| File name: | abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.zip |
| Full analysis: | https://app.any.run/tasks/681957d3-b118-4afd-8327-b128190e4a0c |
| Verdict: | Malicious activity |
| Threats: | NetSupport RAT is a malicious adaptation of the legitimate NetSupport Manager, a remote access tool used for IT support, which cybercriminals exploit to gain unauthorized control over systems. It has gained significant traction due to its sophisticated evasion techniques, widespread distribution campaigns, and the challenge it poses to security professionals who must distinguish between legitimate and malicious uses of the underlying software. |
| Analysis date: | April 24, 2025, 14:11:37 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 8F677B45F97B69835B2C89E18308FB43 |
| SHA1: | 15781F5AE515D445283BA0B3B0374F0E9B92CDB0 |
| SHA256: | 1538874C34CEB5291701813EE728CC797E3837F133F8786D375BB79FC4785594 |
| SSDEEP: | 98304:n4VKTZgkrdif8zb80oQ07w2lv8/VVIqxoTMGX4CPAhSiSjtVB6SjaloPNY7l2BdC:0baAJ1fpGx |
MALICIOUS
RAT has been found (auto)
- WinRAR.exe (PID: 5576)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5576)
- abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe (PID: 7652)
Executes application which crashes
- abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe (PID: 7652)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 5576)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5576)
Checks supported languages
- abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe (PID: 7652)
Creates files or folders in the user directory
- WerFault.exe (PID: 7892)
Reads the machine GUID from the registry
- abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe (PID: 7652)
Checks proxy server information
- abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe (PID: 7652)
Reads the software policy settings
- abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe (PID: 7652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:04:24 14:10:02 |
| ZipCRC: | 0xc3b36a14 |
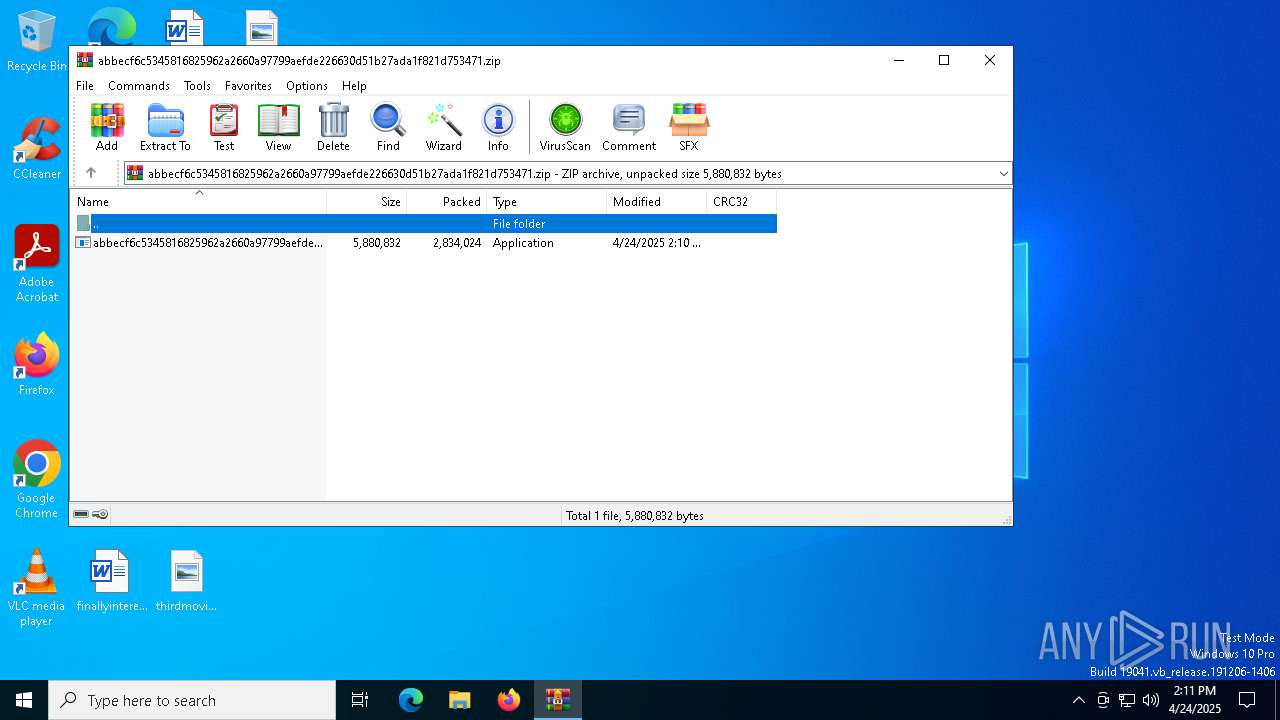
| ZipCompressedSize: | 2834024 |
| ZipUncompressedSize: | 5880832 |
| ZipFileName: | abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe |
Total processes
134
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5576 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7652 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb5576.23153\abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb5576.23153\abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe | WinRAR.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Updater Exit code: 3221226356 Version: 135.0.7023.0 Modules
| |||||||||||||||
| 7892 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7652 -s 1320 | C:\Windows\SysWOW64\WerFault.exe | — | abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 867
Read events
6 855
Write events
12
Delete events
0
Modification events
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.zip | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7652) abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
1
Suspicious files
0
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7892 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_abbecf6c53458168_8e5e5554b722d3d3f8a6825f6aaa9847fe82b5c_c4bf129a_c3abb4cb-6d8a-4b80-b74b-5761e6079ea5\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7892 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER3259.tmp.WERInternalMetadata.xml | xml | |
MD5:C0A38E3DEB79C4181B42F10A9D50393D | SHA256:1809D6BE87465E1022315E4A2620BE3E9C44CAB1EF0206DE9204278E66DBA276 | |||
| 7892 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe.7652.dmp | dmp | |
MD5:4864629662C7FCEFC6899B4720EB739B | SHA256:8CD18D79949C5F79BC0B5D82DC745932DCA7D866FD0165CAD022AC6DA45839D0 | |||
| 5576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb5576.23153\abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe | executable | |
MD5:1D8923D191850A2E38A3519432719BA6 | SHA256:ABBECF6C5345816825962A2660A97799AEFDE226630D51B27ADA1F821D753471 | |||
| 7892 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER2FA8.tmp.dmp | dmp | |
MD5:D74DE93BC8BD55194FBA2801E08C990B | SHA256:B259AB289AA9FD69E2E95EB174572653048F02E6252661512722BF0791EBF484 | |||
| 7892 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER3325.tmp.xml | xml | |
MD5:150F3AA44AEDDB8142FC045F6B40E79A | SHA256:CFE7AB7FEECDD27A4684C389BA7831A445333AE7F8B89E625F1998AE9C387A9A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
23
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7652 | abbecf6c5345816825962a2660a97799aefde226630d51b27ada1f821d753471.exe | GET | 404 | 98.124.224.17:80 | http://akkuat.com/ara/araarc/1ara1.zip | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7768 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7768 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
akkuat.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |