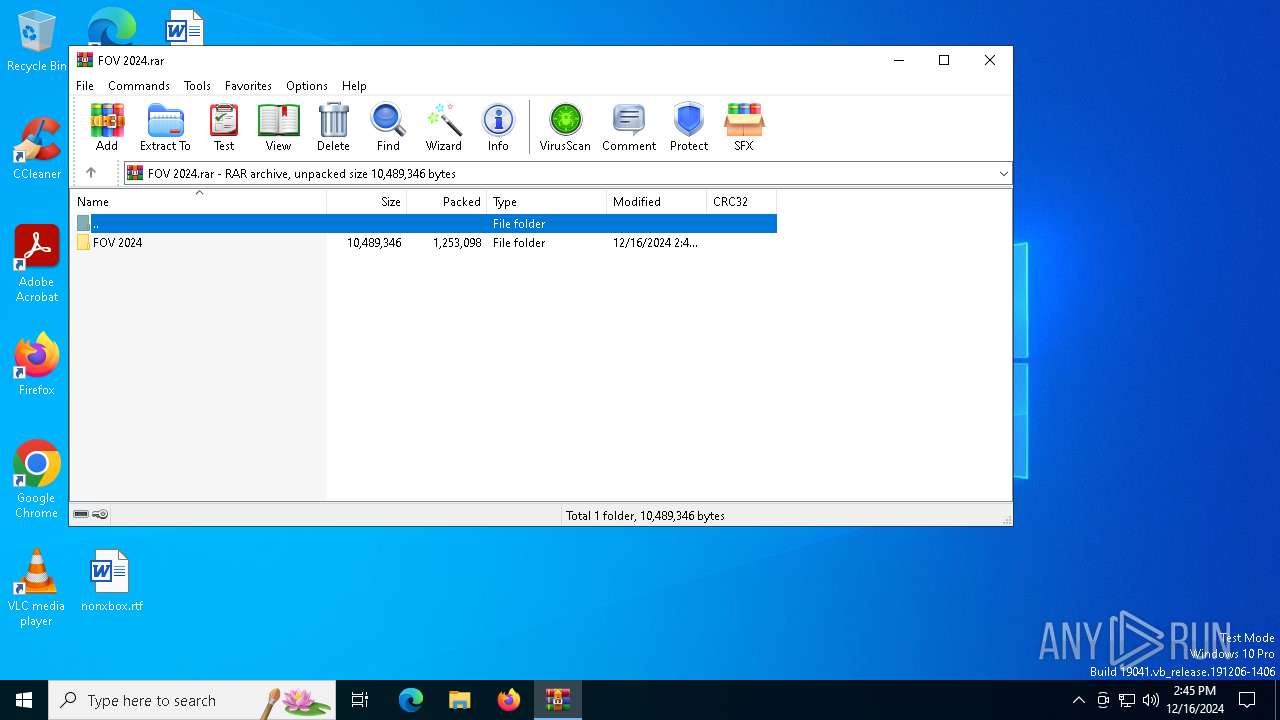
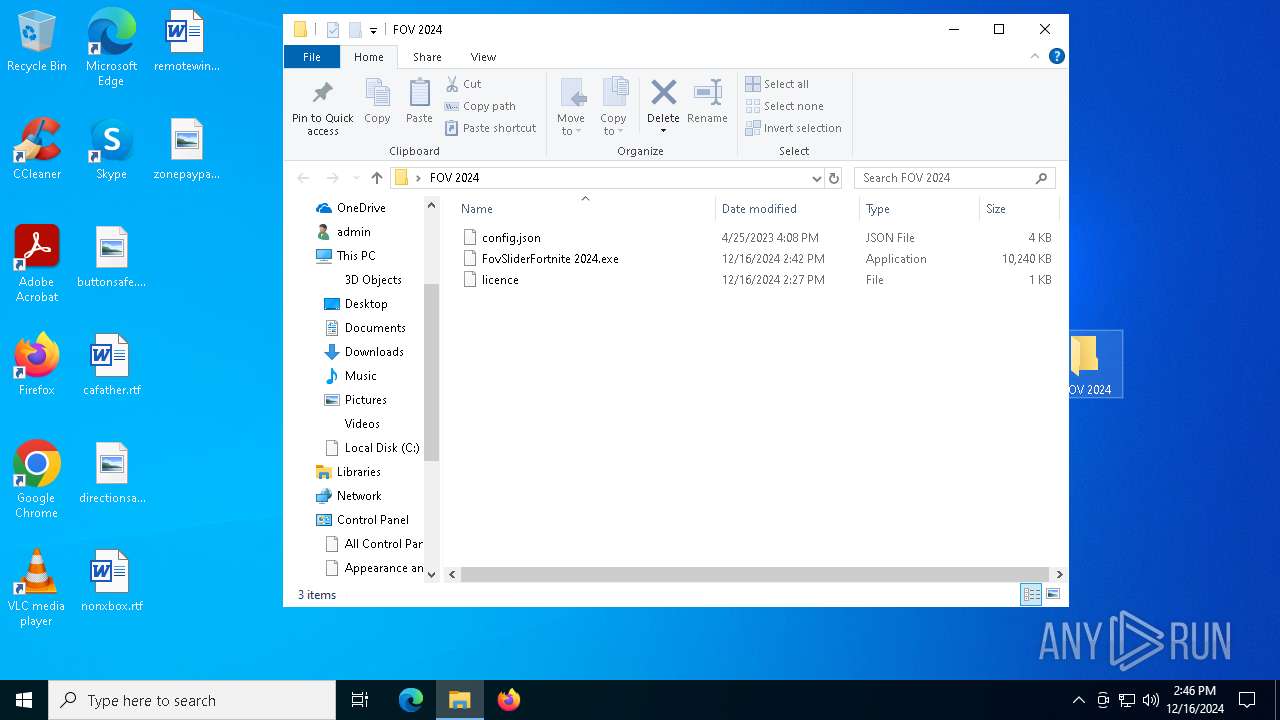
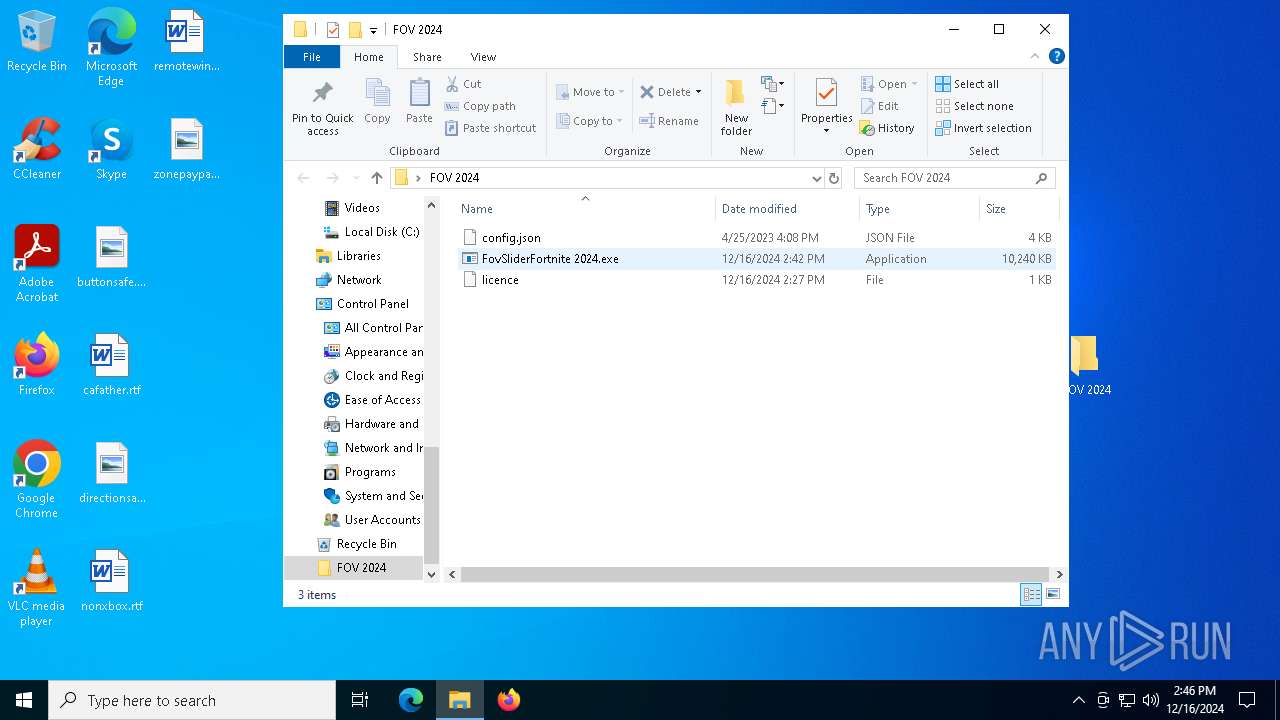
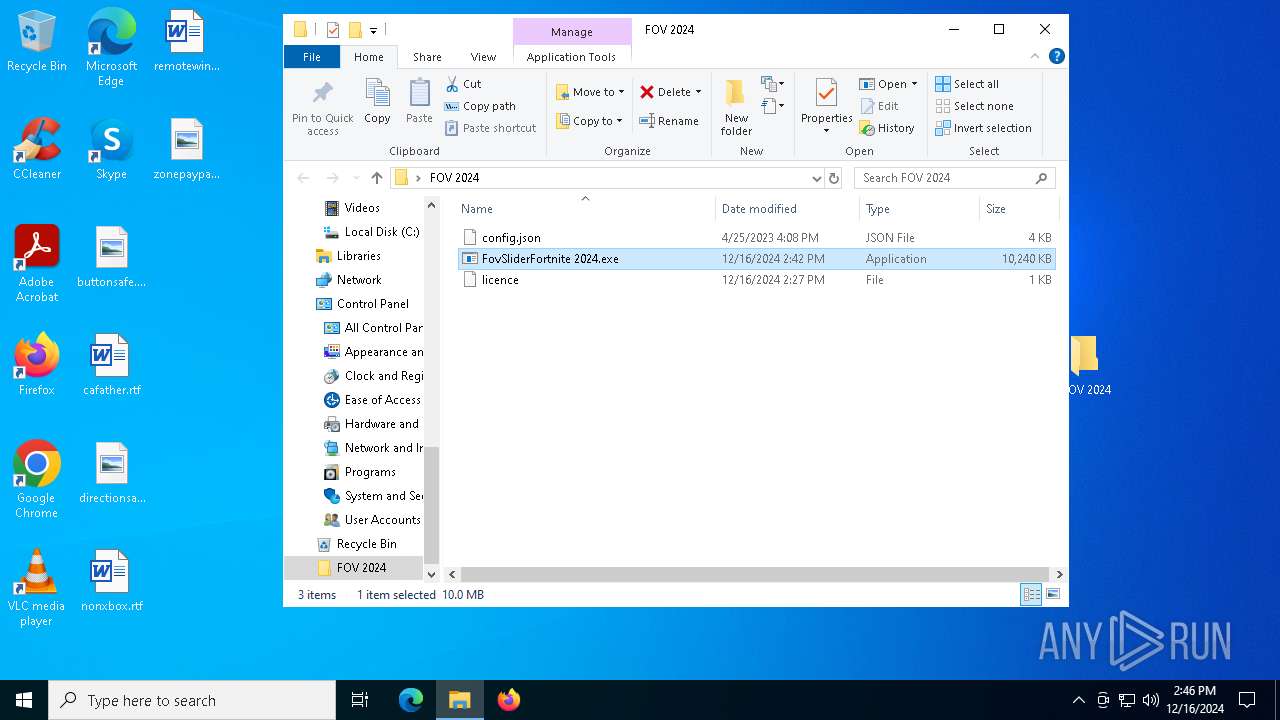
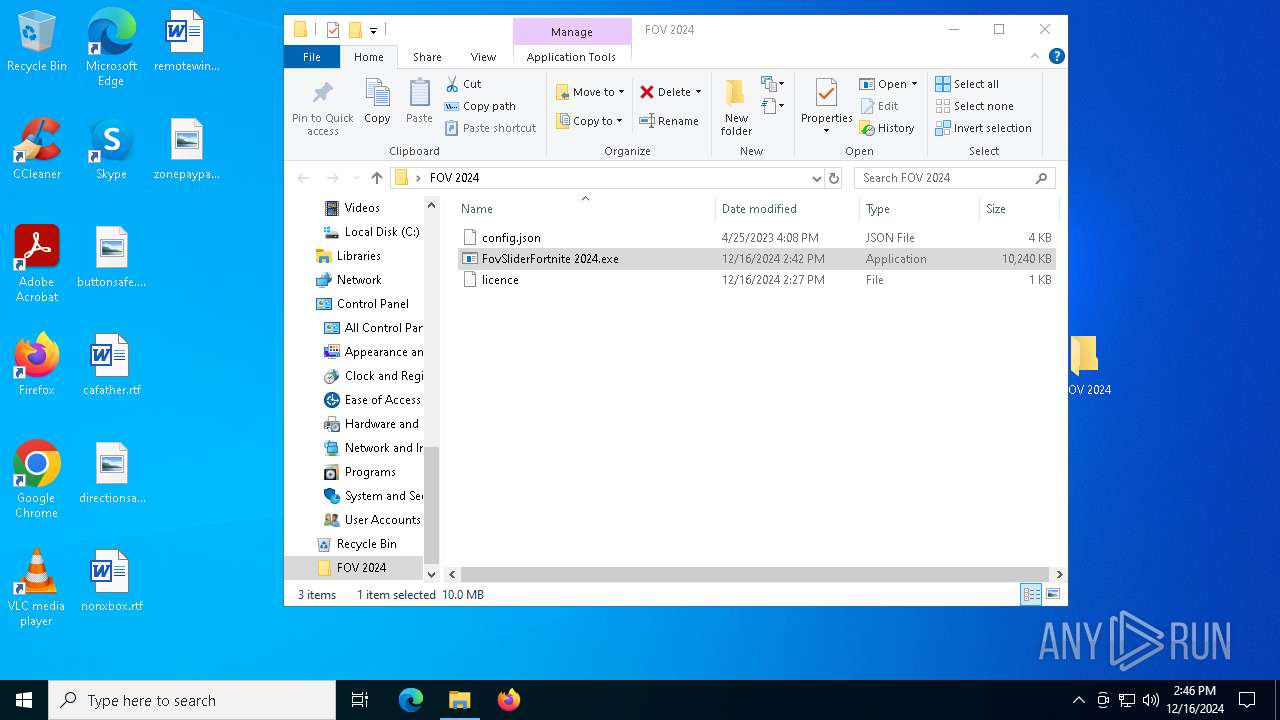
| File name: | FOV 2024.rar |
| Full analysis: | https://app.any.run/tasks/1a812438-64bb-45a6-82c9-d355d208458f |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | December 16, 2024, 14:45:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C2F0321D4689B7925F741F98B33BD31D |
| SHA1: | 5E799A84430F518447280D9DF135328F39114333 |
| SHA256: | 12231B7C238D6A85A956DE2AC7D8FE74EB0E72C7A7F520E7373883002137ED66 |
| SSDEEP: | 49152:/dYXVv3eZBDE5q/FZoI70T0iAUjONf2L59lY2NM92dOa47YqYkMoPvZC7ncjoWZ4:2XVv3e/DE5q/FZoM0TvRjONOzlYV2dOm |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6268)
Uses Task Scheduler to autorun other applications
- RUNER.EXE (PID: 4548)
- Client.exe (PID: 5256)
QUASAR has been detected (SURICATA)
- Client.exe (PID: 5256)
Connects to the CnC server
- READYME.EXE (PID: 4624)
- Client.exe (PID: 5256)
NANOCORE has been detected (SURICATA)
- READYME.EXE (PID: 4624)
ASYNCRAT has been detected (SURICATA)
- Client.exe (PID: 5256)
Changes the autorun value in the registry
- READYME.EXE (PID: 4624)
NANOCORE has been detected (YARA)
- READYME.EXE (PID: 4624)
QUASAR has been detected (YARA)
- Client.exe (PID: 5256)
SUSPICIOUS
Reads security settings of Internet Explorer
- FovSliderFortnite 2024.exe (PID: 5236)
- Client.exe (PID: 5256)
Executable content was dropped or overwritten
- FovSliderFortnite 2024.exe (PID: 5236)
- RUNER.EXE (PID: 4548)
- READYME.EXE (PID: 4624)
Starts itself from another location
- RUNER.EXE (PID: 4548)
Checks for external IP
- svchost.exe (PID: 2192)
Contacting a server suspected of hosting an CnC
- Client.exe (PID: 5256)
- READYME.EXE (PID: 4624)
Connects to unusual port
- READYME.EXE (PID: 4624)
- Client.exe (PID: 5256)
INFO
Manual execution by a user
- FovSliderFortnite 2024.exe (PID: 5236)
- msedge.exe (PID: 3984)
Sends debugging messages
- FovSliderFortnite 2024.exe (PID: 5236)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6268)
Reads the computer name
- FovSliderFortnite 2024.exe (PID: 5236)
- RUNER.EXE (PID: 4548)
- Client.exe (PID: 5256)
Checks supported languages
- FovSliderFortnite 2024.exe (PID: 5236)
- FOVSLIDERFORTNITE 2024.EXE (PID: 3608)
- RUNER.EXE (PID: 4548)
- Client.exe (PID: 5256)
- READYME.EXE (PID: 4624)
- identity_helper.exe (PID: 432)
Process checks computer location settings
- FovSliderFortnite 2024.exe (PID: 5236)
Reads the machine GUID from the registry
- RUNER.EXE (PID: 4548)
- READYME.EXE (PID: 4624)
- Client.exe (PID: 5256)
Create files in a temporary directory
- FovSliderFortnite 2024.exe (PID: 5236)
Process checks whether UAC notifications are on
- READYME.EXE (PID: 4624)
Reads the software policy settings
- Client.exe (PID: 5256)
The process uses the downloaded file
- Client.exe (PID: 5256)
Application launched itself
- msedge.exe (PID: 6428)
- msedge.exe (PID: 3984)
Attempting to use instant messaging service
- msedge.exe (PID: 3680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Nanocore
(PID) Process(4624) READYME.EXE
KeyboardLoggingTrue
BuildTime2024-12-16 14:32:43.066600
Version1.2.2.0
Mutexd3e00fab-b3f3-42d6-9f22-df36b5ccba50
DefaultGroupDefault
PrimaryConnectionHostfinalreps.airdns.org
BackupConnectionHost127.0.0.1
ConnectionPort6734
RunOnStartupTrue
RequestElevationTrue
BypassUserAccountControlFalse
ClearZoneIdentifierTrue
ClearAccessControlTrue
SetCriticalProcessFalse
PreventSystemSleepTrue
ActivateAwayModeTrue
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8000
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
Quasar
(PID) Process(5256) Client.exe
Version1.4.1
C2 (2)finalreps1.airdns.org:6665
Sub_DirSubDir
Install_NameClient.exe
Mutex9c8f8f79-03ae-4338-8c9f-21e381358327
StartupDiscord
TagOffice04
LogDirLogs
SignatureHADkR8vnxmSF/ZGKnejTSpegwsQn3S38GiUHSdIakbiO5xsNVWqLja1D3VYusTT5wvtrYS7qvGDv+xHSpyzuHaspkLuCKu2quIw8lGhfhsHjIvKrid8kvTUQyviucy3j2jgo1fNJSgYAALJAuFHZMW0m0/NGdpnntYrUJUryetHd2zBqdCA2kxMW+bxCmDljNz+cGQo4ImeEEH+Gk3k7hjz8E8mnSv74NfsEdBAyGyuRh8nMbSo7DtNFKJs7RYgkZ8/vniwvR8GbP4GlQFUsHsqvVnOaHtOIVLk2DKI1z/ph...
CertificateMIIE9DCCAtygAwIBAgIQAO/BpMgejyKCbXBkb8djqTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MTIxNDE0MzYzNloYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEApnsy1Vp+1JeVPbJSDWi+S37C2ixJN0E65xJapxCxtxNObX3LznfnFlstfv4MC6aZqvJO70bV...
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1106 |
| UncompressedSize: | 3571 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | FOV 2024/config.json |
Total processes
190
Monitored processes
60
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6476 --field-trial-handle=2356,i,18327533501890042211,10721041664413450347,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1016 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3600 --field-trial-handle=2356,i,18327533501890042211,10721041664413450347,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1416 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1352 --field-trial-handle=2356,i,18327533501890042211,10721041664413450347,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1668 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6476 --field-trial-handle=2356,i,18327533501890042211,10721041664413450347,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1668 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5880 --field-trial-handle=2356,i,18327533501890042211,10721041664413450347,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1920 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4308 --field-trial-handle=2356,i,18327533501890042211,10721041664413450347,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2092 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=video_capture.mojom.VideoCaptureService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4488 --field-trial-handle=2356,i,18327533501890042211,10721041664413450347,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2800 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x310,0x314,0x318,0x308,0x320,0x7ff81a2a5fd8,0x7ff81a2a5fe4,0x7ff81a2a5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2904 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5392 --field-trial-handle=2356,i,18327533501890042211,10721041664413450347,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
14 298
Read events
14 230
Write events
68
Delete events
0
Modification events
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\FOV 2024.rar | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
11
Suspicious files
174
Text files
48
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6268.17313\FOV 2024\config.json | binary | |
MD5:3BEA77EF233E2E32636BA889CEB489E3 | SHA256:A8732F591CBED2B2AB923236D22948F10CB7C4011D6A1018BE2FE3C8E8FBF5F2 | |||
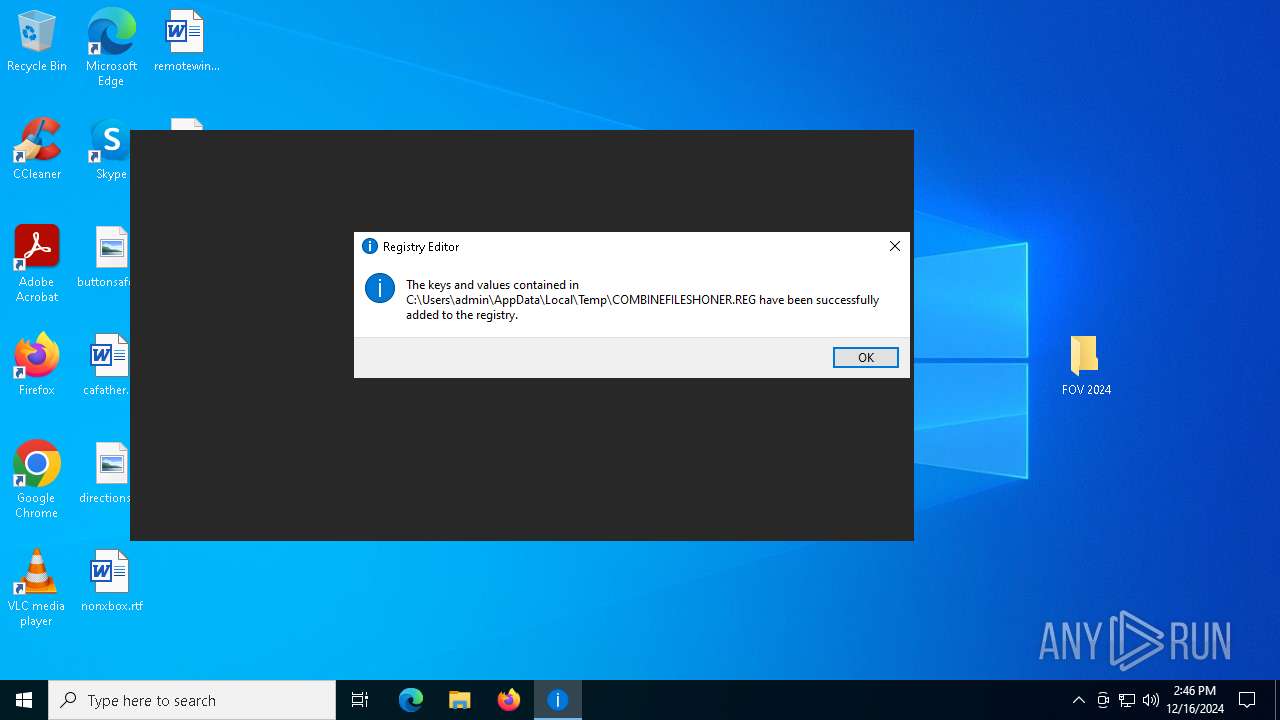
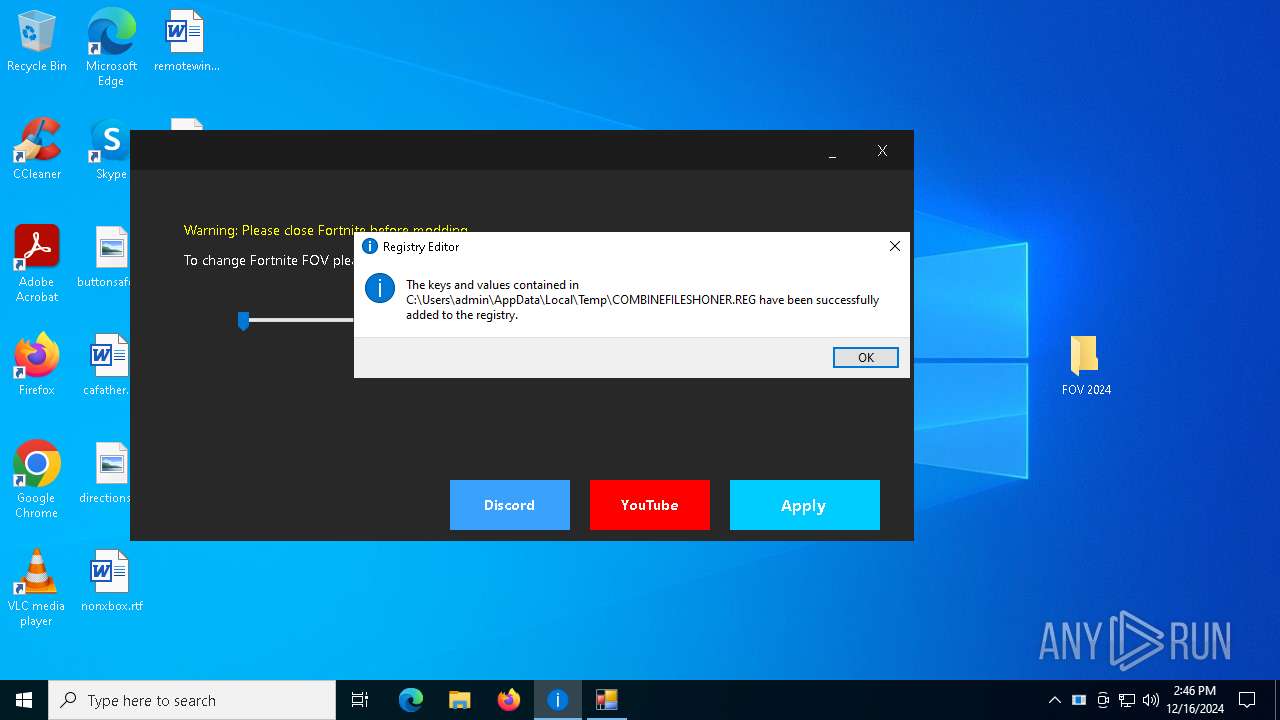
| 5236 | FovSliderFortnite 2024.exe | C:\Users\admin\AppData\Local\Temp\COMBINEFILESHONER.REG | text | |
MD5:67E15FB6C8CB04C848B5351737FF5AF4 | SHA256:3505D91A73E6F23CD50B6A5C832DDFC1EBF5458DCEC2CCA1F63675FF42503563 | |||
| 4624 | READYME.EXE | C:\Users\admin\AppData\Roaming\BB926E54-E3CA-40FD-AE90-2764341E7792\settings.bin | binary | |
MD5:4E5E92E2369688041CC82EF9650EDED2 | SHA256:F8098A6290118F2944B9E7C842BD014377D45844379F863B00D54515A8A64B48 | |||
| 3984 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF146010.TMP | — | |
MD5:— | SHA256:— | |||
| 3984 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3984 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF146010.TMP | — | |
MD5:— | SHA256:— | |||
| 3984 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3984 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF146010.TMP | — | |
MD5:— | SHA256:— | |||
| 3984 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF146010.TMP | — | |
MD5:— | SHA256:— | |||
| 3984 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
262
DNS requests
82
Threats
43
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2736 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2736 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6164 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6652 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6164 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6756 | svchost.exe | HEAD | 200 | 146.75.122.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1734860291&P2=404&P3=2&P4=UWnVqR0AT7puj4S1YP%2ffIfaOxD1%2bSlh3qFlVD7Gs79RO1dYnUR%2bi0WqlmrIITHHLg297TkW5pVGImKpskgYZZw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2736 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2736 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.160:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1752 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4624 | READYME.EXE | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.airdns .org Domain |
4624 | READYME.EXE | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.airdns .org Domain |
5256 | Client.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
5256 | Client.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (Quasar CnC) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO External IP Lookup Domain in DNS Lookup (ipwho .is) |
5256 | Client.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] QuasarRAT Successful Connection (GCM_SHA384) |
4624 | READYME.EXE | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
4624 | READYME.EXE | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT Keep-Alive Beacon (Inbound) |
4624 | READYME.EXE | Malware Command and Control Activity Detected | ET MALWARE NanoCore RAT CnC 7 |
Process | Message |
|---|---|
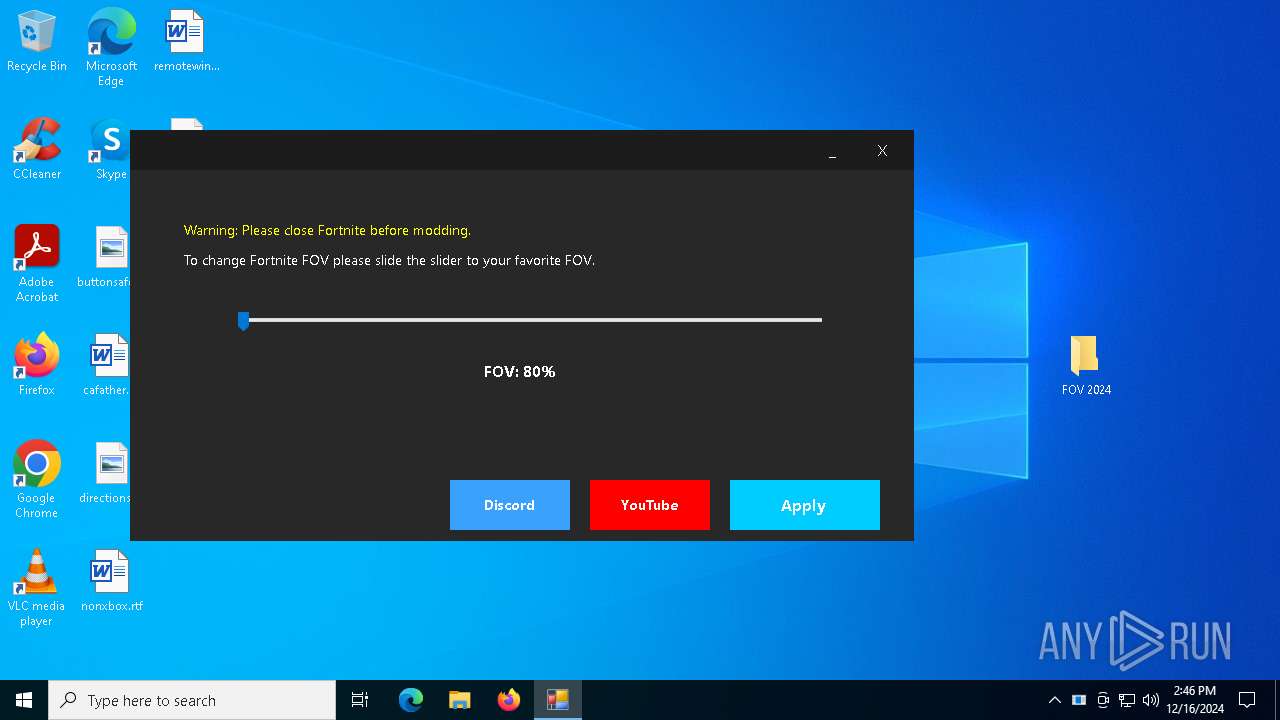
FovSliderFortnite 2024.exe | C:\Users\admin\AppData\Local\Temp\COMBINEFILESHONER.REG |
FovSliderFortnite 2024.exe | C:\Users\admin\AppData\Local\Temp\FOVSLIDERFORTNITE 2024.EXE |
FovSliderFortnite 2024.exe | C:\Users\admin\AppData\Local\Temp\READYME.EXE |
FovSliderFortnite 2024.exe | C:\Users\admin\AppData\Local\Temp\RUNER.EXE |