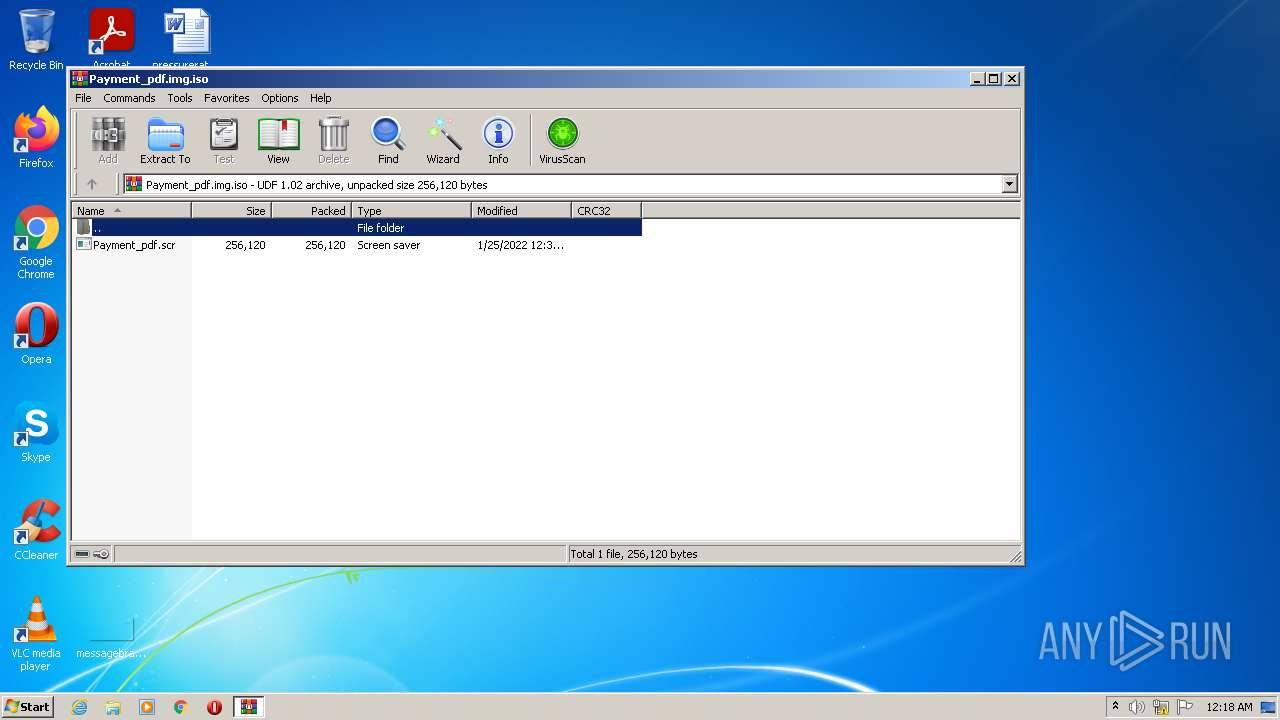
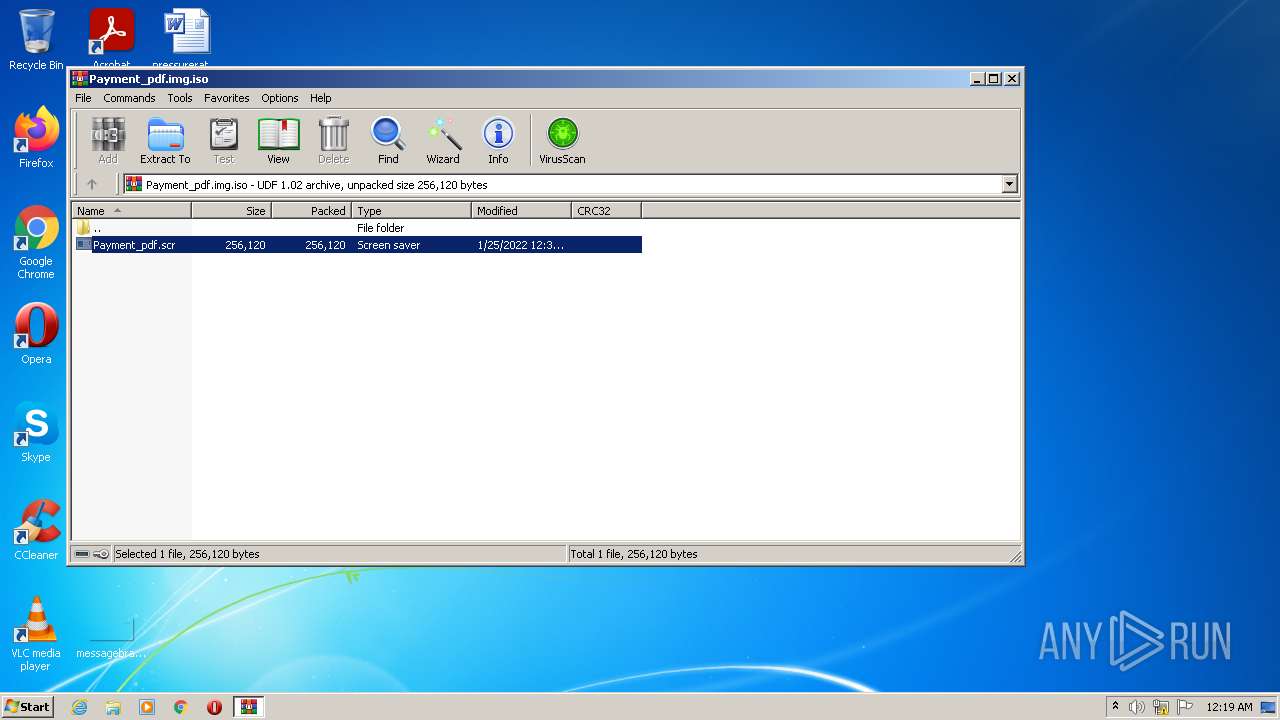
| File name: | Payment_pdf.img |
| Full analysis: | https://app.any.run/tasks/2ecfa5e4-8662-4f1a-93cb-a601db75b517 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | January 25, 2022, 00:18:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-iso9660-image |
| File info: | UDF filesystem data (version 1.5) 'BLUESTACKS' |
| MD5: | D1EC0383116C1E55C908449EB3BF7D48 |
| SHA1: | 907750B320B0D9E5F4166E899432EFA7B0E7DF96 |
| SHA256: | 12EFC041540D5BA12FE9D935943C1E01668EFC39F47F2EC2396A4FD4266B4A38 |
| SSDEEP: | 6144:JMI8vQQvwpcP30S617wMVLoJ9qz8G/mp/U2NBu6:5SnvOT2Tu6 |
MALICIOUS
Drops executable file immediately after starts
- Payment_pdf.scr (PID: 2664)
- Explorer.EXE (PID: 1656)
- DllHost.exe (PID: 3580)
- mscp8lefi.exe (PID: 1876)
Application was dropped or rewritten from another process
- Payment_pdf.scr (PID: 2664)
- Payment_pdf.scr (PID: 3676)
- mscp8lefi.exe (PID: 1876)
- mscp8lefi.exe (PID: 2836)
Loads dropped or rewritten executable
- Payment_pdf.scr (PID: 2664)
- mscp8lefi.exe (PID: 1876)
Changes the autorun value in the registry
- wlanext.exe (PID: 2156)
Actions looks like stealing of personal data
- wlanext.exe (PID: 2156)
FORMBOOK was detected
- Explorer.EXE (PID: 1656)
Connects to CnC server
- Explorer.EXE (PID: 1656)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 1252)
- Payment_pdf.scr (PID: 2664)
- Payment_pdf.scr (PID: 3676)
- mscp8lefi.exe (PID: 1876)
- mscp8lefi.exe (PID: 2836)
Checks supported languages
- WinRAR.exe (PID: 1252)
- Payment_pdf.scr (PID: 2664)
- Payment_pdf.scr (PID: 3676)
- mscp8lefi.exe (PID: 1876)
- mscp8lefi.exe (PID: 2836)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1252)
- Payment_pdf.scr (PID: 2664)
- Explorer.EXE (PID: 1656)
- DllHost.exe (PID: 3580)
- mscp8lefi.exe (PID: 1876)
Drops a file with too old compile date
- WinRAR.exe (PID: 1252)
- Explorer.EXE (PID: 1656)
- DllHost.exe (PID: 3580)
Starts application with an unusual extension
- WinRAR.exe (PID: 1252)
- Payment_pdf.scr (PID: 2664)
Drops a file with a compile date too recent
- Payment_pdf.scr (PID: 2664)
- mscp8lefi.exe (PID: 1876)
Application launched itself
- Payment_pdf.scr (PID: 2664)
- mscp8lefi.exe (PID: 1876)
Starts CMD.EXE for commands execution
- wlanext.exe (PID: 2156)
Reads Environment values
- wlanext.exe (PID: 2156)
Loads DLL from Mozilla Firefox
- wlanext.exe (PID: 2156)
Executed via COM
- DllHost.exe (PID: 3580)
Reads the cookies of Google Chrome
- wlanext.exe (PID: 2156)
Creates a directory in Program Files
- DllHost.exe (PID: 3580)
Creates files in the program directory
- DllHost.exe (PID: 3580)
INFO
Checks supported languages
- wlanext.exe (PID: 2156)
- cmd.exe (PID: 4036)
- DllHost.exe (PID: 3580)
- Firefox.exe (PID: 3404)
Manual execution by user
- wlanext.exe (PID: 2156)
Reads the computer name
- wlanext.exe (PID: 2156)
- DllHost.exe (PID: 3580)
- Firefox.exe (PID: 3404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .iso | | | ISO 9660 CD image (27.6) |
|---|---|---|
| .atn | | | Photoshop Action (27.1) |
| .gmc | | | Game Music Creator Music (6.1) |
EXIF
Composite
| VolumeSize: | 1198 kB |
|---|
ISO
| VolumeModifyDate: | 2022:01:25 01:01:48.00+01:00 |
|---|---|
| VolumeCreateDate: | 2022:01:25 01:01:48.00+01:00 |
| Software: | IMGBURN V2.5.8.0 - THE ULTIMATE IMAGE BURNER! |
| VolumeSetName: | UNDEFINED |
| RootDirectoryCreateDate: | 2022:01:25 01:01:48+01:00 |
| VolumeBlockSize: | 2048 |
| VolumeBlockCount: | 599 |
| VolumeName: | BLUESTACKS |
Total processes
45
Monitored processes
10
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1252 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Payment_pdf.img.iso" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1656 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1876 | "C:\Program Files\Yc8t\mscp8lefi.exe" | C:\Program Files\Yc8t\mscp8lefi.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2156 | "C:\Windows\System32\wlanext.exe" | C:\Windows\System32\wlanext.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Wireless LAN 802.11 Extensibility Framework Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2664 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa1252.9654\Payment_pdf.scr" /S | C:\Users\admin\AppData\Local\Temp\Rar$DIa1252.9654\Payment_pdf.scr | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2836 | "C:\Program Files\Yc8t\mscp8lefi.exe" | C:\Program Files\Yc8t\mscp8lefi.exe | — | mscp8lefi.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3404 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | — | wlanext.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 3580 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3676 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa1252.9654\Payment_pdf.scr" /S | C:\Users\admin\AppData\Local\Temp\Rar$DIa1252.9654\Payment_pdf.scr | — | Payment_pdf.scr | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4036 | /c del "C:\Users\admin\AppData\Local\Temp\Rar$DIa1252.9654\Payment_pdf.scr" | C:\Windows\System32\cmd.exe | — | wlanext.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 686
Read events
2 654
Write events
32
Delete events
0
Modification events
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Payment_pdf.img.iso | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
5
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1252.9654\Payment_pdf.scr | executable | |
MD5:— | SHA256:— | |||
| 2664 | Payment_pdf.scr | C:\Users\admin\AppData\Local\Temp\nsqFDCD.tmp | binary | |
MD5:— | SHA256:— | |||
| 2664 | Payment_pdf.scr | C:\Users\admin\AppData\Local\Temp\svhrfcu513po5jsz5ai | binary | |
MD5:— | SHA256:— | |||
| 3580 | DllHost.exe | C:\Program Files\Yc8t\mscp8lefi.exe | executable | |
MD5:— | SHA256:— | |||
| 1656 | Explorer.EXE | C:\Users\admin\AppData\Local\Temp\Yc8t\mscp8lefi.exe | executable | |
MD5:— | SHA256:— | |||
| 1876 | mscp8lefi.exe | C:\Users\admin\AppData\Local\Temp\nsm5653.tmp | binary | |
MD5:— | SHA256:— | |||
| 2664 | Payment_pdf.scr | C:\Users\admin\AppData\Local\Temp\pkuvzmqvmg | binary | |
MD5:— | SHA256:— | |||
| 2664 | Payment_pdf.scr | C:\Users\admin\AppData\Local\Temp\nsqFDCE.tmp\euudcvzjbf.dll | executable | |
MD5:— | SHA256:— | |||
| 1876 | mscp8lefi.exe | C:\Users\admin\AppData\Local\Temp\nsm5654.tmp\euudcvzjbf.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
79
TCP/UDP connections
87
DNS requests
28
Threats
176
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1656 | Explorer.EXE | GET | — | 35.246.6.109:80 | http://www.tekhelpwi.com/onnm/?mB=RhQNnq9sPZh6MiPeyVYcoNj73w663zjwbHXKEcO9qTeYM36+nleOS9EM9T/RW4xlpbVOkQ==&pP=Ntcl | US | — | — | malicious |
1656 | Explorer.EXE | GET | — | 192.53.120.121:80 | http://www.safeflashloans.com/onnm/?mB=oqFWsZwS4rG8QH5VjvcUn/HwRUg4YYjusi2wEz5owqNXUXkbs3dcf8OS2t9NxX1n0sIMtw==&pP=Ntcl | US | — | — | malicious |
1656 | Explorer.EXE | GET | — | 51.255.135.75:80 | http://www.exclusiveyachtexcellence.com/onnm/?mB=RVh2yLzW6uIKhfoMFPExSCdoowYTd+edm0qOpIgmN/V0a/prx4+C1xWIvgtXrWV9iy7i+Q==&pP=Ntcl | ES | — | — | malicious |
1656 | Explorer.EXE | GET | — | 35.213.168.55:80 | http://www.swipe-kart.info/onnm/?mB=Ka2gMXeq+mncIC4/J7q3sFQUPAFvJaJgDf//Y9W4Aah9NXEJ1vxKRmpVdSNCRLDYQGpbhg==&T8wX=pBeXcndhfL1dhpx0 | US | — | — | malicious |
1656 | Explorer.EXE | GET | 404 | 199.192.25.31:80 | http://www.ceser33.com/onnm/?mB=rr5+YX7TZg0VreuljdbDR9+IXs+cIzV3AmzdzBYxrOjKXZrBertcOHKAT5iBLJ8z5SHFyA==&pP=Ntcl | US | html | 277 b | malicious |
1656 | Explorer.EXE | GET | 403 | 34.98.99.30:80 | http://www.championspoorts.com/onnm/?mB=ryEb+UFJTLhMO0qB5WQlYqbifCxCiHG4TITt7zhnTSIBjH9SgYtVDkv+QFTq5VfSF6nGLw==&T8wX=pBeXcndhfL1dhpx0 | US | html | 275 b | whitelisted |
1656 | Explorer.EXE | POST | — | 35.246.6.109:80 | http://www.tekhelpwi.com/onnm/ | US | — | — | malicious |
1656 | Explorer.EXE | GET | 404 | 50.87.193.142:80 | http://www.mmiaustinhome.com/onnm/?mB=6Xh6Uwx4kTJUqlr6LZiueI6oxNE6VPdIMOEpWIUDyPnwzOs1OHW5FfmtV8DjDwQ1J6e5kQ==&T8wX=pBeXcndhfL1dhpx0 | US | html | 315 b | malicious |
1656 | Explorer.EXE | GET | 403 | 37.123.118.150:80 | http://www.datumhard.quest/onnm/?mB=YhQ80bL7qru0spFZNjjllEJGcqfVVEgmq9fEXGAN6kv1v63f6YOgM5PUve+vxJxg4DS/Sg==&pP=Ntcl | GB | html | 178 b | malicious |
1656 | Explorer.EXE | GET | 301 | 45.76.85.102:80 | http://www.ketchuphub.com/onnm/?mB=eZxEjN+IqEBYO1y8t2d535guTdE9s09GyKLeVeeFtH/AteeCQhyWgLQ64EwRvn2rv1NT6Q==&T8wX=pBeXcndhfL1dhpx0 | DE | html | 510 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1656 | Explorer.EXE | 192.53.120.121:80 | www.safeflashloans.com | — | US | malicious |
1656 | Explorer.EXE | 199.192.25.31:80 | www.ceser33.com | — | US | malicious |
— | — | 94.136.40.51:80 | www.colt.business | Host Europe GmbH | GB | malicious |
1656 | Explorer.EXE | 13.56.33.8:80 | www.swiftspectra.com | Amazon.com, Inc. | US | malicious |
1656 | Explorer.EXE | 35.246.6.109:80 | www.tekhelpwi.com | — | US | malicious |
1656 | Explorer.EXE | 51.255.135.75:80 | www.exclusiveyachtexcellence.com | OVH SAS | ES | malicious |
1656 | Explorer.EXE | 44.227.76.166:80 | www.2546452.xyz | University of California, San Diego | US | malicious |
— | — | 15.197.142.173:80 | www.pacificsolarpros.com | Hewlett-Packard Company | US | malicious |
1656 | Explorer.EXE | 72.14.185.43:80 | www.cloudplanet.pro | Linode, LLC | US | malicious |
1656 | Explorer.EXE | 45.76.85.102:80 | www.ketchuphub.com | Choopa, LLC | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.blademor.com |
| unknown |
www.datumhard.quest |
| malicious |
www.safeflashloans.com |
| malicious |
www.ceser33.com |
| malicious |
www.colt.business |
| malicious |
www.creativehouseglobal.com |
| unknown |
www.swiftspectra.com |
| malicious |
www.tekhelpwi.com |
| malicious |
www.exclusiveyachtexcellence.com |
| malicious |
www.pacificsolarpros.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1656 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1656 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1656 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1656 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1656 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1656 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1656 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1656 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1656 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1656 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
29 ETPRO signatures available at the full report