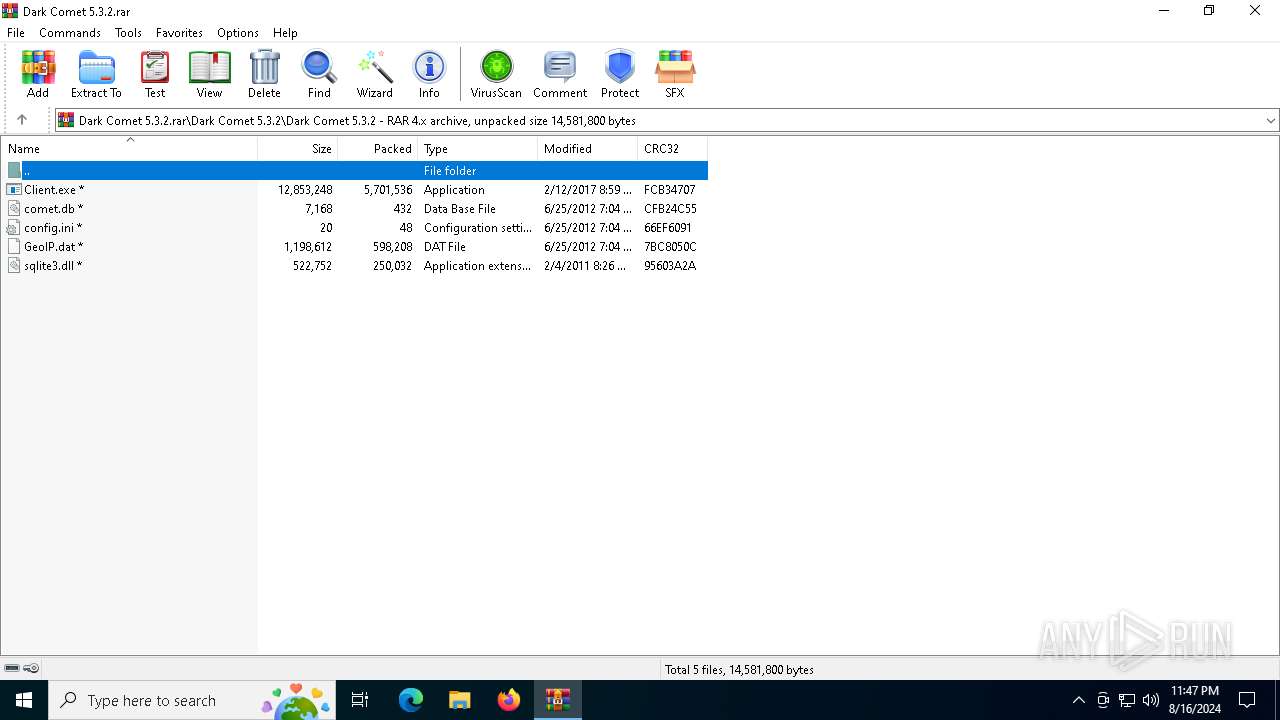
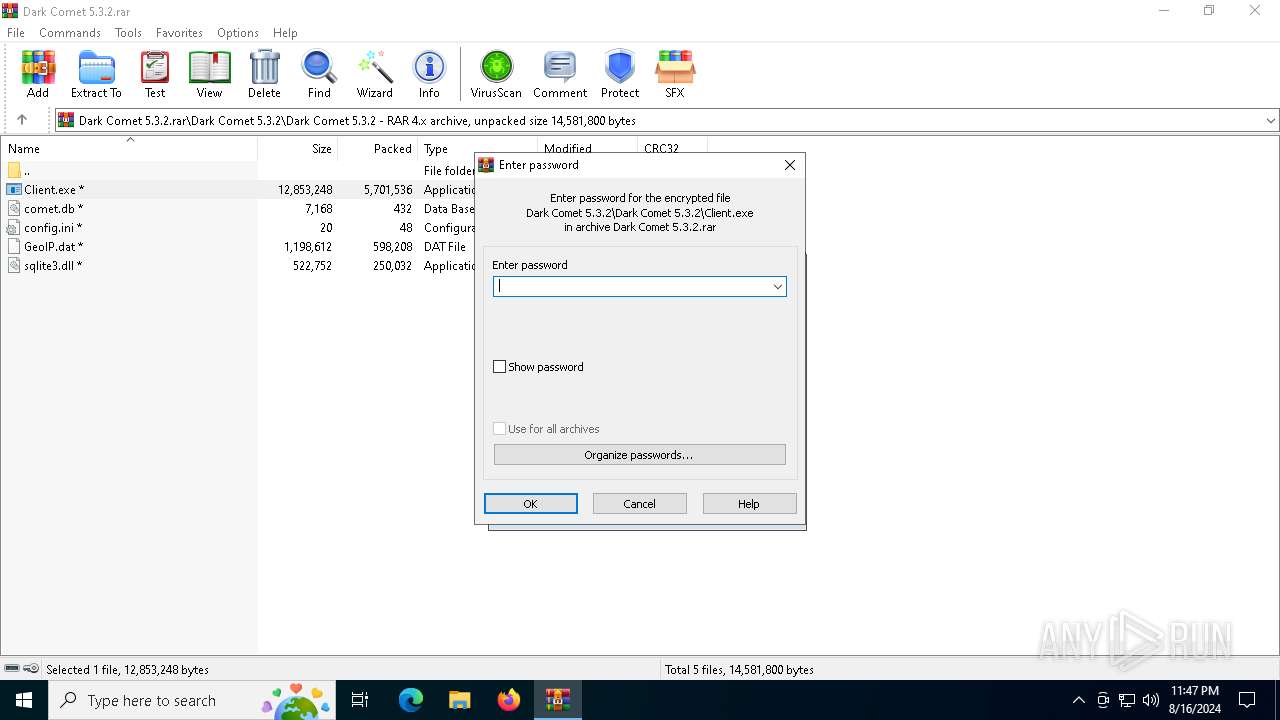
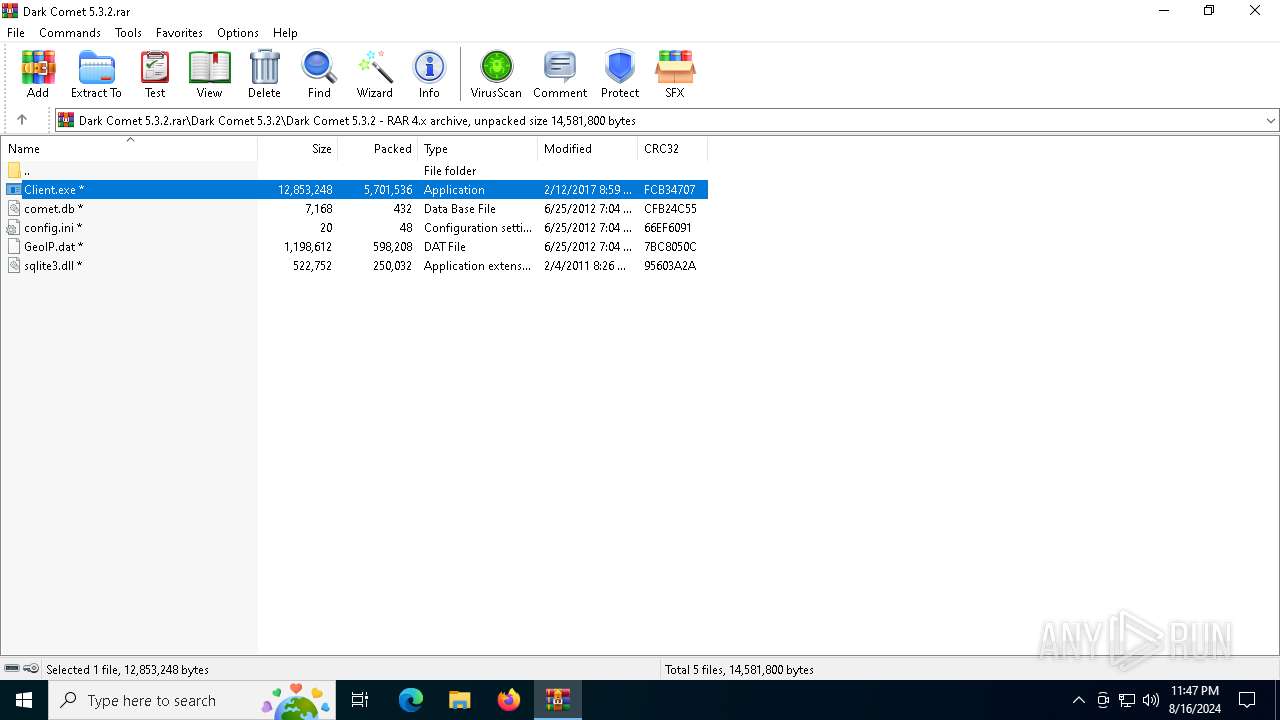
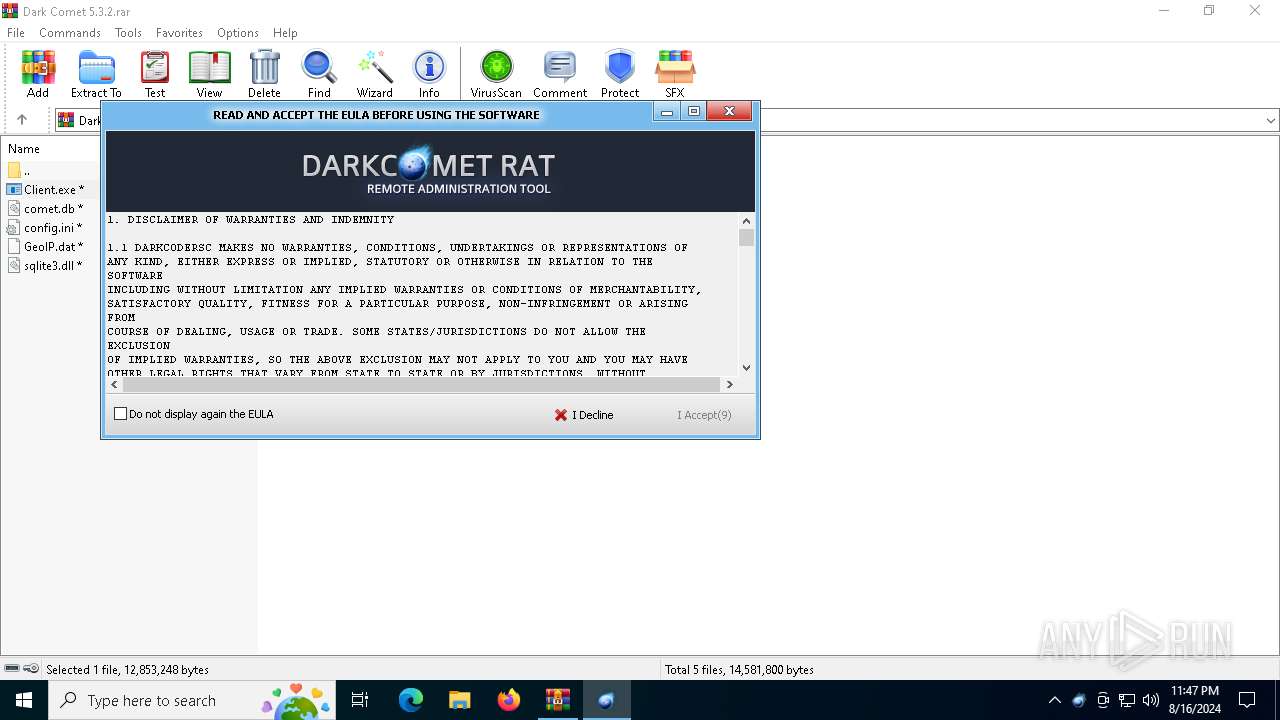
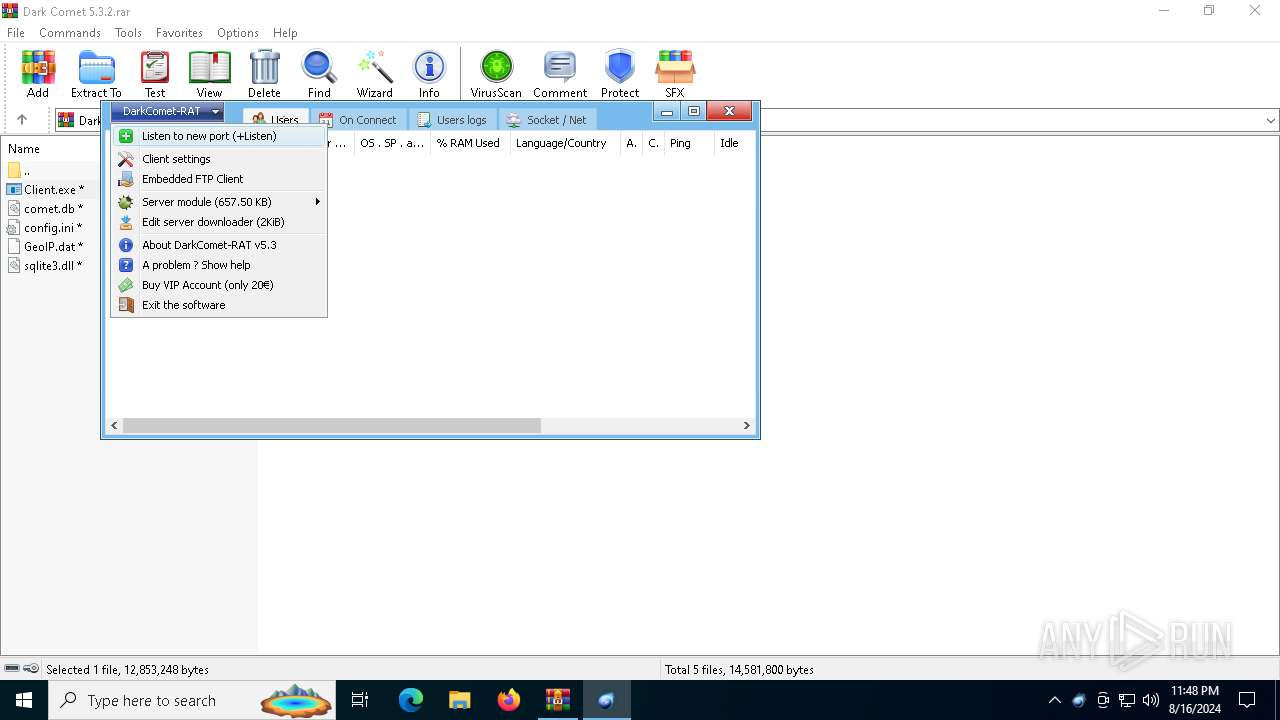
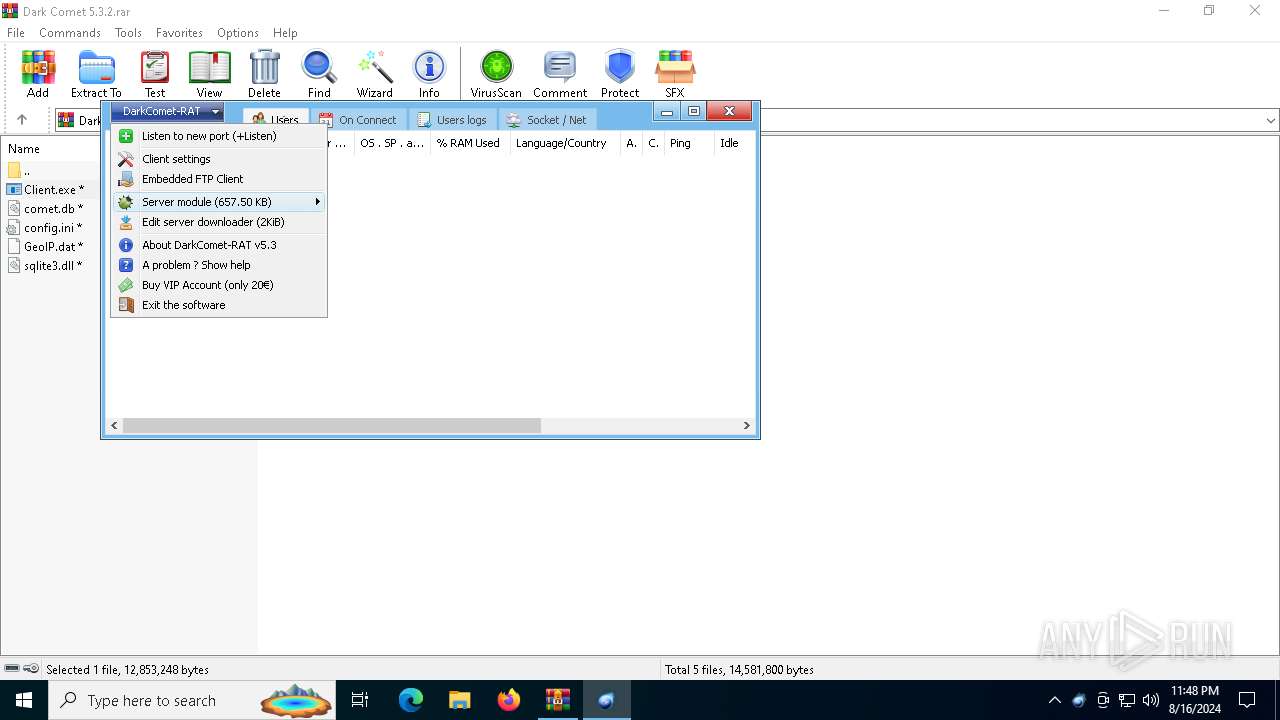
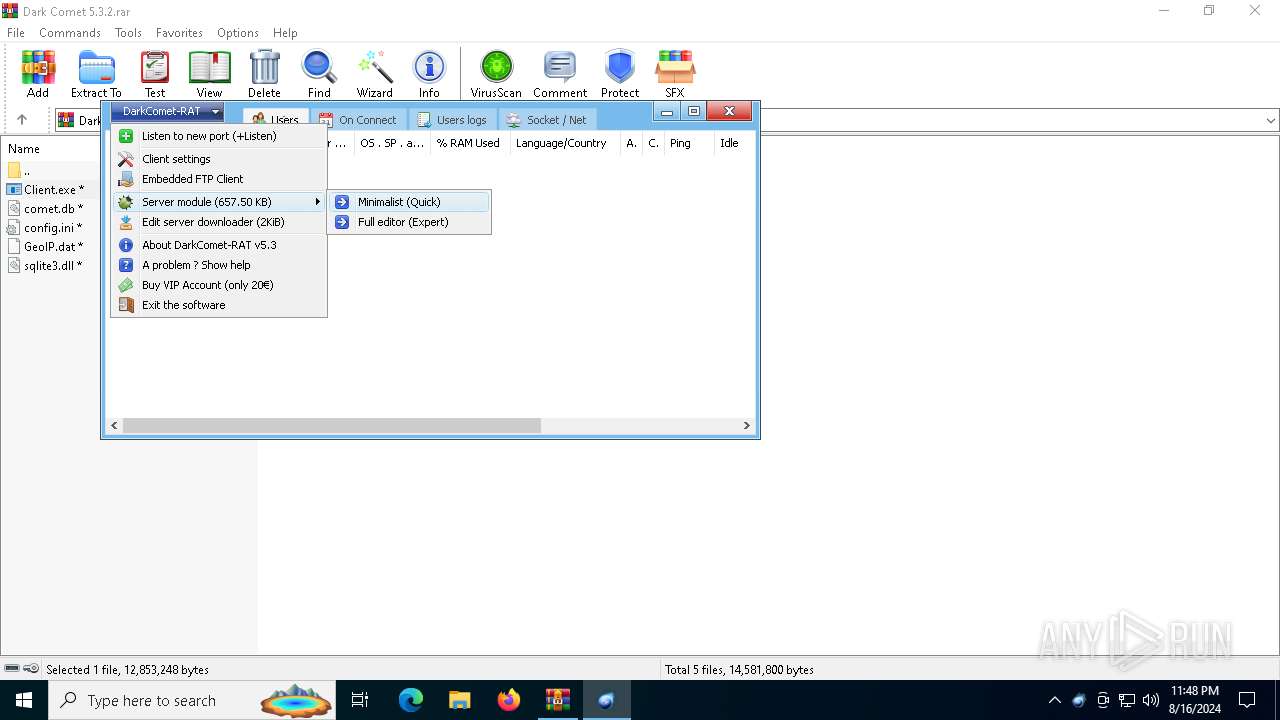
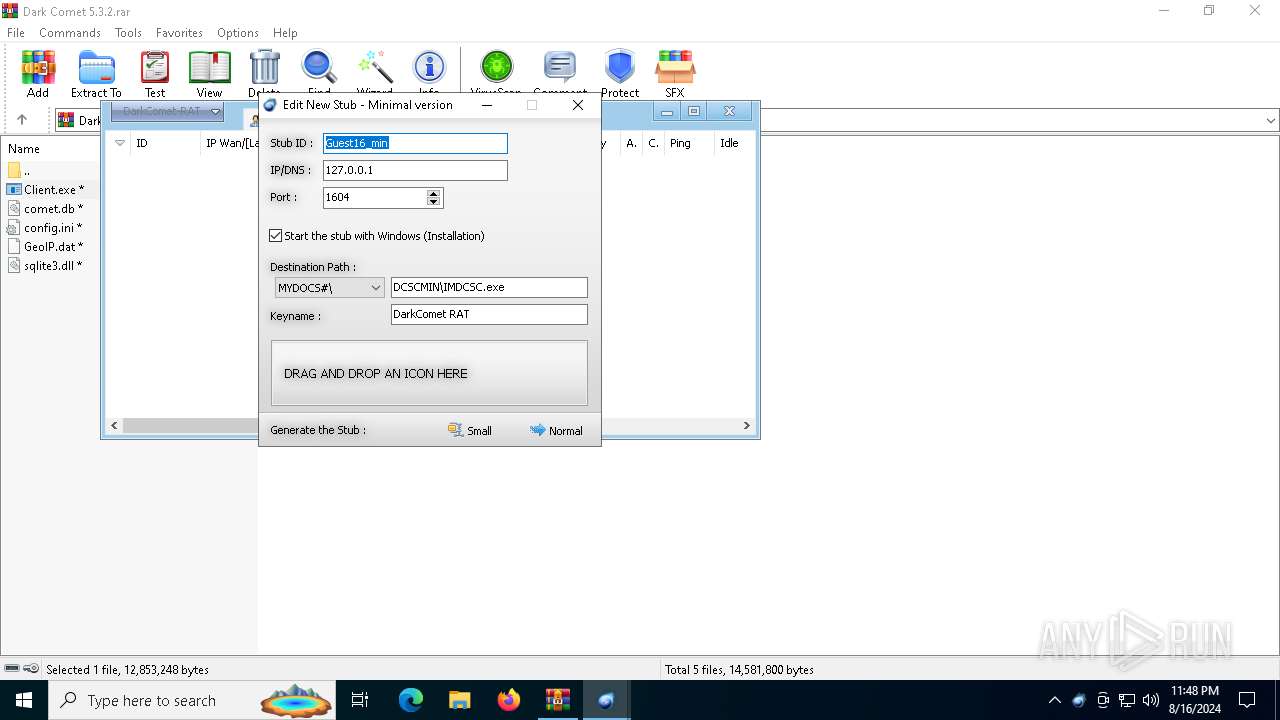
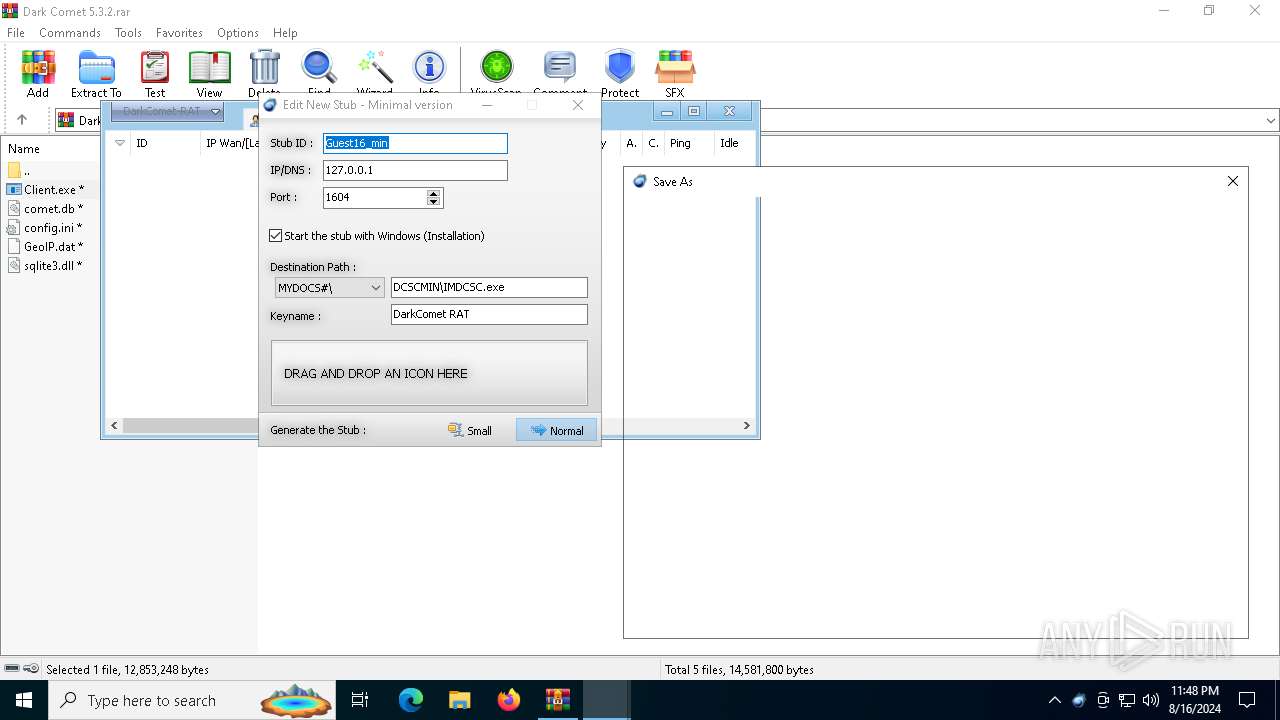
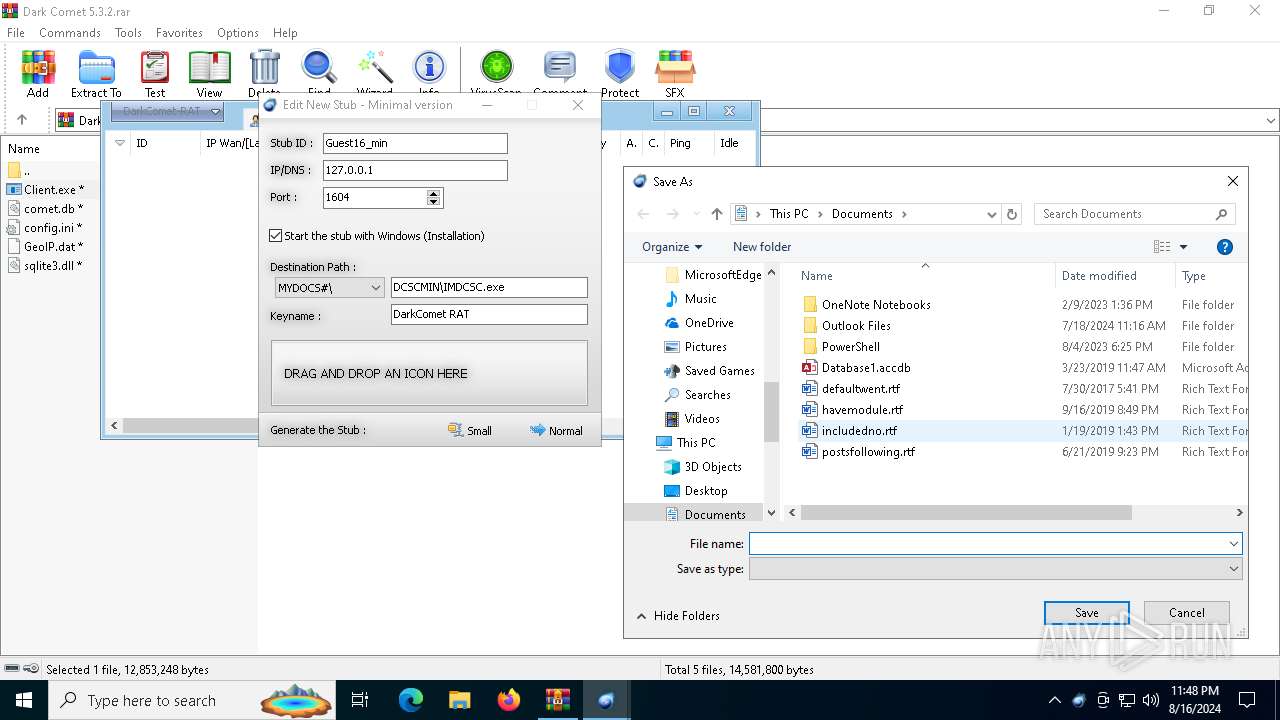
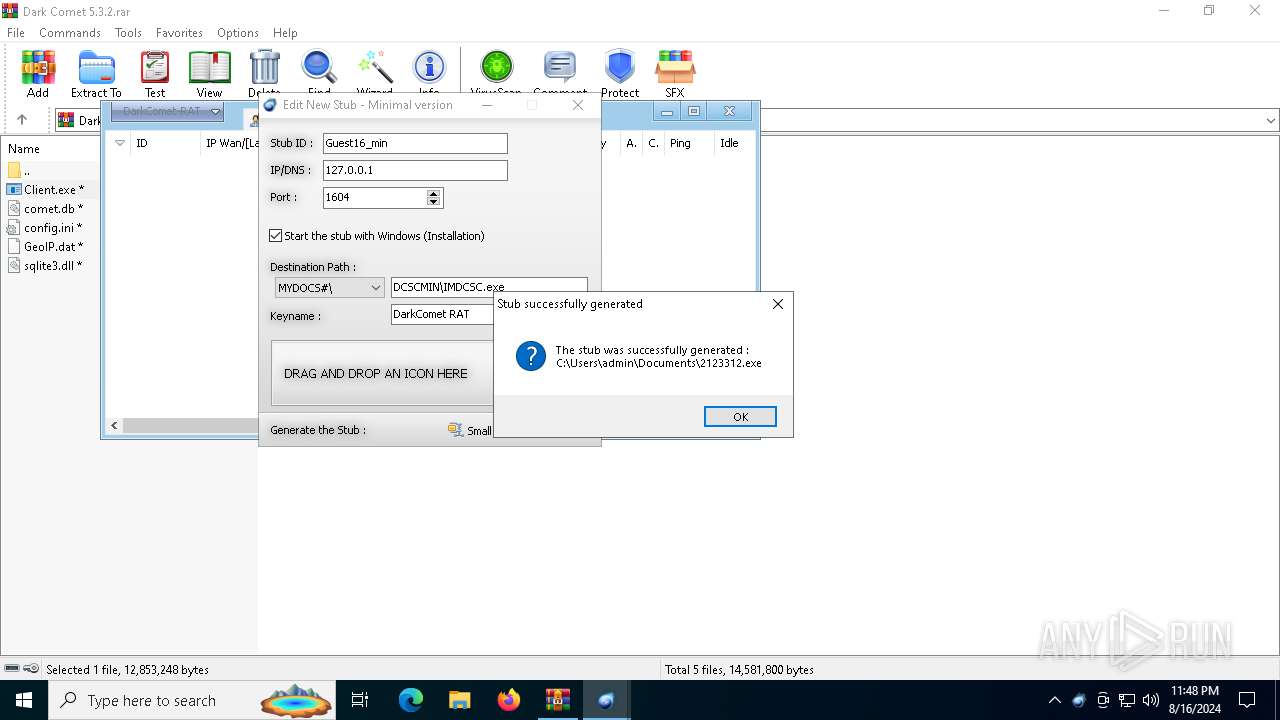
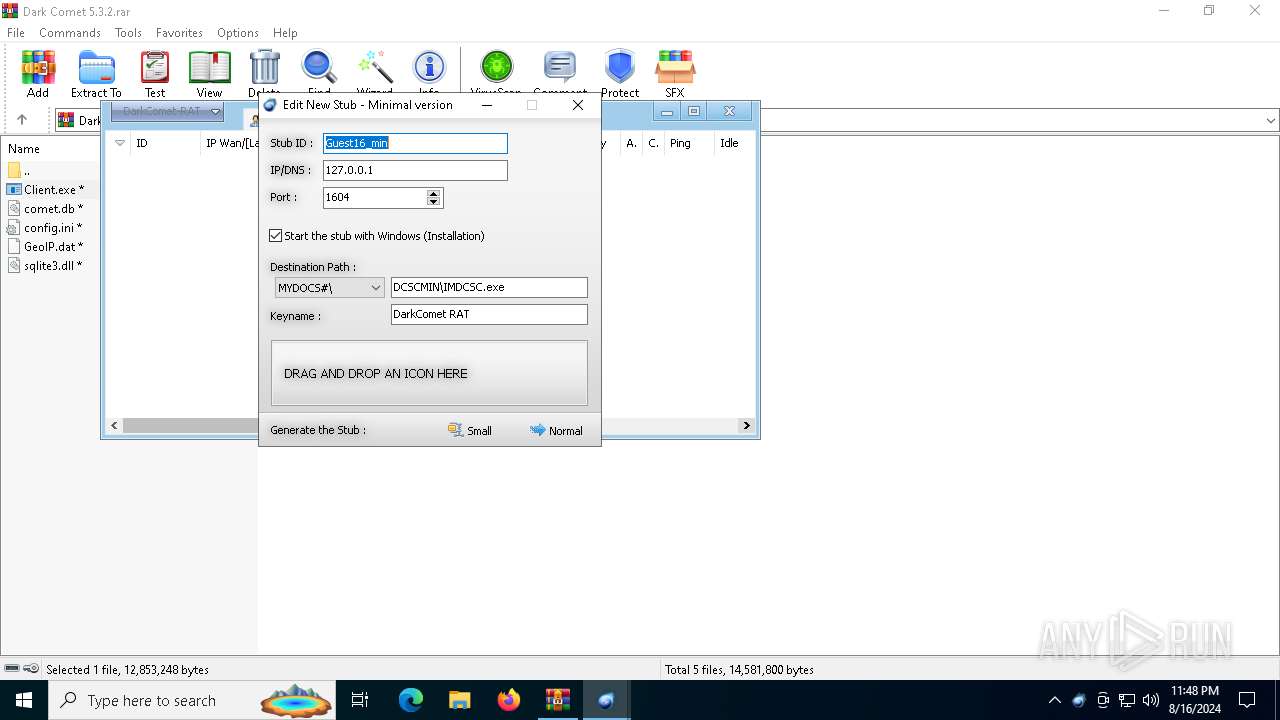
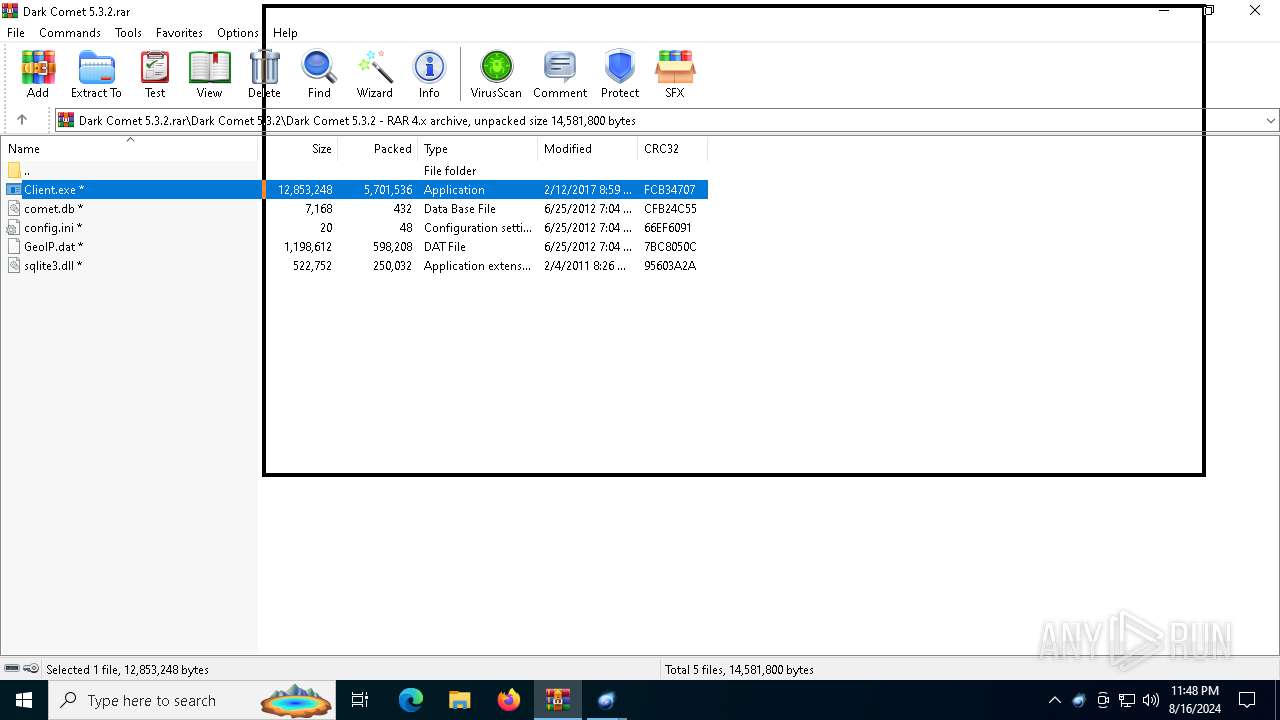
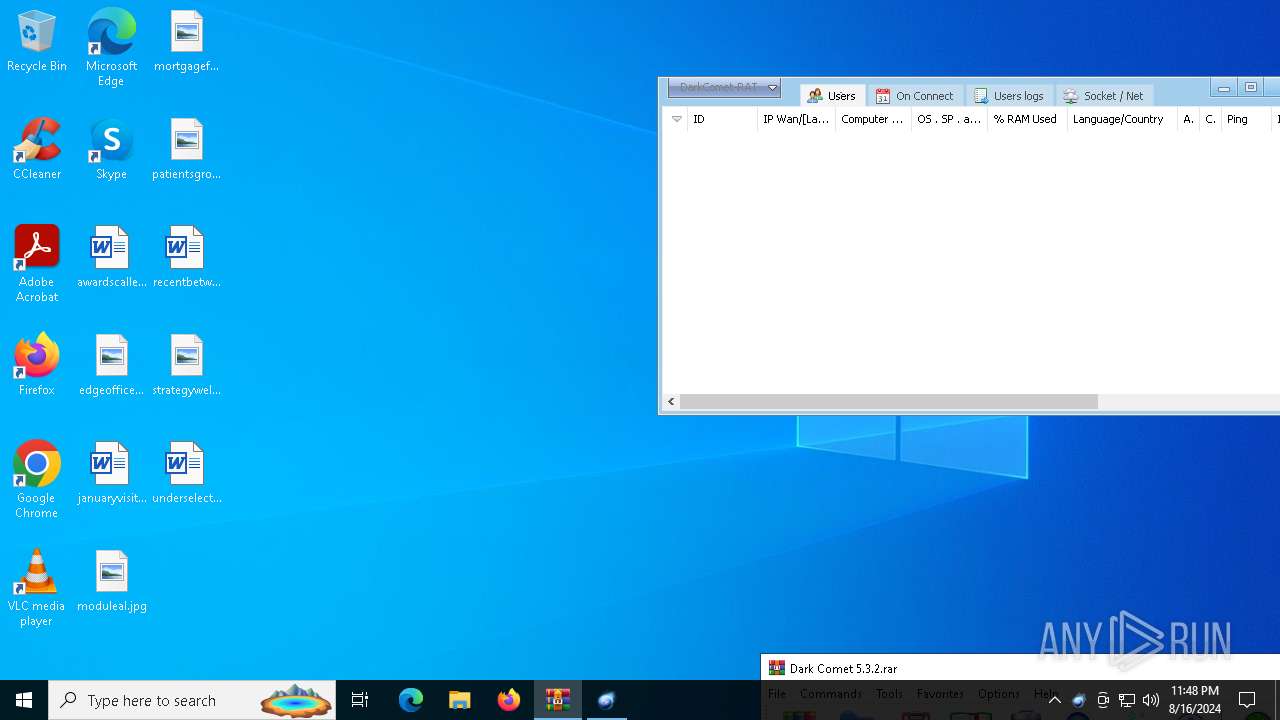
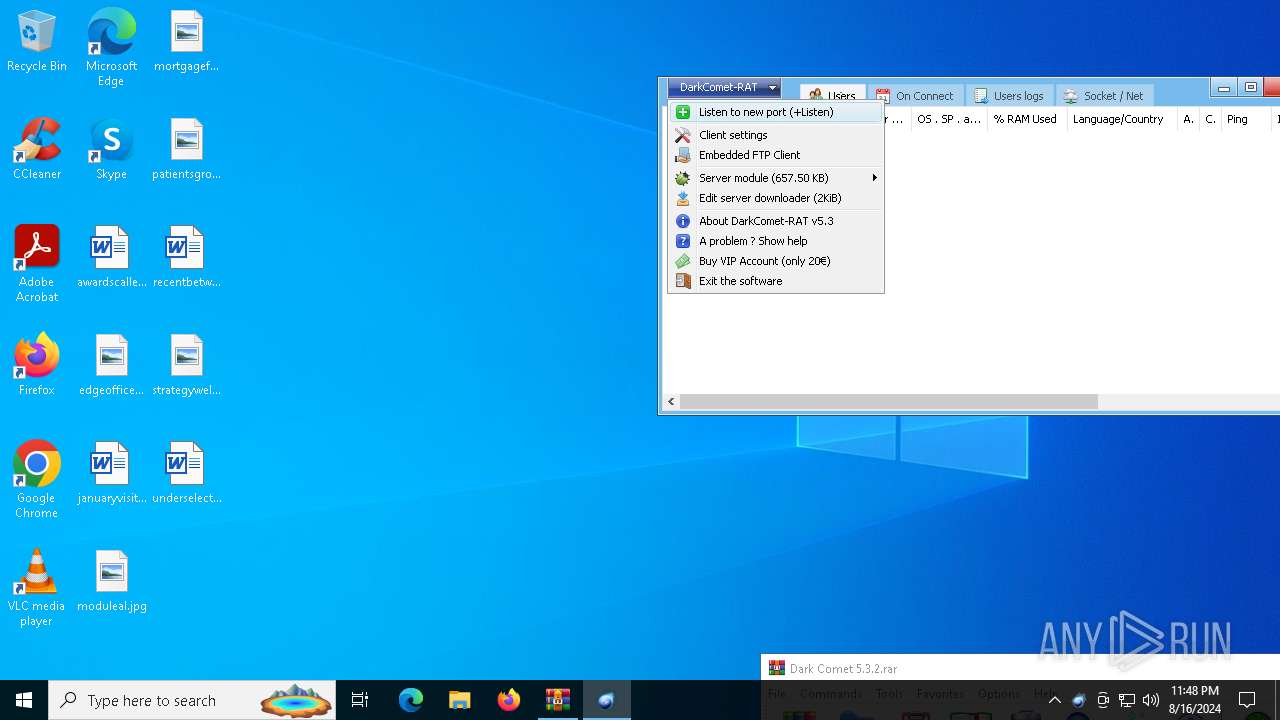
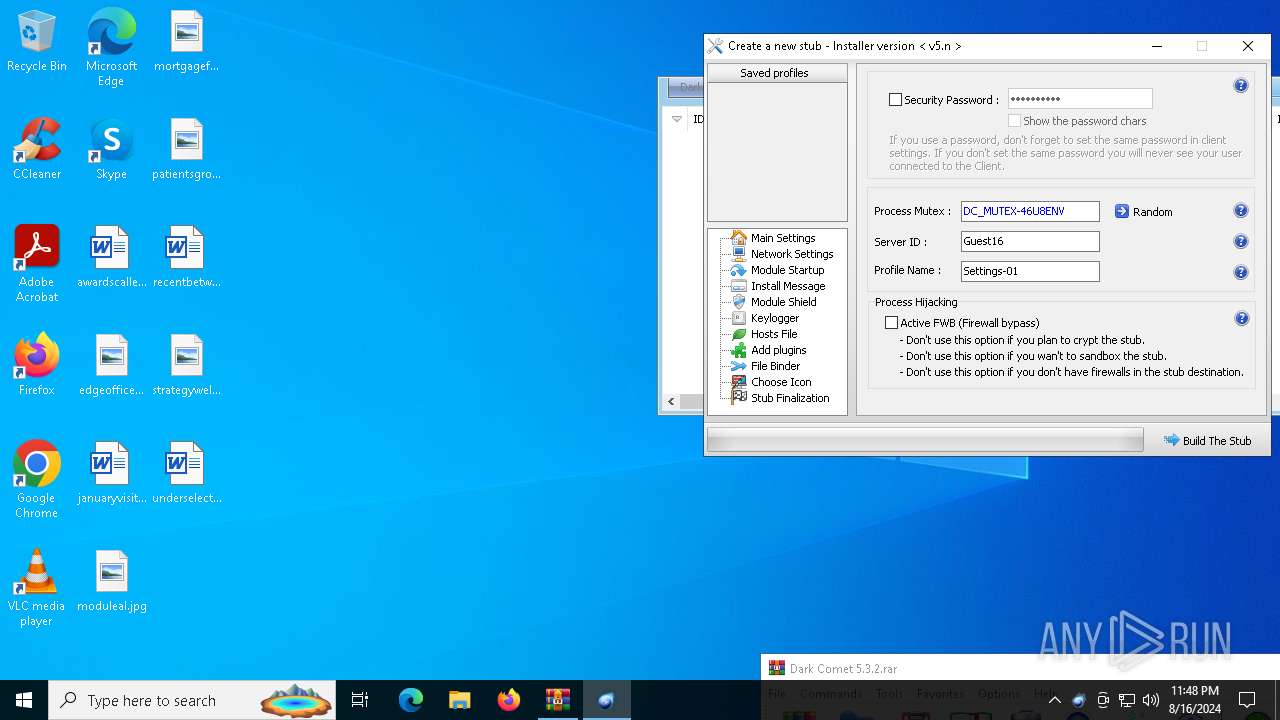
| File name: | Dark Comet 5.3.2.rar |
| Full analysis: | https://app.any.run/tasks/f73d8f60-e7d6-4a7f-848d-ca31ca5d97c4 |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | August 16, 2024, 23:47:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 9C9E0C14563E43CFDBD3B684EEA54DCD |
| SHA1: | D8261D6F6FBDD3BF647E90B5E8FA979A16AA9216 |
| SHA256: | 14E03138B1AD73F6C8214743A608267A7D0BBCBFFE78B31F8FB3AD343F48AB0D |
| SSDEEP: | 98304:tiQarIeXhpgR4JN+xBQpXm+dU1ehu9YPutW5fNYYs6eiv7QMmUo1NzEokuwVP7ux:cur7I+wsWvs6d85Z5 |
MALICIOUS
Changes the autorun value in the registry
- cxcc.exe (PID: 6952)
- msdcsc.exe (PID: 6380)
Changes the login/logoff helper path in the registry
- cxcc.exe (PID: 6952)
Changes Security Center notification settings
- msdcsc.exe (PID: 6380)
- iexplore.exe (PID: 1432)
DARKCOMET has been detected (YARA)
- Client.exe (PID: 6972)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6536)
- Client.exe (PID: 6908)
- cxcc.exe (PID: 6952)
- Client.exe (PID: 6972)
Executable content was dropped or overwritten
- Client.exe (PID: 6908)
- cxcc.exe (PID: 6952)
- Client.exe (PID: 6972)
Drops the executable file immediately after the start
- Client.exe (PID: 6908)
- cxcc.exe (PID: 6952)
- Client.exe (PID: 6972)
Reads the date of Windows installation
- Client.exe (PID: 6908)
- cxcc.exe (PID: 6952)
Starts CMD.EXE for commands execution
- cxcc.exe (PID: 6952)
Start notepad (likely ransomware note)
- cxcc.exe (PID: 6952)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7028)
- cmd.exe (PID: 7036)
Starts itself from another location
- cxcc.exe (PID: 6952)
There is functionality for communication dyndns network (YARA)
- Client.exe (PID: 6972)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6536)
Reads the computer name
- Client.exe (PID: 6908)
- cxcc.exe (PID: 6952)
- Client.exe (PID: 6972)
- msdcsc.exe (PID: 6380)
Create files in a temporary directory
- Client.exe (PID: 6908)
- Client.exe (PID: 6972)
Process checks computer location settings
- Client.exe (PID: 6908)
- cxcc.exe (PID: 6952)
Checks supported languages
- Client.exe (PID: 6908)
- cxcc.exe (PID: 6952)
- Client.exe (PID: 6972)
- msdcsc.exe (PID: 6380)
UPX packer has been detected
- Client.exe (PID: 6972)
Mpress packer has been detected
- Client.exe (PID: 6972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 5701614 |
|---|---|
| UncompressedSize: | 12853248 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2017:02:12 20:59:30 |
| PackingMethod: | Normal |
| ArchivedFileName: | Dark Comet 5.3.2\Dark Comet 5.3.2\Client.exe |
Total processes
148
Monitored processes
15
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1432 | "C:\Program Files (x86)\Internet Explorer\iexplore.exe" | C:\Program Files (x86)\Internet Explorer\iexplore.exe | — | msdcsc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5040 | notepad | C:\Windows\SysWOW64\notepad.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6380 | "C:\Users\admin\Documents\MSDCSC\msdcsc.exe" | C:\Users\admin\Documents\MSDCSC\msdcsc.exe | cxcc.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: MEDIUM Description: Remote Service Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 6536 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Dark Comet 5.3.2.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6908 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb6536.37689\Dark Comet 5.3.2\Dark Comet 5.3.2\Client.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb6536.37689\Dark Comet 5.3.2\Dark Comet 5.3.2\Client.exe | WinRAR.exe | ||||||||||||
User: admin Company: Unremote.org Integrity Level: MEDIUM Description: A remote administration tool from the cosmos Exit code: 0 Version: 4.2.0.29 Modules
| |||||||||||||||
| 6952 | "C:\Users\admin\AppData\Local\Temp\cxcc.exe" | C:\Users\admin\AppData\Local\Temp\cxcc.exe | Client.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: MEDIUM Description: Remote Service Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 6972 | "C:\Users\admin\AppData\Local\Temp\Client.exe" | C:\Users\admin\AppData\Local\Temp\Client.exe | Client.exe | ||||||||||||
User: admin Company: Unremote.org Integrity Level: MEDIUM Description: A remote administration tool from the cosmos Version: 4.2.0.29 Modules
| |||||||||||||||
| 7028 | "C:\Windows\System32\cmd.exe" /k attrib "C:\Users\admin\AppData\Local\Temp\cxcc.exe" +s +h | C:\Windows\SysWOW64\cmd.exe | — | cxcc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7036 | "C:\Windows\System32\cmd.exe" /k attrib "C:\Users\admin\AppData\Local\Temp" +s +h | C:\Windows\SysWOW64\cmd.exe | — | cxcc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 895
Read events
22 782
Write events
110
Delete events
3
Modification events
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Dark Comet 5.3.2.rar | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
8
Suspicious files
4
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6536.37689\Dark Comet 5.3.2\Dark Comet 5.3.2\Client.exe | executable | |
MD5:77ABEFC4384D002091E8BFFE0E26BE64 | SHA256:944E5D5196A415B19539BFBD9AE14795F2A4FFB4F05C2EA4ACBF53C52110EF90 | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6536.37689\Dark Comet 5.3.2\Dark Comet 5.3.2\config.ini | text | |
MD5:8BB400D926ED7F40BE31FADA430F45EA | SHA256:68A10A393C2FE6E8E1F47BD3B42564456CF55A7FC881550B1D7DCC765462C405 | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6536.37689\Dark Comet 5.3.2\Dark Comet 5.3.2\sqlite3.dll | executable | |
MD5:D3979DB259F55D59B4EDB327673C1905 | SHA256:043E5570299C6099756C1809C5632EABEAB95ED3C1A55C86843C0EC218940E5A | |||
| 6908 | Client.exe | C:\Users\admin\AppData\Local\Temp\cxcc.exe | executable | |
MD5:8006CC9D227E537286EADB5EFCEBBD7A | SHA256:35420715B18EB5647264E6F80F634F747C68F363FB056F44A7EA723E375C04FD | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6536.37689\Dark Comet 5.3.2\Dark Comet 5.3.2\comet.db | sqlite | |
MD5:EB1551B704EEA54D1869FA70AA7F0A14 | SHA256:F81162B1FC7730ADB489299070F9810C1736FB5E904E849EB842A72E71FFA5A4 | |||
| 6952 | cxcc.exe | C:\Users\admin\Documents\MSDCSC\msdcsc.exe | executable | |
MD5:8006CC9D227E537286EADB5EFCEBBD7A | SHA256:35420715B18EB5647264E6F80F634F747C68F363FB056F44A7EA723E375C04FD | |||
| 1432 | iexplore.exe | C:\Users\admin\AppData\Roaming\dclogs\2024-08-16-6.dc | text | |
MD5:8C423429D9B748862F61F0E46578828F | SHA256:6A24865109FA3F2CBA5A4CBF2F704FCACA864217ACF2B72B782363EC118F8983 | |||
| 6908 | Client.exe | C:\Users\admin\AppData\Local\Temp\Client.exe | executable | |
MD5:8352362133E198175DD5627D2DAA789F | SHA256:AA4D480B4C82F701BB5A741B26456673AE1193953E34E69D8EAFB7E96A1387FD | |||
| 6972 | Client.exe | C:\Users\admin\Documents\RCXE50C.tmp | executable | |
MD5:BD7F5EA4E6942A7BD5CA254287D750A4 | SHA256:1EEE329028AB994CCB919BA86F5CDC81256C0625FCB9165868B343FCC7DA271C | |||
| 6972 | Client.exe | C:\Users\admin\AppData\Local\Temp\config.ini | text | |
MD5:8BB400D926ED7F40BE31FADA430F45EA | SHA256:68A10A393C2FE6E8E1F47BD3B42564456CF55A7FC881550B1D7DCC765462C405 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
54
DNS requests
29
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5092 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5092 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2392 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1360 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2536 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2536 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5336 | SearchApp.exe | 95.100.146.34:443 | www.bing.com | Akamai International B.V. | CZ | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5092 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
mrchlen228.ddns.net |
| malicious |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
Process | Message |
|---|---|
Client.exe | Thumbnail Cache: Attempting to replace an entry that is in use
|