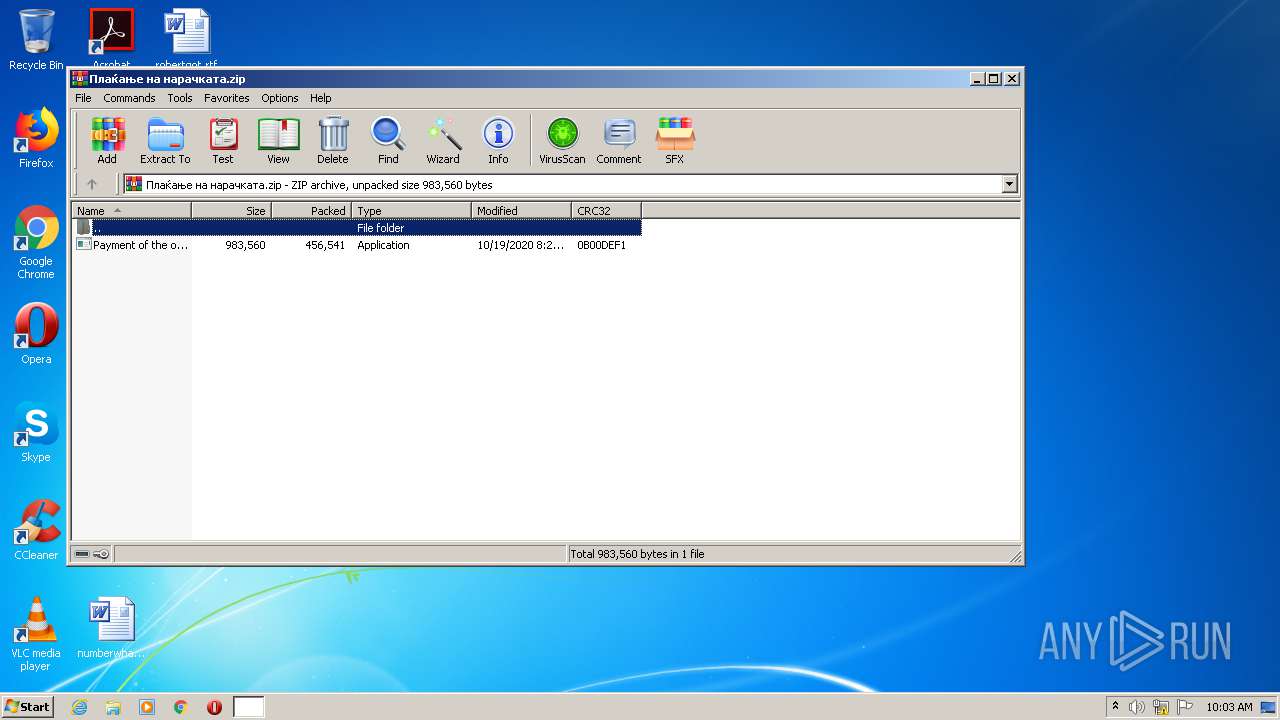
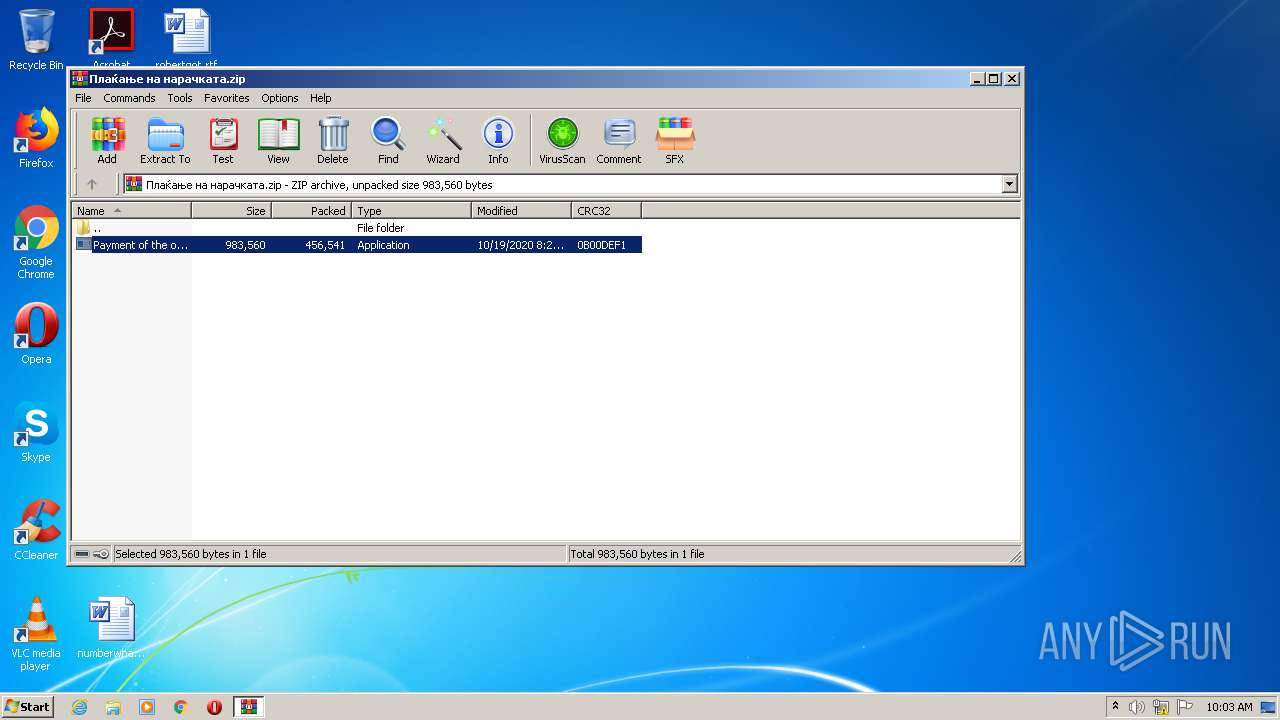
| File name: | Плаќање на нарачката.zip |
| Full analysis: | https://app.any.run/tasks/9fd382b5-6d15-46c6-ba5a-ab55f82c37e1 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | October 20, 2020, 09:03:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F075C4D54815972E0EFD57FAC60A990F |
| SHA1: | 1946BBF5C8281BFA650910FB5C893365986E2B29 |
| SHA256: | 14B71307278A520704F0E50768138DB6A8EEEC9093BD058451456E09285FB9B5 |
| SSDEEP: | 12288:p+bR2p8zKACuit3pQNfkOlLi6pspjrfGWfvaySk:p+bAp9APq5wfkOlLfmvG0va9k |
MALICIOUS
Application was dropped or rewritten from another process
- Payment of the order.exe (PID: 2104)
FORMBOOK was detected
- explorer.exe (PID: 392)
Connects to CnC server
- explorer.exe (PID: 392)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2728)
Reads Internet Cache Settings
- Payment of the order.exe (PID: 2104)
Creates files in the user directory
- Payment of the order.exe (PID: 2104)
Starts CMD.EXE for commands execution
- wininit.exe (PID: 2628)
INFO
Manual execution by user
- wininit.exe (PID: 2628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:10:19 08:29:08 |
| ZipCRC: | 0x0b00def1 |
| ZipCompressedSize: | 456541 |
| ZipUncompressedSize: | 983560 |
| ZipFileName: | Payment of the order.exe |
Total processes
41
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1084 | C:\Windows\System32\TapiUnattend.exe | C:\Windows\System32\TapiUnattend.exe | — | Payment of the order.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Windows(TM) Telephony Unattend Action Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2104 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.43572\Payment of the order.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.43572\Payment of the order.exe | WinRAR.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Sysinternals Process Explorer Exit code: 0 Version: 16.21 Modules
| |||||||||||||||
| 2628 | "C:\Windows\System32\wininit.exe" | C:\Windows\System32\wininit.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Start-Up Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2728 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Плаќање на нарачката.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2868 | /c del "C:\Windows\System32\TapiUnattend.exe" | C:\Windows\System32\cmd.exe | — | wininit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
500
Read events
465
Write events
35
Delete events
0
Modification events
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Плаќање на нарачката.zip | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (392) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (392) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
1
Suspicious files
7
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2104 | Payment of the order.exe | C:\Users\admin\AppData\Local\Temp\TarD6CE.tmp | — | |
MD5:— | SHA256:— | |||
| 2104 | Payment of the order.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\64DCC9872C5635B1B7891B30665E0558_5552C20A2631357820903FD38A8C0F9F | binary | |
MD5:— | SHA256:— | |||
| 2728 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.43572\Payment of the order.exe | executable | |
MD5:— | SHA256:— | |||
| 2104 | Payment of the order.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_979AB563CEB98F2581C14ED89B8957D4 | binary | |
MD5:— | SHA256:— | |||
| 2104 | Payment of the order.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6AF4EE75E3A4ABA658C0087EB9A0BB5B_F80805103A05D4F74523519C6EAD8FC0 | binary | |
MD5:— | SHA256:— | |||
| 2104 | Payment of the order.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_979AB563CEB98F2581C14ED89B8957D4 | der | |
MD5:— | SHA256:— | |||
| 2104 | Payment of the order.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\WWRY52G0.txt | text | |
MD5:— | SHA256:— | |||
| 2104 | Payment of the order.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\Cfabbbb[1] | text | |
MD5:— | SHA256:— | |||
| 2104 | Payment of the order.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6AF4EE75E3A4ABA658C0087EB9A0BB5B_F80805103A05D4F74523519C6EAD8FC0 | der | |
MD5:— | SHA256:— | |||
| 2104 | Payment of the order.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\64DCC9872C5635B1B7891B30665E0558_5552C20A2631357820903FD38A8C0F9F | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
12
DNS requests
12
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
392 | explorer.exe | GET | — | 49.156.179.92:80 | http://www.5yg7lidmzsj9gw.xyz/m3px/?1b0l=M/L2CxeXfQ9uCPhwF2iOpdLlAOIrHulaftlfvPNPk+mcu9y4+KuFF2qp61Wvr9FqJWgjAw==&4hD=uDzxV4Ux-27x5Pi | JP | — | — | malicious |
392 | explorer.exe | GET | 403 | 34.102.136.180:80 | http://www.watchdoglogistics.com/m3px/?1b0l=wVwQk1jBEX18feWJFYfDdlG9aKclO+LavpqocmEZ2rB6cEzVz0BKRa1+VXNPTcUYZdmzxw==&4hD=uDzxV4Ux-27x5Pi | US | html | 275 b | whitelisted |
2104 | Payment of the order.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 314 b | whitelisted |
392 | explorer.exe | GET | 403 | 34.102.136.180:80 | http://www.useae.com/m3px/?1b0l=oDKLHSUM9/RFTVhgcLaNFx49hQzKuAGOdb7EnICeqxRvRkGQ0aTFRQdDlweRKXxP/hWeog==&4hD=uDzxV4Ux-27x5Pi | US | html | 275 b | whitelisted |
2104 | Payment of the order.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEBblhnjgcJQ5S9%2FbTvymO98%3D | US | der | 471 b | whitelisted |
392 | explorer.exe | GET | 403 | 34.102.136.180:80 | http://www.wiscoed.com/m3px/?1b0l=JdaMrUsBsDNiP7lidk3lG7bFf6pED3ud+ifqRIlrQwrtfXAbc/Y2888vm28gWujWJLEhoA==&4hD=uDzxV4Ux-27x5Pi | US | html | 275 b | whitelisted |
392 | explorer.exe | GET | 403 | 34.102.136.180:80 | http://www.erotichypnotheapist.com/m3px/?1b0l=odazrgnMKT5oLEGvhfCK74iR1pKRj0c/jb7buhBrEkByqu5/qG/9Wv/izJZgXNsQlBT00Q==&4hD=uDzxV4Ux-27x5Pi | US | html | 275 b | whitelisted |
2104 | Payment of the order.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEDJAnJQUGG0bwuno3m2vDJ8%3D | US | der | 278 b | whitelisted |
392 | explorer.exe | GET | 403 | 34.102.136.180:80 | http://www.kvtlawyers.net/m3px/?1b0l=OuKuNjxbJmXzrAbYb5ePnb1TwpR+6zf5ab1W/6jpGt2Bd29/YTDVCu2bg4LIP6s6yRMp9A==&4hD=uDzxV4Ux-27x5Pi | US | html | 275 b | whitelisted |
392 | explorer.exe | GET | 301 | 184.168.131.241:80 | http://www.militaryhomedecisions.com/m3px/?1b0l=Azg8whItreoVKK3pHw/p3xAQsUof+k6iKzJRyf/ew2+zE/0Cnsv/aEhb7JaDUlmGf8Y+wg==&4hD=uDzxV4Ux-27x5Pi | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | Payment of the order.exe | 162.159.135.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
2104 | Payment of the order.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
— | — | 34.102.136.180:80 | www.erotichypnotheapist.com | — | US | whitelisted |
392 | explorer.exe | 184.168.131.241:80 | www.militaryhomedecisions.com | GoDaddy.com, LLC | US | shared |
— | — | 23.210.249.93:443 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
392 | explorer.exe | 34.102.136.180:80 | www.erotichypnotheapist.com | — | US | whitelisted |
392 | explorer.exe | 49.156.179.92:80 | www.5yg7lidmzsj9gw.xyz | Ace, Inc. | JP | malicious |
392 | explorer.exe | 5.182.210.249:80 | www.nibblemirror.com | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
cdn.discordapp.com |
| shared |
ocsp.comodoca.com |
| whitelisted |
ocsp.comodoca4.com |
| whitelisted |
www.erotichypnotheapist.com |
| whitelisted |
www.watchdoglogistics.com |
| whitelisted |
www.5yg7lidmzsj9gw.xyz |
| malicious |
www.useae.com |
| whitelisted |
www.wiscoed.com |
| whitelisted |
www.nibblemirror.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
392 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
392 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
392 | explorer.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 3 |
392 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
392 | explorer.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
392 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
392 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
392 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
392 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
392 | explorer.exe | A Network Trojan was detected | SPYWARE [PTsecurity] FormBook |
8 ETPRO signatures available at the full report