| File name: | ab.bin |
| Full analysis: | https://app.any.run/tasks/e0568d5c-9174-4604-b029-43b5f7fe824e |
| Verdict: | Malicious activity |
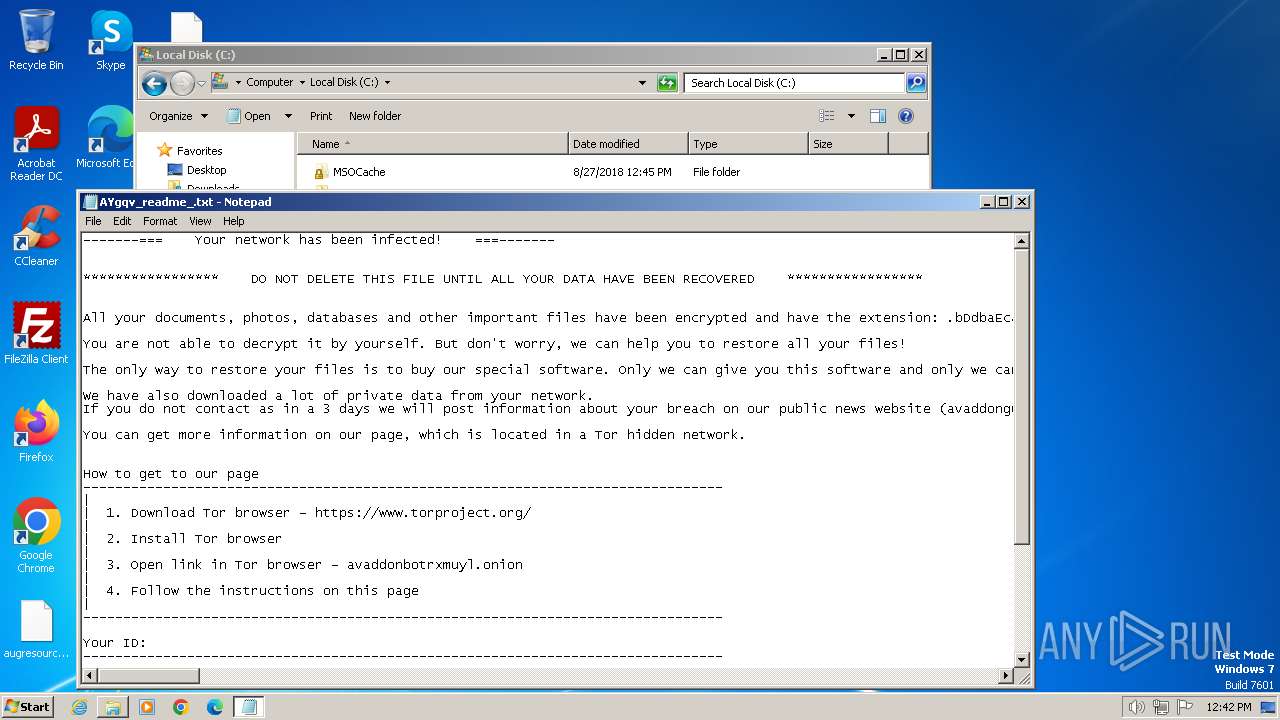
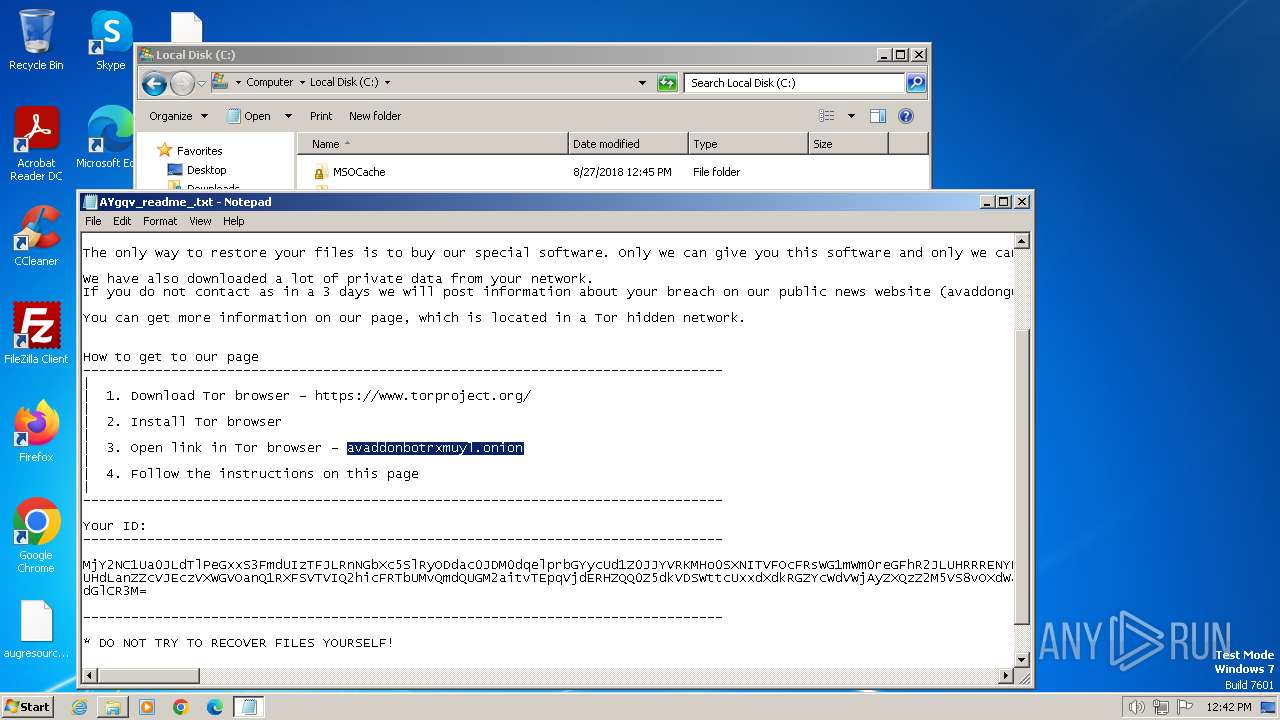
| Threats: | Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying. |
| Analysis date: | January 07, 2024, 12:41:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0B486FE0503524CFE4726A4022FA6A68 |
| SHA1: | 297DEA71D489768CE45D23B0F8A45424B469AB00 |
| SHA256: | 1228D0F04F0BA82569FC1C0609F9FD6C377A91B9EA44C1E7F9F84B2B90552DA2 |
| SSDEEP: | 24576:TCs99+OXLpMePfI8TgmBTCDqEbOpPtpFhyxfqC:5GOXLpMePfzVTCD7gPtLhSfqC |
MALICIOUS
UAC/LUA settings modification
- ab.bin.exe (PID: 2080)
Using BCDEDIT.EXE to modify recovery options
- ab.bin.exe (PID: 2080)
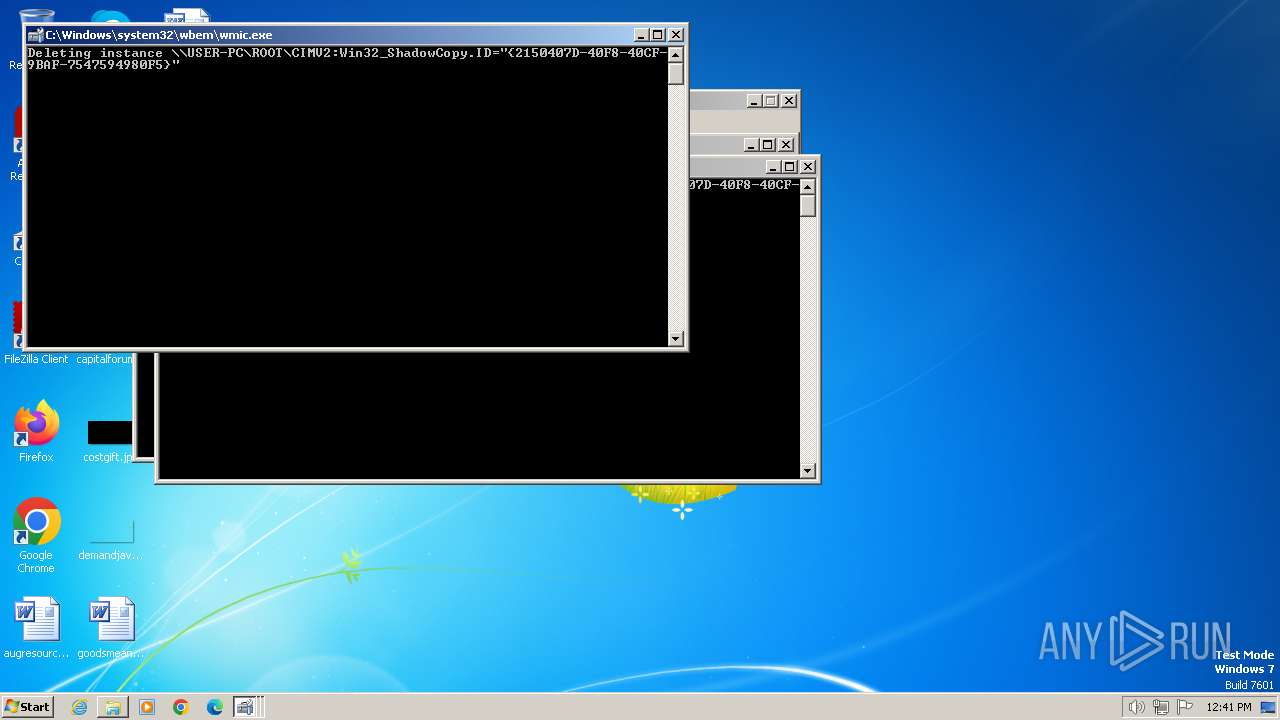
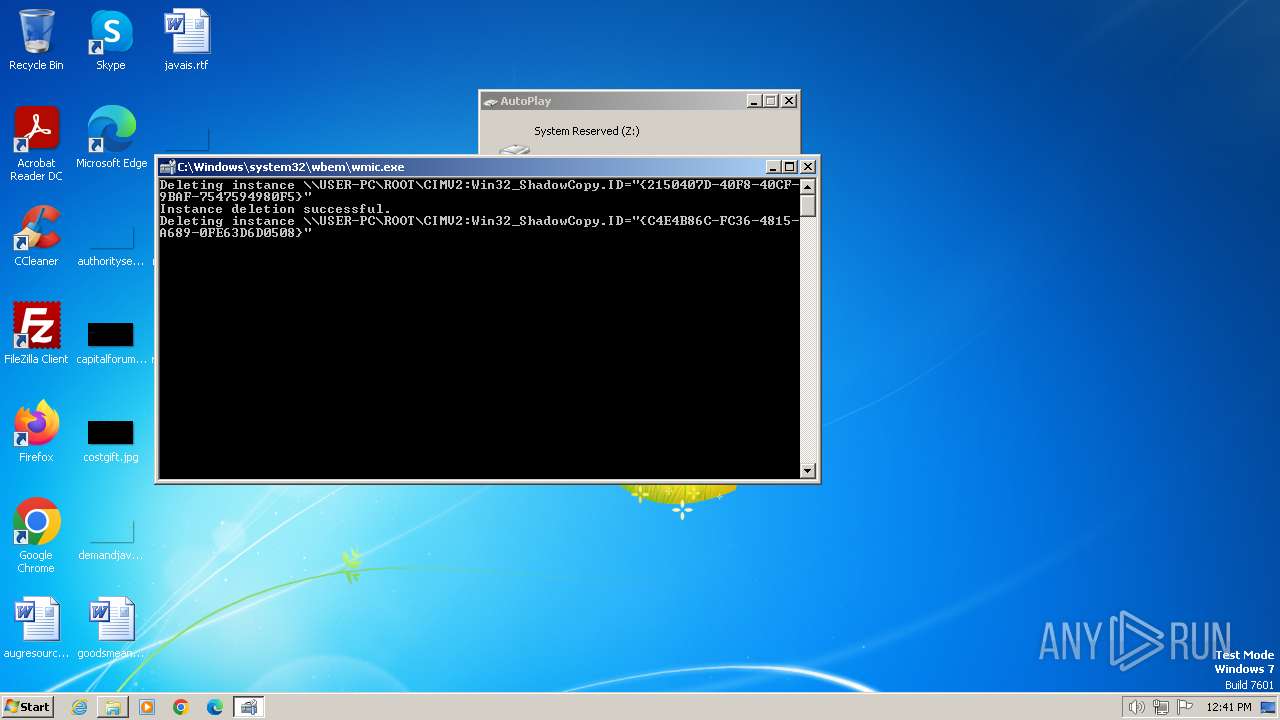
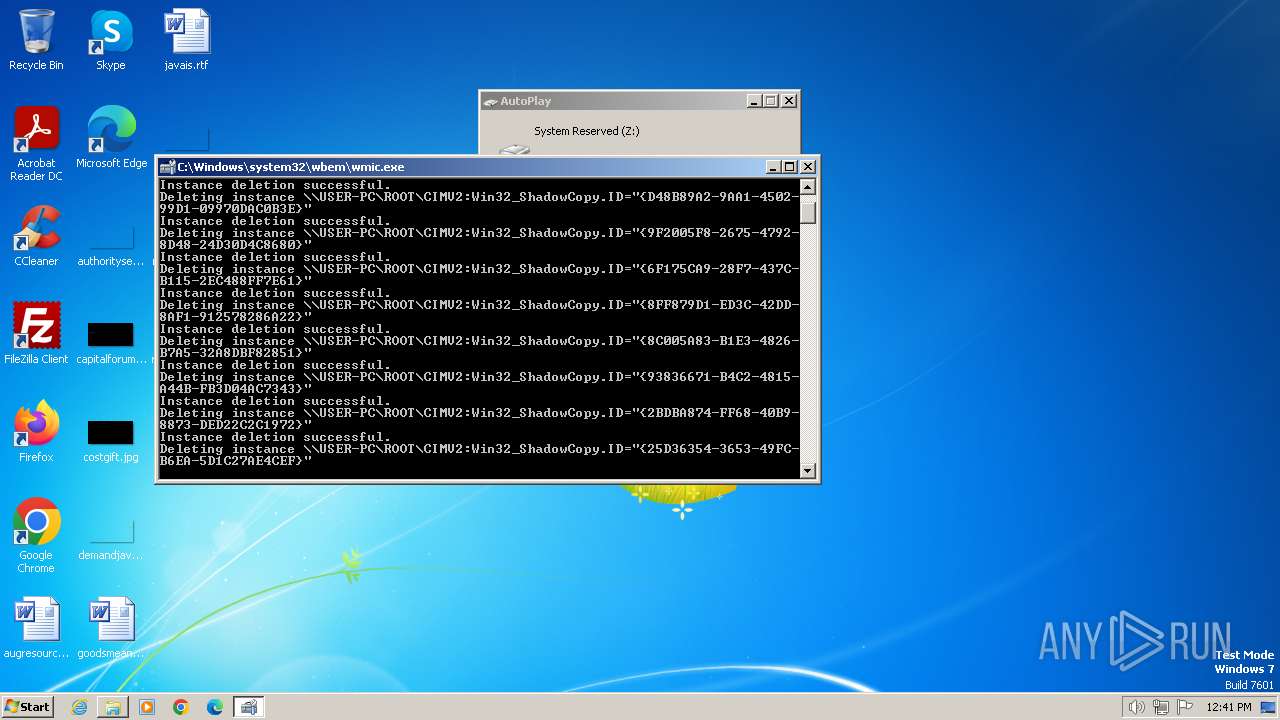
Deletes shadow copies
- ab.bin.exe (PID: 2080)
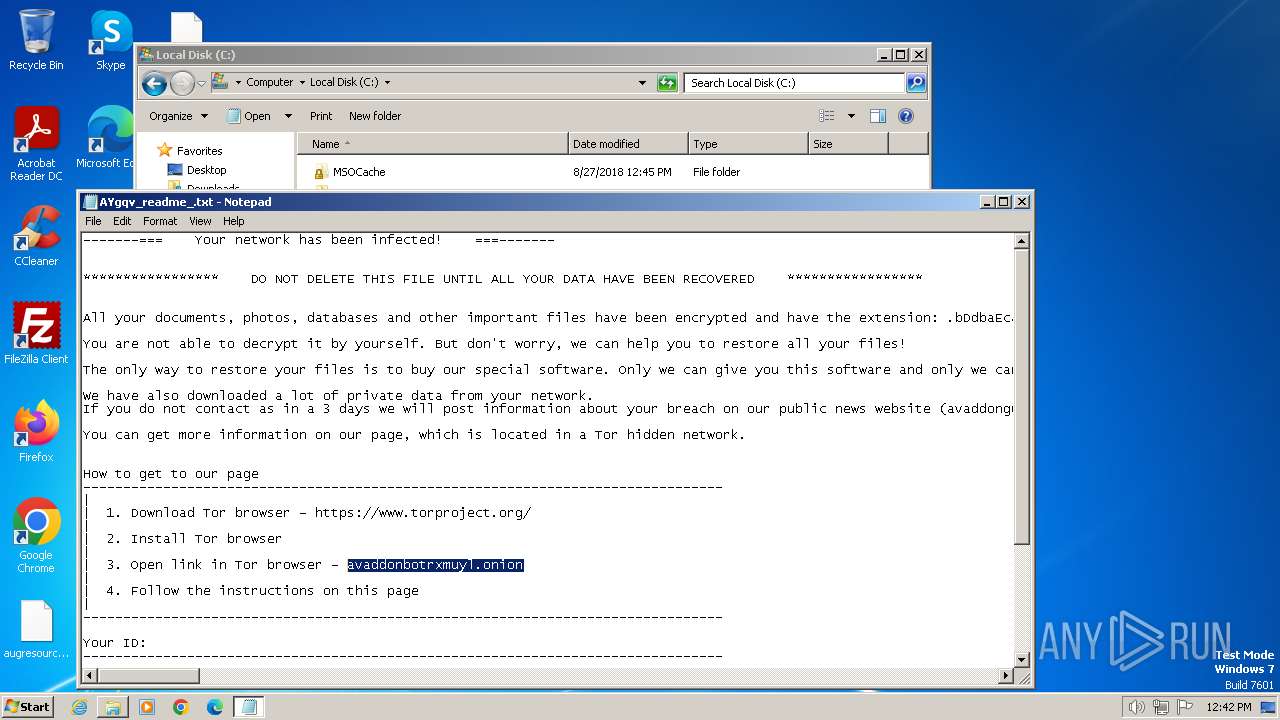
Renames files like ransomware
- ab.bin.exe (PID: 2080)
SUSPICIOUS
Reads the Internet Settings
- WMIC.exe (PID: 956)
- WMIC.exe (PID: 2788)
- WMIC.exe (PID: 1264)
- WMIC.exe (PID: 1932)
- WMIC.exe (PID: 2000)
- WMIC.exe (PID: 1596)
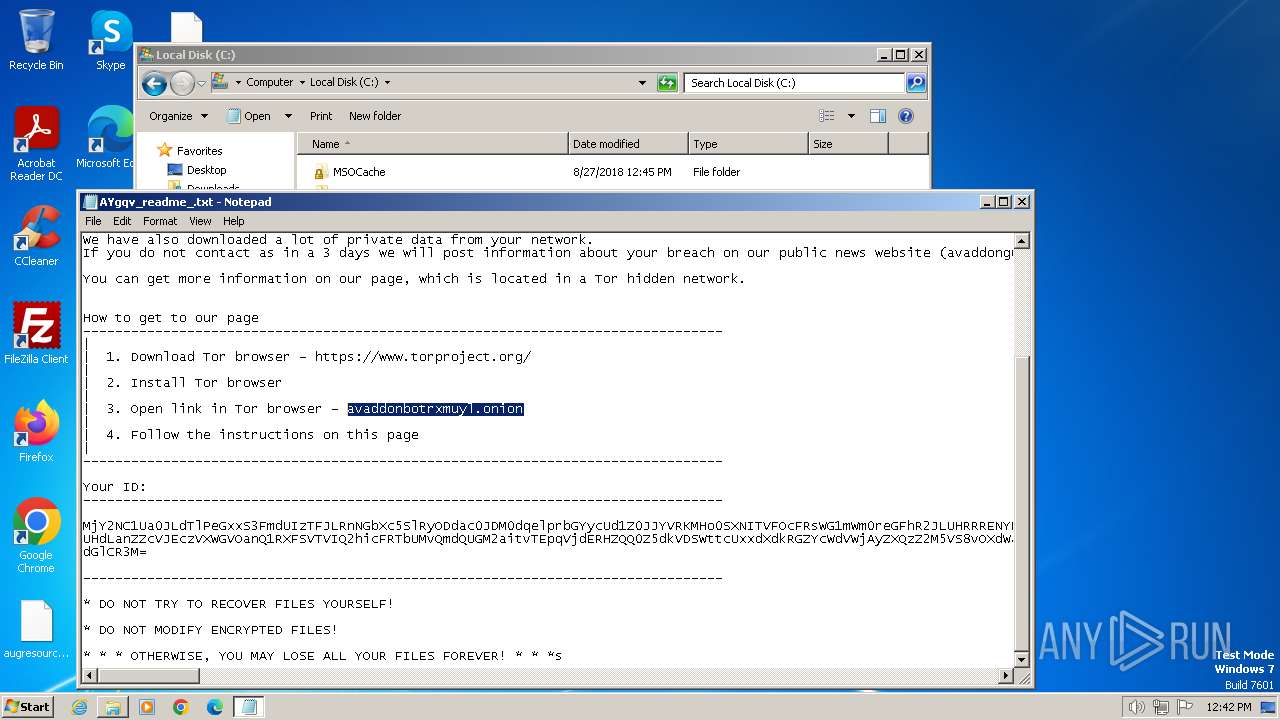
Creates files like ransomware instruction
- ab.bin.exe (PID: 2080)
Write to the desktop.ini file (may be used to cloak folders)
- ab.bin.exe (PID: 2080)
Uses pipe srvsvc via SMB (transferring data)
- ab.bin.exe (PID: 2080)
INFO
Process drops legitimate windows executable
- ab.bin.exe (PID: 2080)
Checks supported languages
- ab.bin.exe (PID: 2080)
- ab.bin.exe (PID: 3832)
Drops the executable file immediately after the start
- ab.bin.exe (PID: 2080)
Reads the computer name
- ab.bin.exe (PID: 2080)
- ab.bin.exe (PID: 3832)
Executed via WMI
- WMIC.exe (PID: 1264)
- WMIC.exe (PID: 956)
- WMIC.exe (PID: 1596)
Creates files or folders in the user directory
- ab.bin.exe (PID: 2080)
Reads the machine GUID from the registry
- ab.bin.exe (PID: 2080)
Executes as Windows Service
- VSSVC.exe (PID: 1900)
Dropped object may contain TOR URL's
- ab.bin.exe (PID: 2080)
Manual execution by a user
- notepad.exe (PID: 4084)
- rundll32.exe (PID: 1816)
The process executes via Task Scheduler
- ab.bin.exe (PID: 3832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:04:03 18:35:19+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.28 |
| CodeSize: | 535040 |
| InitializedDataSize: | 262656 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3f186 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Host Process for Windows Tasks |
| FileVersion: | 10.0.17763.831 (WinBuild.160101.0800) |
| InternalName: | taskhost.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | taskhost.exe |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 10.0.17763.831 |
Total processes
97
Monitored processes
30
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Users\admin\AppData\Local\Temp\ab.bin.exe" | C:\Users\admin\AppData\Local\Temp\ab.bin.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Tasks Exit code: 3221226540 Version: 10.0.17763.831 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 452 | wbadmin DELETE SYSTEMSTATEBACKUP | C:\Windows\System32\wbadmin.exe | — | ab.bin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® BLB Backup Exit code: 4294967293 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest | C:\Windows\System32\wbadmin.exe | — | ab.bin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® BLB Backup Exit code: 4294967293 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | bcdedit /set {default} recoveryenabled No | C:\Windows\System32\bcdedit.exe | — | ab.bin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 948 | bcdedit /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\System32\bcdedit.exe | — | ab.bin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 956 | wmic SHADOWCOPY DELETE /nointeractive | C:\Windows\System32\wbem\WMIC.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 2147749890 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1196 | wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest | C:\Windows\System32\wbadmin.exe | — | ab.bin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® BLB Backup Exit code: 4294967293 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1264 | wmic SHADOWCOPY DELETE /nointeractive | C:\Windows\System32\wbem\WMIC.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 2147749890 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | wmic SHADOWCOPY DELETE /nointeractive | C:\Windows\System32\wbem\WMIC.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 2147749890 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1644 | bcdedit /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\System32\bcdedit.exe | — | ab.bin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
4 743
Read events
3 980
Write events
115
Delete events
648
Modification events
| (PID) Process: | (2080) ab.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 1 | |||
| (PID) Process: | (2080) ab.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (2732) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\16000009 |
| Operation: | write | Name: | Element |
Value: 01 | |||
| (PID) Process: | (900) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\16000009 |
| Operation: | write | Name: | Element |
Value: 00 | |||
| (PID) Process: | (948) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\250000e0 |
| Operation: | write | Name: | Element |
Value: 0100000000000000 | |||
| (PID) Process: | (3260) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\16000009 |
| Operation: | write | Name: | Element |
Value: 00 | |||
| (PID) Process: | (1644) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\250000e0 |
| Operation: | write | Name: | Element |
Value: 0100000000000000 | |||
| (PID) Process: | (2080) ab.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2080) ab.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2080) ab.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0002 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
Executable files
3
Suspicious files
238
Text files
30
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2760 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.1.etl | binary | |
MD5:648E2E5FDFB02C71C76DB1AFDBA86A61 | SHA256:7411075B61219D67B1ECF35D34BC0AEC5F5A9CBC940F814CED51205FCABBBA8D | |||
| 2760 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.0.etl | binary | |
MD5:648E2E5FDFB02C71C76DB1AFDBA86A61 | SHA256:7411075B61219D67B1ECF35D34BC0AEC5F5A9CBC940F814CED51205FCABBBA8D | |||
| 664 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.2.etl | binary | |
MD5:E45699A3F3A6EF614FB11D78B3896BDB | SHA256:3C913A8DDC71814EE573210F85393E54CD9C9BAE15761F4B283650EE46B7DA4A | |||
| 2760 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.2.etl | binary | |
MD5:1E0623D27868EAB62E429252EF4DFE3F | SHA256:EA5B7045D3AE18132F6C1B0785803AD2A3398963E3EB9AE9BF371F4EDE284B0C | |||
| 452 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.0.etl | binary | |
MD5:E45699A3F3A6EF614FB11D78B3896BDB | SHA256:3C913A8DDC71814EE573210F85393E54CD9C9BAE15761F4B283650EE46B7DA4A | |||
| 664 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.0.etl | binary | |
MD5:1E0623D27868EAB62E429252EF4DFE3F | SHA256:EA5B7045D3AE18132F6C1B0785803AD2A3398963E3EB9AE9BF371F4EDE284B0C | |||
| 2816 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.1.etl | binary | |
MD5:CFB4B20504FF63D5B29109D18C2DB6AA | SHA256:CDD432A71A8F3B241F4AC1D87F589D15AA1C46E63A3BB2DCF122D9DB86E46C4D | |||
| 2816 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.2.etl | etl | |
MD5:648E2E5FDFB02C71C76DB1AFDBA86A61 | SHA256:7411075B61219D67B1ECF35D34BC0AEC5F5A9CBC940F814CED51205FCABBBA8D | |||
| 2528 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.3.etl | binary | |
MD5:CFB4B20504FF63D5B29109D18C2DB6AA | SHA256:CDD432A71A8F3B241F4AC1D87F589D15AA1C46E63A3BB2DCF122D9DB86E46C4D | |||
| 1196 | wbadmin.exe | C:\Windows\Logs\WindowsBackup\Wbadmin.2.etl | binary | |
MD5:CFB4B20504FF63D5B29109D18C2DB6AA | SHA256:CDD432A71A8F3B241F4AC1D87F589D15AA1C46E63A3BB2DCF122D9DB86E46C4D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
16
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.1:445 | — | — | — | unknown |
4 | System | 192.168.100.1:139 | — | — | — | unknown |
4 | System | 192.168.100.1:137 | — | — | — | unknown |
4 | System | 192.168.100.2:445 | — | — | — | whitelisted |
4 | System | 192.168.100.2:139 | — | — | — | whitelisted |
4 | System | 192.168.100.2:137 | — | — | — | whitelisted |