| File name: | stretcher.exe |
| Full analysis: | https://app.any.run/tasks/4e96692b-c743-4d94-8fd7-1205725a0b63 |
| Verdict: | Malicious activity |
| Threats: | Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying. |
| Analysis date: | April 15, 2025, 17:17:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 19 sections |
| MD5: | DBDC0ECA0F8B2C5FDFB062622C99E3FD |
| SHA1: | B7FD9592CEFB8A05B50D8DC0321C4A1E28F5A147 |
| SHA256: | 164B01071C8ACBE4A3993CB9B55CF43E8BDF8CB1AADA020CE2D1090CADB492E5 |
| SSDEEP: | 49152:dspDMytgxyPJbzZ+pnfCM1FLZ8NaNC1+ZrS5huGNQ/EWhgLdT:dIDPOnJ/ZrS5huGNQ/EWhgLdT |
MALICIOUS
Changes the autorun value in the registry
- stretcher.exe (PID: 2136)
- stretcher.exe (PID: 6476)
Deletes shadow copies
- cmd.exe (PID: 4652)
- cmd.exe (PID: 1676)
RANSOMWARE has been detected
- stretcher.exe (PID: 2136)
- stretcher.exe (PID: 6476)
SUSPICIOUS
Hides command output
- cmd.exe (PID: 4652)
- cmd.exe (PID: 1676)
Executes application which crashes
- stretcher.exe (PID: 2136)
- stretcher.exe (PID: 6476)
Write to the desktop.ini file (may be used to cloak folders)
- stretcher.exe (PID: 2136)
Starts CMD.EXE for commands execution
- stretcher.exe (PID: 2136)
- stretcher.exe (PID: 6476)
INFO
Checks supported languages
- stretcher.exe (PID: 2136)
- stretcher.exe (PID: 6476)
Creates files or folders in the user directory
- WerFault.exe (PID: 1228)
- WerFault.exe (PID: 1532)
Manual execution by a user
- stretcher.exe (PID: 6476)
- WINWORD.EXE (PID: 1532)
- mspaint.exe (PID: 1184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:04:15 17:17:18+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.44 |
| CodeSize: | 916480 |
| InitializedDataSize: | 236032 |
| UninitializedDataSize: | 3584 |
| EntryPoint: | 0x1125 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
149
Monitored processes
17
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 904 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
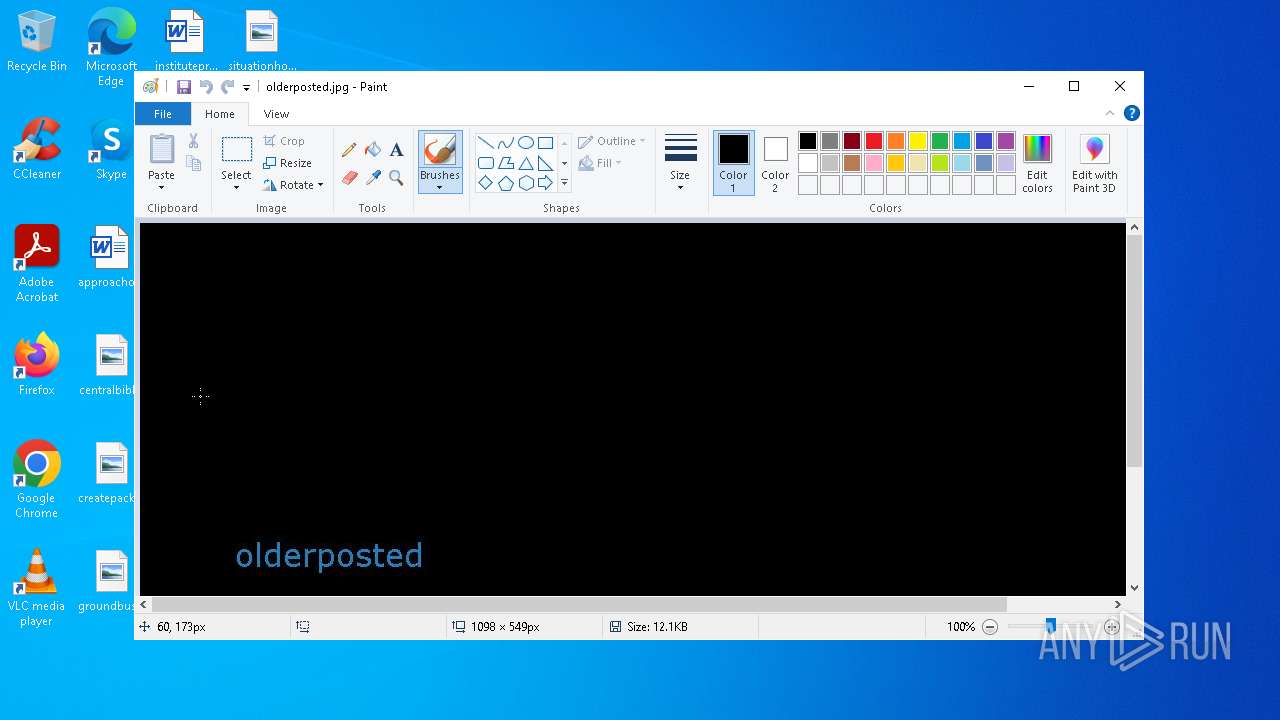
| 1184 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\olderposted.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | C:\WINDOWS\system32\WerFault.exe -u -p 2136 -s 72 | C:\Windows\System32\WerFault.exe | — | stretcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | C:\WINDOWS\system32\WerFault.exe -u -p 6476 -s 84 | C:\Windows\System32\WerFault.exe | — | stretcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\significantbill.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1676 | C:\WINDOWS\system32\cmd.exe /c vssadmin delete shadows /all /quiet >nul 2>&1 | C:\Windows\System32\cmd.exe | — | stretcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Users\admin\Desktop\stretcher.exe" | C:\Users\admin\Desktop\stretcher.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226505 Modules
| |||||||||||||||
| 2552 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "7FC01B89-F46A-40C5-B502-FFBA432580FC" "FB0047DB-7DCC-46A6-B8AB-10C75ACF965B" "1532" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 4120 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4408 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 745
Read events
8 634
Write events
96
Delete events
15
Modification events
| (PID) Process: | (2136) stretcher.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | StretcherUpdate |
Value: C:\Users\admin\Desktop\stretcher.exe | |||
| (PID) Process: | (6476) stretcher.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | StretcherUpdate |
Value: C:\Users\admin\Desktop\stretcher.exe | |||
| (PID) Process: | (1184) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | WindowPlacement |
Value: 2C00000000000000010000000000000000000000FFFFFFFFFFFFFFFF7F000000470000007F04000087020000 | |||
| (PID) Process: | (1184) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ShowThumbnail |
Value: 0 | |||
| (PID) Process: | (1184) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | BMPWidth |
Value: 0 | |||
| (PID) Process: | (1184) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | BMPHeight |
Value: 0 | |||
| (PID) Process: | (1184) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbXPos |
Value: 0 | |||
| (PID) Process: | (1184) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbYPos |
Value: 0 | |||
| (PID) Process: | (1184) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbWidth |
Value: 0 | |||
| (PID) Process: | (1184) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbHeight |
Value: 0 | |||
Executable files
2
Suspicious files
24
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1228 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_stretcher.exe_2db079223fbaf7a79c8ce1237d3719ea46d8d55_138749ae_ca8ae906-9c3a-40e8-953b-d776df582af8\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1532 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_stretcher.exe_2db079223fbaf7a79c8ce1237d3719ea46d8d55_138749ae_a4e31525-b349-4fb0-8d2d-e9851f92aa30\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1532 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERDBAD.tmp.WERInternalMetadata.xml | binary | |
MD5:FEF603C26C43B5E834790113A3B03F1F | SHA256:A1230E249B546D0050D9B4E307E30B733D44F18887F741F22197A39201FFA96F | |||
| 2136 | stretcher.exe | C:\$Recycle.Bin\S-1-5-21-1693682860-607145093-2874071422-1001\desktop.ini | text | |
MD5:B4A3082FC4AACCCBF5288CF374426A2E | SHA256:295D88E9A46D5750BF245E8EE7B46D859568C83AE97A086B94251931B15AFBA3 | |||
| 1228 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERBE24.tmp.xml | xml | |
MD5:77CBAA05A9209004AB3D6CB8ECA08505 | SHA256:513D24C571018788F91B148CF88F401E158204F1530CF5537DF238D26CC15FDE | |||
| 1532 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\Features\6FeatureCache.txt | binary | |
MD5:79A22F4E754991FB51F73F0B26C85324 | SHA256:E6FB6546D3BC59FCC139767277C294A5E83068D710C9920174C3009AA4F33785 | |||
| 6476 | stretcher.exe | C:\$Recycle.Bin\S-1-5-21-1693682860-607145093-2874071422-1001\desktop.ini.stretched.stretched | text | |
MD5:A526B9E7C716B3489D8CC062FBCE4005 | SHA256:E1B9CE9B57957B1A0607A72A057D6B7A9B34EA60F3F8AA8F38A3AF979BD23066 | |||
| 1228 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERBDC5.tmp.WERInternalMetadata.xml | binary | |
MD5:0F3A47740C59DC0C00C8402DE3BE197B | SHA256:1F7BEAF4029BD7D0F4EBB1A113B211798C828F8F95E324A95FE77CF6C03EE317 | |||
| 1532 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{984B1FAC-C872-4B65-A918-321E6A7D5CAC}.tmp | binary | |
MD5:830FBF83999E052538EAF156AB6ECB17 | SHA256:D5098A2CEAE815DB29CD53C76F85240C95DC4D2E3FEDDD71D628617064C29869 | |||
| 1228 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\stretcher.exe.2136.dmp | binary | |
MD5:9854B1AB87EDC8ED17CE7A8A448F783B | SHA256:1D1BA17C6DE95EA8A5C494C8893C01F14E69C13ACBC38548896585C2467E9DF6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
17
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.179:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.179:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4244 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1532 | WINWORD.EXE | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |