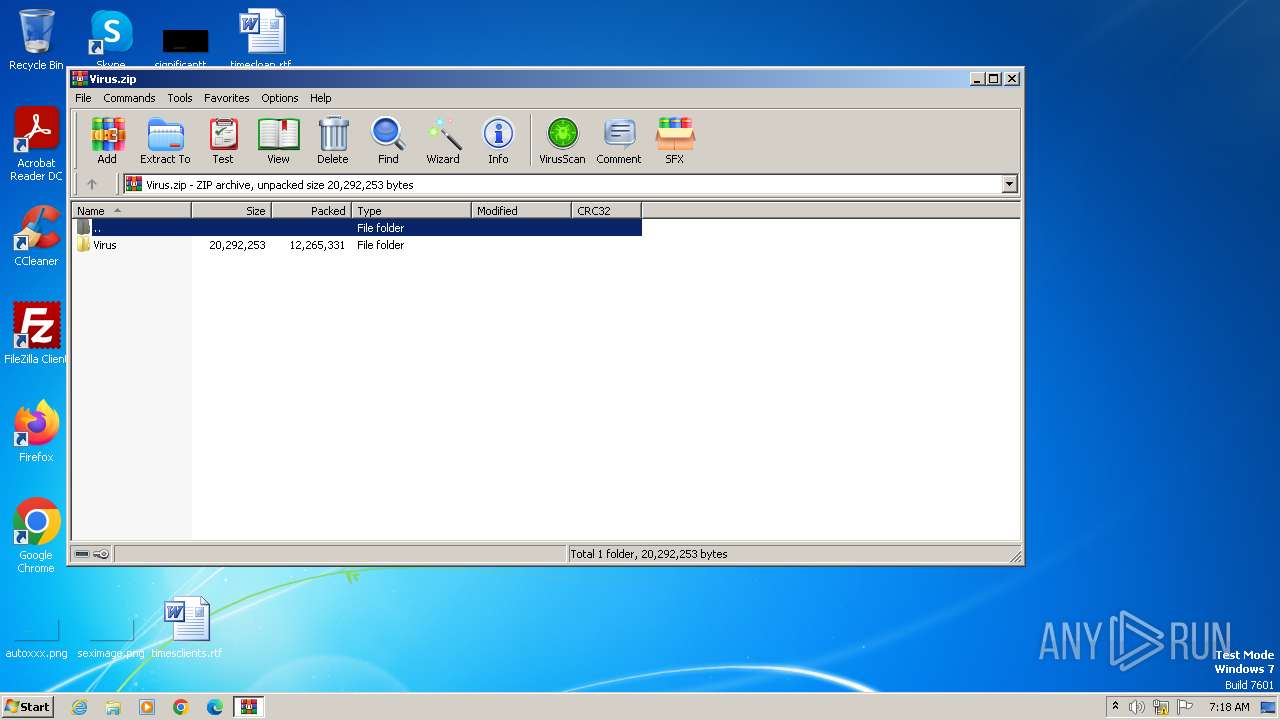
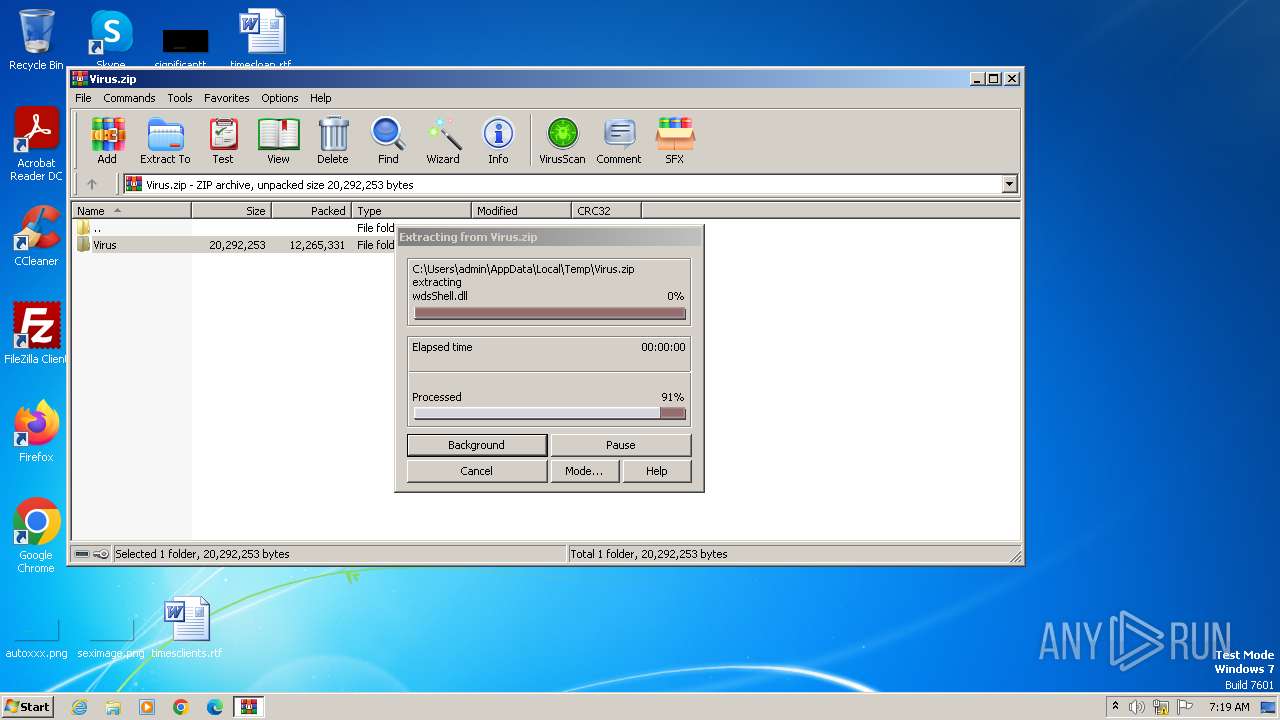
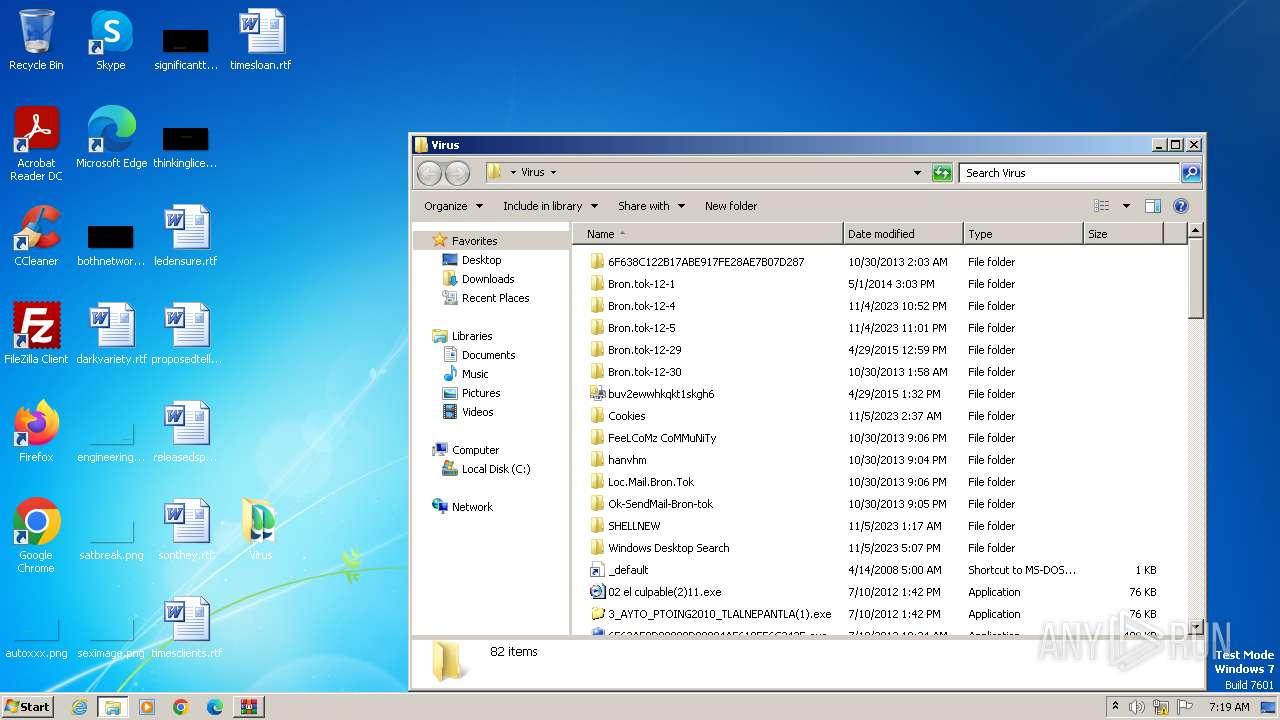
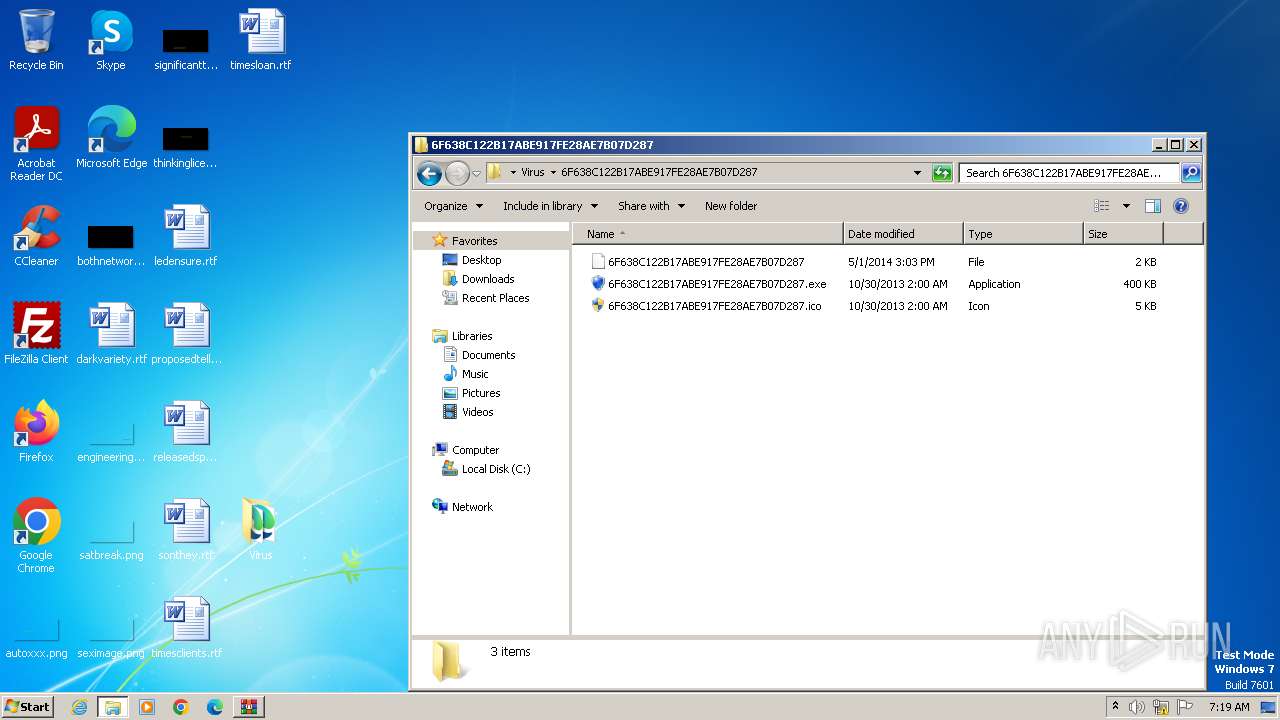
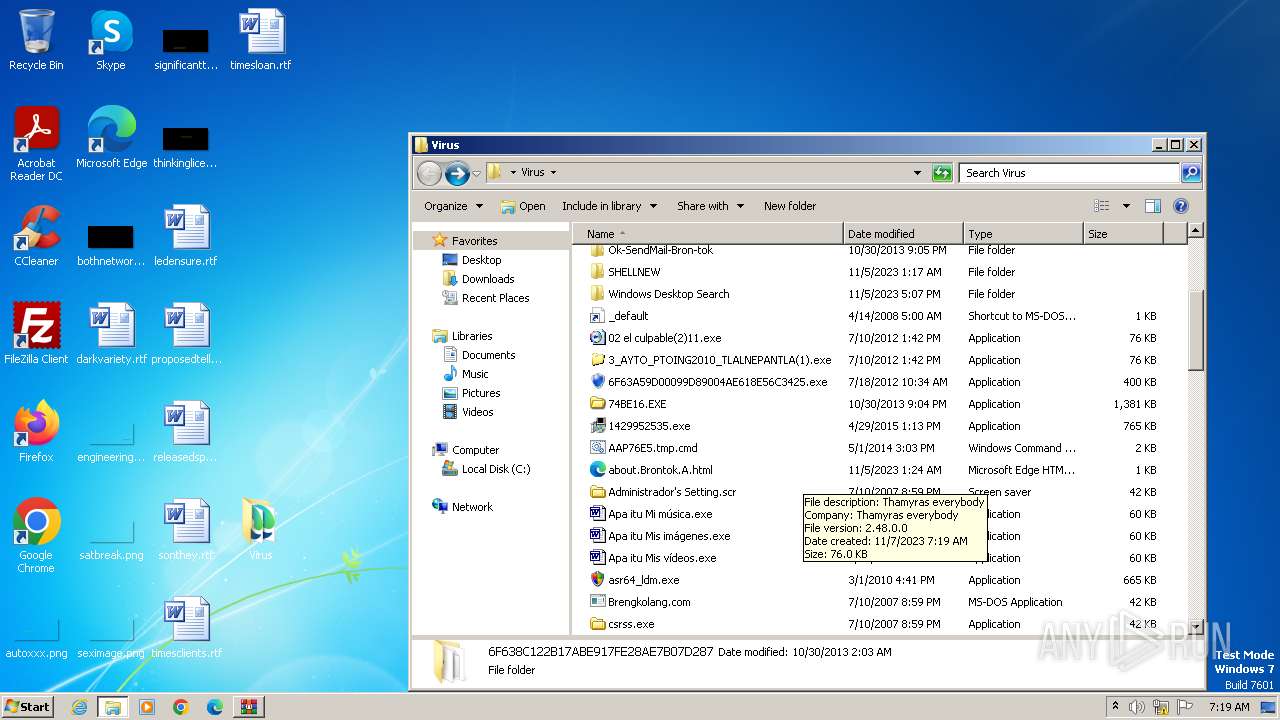
| File name: | Virus.zip |
| Full analysis: | https://app.any.run/tasks/3f0967f7-03f2-4610-8312-a0abc5c26a39 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | November 07, 2023, 07:18:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 3CA9B55E573DCC977BB1167D5A3D6FD0 |
| SHA1: | 50AE8AFE81B62BBB170523E6A3E6404F5460C1D7 |
| SHA256: | 15016FB331CEF2F2CE4FEDA5CE61B5560E7BE4CA031D0759531C9A639229FB06 |
| SSDEEP: | 98304:/dOmsMV7Q1TpfJd5DkBhMwHeqnBHAJ0wOqwHeqnBHAJ0wORXauNeeGhmXc8KH1Zs:mdgaLJLP8PGACaLOxpJQ |
MALICIOUS
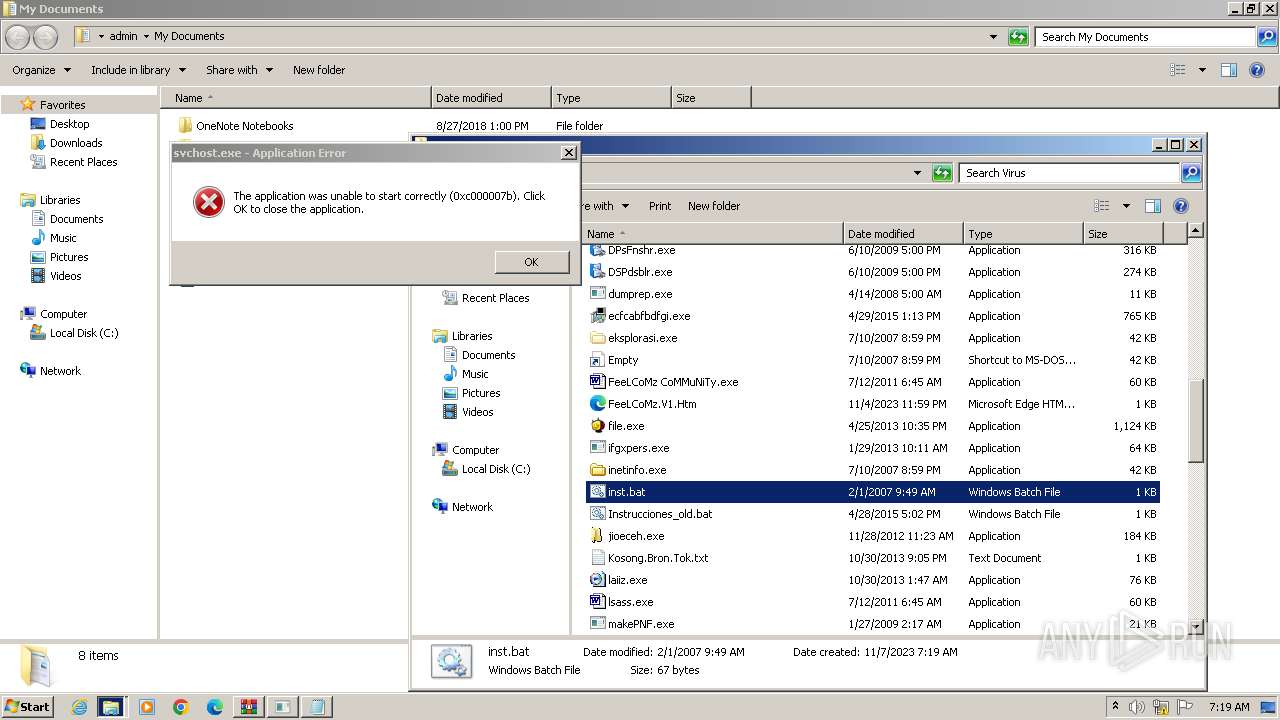
Drops the executable file immediately after the start
- 74BE16.EXE (PID: 3956)
- FeeLCoMz CoMMuNiTy.exe (PID: 2164)
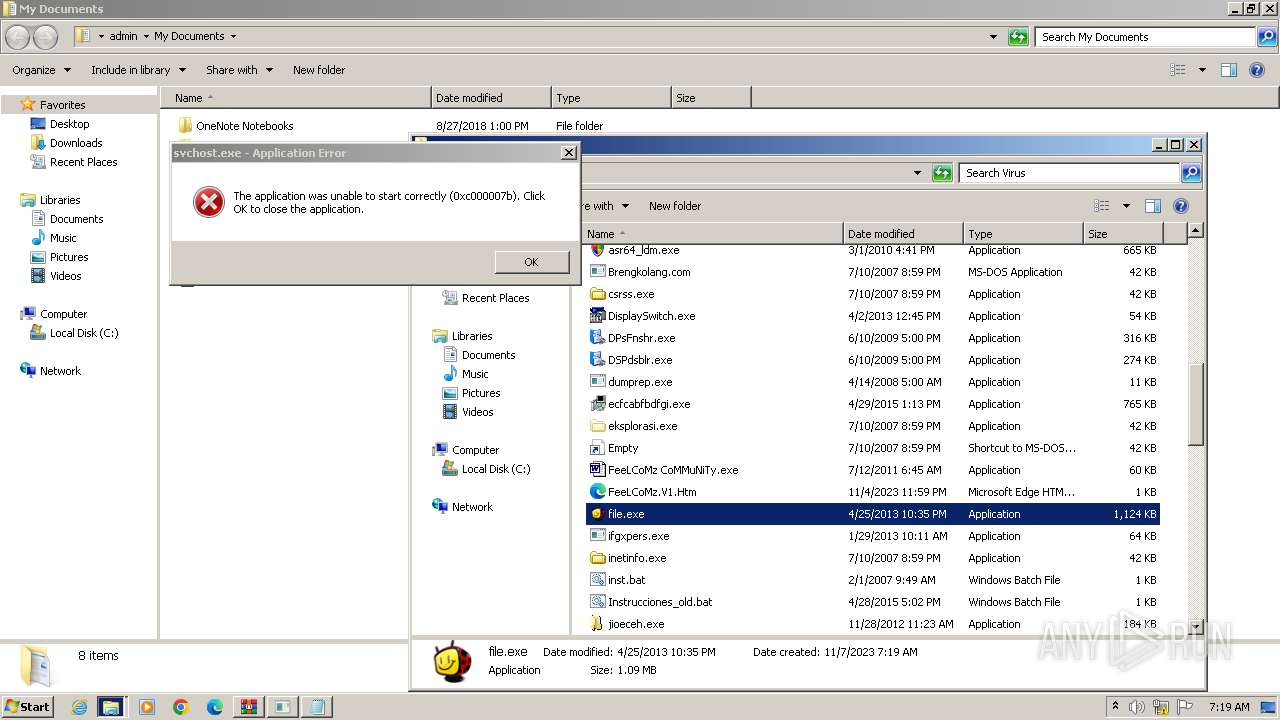
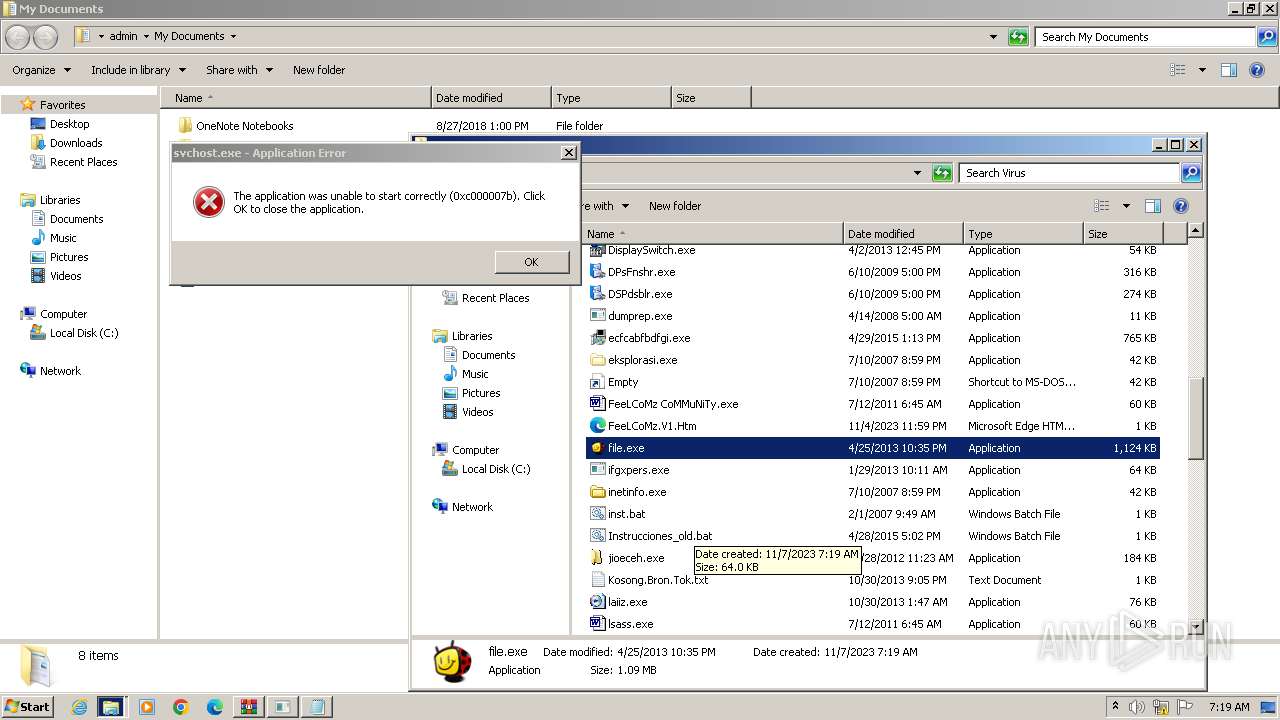
- file.exe (PID: 1612)
- file.exe (PID: 1812)
- asr64_ldm.exe (PID: 3788)
Connects to the CnC server
- asr64_ldm.exe (PID: 3788)
Create files in the Startup directory
- FeeLCoMz CoMMuNiTy.exe (PID: 2164)
Changes the login/logoff helper path in the registry
- FeeLCoMz CoMMuNiTy.exe (PID: 2164)
Changes the autorun value in the registry
- qpqpdndnn.exe (PID: 1560)
- wuauclt.exe (PID: 2324)
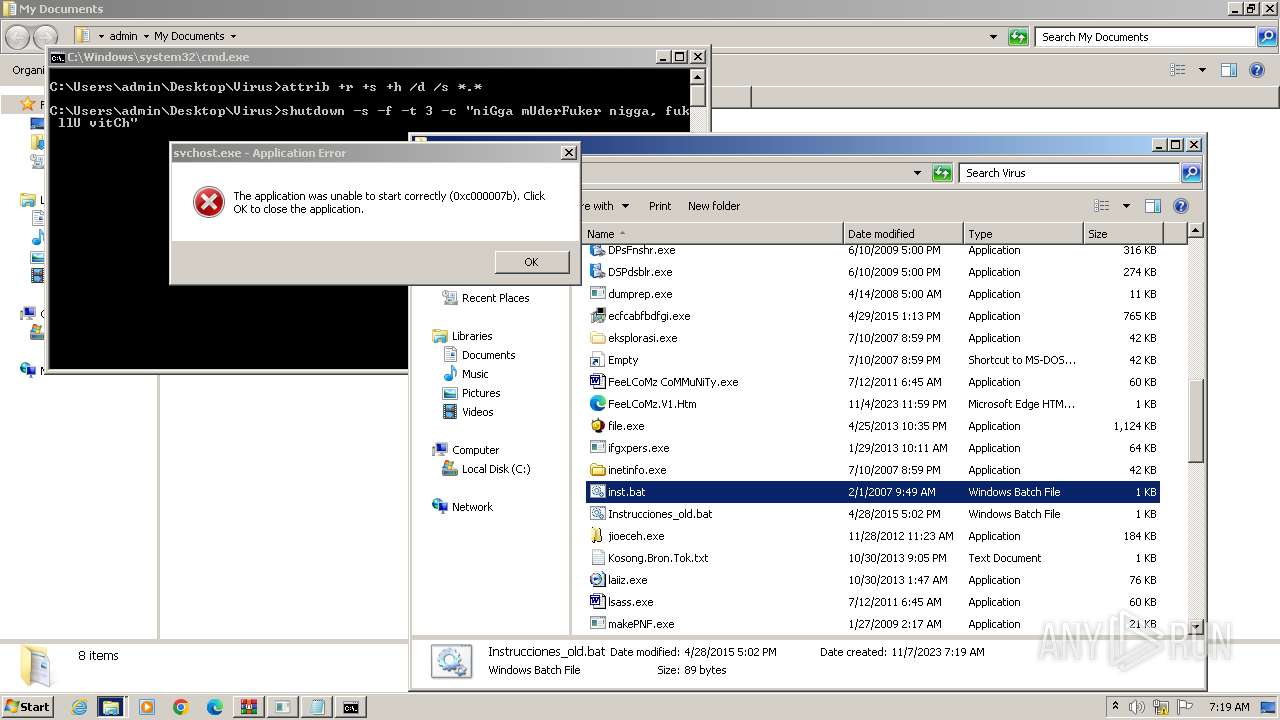
- attrib.exe (PID: 2828)
- shutdown.exe (PID: 372)
- explorer.exe (PID: 984)
- 6F638C122B17ABE917FE28AE7B07D287.exe (PID: 3944)
- regsvr32.exe (PID: 2652)
- WinRAR.exe (PID: 2928)
Starts NET.EXE for service management
- net.exe (PID: 2392)
- asr64_ldm.exe (PID: 3788)
Uses NET.EXE to stop Windows Security Center service
- net.exe (PID: 2392)
- asr64_ldm.exe (PID: 3788)
Actions looks like stealing of personal data
- wuauclt.exe (PID: 2324)
WINWEBSEC has been detected (SURICATA)
- 6F638C122B17ABE917FE28AE7B07D287.exe (PID: 3944)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 3152)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 2928)
Process drops legitimate windows executable
- WinRAR.exe (PID: 2928)
Creates executable files that already exist in Windows
- WinRAR.exe (PID: 2928)
Connects to the server without a host name
- 6F638C122B17ABE917FE28AE7B07D287.exe (PID: 3944)
- 74BE16.EXE (PID: 3956)
Reads the Internet Settings
- asr64_ldm.exe (PID: 3788)
- asr64_ldm.exe (PID: 1068)
- 74BE16.EXE (PID: 3956)
Reads security settings of Internet Explorer
- asr64_ldm.exe (PID: 3788)
Reads settings of System Certificates
- asr64_ldm.exe (PID: 3788)
Checks Windows Trust Settings
- asr64_ldm.exe (PID: 3788)
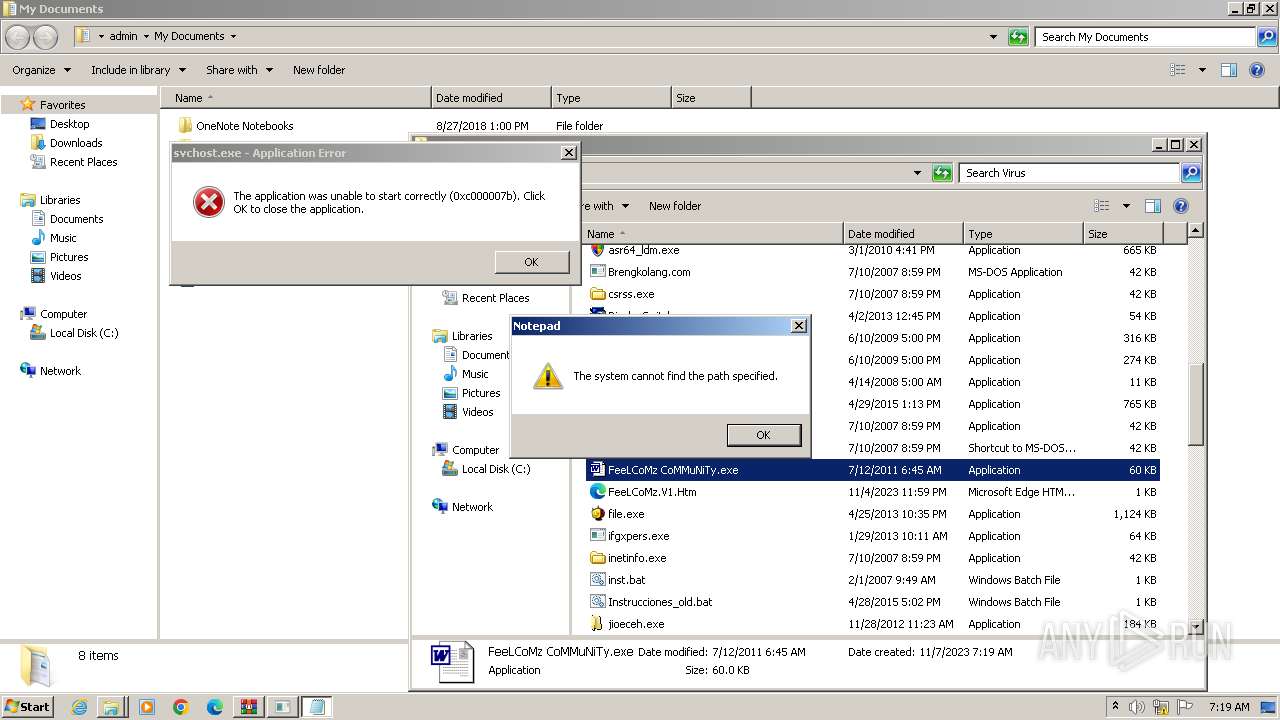
Start notepad (likely ransomware note)
- FeeLCoMz CoMMuNiTy.exe (PID: 2164)
Application launched itself
- file.exe (PID: 1880)
- file.exe (PID: 1612)
- qpqpdndnn.exe (PID: 1904)
- qpqpdndnn.exe (PID: 1560)
Starts itself from another location
- file.exe (PID: 1812)
- asr64_ldm.exe (PID: 3788)
Starts CMD.EXE for commands execution
- asr64_ldm.exe (PID: 3788)
Changes internet zones settings
- wuauclt.exe (PID: 2324)
- attrib.exe (PID: 2828)
- shutdown.exe (PID: 372)
- explorer.exe (PID: 984)
- cmd.exe (PID: 3148)
- cmd.exe (PID: 3152)
- regsvr32.exe (PID: 2652)
- 6F638C122B17ABE917FE28AE7B07D287.exe (PID: 3944)
- WinRAR.exe (PID: 2928)
Starts SC.EXE for service management
- asr64_ldm.exe (PID: 3788)
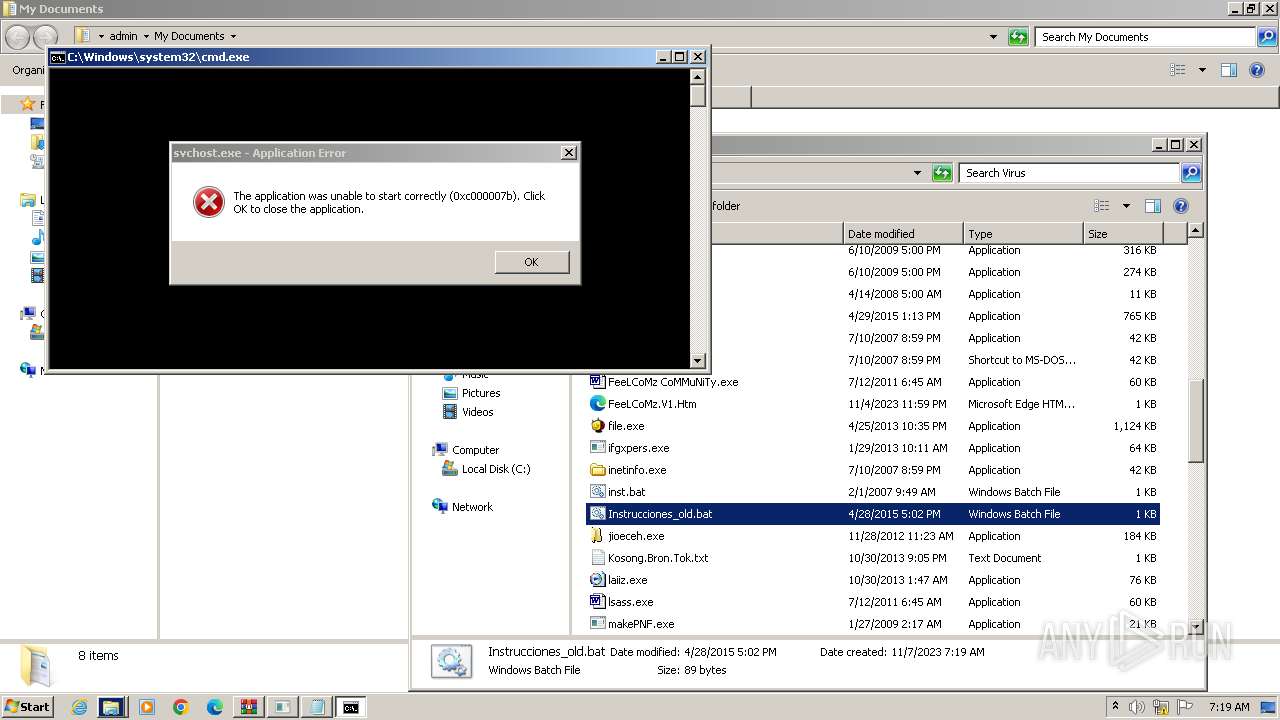
Executing commands from a ".bat" file
- asr64_ldm.exe (PID: 3788)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 328)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 328)
Reads Internet Explorer settings
- asr64_ldm.exe (PID: 1068)
Reads Microsoft Outlook installation path
- asr64_ldm.exe (PID: 1068)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3148)
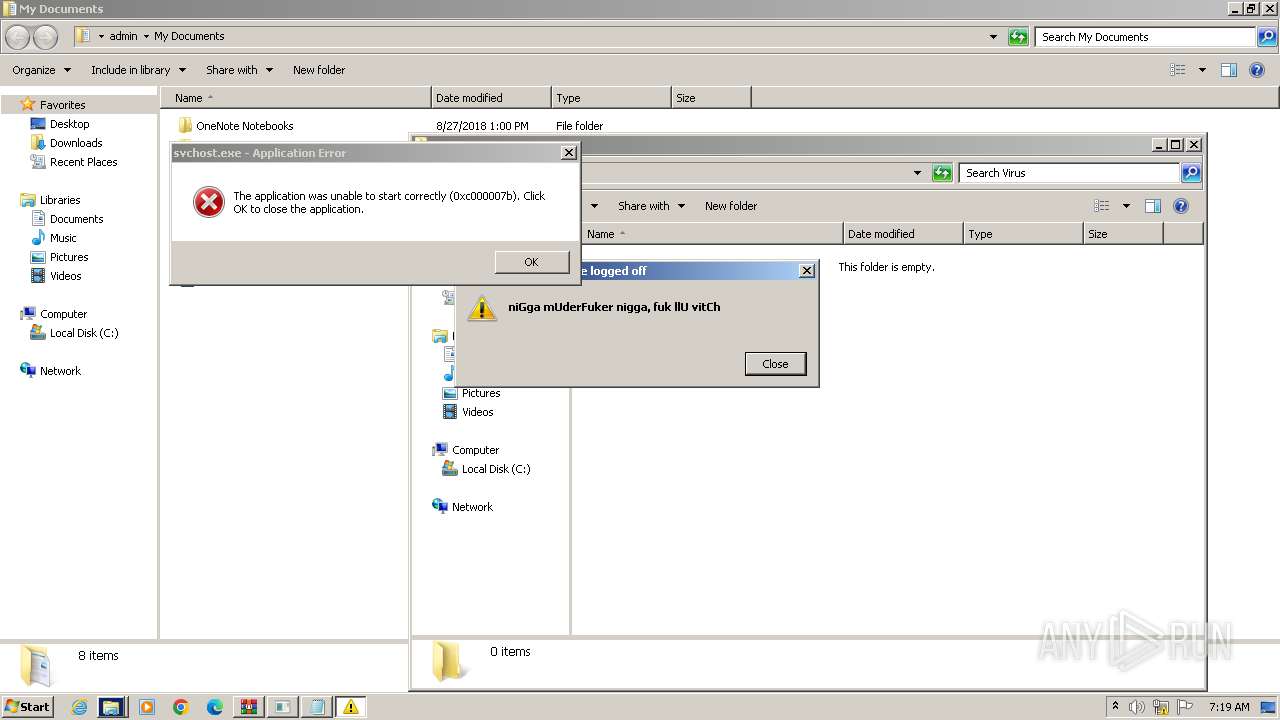
The system shut down or reboot
- cmd.exe (PID: 3148)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 3416)
- 6F638C122B17ABE917FE28AE7B07D287.exe (PID: 3944)
- 6F63A59D00099D89004AE618E56C3425.exe (PID: 3684)
- asr64_ldm.exe (PID: 3788)
- DisplaySwitch.exe (PID: 1436)
- FeeLCoMz CoMMuNiTy.exe (PID: 2164)
- file.exe (PID: 1880)
- file.exe (PID: 1612)
- file.exe (PID: 1812)
- qpqpdndnn.exe (PID: 1904)
- qpqpdndnn.exe (PID: 1560)
- qpqpdndnn.exe (PID: 2300)
- asr64_ldm.exe (PID: 1068)
- 74BE16.EXE (PID: 3956)
Reads the machine GUID from the registry
- 74BE16.EXE (PID: 3956)
- wmpnscfg.exe (PID: 3416)
- asr64_ldm.exe (PID: 3788)
- FeeLCoMz CoMMuNiTy.exe (PID: 2164)
- asr64_ldm.exe (PID: 1068)
Reads the computer name
- wmpnscfg.exe (PID: 3416)
- 6F638C122B17ABE917FE28AE7B07D287.exe (PID: 3944)
- 6F63A59D00099D89004AE618E56C3425.exe (PID: 3684)
- asr64_ldm.exe (PID: 3788)
- file.exe (PID: 1812)
- qpqpdndnn.exe (PID: 2300)
- asr64_ldm.exe (PID: 1068)
- 74BE16.EXE (PID: 3956)
Manual execution by a user
- 6F638C122B17ABE917FE28AE7B07D287.exe (PID: 3944)
- 6F63A59D00099D89004AE618E56C3425.exe (PID: 3684)
- asr64_ldm.exe (PID: 3788)
- cmd.exe (PID: 3820)
- DisplaySwitch.exe (PID: 1436)
- FeeLCoMz CoMMuNiTy.exe (PID: 2164)
- file.exe (PID: 1880)
- 74BE16.EXE (PID: 3956)
- cmd.exe (PID: 3148)
- cmd.exe (PID: 3152)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2928)
Create files in a temporary directory
- 74BE16.EXE (PID: 3956)
- FeeLCoMz CoMMuNiTy.exe (PID: 2164)
- file.exe (PID: 1612)
- qpqpdndnn.exe (PID: 1560)
- asr64_ldm.exe (PID: 3788)
Checks proxy server information
- asr64_ldm.exe (PID: 3788)
- asr64_ldm.exe (PID: 1068)
- 74BE16.EXE (PID: 3956)
Reads the Internet Settings
- explorer.exe (PID: 984)
Creates files or folders in the user directory
- FeeLCoMz CoMMuNiTy.exe (PID: 2164)
- asr64_ldm.exe (PID: 3788)
- asr64_ldm.exe (PID: 1068)
Creates files in the program directory
- file.exe (PID: 1812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2008:04:14 05:00:00 |
| ZipCRC: | 0x0d7438c2 |
| ZipCompressedSize: | 196 |
| ZipUncompressedSize: | 707 |
| ZipFileName: | Virus/_default.pif |
Total processes
91
Monitored processes
36
Malicious processes
19
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | C:\Windows\system32\cmd.exe /c C:\Users\admin\AppData\Local\Temp\test.bat | C:\Windows\System32\cmd.exe | — | asr64_ldm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1073807364 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 372 | shutdown -s -f -t 3 -c "niGga mUderFuker nigga, fuk llU vitCh" | C:\Windows\System32\shutdown.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 732 | icacls C:\Windows\system32\wscui.cpl /grant administrators:F | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 984 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1068 | "C:\Users\admin\AppData\Local\Temp\asr64_ldm.exe" | C:\Users\admin\AppData\Local\Temp\asr64_ldm.exe | asr64_ldm.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: HIGH Description: Logical Disk Manager ASR Utility Exit code: 1073807364 Version: 2600.0.503.0 Modules
| |||||||||||||||
| 1228 | takeown /f C:\Windows\system32\wscui.cpl | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Takes ownership of a file Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | Notepad.exe C:\Windows\FeeLCoMz\FeeLCoMz CoMMuNiTy.txt | C:\Windows\System32\notepad.exe | — | FeeLCoMz CoMMuNiTy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1436 | "C:\Users\admin\Desktop\Virus\DisplaySwitch.exe" | C:\Users\admin\Desktop\Virus\DisplaySwitch.exe | — | explorer.exe | |||||||||||
User: admin Company: Корпорация Майкрософт Integrity Level: MEDIUM Description: Конвертор групп диспетчера программ Windows Exit code: 0 Version: 5.1.2600.5512 (xpsp.080413-2105) Modules
| |||||||||||||||
| 1560 | "C:\ProgramData\buv2ewwhkqkt1skgh60\qpqpdndnn.exe" | C:\ProgramData\buv2ewwhkqkt1skgh60\qpqpdndnn.exe | qpqpdndnn.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1608 | explorer C:\Users\admin\Desktop\Virus\74BE16 | C:\Windows\explorer.exe | — | 74BE16.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
11 061
Read events
10 890
Write events
168
Delete events
3
Modification events
| (PID) Process: | (3416) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{D778FB0E-B10B-4535-A09E-630BBE9CEFB4}\{857FCC3A-0568-40B3-BF83-E5A324CC6E41} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3416) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{D778FB0E-B10B-4535-A09E-630BBE9CEFB4} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3416) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{CF6B7DA6-DD6D-4944-A393-9639369FCADE} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2928) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
119
Suspicious files
9
Text files
54
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.2855\Virus\02 el culpable(2)11.exe | executable | |
MD5:AB2C5D3C4BD6615301A767B9FE9046DF | SHA256:0FD6A7B40D3D324BF84827EE1BE8F336D339A9778AAE4A900B565B34AD31719C | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.2855\Virus\6F638C122B17ABE917FE28AE7B07D287\6F638C122B17ABE917FE28AE7B07D287 | binary | |
MD5:8819E6E359C933C6D2C9BD2A5ECFCEE9 | SHA256:B5032B298FE9052B9738F06757729EE17D9DE3F9C7CDBD431C2BB1D6D96F56DB | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.2855\Virus\buv2ewwhkqkt1skgh6.{2227A280-3AEA-1069-A2DE-08002B30309D}\bbnlmyqqs.exe | executable | |
MD5:F752133B5028B28DA8725A7E684EB7D1 | SHA256:1FDFA134673813CFA0EB87F8442322D9391D7C28BA7F162124A74AD7BC5537F8 | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.2855\Virus\asr64_ldm.exe | executable | |
MD5:EC27DCA4E5B59C91E3291DFCDBE2F8BA | SHA256:02FA72881A596B75820BE43E9E94AE71ED1B0D8E773A507B79019F1FA41DFDF0 | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.2855\Virus\1429952535.exe | executable | |
MD5:17D34AB78A0C4146046C72FA59F9245F | SHA256:AEA5837BFFCB59FD382D14F4C4A6E96CF8099A2650FDCF709E7CB9735A0275DC | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.2855\Virus\6F63A59D00099D89004AE618E56C3425.exe | executable | |
MD5:D8103D27E795B9753DF3239AB804B03E | SHA256:4315838DBAD913ADD8E05A1044CFB85D72E472FD65664F198EB841B0F831AC25 | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.2855\Virus\6F638C122B17ABE917FE28AE7B07D287\6F638C122B17ABE917FE28AE7B07D287.ico | image | |
MD5:EF6B46F858745A383AEAD66FBC674763 | SHA256:DE6E0C84C97C14E51667447AB59B9A83DC7517DF0D48D8F72D58729107BF8BC7 | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.2855\Virus\74BE16.EXE | executable | |
MD5:65A8F67B004575C3B3D153860BADB665 | SHA256:1019A6D31B4BF33A3C93A282D42B9CD196D8F4BF77526587EA3392D35B849981 | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.2855\Virus\Brengkolang.com | executable | |
MD5:483FCF432217D71544246AA760D98CDC | SHA256:70D98B736C32160617E8E272C2F5B2C10C72789FE40E27EC16F94FFA09394CD7 | |||
| 2928 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2928.2855\Virus\Apa itu Mis imágenes.exe | executable | |
MD5:6C08BD41F70D51662DF04EB4ECD2F9EE | SHA256:D24596A87B810ED934078EB7F474973FDE52DD4866C9114BE2E53E720C118750 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
23
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3956 | 74BE16.EXE | GET | — | 193.104.27.98:80 | http://193.104.27.98/2krn.bin | unknown | — | — | unknown |
3788 | asr64_ldm.exe | GET | 302 | 3.130.204.160:80 | http://Beinahe.com/readdatagateway.php?type=stats&affid=139&subid=1&version=3.0&adwareok | unknown | — | — | unknown |
3788 | asr64_ldm.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/Omniroot2025.crl | unknown | binary | 7.94 Kb | unknown |
3944 | 6F638C122B17ABE917FE28AE7B07D287.exe | GET | 404 | 112.121.178.189:80 | http://112.121.178.189/api/urls/?ts=e711e20e&affid=46200 | unknown | html | 146 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3944 | 6F638C122B17ABE917FE28AE7B07D287.exe | 112.121.178.189:80 | — | Netsec Limited | HK | unknown |
3956 | 74BE16.EXE | 193.104.27.98:80 | — | MTS PJSC | RU | unknown |
3788 | asr64_ldm.exe | 3.130.204.160:80 | beinahe.com | AMAZON-02 | US | unknown |
3788 | asr64_ldm.exe | 104.26.7.37:443 | www.hugedomains.com | CLOUDFLARENET | US | shared |
3788 | asr64_ldm.exe | 192.229.221.95:80 | crl3.digicert.com | EDGECAST | US | whitelisted |
2324 | wuauclt.exe | 20.72.235.82:80 | update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fast-online.org |
| unknown |
beinahe.com |
| unknown |
www.hugedomains.com |
| whitelisted |
ctldl.windowsupdate.com |
| unknown |
ocsp.digicert.com |
| unknown |
crl3.digicert.com |
| whitelisted |
update.microsoft.com |
| whitelisted |
steroids-buy-anabolic.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3944 | 6F638C122B17ABE917FE28AE7B07D287.exe | Unknown Traffic | ET HUNTING Suspicious Empty User-Agent |
3788 | asr64_ldm.exe | A Network Trojan was detected | ET MALWARE Fake AV GET |
3788 | asr64_ldm.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP RogueAntiSpyware.AntiVirusPro Checkin |
3788 | asr64_ldm.exe | A Network Trojan was detected | ET USER_AGENTS Long Fake wget 3.0 User-Agent Detected |
3788 | asr64_ldm.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Fake Wget User-Agent (wget 3.0) - Likely Hostile |
3956 | 74BE16.EXE | A Network Trojan was detected | ET MALWARE Zbot Generic URI/Header Struct .bin |
3956 | 74BE16.EXE | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
asr64_ldm.exe | C:\Users\admin\AppData\Roaming\Dr. Guard\drguard.exe |
asr64_ldm.exe | C:\Program Files\Dr. Guard\drguard.exe |
asr64_ldm.exe | C:\Users\admin\AppData\Roaming\Dr. Guard\drguard.exe |
asr64_ldm.exe | C:\Program Files\Dr. Guard\drguard.exe |