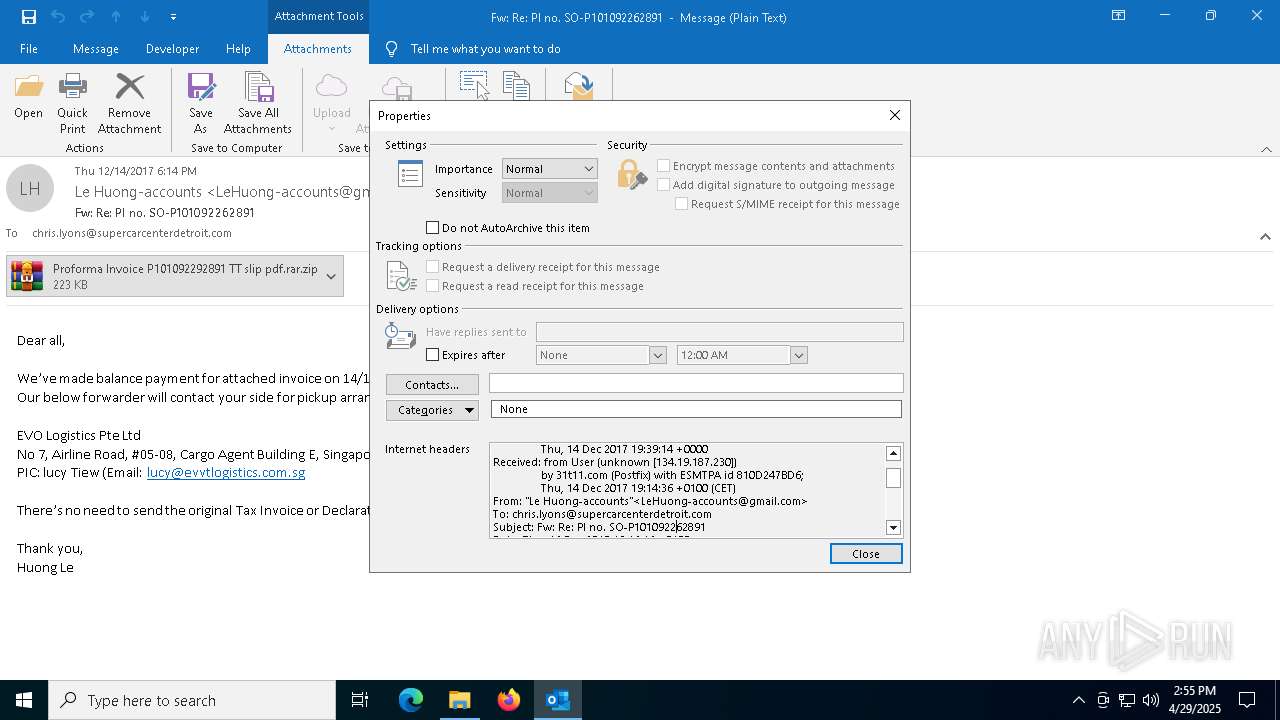
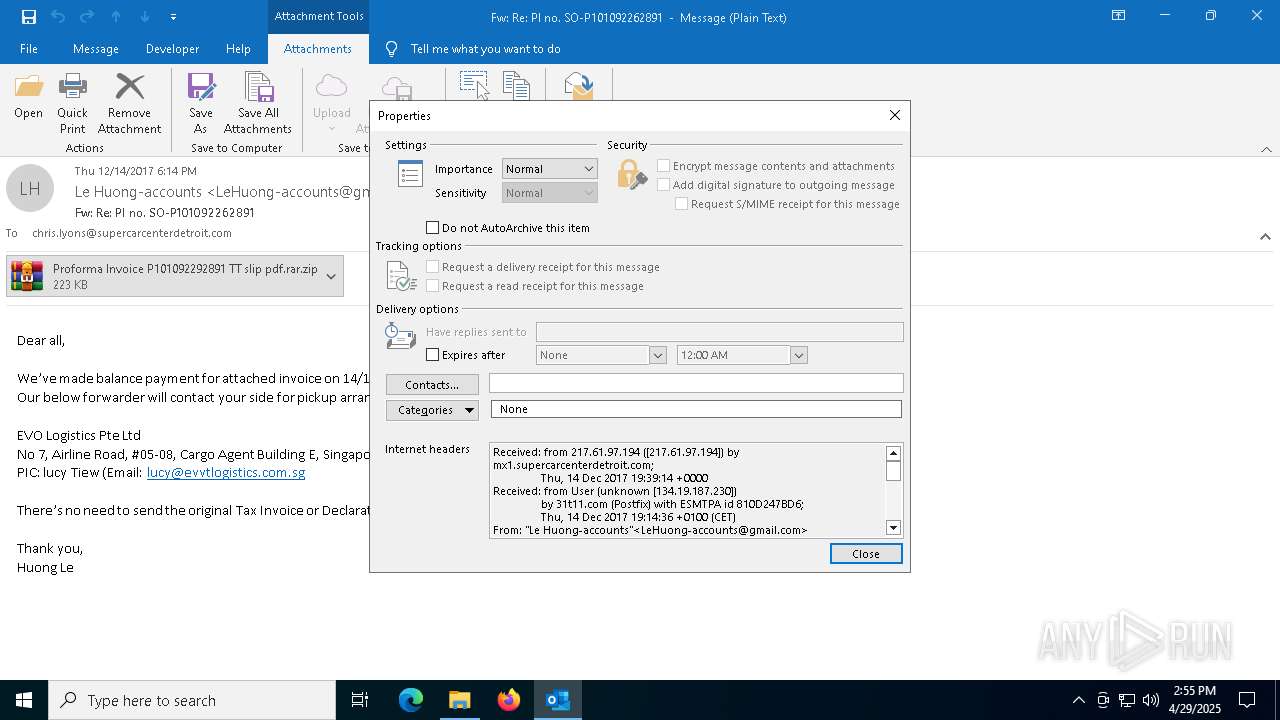
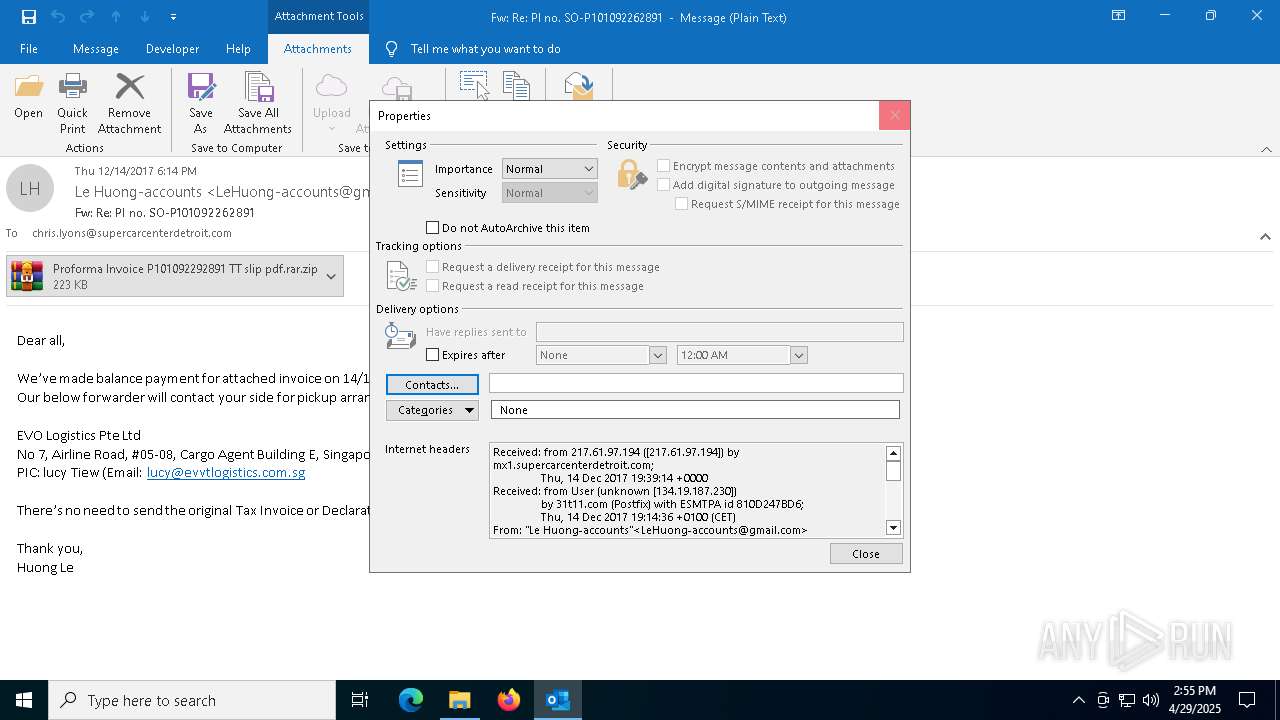
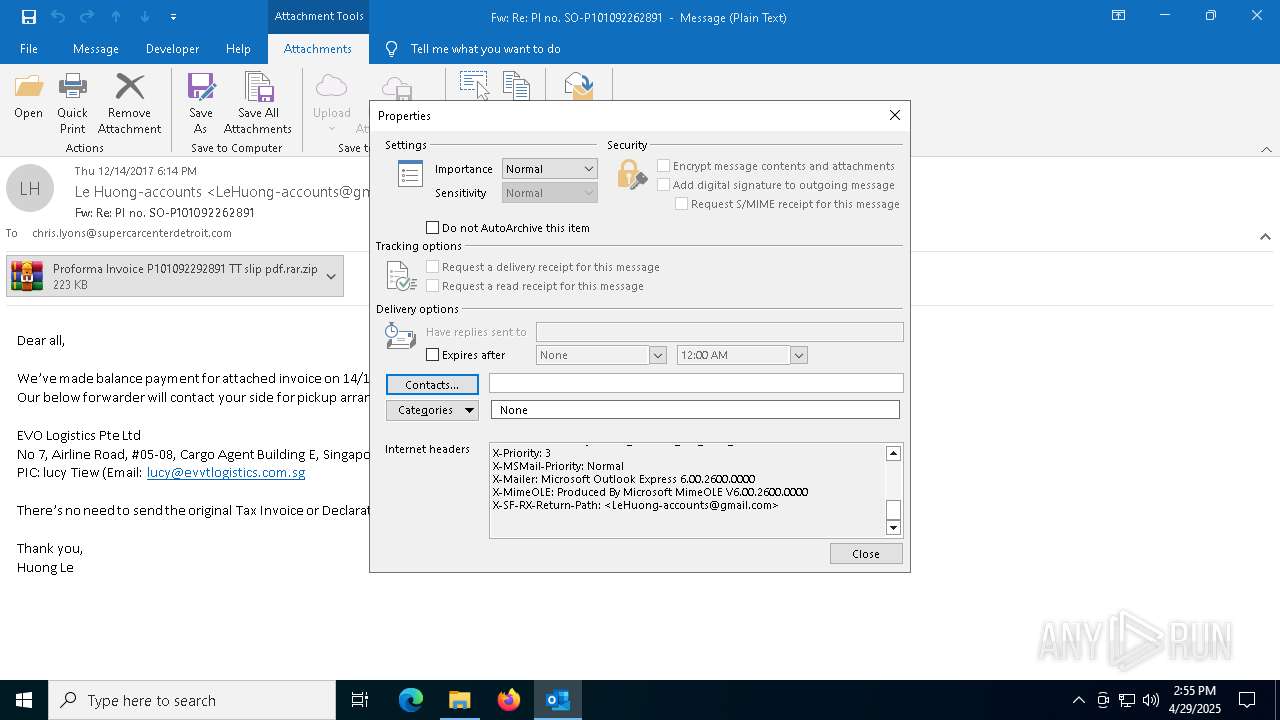
| File name: | malicious-email-1814-UTC.eml |
| Full analysis: | https://app.any.run/tasks/f871a84e-e809-4a8b-9c76-bc11a0d3aba8 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | April 29, 2025, 14:50:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, Non-ISO extended-ASCII text, with CRLF line terminators |
| MD5: | AB0161DCE4B3DA647CE46269BAB3405C |
| SHA1: | A1ECA086CDCEB47DB3F75FBE9621C7C075118649 |
| SHA256: | 1680370D9EE294BA8A3BEBCFFC3995FCEE6906D3201281BF85EF39537C7B3B92 |
| SSDEEP: | 6144:uvhxWOuktmi+44iFfCOmc6++wg+wSo0uE0kbF3/IoqNqdmib+GC:BEJVhL6KwSbuE0QF3/Iocqnc |
MALICIOUS
FORMBOOK has been detected (YARA)
- chkdsk.exe (PID: 4188)
FORMBOOK has been detected (SURICATA)
- explorer.exe (PID: 5492)
Connects to the CnC server
- explorer.exe (PID: 5492)
SUSPICIOUS
Application launched itself
- Proforma Invoice P101092292891 TT slip pdf.rar.exe (PID: 2420)
- ohmxwpep8pedo0q8.exe (PID: 2644)
Starts CMD.EXE for commands execution
- chkdsk.exe (PID: 4188)
Reads Microsoft Outlook installation path
- explorer.exe (PID: 5492)
Executable content was dropped or overwritten
- explorer.exe (PID: 5492)
- dllhost.exe (PID: 8172)
Contacting a server suspected of hosting an CnC
- explorer.exe (PID: 5492)
INFO
The sample compiled with chinese language support
- OUTLOOK.EXE (PID: 2564)
- WinRAR.exe (PID: 668)
- dllhost.exe (PID: 8172)
- explorer.exe (PID: 5492)
- WinRAR.exe (PID: 8080)
Manual execution by a user
- WinRAR.exe (PID: 668)
- chkdsk.exe (PID: 4188)
- Proforma Invoice P101092292891 TT slip pdf.rar.exe (PID: 2420)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 668)
- WinRAR.exe (PID: 8080)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Formbook
(PID) Process(4188) chkdsk.exe
C2www.ellentscm.info/ob/
Strings (79)USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
ProgramFiles
CommonProgramFiles
ALLUSERSPROFILE
/c copy "
/c del "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\signons.sqlite
\Microsoft\Vault\
SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins
\Google\Chrome\User Data\Default\Login Data
SELECT origin_url, username_value, password_value FROM logins
.exe
.com
.scr
.pif
.cmd
.bat
ms
win
gdi
mfc
vga
igfx
user
help
config
update
regsvc
chkdsk
systray
audiodg
certmgr
autochk
taskhost
colorcpl
services
IconCache
ThumbCache
Cookies
SeDebugPrivilege
SeShutdownPrivilege
\BaseNamedObjects
config.php
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control: no-cache
Origin: http://
User-Agent: Mozilla Firefox/4.0
Content-Type: application/x-www-form-urlencoded
Accept: */*
Referer: http://
Accept-Language: en-US
Accept-Encoding: gzip, deflate
dat=
f-start
f-end
Decoy C2 (64)maneresidenties.com
daylighttheatre.foundation
xn--jjq193ajmav75c.com
gatinhas.net
cerebrumfriend.info
gikyokudan.net
sosssou.com
texowipu14.win
askserene.com
lookbooks.net
salomst.reisen
hotsexchatwithmilfs.com
marcelaeerico.com
school79.info
zhongguowuzixu.com
b106879210.win
bishermarket.com
coincaucus.com
incomecan.net
alldayexchange.com
107hamiltonroad.com
claireaumatcha.com
xn--fiqs8spwb006g.com
jufa123.com
kowollik.email
sparkyoursukha.com
www8458v.com
jvfilmmakers.com
yifch.info
yunshangcms.com
seorowipe.com
gotrkx.com
xiangxiangbi.com
youxinyidai.com
turizmbelgesi.online
nolahmattresscoupon.com
goaskincancerhelpok.live
amiratu.com
dapsic.men
b2bcopybyjane.com
prozactruth.net
06mm9dj84r.com
heapto.com
xn--trivioonline-ehb.com
weddingpetattendant.com
4legs1heart.com
privacyguide.net
theitblogs.com
lukshan.com
juhanzaitu.com
100placesbandb.com
studioa93.com
canamultimedia.com
preprod.football
behrimen.com
hylexus.com
iangng.com
harrisrobertslimited.com
b3s669u-fzy.com
templatediprova.info
incoalth.com
adcecija.com
pleredberseka.com
refuright.com
Total processes
157
Monitored processes
22
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\Proforma Invoice P101092292891 TT slip pdf.rar.zip" "?\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1040 | "C:\Users\admin\Downloads\Proforma Invoice P101092292891 TT slip pdf.rar\Proforma Invoice P101092292891 TT slip pdf.rar.exe" | C:\Users\admin\Downloads\Proforma Invoice P101092292891 TT slip pdf.rar\Proforma Invoice P101092292891 TT slip pdf.rar.exe | — | Proforma Invoice P101092292891 TT slip pdf.rar.exe | |||||||||||
User: admin Company: lexus Integrity Level: MEDIUM Description: lexus Exit code: 0 Version: 8.05 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\Downloads\Proforma Invoice P101092292891 TT slip pdf.rar\Proforma Invoice P101092292891 TT slip pdf.rar.exe" | C:\Users\admin\Downloads\Proforma Invoice P101092292891 TT slip pdf.rar\Proforma Invoice P101092292891 TT slip pdf.rar.exe | — | explorer.exe | |||||||||||
User: admin Company: lexus Integrity Level: MEDIUM Description: lexus Exit code: 0 Version: 8.05 Modules
| |||||||||||||||
| 2564 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\malicious-email-1814-UTC.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2644 | "C:\Program Files (x86)\Zgzndsznp\ohmxwpep8pedo0q8.exe" | C:\Program Files (x86)\Zgzndsznp\ohmxwpep8pedo0q8.exe | — | explorer.exe | |||||||||||
User: admin Company: lexus Integrity Level: MEDIUM Description: lexus Exit code: 0 Version: 8.05 Modules
| |||||||||||||||
| 4152 | "C:\Windows\SysWOW64\WWAHost.exe" | C:\Windows\SysWOW64\WWAHost.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft WWA Host Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4188 | "C:\Windows\SysWOW64\chkdsk.exe" | C:\Windows\SysWOW64\chkdsk.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Check Disk Utility Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
Formbook(PID) Process(4188) chkdsk.exe C2www.ellentscm.info/ob/ Strings (79)USERNAME LOCALAPPDATA USERPROFILE APPDATA TEMP ProgramFiles CommonProgramFiles ALLUSERSPROFILE /c copy " /c del " \Run \Policies \Explorer \Registry\User \Registry\Machine \SOFTWARE\Microsoft\Windows\CurrentVersion Office\15.0\Outlook\Profiles\Outlook\ NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ \SOFTWARE\Mozilla\Mozilla \Mozilla Username: Password: formSubmitURL usernameField encryptedUsername encryptedPassword \logins.json \signons.sqlite \Microsoft\Vault\ SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins \Google\Chrome\User Data\Default\Login Data SELECT origin_url, username_value, password_value FROM logins .exe .com .scr .pif .cmd .bat ms win gdi mfc vga igfx user help config update regsvc chkdsk systray audiodg certmgr autochk taskhost colorcpl services IconCache ThumbCache Cookies SeDebugPrivilege SeShutdownPrivilege \BaseNamedObjects config.php POST HTTP/1.1 Host: Connection: close Content-Length: Cache-Control: no-cache Origin: http:// User-Agent: Mozilla Firefox/4.0 Content-Type: application/x-www-form-urlencoded Accept: */* Referer: http:// Accept-Language: en-US Accept-Encoding: gzip, deflate
dat= f-start f-end Decoy C2 (64)maneresidenties.com daylighttheatre.foundation xn--jjq193ajmav75c.com gatinhas.net cerebrumfriend.info gikyokudan.net sosssou.com texowipu14.win askserene.com lookbooks.net salomst.reisen hotsexchatwithmilfs.com marcelaeerico.com school79.info zhongguowuzixu.com b106879210.win bishermarket.com coincaucus.com incomecan.net alldayexchange.com 107hamiltonroad.com claireaumatcha.com xn--fiqs8spwb006g.com jufa123.com kowollik.email sparkyoursukha.com www8458v.com jvfilmmakers.com yifch.info yunshangcms.com seorowipe.com gotrkx.com xiangxiangbi.com youxinyidai.com turizmbelgesi.online nolahmattresscoupon.com goaskincancerhelpok.live amiratu.com dapsic.men b2bcopybyjane.com prozactruth.net 06mm9dj84r.com heapto.com xn--trivioonline-ehb.com weddingpetattendant.com 4legs1heart.com privacyguide.net theitblogs.com lukshan.com juhanzaitu.com 100placesbandb.com studioa93.com canamultimedia.com preprod.football behrimen.com hylexus.com iangng.com harrisrobertslimited.com b3s669u-fzy.com templatediprova.info incoalth.com adcecija.com pleredberseka.com refuright.com | |||||||||||||||
Total events
57 525
Read events
55 904
Write events
1 420
Delete events
201
Modification events
| (PID) Process: | (2564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (2564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\2564 |
| Operation: | write | Name: | 0 |
Value: 0B0E10C2F3A318E331AF49A52AD1E77D1F7F4D230046A0A4BFF8E0A2EEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5118414D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (2564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (2564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (2564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (2564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (2564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (2564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (2564) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
4
Suspicious files
17
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2564 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 2564 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:5EB5DEF34748487EED3D8E6DCA5EB602 | SHA256:C0812947766BE364B42982863484259B68AA17B56977410060B47F501AB118FE | |||
| 2564 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:4A616C03A38A5455B78DC20677E1CC1F | SHA256:0D8CCFCD9D27226B33F6AD1A6749DA4B008B34DB7865F34B11EFFD43E988C5BC | |||
| 2564 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\JA2CNSX3\Proforma Invoice P101092292891 TT slip pdf.rar.zip:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2564 | OUTLOOK.EXE | C:\Users\admin\Downloads\Proforma Invoice P101092292891 TT slip pdf.rar.zip:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2564 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:96EF448D1200F435C6D33BB7EF0E9656 | SHA256:52CD56B2B1B009E1D18666BDF0C1D0794759976C09F246C76BD210DD307F2BDE | |||
| 2564 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:E906C4E6EC0C49B734210A423FD60A36 | SHA256:374306CAC9CEC6486BEA832063AFBA5564D511E3049167B918012D3C004808F7 | |||
| 2564 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:DDE5B62D4556A6B5AF9B35783AC54BD5 | SHA256:6D02C20CD6DC2ADB37DF6C47FE7DD4257B6BA91CC8C1437D39FCE4F411C2DE26 | |||
| 5492 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 2564 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:83F670DCB4799CB2ECB273C9F8B47E7C | SHA256:DB2B8ED639D3D66DE7A3DEF39281344F80E2700F36C2EFCD73F6032195F6A6F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
41
DNS requests
34
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2564 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2564 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
3300 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3300 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5492 | explorer.exe | GET | 404 | 200.58.119.215:80 | http://www.amiratu.com/ob/?id=/XOX991UuoWKQeOUzg6tQXIzS2Hh6cF7p30NYiLVEhdrnUZRBcNonon9zY/jI/Elh5Y3&uvpXQL=r4w4yPRh7bV0aJi | unknown | — | — | malicious |
5492 | explorer.exe | POST | 404 | 81.169.145.86:80 | http://www.kowollik.email/ob/ | unknown | — | — | malicious |
5492 | explorer.exe | GET | 404 | 81.169.145.86:80 | http://www.kowollik.email/ob/?id=7DADu/+n5xl4pvqijm258g+TyvMSwn/8W2GB3FRFuGdvWui7bYShv2N3sNaYjVb+iX+w&uvpXQL=r4w4yPRh7bV0aJi | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2564 | OUTLOOK.EXE | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2564 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5492 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) |
5492 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE Formbook 0.3 Checkin |
5492 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE Formbook 0.3 Checkin |
5492 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) |