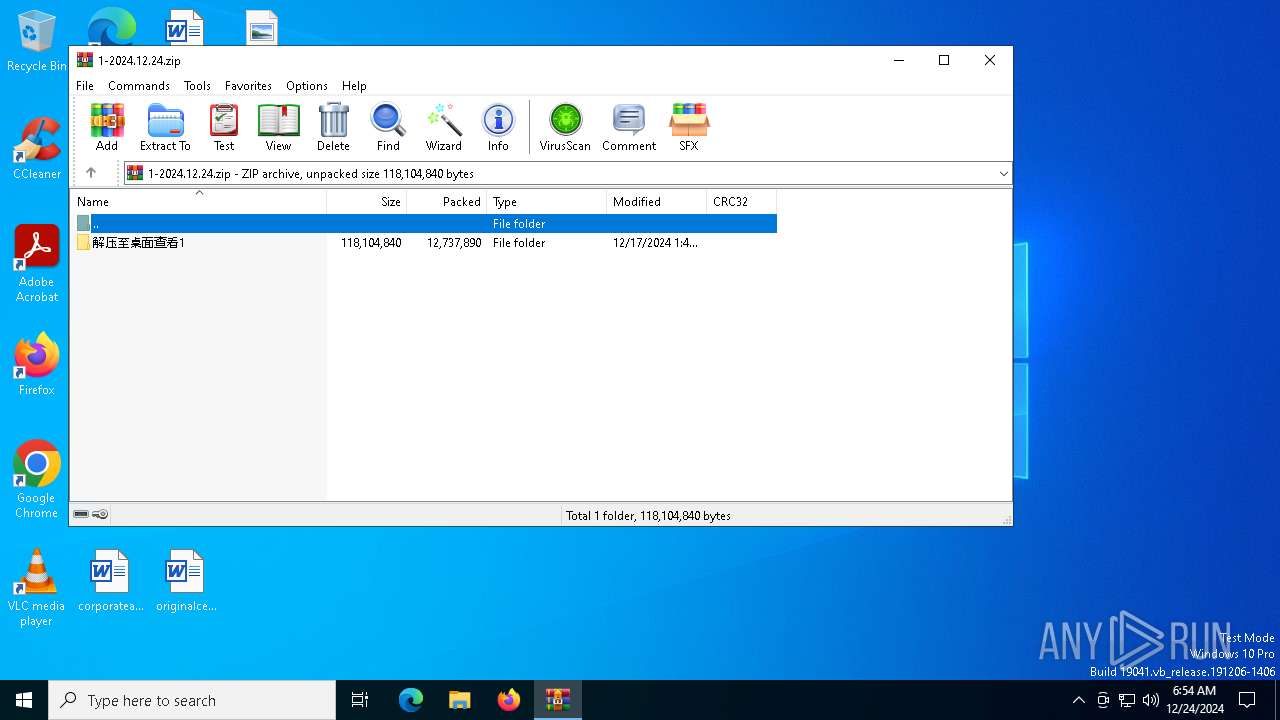
| File name: | 1-2024.12.24.zip |
| Full analysis: | https://app.any.run/tasks/28f5b646-473a-4b33-b3ca-0a79ee9d11c3 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | December 24, 2024, 06:54:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
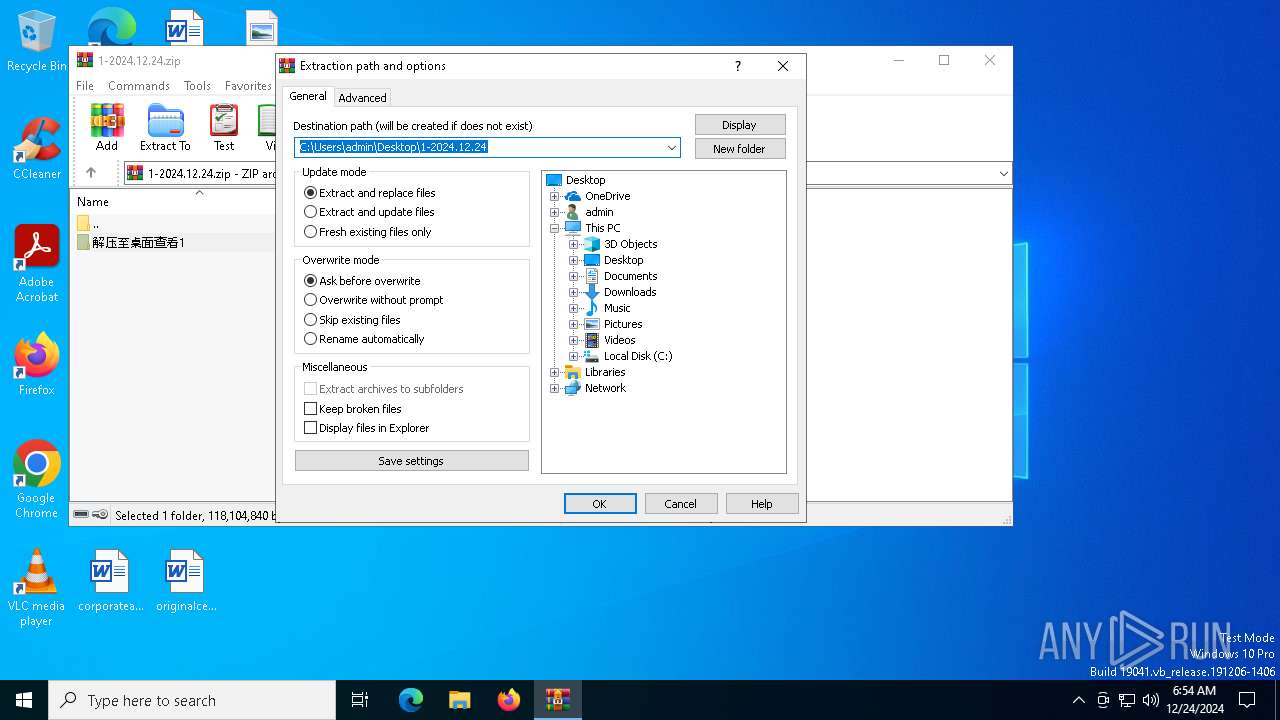
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 07170FE11BE60C1103B112C1CCDDBB69 |
| SHA1: | 55C37EE70FEF304A49F34A6595CE0CF40DDEE606 |
| SHA256: | 12C4E709F2EE2427A029B00F0F4E1F0AA601694E7A67E42545B229C5ABA3AC6F |
| SSDEEP: | 98304:ecDyEtSnXW0QztL3l/UZhCJfVq+P0Ib+uMEWmxCGFrAtwzcx09oAbXV/VOqECjU2:z46dJw1MtiR8Tiadqo2DrU |
MALICIOUS
Application was injected by another process
- explorer.exe (PID: 4488)
Generic archive extractor
- WinRAR.exe (PID: 6356)
Runs injected code in another process
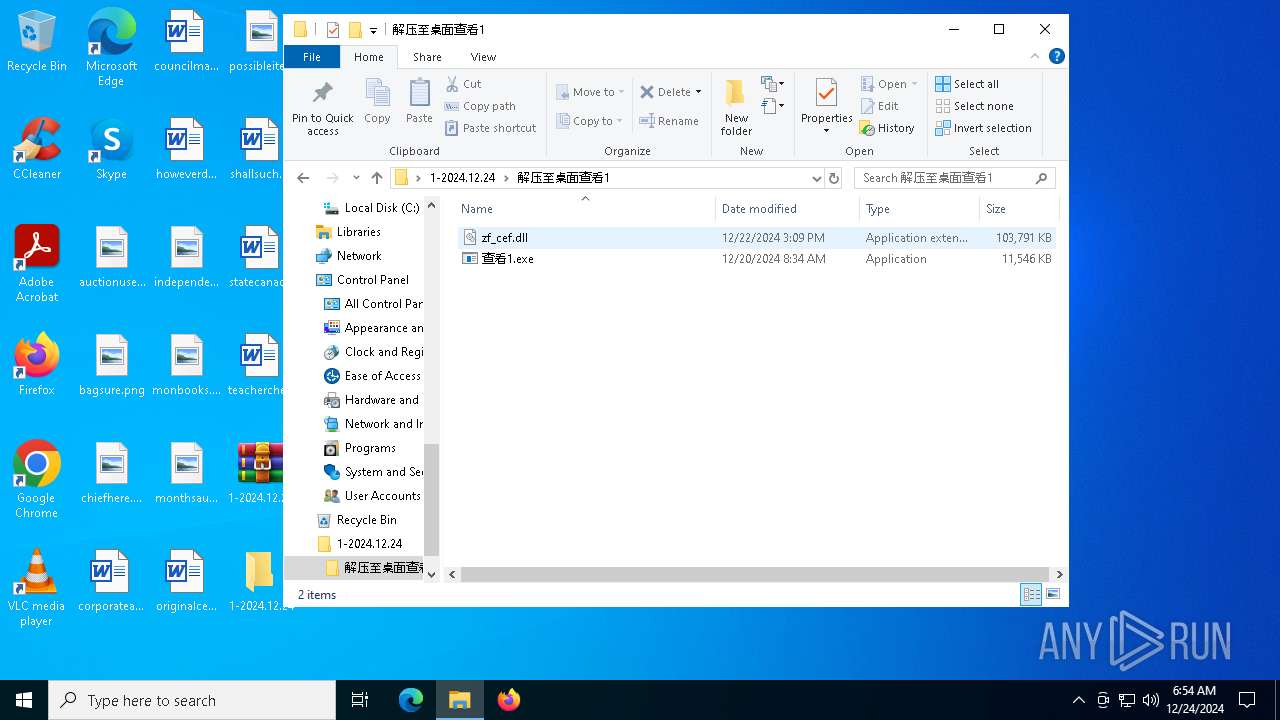
- 查看1.exe (PID: 4024)
ASYNCRAT has been detected (SURICATA)
- explorer.exe (PID: 4488)
Connects to the CnC server
- explorer.exe (PID: 4488)
Changes the autorun value in the registry
- explorer.exe (PID: 4488)
SUSPICIOUS
Executable content was dropped or overwritten
- explorer.exe (PID: 4488)
Process requests binary or script from the Internet
- explorer.exe (PID: 4488)
Connects to unusual port
- explorer.exe (PID: 4488)
Potential Corporate Privacy Violation
- explorer.exe (PID: 4488)
Connects to the server without a host name
- explorer.exe (PID: 4488)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6356)
- explorer.exe (PID: 4488)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4488)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6356)
Creates files in the program directory
- explorer.exe (PID: 4488)
Manual execution by a user
- 查看1.exe (PID: 4024)
The sample compiled with english language support
- explorer.exe (PID: 4488)
Checks supported languages
- 查看1.exe (PID: 5872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:17 09:42:42 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
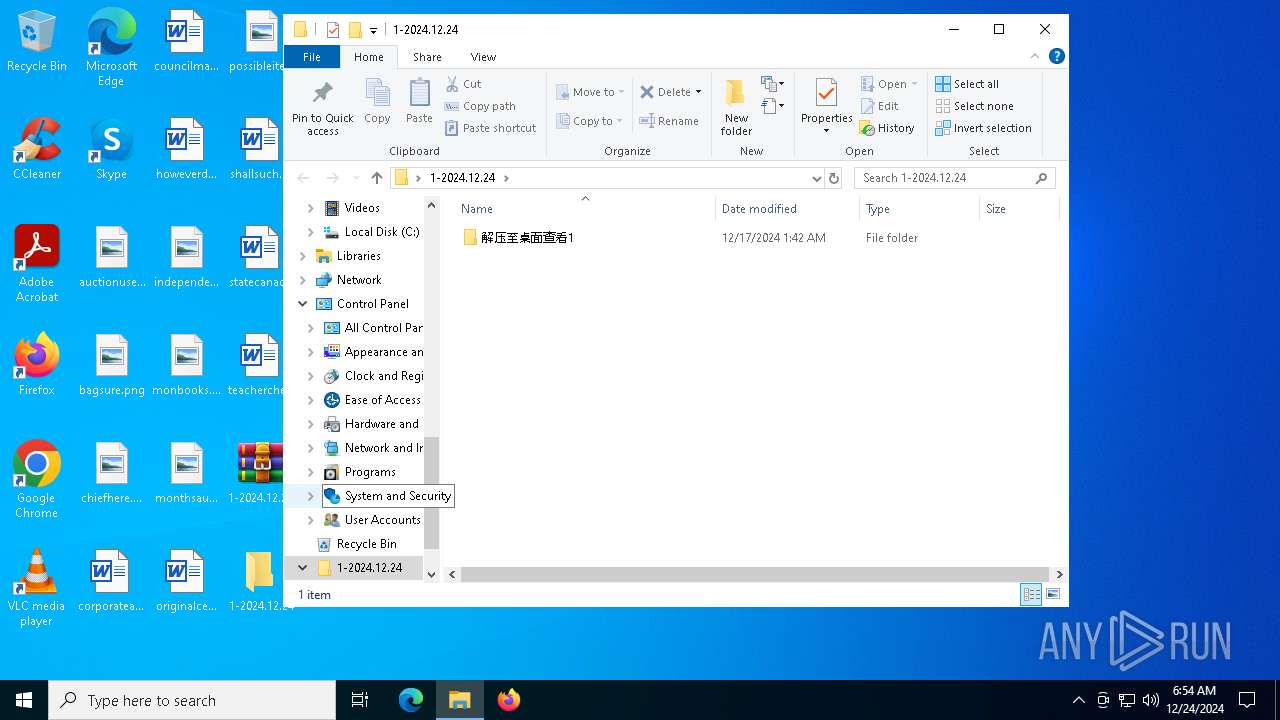
| ZipFileName: | 解压至桌面查看1/ |
Total processes
130
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2676 | "C:\Users\admin\Desktop\1-2024.12.24\解压至桌面查看1\查看1.exe" | C:\Users\admin\Desktop\1-2024.12.24\解压至桌面查看1\查看1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4024 | "C:\Users\admin\Desktop\1-2024.12.24\解压至桌面查看1\查看1.exe" | C:\Users\admin\Desktop\1-2024.12.24\解压至桌面查看1\查看1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4488 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5872 | "C:\Users\admin\Desktop\1-2024.12.24\解压至桌面查看1\查看1.exe" | C:\Users\admin\Desktop\1-2024.12.24\解压至桌面查看1\查看1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6356 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\1-2024.12.24.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6876 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 458
Read events
13 330
Write events
110
Delete events
18
Modification events
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000501E8 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A48A294F7A40804AB924005FF030B61F | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\1-2024.12.24.zip | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
Executable files
20
Suspicious files
7
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6356 | WinRAR.exe | C:\Users\admin\Desktop\1-2024.12.24\解压至桌面查看1\zf_cef.dll | — | |
MD5:— | SHA256:— | |||
| 4488 | explorer.exe | C:\ProgramData\iuYbpW\intl.dll | — | |
MD5:— | SHA256:— | |||
| 4488 | explorer.exe | C:\Users\Public\Downloads\QQgames.exe | executable | |
MD5:C3AF518D7BB5F7F368FEBCE09C7E57CE | SHA256:8F490791F7164633E2BC3BFE129C829986A45B918566C2FE1D63F3C77B0EB28C | |||
| 4024 | 查看1.exe | C:\Users\Public\Downloads\tjqd.jpg | binary | |
MD5:092FF96DFB0A09DA2CECEA18443A0AE9 | SHA256:5816F061335B4061A2D1769A85FACCC6E4CCFADD211819E19F8709BBEFE36558 | |||
| 4488 | explorer.exe | C:\ProgramData\iuYbpW\gmodule-2.0.dll | executable | |
MD5:D541E6AFF57DAB928B8C3CBA7C5EFDF2 | SHA256:5E3169122A06885A06ACA3E95B894884165B944FD79EFB5AAF133863E1E7F0F9 | |||
| 4488 | explorer.exe | C:\ProgramData\iuYbpW\gobject-2.0.dll | executable | |
MD5:04F3300D00CA0AB0964DD14C71639D36 | SHA256:D701B3F556B370D6C0BE5F37B5028AC8A61169F06D9B4065AEAE23621F122572 | |||
| 4488 | explorer.exe | C:\ProgramData\iuYbpW\HFqLnc.exe | executable | |
MD5:C3AF518D7BB5F7F368FEBCE09C7E57CE | SHA256:8F490791F7164633E2BC3BFE129C829986A45B918566C2FE1D63F3C77B0EB28C | |||
| 4488 | explorer.exe | C:\Users\Public\Downloads\1.dll | binary | |
MD5:A326F18C1F5EDD0CE2CBD9097A44ECB2 | SHA256:F696FCA76F9B9163B04A66246F17C83656CDDE2C59A2D28CA8EBE120D68F2242 | |||
| 4488 | explorer.exe | C:\ProgramData\anjeOY\gmodule-2.0.dll | executable | |
MD5:D541E6AFF57DAB928B8C3CBA7C5EFDF2 | SHA256:5E3169122A06885A06ACA3E95B894884165B944FD79EFB5AAF133863E1E7F0F9 | |||
| 4024 | 查看1.exe | C:\Users\Public\Downloads\bb.jpg | binary | |
MD5:576581FAF20831DFB4DBB40E8E6423D9 | SHA256:00F760C4BBDAAC16D679D72D23FD25A5E4D8131D7BB1967E226ED5EB52A5CF79 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
38
DNS requests
18
Threats
59
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3564 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4488 | explorer.exe | GET | 200 | 8.134.199.119:80 | http://8.134.199.119/regname.txt | unknown | — | — | unknown |
6916 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4488 | explorer.exe | GET | 200 | 8.134.199.119:80 | http://8.134.199.119/wj/vmtoolsd.exe | unknown | — | — | malicious |
4488 | explorer.exe | GET | 200 | 8.134.199.119:80 | http://8.134.199.119/wj/glib-2.0.dll | unknown | — | — | malicious |
4488 | explorer.exe | GET | 200 | 8.134.199.119:80 | http://8.134.199.119/wj/gobject-2.0.dll | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2624 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.209.185:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4488 | explorer.exe | A Network Trojan was detected | ET MALWARE Suspicious User Agent Detected (RookIE) - Common with Downloaders |
4488 | explorer.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4488 | explorer.exe | A Network Trojan was detected | ET MALWARE Potential Dridex.Maldoc Minimal Executable Request |
4488 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
4488 | explorer.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
4488 | explorer.exe | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
4488 | explorer.exe | A Network Trojan was detected | ET MALWARE Suspicious User Agent Detected (RookIE) - Common with Downloaders |
4488 | explorer.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
4488 | explorer.exe | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
4488 | explorer.exe | A Network Trojan was detected | ET MALWARE Suspicious User Agent Detected (RookIE) - Common with Downloaders |
3 ETPRO signatures available at the full report