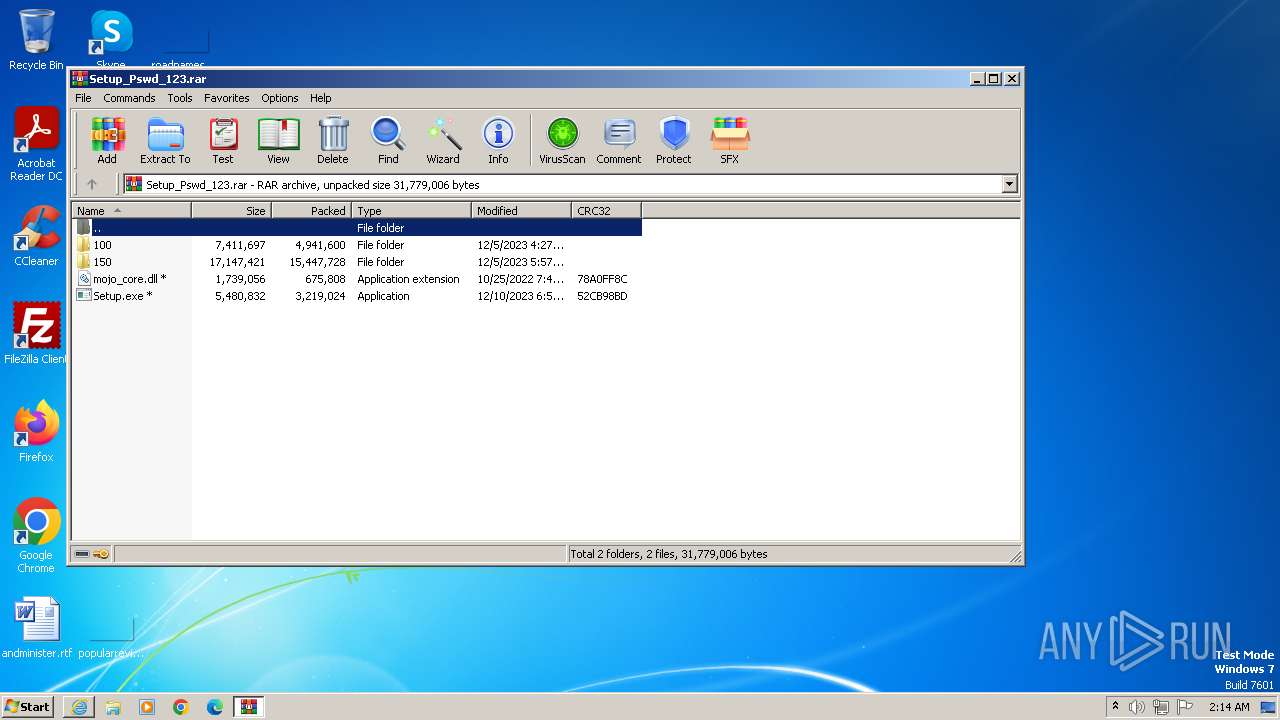
| URL: | https://download2391.mediafire.com/te2wqcph72kgq4S8J_8Zi-Bj579787qk7ythvTA-fVy4XUEuBEKuC5R0vyaG9F3qMsP1gqRNSiFlJe4PKRzXboYYVF6QBXZWfHtrzAvMBDIZ1zKO_kXh4Rgld8Mxi3j2zTk_r0QRQIprLtL76_c-te0UqdM8UzA0a7xGamgBCtpBVQ/44qczly0v31xon0/Setup_Pswd_123.rar |
| Full analysis: | https://app.any.run/tasks/7f54be80-f4cc-4f58-8dee-30635c0aebc9 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | December 11, 2023, 02:13:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E776C3256F8FD8CD40FE4917E85C8743 |
| SHA1: | C94C934A728511A0B85EA0B5C3BF2D3BC0B3D5C1 |
| SHA256: | 12C4164F3822BEB420F024A727E6DF62F1B94147165EDAFE206F7B4B21A7BABF |
| SSDEEP: | 6:2SWbUFQeGXAvkfe/8vlvVgoyTWoPZ22pzRR5aByPUGa:2tbJei1vjVoPI2Dah7 |
MALICIOUS
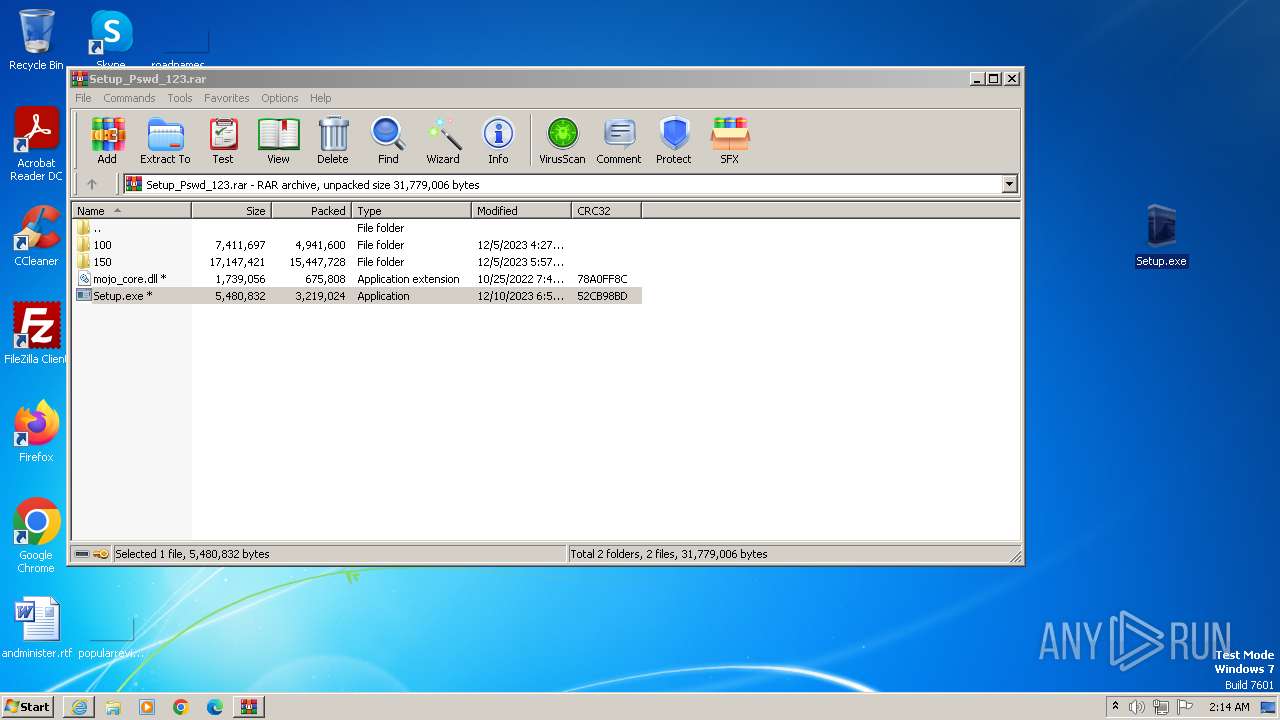
Drops the executable file immediately after the start
- Setup.exe (PID: 2728)
LUMMA has been detected (SURICATA)
- RegSvcs.exe (PID: 3632)
Connects to the CnC server
- RegSvcs.exe (PID: 3632)
LUMMA has been detected (YARA)
- RegSvcs.exe (PID: 3632)
- Setup.exe (PID: 2728)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 3632)
SUSPICIOUS
Reads browser cookies
- RegSvcs.exe (PID: 3632)
Searches for installed software
- RegSvcs.exe (PID: 3632)
INFO
Reads the computer name
- Setup.exe (PID: 2728)
- wmpnscfg.exe (PID: 1860)
- RegSvcs.exe (PID: 3632)
Manual execution by a user
- wmpnscfg.exe (PID: 1860)
- Setup.exe (PID: 2728)
Application launched itself
- iexplore.exe (PID: 1556)
The process uses the downloaded file
- iexplore.exe (PID: 1556)
- WinRAR.exe (PID: 3276)
Reads the machine GUID from the registry
- Setup.exe (PID: 2728)
Create files in a temporary directory
- Setup.exe (PID: 2728)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3276)
Checks supported languages
- Setup.exe (PID: 2728)
- wmpnscfg.exe (PID: 1860)
- RegSvcs.exe (PID: 3632)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
45
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1116 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1556 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://download2391.mediafire.com/te2wqcph72kgq4S8J_8Zi-Bj579787qk7ythvTA-fVy4XUEuBEKuC5R0vyaG9F3qMsP1gqRNSiFlJe4PKRzXboYYVF6QBXZWfHtrzAvMBDIZ1zKO_kXh4Rgld8Mxi3j2zTk_r0QRQIprLtL76_c-te0UqdM8UzA0a7xGamgBCtpBVQ/44qczly0v31xon0/Setup_Pswd_123.rar" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1860 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
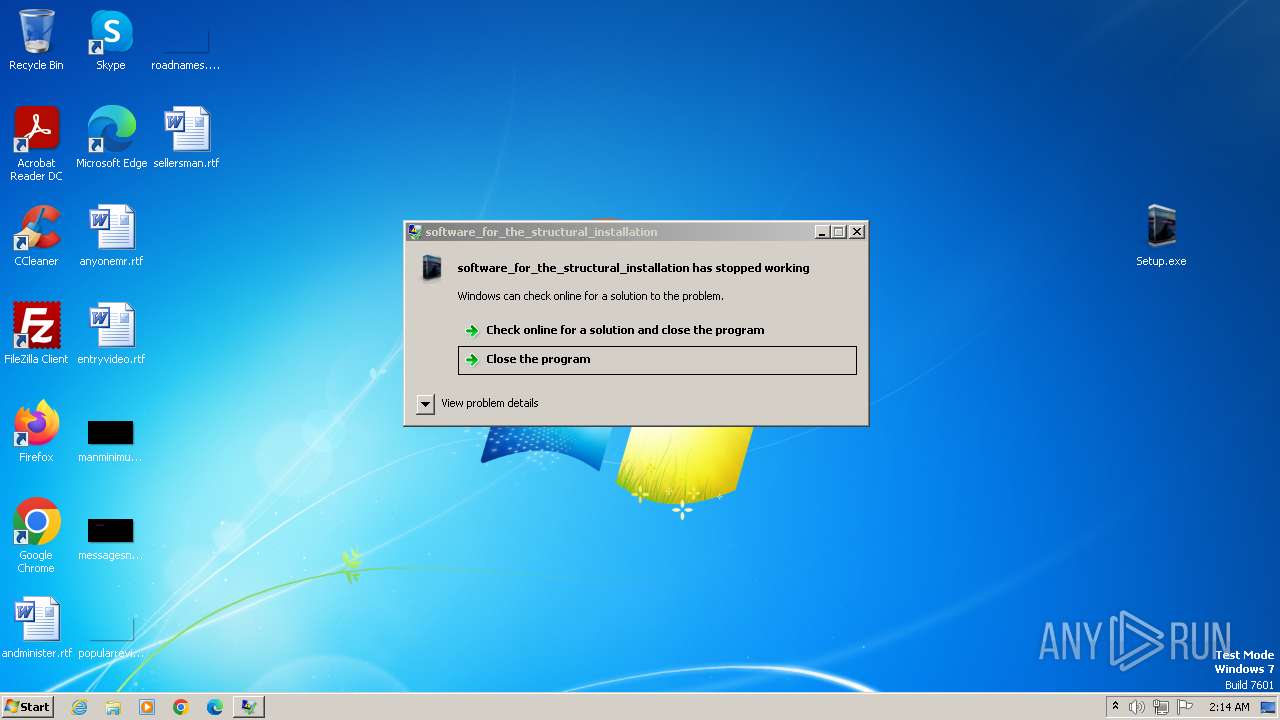
| 2728 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: software_for_the_structural_installation Exit code: 3221225477 Version: 1.2.0.0 Modules
| |||||||||||||||
| 3276 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Setup_Pswd_123.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3632 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
Total events
18 670
Read events
18 596
Write events
73
Delete events
1
Modification events
| (PID) Process: | (1556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
2
Suspicious files
14
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Setup_Pswd_123.rar.y96eoow.partial | — | |
MD5:— | SHA256:— | |||
| 1556 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Setup_Pswd_123.rar | — | |
MD5:— | SHA256:— | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\72BA427A91F50409B9EAC87F2B59B951_8FD6BB79A5EEF06F3F8595CB48A9AB04 | binary | |
MD5:7E0646E5931764164EB1AC9210CBAF8B | SHA256:547F305203AFE34F7EBCF2785B49F8FB40292C47F4F7F65AE1BE2211B697A827 | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:477381B89393A73BB947FCC925C09C80 | SHA256:6C941ED7EA511670E065D7F38999FC649CCC3C318F0456AE7E22134B517E5A78 | |||
| 1556 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB6A568B2A4BF9AA6.TMP | binary | |
MD5:A4B76342B62D57A1DC5CFCB8BAB4C7EF | SHA256:20E4BA319137E3D6ACAB3748A718C564EA43127FDF4BBD3EA4372405476800B0 | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_BACC6CD2B29F18349081C9FD2343833B | binary | |
MD5:CDA3E41EF166E7069D81BB8B07990E73 | SHA256:7CB7CDDB132B7A6F7EE7E495FDBD2C811675403F93D77CEC86E33F8524CE2E4E | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\72BA427A91F50409B9EAC87F2B59B951_8FD6BB79A5EEF06F3F8595CB48A9AB04 | binary | |
MD5:77321E1A529CD02CB4D26648C117FB2D | SHA256:816D720863CE30A14D452D08583F298419F684C396AF96D9EFEEF82C007B4B18 | |||
| 1556 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
| 1556 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{E1A20027-97CA-11EE-A826-12A9866C77DE}.dat | binary | |
MD5:56D0FF379EF7A6945938D59B1865022E | SHA256:A40F07DAD12EC4EFB770A322AF982B0641DD1640EC926766CAD25868990E8E9F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
53
DNS requests
8
Threats
48
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1116 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEBN9U5yqfDGppDNwGWiEeo0%3D | unknown | binary | 2.18 Kb | unknown |
1116 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQh80WaEMqmyEvaHjlisSfVM4p8SAQUF9nWJSdn%2BTHCSUPZMDZEjGypT%2BsCED%2B0KeRQ8NP60VP53TIby3A%3D | unknown | binary | 471 b | unknown |
3632 | RegSvcs.exe | POST | 200 | 188.114.97.3:80 | http://suburbmeetabuseowp.pw/api | unknown | text | 2 b | unknown |
3632 | RegSvcs.exe | POST | 200 | 188.114.97.3:80 | http://suburbmeetabuseowp.pw/api | unknown | text | 16.5 Kb | unknown |
1116 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a88ccd45ad45c010 | unknown | compressed | 4.66 Kb | unknown |
3632 | RegSvcs.exe | POST | 200 | 188.114.97.3:80 | http://suburbmeetabuseowp.pw/api | unknown | text | 21 b | unknown |
3632 | RegSvcs.exe | POST | 200 | 188.114.97.3:80 | http://suburbmeetabuseowp.pw/api | unknown | text | 21 b | unknown |
3632 | RegSvcs.exe | POST | 200 | 188.114.97.3:80 | http://suburbmeetabuseowp.pw/api | unknown | text | 21 b | unknown |
3632 | RegSvcs.exe | POST | 200 | 188.114.97.3:80 | http://suburbmeetabuseowp.pw/api | unknown | text | 21 b | unknown |
3632 | RegSvcs.exe | POST | 200 | 188.114.97.3:80 | http://suburbmeetabuseowp.pw/api | unknown | text | 21 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1116 | iexplore.exe | 199.91.155.132:443 | download2391.mediafire.com | MEDIAFIRE | US | unknown |
1116 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1116 | iexplore.exe | 172.64.149.23:80 | ocsp.usertrust.com | CLOUDFLARENET | US | unknown |
1116 | iexplore.exe | 104.18.38.233:80 | ocsp.usertrust.com | CLOUDFLARENET | — | shared |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1556 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
1556 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download2391.mediafire.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
suburbmeetabuseowp.pw |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
3632 | RegSvcs.exe | Misc activity | ET INFO HTTP Request to a *.pw domain |
3632 | RegSvcs.exe | Malware Command and Control Activity Detected | ET MALWARE [ANY.RUN] Win32/Lumma Stealer Check-In |
3632 | RegSvcs.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Win32/Lumma Stealer Check-In |
3632 | RegSvcs.exe | Misc activity | ET INFO HTTP Request to a *.pw domain |
3632 | RegSvcs.exe | Malware Command and Control Activity Detected | ET MALWARE [ANY.RUN] Win32/Lumma Stealer Exfiltration |
3632 | RegSvcs.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Win32/Lumma Stealer Exfiltration |
3632 | RegSvcs.exe | Misc activity | ET INFO HTTP Request to a *.pw domain |
3632 | RegSvcs.exe | Misc activity | ET INFO HTTP Request to a *.pw domain |
2 ETPRO signatures available at the full report