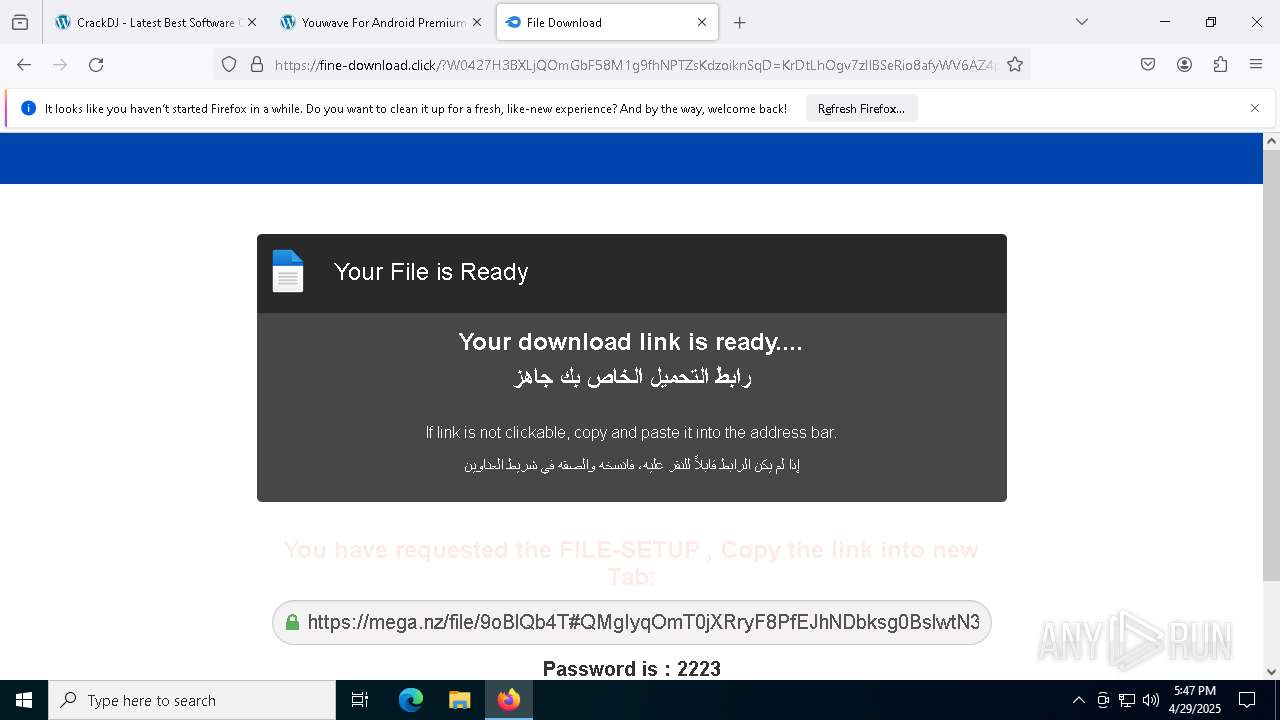
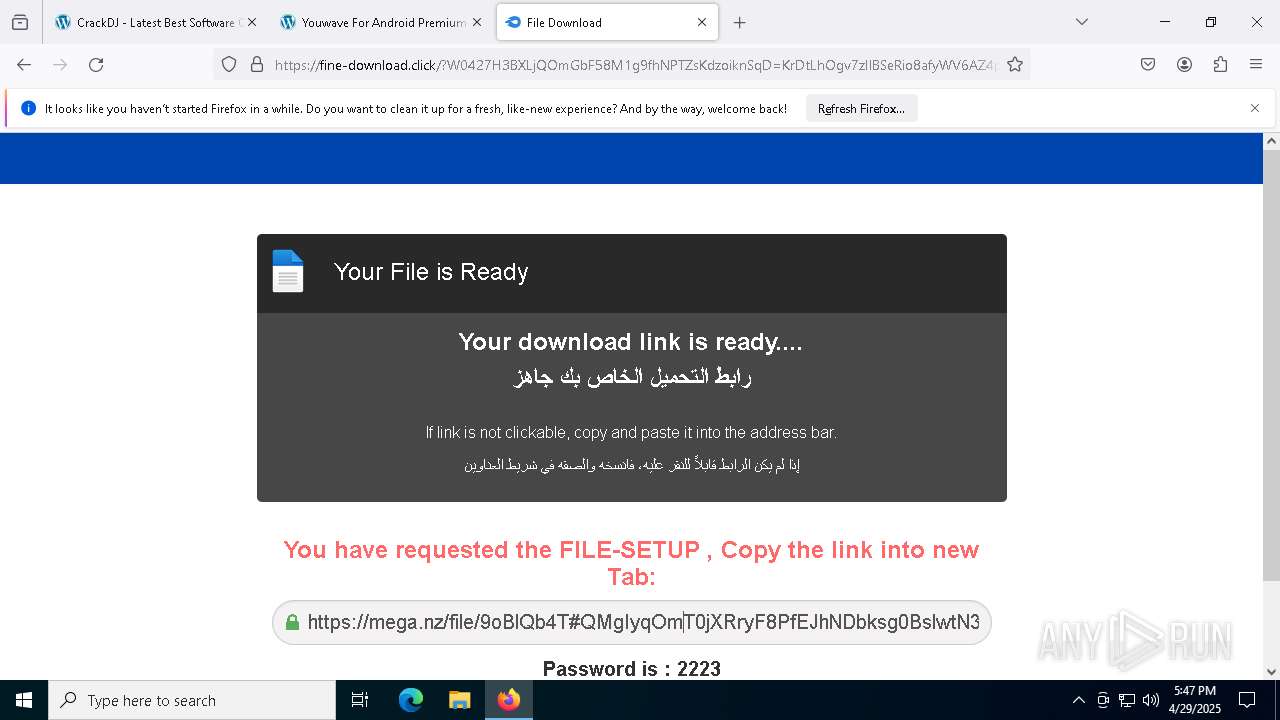
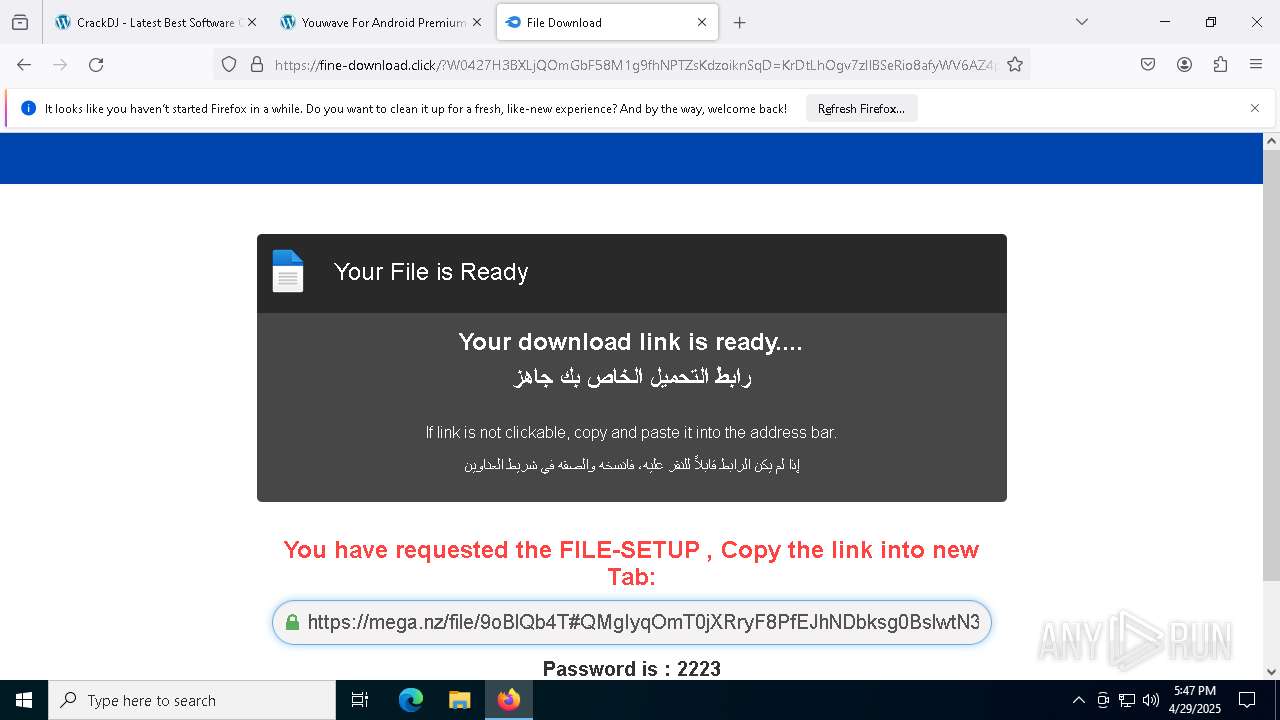
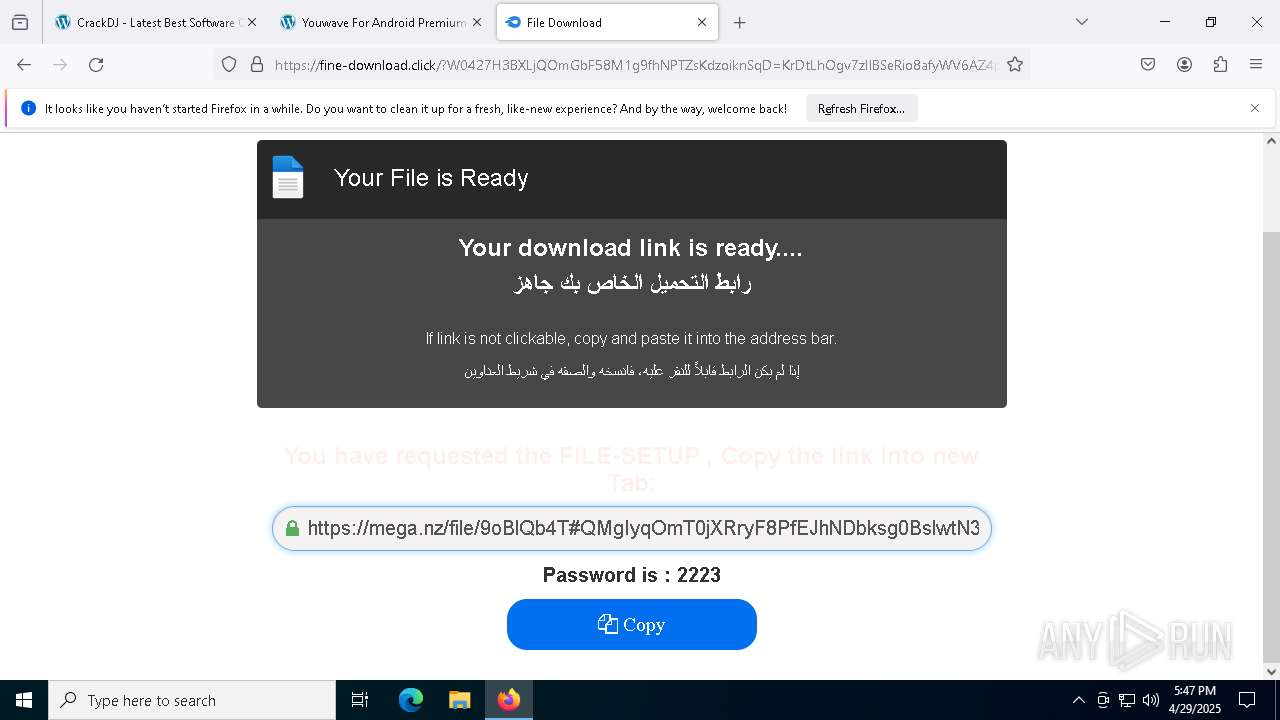
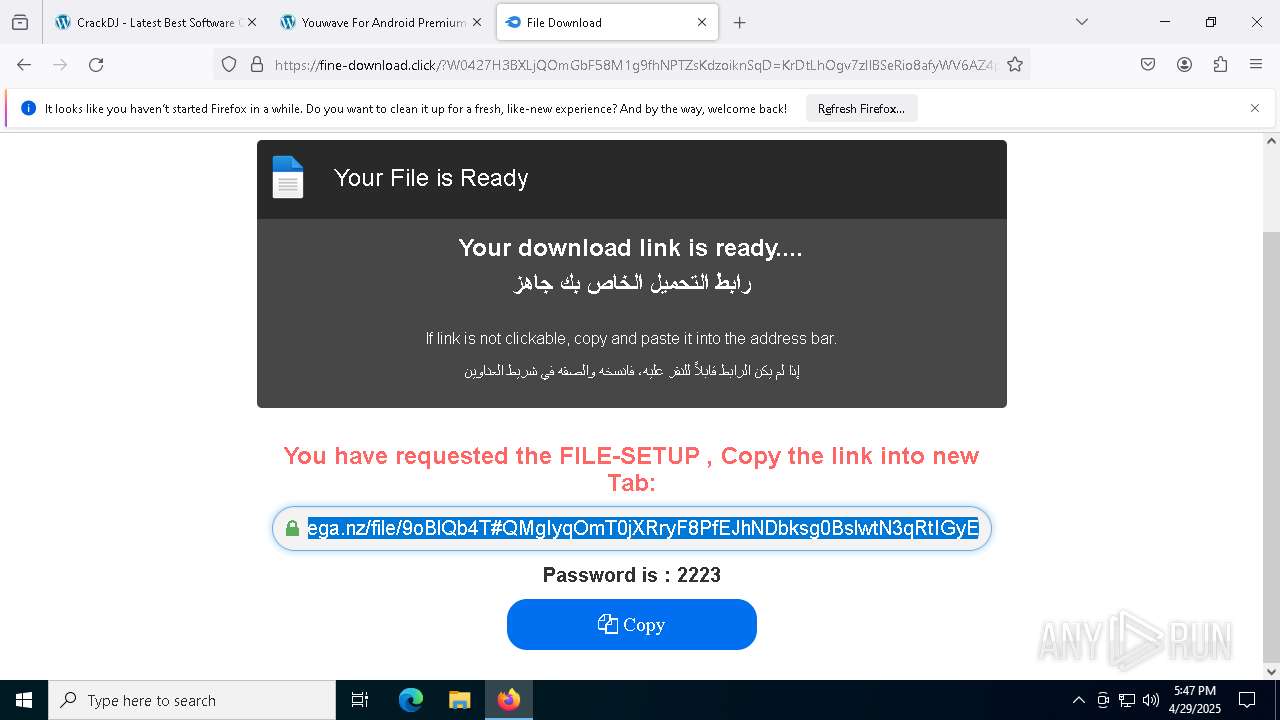
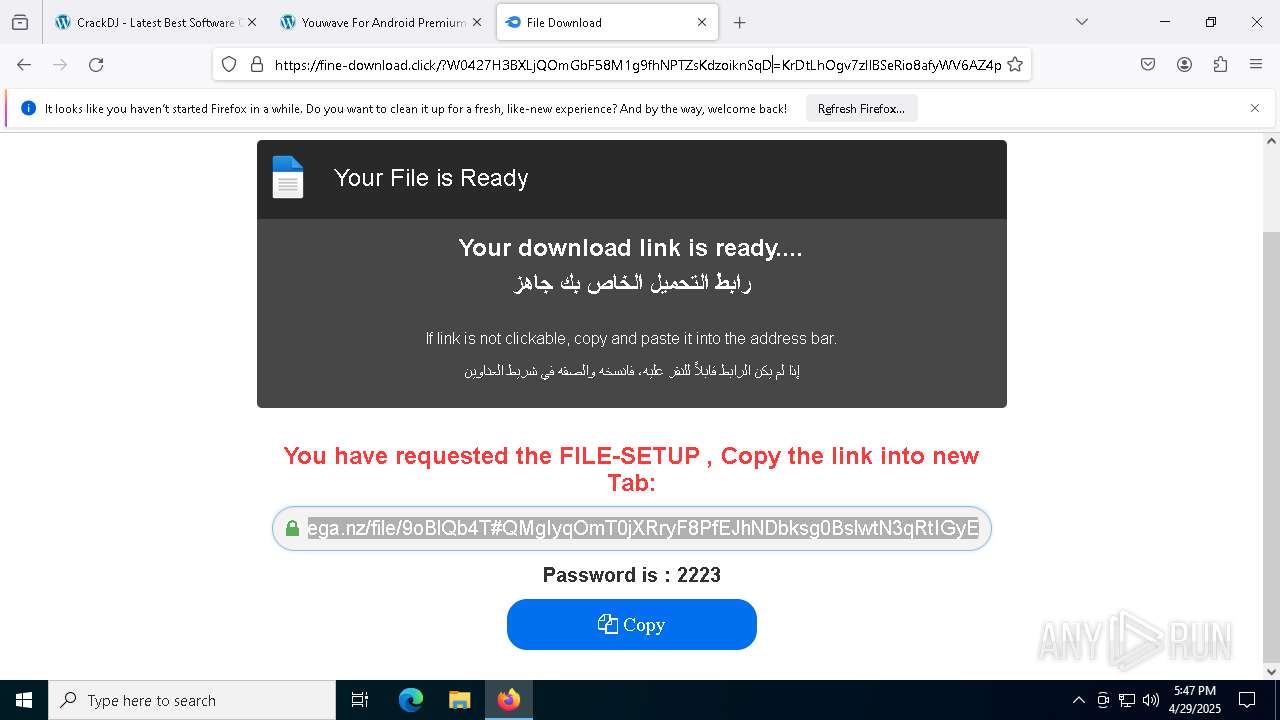
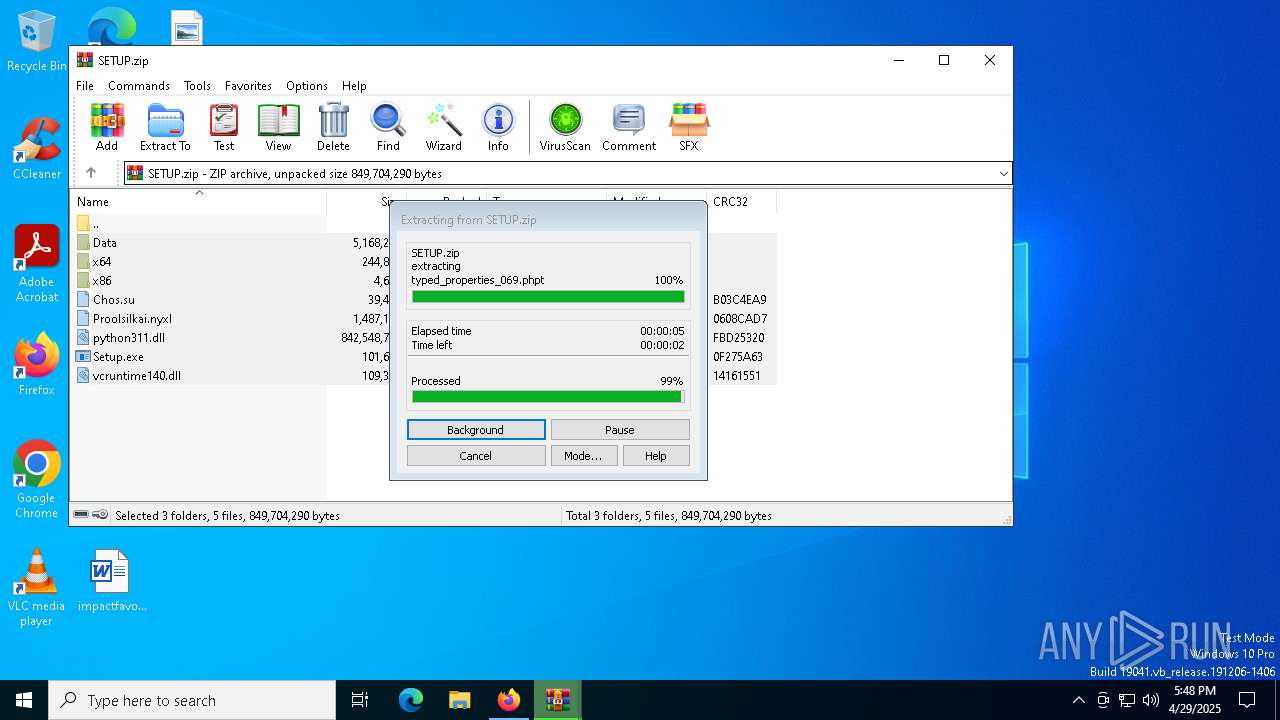
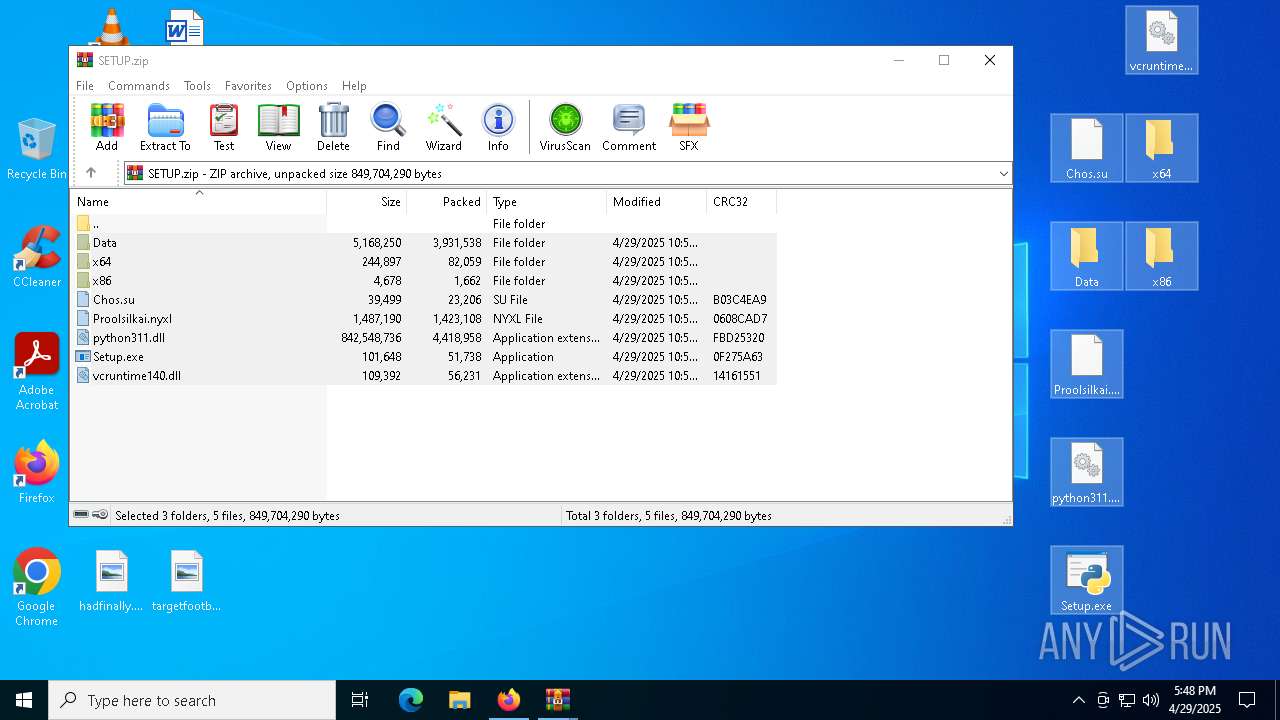
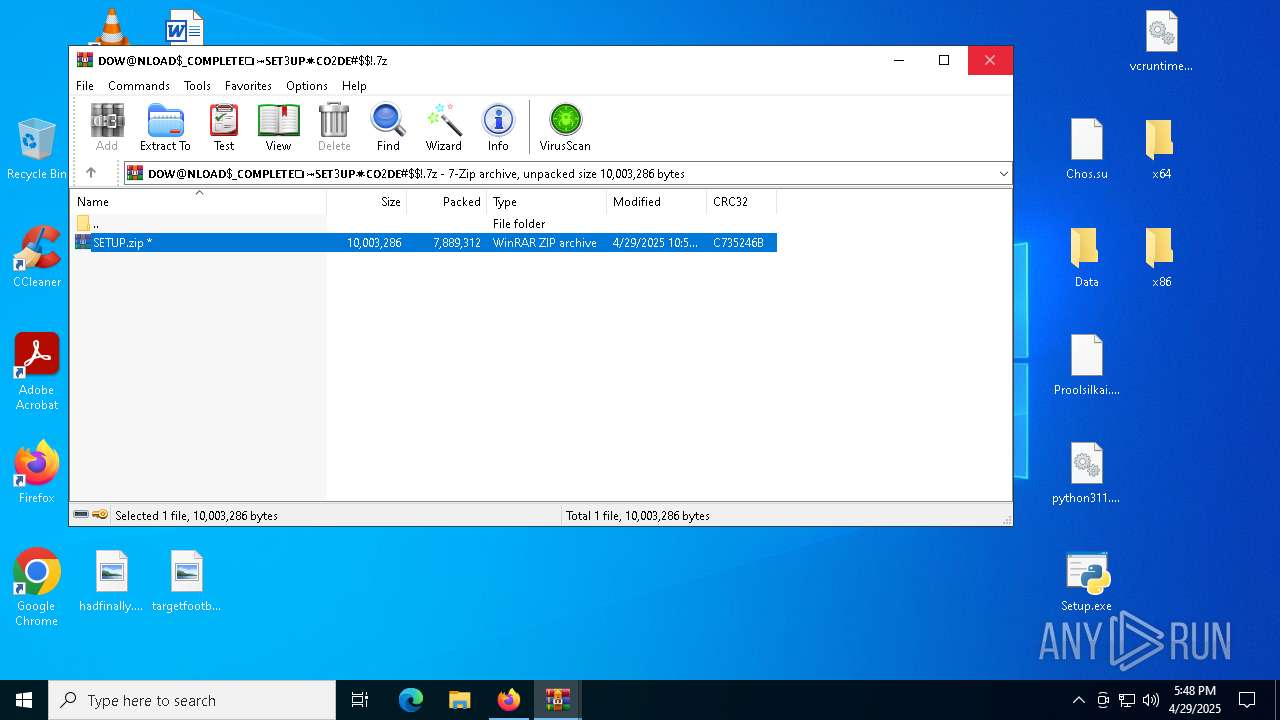
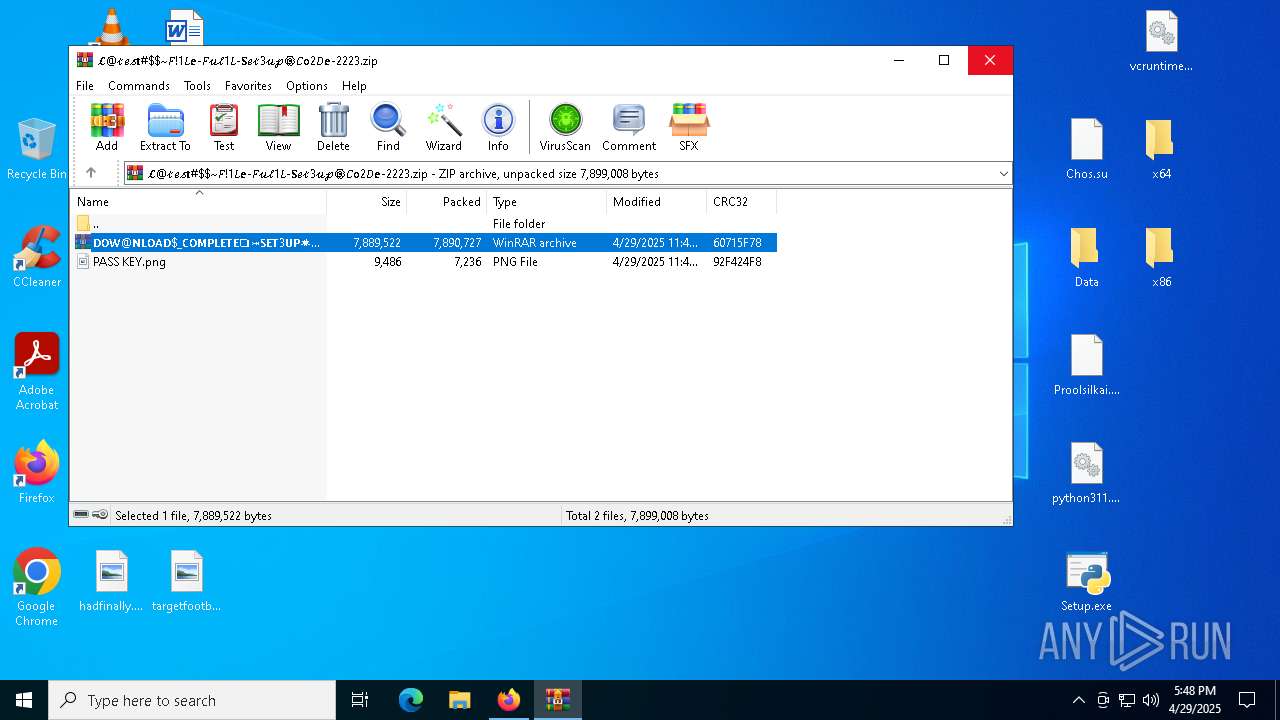
| URL: | https://crackdj.com |
| Full analysis: | https://app.any.run/tasks/00f639d3-2c11-4c36-81ca-d68effea22a7 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 29, 2025, 17:47:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 011288459A04E50A48854F3A1C8A9FC8 |
| SHA1: | 7E55ACAEFEE5260580A118769932C0682C06BFFD |
| SHA256: | 1332F2F4EC17D58EC774E9EE35C3542570801D7ACC3C28DDBF9141F40A090305 |
| SSDEEP: | 3:N8KmGT:2KJ |
MALICIOUS
LUMMA has been detected (YARA)
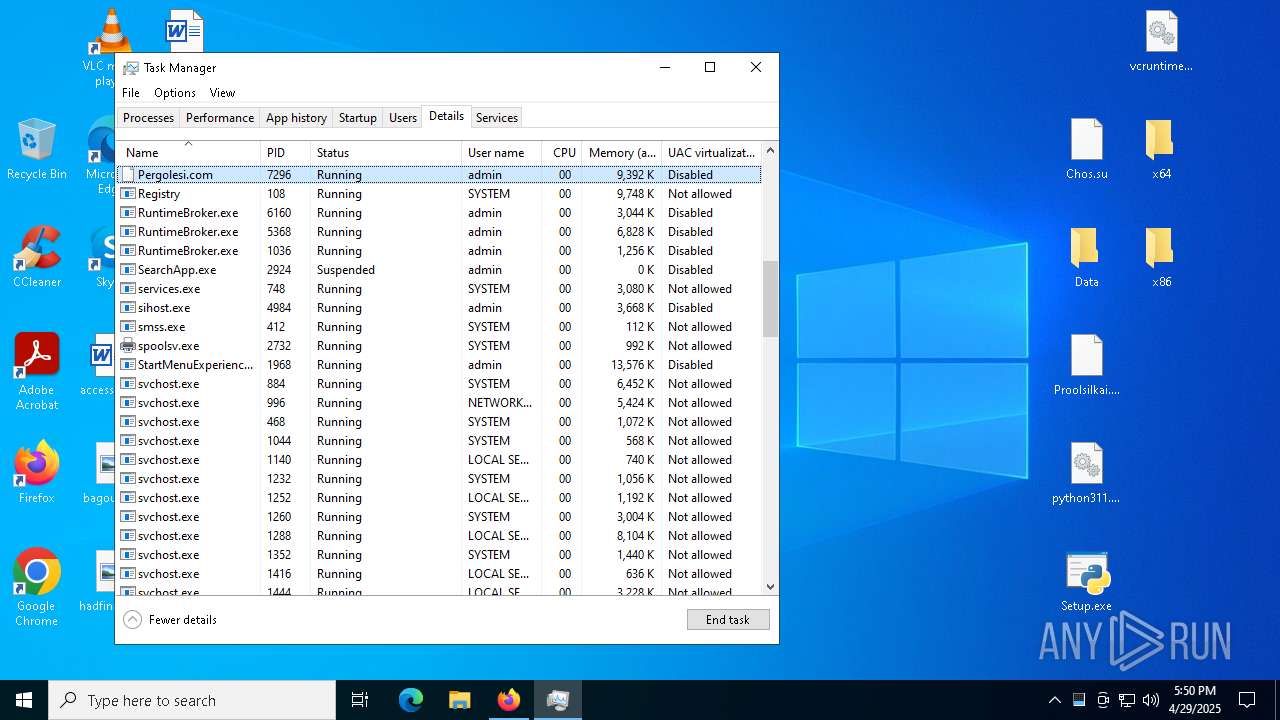
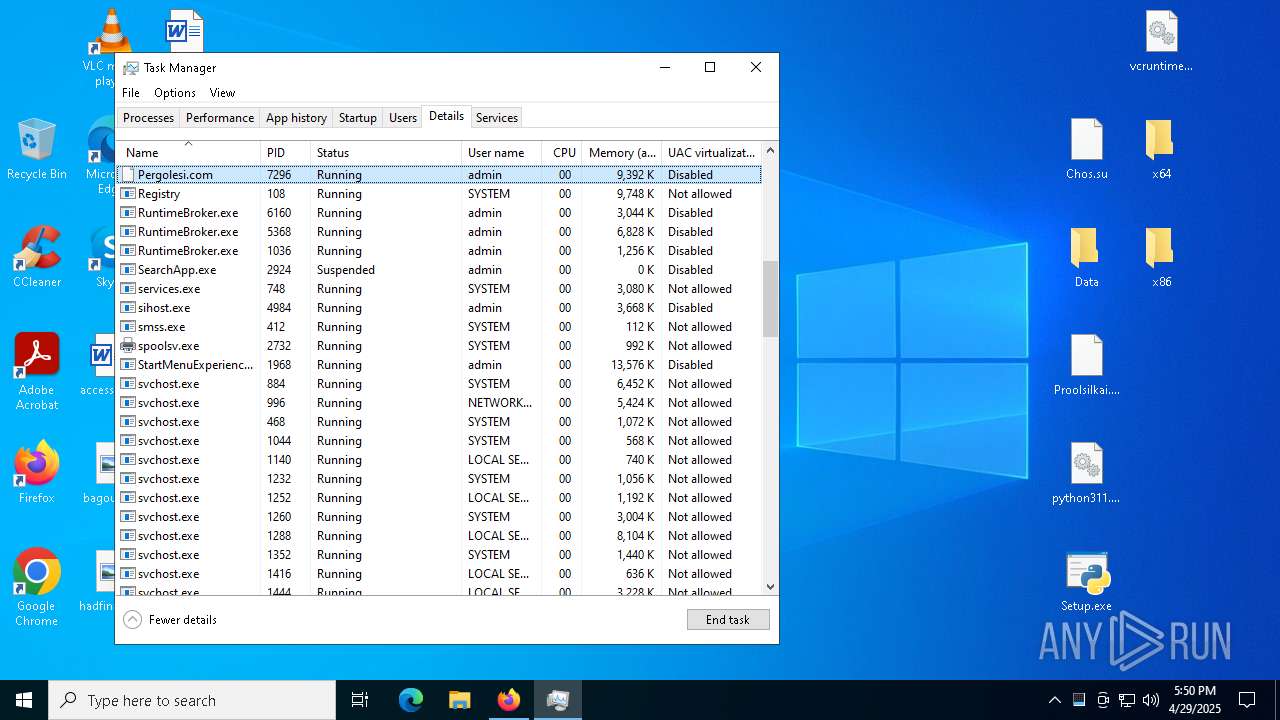
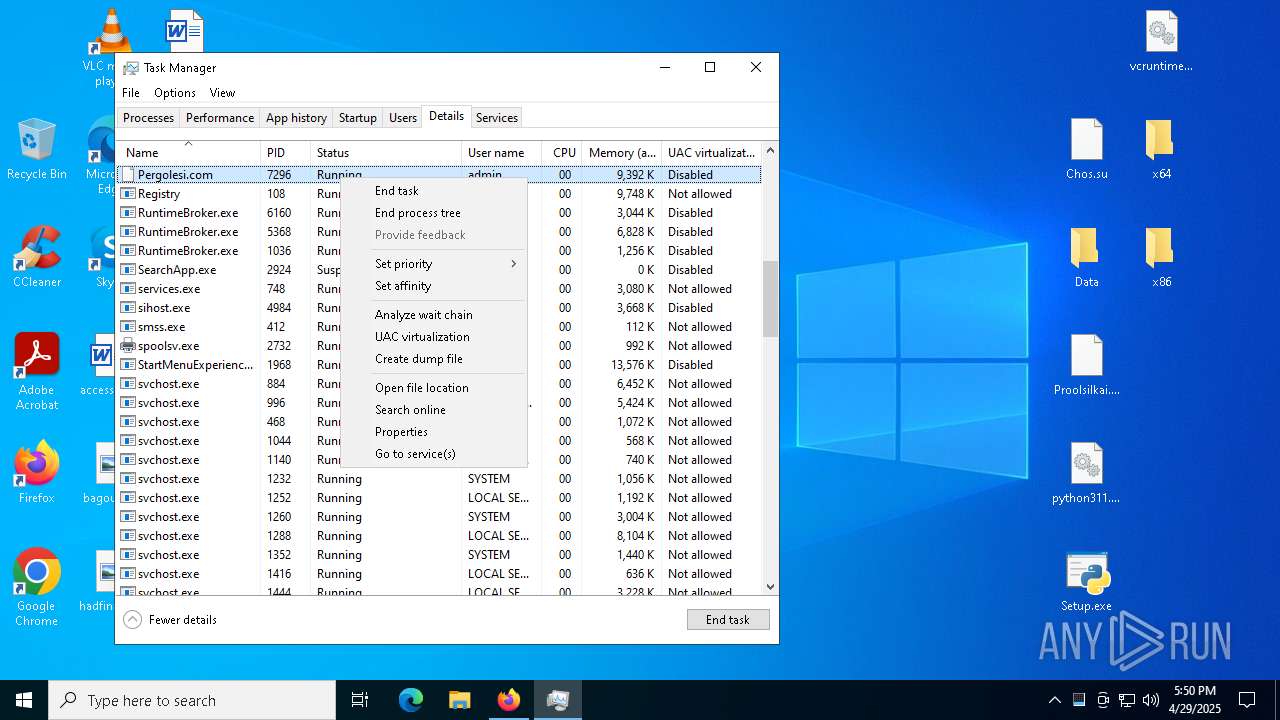
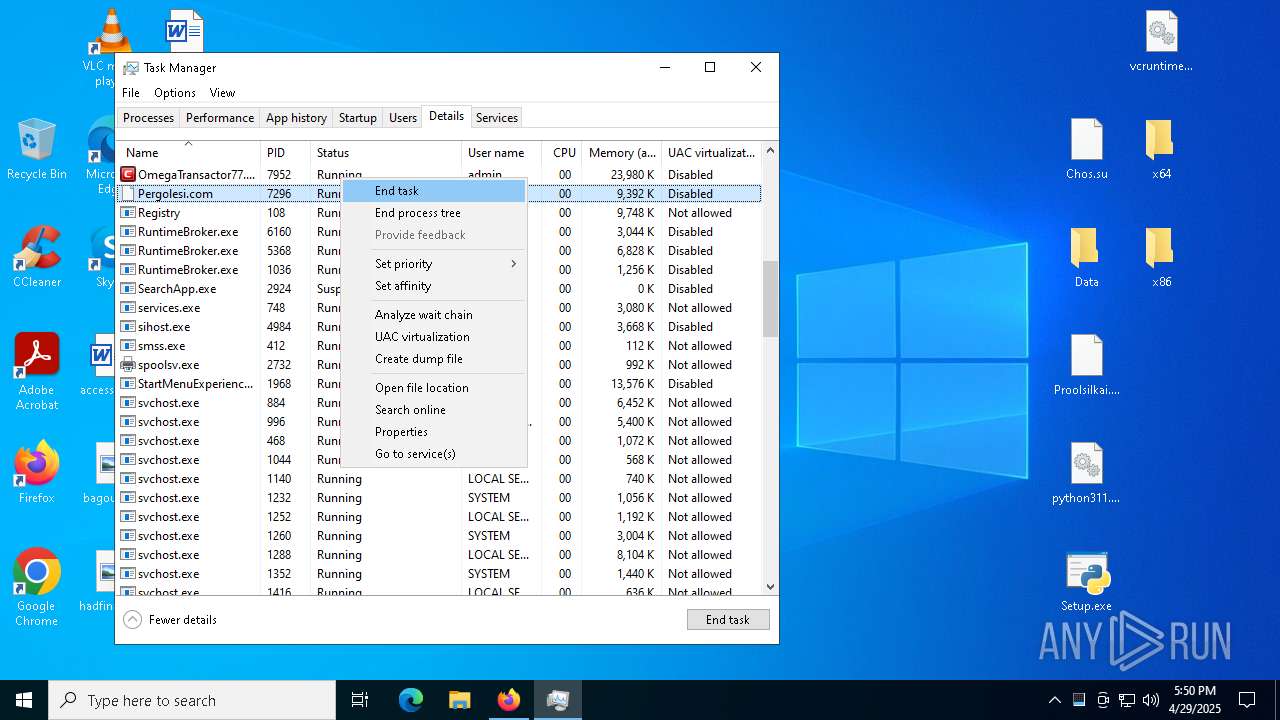
- Pergolesi.com (PID: 7296)
HIJACKLOADER has been detected (YARA)
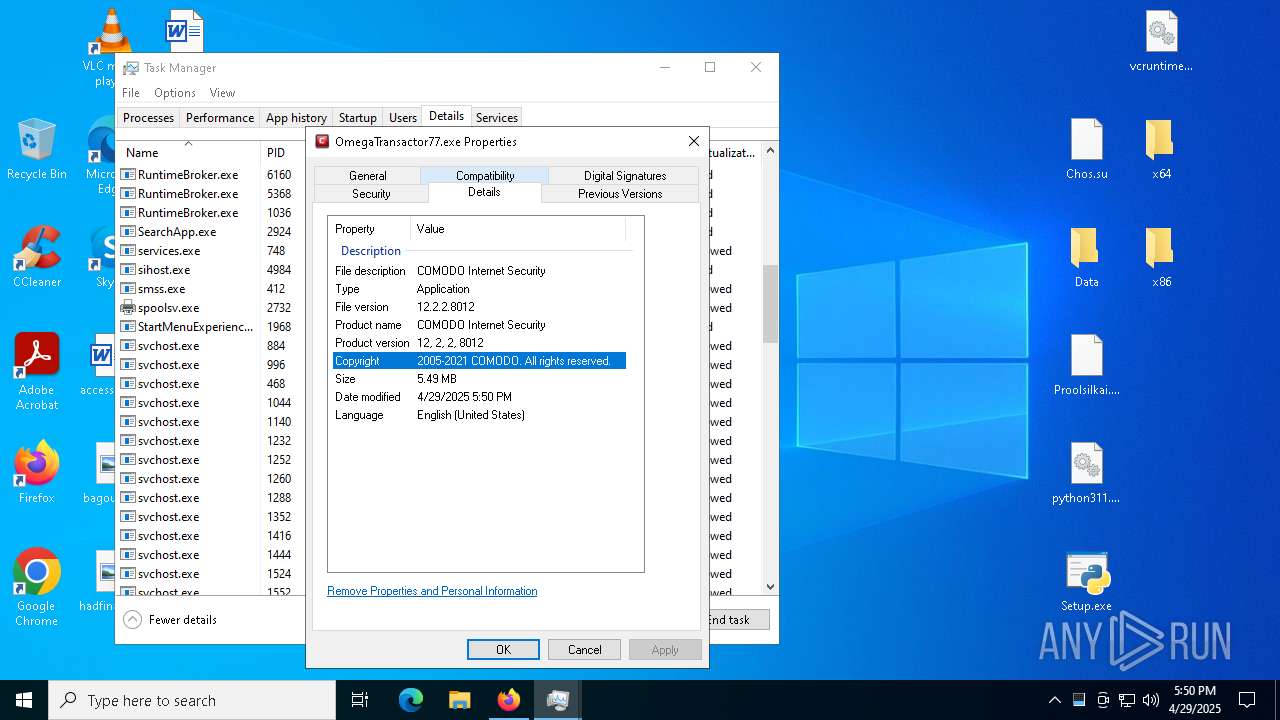
- Setup.exe (PID: 1240)
- OmegaTransactor77.exe (PID: 7952)
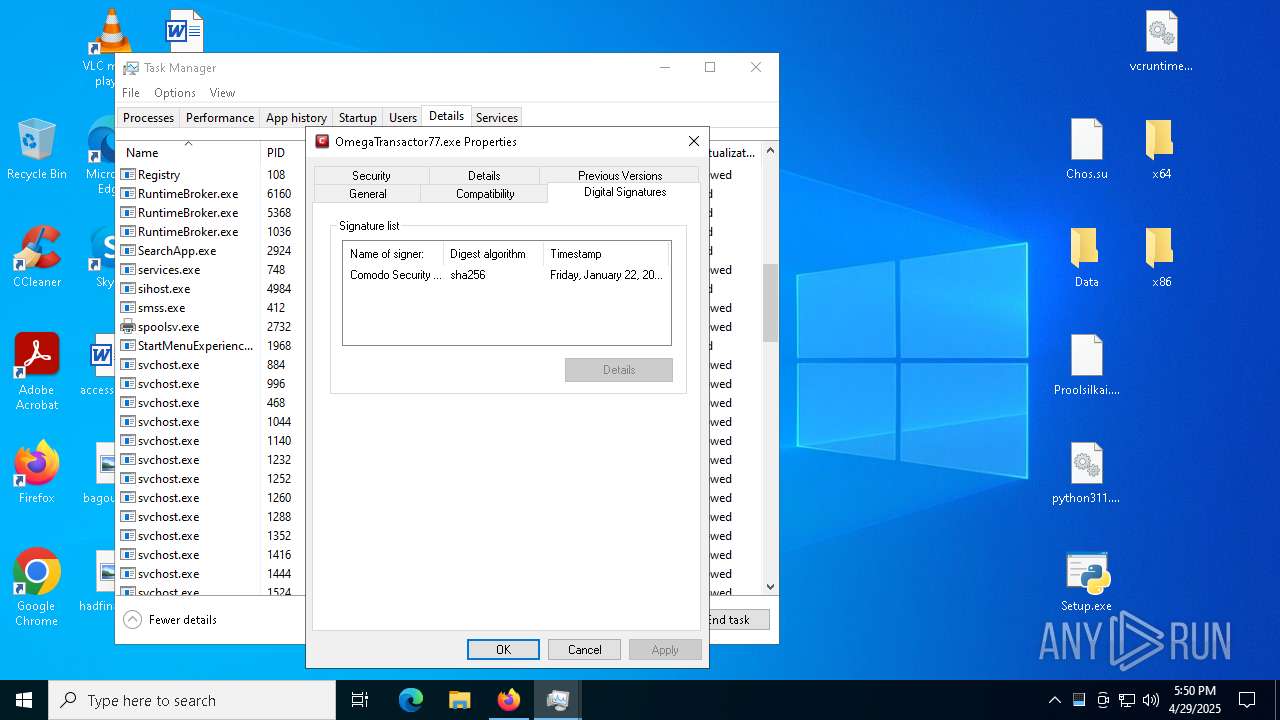
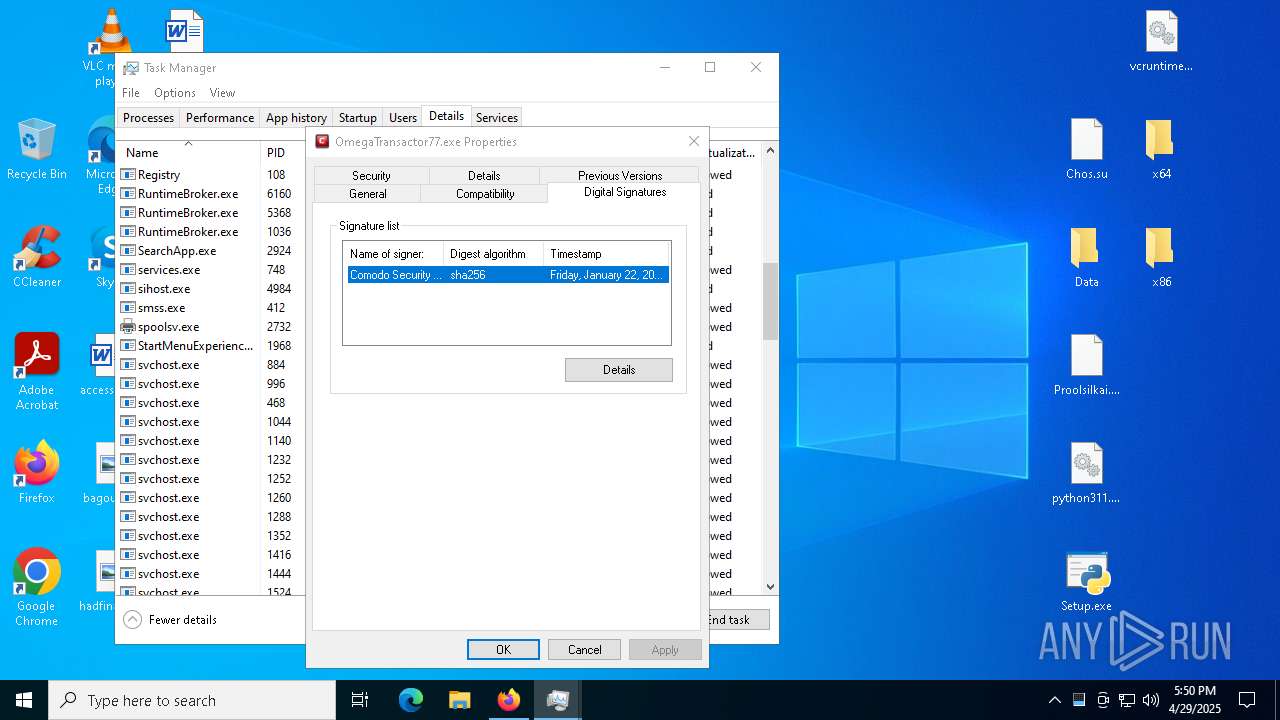
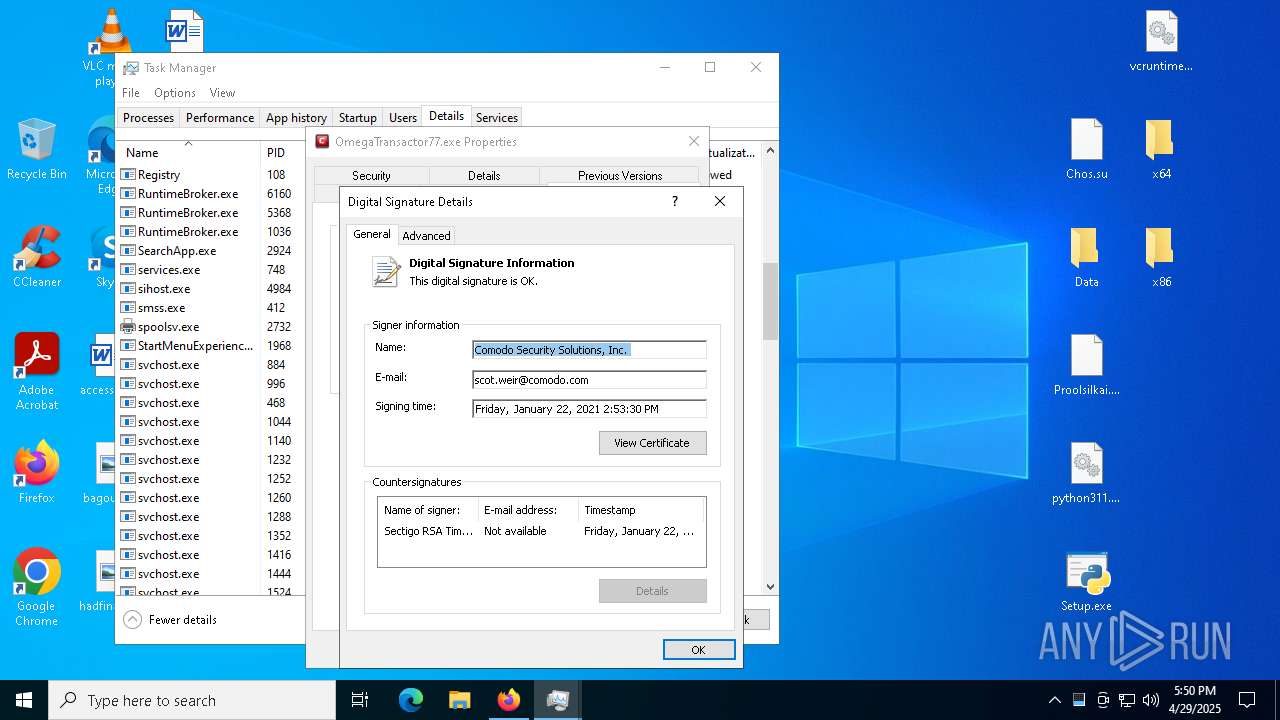
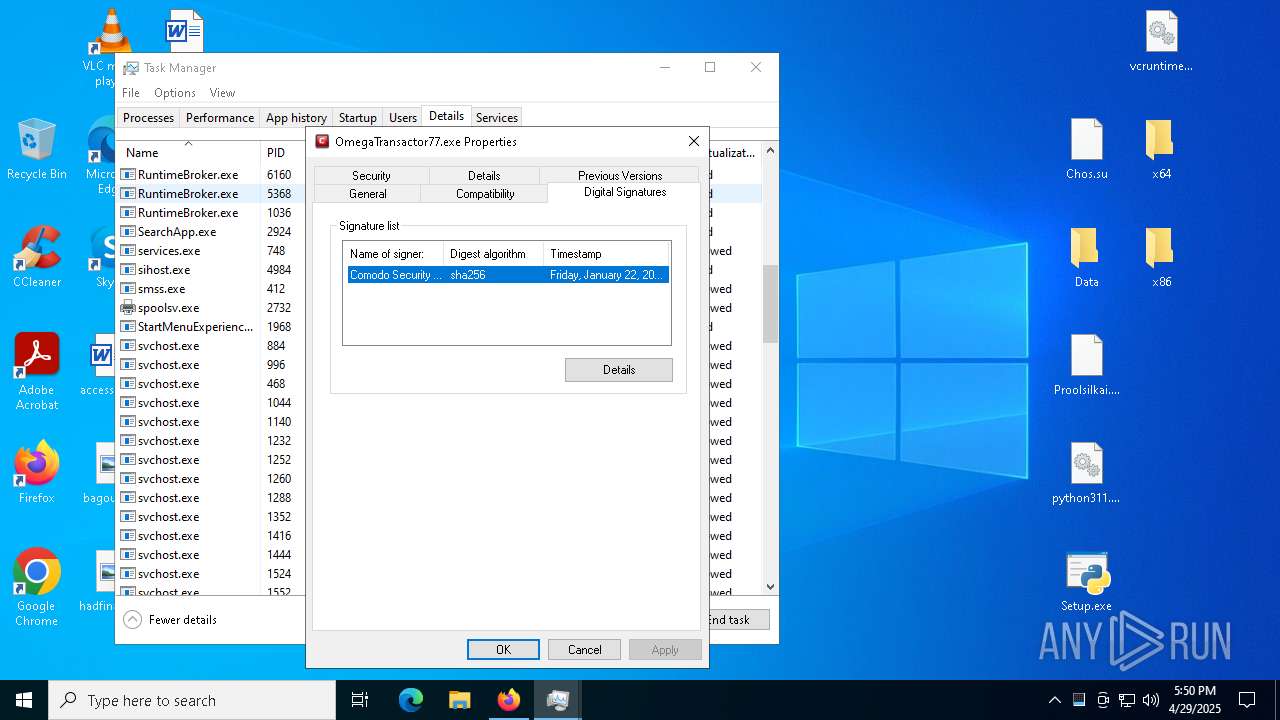
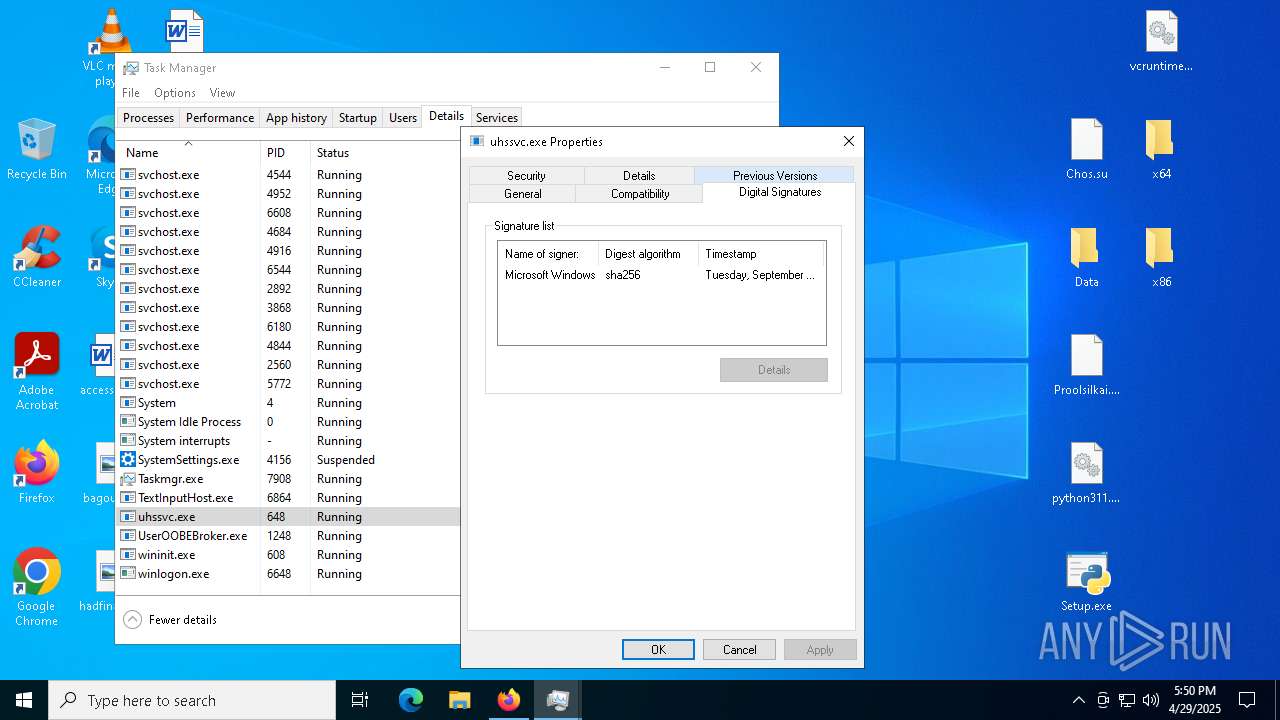
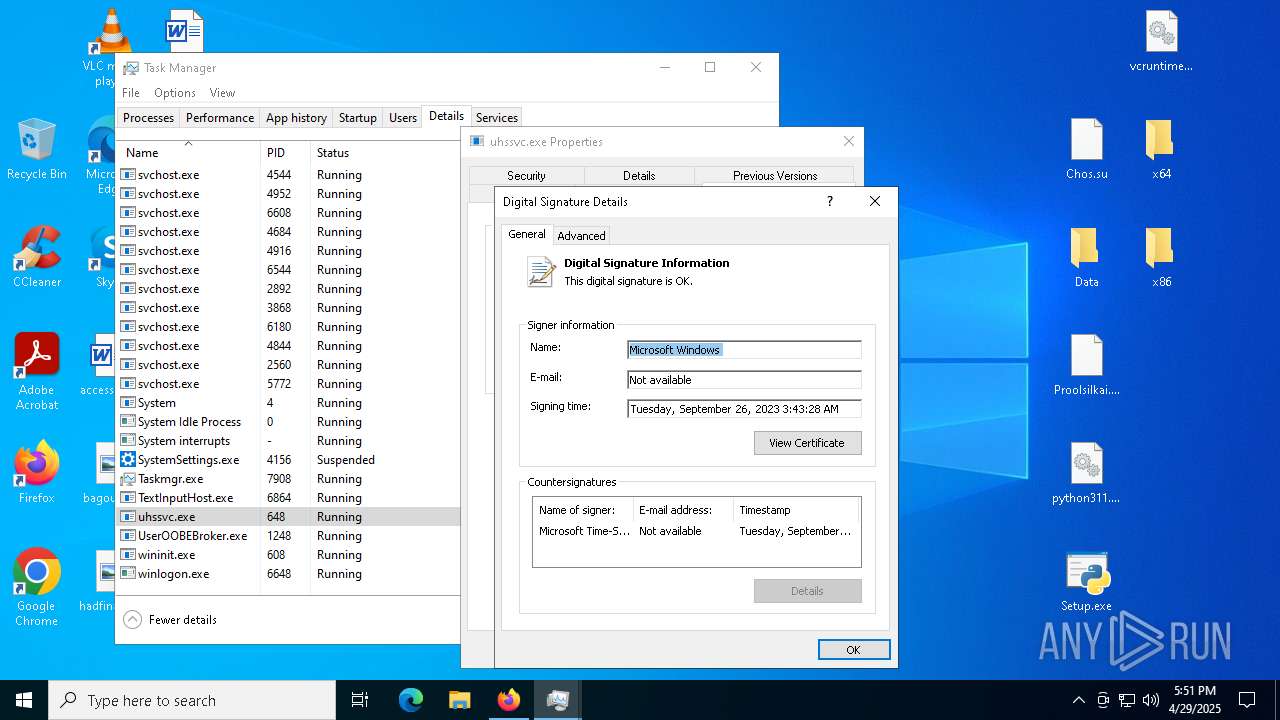
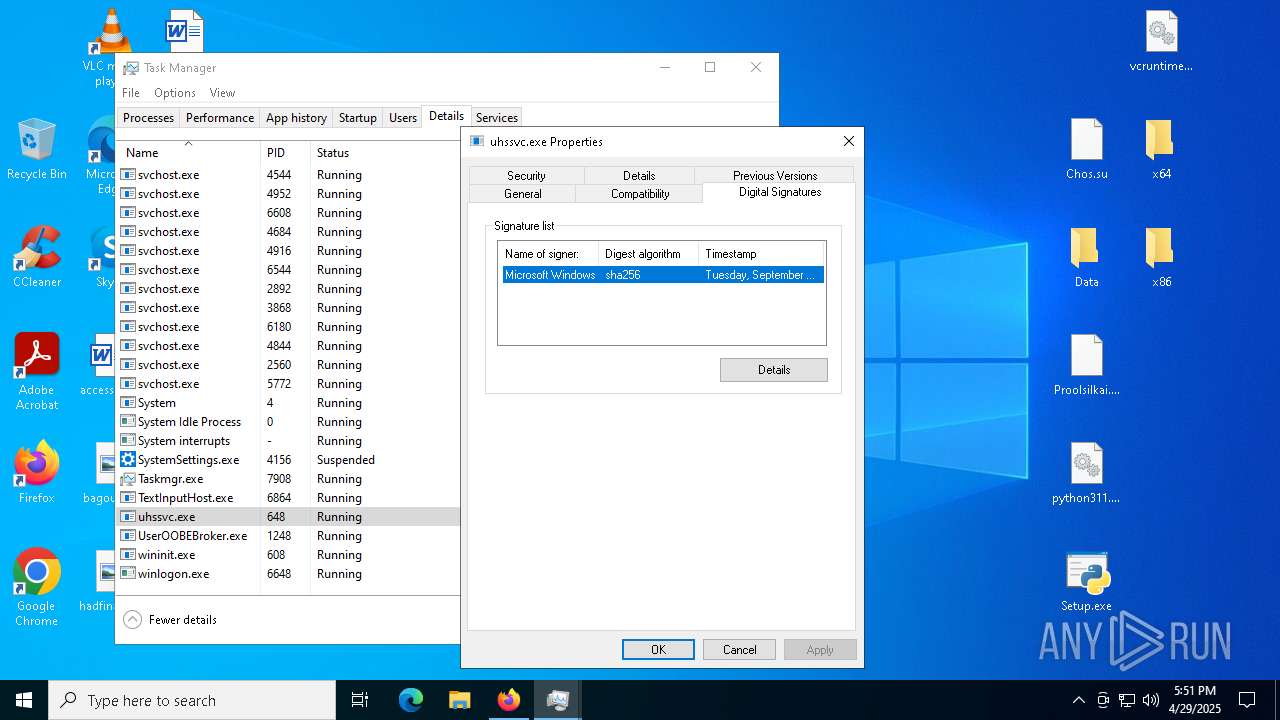
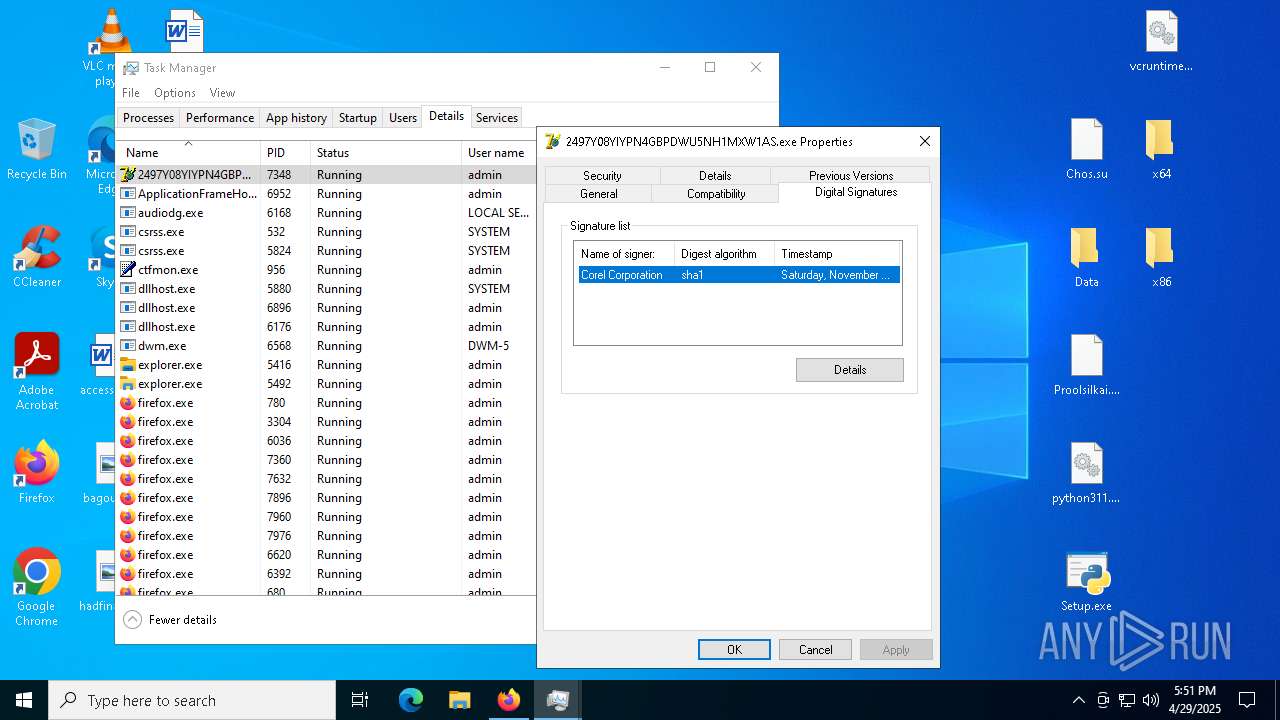
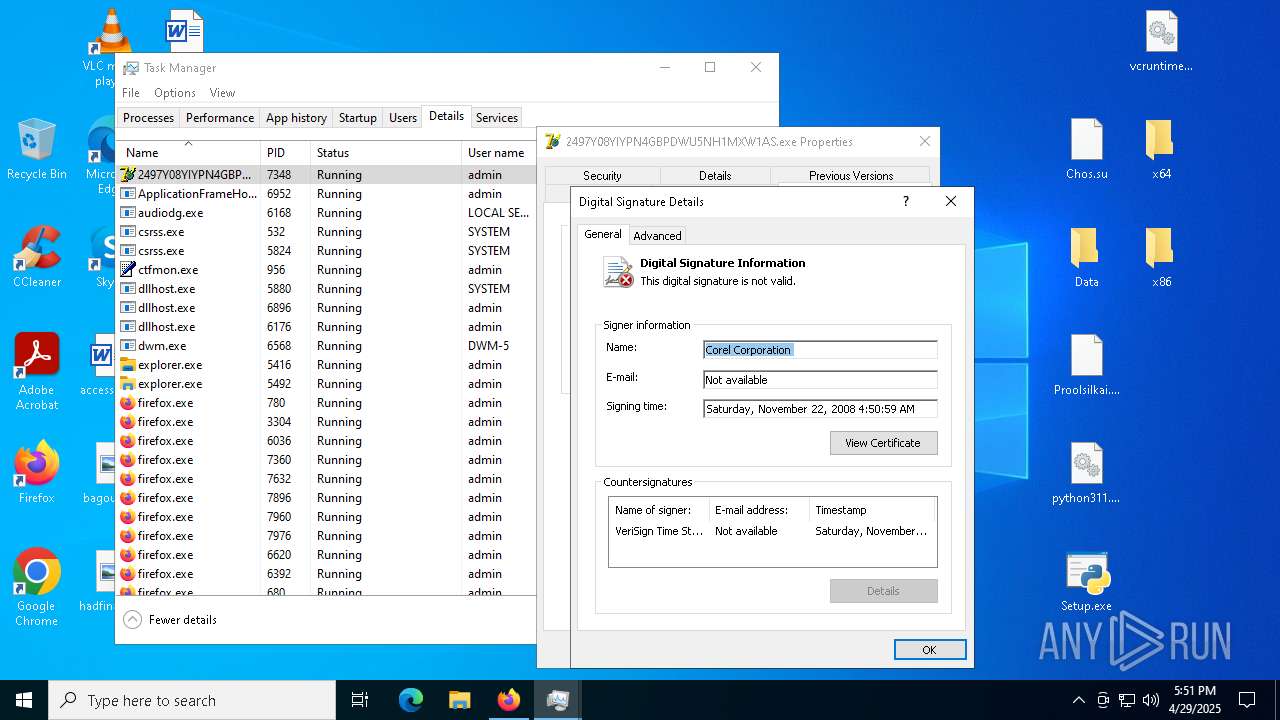
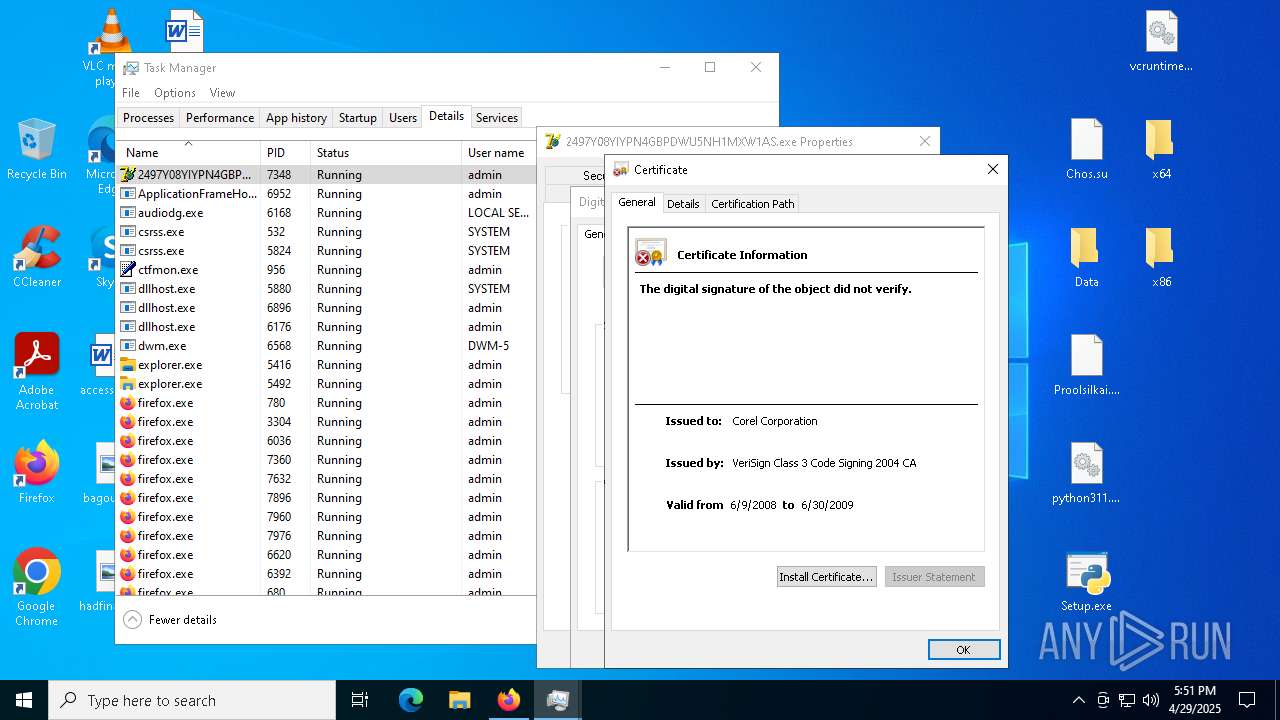
Executing a file with an untrusted certificate
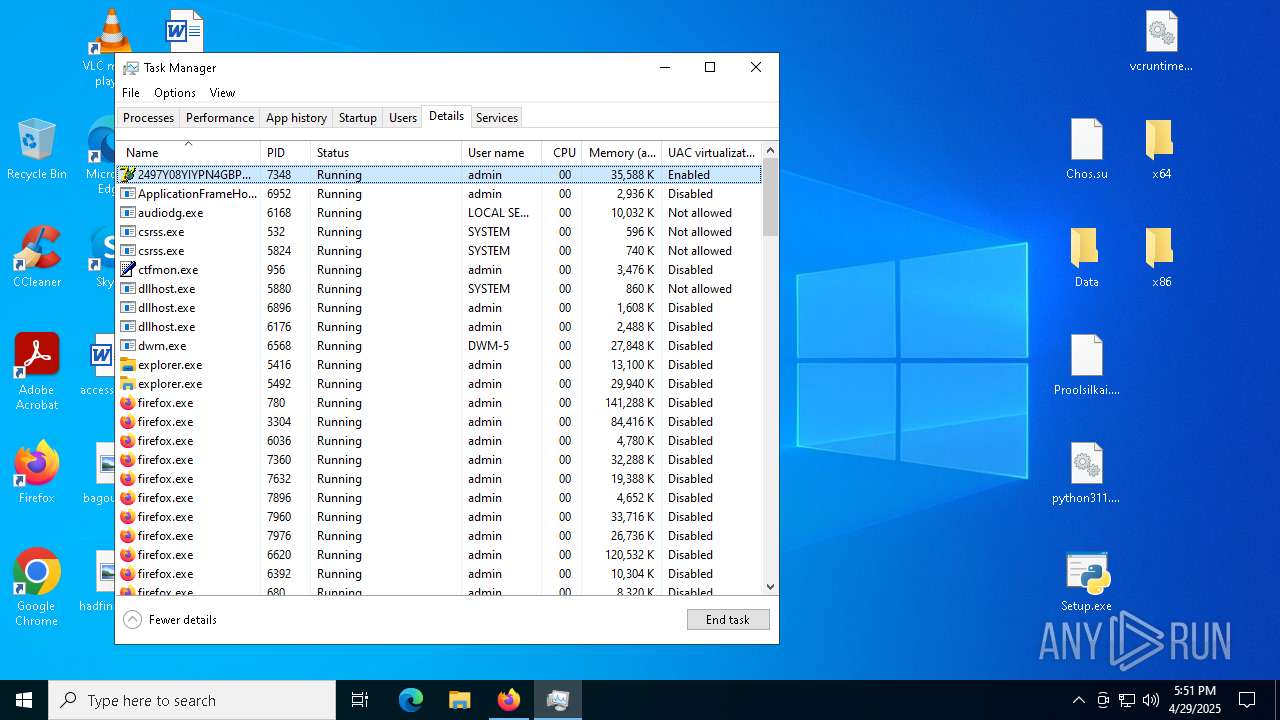
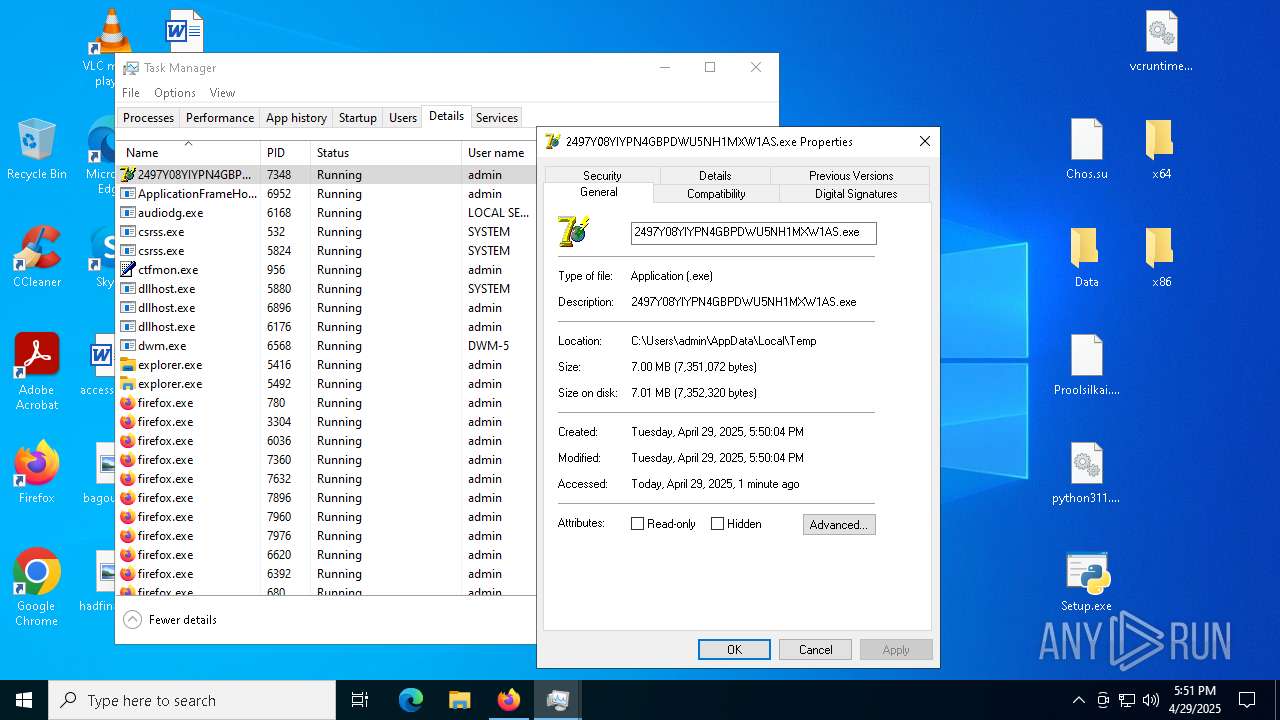
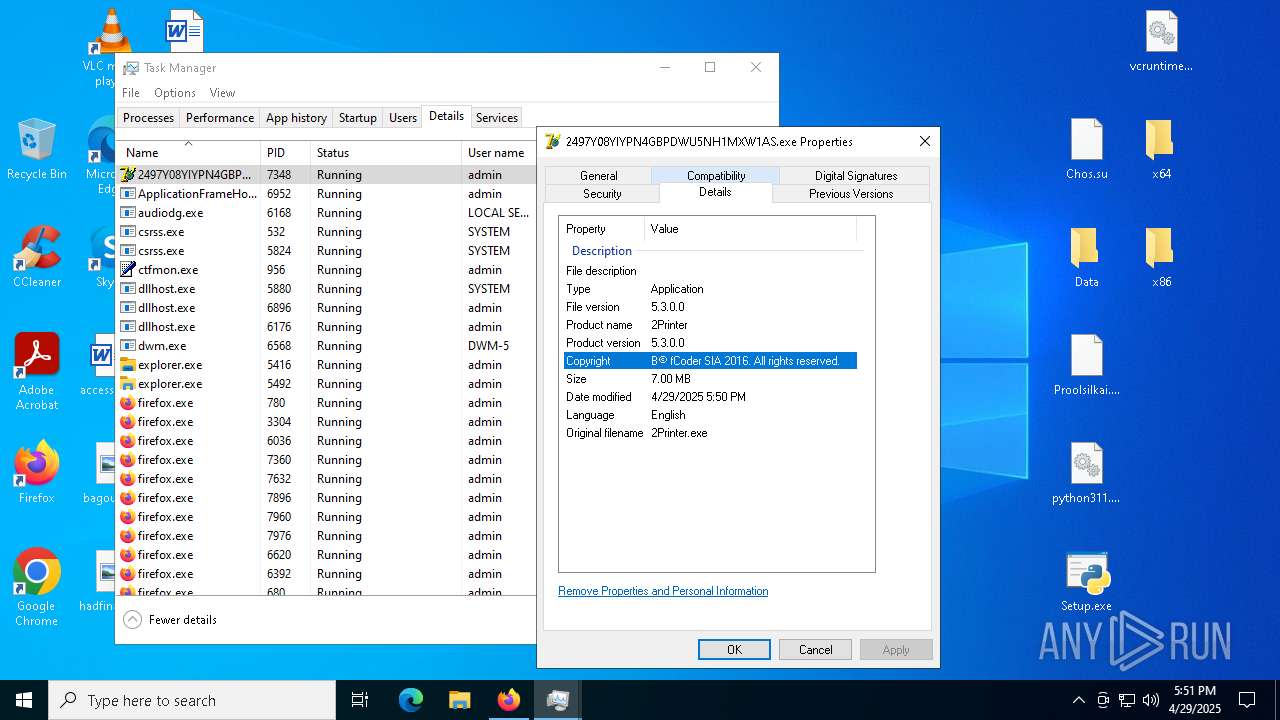
- 2497Y08YIYPN4GBPDWU5NH1MXW1AS.exe (PID: 7348)
AMADEY has been detected (YARA)
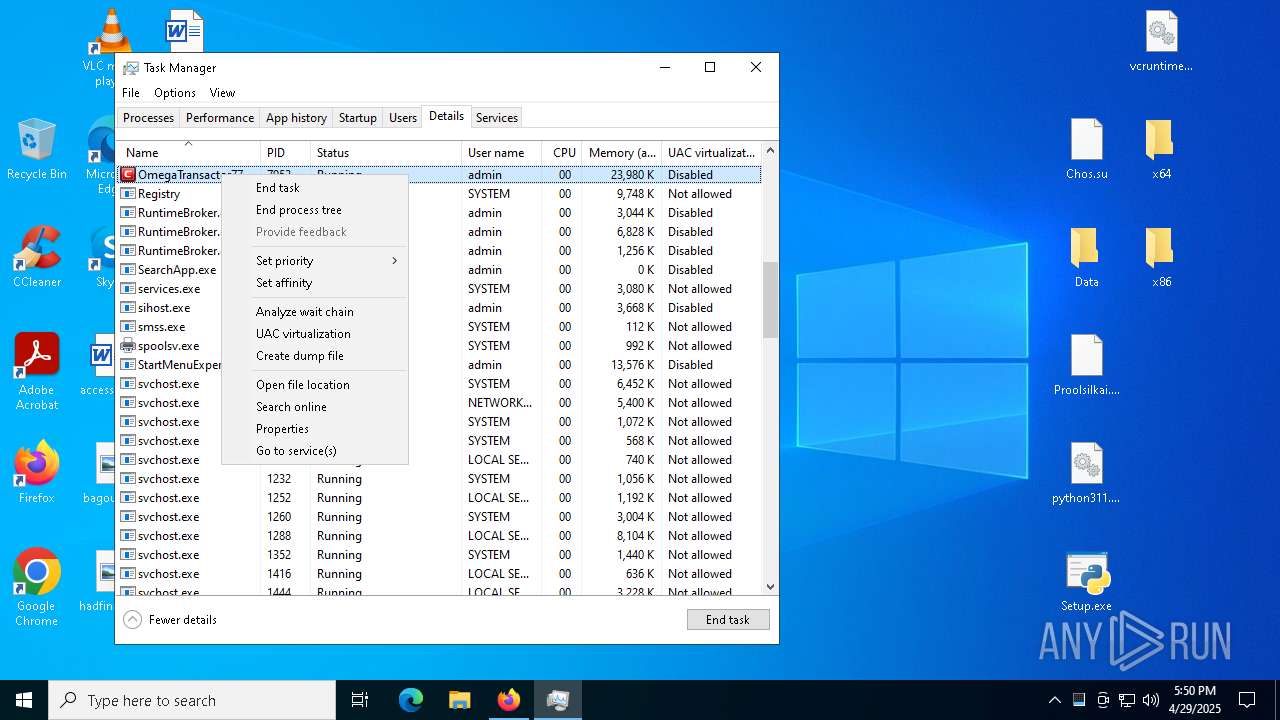
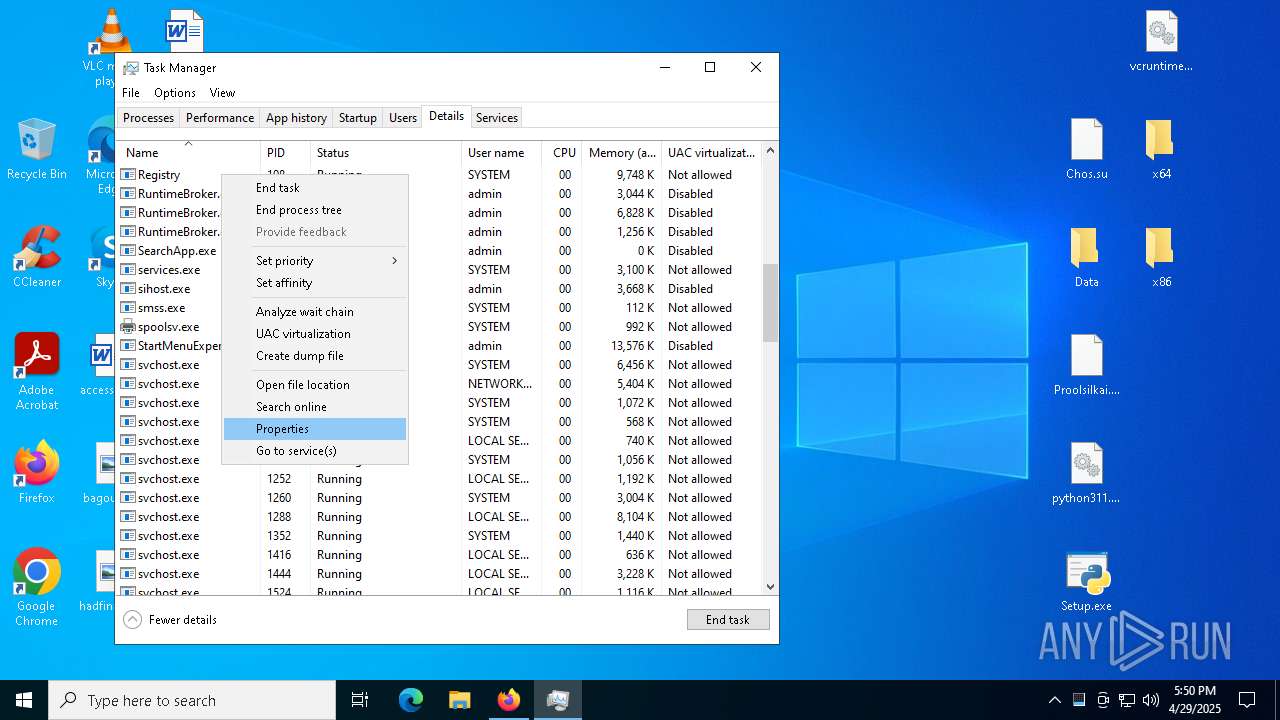
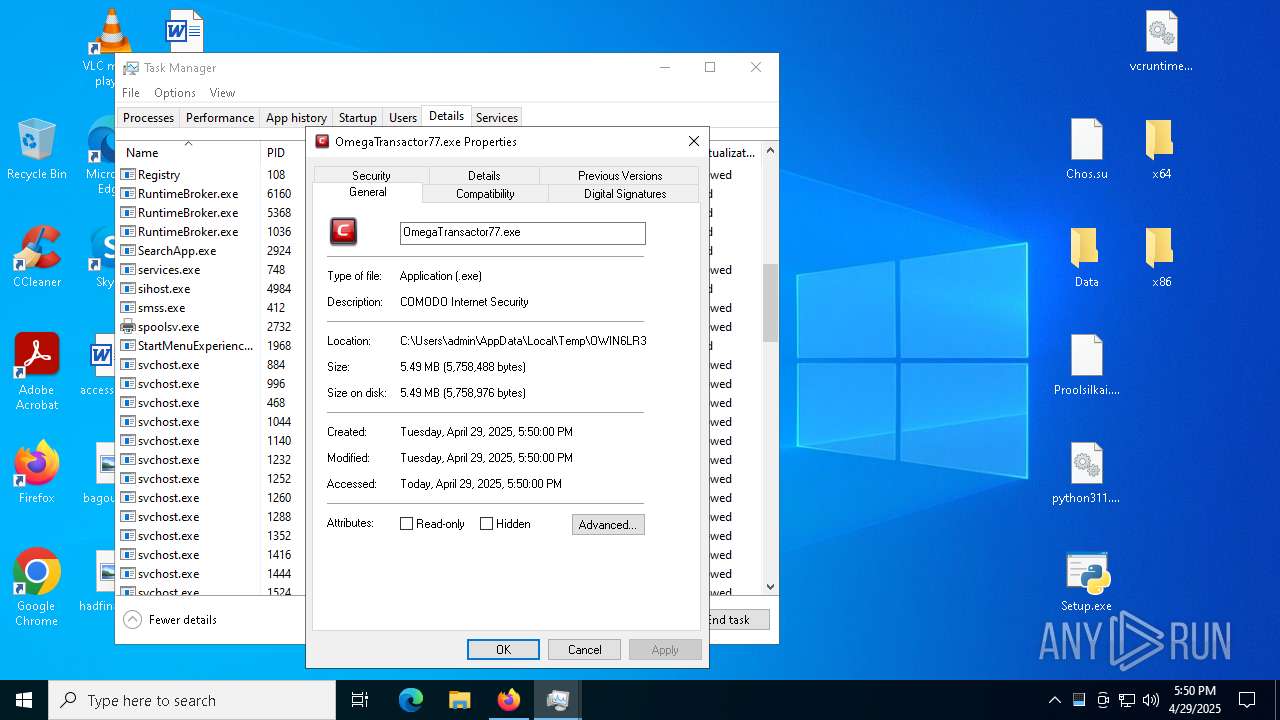
- OmegaTransactor77.exe (PID: 7952)
- explorer.exe (PID: 5416)
Connects to the CnC server
- explorer.exe (PID: 5416)
AMADEY has been detected (SURICATA)
- explorer.exe (PID: 5416)
SUSPICIOUS
The process drops C-runtime libraries
- Setup.exe (PID: 1240)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5024)
- WinRAR.exe (PID: 8008)
Process drops legitimate windows executable
- Setup.exe (PID: 1240)
- WinRAR.exe (PID: 4884)
- OmegaTransactor77.exe (PID: 7952)
Application launched itself
- WinRAR.exe (PID: 8008)
- WinRAR.exe (PID: 5024)
Executable content was dropped or overwritten
- Setup.exe (PID: 1240)
- Pergolesi.com (PID: 7296)
- OmegaTransactor77.exe (PID: 7952)
- 2497Y08YIYPN4GBPDWU5NH1MXW1AS.exe (PID: 7348)
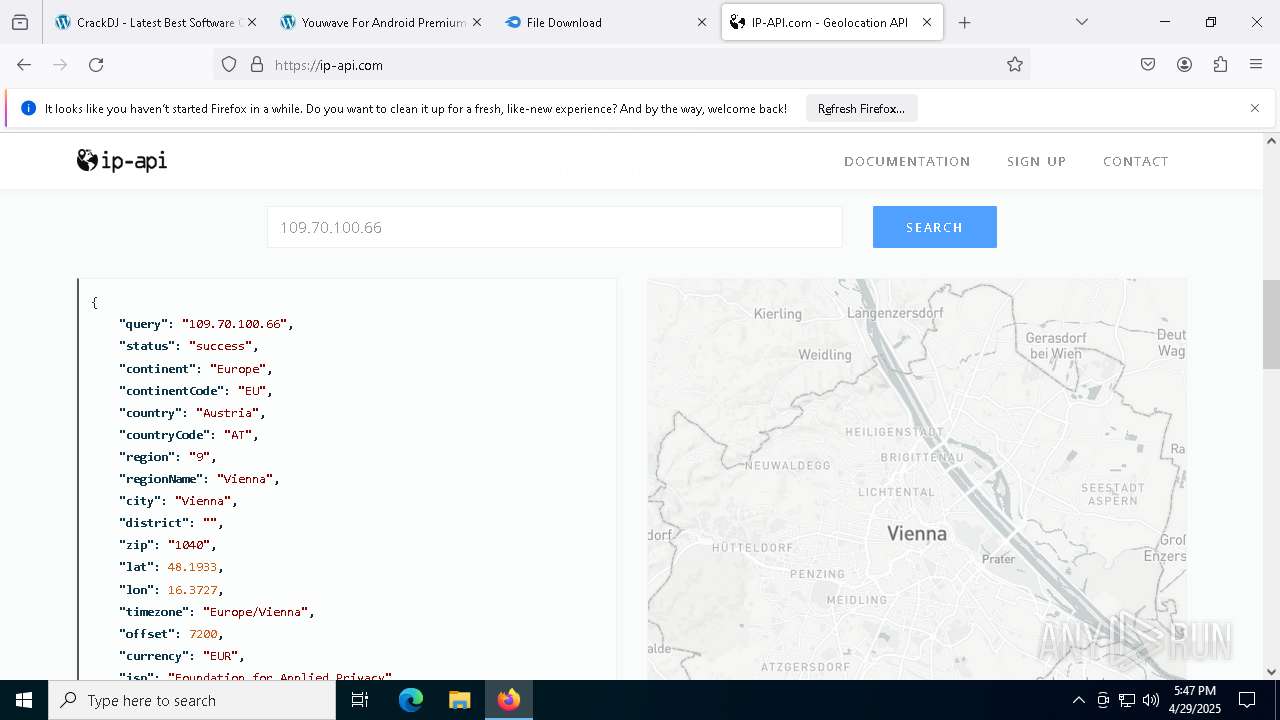
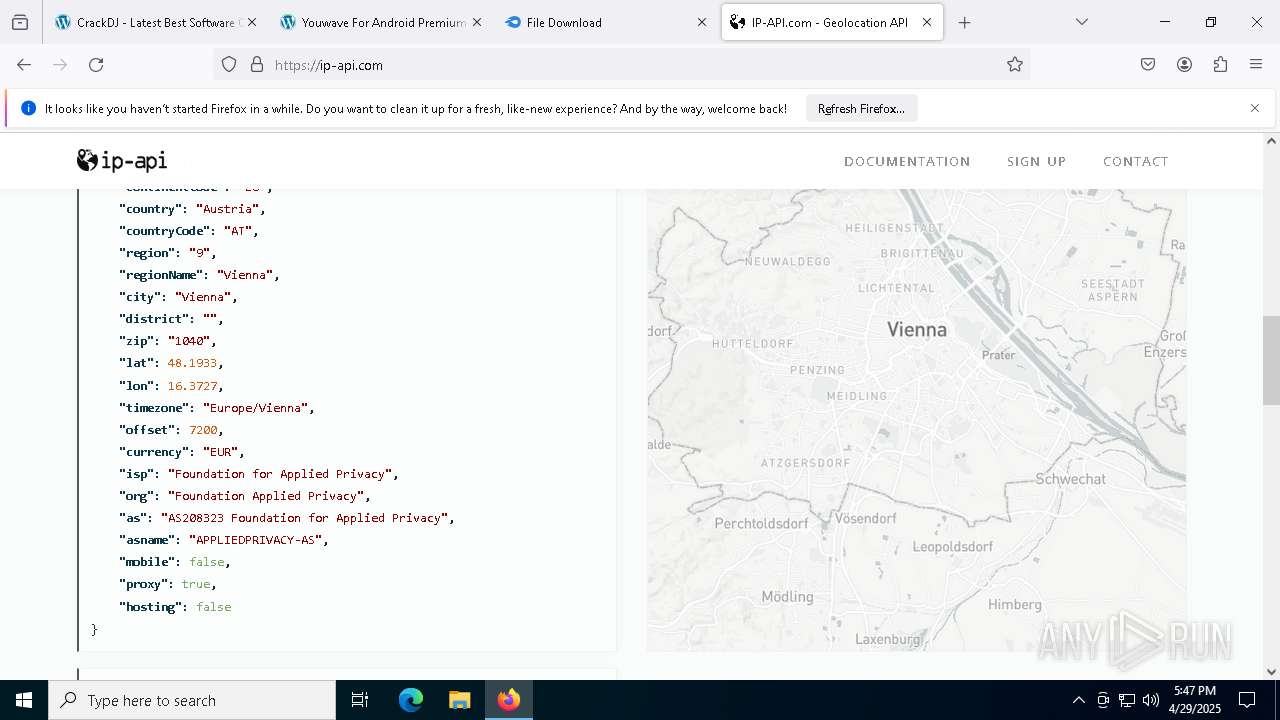
Checks for external IP
- svchost.exe (PID: 2196)
Starts application with an unusual extension
- Setup.exe (PID: 1240)
There is functionality for taking screenshot (YARA)
- Pergolesi.com (PID: 7296)
- explorer.exe (PID: 5416)
Contacting a server suspected of hosting an CnC
- explorer.exe (PID: 5416)
Starts a Microsoft application from unusual location
- explorer.exe (PID: 5416)
There is functionality for enable RDP (YARA)
- explorer.exe (PID: 5416)
Executes application which crashes
- 2497Y08YIYPN4GBPDWU5NH1MXW1AS.exe (PID: 7348)
Starts CMD.EXE for commands execution
- 2497Y08YIYPN4GBPDWU5NH1MXW1AS.exe (PID: 7348)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5132)
Connects to unusual port
- 2497Y08YIYPN4GBPDWU5NH1MXW1AS.exe (PID: 7348)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 5024)
Reads the software policy settings
- slui.exe (PID: 1272)
Manual execution by a user
- Setup.exe (PID: 1240)
- WinRAR.exe (PID: 5024)
- Taskmgr.exe (PID: 7616)
- Taskmgr.exe (PID: 7908)
- notepad++.exe (PID: 5072)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4884)
Application launched itself
- firefox.exe (PID: 780)
- firefox.exe (PID: 7000)
The sample compiled with english language support
- WinRAR.exe (PID: 4884)
- Setup.exe (PID: 1240)
- Pergolesi.com (PID: 7296)
- OmegaTransactor77.exe (PID: 7952)
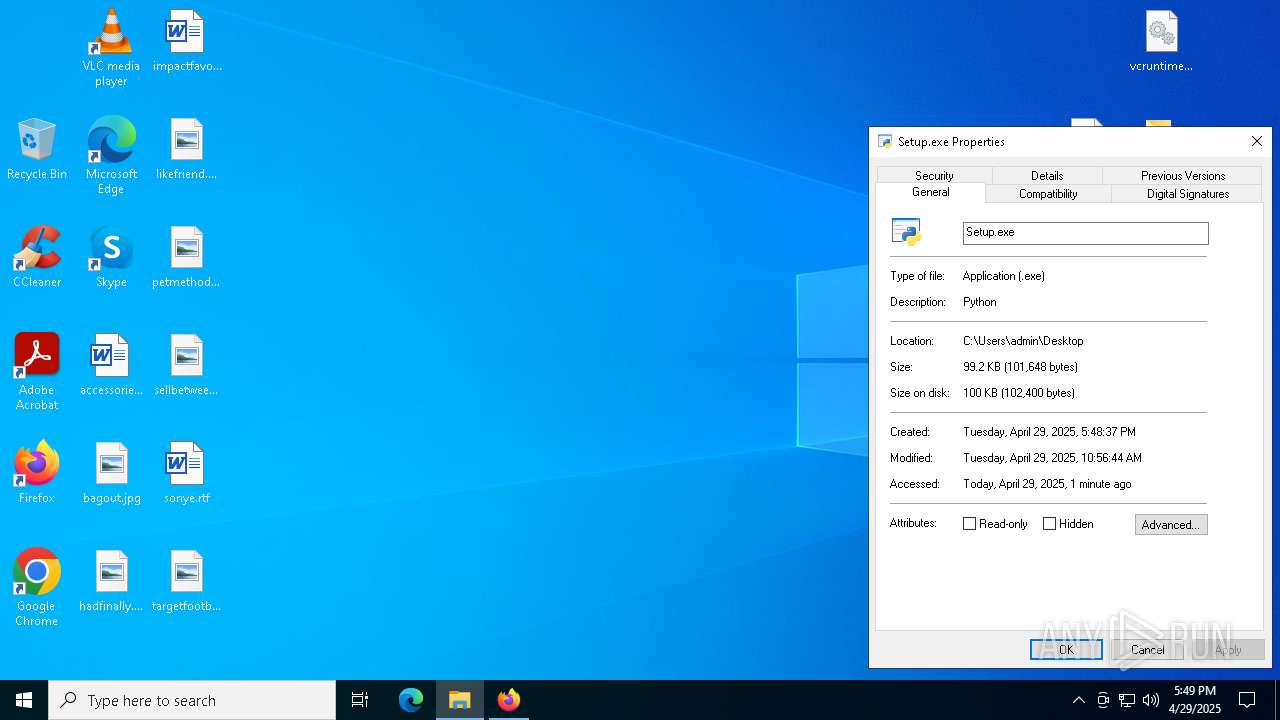
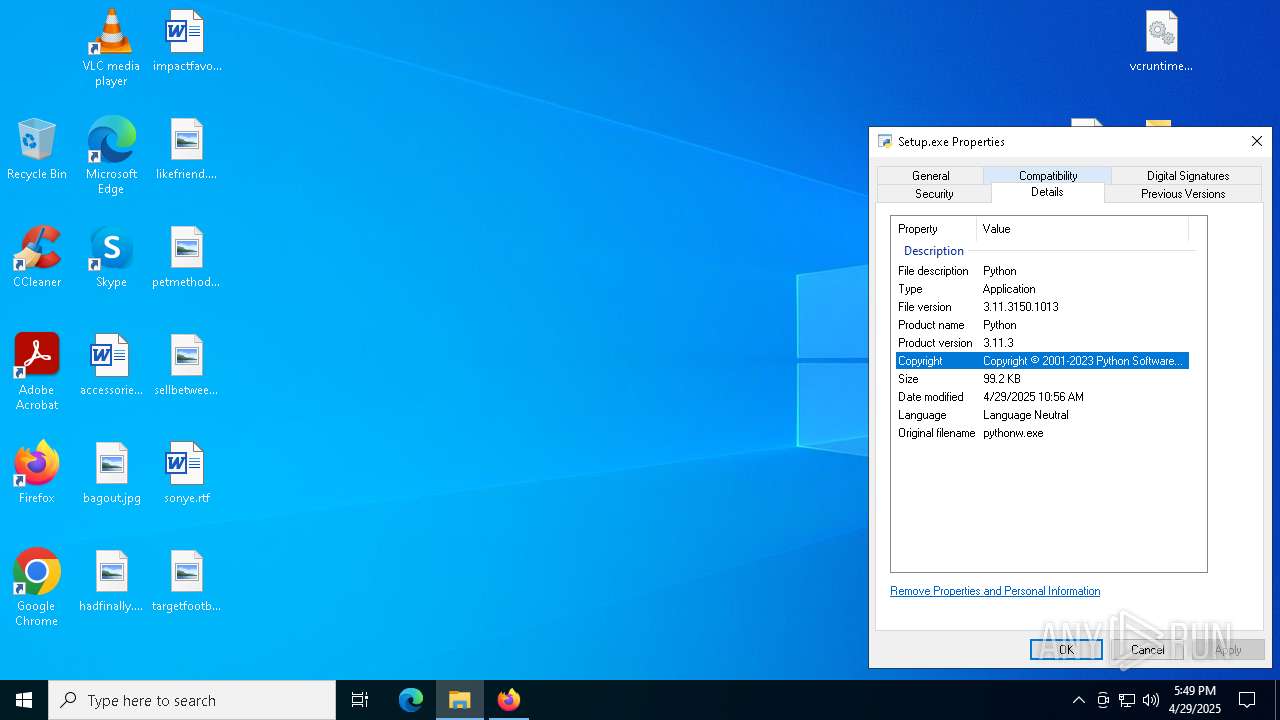
Python executable
- Setup.exe (PID: 1240)
Compiled with Borland Delphi (YARA)
- 2497Y08YIYPN4GBPDWU5NH1MXW1AS.exe (PID: 7348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
196
Monitored processes
50
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7348 -s 636 | C:\Windows\SysWOW64\WerFault.exe | — | 2497Y08YIYPN4GBPDWU5NH1MXW1AS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6660 -childID 11 -isForBrowser -prefsHandle 6108 -prefMapHandle 5532 -prefsLen 31575 -prefMapSize 244583 -jsInitHandle 1372 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {9d5e68d1-0394-4320-a8a2-9b3c4caba832} 780 "\\.\pipe\gecko-crash-server-pipe.780" 1f8c221bf50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 728 | "C:\ProgramData\Microsoft SQL Server\tcpvcon.exe" "C:\ProgramData\Microsoft SQL Server\tcpvcon.exe" /accepteula | C:\ProgramData\Microsoft SQL Server\tcpvcon.exe | — | OmegaTransactor77.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Sysinternals TcpVcon Exit code: 0 Version: 4.18 Modules
| |||||||||||||||
| 780 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://crackdj.com | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 856 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.11.3 Modules
| |||||||||||||||
| 1272 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5572 -childID 9 -isForBrowser -prefsHandle 4240 -prefMapHandle 6256 -prefsLen 31332 -prefMapSize 244583 -jsInitHandle 1372 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {a38b97af-b705-4103-b69a-348112f1f7df} 780 "\\.\pipe\gecko-crash-server-pipe.780" 1f8c221b4d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
44 676
Read events
44 565
Write events
100
Delete events
11
Modification events
| (PID) Process: | (780) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (5024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
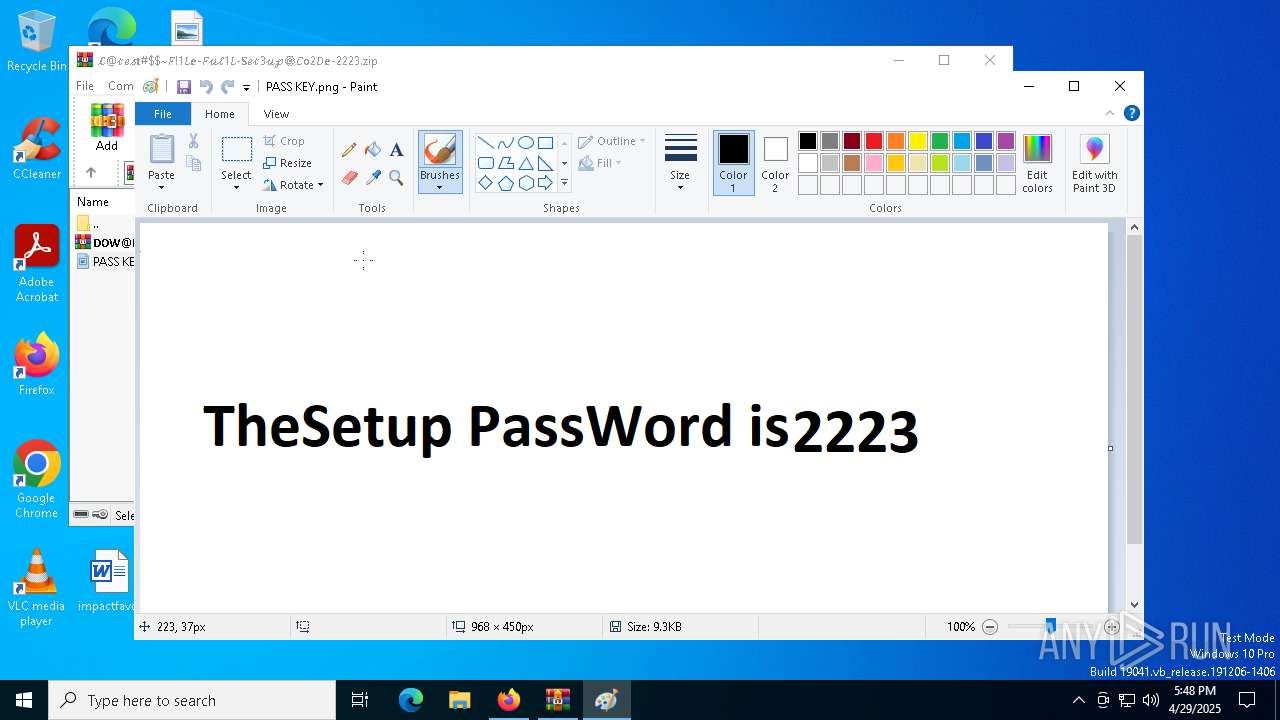
Value: C:\Users\admin\Downloads\𝓛@𝓉𝑒𝓈𝐭#$~𝐹!1𝐿𝐞-𝐹𝓊𝓁1𝐿-𝐒𝑒𝓉3𝓊𝓅⚙️𝐶𝐨2𝐷𝐞-2223.zip | |||
| (PID) Process: | (5024) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.png\OpenWithProgids |
| Operation: | write | Name: | pngfile |
Value: | |||
Executable files
13
Suspicious files
241
Text files
99
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 780 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:4D6BEE777EF94ED622897C0C6B9EC0AF | SHA256:AA07E227121171B851F7202696A0C00ACB3390A7B8FC222EC81D44FAAD5B9F2C | |||
| 780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 780 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:B3105A9EA81139206335141C6C10A676 | SHA256:069D32491D35273027B2AE836C93C0B304FB56BFDE66CA9967C616410AB488C3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
68
TCP/UDP connections
184
DNS requests
201
Threats
65
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.21.245.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.21.245.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.21.245.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
780 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
780 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
780 | firefox.exe | POST | 200 | 2.22.231.8:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
780 | firefox.exe | POST | 200 | 2.22.231.8:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.21.245.180:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.21.245.180:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.21.245.180:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 23.222.86.92:80 | www.microsoft.com | AKAMAI-AS | NZ | whitelisted |
— | — | 23.222.86.92:80 | www.microsoft.com | AKAMAI-AS | NZ | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.222.86.92:80 | www.microsoft.com | AKAMAI-AS | NZ | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
crackdj.com |
| unknown |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
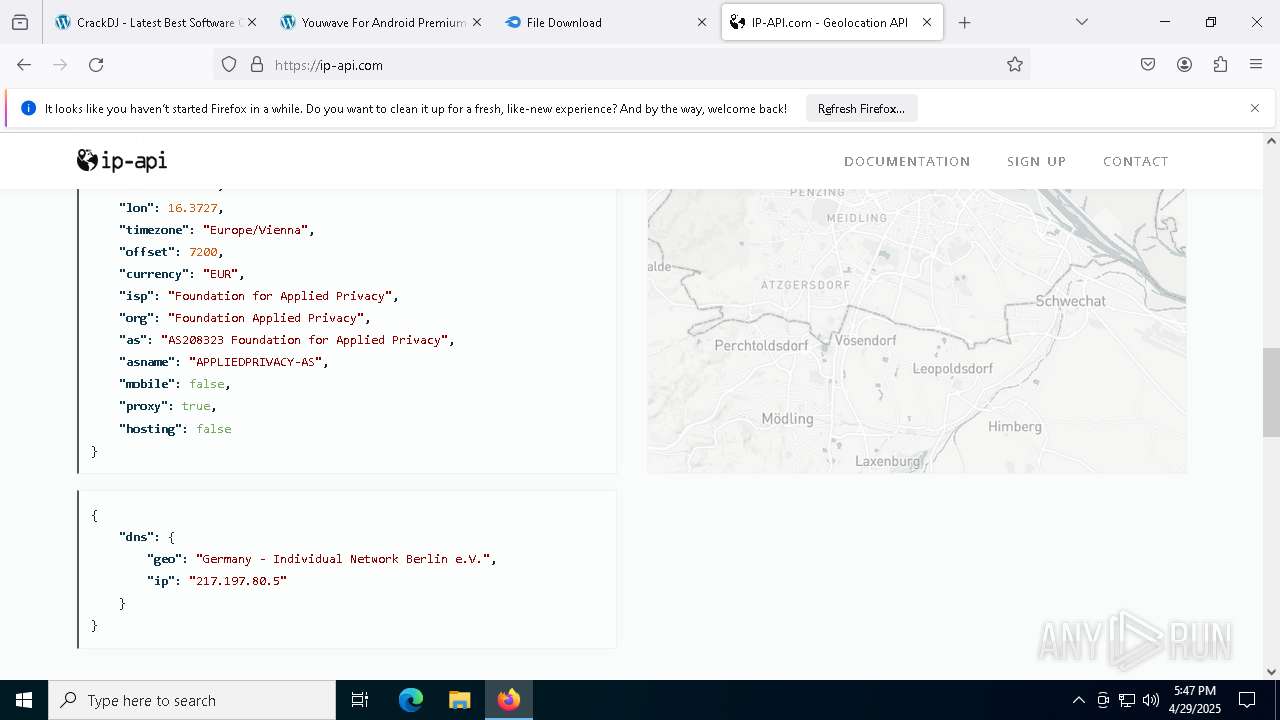
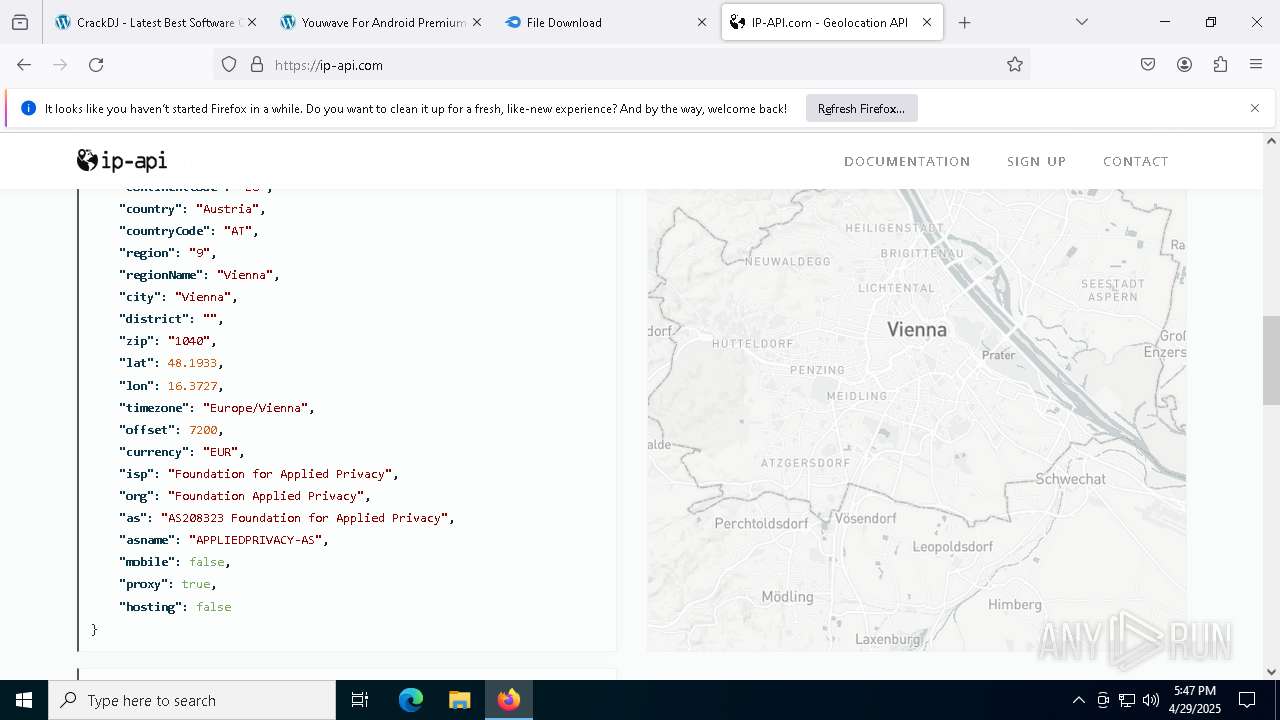
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |