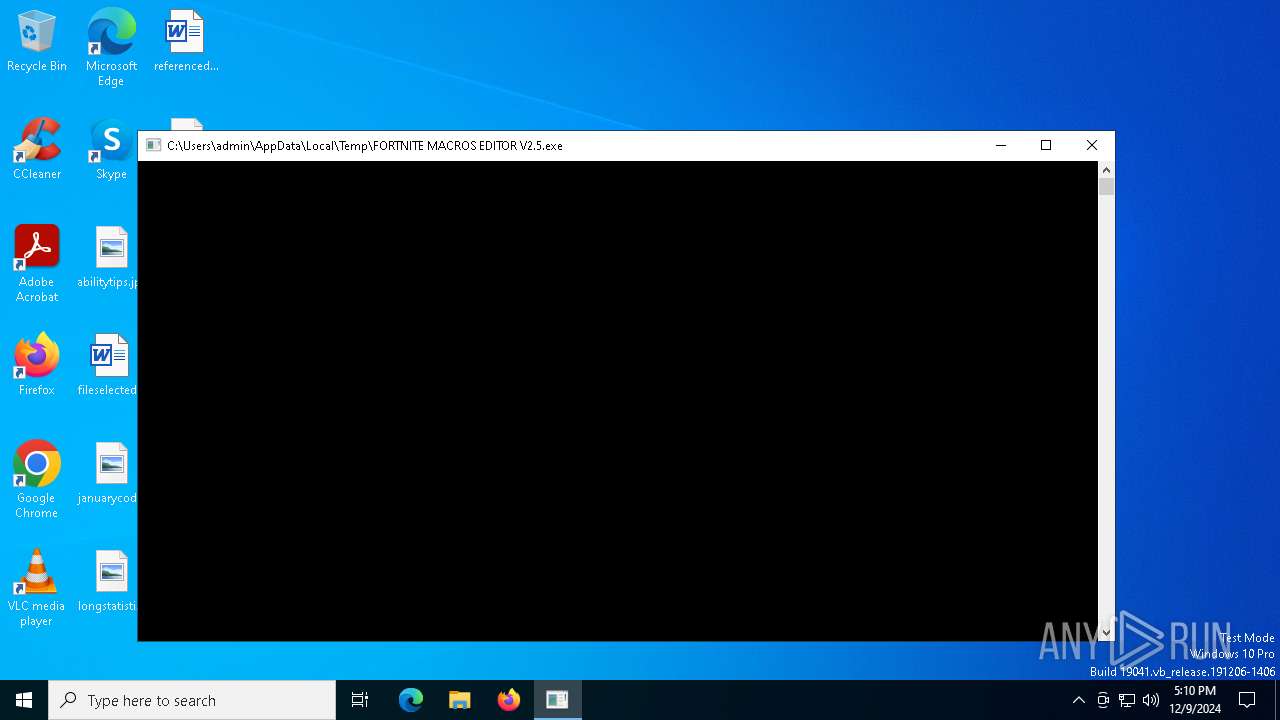
| File name: | FORTNITE MACROS EDITOR V2.5.exe |
| Full analysis: | https://app.any.run/tasks/452b4b46-c7fe-4c16-b04f-f3363492d0b9 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | December 09, 2024, 17:10:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 5 sections |
| MD5: | B6FFC5AB3D9C3D132B0CDB490ED800D2 |
| SHA1: | 69F55A57D6353649C3F709163BB7D440A3A7EB7F |
| SHA256: | 138671F56898C4504A02588C6F9C4DE6A3961CE015BB147D579BD54BC454DED1 |
| SSDEEP: | 24576:ROsd3ML+s+chtJ6gynFz+Dto8rP9koMe5e+MkdeIzTI99fjcB2msnsWdWPpaM:ROsd3MLP+chtJ6gyFz+Dto8b9koMe5e0 |
MALICIOUS
Connects to the CnC server
- svchost.exe (PID: 2192)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2192)
- aspnet_regiis.exe (PID: 6268)
Actions looks like stealing of personal data
- aspnet_regiis.exe (PID: 6268)
SUSPICIOUS
Process drops legitimate windows executable
- FORTNITE MACROS EDITOR V2.5.exe (PID: 5464)
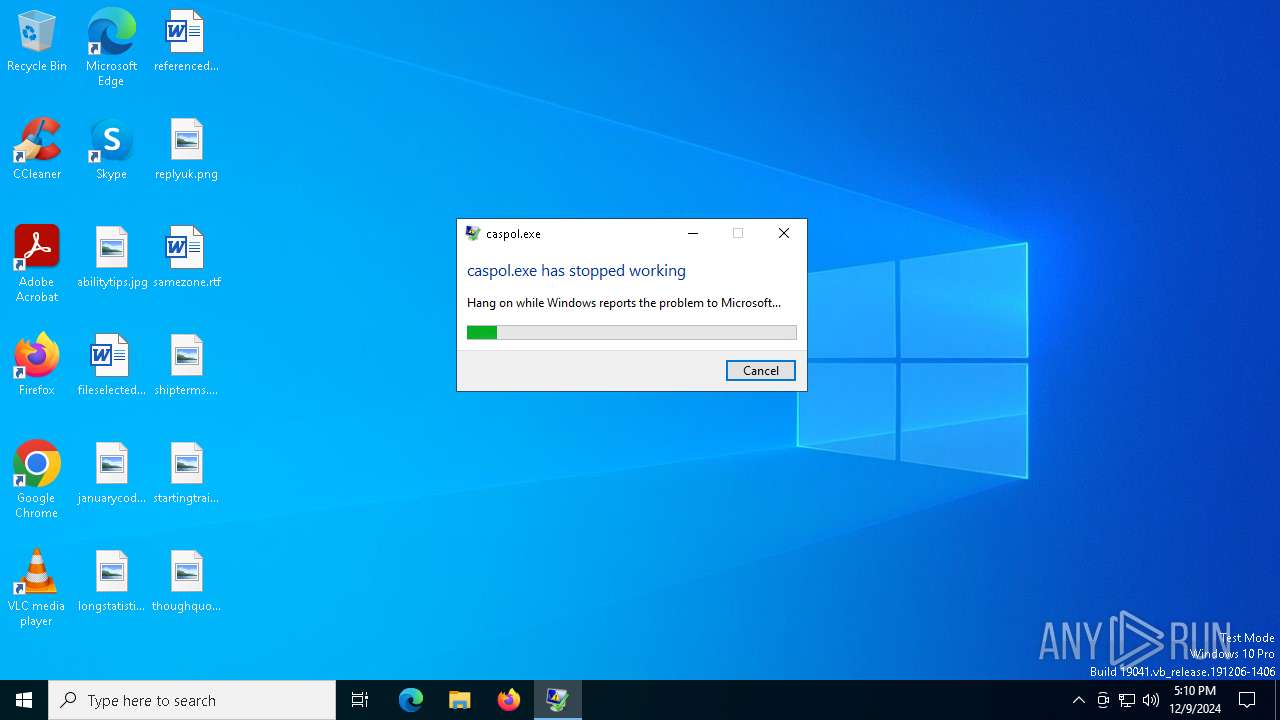
Executes application which crashes
- FORTNITE MACROS EDITOR V2.5.exe (PID: 5464)
Starts a Microsoft application from unusual location
- FORTNITE MACROS EDITOR V2.5.exe (PID: 5464)
Executable content was dropped or overwritten
- FORTNITE MACROS EDITOR V2.5.exe (PID: 5464)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2192)
- aspnet_regiis.exe (PID: 6268)
INFO
Reads the computer name
- FORTNITE MACROS EDITOR V2.5.exe (PID: 5464)
Checks supported languages
- FORTNITE MACROS EDITOR V2.5.exe (PID: 5464)
- aspnet_regiis.exe (PID: 6268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:11:29 06:07:52+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 127488 |
| InitializedDataSize: | 574464 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb200a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 4.8.9037.0 |
| ProductVersionNumber: | 4.8.9037.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | caspol.exe |
| CompanyName: | Microsoft Corporation |
| FileDescription: | caspol.exe |
| FileVersion: | 4.8.9037.0 |
| InternalName: | EleanorUlyssesLiam.ExjX |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | EleanorUlyssesLiam.ExjX |
| ProductName: | Microsoft® .NET Framework |
| ProductVersion: | 4.8.9037.0 |
| AssemblyVersion: | 4.0.0.0 |
Total processes
131
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | FORTNITE MACROS EDITOR V2.5.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5464 | "C:\Users\admin\AppData\Local\Temp\FORTNITE MACROS EDITOR V2.5.exe" | C:\Users\admin\AppData\Local\Temp\FORTNITE MACROS EDITOR V2.5.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: caspol.exe Version: 4.8.9037.0 Modules
| |||||||||||||||
| 6268 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regiis.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regiis.exe | FORTNITE MACROS EDITOR V2.5.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_regiis.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 6412 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5464 -s 1196 | C:\Windows\SysWOW64\WerFault.exe | FORTNITE MACROS EDITOR V2.5.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 937
Read events
3 937
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
3
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6412 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_FORTNITE MACROS _76de8ecd7ce9ccaa5297163e7aaf1ef4cdc170_c11c0eac_0584c735-3d65-4042-878b-686cd4318abe\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6412 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FB8D3C072ED65E98BBB8F753D862FB9C | SHA256:89F85DCA9F010230D1DBBB9F872EB2AA847A263E4BF341FE20138A1D09F03130 | |||
| 6412 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5C6D.tmp.xml | xml | |
MD5:4A6CF7C91097F429B290A2223A3F0AA8 | SHA256:4607F7A02C3A5C29C9B38F04692066F7CB086FC744E7249A70D866F51A67CF42 | |||
| 6412 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5B04.tmp.dmp | binary | |
MD5:F693E301D09C7B1EAE66280B4EF2C994 | SHA256:309EA0C03D01B107679EAE4A8EFD15566783DF47A8DCFFFA00B84993A0EA4B5C | |||
| 6412 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:BADDDEDAB86C55CB31F81BF25BA4133E | SHA256:6BE1DBDDEC786BF38423CAE2CE368A7BFEA2D69658004294DA4B183ED3E68F71 | |||
| 6412 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:F0CF5B1794ECA7CD73F9C020DAAB8EF2 | SHA256:2AF00EDCE7EF3266897E52DC81E8DE3B7A079028C0F1F96EAFF9E38AD342F617 | |||
| 6412 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5C3D.tmp.WERInternalMetadata.xml | xml | |
MD5:F8271F41CB86CE1151CE5DE74F3278E7 | SHA256:B78032A09D41E6E485C33B0A3D10FAE173C6FB4F9925E2D94130B68FB57BED73 | |||
| 6412 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:F6F53CD09A41E968C363419B279D3112 | SHA256:6D2BB01CC7A9BADE2113B219CAC1BDA86B2733196B7E1BD0C807CE1E396B1892 | |||
| 5464 | FORTNITE MACROS EDITOR V2.5.exe | C:\Users\admin\AppData\Roaming\gdi32.dll | executable | |
MD5:EADCFD7C84686DA06B4FC381BFC96C72 | SHA256:ABB95C10AE4B1FF0AA36895D5001D3259F91DFD1BC5C6DFE77F6194BE1B41D4B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
38
DNS requests
21
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7068 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7068 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6412 | WerFault.exe | GET | 200 | 2.16.164.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6412 | WerFault.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
440 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6268 | aspnet_regiis.exe | 172.67.162.65:443 | se-blurry.biz | CLOUDFLARENET | US | malicious |
1176 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
farewellnzu.icu |
| unknown |
se-blurry.biz |
| malicious |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (farewellnzu .icu) |
6268 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (se-blurry .biz in TLS SNI) |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (se-blurry .biz) |
6268 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (se-blurry .biz in TLS SNI) |
6268 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (se-blurry .biz in TLS SNI) |
6268 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (se-blurry .biz in TLS SNI) |
6268 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (se-blurry .biz in TLS SNI) |
6268 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (se-blurry .biz in TLS SNI) |
6268 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (se-blurry .biz in TLS SNI) |