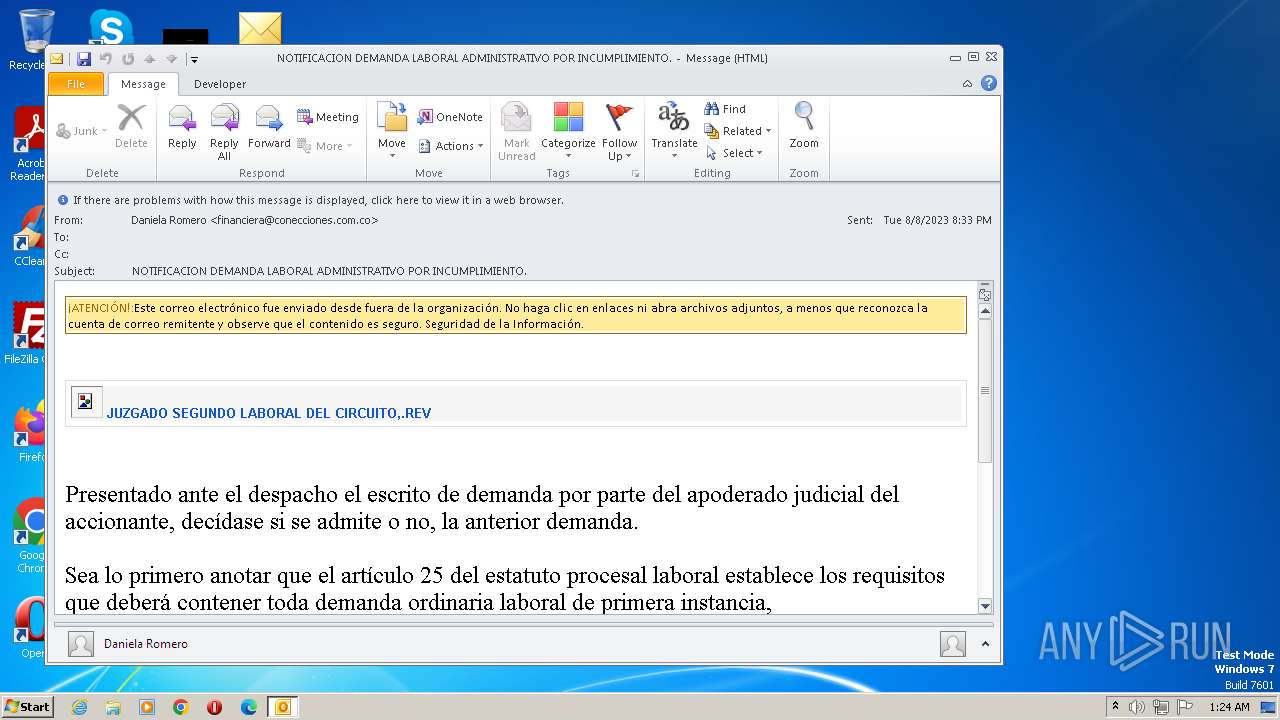
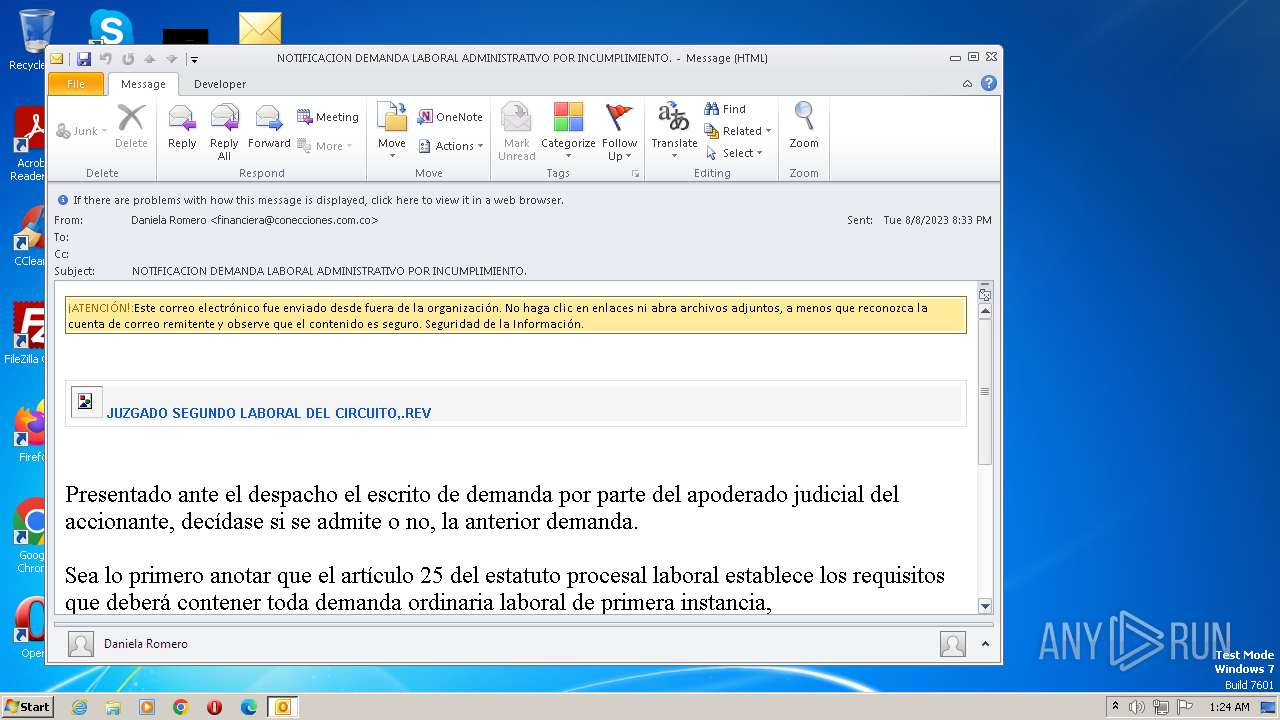
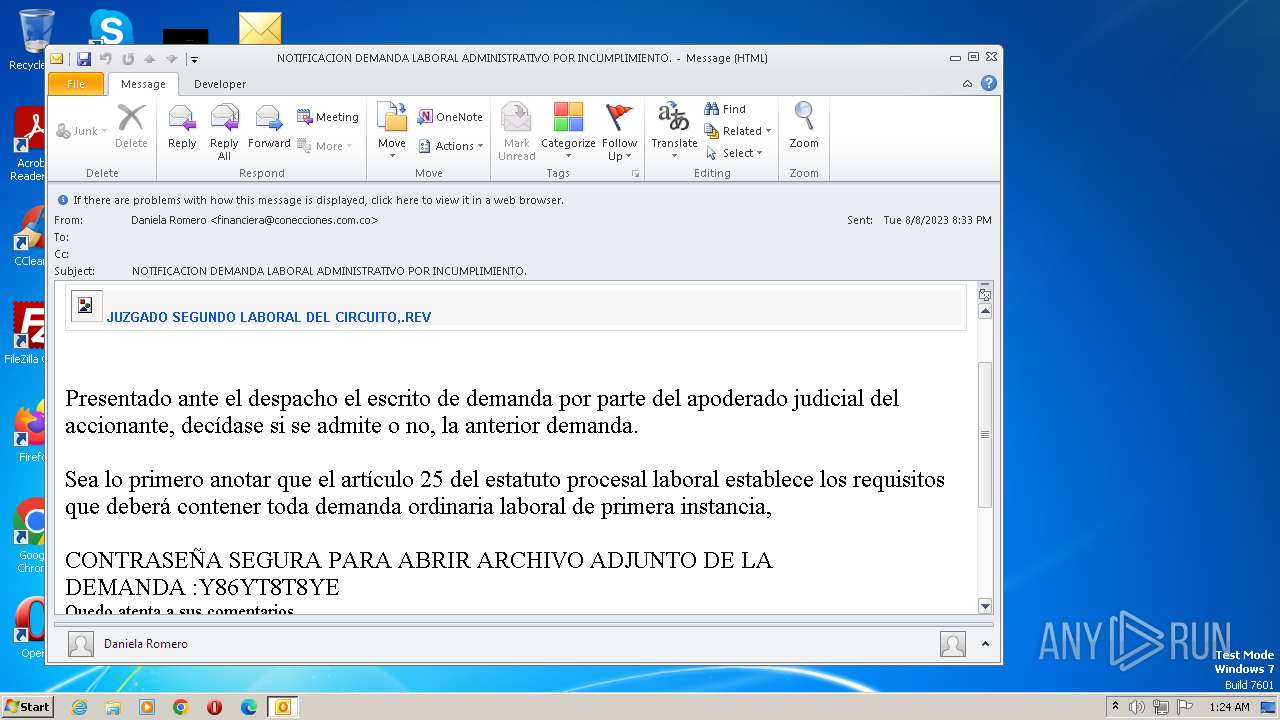
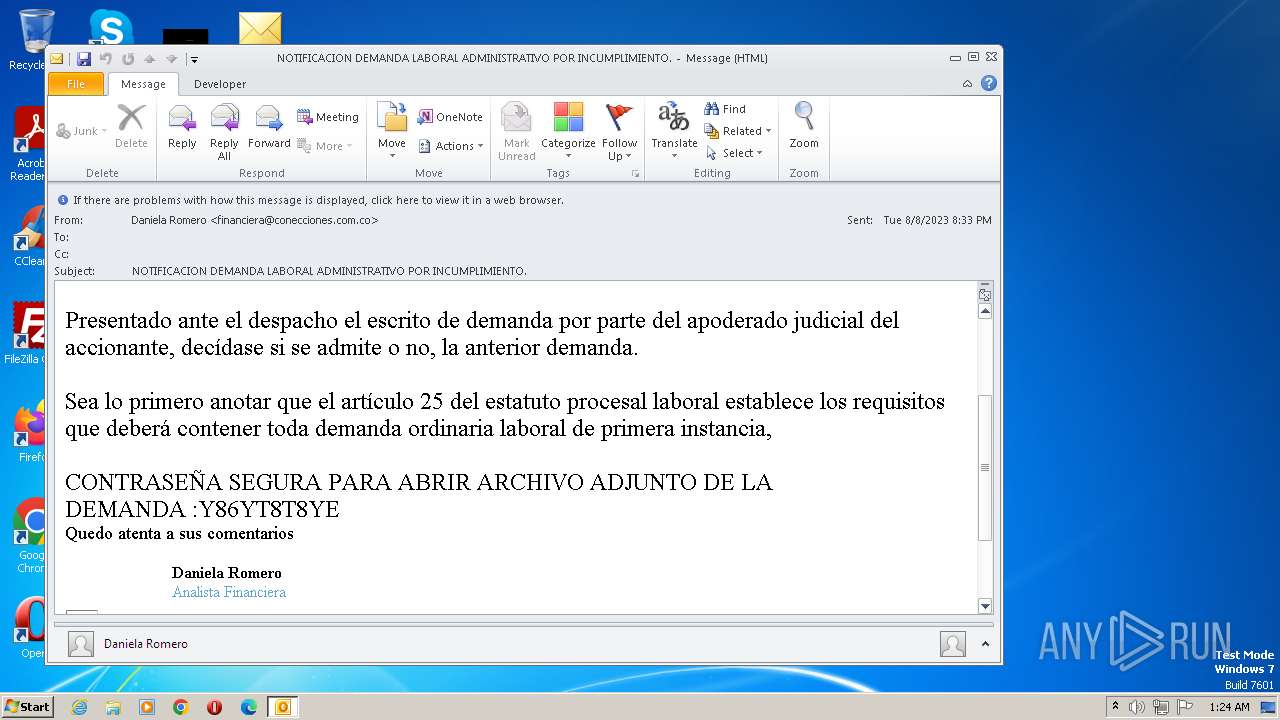
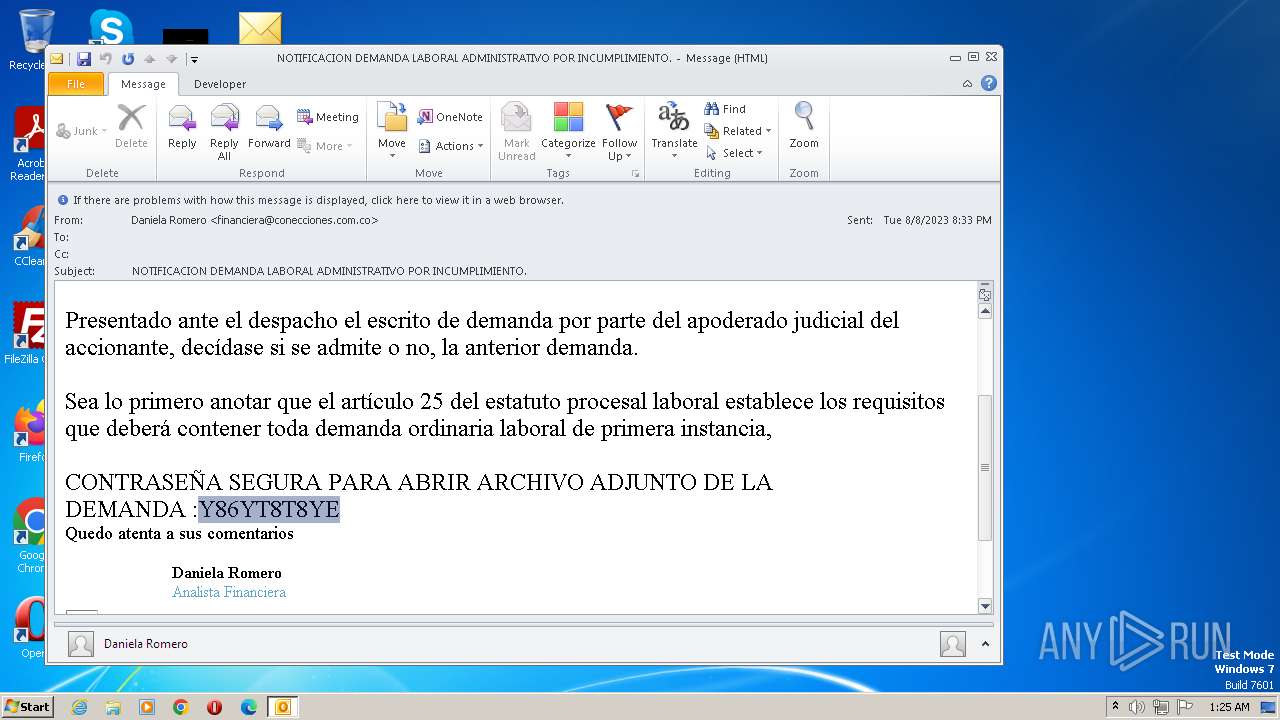
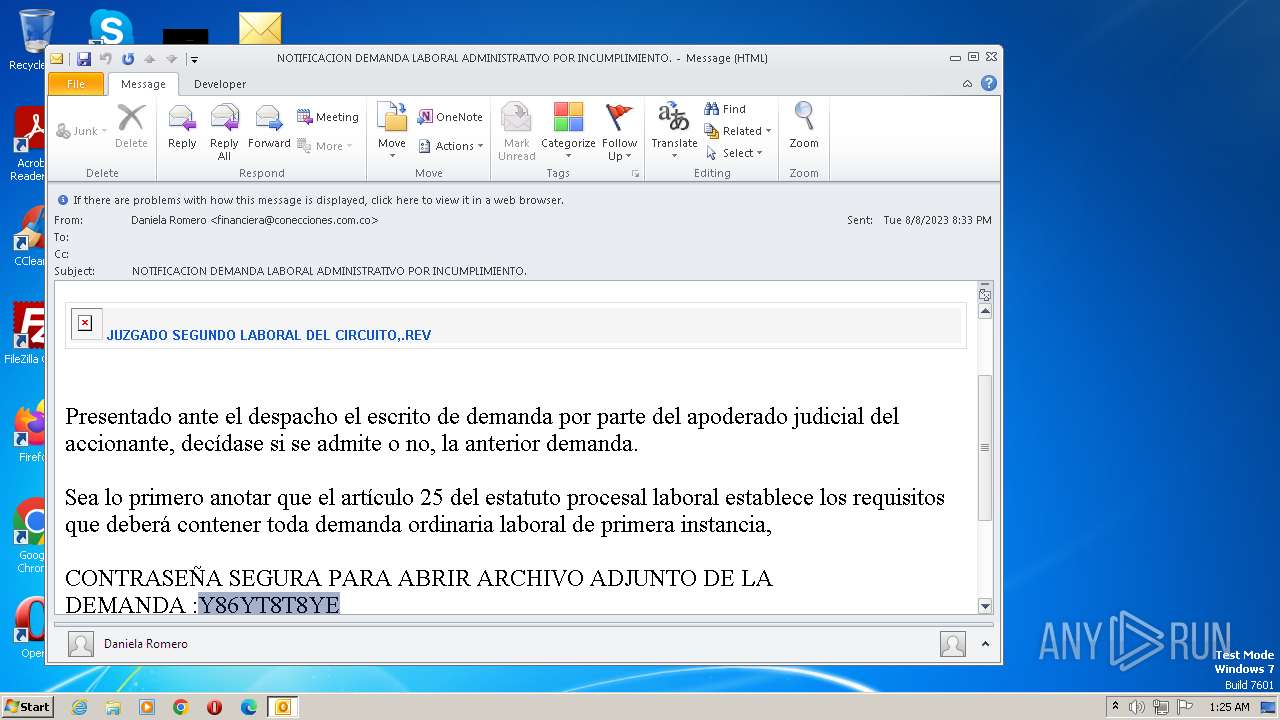
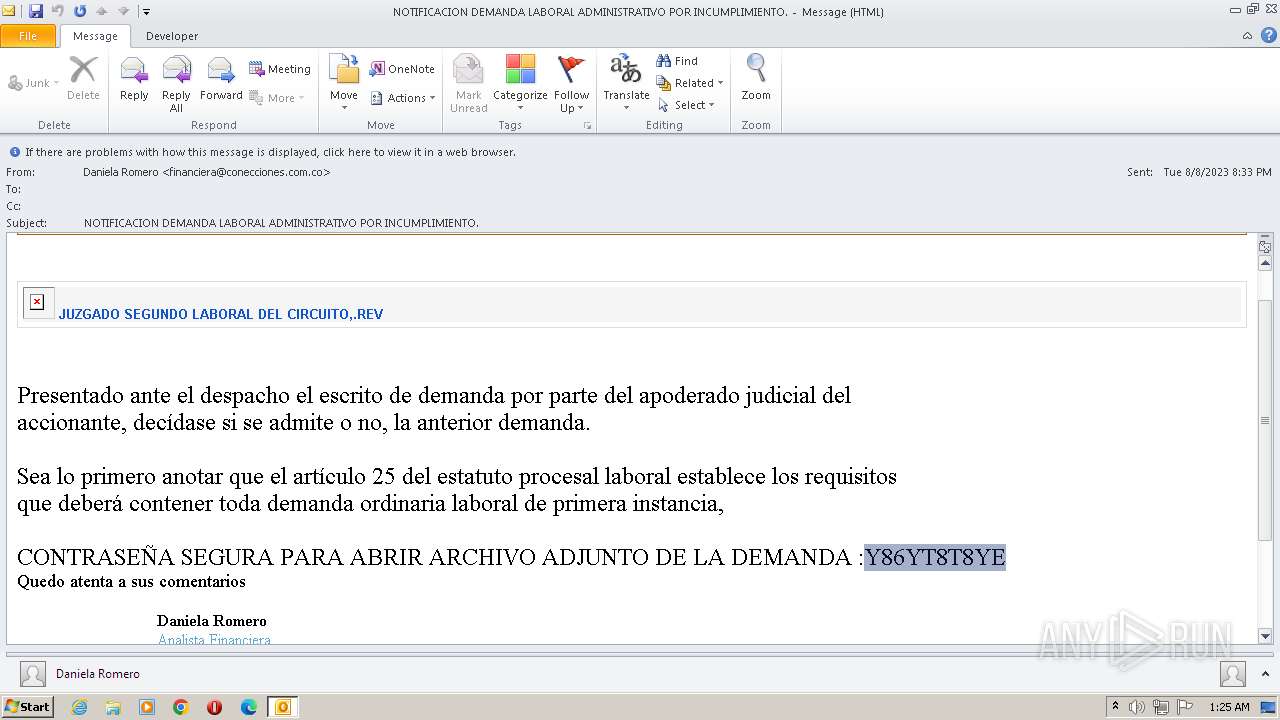
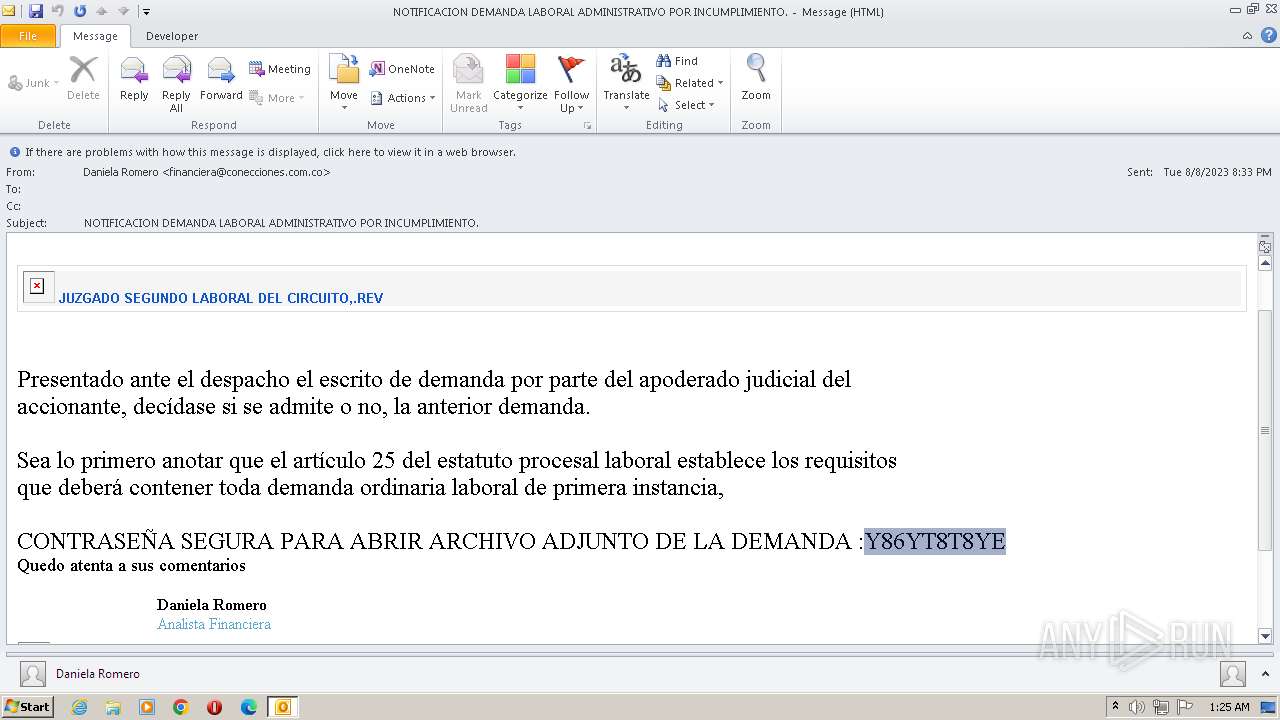
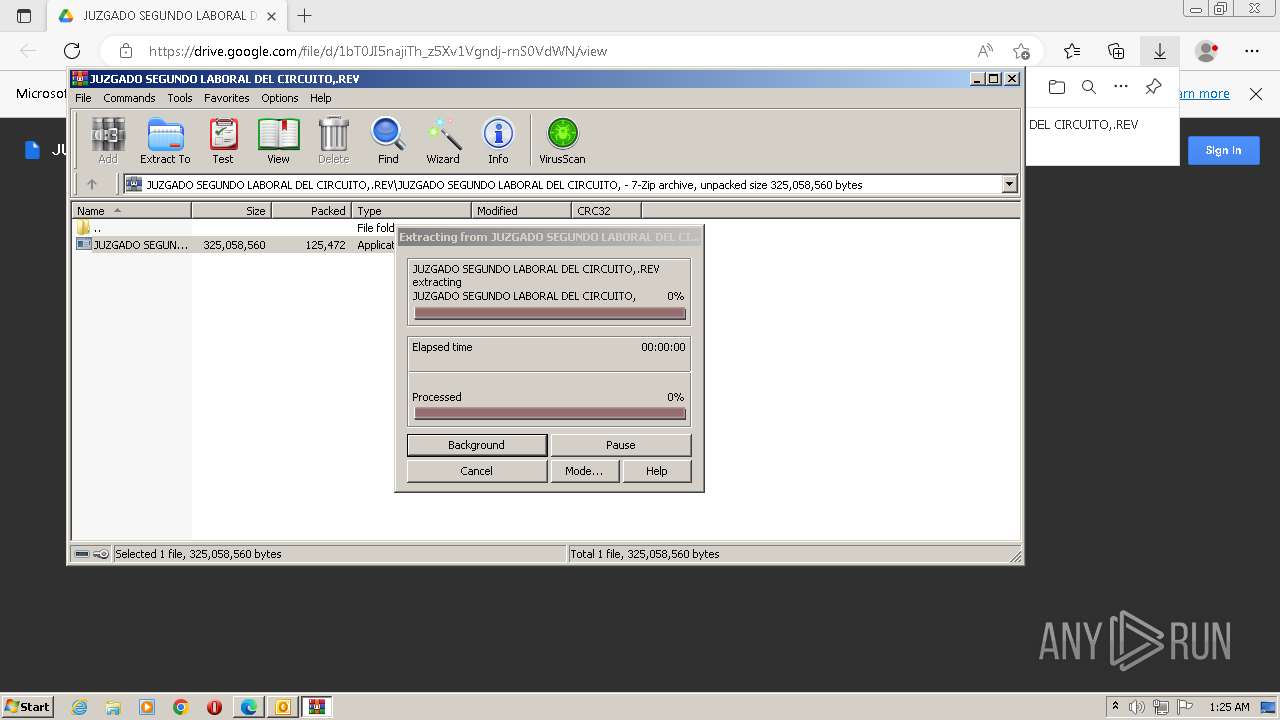
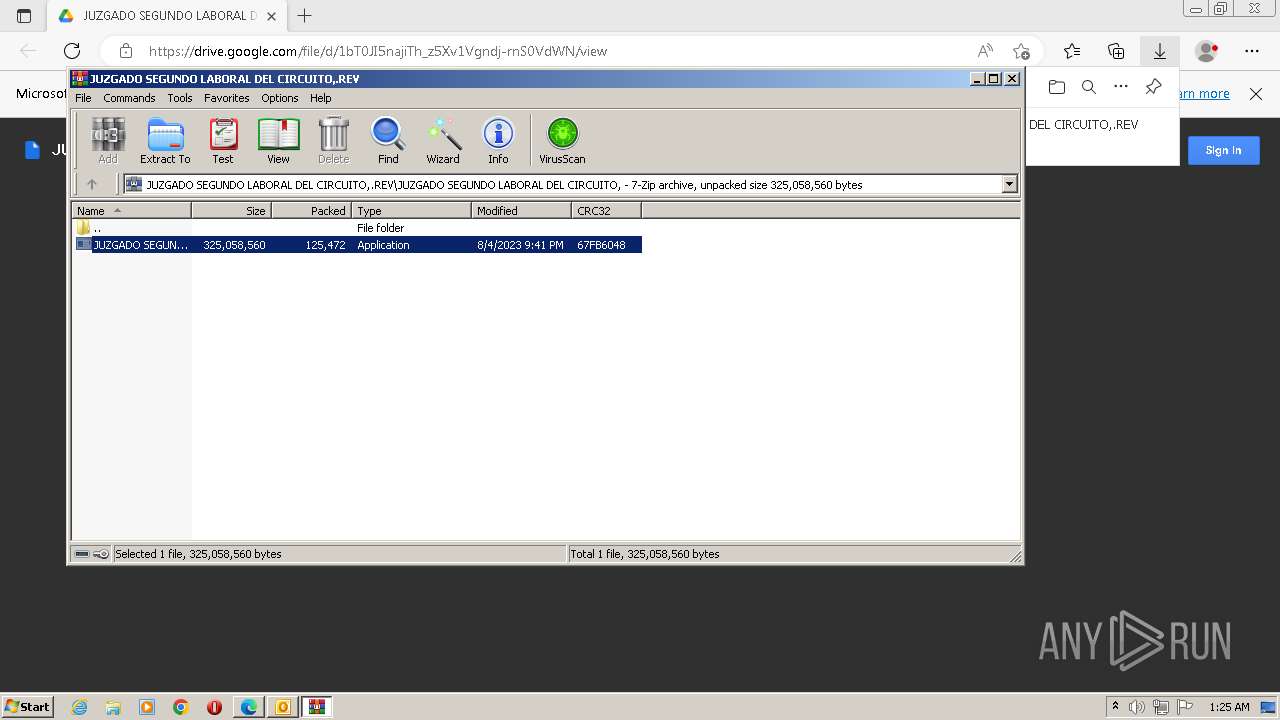
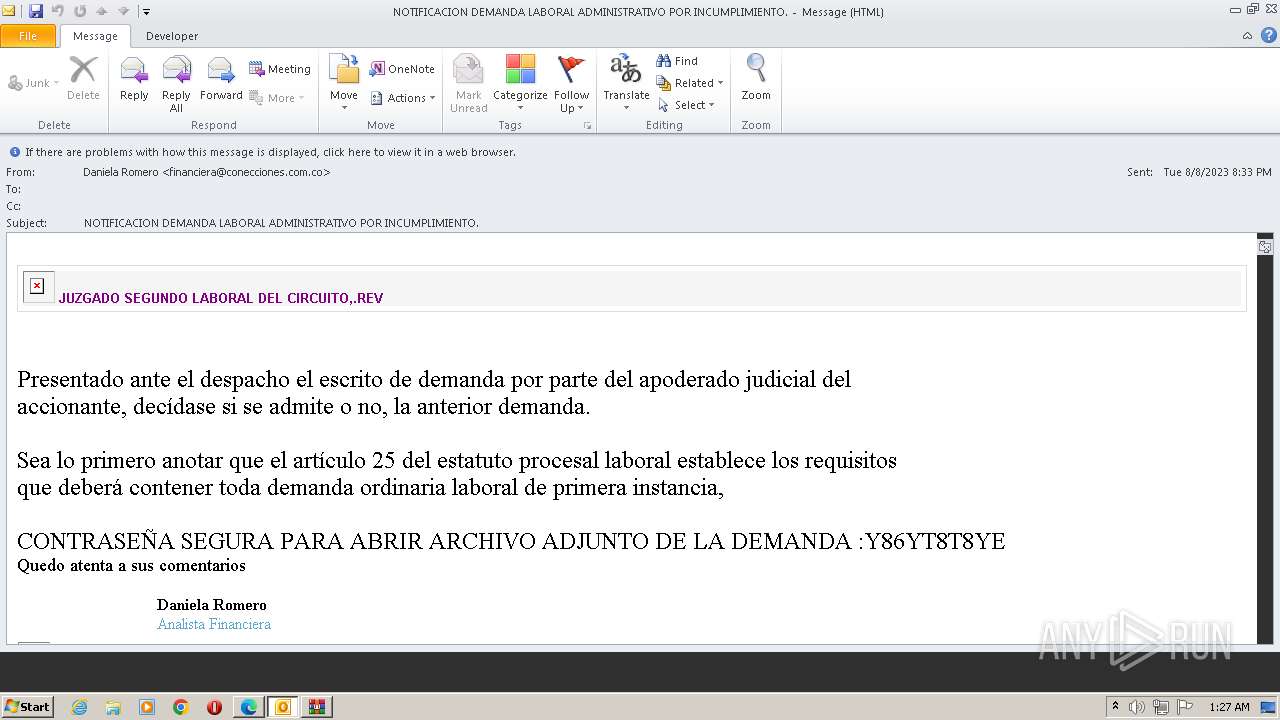
| File name: | NOTIFICACION DEMANDA LABORAL ADMINISTRATIVO POR INCUMPLIMIENTO..msg |
| Full analysis: | https://app.any.run/tasks/d6f9ed7c-2f3e-4ccc-ba3d-bc46cb0b41cb |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | August 10, 2023, 00:24:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 8EBD31C2F89307564D34FF714B3112DF |
| SHA1: | F01A7AF2F288D27677B5BBDD8E6A4038E4659328 |
| SHA256: | 12F5844230FA33CDB28BBCD29207E620F20806DFB3968E7DCB00BA01033EC55F |
| SSDEEP: | 1536:E167W/Wmjfx9vrbI///izRWpWujbLIXFI+FIfDeb4Tri0LUUfmDf:E16qjfbXK///roFI+FIFTri0LBfyf |
MALICIOUS
Actions looks like stealing of personal data
- SearchIndexer.exe (PID: 3496)
Unusual connection from system programs
- vbc.exe (PID: 1908)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 4056)
- cmd.exe (PID: 1000)
- cmd.exe (PID: 3860)
ASYNCRAT detected by memory dumps
- vbc.exe (PID: 1908)
SUSPICIOUS
Reads the Internet Settings
- SearchProtocolHost.exe (PID: 3224)
The process executes VB scripts
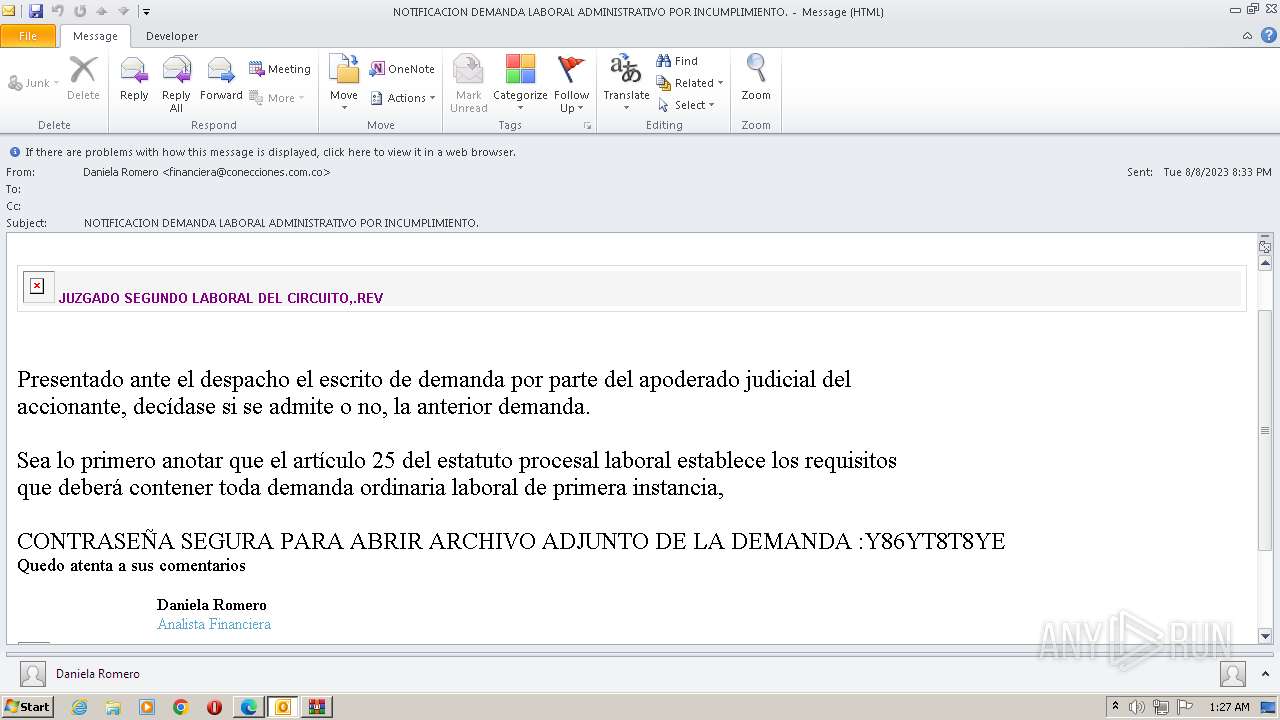
- JUZGADO SEGUNDO LABORAL DEL CIRCUITO,.exe (PID: 3316)
- chopst.exe (PID: 1824)
- chopst.exe (PID: 4092)
Starts CMD.EXE for commands execution
- JUZGADO SEGUNDO LABORAL DEL CIRCUITO,.exe (PID: 3316)
- chopst.exe (PID: 1824)
- chopst.exe (PID: 4092)
The process executes via Task Scheduler
- chopst.exe (PID: 1824)
- chopst.exe (PID: 4092)
Connects to unusual port
- vbc.exe (PID: 1908)
Accesses Microsoft Outlook profiles
- SearchProtocolHost.exe (PID: 3224)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 980)
- JUZGADO SEGUNDO LABORAL DEL CIRCUITO,.exe (PID: 3316)
- vbc.exe (PID: 1908)
- chopst.exe (PID: 1824)
- vbc.exe (PID: 4024)
- chopst.exe (PID: 4092)
- vbc.exe (PID: 1640)
Manual execution by a user
- wmpnscfg.exe (PID: 980)
- taskmgr.exe (PID: 2148)
Checks supported languages
- wmpnscfg.exe (PID: 980)
- JUZGADO SEGUNDO LABORAL DEL CIRCUITO,.exe (PID: 3316)
- vbc.exe (PID: 4024)
- vbc.exe (PID: 1908)
- chopst.exe (PID: 1824)
- chopst.exe (PID: 4092)
- vbc.exe (PID: 1640)
Executes as Windows Service
- SearchIndexer.exe (PID: 3496)
The process checks LSA protection
- wmpnscfg.exe (PID: 980)
- SearchIndexer.exe (PID: 3496)
- SearchProtocolHost.exe (PID: 1700)
- SearchProtocolHost.exe (PID: 3224)
- SearchFilterHost.exe (PID: 2344)
- JUZGADO SEGUNDO LABORAL DEL CIRCUITO,.exe (PID: 3316)
- chopst.exe (PID: 1824)
- vbc.exe (PID: 1908)
- vbc.exe (PID: 4024)
- chopst.exe (PID: 4092)
- vbc.exe (PID: 1640)
Application launched itself
- msedge.exe (PID: 1988)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 980)
- JUZGADO SEGUNDO LABORAL DEL CIRCUITO,.exe (PID: 3316)
- vbc.exe (PID: 1908)
- chopst.exe (PID: 1824)
- chopst.exe (PID: 4092)
- vbc.exe (PID: 1640)
- vbc.exe (PID: 4024)
Creates files in the program directory
- SearchIndexer.exe (PID: 3496)
The process uses the downloaded file
- msedge.exe (PID: 3180)
- WinRAR.exe (PID: 3796)
Reads Microsoft Office registry keys
- SearchProtocolHost.exe (PID: 3224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(1908) vbc.exe
C2 (1)roy2023.kozow.com
Ports (1)8000
BotnetDefault
Version| Edit 3LOSH RAT
Options
AutoRunfalse
MutexAsyncMutex_Default
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignatureGCApY6XX/YDXMazlfcl9f248t/EdXM3dYGBxMLf63pUtz+J81dwot6d9wPwkRFy47p2JHfG9aIK+TzctZlBmxdV7oxj4xe5VH78mXHjfDfWl0tJ58bZjzjGE9ow3DRiVLWp8wF1gRHgrOaRcUtAN3jHDChbxaDzBLvKX57aIcazAmyHaWlOChkmVG7OX0/dFbHoWBuNRMHpGrqW44mlFAkdqztrIDbxhLMIrh0F/lbMB85ZX3sC/7FUFHIpBypLWX6HX+ii8r6Zw6/a1ndHTqI7vxLjRrHjHgkaeHhJCAkle...
Keys
AES708e5b413fbf2c01d5cd9aca92070130918ceb4fdcfe6e699bc4c557d111f8f8
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
96
Monitored processes
50
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 628 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=5056 --field-trial-handle=1312,i,4419969699952160819,7991014248749427562,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 644 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2272 --field-trial-handle=1312,i,4419969699952160819,7991014248749427562,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 944 | "cmd.exe" /C copy "C:\Users\admin\AppData\Local\Temp\Rar$EXb3796.12146\JUZGADO SEGUNDO LABORAL DEL CIRCUITO,\JUZGADO SEGUNDO LABORAL DEL CIRCUITO,.exe" "C:\Users\admin\AppData\Roaming\chopst\chopst.exe" | C:\Windows\System32\cmd.exe | — | JUZGADO SEGUNDO LABORAL DEL CIRCUITO,.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 980 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 996 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3916 --field-trial-handle=1312,i,4419969699952160819,7991014248749427562,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1000 | "cmd.exe" /C schtasks /create /sc minute /mo 1 /tn "Nafifas" /tr "'C:\Users\admin\AppData\Roaming\chopst\chopst.exe'" /f | C:\Windows\System32\cmd.exe | — | JUZGADO SEGUNDO LABORAL DEL CIRCUITO,.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1052 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1244 --field-trial-handle=1312,i,4419969699952160819,7991014248749427562,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1656 --field-trial-handle=1312,i,4419969699952160819,7991014248749427562,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1368 | "cmd.exe" /C copy "C:\Users\admin\AppData\Roaming\chopst\chopst.exe" "C:\Users\admin\AppData\Roaming\chopst\chopst.exe" | C:\Windows\System32\cmd.exe | — | chopst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1640 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | — | chopst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 12.0.51209.34209 Modules
| |||||||||||||||
Total events
27 123
Read events
25 621
Write events
1 273
Delete events
229
Modification events
| (PID) Process: | (2784) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2784) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2784) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2784) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2784) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2784) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2784) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2784) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2784) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2784) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
2
Suspicious files
147
Text files
97
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2784 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR6F11.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2784 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 2784 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:CC0F4765383C088AEDE2FA0326683AC3 | SHA256:D76E1DAACDE434000C652B32FA54F09CA546DF3791EC6FDA4212C1651E7F7F75 | |||
| 2784 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:0E970564A21F67A5D654A4F38496EAAC | SHA256:25B57913E48F75EA6E9509510A354EE98976D0146134B5B1AE99ACD6B39CF87D | |||
| 2784 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 2784 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_D487D863E740C8499FC035E6C29F9FE8.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
| 2784 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_RssRule_2_04C8CAAEB7D6CD40B8DD0F88CEE27848.dat | xml | |
MD5:D8B37ED0410FB241C283F72B76987F18 | SHA256:31E68049F6B7F21511E70CD7F2D95B9CF1354CF54603E8F47C1FC40F40B7A114 | |||
| 2784 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TCPrefs_2_1F8A8F2091348147B9CDF7E50F3546BF.dat | xml | |
MD5:F194B1FA12F9B6F46A47391FAE8BEEC2 | SHA256:FCD8D7E030BE6EA7588E5C6CB568E3F1BDFC263942074B693942A27DF9521A74 | |||
| 2784 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5080DC7A65DB6A5960ECD874088F3328_862BA1770B2FEE013603D2FF9ABEAFDA | binary | |
MD5:AF000E3E443E407BEF8F6F5ED3EAC278 | SHA256:3700C06EA45CCBEB8E5BC3F4591CF4190F925D7D8EF0DEC62E6491FCE50107F5 | |||
| 1988 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF47136f.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
90
DNS requests
66
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
860 | svchost.exe | HEAD | 200 | 95.140.236.128:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c78f9967-7a8c-44b0-ad94-732b63c89638?P1=1692045433&P2=404&P3=2&P4=nxHSTXYlNC8qpwIWrP9y%2buEay%2bWg7rKPz8qwD34VRHhK%2bi4bHE4KsIvJ5HWs9Qglp9GlLlG%2bmMTmmMxew70FQg%3d%3d | GB | — | — | whitelisted |
2784 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
1088 | svchost.exe | GET | 304 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d0fb5dcd91188ca3 | US | compressed | 62.3 Kb | whitelisted |
2784 | OUTLOOK.EXE | GET | 200 | 104.18.15.101:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEQDwHUvue3yjezwFZqwFlyRY | unknown | binary | 2.18 Kb | whitelisted |
2784 | OUTLOOK.EXE | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?46bec8bb32e882e3 | US | compressed | 4.70 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 95.140.236.128:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c78f9967-7a8c-44b0-ad94-732b63c89638?P1=1692045433&P2=404&P3=2&P4=nxHSTXYlNC8qpwIWrP9y%2buEay%2bWg7rKPz8qwD34VRHhK%2bi4bHE4KsIvJ5HWs9Qglp9GlLlG%2bmMTmmMxew70FQg%3d%3d | GB | binary | 16.2 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 95.140.236.128:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c78f9967-7a8c-44b0-ad94-732b63c89638?P1=1692045433&P2=404&P3=2&P4=nxHSTXYlNC8qpwIWrP9y%2buEay%2bWg7rKPz8qwD34VRHhK%2bi4bHE4KsIvJ5HWs9Qglp9GlLlG%2bmMTmmMxew70FQg%3d%3d | GB | binary | 10.0 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 95.140.236.128:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c78f9967-7a8c-44b0-ad94-732b63c89638?P1=1692045433&P2=404&P3=2&P4=nxHSTXYlNC8qpwIWrP9y%2buEay%2bWg7rKPz8qwD34VRHhK%2bi4bHE4KsIvJ5HWs9Qglp9GlLlG%2bmMTmmMxew70FQg%3d%3d | GB | binary | 21.4 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 95.140.236.128:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c78f9967-7a8c-44b0-ad94-732b63c89638?P1=1692045433&P2=404&P3=2&P4=nxHSTXYlNC8qpwIWrP9y%2buEay%2bWg7rKPz8qwD34VRHhK%2bi4bHE4KsIvJ5HWs9Qglp9GlLlG%2bmMTmmMxew70FQg%3d%3d | GB | binary | 204 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 95.140.236.128:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c78f9967-7a8c-44b0-ad94-732b63c89638?P1=1692045433&P2=404&P3=2&P4=nxHSTXYlNC8qpwIWrP9y%2buEay%2bWg7rKPz8qwD34VRHhK%2bi4bHE4KsIvJ5HWs9Qglp9GlLlG%2bmMTmmMxew70FQg%3d%3d | GB | binary | 14.3 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2784 | OUTLOOK.EXE | 172.217.18.1:443 | drive-thirdparty.googleusercontent.com | GOOGLE | US | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2784 | OUTLOOK.EXE | 66.225.241.7:443 | centrodeeventos.com.co | SERVERCENTRAL | US | unknown |
2784 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2784 | OUTLOOK.EXE | 104.18.15.101:80 | ocsp.comodoca.com | CLOUDFLARENET | — | whitelisted |
2784 | OUTLOOK.EXE | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
3532 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
drive-thirdparty.googleusercontent.com |
| whitelisted |
centrodeeventos.com.co |
| unknown |
config.messenger.msn.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
dns.msftncsi.com |
| shared |
drive.google.com |
| shared |
edge.microsoft.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
config.edge.skype.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.kozow .com Domain |