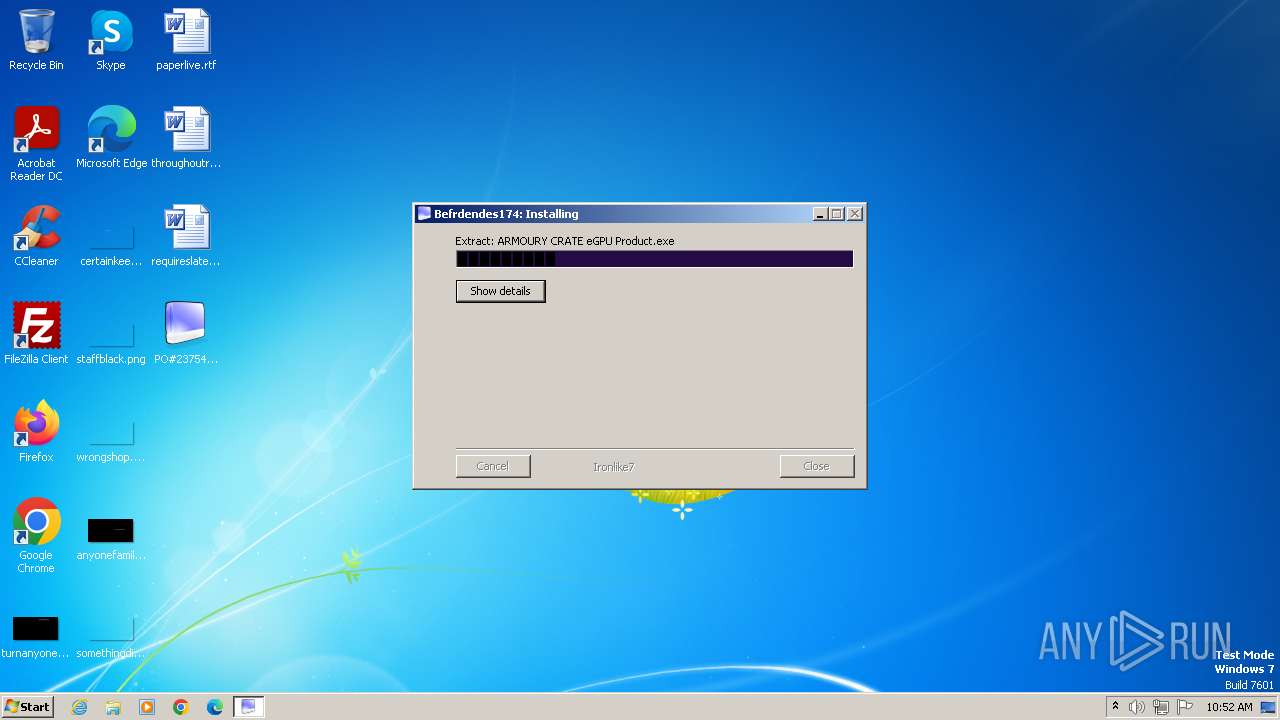
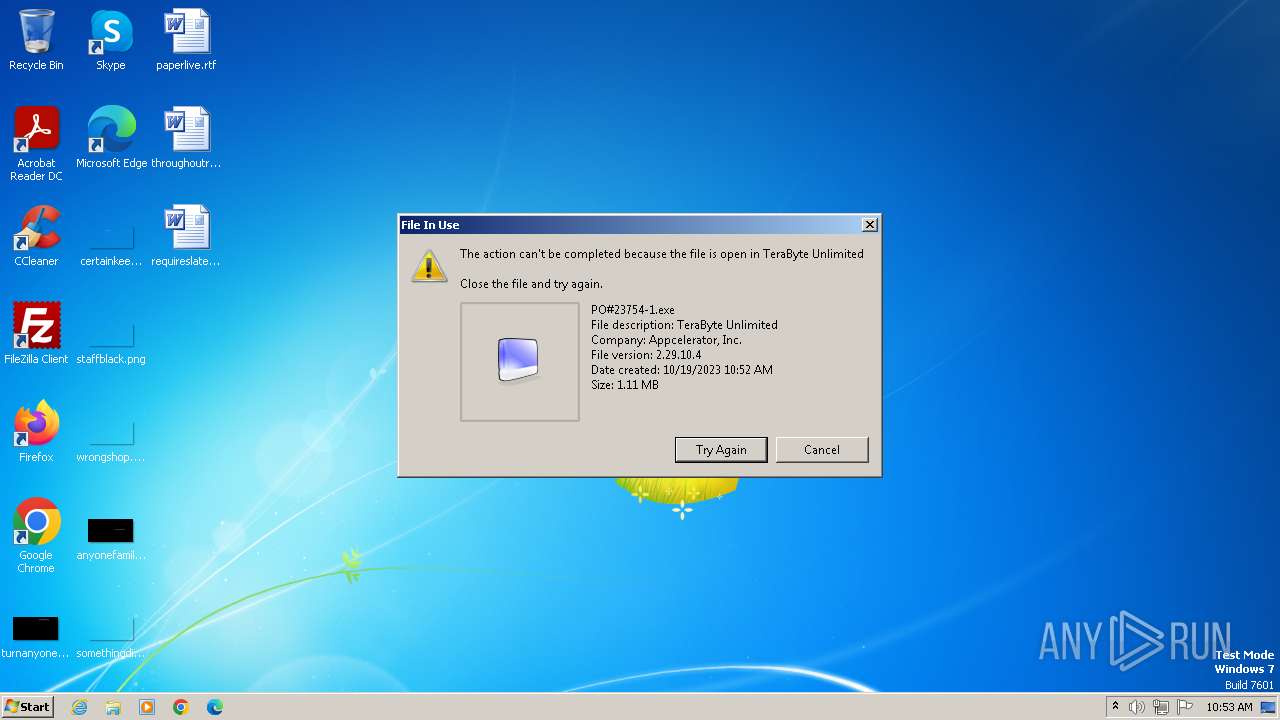
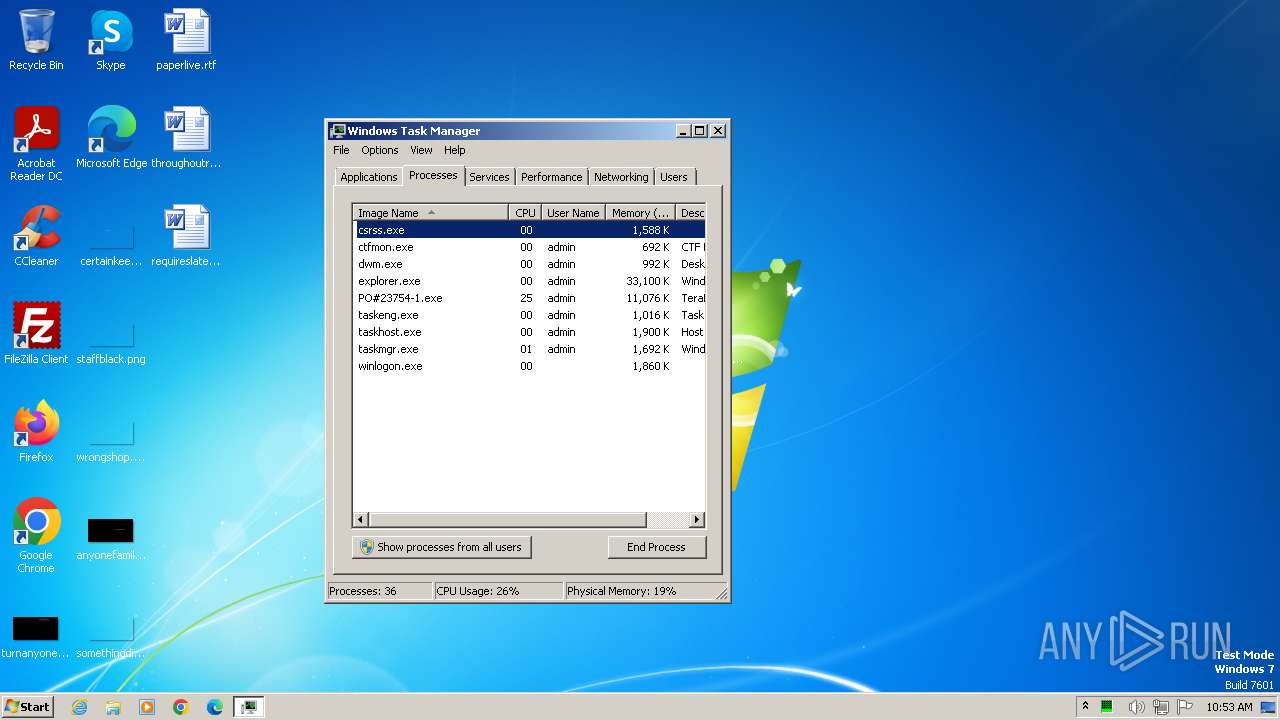
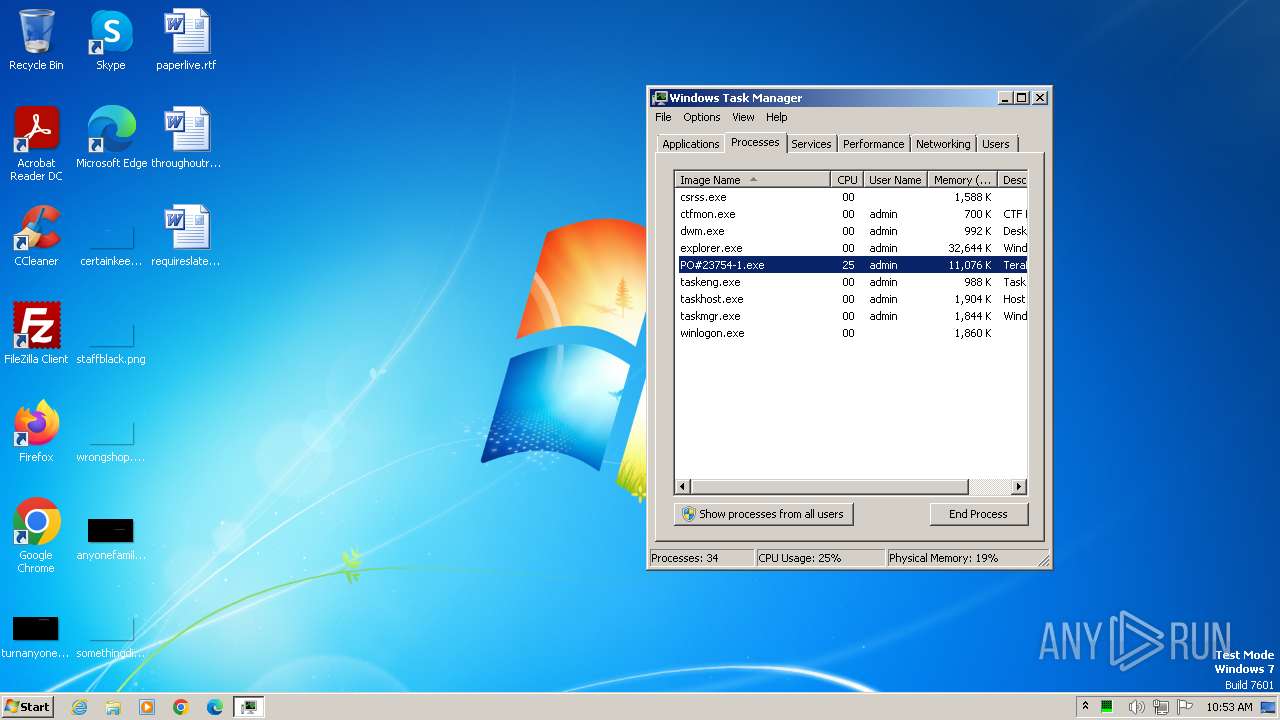
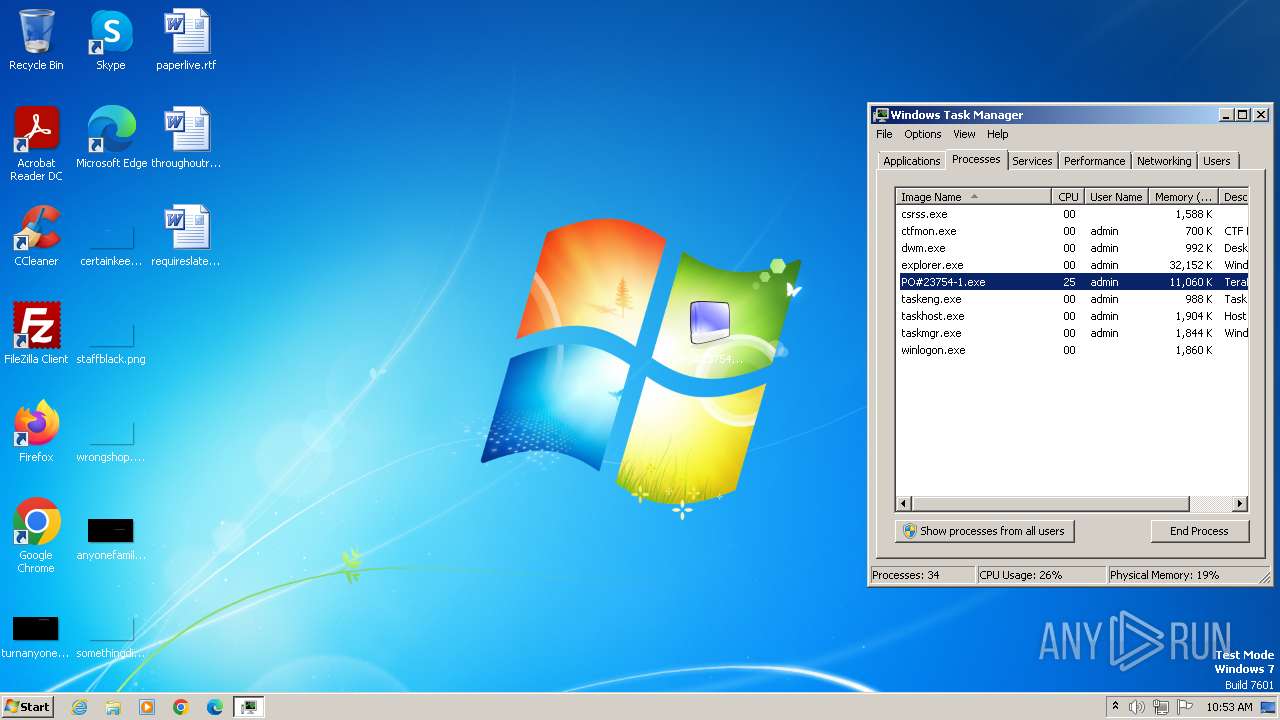
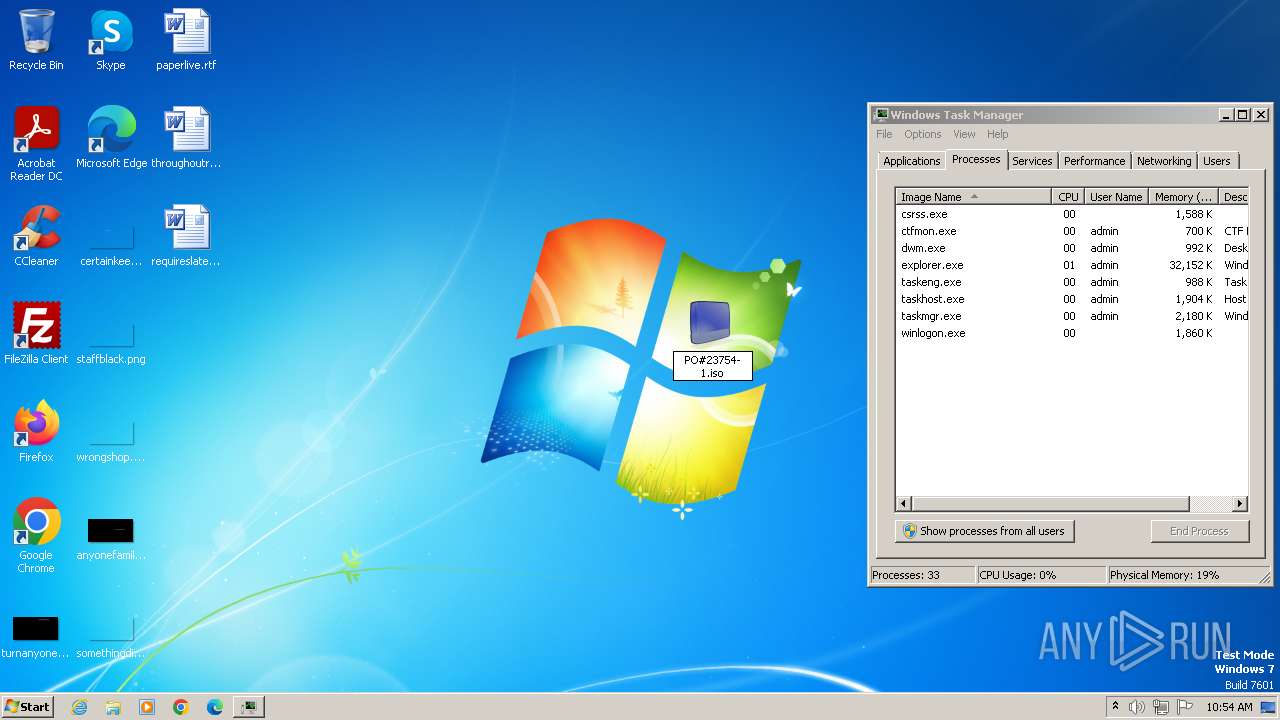
| File name: | PO#23754-1.exe |
| Full analysis: | https://app.any.run/tasks/e8e35173-5f82-4ff3-b645-8f7317702ae7 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | October 19, 2023, 09:52:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | C012417C6E5D2210FBE0BC36A79D577B |
| SHA1: | 041EF39A95C810DAF4F02F80E3E858175BB1902E |
| SHA256: | 14D52119459EF12BE3A2F9A3A6578EE3255580F679B1B54DE0990B6BA403B0FE |
| SSDEEP: | 49152:6J8Ma61n8hmcDSjV++dVbOMEwX47zZm8ojgtXt7QF9I4ZLf98FlwhVxIJYYMJOrv:6J8A1MmOs3EwX47zZHosJt7QbZbO4hTQ |
MALICIOUS
GULOADER has been detected (YARA)
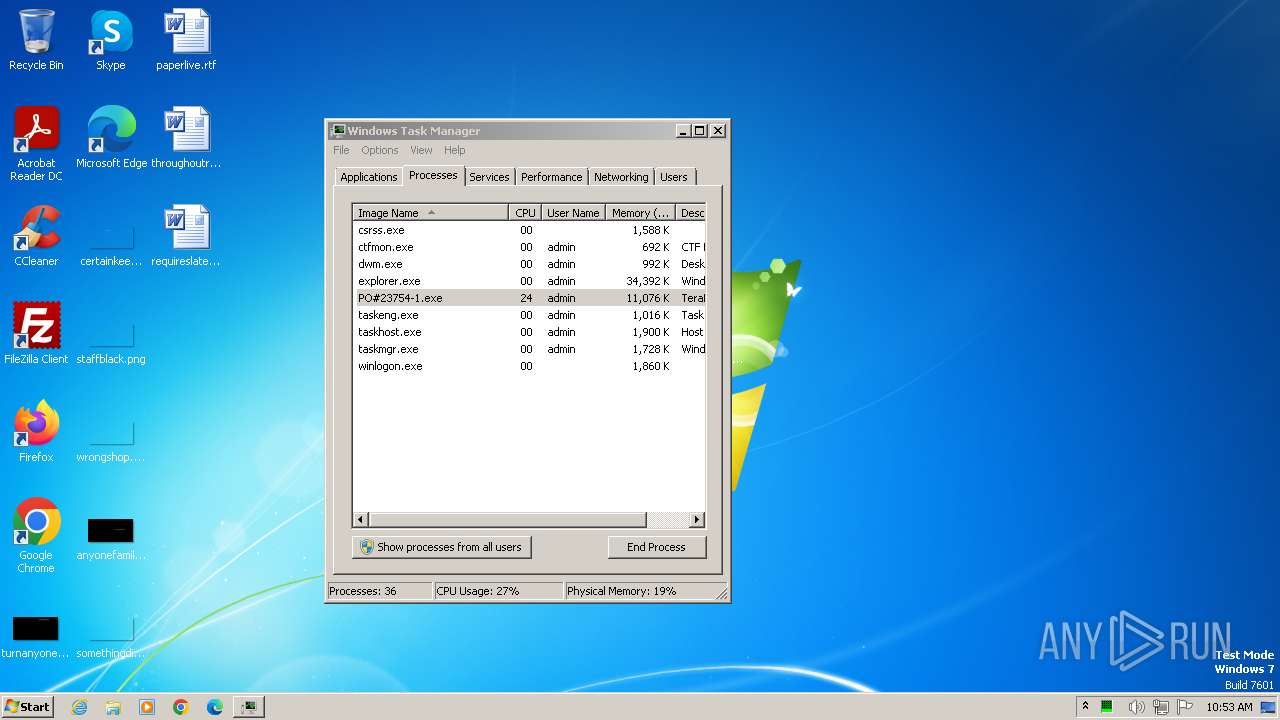
- PO#23754-1.exe (PID: 3852)
Loads dropped or rewritten executable
- PO#23754-1.exe (PID: 3852)
- PO#23754-1.exe (PID: 3544)
Application was dropped or rewritten from another process
- PO#23754-1.exe (PID: 3852)
- PO#23754-1.exe (PID: 3544)
Drops the executable file immediately after the start
- PO#23754-1.exe (PID: 3852)
- PO#23754-1.exe (PID: 3544)
SUSPICIOUS
Process drops legitimate windows executable
- PO#23754-1.exe (PID: 3852)
Malware-specific behavior (creating "System.dll" in Temp)
- PO#23754-1.exe (PID: 3852)
- PO#23754-1.exe (PID: 3544)
The process creates files with name similar to system file names
- PO#23754-1.exe (PID: 3852)
- PO#23754-1.exe (PID: 3544)
INFO
Create files in a temporary directory
- PO#23754-1.exe (PID: 3852)
- PO#23754-1.exe (PID: 3544)
Checks supported languages
- PO#23754-1.exe (PID: 3852)
- PO#23754-1.exe (PID: 3544)
Reads the computer name
- PO#23754-1.exe (PID: 3852)
- PO#23754-1.exe (PID: 3544)
Manual execution by a user
- mmc.exe (PID: 3304)
- taskmgr.exe (PID: 3268)
- mmc.exe (PID: 2148)
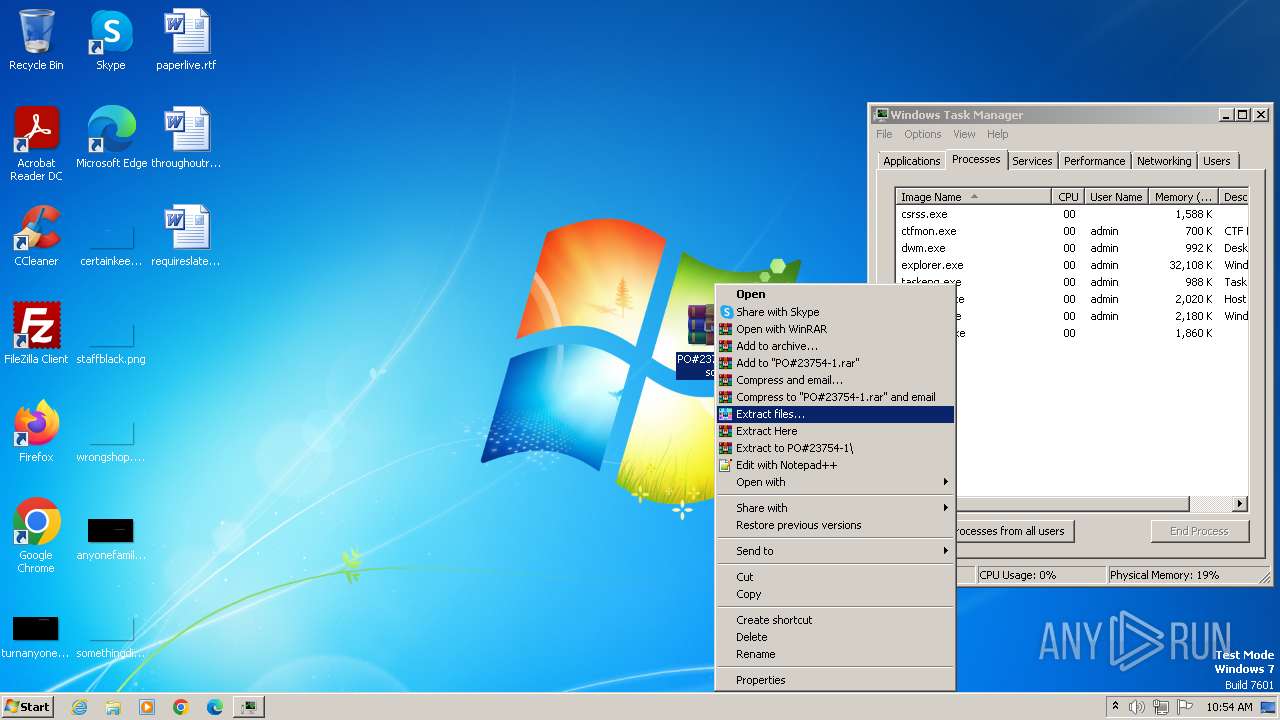
- WinRAR.exe (PID: 3860)
- PO#23754-1.exe (PID: 3544)
- WinRAR.exe (PID: 1796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
guloader
(PID) Process(3852) PO#23754-1.exe
C2 (1)http://bounceclick.live/VVB/COrg_RYGGqN229.bin
Strings (22)C:\Program Files\Qemu-ga\qemu-ga.exe
C:\Program Files\qga\qga.exe
Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko
Msi.dll
Publisher
Software\Microsoft\Windows\CurrentVersion\RunOnce
Startup key
TEMP=
\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe
\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe
\Microsoft.NET\Framework\v4.0.30319\caspol.exe
\system32\
\syswow64\
advapi32
iertutil.dll
kernel32
ntdll
psapi.dll
shell32
user32
windir=
wininet.dll
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 23:56:47+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3640 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.29.10.4 |
| ProductVersionNumber: | 2.29.10.4 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | Felcor Lodging Trust Inc. |
| CompanyName: | Appcelerator, Inc. |
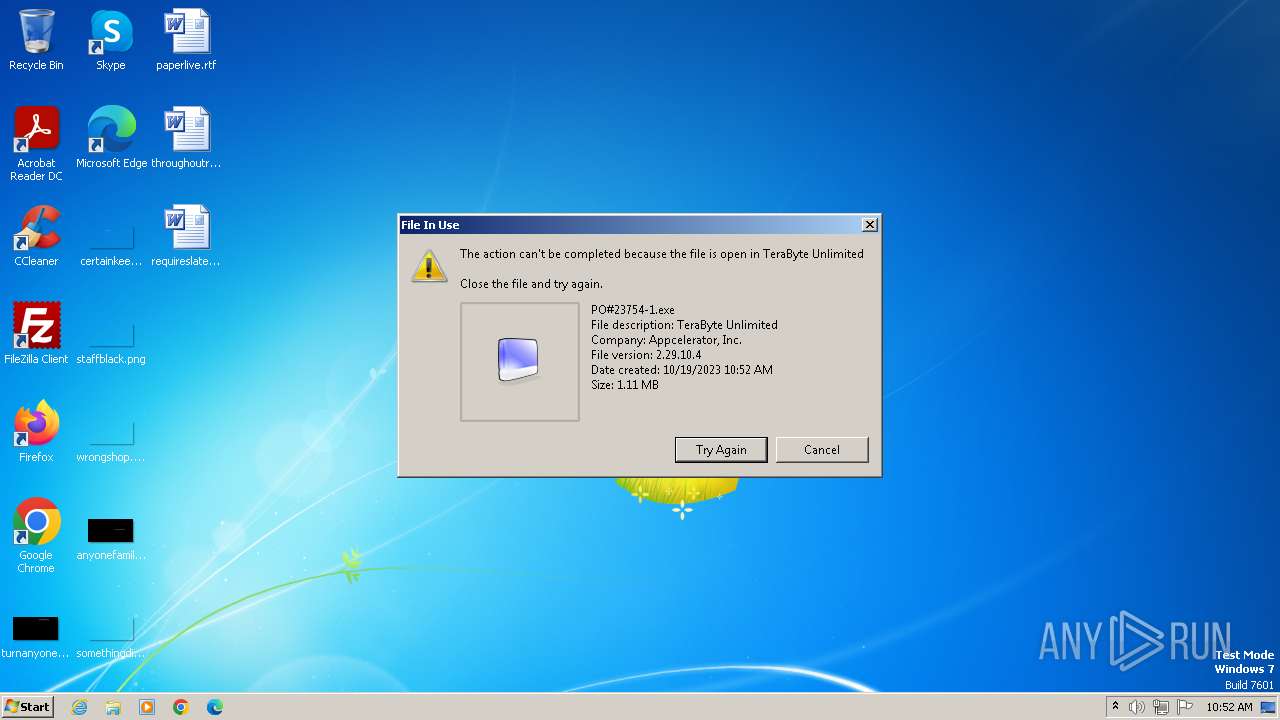
| FileDescription: | TeraByte Unlimited |
| FileVersion: | 3.10.16 |
| LegalCopyright: | Hilton Hotels Corp. |
| LegalTrademarks: | Nortek Inc |
| ProductName: | Kimberly-Clark Corporation |
Total processes
49
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
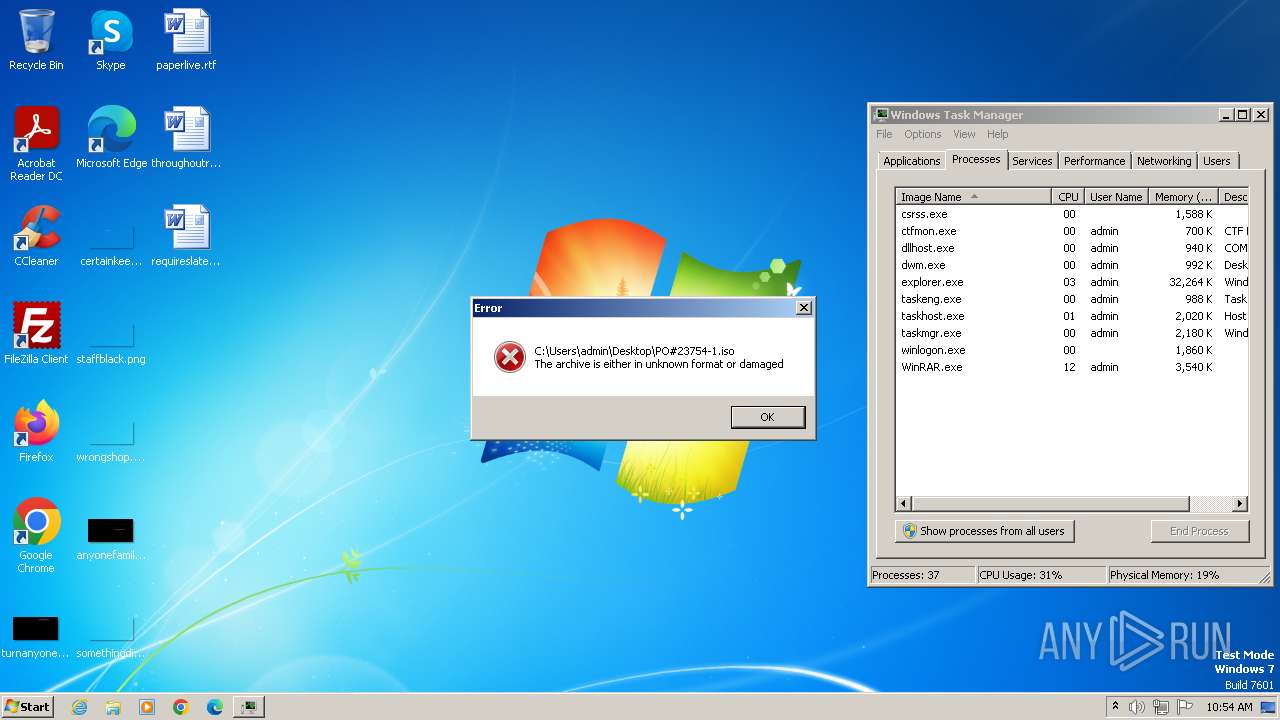
| 1796 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\PO#23754-1.iso" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.91.0 Modules
| |||||||||||||||
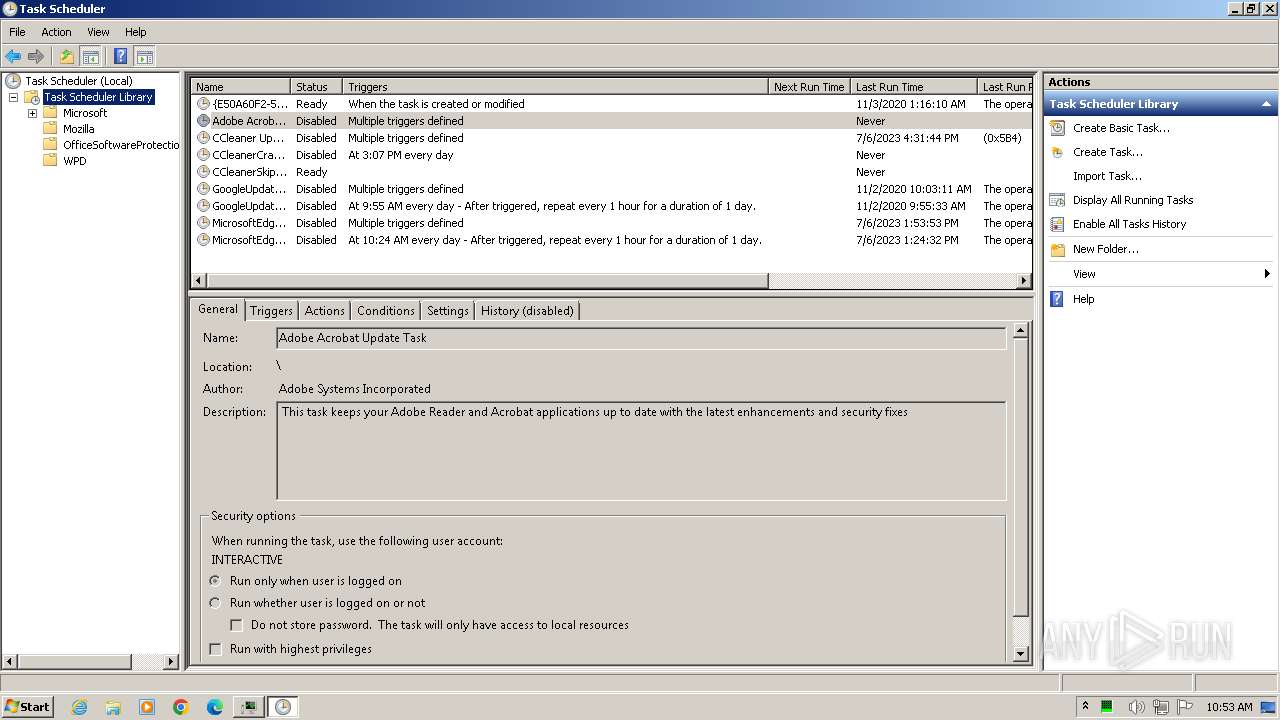
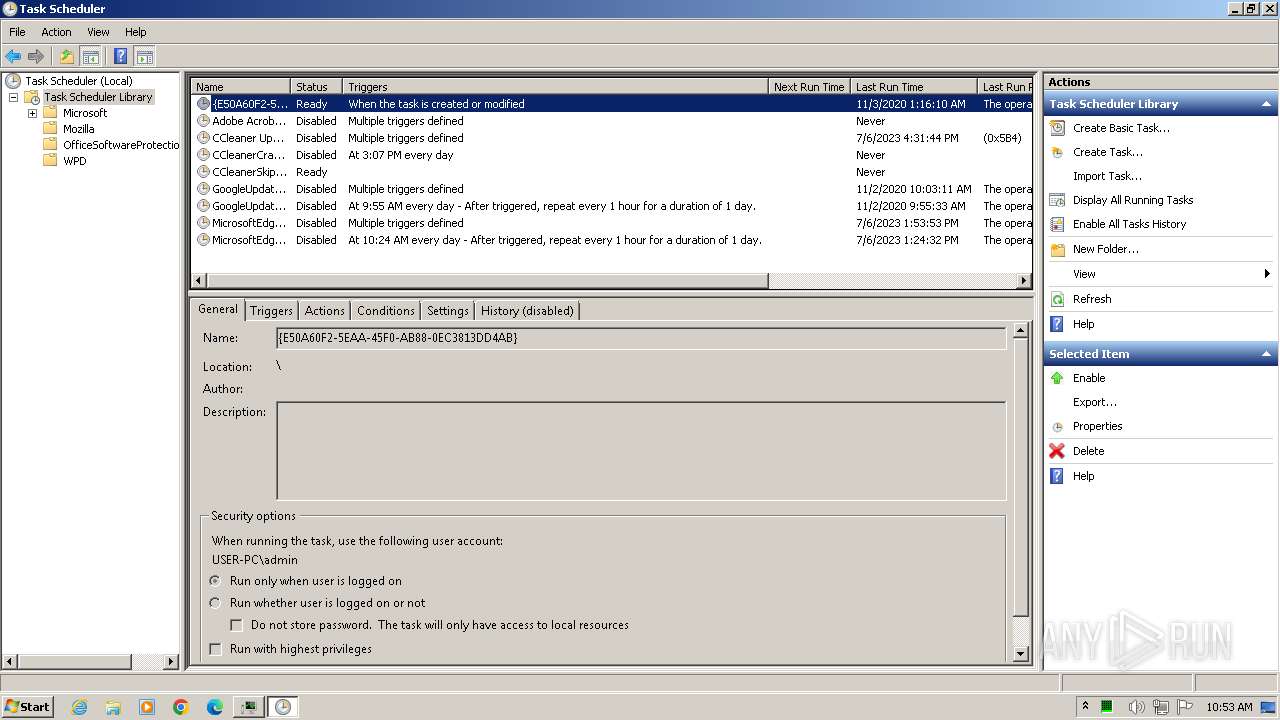
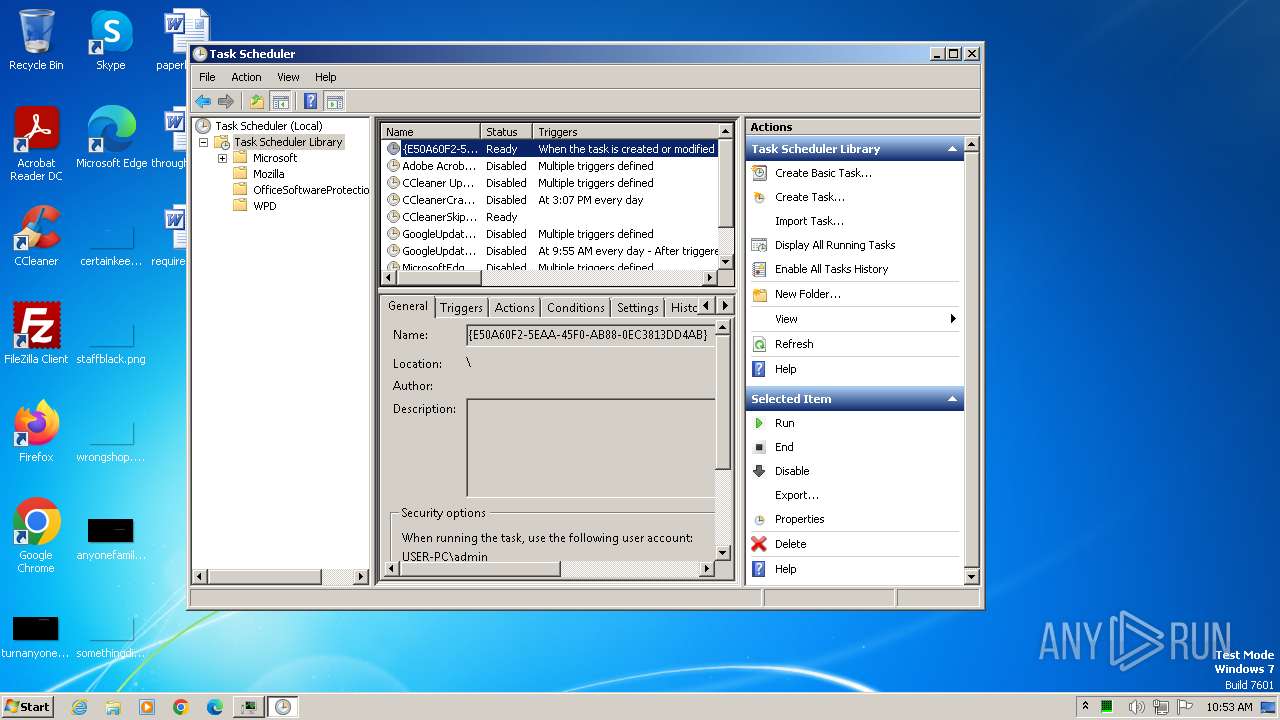
| 2148 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
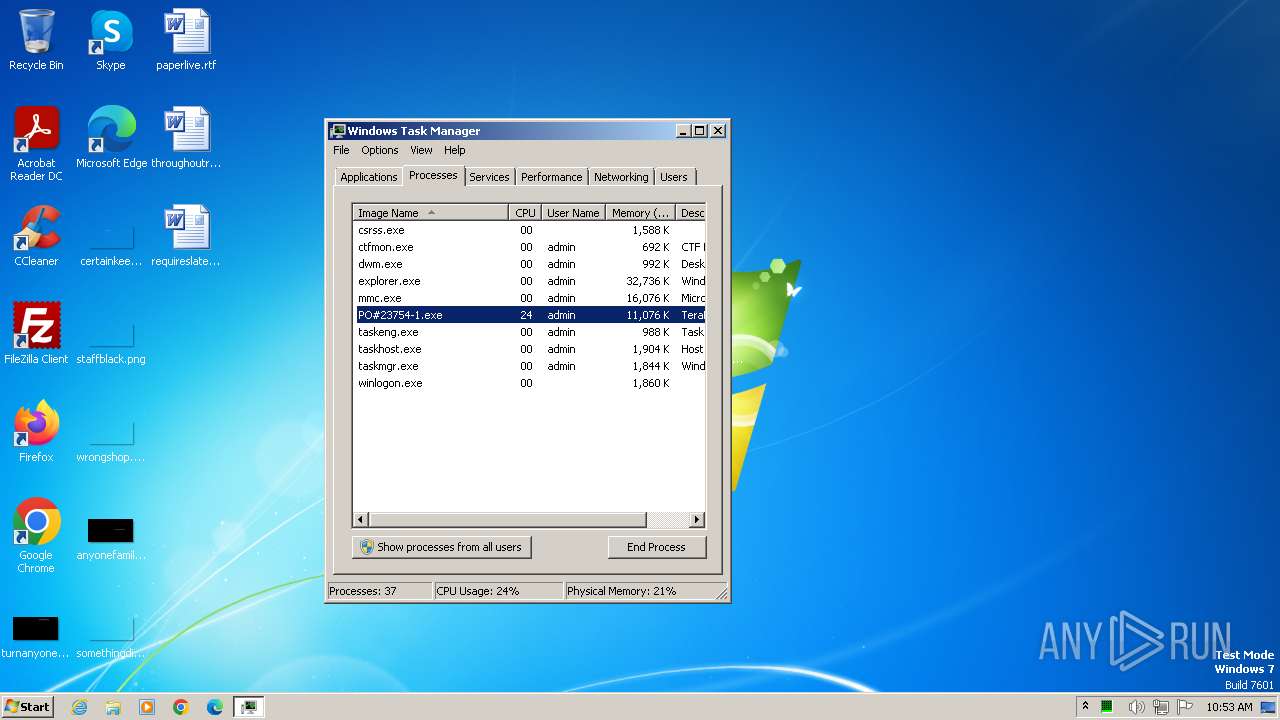
| 3268 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3304 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
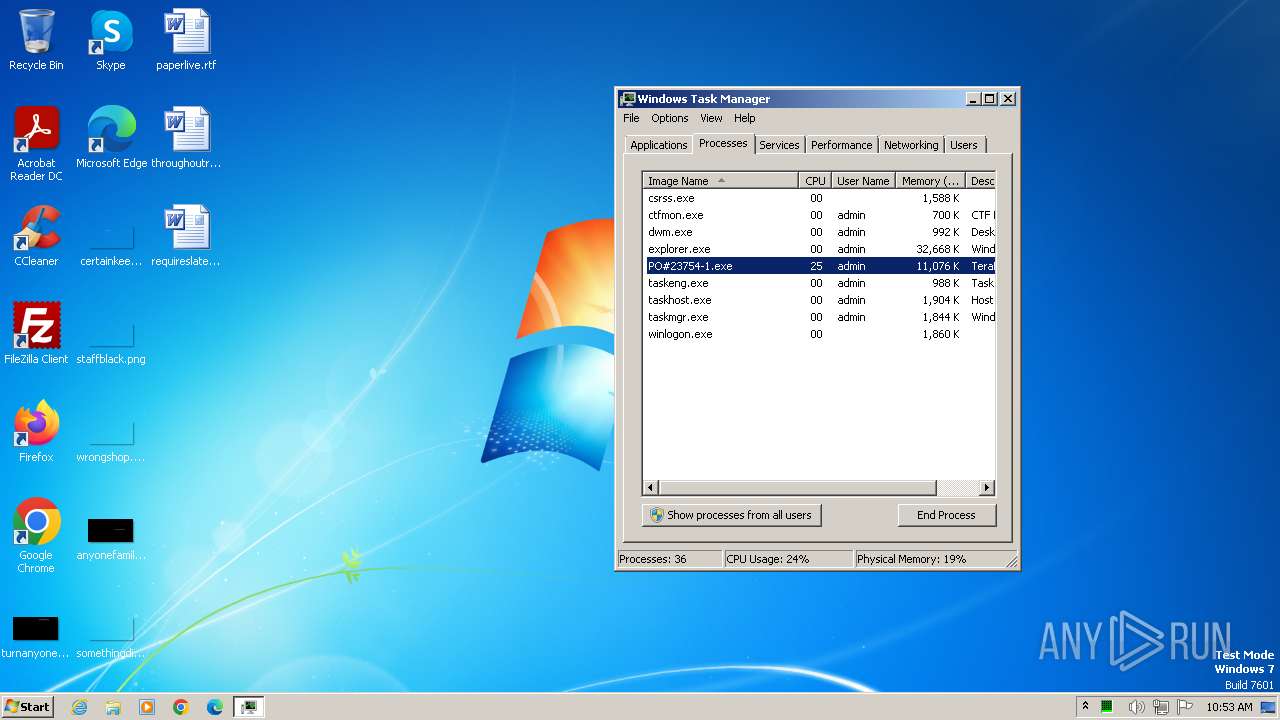
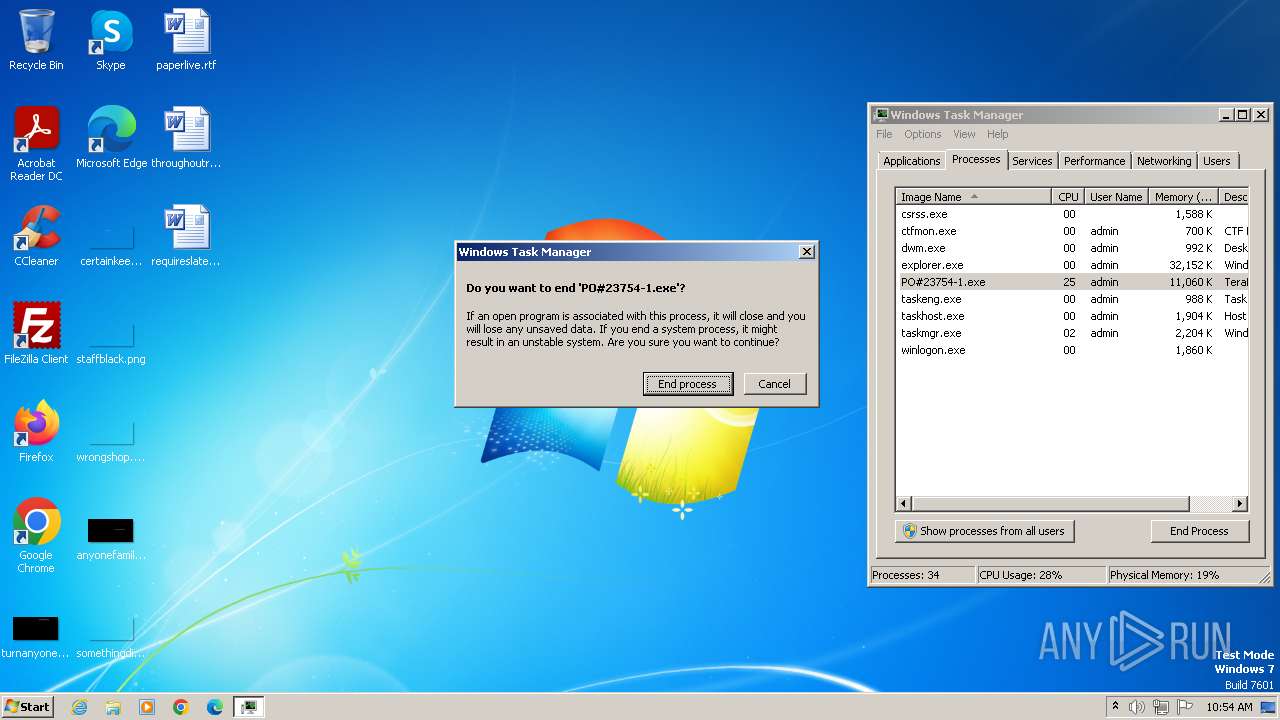
| 3544 | "C:\Users\admin\Desktop\PO#23754-1.exe" | C:\Users\admin\Desktop\PO#23754-1.exe | — | explorer.exe | |||||||||||
User: admin Company: Appcelerator, Inc. Integrity Level: MEDIUM Description: TeraByte Unlimited Exit code: 0 Version: 3.10.16 Modules
| |||||||||||||||
| 3852 | "C:\Users\admin\Desktop\PO#23754-1.exe" | C:\Users\admin\Desktop\PO#23754-1.exe | explorer.exe | ||||||||||||
User: admin Company: Appcelerator, Inc. Integrity Level: MEDIUM Description: TeraByte Unlimited Exit code: 1 Version: 3.10.16 Modules
guloader(PID) Process(3852) PO#23754-1.exe C2 (1)http://bounceclick.live/VVB/COrg_RYGGqN229.bin Strings (22)C:\Program Files\Qemu-ga\qemu-ga.exe C:\Program Files\qga\qga.exe Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko Msi.dll Publisher Software\Microsoft\Windows\CurrentVersion\RunOnce Startup key TEMP= \Microsoft.NET\Framework\v4.0.30319\RegAsm.exe \Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe \Microsoft.NET\Framework\v4.0.30319\caspol.exe \system32\ \syswow64\ advapi32 iertutil.dll kernel32 ntdll psapi.dll shell32 user32 windir= wininet.dll | |||||||||||||||
| 3860 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\PO#23754-1.iso" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 495
Read events
1 478
Write events
16
Delete events
1
Modification events
| (PID) Process: | (3304) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | HelpTopic |
Value: C:\Windows\Help\taskscheduler.chm | |||
| (PID) Process: | (3304) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | LinkedHelpTopics |
Value: C:\Windows\Help\taskscheduler.chm | |||
| (PID) Process: | (3304) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Microsoft Management Console\Recent File List |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band56_0 |
Value: 38000000730100000402000000000000D4D0C800000000000000000000000000CC0113000000000039000000B40200000000000001000000 | |||
Executable files
7
Suspicious files
5
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3852 | PO#23754-1.exe | C:\Users\admin\AppData\Local\Temp\edit-delete.png | image | |
MD5:FEB3F09A51CB6472B9C24EEF8388F29B | SHA256:866C0ABB7618AD93D38E46BE2F98E7EB131D90949B06C435EF4406F091243197 | |||
| 3852 | PO#23754-1.exe | C:\Users\admin\AppData\Local\Temp\AsusMemoryHelper.exe | executable | |
MD5:B1FD063C09591100F9B002D1A023742E | SHA256:EE1CF0337CDF46DD63E5241AE4409FABE9F9CA2E8493063FA465F6E0E50E7725 | |||
| 3852 | PO#23754-1.exe | C:\Users\admin\AppData\Local\Temp\preferences-system-time-symbolic.symbolic.png | image | |
MD5:0925DDD685FA80B53628DD425D9FF667 | SHA256:E712DF36B7D82D547185C58222BECD976CB4039364B84DFD9C87A15913ABF72C | |||
| 3852 | PO#23754-1.exe | C:\Users\admin\AppData\Local\Temp\msvcp140_1.dll | executable | |
MD5:BAEB5294985628E64660CBC1EB8A5C92 | SHA256:6527B9B5A1B7D08B537375DADA65BC79F6B6A9BCECA55BC28F44EADA20E4CE8D | |||
| 3852 | PO#23754-1.exe | C:\Users\admin\AppData\Local\Temp\pan-start-symbolic-rtl.svg | binary | |
MD5:0463D94B405B42C5079CB27FEF8FF48F | SHA256:197F7ED3B106A2EEF1E64E33C4DEFB2D4C638CB69C280090964C50D62E9046E2 | |||
| 3852 | PO#23754-1.exe | C:\Users\admin\AppData\Local\Temp\nspD706.tmp | binary | |
MD5:59924AA0AC361C4FD6A6264AC02566E8 | SHA256:D089C4EDB66D55282C0427CE7187CDC52FE8081E1073246C7350216BE7E11DE1 | |||
| 3304 | mmc.exe | C:\Users\admin\AppData\Roaming\Microsoft\MMC\taskschd | xml | |
MD5:0D771A3C7102B71681726614A7BBA42A | SHA256:0B9BA1B52B1C5635E8A72C962A767CDABE8B2A7DC3CEFC64ADF9696D4B5A4D94 | |||
| 3544 | PO#23754-1.exe | C:\Users\admin\AppData\Local\Temp\nsp6E31.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 3852 | PO#23754-1.exe | C:\Users\admin\AppData\Local\Temp\system-run-symbolic.svg | image | |
MD5:B5F0AD599938A204B3FDCA3DEE9BC5BA | SHA256:A8D093B9C8DB36FCB276C7CD80580DDE2EAD3B708D02BDF79472C65F9164D457 | |||
| 3852 | PO#23754-1.exe | C:\Users\admin\AppData\Local\Temp\Bluetooth Suite help_CHS.chm | binary | |
MD5:61F393963844C9B470DF60260B433EEF | SHA256:990A82BED0498F2FA1DA7160AF3C06449A7529EBCAE09EAA0F67DF60346A0F3F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Threats
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|