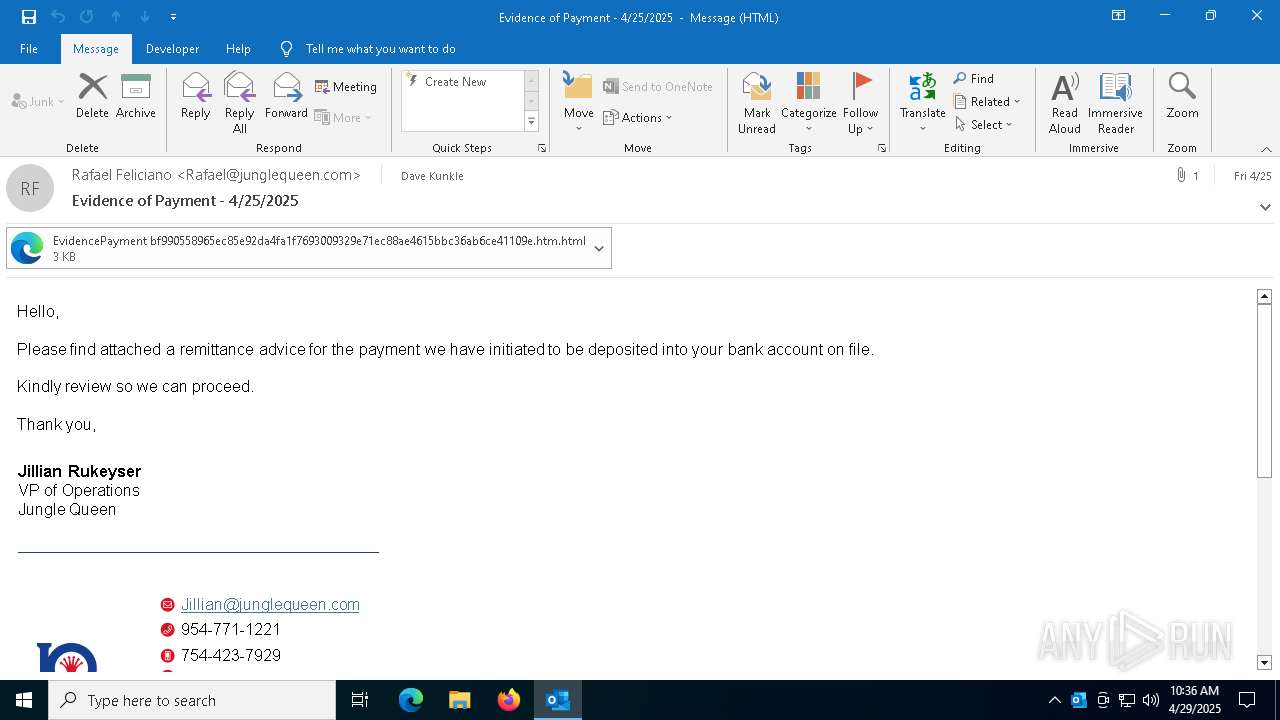
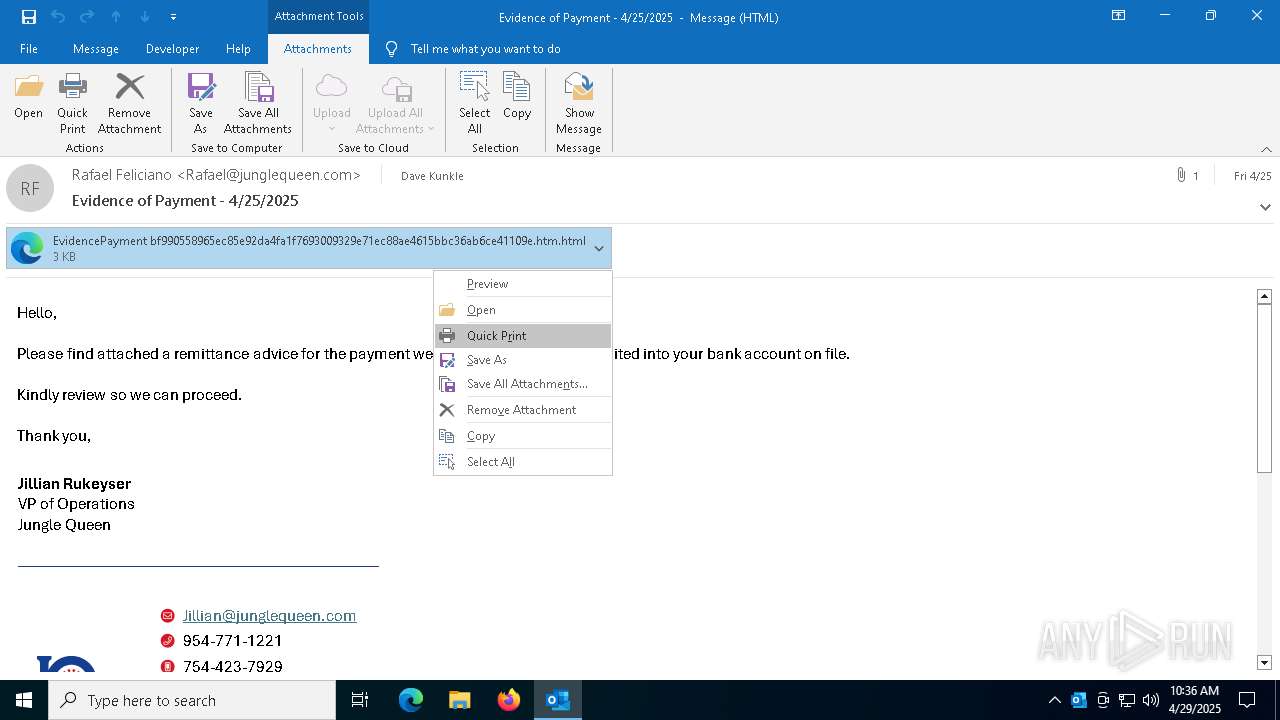
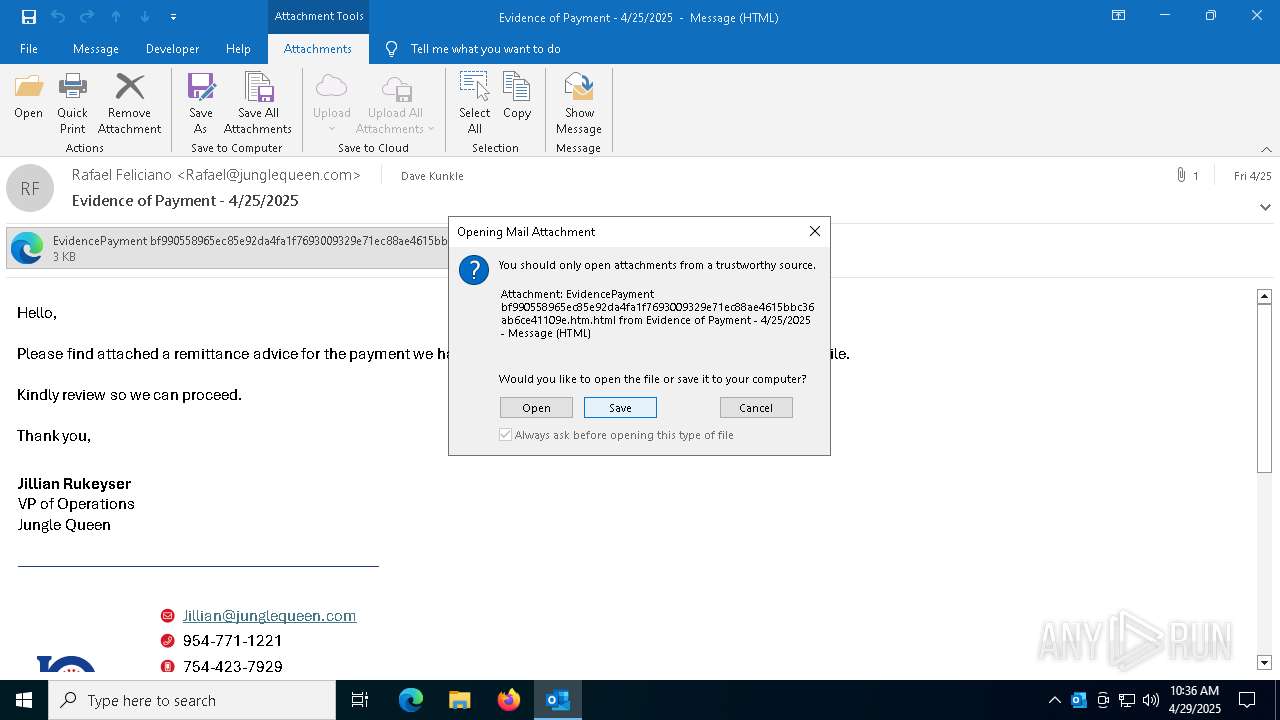
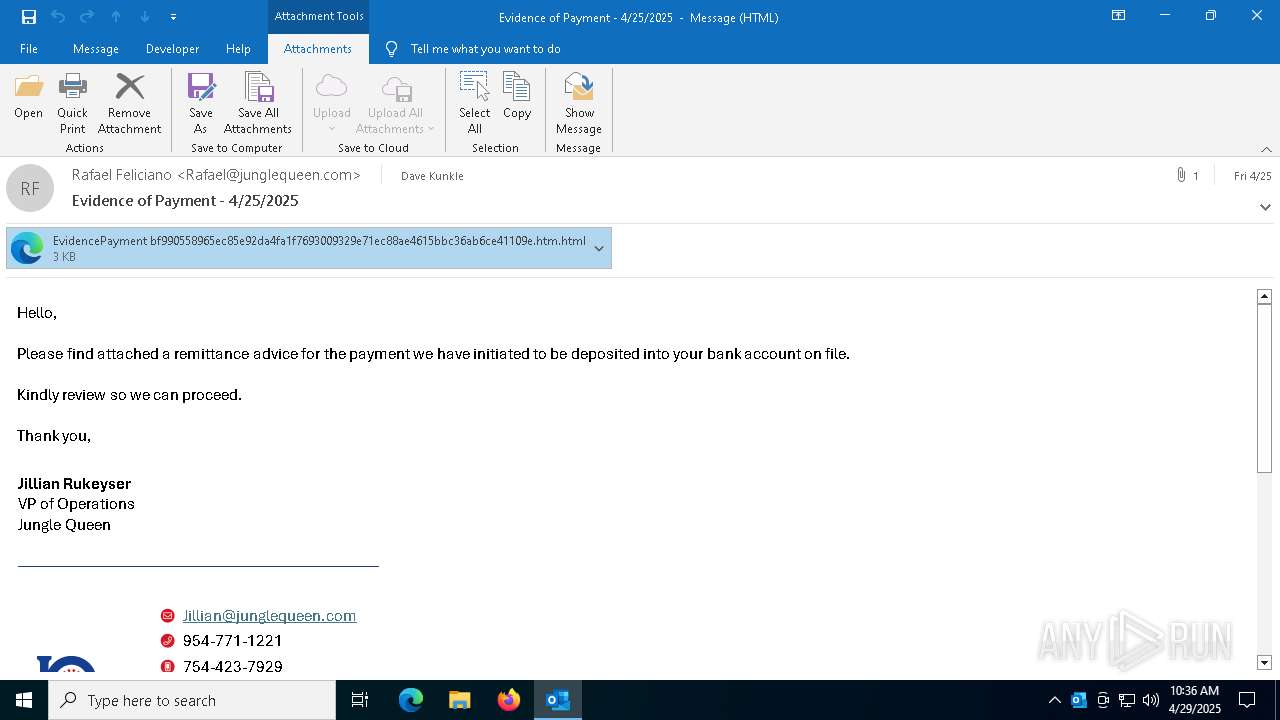
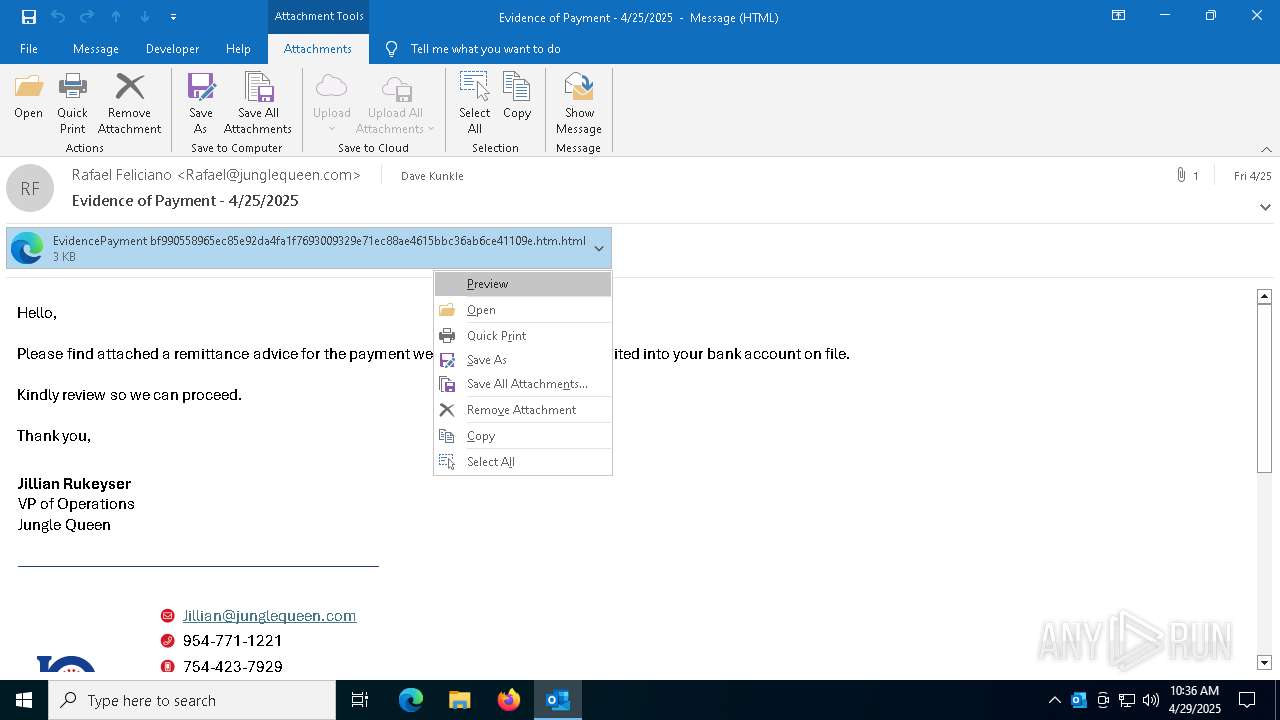
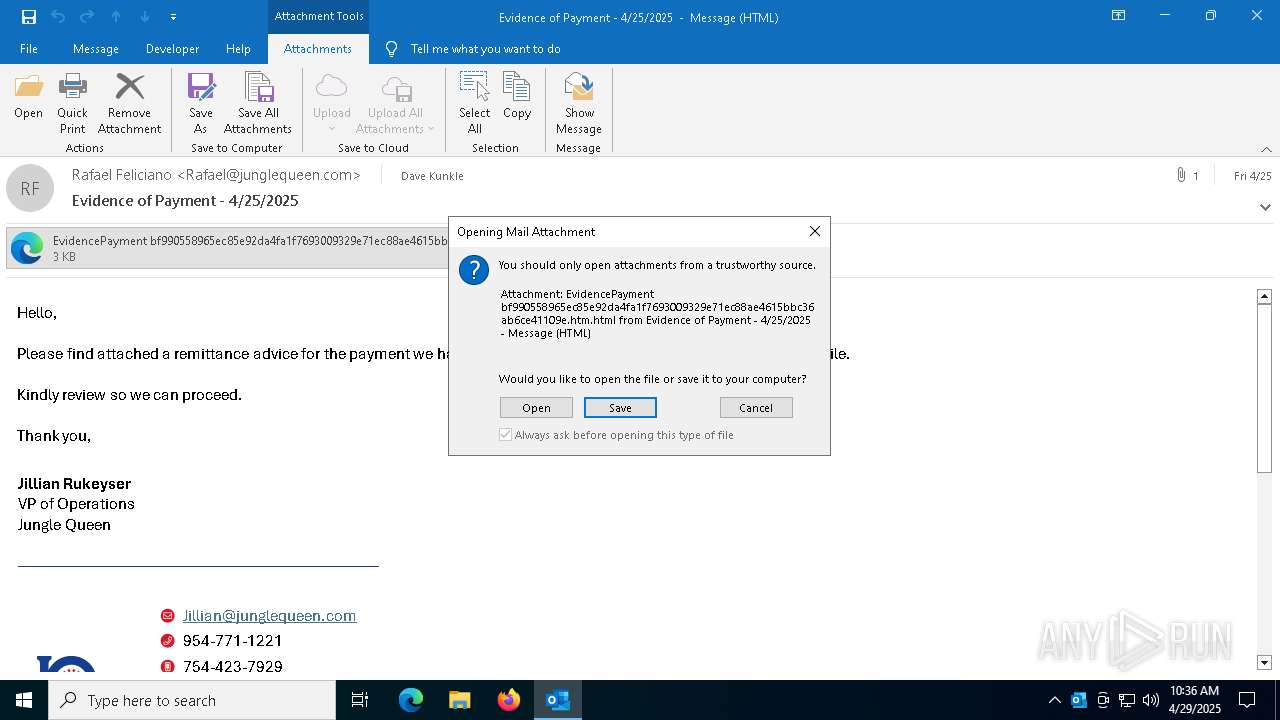
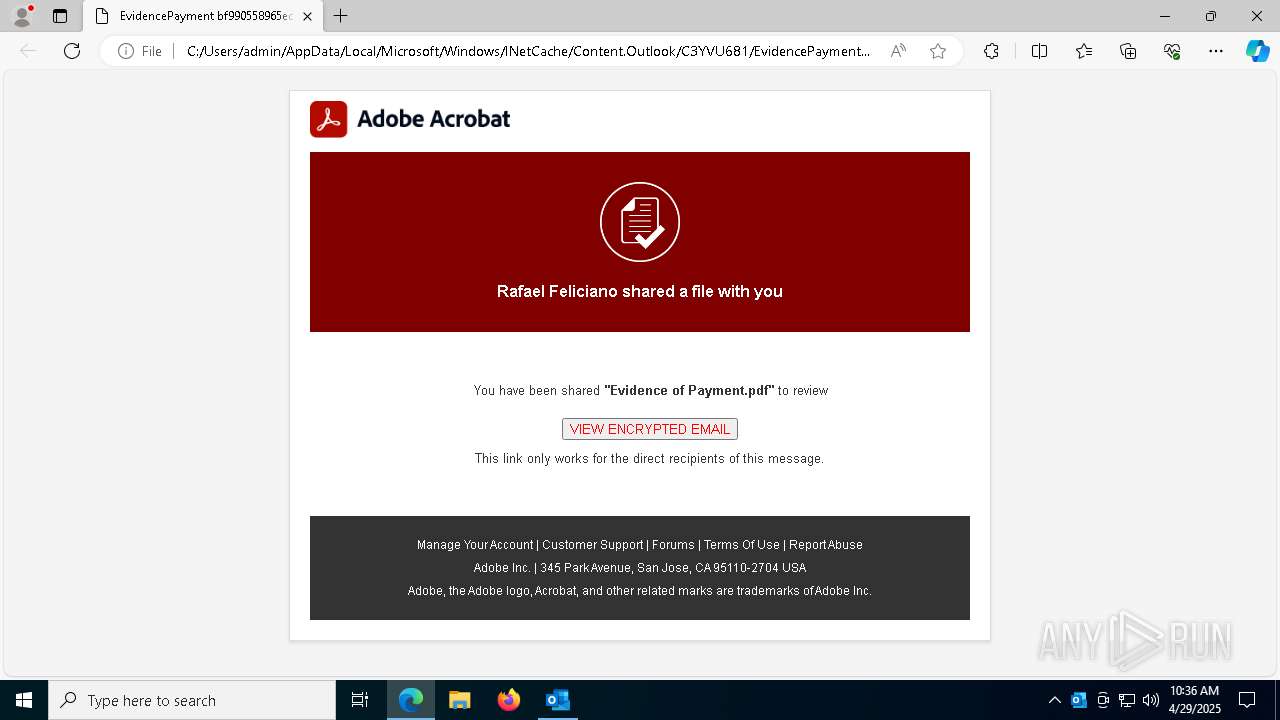
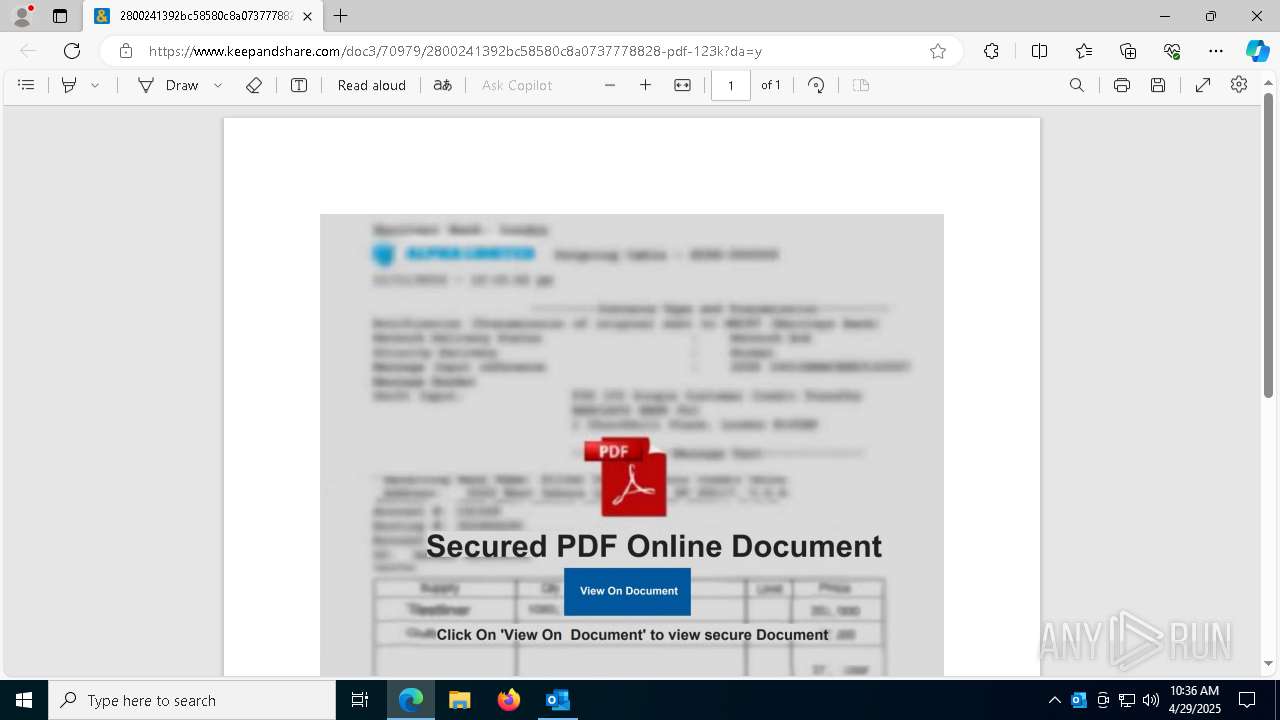
| File name: | phish_alert_sp2_2.0.0.0.eml |
| Full analysis: | https://app.any.run/tasks/fdc0abea-c9f2-4724-9b15-1588ed4d3261 |
| Verdict: | Malicious activity |
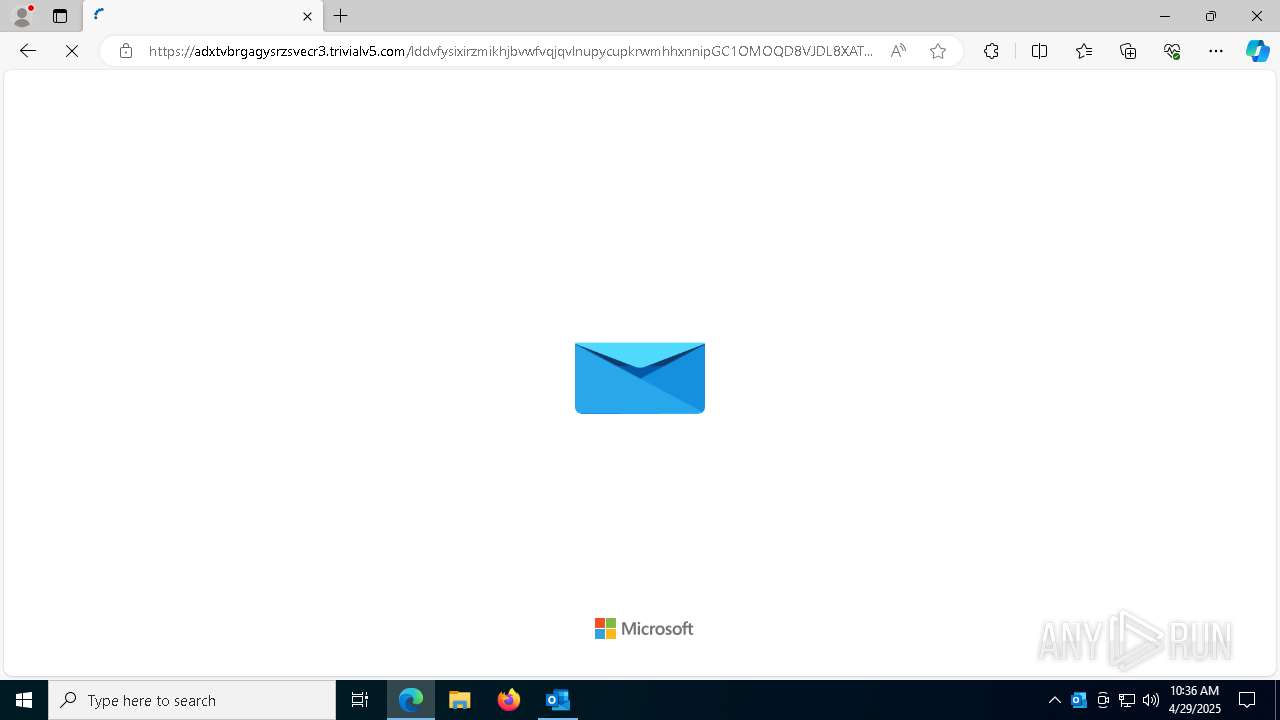
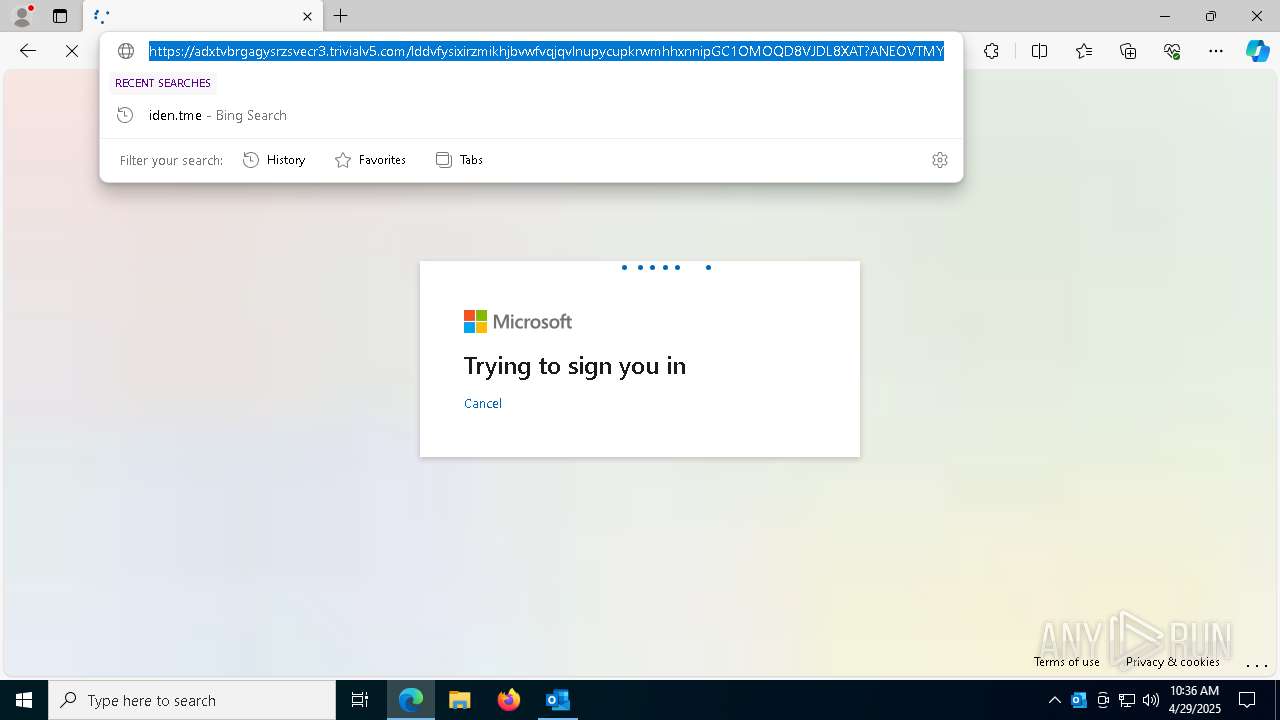
| Threats: | Tycoon 2FA is a phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts. Its advanced evasion techniques and modular architecture make it a significant threat to organizations relying on MFA for security. |
| Analysis date: | April 29, 2025, 10:36:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines (2285), with CRLF line terminators |
| MD5: | A14938E2602B88F398B0B9847E0AE735 |
| SHA1: | C348E68F4C6C197F1ABA2487DF497682753923CE |
| SHA256: | 151EC789BDD10EDB92B2CCEB673495BED15DB3487362B60A0FF68413EE739E42 |
| SSDEEP: | 768:GBfWAFZ0JYXNBm6EJva2HE8QyzQj0HwTbwSWtFBMPf2qSRjTyFJOsjRLury6jrme:GFdFmJYXVca2HEozQ6eDyFkVSRjTtsj4 |
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 2152)
SUSPICIOUS
Unnecessary Base64 encoding in Email Subject
- OUTLOOK.EXE (PID: 7472)
Email with suspicious attachment
- OUTLOOK.EXE (PID: 7472)
INFO
Email with attachments
- OUTLOOK.EXE (PID: 7472)
Application launched itself
- msedge.exe (PID: 5968)
Checks supported languages
- identity_helper.exe (PID: 6136)
Reads the computer name
- identity_helper.exe (PID: 6136)
Reads Environment values
- identity_helper.exe (PID: 6136)
Checks proxy server information
- slui.exe (PID: 6744)
Reads the software policy settings
- slui.exe (PID: 6744)
- slui.exe (PID: 8012)
The sample compiled with english language support
- msedge.exe (PID: 6072)
Executable content was dropped or overwritten
- msedge.exe (PID: 6072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
210
Monitored processes
67
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4256 --field-trial-handle=2432,i,16761772018503516287,12118624373303696870,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 672 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1508 --field-trial-handle=2432,i,16761772018503516287,12118624373303696870,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 672 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 856 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=26 --mojo-platform-channel-handle=3548 --field-trial-handle=2432,i,16761772018503516287,12118624373303696870,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6320 --field-trial-handle=2432,i,16761772018503516287,12118624373303696870,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x300,0x304,0x308,0x2f8,0x310,0x7ffc899e5fd8,0x7ffc899e5fe4,0x7ffc899e5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2040 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6796 --field-trial-handle=2432,i,16761772018503516287,12118624373303696870,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2152 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2488 --field-trial-handle=2432,i,16761772018503516287,12118624373303696870,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2192 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=25 --mojo-platform-channel-handle=3804 --field-trial-handle=2432,i,16761772018503516287,12118624373303696870,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2316 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5920 --field-trial-handle=2432,i,16761772018503516287,12118624373303696870,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
21 409
Read events
20 101
Write events
1 152
Delete events
156
Modification events
| (PID) Process: | (7472) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (7472) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\7472 |
| Operation: | write | Name: | 0 |
Value: 0B0E10F9DF3A9B7E4C6B46AD53B23C18B9FB7E230046FE9BE5D9A89EEEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B03AD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7472) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (7472) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (7472) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7472) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (7472) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (7472) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (7472) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (7472) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
11
Suspicious files
399
Text files
98
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7472 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7472 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:32C1726D2A17C4C1CF839272014A4E7F | SHA256:5CF5719F0B9B3526DA38F4B08FF3F1A160ADC1CFC3867160BAF84560D48E3C15 | |||
| 7472 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\AFC5736E.dat | image | |
MD5:620D8F2D16DFCA0C90F580EC57675920 | SHA256:FFAAE4835224D184DEBA165E05061CDACB5873616DFC952D5AC65EBE60DE5C95 | |||
| 7472 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\CD11D104-2877-4351-9F23-8117A84F9C77 | xml | |
MD5:F2730C01321265FCF5E2872736FE88AA | SHA256:3ACB9F960A186D7A96EF05CCBC0F41AC6A6697D2AC6127D8CA7CD4FE1A6197AE | |||
| 7472 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:2951D70AA10AF3123F60D13AE1ECD806 | SHA256:FFABF07560BD4652A4C79B3C8DE79707F9CCECEECDCD12787604CC192678824E | |||
| 7472 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\381E3DBD.dat | image | |
MD5:06F16C47D7199B4D34CCFAF6C9734B6D | SHA256:B9BDE3E44A95A3E2D4470548E4A5E8F15E8D2D3E35A6E1D48087267CDB385BF7 | |||
| 7472 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:F88433F3FB554A74DD722327D9E1EA28 | SHA256:6DD502146ECA9856F4A566A8C80F9B952C28F6B55BB90C179FB3FC95C00EB012 | |||
| 7472 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\DEC2B097.dat | image | |
MD5:FFBFE5A3E86702666C105D1125201048 | SHA256:0E5F5285A6A429504C8E7847AD5088F0A5389B140F135AC8DF15789873924C24 | |||
| 7472 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\20FE21AC.dat | image | |
MD5:FA9F6F07C6B588DBE059743D22A7920E | SHA256:763B46CB08CC26795BB9D479797C4FF865DA27E50C6D4BA3AC5BD39D730C331D | |||
| 7472 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\669813D3.dat | image | |
MD5:C2DBE4D71893DCA98215359AA0B670AD | SHA256:270754BE40183FBF3E2959BE84F661C21EB15DDE1E9DC06325CC1AACCC019D6E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
126
DNS requests
124
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7472 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5008 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7472 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5008 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2332 | svchost.exe | HEAD | 200 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9530bc3d-28ec-4dca-8d8d-874a68b1b861?P1=1746514396&P2=404&P3=2&P4=S9z98uSjqz01aR9SfFGTsy8FsBpYY3rXT3789OMH3%2bpN9o%2blcm5HeDWqADVa%2bb55wW%2bfhCn21ybZkXc%2bVBgGUA%3d%3d | unknown | — | — | whitelisted |
2332 | svchost.exe | GET | 206 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9530bc3d-28ec-4dca-8d8d-874a68b1b861?P1=1746514396&P2=404&P3=2&P4=S9z98uSjqz01aR9SfFGTsy8FsBpYY3rXT3789OMH3%2bpN9o%2blcm5HeDWqADVa%2bb55wW%2bfhCn21ybZkXc%2bVBgGUA%3d%3d | unknown | — | — | whitelisted |
2332 | svchost.exe | GET | 206 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9530bc3d-28ec-4dca-8d8d-874a68b1b861?P1=1746514396&P2=404&P3=2&P4=S9z98uSjqz01aR9SfFGTsy8FsBpYY3rXT3789OMH3%2bpN9o%2blcm5HeDWqADVa%2bb55wW%2bfhCn21ybZkXc%2bVBgGUA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.180:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7472 | OUTLOOK.EXE | 52.109.89.18:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7472 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7472 | OUTLOOK.EXE | 23.212.222.21:443 | fs.microsoft.com | AKAMAI-AS | AU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2152 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2152 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2152 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain by CrossDomain ( .trivialv5 .com) |
2152 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain by CrossDomain ( .trivialv5 .com) |
2152 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2152 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2152 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2152 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2152 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
2152 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |